Product Offering

Generative AI Architecture Feedback And Improvement How Generative AI Tools Work AI SS V
This slide provides information regarding feedback and improvement layer associated with generative AI architecture. This layer comprises of several key considerations related to success of layer, techniques used for feedback collection, way through which generated data assessment is done, etc. Explore a selection of the finest Generative AI Architecture Feedback And Improvement How Generative AI Tools Work AI SS V here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Generative AI Architecture Feedback And Improvement How Generative AI Tools Work AI SS V to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide provides information regarding feedback and improvement layer associated with generative AI architecture. This layer comprises of several key considerations related to success of layer, techniques used for feedback collection, way through which generated data assessment is done, etc.

Pictory Generative AI Video Editing Tool How Generative AI Tools Work AI SS V
This slide provides information regarding PictoryAI is video generation and editing platform. It helps users to add text to videos using audio, edit captions, addition of transcription. It also highlights pros and cons associated with platform. Slidegeeks is here to make your presentations a breeze with Pictory Generative AI Video Editing Tool How Generative AI Tools Work AI SS V With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide provides information regarding PictoryAI is video generation and editing platform. It helps users to add text to videos using audio, edit captions, addition of transcription. It also highlights pros and cons associated with platform.

Replit Generative AI Tool Competent In How Generative AI Tools Work AI SS V
This slide provides information regarding replit platform which is browser-based integrated development environment for collaborative coding. It suitable for beginners who wants to learn coding with feature to run-code in real time for error detection. If you are looking for a format to display your unique thoughts, then the professionally designed Replit Generative AI Tool Competent In How Generative AI Tools Work AI SS V is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Replit Generative AI Tool Competent In How Generative AI Tools Work AI SS V and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide provides information regarding replit platform which is browser-based integrated development environment for collaborative coding. It suitable for beginners who wants to learn coding with feature to run-code in real time for error detection.
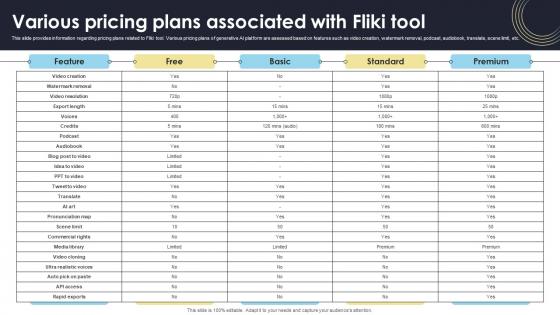
Various Pricing Plans Associated With Fliki Tool How Generative AI Tools Work AI SS V
This slide provides information regarding pricing plans related to Fliki tool. Various pricing plans of generative AI platform are assessed based on features such as video creation, watermark removal, podcast, audiobook, translate, scene limit, etc. Retrieve professionally designed Various Pricing Plans Associated With Fliki Tool How Generative AI Tools Work AI SS V to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide provides information regarding pricing plans related to Fliki tool. Various pricing plans of generative AI platform are assessed based on features such as video creation, watermark removal, podcast, audiobook, translate, scene limit, etc.
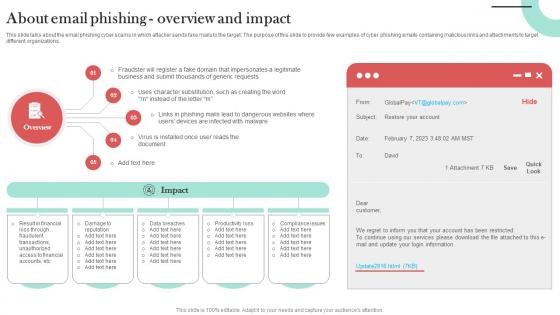
About Email Phishing Overview And Impact Man In The Middle Phishing IT
This slide talks about the email phishing cyber scams in which attacker sends fake mails to the target. The purpose of this slide to provide few examples of cyber phishing emails containing malicious links and attachments to target different organizations. Create an editable About Email Phishing Overview And Impact Man In The Middle Phishing IT that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. About Email Phishing Overview And Impact Man In The Middle Phishing IT is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide talks about the email phishing cyber scams in which attacker sends fake mails to the target. The purpose of this slide to provide few examples of cyber phishing emails containing malicious links and attachments to target different organizations.

About Phishing Attacks Overview And Impact Man In The Middle Phishing IT
This slide demonstrates the overview of cyber phishing attacks. The purpose of this slide is to talk about the effectiveness of phishing scams. This slide also outlines the issues which can be caused by phishing attacks such as disclosure of private data, etc. Get a simple yet stunning designed About Phishing Attacks Overview And Impact Man In The Middle Phishing IT. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit About Phishing Attacks Overview And Impact Man In The Middle Phishing IT can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide demonstrates the overview of cyber phishing attacks. The purpose of this slide is to talk about the effectiveness of phishing scams. This slide also outlines the issues which can be caused by phishing attacks such as disclosure of private data, etc.
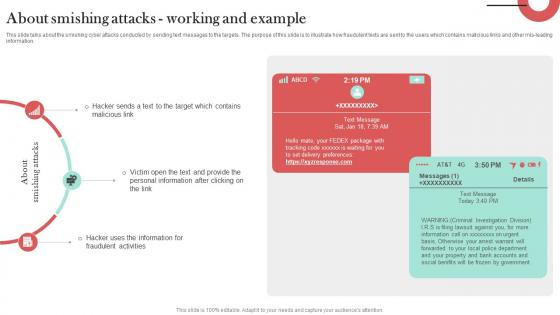
About Smishing Attacks Working And Example Man In The Middle Phishing IT
This slide talks about the smishing cyber attacks conducted by sending text messages to the targets. The purpose of this slide is to illustrate how fraudulent texts are sent to the users which contains malicious links and other mis-leading information. Slidegeeks is here to make your presentations a breeze with About Smishing Attacks Working And Example Man In The Middle Phishing IT With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide talks about the smishing cyber attacks conducted by sending text messages to the targets. The purpose of this slide is to illustrate how fraudulent texts are sent to the users which contains malicious links and other mis-leading information.

