Purpose Slides

As A Service Deployment Approach Of ZTNA Architecture Rules PDF
This slide outlines the overview of the as-a-service implementation approach of ZTNA architecture. The purpose of this slide is to highlight the ZTNA as a service architecture, including its advantages and disadvantages. The pros include fewer internal resources requirements and reassurance of up-to-date software. Get a simple yet stunning designed As A Service Deployment Approach Of ZTNA Architecture Rules PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit As A Service Deployment Approach Of ZTNA Architecture Rules PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
Case Study Intellectual Property Protection With Zero Trust Model Icons PDF
This slide represents the case study for implementing the ZTNA security model into a food and beverage organization to secure intellectual property, supply chain and manufacturing. The purpose of this slide is to highlight the key requirements, solutions and impact of ZTNA implementation on the business. Slidegeeks is here to make your presentations a breeze with Case Study Intellectual Property Protection With Zero Trust Model Icons PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first
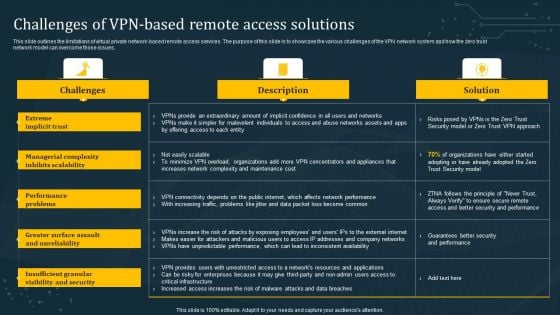
Challenges Of VPN Based Remote Access Solutions Template PDF
This slide outlines the limitations of virtual private network-based remote access services. The purpose of this slide is to showcase the various challenges of the VPN network system and how the zero trust network model can overcome those issues. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Challenges Of VPN Based Remote Access Solutions Template PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Challenges Of VPN Based Remote Access Solutions Template PDF today and make your presentation stand out from the rest
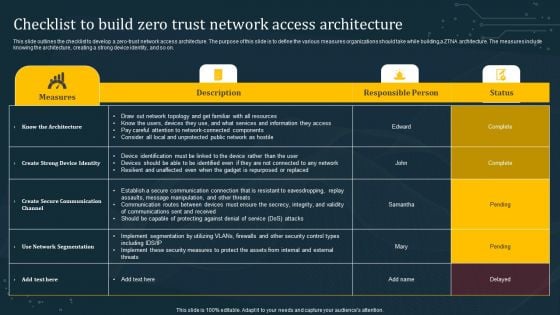
Checklist To Build Zero Trust Network Access Architecture Diagrams PDF
This slide outlines the checklist to develop a zero-trust network access architecture. The purpose of this slide is to define the various measures organizations should take while building a ZTNA architecture. The measures include knowing the architecture, creating a strong device identity, and so on. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Checklist To Build Zero Trust Network Access Architecture Diagrams PDF can be your best option for delivering a presentation. Represent everything in detail using Checklist To Build Zero Trust Network Access Architecture Diagrams PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
Client Based Approach Of ZTNA Architecture Icons PDF
This slide describes the overview of the client-based approach of zero trust network access architecture. The purpose of this slide is to highlight the architecture, including its benefits and drawbacks. The main advantages include its capacity to apply zero trust to all private resources and improved device checks. Find highly impressive Client Based Approach Of ZTNA Architecture Icons PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Client Based Approach Of ZTNA Architecture Icons PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now
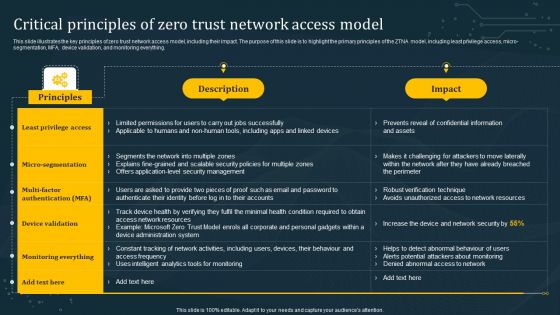
Critical Principles Of Zero Trust Network Access Model Graphics PDF
This slide illustrates the key principles of zero trust network access model, including their impact. The purpose of this slide is to highlight the primary principles of the ZTNA model, including least privilege access, micro-segmentation, MFA, device validation, and monitoring everything. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Critical Principles Of Zero Trust Network Access Model Graphics PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Critical Principles Of Zero Trust Network Access Model Graphics PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers

Endpoint Initiated Vs Service Initiated Portrait PDF
This slide represents the comparison between the two primary approaches to implementing zero-trust network access for organizations. The purpose of this slide is to showcase the endpoint-initiated and service-initiated approach of zero-trust network access. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Endpoint Initiated Vs Service Initiated Portrait PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
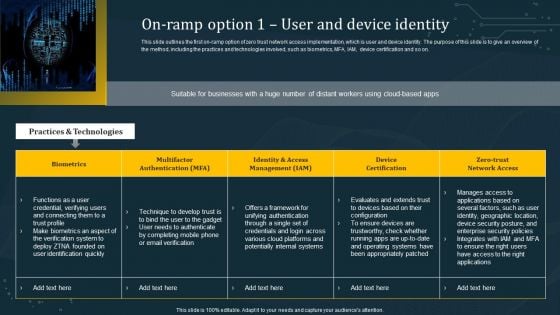
On Ramp Option 1 User And Device Identity Themes PDF
This slide outlines the first on-ramp option of zero trust network access implementation, which is user and device identity. The purpose of this slide is to give an overview of the method, including the practices and technologies involved, such as biometrics, MFA, IAM, device certification and so on. This On Ramp Option 1 User And Device Identity Themes PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
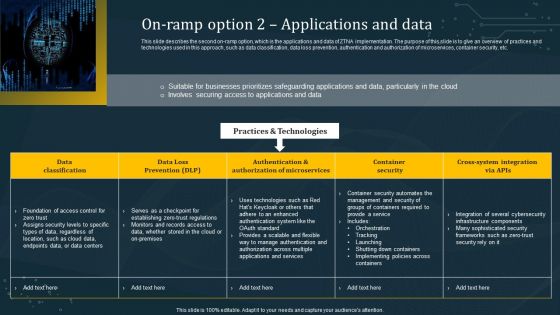
On Ramp Option 2 Applications And Data Template PDF
This slide describes the second on-ramp option, which is the applications and data of ZTNA implementation. The purpose of this slide is to give an overview of practices and technologies used in this approach, such as data classification, data loss prevention, authentication and authorization of microservices, container security, etc. Take your projects to the next level with our ultimate collection of On Ramp Option 2 Applications And Data Template PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest

Overview Of Zero Trust Solution Categories Background PDF
This slide represents the overview of zero-trust solution categories, including MFA, SSO, identity and access management, zero-trust network access and secure access service edge. The purpose of this slide is to give an overview of zero-trust technologies and their benefits. Boost your pitch with our creative Overview Of Zero Trust Solution Categories Background PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
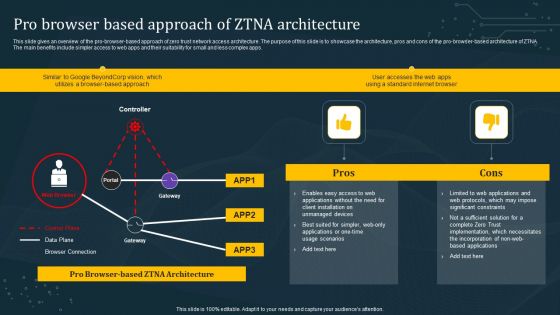
Pro Browser Based Approach Of ZTNA Architecture Template PDF
This slide gives an overview of the pro-browser-based approach of zero trust network access architecture. The purpose of this slide is to showcase the architecture, pros and cons of the pro-browser-based architecture of ZTNA. The main benefits include simpler access to web apps and their suitability for small and less complex apps. Create an editable Pro Browser Based Approach Of ZTNA Architecture Template PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Pro Browser Based Approach Of ZTNA Architecture Template PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Roadmap To Implement Zero Trust Network Access Model Structure PDF
This slide outlines the roadmap to implementing an organizations zero-trust network access model. The purpose of this slide is to showcase the various steps to be taken while deploying the ZTNA security model, including assessing current network infrastructure, developing a ZTNA strategy, choosing a ZTNA solution, etc. Want to ace your presentation in front of a live audience Our Roadmap To Implement Zero Trust Network Access Model Structure PDF can help you do that by engaging all the users towards you.. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.