About Spear Phishing Overview And Example Man In The Middle Phishing IT
This slide talks about spear phishing cyber attacks in which scammer targets a specific individual or specific group of persons. The purpose of this slide is to illustrate example of a mail used by phishers to conduct spear phishing cyber attacks. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than About Spear Phishing Overview And Example Man In The Middle Phishing IT. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab About Spear Phishing Overview And Example Man In The Middle Phishing IT today and make your presentation stand out from the rest This slide talks about spear phishing cyber attacks in which scammer targets a specific individual or specific group of persons. The purpose of this slide is to illustrate example of a mail used by phishers to conduct spear phishing cyber attacks.
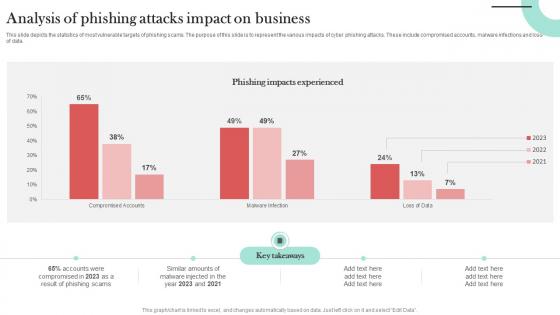
Analysis Of Phishing Attacks Impact Man In The Middle Phishing IT
This slide depicts the statistics of most vulnerable targets of phishing scams. The purpose of this slide is to represent the various impacts of cyber phishing attacks. These include compromised accounts, malware infections and loss of data. If you are looking for a format to display your unique thoughts, then the professionally designed Analysis Of Phishing Attacks Impact Man In The Middle Phishing IT is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Analysis Of Phishing Attacks Impact Man In The Middle Phishing IT and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide depicts the statistics of most vulnerable targets of phishing scams. The purpose of this slide is to represent the various impacts of cyber phishing attacks. These include compromised accounts, malware infections and loss of data.
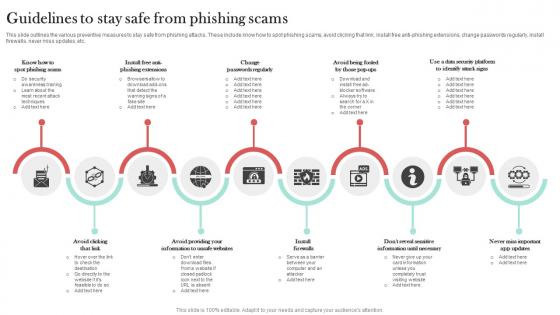
Guidelines To Stay Safe From Phishing Scams Man In The Middle Phishing IT
This slide outlines the various preventive measures to stay safe from phishing attacks. These include know how to spot phishing scams, avoid clicking that link, install free anti-phishing extensions, change passwords regularly, install firewalls, never miss updates, etc. Explore a selection of the finest Guidelines To Stay Safe From Phishing Scams Man In The Middle Phishing IT here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Guidelines To Stay Safe From Phishing Scams Man In The Middle Phishing IT to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide outlines the various preventive measures to stay safe from phishing attacks. These include know how to spot phishing scams, avoid clicking that link, install free anti-phishing extensions, change passwords regularly, install firewalls, never miss updates, etc.
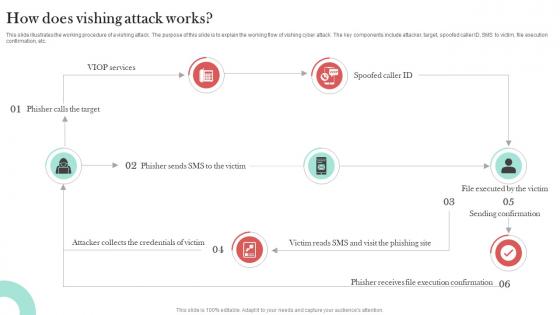
How Does Vishing Attack Works Man In The Middle Phishing IT
This slide illustrates the working procedure of a vishing attack. The purpose of this slide is to explain the working flow of vishing cyber attack. The key components include attacker, target, spoofed caller ID, SMS to victim, file execution confirmation, etc. The How Does Vishing Attack Works Man In The Middle Phishing IT is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide illustrates the working procedure of a vishing attack. The purpose of this slide is to explain the working flow of vishing cyber attack. The key components include attacker, target, spoofed caller ID, SMS to victim, file execution confirmation, etc.
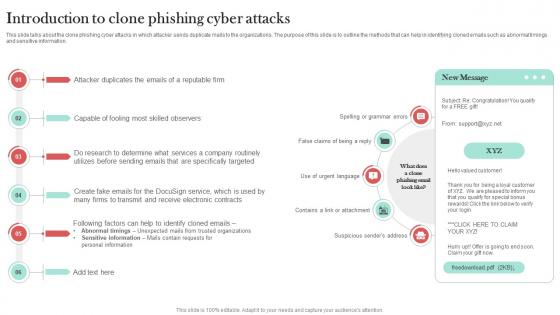
Introduction To Clone Phishing Cyber Man In The Middle Phishing IT
This slide talks about the clone phishing cyber attacks in which attacker sends duplicate mails to the organizations. The purpose of this slide is to outline the methods that can help in identifying cloned emails such as abnormal timings and sensitive information. This Introduction To Clone Phishing Cyber Man In The Middle Phishing IT from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide talks about the clone phishing cyber attacks in which attacker sends duplicate mails to the organizations. The purpose of this slide is to outline the methods that can help in identifying cloned emails such as abnormal timings and sensitive information.

Overview Of Business Disruption Caused Man In The Middle Phishing IT
This slide discusses the impact of phishing attacks on businesses. The purpose of this slide is to outline the amount of money lost by well-reputed companies due to phishing scams. The companies included are Facebook and Google, Crelan Bank in Belgium, etc. Create an editable Overview Of Business Disruption Caused Man In The Middle Phishing IT that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Overview Of Business Disruption Caused Man In The Middle Phishing IT is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide discusses the impact of phishing attacks on businesses. The purpose of this slide is to outline the amount of money lost by well-reputed companies due to phishing scams. The companies included are Facebook and Google, Crelan Bank in Belgium, etc.
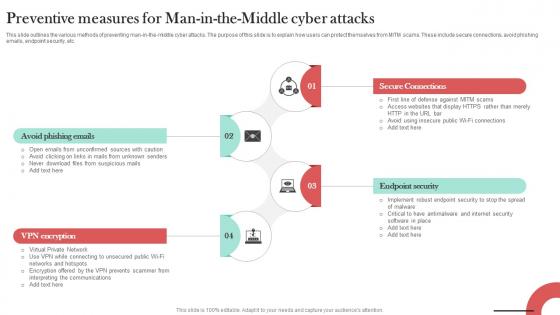
Preventive Measures For Man In The Middle Man In The Middle Phishing IT
This slide outlines the various methods of preventing man-in-the-middle cyber attacks. The purpose of this slide is to explain how users can protect themselves from MITM scams. These include secure connections, avoid phishing emails, endpoint security, etc. Get a simple yet stunning designed Preventive Measures For Man In The Middle Man In The Middle Phishing IT. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Preventive Measures For Man In The Middle Man In The Middle Phishing IT can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide outlines the various methods of preventing man-in-the-middle cyber attacks. The purpose of this slide is to explain how users can protect themselves from MITM scams. These include secure connections, avoid phishing emails, endpoint security, etc.
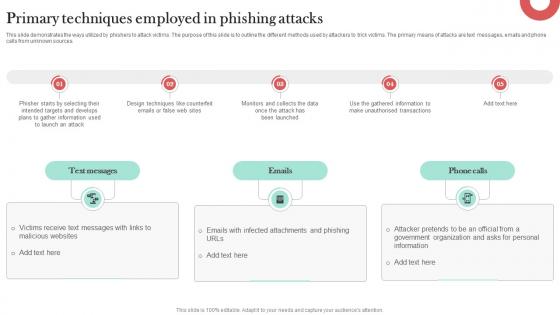
Primary Techniques Employed In Phishing Man In The Middle Phishing IT
This slide demonstrates the ways utilized by phishers to attack victims. The purpose of this slide is to outline the different methods used by attackers to trick victims. The primary means of attacks are text messages, emails and phone calls from unknown sources. Slidegeeks is here to make your presentations a breeze with Primary Techniques Employed In Phishing Man In The Middle Phishing IT With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide demonstrates the ways utilized by phishers to attack victims. The purpose of this slide is to outline the different methods used by attackers to trick victims. The primary means of attacks are text messages, emails and phone calls from unknown sources.
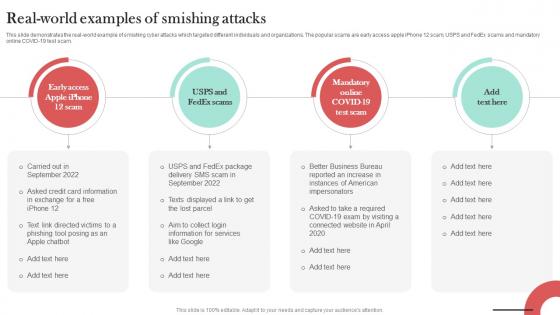
Real World Examples Of Smishing Attacks Man In The Middle Phishing IT
This slide demonstrates the real-world example of smishing cyber attacks which targeted different individuals and organizations. The popular scams are early access apple iPhone 12 scam, USPS and FedEx scams and mandatory online COVID-19 test scam. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Real World Examples Of Smishing Attacks Man In The Middle Phishing IT. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Real World Examples Of Smishing Attacks Man In The Middle Phishing IT today and make your presentation stand out from the rest This slide demonstrates the real-world example of smishing cyber attacks which targeted different individuals and organizations. The popular scams are early access apple iPhone 12 scam, USPS and FedEx scams and mandatory online COVID-19 test scam.
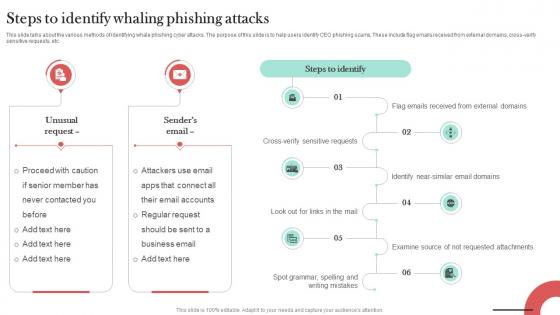
Steps To Identify Whaling Phishing Attacks Man In The Middle Phishing IT
This slide talks about the various methods of identifying whale phishing cyber attacks. The purpose of this slide is to help users identify CEO phishing scams. These include flag emails received from external domains, cross-verify sensitive requests, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Steps To Identify Whaling Phishing Attacks Man In The Middle Phishing IT is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Steps To Identify Whaling Phishing Attacks Man In The Middle Phishing IT and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide talks about the various methods of identifying whale phishing cyber attacks. The purpose of this slide is to help users identify CEO phishing scams. These include flag emails received from external domains, cross-verify sensitive requests, etc.

Warning Signs Of Pop Up Phishing Scams Man In The Middle Phishing IT
This slide outlines the various warning signs which helps in identifying pop-up phishing cyber attacks. These include terrible pop-up advertisement, warnings to act fast, immediate scan of computer virus, pop-ups are difficult to close and unpopular company names. Retrieve professionally designed Warning Signs Of Pop Up Phishing Scams Man In The Middle Phishing IT to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide outlines the various warning signs which helps in identifying pop-up phishing cyber attacks. These include terrible pop-up advertisement, warnings to act fast, immediate scan of computer virus, pop-ups are difficult to close and unpopular company names.
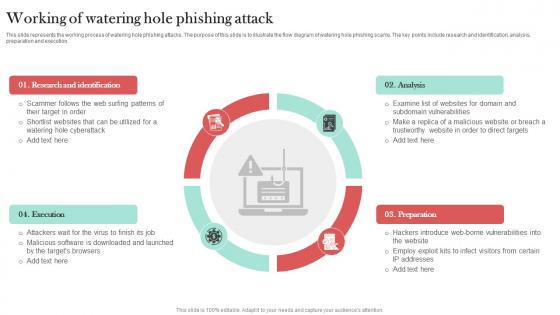
Working Of Watering Hole Phishing Attack Man In The Middle Phishing IT
This slide represents the working process of watering hole phishing attacks. The purpose of this slide is to illustrate the flow diagram of watering hole phishing scams. The key points include research and identification, analysis, preparation and execution. This Working Of Watering Hole Phishing Attack Man In The Middle Phishing IT from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide represents the working process of watering hole phishing attacks. The purpose of this slide is to illustrate the flow diagram of watering hole phishing scams. The key points include research and identification, analysis, preparation and execution.

Wine Lounge Business Plan Choosing An Ideal Business Location For Wine Bar BP SS V
This slide portrays an ideal business location for a wine bar that minimizes the risk of failure. It covers gathering and analyzing data in order to select the optimal location in terms of feasibility, economy, and future sustainability. Get a simple yet stunning designed Wine Lounge Business Plan Choosing An Ideal Business Location For Wine Bar BP SS V. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Wine Lounge Business Plan Choosing An Ideal Business Location For Wine Bar BP SS V can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide portrays an ideal business location for a wine bar that minimizes the risk of failure. It covers gathering and analyzing data in order to select the optimal location in terms of feasibility, economy, and future sustainability.
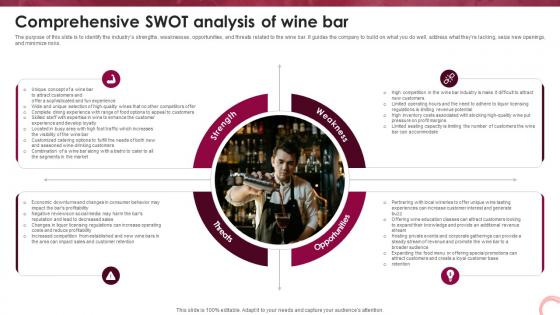
Wine Lounge Business Plan Comprehensive Swot Analysis Of Wine Bar BP SS V
The purpose of this slide is to identify the industrys strengths, weaknesses, opportunities, and threats related to the wine bar. It guides the company to build on what you do well, address what they are lacking, seize new openings, and minimize risks. Slidegeeks is here to make your presentations a breeze with Wine Lounge Business Plan Comprehensive Swot Analysis Of Wine Bar BP SS V With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first The purpose of this slide is to identify the industrys strengths, weaknesses, opportunities, and threats related to the wine bar. It guides the company to build on what you do well, address what they are lacking, seize new openings, and minimize risks.