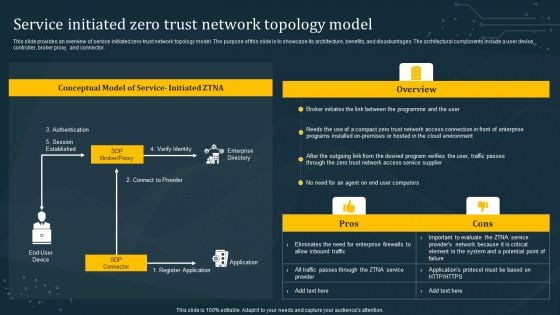
Service Initiated Zero Trust Network Topology Model Clipart PDF
This slide provides an overview of service initiated zero-trust network topology model. The purpose of this slide is to showcase its architecture, benefits, and disadvantages. The architectural components include a user device, controller, broker proxy, and connector. Get a simple yet stunning designed Service Initiated Zero Trust Network Topology Model Clipart PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Service Initiated Zero Trust Network Topology Model Clipart PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
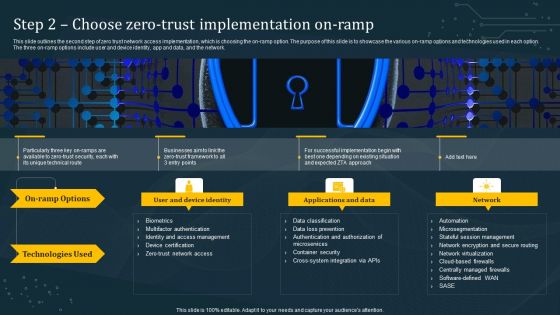
Step 2 Choose Zero Trust Implementation On Ramp Information PDF
This slide outlines the second step of zero trust network access implementation, which is choosing the on-ramp option. The purpose of this slide is to showcase the various on-ramp options and technologies used in each option. The three on-ramp options include user and device identity, app and data, and the network. Slidegeeks is here to make your presentations a breeze with Step 2 Choose Zero Trust Implementation On Ramp Information PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first

Step 3 Assess The Environment Elements PDF
This slide outlines the third step of ZTNA deployment, which is assessing the environment. The purpose of this slide is to highlight the questions that should be answered to evaluate the ecosystem and the questions include knowing the security controls, knowledge gaps and so on. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Step 3 Assess The Environment Elements PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Step 3 Assess The Environment Elements PDF today and make your presentation stand out from the rest
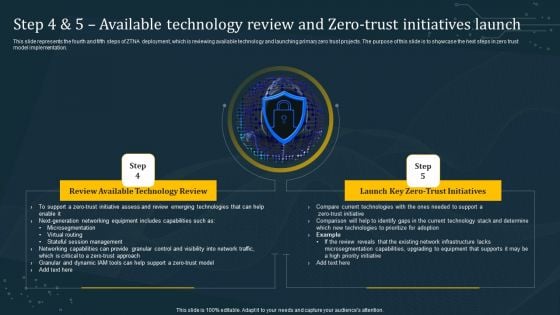
Step 4 And 5 Available Technology Review And Zero Trust Initiatives Launch Formats PDF
This slide represents the fourth and fifth steps of ZTNA deployment, which is reviewing available technology and launching primary zero trust projects. The purpose of this slide is to showcase the next steps in zero trust model implementation. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Step 4 And 5 Available Technology Review And Zero Trust Initiatives Launch Formats PDF can be your best option for delivering a presentation. Represent everything in detail using Step 4 And 5 Available Technology Review And Zero Trust Initiatives Launch Formats PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
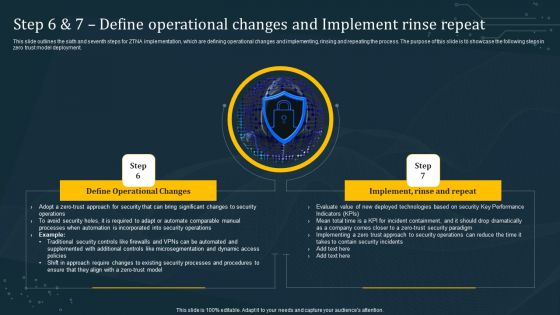
Step 6 And 7 Define Operational Changes And Implement Rinse Repeat Professional PDF
This slide outlines the sixth and seventh steps for ZTNA implementation, which are defining operational changes and implementing, rinsing and repeating the process. The purpose of this slide is to showcase the following steps in zero trust model deployment. Find highly impressive Step 6 And 7 Define Operational Changes And Implement Rinse Repeat Professional PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Step 6 And 7 Define Operational Changes And Implement Rinse Repeat Professional PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now