Wine Lounge Business Plan Consolidated Statements Of Cash Flows For Wine Bar BP SS V
The slides highlight the company cash flow statement to provide a detailed picture of what happened to a business cash during a specified period. It represents net cash flow from operating, investing, and financing activities from the historical year 2023 till the forecasted the year 2027. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Wine Lounge Business Plan Consolidated Statements Of Cash Flows For Wine Bar BP SS V. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Wine Lounge Business Plan Consolidated Statements Of Cash Flows For Wine Bar BP SS V today and make your presentation stand out from the rest The slides highlight the company cash flow statement to provide a detailed picture of what happened to a business cash during a specified period. It represents net cash flow from operating, investing, and financing activities from the historical year 2023 till the forecasted the year 2027.
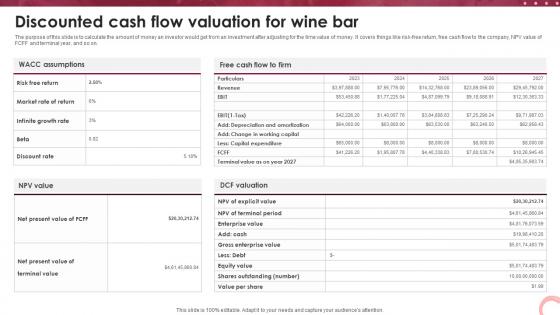
Wine Lounge Business Plan Discounted Cash Flow Valuation For Wine Bar BP SS V
The purpose of this slide is to calculate the amount of money an investor would get from an investment after adjusting for the time value of money. It covers things like risk-free return, free cash flow to the company, NPV value of FCFF and terminal year, and so on. If you are looking for a format to display your unique thoughts, then the professionally designed Wine Lounge Business Plan Discounted Cash Flow Valuation For Wine Bar BP SS V is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Wine Lounge Business Plan Discounted Cash Flow Valuation For Wine Bar BP SS V and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. The purpose of this slide is to calculate the amount of money an investor would get from an investment after adjusting for the time value of money. It covers things like risk-free return, free cash flow to the company, NPV value of FCFF and terminal year, and so on.

Wine Lounge Business Plan Key Financial Assumptions For Wine Bar BP SS V
This slide provides a glimpse of important financial assumptions that are to be made while setting wine bar in terms of income, expense, and balance sheet. The computations are based on market trends and conditions prevailing in the wine industry. Explore a selection of the finest Wine Lounge Business Plan Key Financial Assumptions For Wine Bar BP SS V here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Wine Lounge Business Plan Key Financial Assumptions For Wine Bar BP SS V to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide provides a glimpse of important financial assumptions that are to be made while setting wine bar in terms of income, expense, and balance sheet. The computations are based on market trends and conditions prevailing in the wine industry.

Increasing Business Awareness Advancing Impact Of Strategic Insurance Marketing Strategy SS V
This slide analyzes the performance of key metrics of insurance business after the implementation of strategic marketing plan to promote business. It includes information about metrics such as renewal or retention, customer acquisition cost, number of referrals, social media engagement and website traffic. Create an editable Increasing Business Awareness Advancing Impact Of Strategic Insurance Marketing Strategy SS V that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Increasing Business Awareness Advancing Impact Of Strategic Insurance Marketing Strategy SS V is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide analyzes the performance of key metrics of insurance business after the implementation of strategic marketing plan to promote business. It includes information about metrics such as renewal or retention, customer acquisition cost, number of referrals, social media engagement and website traffic.

Increasing Business Awareness Establishing Effective Partnerships With Local Strategy SS V
This slide outlines a partnership program for establishing effective partnerships with local businesses to promote insurance companies and sell policies. It includes information about aspects such as partner name, partnership benefits, target audience and duration. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Increasing Business Awareness Establishing Effective Partnerships With Local Strategy SS V. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Increasing Business Awareness Establishing Effective Partnerships With Local Strategy SS V today and make your presentation stand out from the rest This slide outlines a partnership program for establishing effective partnerships with local businesses to promote insurance companies and sell policies. It includes information about aspects such as partner name, partnership benefits, target audience and duration.

Increasing Business Awareness Expected Benefits Of Optimizing Insurance Strategy SS V
This slide defines the importance and objectives of insurance marketing to increase overall business performance. It includes objectives such as about customer retention, brand awareness, market share, communication and building trust. If you are looking for a format to display your unique thoughts, then the professionally designed Increasing Business Awareness Expected Benefits Of Optimizing Insurance Strategy SS V is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Increasing Business Awareness Expected Benefits Of Optimizing Insurance Strategy SS V and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide defines the importance and objectives of insurance marketing to increase overall business performance. It includes objectives such as about customer retention, brand awareness, market share, communication and building trust.

Increasing Business Awareness Setting Up Unique Identity Of Brand To Create Strategy SS V
This slide presents an outline of a plan to create a unique value proposition and set a brand identity to stand out amongst the competition. It includes information about brand values, unique value propositions, logo concepts, and taglines. If you are looking for a format to display your unique thoughts, then the professionally designed Increasing Business Awareness Setting Up Unique Identity Of Brand To Create Strategy SS V is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Increasing Business Awareness Setting Up Unique Identity Of Brand To Create Strategy SS V and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide presents an outline of a plan to create a unique value proposition and set a brand identity to stand out amongst the competition. It includes information about brand values, unique value propositions, logo concepts, and taglines.
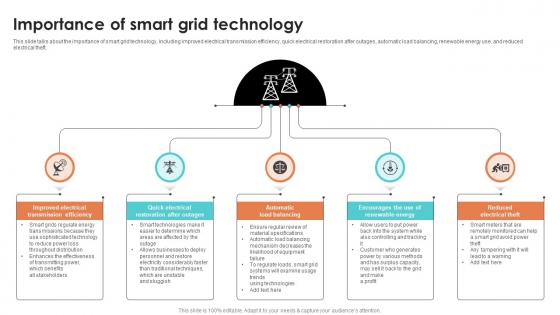
Importance Of Smart Grid Technology Smart Grid Working
This slide talks about the importance of smart grid technology, including improved electrical transmission efficiency, quick electrical restoration after outages, automatic load balancing, renewable energy use, and reduced electrical theft. If you are looking for a format to display your unique thoughts, then the professionally designed Importance Of Smart Grid Technology Smart Grid Working is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Importance Of Smart Grid Technology Smart Grid Working and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide talks about the importance of smart grid technology, including improved electrical transmission efficiency, quick electrical restoration after outages, automatic load balancing, renewable energy use, and reduced electrical theft.
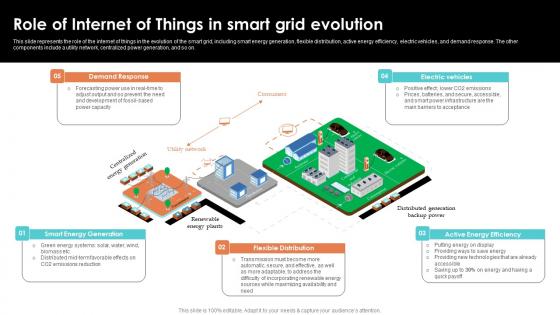
Role Of Internet Of Things In Smart Grid Evolution Smart Grid Working
This slide represents the role of the internet of things in the evolution of the smart grid, including smart energy generation, flexible distribution, active energy efficiency, electric vehicles, and demand response. The other components include a utility network, centralized power generation, and so on. Retrieve professionally designed Role Of Internet Of Things In Smart Grid Evolution Smart Grid Working to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide represents the role of the internet of things in the evolution of the smart grid, including smart energy generation, flexible distribution, active energy efficiency, electric vehicles, and demand response. The other components include a utility network, centralized power generation, and so on.
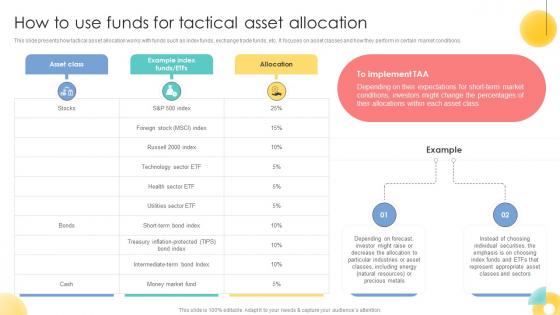
How To Use Funds For Tactical Asset Allocation Strategic Investment Plan For Optimizing Risk SS V
This slide presents how tactical asset allocation works with funds such as index funds, exchange trade funds, etc. It focuses on asset classes and how they perform in certain market conditions.Explore a selection of the finest How To Use Funds For Tactical Asset Allocation Strategic Investment Plan For Optimizing Risk SS V here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our How To Use Funds For Tactical Asset Allocation Strategic Investment Plan For Optimizing Risk SS V to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide presents how tactical asset allocation works with funds such as index funds, exchange trade funds, etc. It focuses on asset classes and how they perform in certain market conditions.

A49 Zero Trust Network Access Architecture Overview
This slide gives an overview of zero trust network access architecture. The purpose of this slide is to showcase the ZTNA architecture and its benefits, covering granting safe and fast access, protecting reliable remote access, protecting sensitive data and apps, stopping insider threats, and so on. Create an editable A49 Zero Trust Network Access Architecture Overview that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. A49 Zero Trust Network Access Architecture Overview is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide gives an overview of zero trust network access architecture. The purpose of this slide is to showcase the ZTNA architecture and its benefits, covering granting safe and fast access, protecting reliable remote access, protecting sensitive data and apps, stopping insider threats, and so on.

On Ramp Option 2 Applications And Data Zero Trust Network Access
This slide describes the second on-ramp option, which is the applications and data of ZTNA implementation. The purpose of this slide is to give an overview of practices and technologies used in this approach, such as data classification, data loss prevention, authentication and authorization of microservices, container security, etc. Slidegeeks is here to make your presentations a breeze with On Ramp Option 2 Applications And Data Zero Trust Network Access With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide describes the second on-ramp option, which is the applications and data of ZTNA implementation. The purpose of this slide is to give an overview of practices and technologies used in this approach, such as data classification, data loss prevention, authentication and authorization of microservices, container security, etc.

On Ramp Option 3 The Network Zero Trust Network Access
This slide outlines the third on-ramp option for ZTNA deployment, which is the network. The purpose of this slide is to showcase the practices and technologies used in this approach, including automation, microsegmentation, stateful session management, network encryption and secure routing, and so on. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than On Ramp Option 3 The Network Zero Trust Network Access. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab On Ramp Option 3 The Network Zero Trust Network Access today and make your presentation stand out from the rest This slide outlines the third on-ramp option for ZTNA deployment, which is the network. The purpose of this slide is to showcase the practices and technologies used in this approach, including automation, microsegmentation, stateful session management, network encryption and secure routing, and so on.
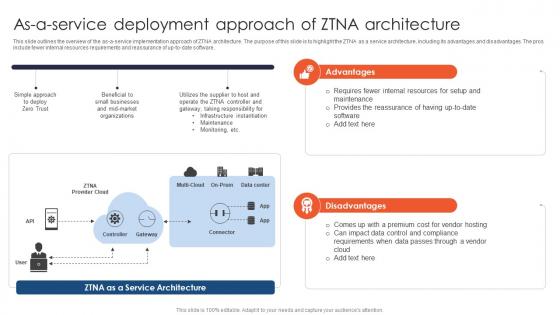
Zero Trust Network Access As A Service Deployment Approach Of ZTNA Architecture
This slide outlines the overview of the as-a-service implementation approach of ZTNA architecture. The purpose of this slide is to highlight the ZTNA as a service architecture, including its advantages and disadvantages. The pros include fewer internal resources requirements and reassurance of up-to-date software. If you are looking for a format to display your unique thoughts, then the professionally designed Zero Trust Network Access As A Service Deployment Approach Of ZTNA Architecture is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Zero Trust Network Access As A Service Deployment Approach Of ZTNA Architecture and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide outlines the overview of the as-a-service implementation approach of ZTNA architecture. The purpose of this slide is to highlight the ZTNA as a service architecture, including its advantages and disadvantages. The pros include fewer internal resources requirements and reassurance of up-to-date software.

Zero Trust Network Access External Components Of Zero Trust Network Architecture
This slide gives an overview of external elements of zero trust network architecture. The purpose of this slide is to showcase the various external components and their working, covering CDM systems, industry compliance, threat intelligence, activity logs, data access policy, and so on. Retrieve professionally designed Zero Trust Network Access External Components Of Zero Trust Network Architecture to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide gives an overview of external elements of zero trust network architecture. The purpose of this slide is to showcase the various external components and their working, covering CDM systems, industry compliance, threat intelligence, activity logs, data access policy, and so on.