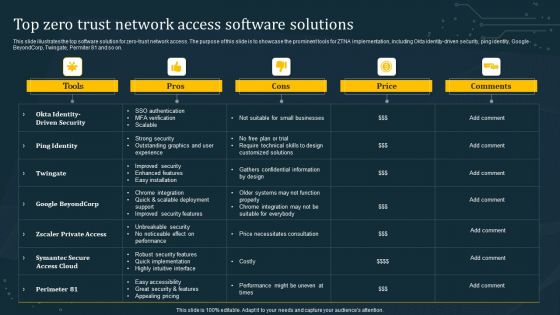
Top Zero Trust Network Access Software Solutions Microsoft PDF
This slide illustrates the top software solution for zero-trust network access. The purpose of this slide is to showcase the prominent tools for ZTNA implementation, including Okta identity-driven security, ping identity, Google BeyondCorp, Twingate, Permiter 81 and so on. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Top Zero Trust Network Access Software Solutions Microsoft PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Top Zero Trust Network Access Software Solutions Microsoft PDF.

Traditional Perimeter Based Network Security Overview And Limitations Inspiration PDF
This slide represents the overview of traditional perimeter-based network security. The purpose of this slide is to showcase the various challenges of conventional perimeter-based security and how ZTNA can overcomethose challenges. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Traditional Perimeter Based Network Security Overview And Limitations Inspiration PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Zero Trust Network Access System Use Cases Summary PDF
This slide outlines multiple use cases of zero-trust network access systems. The purpose of this slide is to showcase the main use cases of the ZTNA model, which are replacing VPN and MPLS connections, internal firewall replacement, securing remote access to private apps, limiting user access, and so on. Boost your pitch with our creative Zero Trust Network Access System Use Cases Summary PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
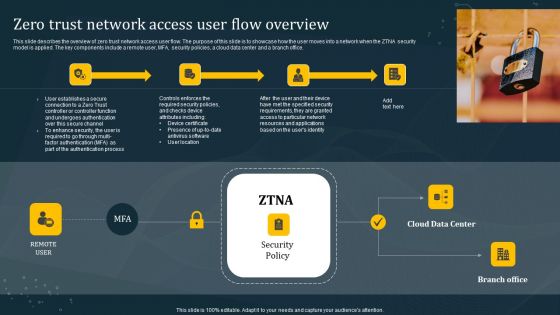
Zero Trust Network Access User Flow Overview Mockup PDF
This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office. Create an editable Zero Trust Network Access User Flow Overview Mockup PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Zero Trust Network Access User Flow Overview Mockup PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
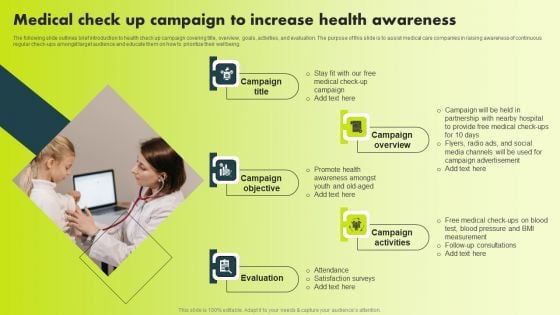
Medical Check Up Campaign To Increase Health Awareness Professional PDF
The following slide outlines brief introduction to health check up campaign covering title, overview, goals, activities, and evaluation. The purpose of this slide is to assist medical care companies in raising awareness of continuous regular check-ups amongst target audience and educate them on how to prioritize their wellbeing. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Medical Check Up Campaign To Increase Health Awareness Professional PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Medical Check Up Campaign To Increase Health Awareness Professional PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers
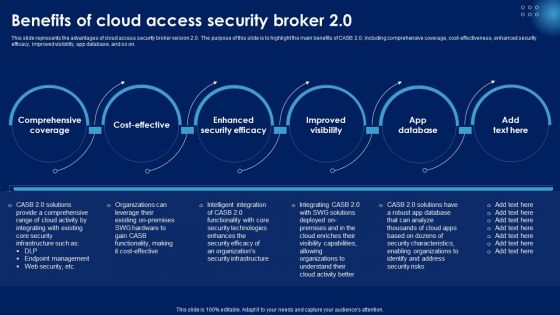
Benefits Of Cloud Access Security Broker 2 0 Ppt PowerPoint Presentation File Professional PDF