Zero Trust Network Access Key Points To Choose Zero Trust Solution
This slide highlights the main criteria while choosing the right zero trust solution for the organization. The purpose of this slide is to showcase the key points the businesses should keep in mind while selecting the ZTNA vendor. The main points include vendor support, zero trust technology type, and so on. This Zero Trust Network Access Key Points To Choose Zero Trust Solution from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide highlights the main criteria while choosing the right zero trust solution for the organization. The purpose of this slide is to showcase the key points the businesses should keep in mind while selecting the ZTNA vendor. The main points include vendor support, zero trust technology type, and so on.
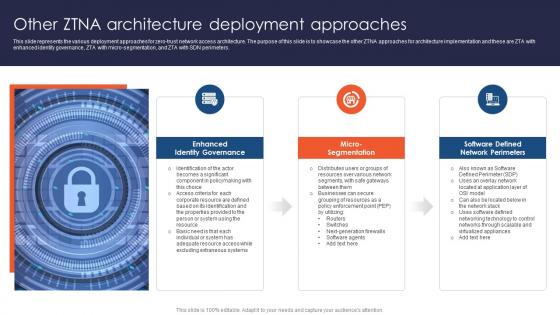
Zero Trust Network Access Other ZTNA Architecture Deployment Approaches
This slide represents the various deployment approaches for zero-trust network access architecture. The purpose of this slide is to showcase the other ZTNA approaches for architecture implementation and these are ZTA with enhanced identity governance, ZTA with micro-segmentation, and ZTA with SDN perimeters. Create an editable Zero Trust Network Access Other ZTNA Architecture Deployment Approaches that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Zero Trust Network Access Other ZTNA Architecture Deployment Approaches is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide represents the various deployment approaches for zero-trust network access architecture. The purpose of this slide is to showcase the other ZTNA approaches for architecture implementation and these are ZTA with enhanced identity governance, ZTA with micro-segmentation, and ZTA with SDN perimeters.

Zero Trust Network Access Solutions To Overcome ZTNA Implementation Challenges
This slide talks about the various solutions to overcome the ZTNA deployment challenges. The purpose of this slide is to showcase the remedies to overcome ZTNA obstacles. The leading solutions include running zero-trust trials, starting small, scaling slowly, and keeping people and zero trust in mind. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Zero Trust Network Access Solutions To Overcome ZTNA Implementation Challenges. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Zero Trust Network Access Solutions To Overcome ZTNA Implementation Challenges today and make your presentation stand out from the rest This slide talks about the various solutions to overcome the ZTNA deployment challenges. The purpose of this slide is to showcase the remedies to overcome ZTNA obstacles. The leading solutions include running zero-trust trials, starting small, scaling slowly, and keeping people and zero trust in mind.

Zero Trust Network Access Vs Zero Trust Architecture Ppt File Infographic Template
This slide represents the comparison between zero-trust network access and zero-trust architecture. The purpose of this slide is to highlight the key differences between ZTNA and ZTA based on definition, focus, objective, technologies, and implementation. Retrieve professionally designed Zero Trust Network Access Vs Zero Trust Architecture Ppt File Infographic Template to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide represents the comparison between zero-trust network access and zero-trust architecture. The purpose of this slide is to highlight the key differences between ZTNA and ZTA based on definition, focus, objective, technologies, and implementation.
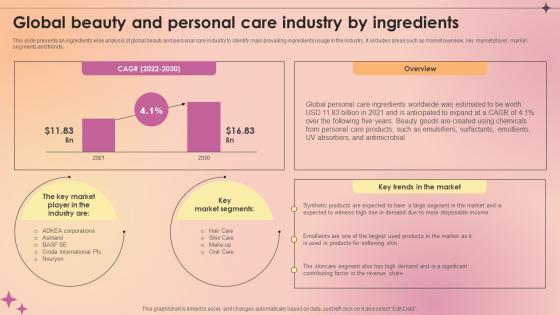
Global Beauty And Personal Care Industry By Ingredients Makeup And Skincare Market IR SS V
This slide presents an ingredients wise analysis of global beauty and personal care industry to identify main prevailing ingredients usage in the industry. It includes areas such as market overview, key market player, market segments and trends. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Global Beauty And Personal Care Industry By Ingredients Makeup And Skincare Market IR SS V. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Global Beauty And Personal Care Industry By Ingredients Makeup And Skincare Market IR SS V today and make your presentation stand out from the rest This slide presents an ingredients wise analysis of global beauty and personal care industry to identify main prevailing ingredients usage in the industry. It includes areas such as market overview, key market player, market segments and trends.
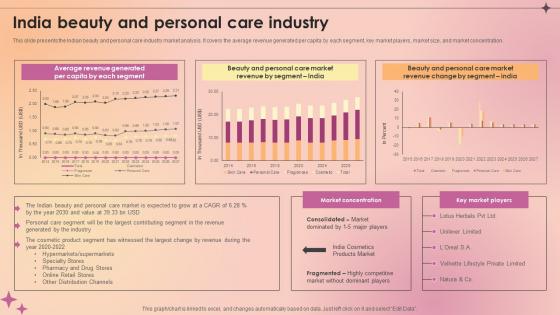
India Beauty And Personal Care Industry Makeup And Skincare Market IR SS V
This slide presents the Indian beauty and personal care industry market analysis. It covers the average revenue generated per capita by each segment, key market players, market size, and market concentration. If you are looking for a format to display your unique thoughts, then the professionally designed India Beauty And Personal Care Industry Makeup And Skincare Market IR SS V is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download India Beauty And Personal Care Industry Makeup And Skincare Market IR SS V and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide presents the Indian beauty and personal care industry market analysis. It covers the average revenue generated per capita by each segment, key market players, market size, and market concentration.

CASB 2 0 IT Advantages And Disadvantages Of Proxy Based Deployment
This slide represents the benefits and drawbacks of proxy-based CASB deployment. The purpose of this slide is to showcase the various pros and cons of proxy-based cloud access security brokers and the advantages cover flexibility, secure SaaS applications, and so on. Create an editable CASB 2 0 IT Advantages And Disadvantages Of Proxy Based Deployment that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. CASB 2 0 IT Advantages And Disadvantages Of Proxy Based Deployment is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide represents the benefits and drawbacks of proxy-based CASB deployment. The purpose of this slide is to showcase the various pros and cons of proxy-based cloud access security brokers and the advantages cover flexibility, secure SaaS applications, and so on.

CASB 2 0 IT Best Practices To Implement Cloud Access Security Broker
This slide represents the best practices for implementing a cloud access security broker within an organization. The purpose of this slide is to demonstrate the best practices and their possible impact on the overall business operations. The best practices include building visibility, forecasting risk and releasing CASB. Get a simple yet stunning designed CASB 2 0 IT Best Practices To Implement Cloud Access Security Broker. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit CASB 2 0 IT Best Practices To Implement Cloud Access Security Broker can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide represents the best practices for implementing a cloud access security broker within an organization. The purpose of this slide is to demonstrate the best practices and their possible impact on the overall business operations. The best practices include building visibility, forecasting risk and releasing CASB.

CASB 2 0 IT CASB As A Streamline Endpoint Protection Solution
This slide outlines how cloud access security broker 2.0 streamlines endpoint protection. The purpose of this slide is to showcase how CASB 2.0 improves endpoint security for streamlined deployment. It also includes the features of CASB 2.0 and endpoint security integration. Slidegeeks is here to make your presentations a breeze with CASB 2 0 IT CASB As A Streamline Endpoint Protection Solution With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide outlines how cloud access security broker 2.0 streamlines endpoint protection. The purpose of this slide is to showcase how CASB 2.0 improves endpoint security for streamlined deployment. It also includes the features of CASB 2.0 and endpoint security integration.

CASB 2 0 IT CASB Deployment With Optional Components Pricing
This slide outlines the pricing of CASB deployment with optional or add-on components. The purpose of this slide is to showcase the pricing of additional components in CASB deployment, including data security subscription, support, threat protection subscription, data retention, and so on. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than CASB 2 0 IT CASB Deployment With Optional Components Pricing. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab CASB 2 0 IT CASB Deployment With Optional Components Pricing today and make your presentation stand out from the rest This slide outlines the pricing of CASB deployment with optional or add-on components. The purpose of this slide is to showcase the pricing of additional components in CASB deployment, including data security subscription, support, threat protection subscription, data retention, and so on.

CASB 2 0 IT Cloud Security Standards And Control Frameworks
This slide provides an overview of the cloud security protocols and control frameworks. The purpose of this slide is to showcase the various information security standards and control frameworks, including ISO-27001, ISO-27017, ISO-27018, GDPR, SOC reporting, PCI DSS, and HIPAA. This CASB 2 0 IT Cloud Security Standards And Control Frameworks from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide provides an overview of the cloud security protocols and control frameworks. The purpose of this slide is to showcase the various information security standards and control frameworks, including ISO-27001, ISO-27017, ISO-27018, GDPR, SOC reporting, PCI DSS, and HIPAA.

CASB 2 0 IT Overview Of Cloud Access Security Broker Architecture
This slide gives an overview of cloud access security broker architecture. The purpose of this slide is to highlight architecture and its main components covering immediate enterprise core, secondary enterprise core, PaaS, SaaS, IaaS, connectivity gateway, security and compliance rules, etc. Get a simple yet stunning designed CASB 2 0 IT Overview Of Cloud Access Security Broker Architecture. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit CASB 2 0 IT Overview Of Cloud Access Security Broker Architecture can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide gives an overview of cloud access security broker architecture. The purpose of this slide is to highlight architecture and its main components covering immediate enterprise core, secondary enterprise core, PaaS, SaaS, IaaS, connectivity gateway, security and compliance rules, etc.
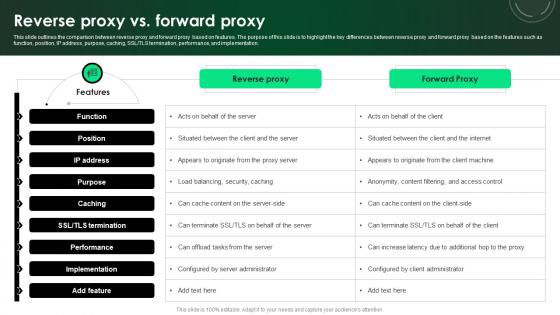
CASB 2 0 IT Reverse Proxy Vs Forward Proxy
This slide outlines the comparison between reverse proxy and forward proxy based on features. The purpose of this slide is to highlight the key differences between reverse proxy and forward proxy based on the features such as function, position, IP address, purpose, caching, SSL or TLS termination, performance, and implementation. If you are looking for a format to display your unique thoughts, then the professionally designed CASB 2 0 IT Reverse Proxy Vs Forward Proxy is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download CASB 2 0 IT Reverse Proxy Vs Forward Proxy and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide outlines the comparison between reverse proxy and forward proxy based on features. The purpose of this slide is to highlight the key differences between reverse proxy and forward proxy based on the features such as function, position, IP address, purpose, caching, SSL or TLS termination, performance, and implementation.

Esteemed Clientele Task Management System Investor Funding Elevator Pitch Deck
This slide covers a list of clients that the company has served or collaborated with by providing satisfactory services to them. The purpose of this template is to provide an overview on top notch customers generating maximum revenue for the company. Get a simple yet stunning designed Esteemed Clientele Task Management System Investor Funding Elevator Pitch Deck. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Esteemed Clientele Task Management System Investor Funding Elevator Pitch Deck can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide covers a list of clients that the company has served or collaborated with by providing satisfactory services to them. The purpose of this template is to provide an overview on top notch customers generating maximum revenue for the company.
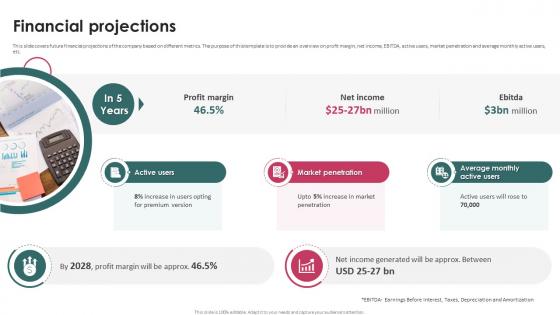
Financial Projections Task Management System Investor Funding Elevator Pitch Deck
This slide covers future financial projections of the company based on different metrics. The purpose of this template is to provide an overview on profit margin, net income, EBITDA, active users, market penetration and average monthly active users, etc. Slidegeeks is here to make your presentations a breeze with Financial Projections Task Management System Investor Funding Elevator Pitch Deck With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide covers future financial projections of the company based on different metrics. The purpose of this template is to provide an overview on profit margin, net income, EBITDA, active users, market penetration and average monthly active users, etc.
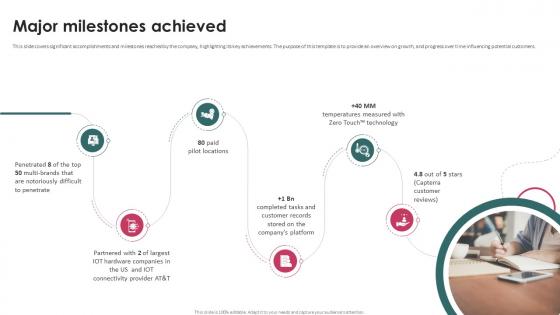
Major Milestones Achieved Task Management System Investor Funding Elevator Pitch Deck
This slide covers significant accomplishments and milestones reached by the company, highlighting its key achievements. The purpose of this template is to provide an overview on growth, and progress over time influencing potential customers. If you are looking for a format to display your unique thoughts, then the professionally designed Major Milestones Achieved Task Management System Investor Funding Elevator Pitch Deck is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Major Milestones Achieved Task Management System Investor Funding Elevator Pitch Deck and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide covers significant accomplishments and milestones reached by the company, highlighting its key achievements. The purpose of this template is to provide an overview on growth, and progress over time influencing potential customers.
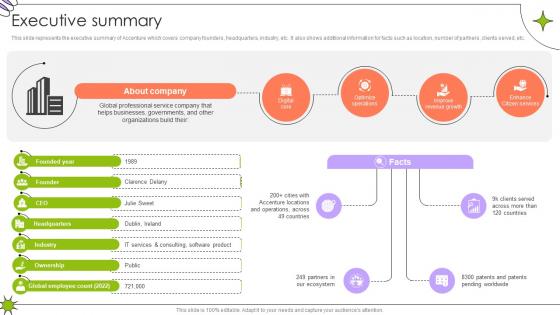
Executive Summary Global Innovation And Business Solutions Company Profile CP SS V
This slide represents the executive summary of Accenture which covers company founders, headquarters, industry, etc. It also shows additional information for facts such as location, number of partners, clients served, etc.If you are looking for a format to display your unique thoughts, then the professionally designed Executive Summary Global Innovation And Business Solutions Company Profile CP SS V is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Executive Summary Global Innovation And Business Solutions Company Profile CP SS V and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide represents the executive summary of Accenture which covers company founders, headquarters, industry, etc. It also shows additional information for facts such as location, number of partners, clients served, etc.
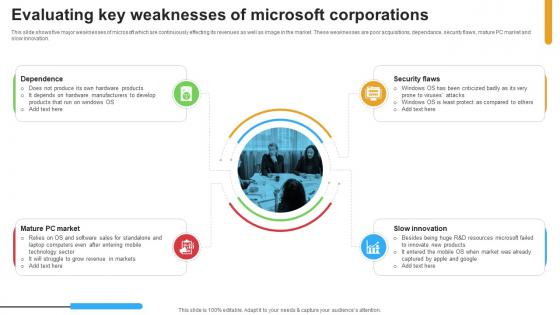
Micosoft Intensive Growth Evaluating Key Weaknesses Of Microsoft Corporations Strategy SS V
This slide shows five major weaknesses of microsoft which are continuously effecting its revenues as well as image in the market. These weaknesses are poor acquisitions, dependance, security flaws, mature PC market and slow innovation. If you are looking for a format to display your unique thoughts, then the professionally designed Micosoft Intensive Growth Evaluating Key Weaknesses Of Microsoft Corporations Strategy SS V is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Micosoft Intensive Growth Evaluating Key Weaknesses Of Microsoft Corporations Strategy SS V and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide shows five major weaknesses of microsoft which are continuously effecting its revenues as well as image in the market. These weaknesses are poor acquisitions, dependance, security flaws, mature PC market and slow innovation.

Create A Restaurant Marketing Facebook Marketing Strategy For Restaurant
This slide shows various Facebook promotional strategies for the food industry. The purpose of this slide is to implement these strategies in the best possible way. The strategies are customer testimonials, run paid ads, posting regularly, etc. Slidegeeks is here to make your presentations a breeze with Create A Restaurant Marketing Facebook Marketing Strategy For Restaurant With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide shows various Facebook promotional strategies for the food industry. The purpose of this slide is to implement these strategies in the best possible way. The strategies are customer testimonials, run paid ads, posting regularly, etc.
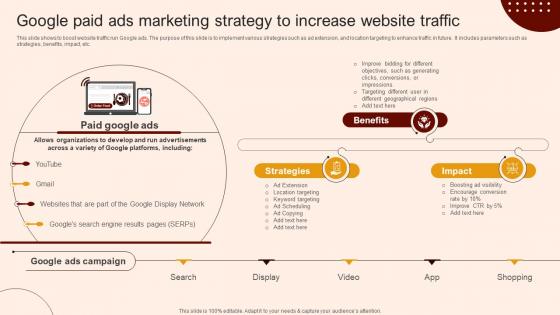
Create A Restaurant Marketing Google Paid Ads Marketing Strategy To Increase
This slide shows to boost website traffic run Google ads. The purpose of this slide is to implement various strategies such as ad extension, and location targeting to enhance traffic in future. It includes parameters such as strategies, benefits, impact, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Create A Restaurant Marketing Google Paid Ads Marketing Strategy To Increase. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Create A Restaurant Marketing Google Paid Ads Marketing Strategy To Increase today and make your presentation stand out from the rest This slide shows to boost website traffic run Google ads. The purpose of this slide is to implement various strategies such as ad extension, and location targeting to enhance traffic in future. It includes parameters such as strategies, benefits, impact, etc.

Create A Restaurant Marketing Introduction Of Marketing Plan To Determine
This slide shows the complete overview of the marketing plan. This slide aims to make the target audience aware by creating an effective or successful marketing plan. It includes parameters such as marketing focus, elements, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Create A Restaurant Marketing Introduction Of Marketing Plan To Determine is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Create A Restaurant Marketing Introduction Of Marketing Plan To Determine and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide shows the complete overview of the marketing plan. This slide aims to make the target audience aware by creating an effective or successful marketing plan. It includes parameters such as marketing focus, elements, etc.

Create A Restaurant Marketing Pestel Analysis Of Restaurant Marketing Plan
This slide shows the PESTEL political, economic, social, technological, environmental, legal Analysis of the advertisement plan. The purpose of this slide is to analyse the market condition. It includes parameters such as political, economic, social, technological, environment, legal. Retrieve professionally designed Create A Restaurant Marketing Pestel Analysis Of Restaurant Marketing Plan to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide shows the PESTEL political, economic, social, technological, environmental, legal Analysis of the advertisement plan. The purpose of this slide is to analyse the market condition. It includes parameters such as political, economic, social, technological, environment, legal.

Create A Restaurant Marketing Plan For Any Restaurant Marketing Through
This slide shows Instagram promotional strategies for the food industry using reels. The purpose of this slide is to implement these strategies in the best possible way. The strategies are engaging with followers, using hashtags, food bloggers collaboration etc. This Create A Restaurant Marketing Plan For Any Restaurant Marketing Through from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide shows Instagram promotional strategies for the food industry using reels. The purpose of this slide is to implement these strategies in the best possible way. The strategies are engaging with followers, using hashtags, food bloggers collaboration etc.

Create A Restaurant Marketing Strategies Deploy On Instagram For Restaurant
This slide shows various Instagram promotional strategies for the food industry. The purpose of this slide is to implement these strategies in the best possible way. The strategies are engaging with followers, using hashtags, food bloggers collaboration etc. If you are looking for a format to display your unique thoughts, then the professionally designed Create A Restaurant Marketing Strategies Deploy On Instagram For Restaurant is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Create A Restaurant Marketing Strategies Deploy On Instagram For Restaurant and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide shows various Instagram promotional strategies for the food industry. The purpose of this slide is to implement these strategies in the best possible way. The strategies are engaging with followers, using hashtags, food bloggers collaboration etc.


 Continue with Email
Continue with Email

 Home
Home


