This slide represents the advantages of cloud access security broker version 2.0. The purpose of this slide is to highlight the main benefits of CASB 2.0, including comprehensive coverage, cost-effectiveness, enhanced security efficacy, improved visibility, app database, and so on. Create an editable Benefits Of Cloud Access Security Broker 2 0 Ppt PowerPoint Presentation File Professional PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Benefits Of Cloud Access Security Broker 2 0 Ppt PowerPoint Presentation File Professional PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

CASB Application In Learning And Education Sector Ppt PowerPoint Presentation File Professional PDF
This slide represents the application of a cloud access security broker in the learning and education department. The purpose of this slide is to highlight the overview, challenges caused by the transition in education, and CASB solutions. Want to ace your presentation in front of a live audience Our CASB Application In Learning And Education Sector Ppt PowerPoint Presentation File Professional PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.
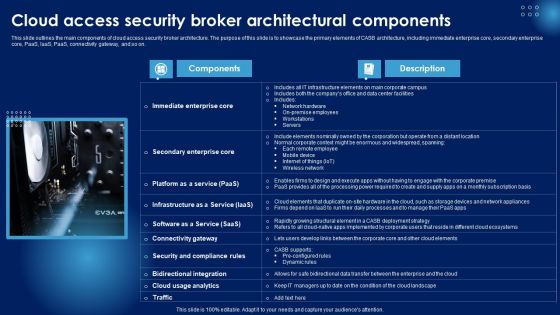
Cloud Access Security Broker Architectural Components Ppt PowerPoint Presentation File Show PDF
This slide outlines the main components of cloud access security broker architecture. The purpose of this slide is to showcase the primary elements of CASB architecture, including immediate enterprise core, secondary enterprise core, PaaS, IaaS, PaaS, connectivity gateway, and so on. Get a simple yet stunning designed Cloud Access Security Broker Architectural Components Ppt PowerPoint Presentation File Show PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Cloud Access Security Broker Architectural Components Ppt PowerPoint Presentation File Show PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Cloud Access Security Broker Pillar Overview Ppt PowerPoint Presentation File Infographics PDF
This slide represents the four major pillars of cloud access security broker. The purpose of this slide is to showcase the main pillars of implementing a cloud access security broker. The pillars include compliance, visibility, threat protection, and data security. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Cloud Access Security Broker Pillar Overview Ppt PowerPoint Presentation File Infographics PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Cloud Access Security Broker Pillar Overview Ppt PowerPoint Presentation File Infographics PDF today and make your presentation stand out from the rest.
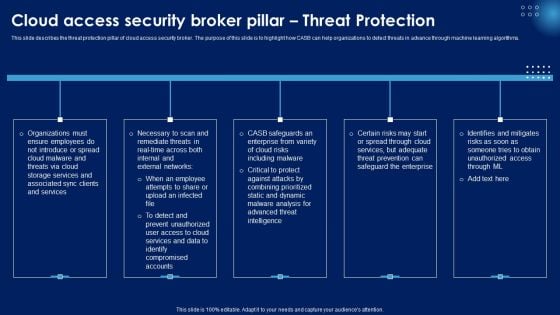
Cloud Access Security Broker Pillar Threat Protection Ppt PowerPoint Presentation File Pictures PDF
This slide describes the threat protection pillar of cloud access security broker. The purpose of this slide is to highlight how CASB can help organizations to detect threats in advance through machine learning algorithms. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Cloud Access Security Broker Pillar Threat Protection Ppt PowerPoint Presentation File Pictures PDF can be your best option for delivering a presentation. Represent everything in detail using Cloud Access Security Broker Pillar Threat Protection Ppt PowerPoint Presentation File Pictures PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Cloud Access Security Broker Working Process Ppt PowerPoint Presentation File Infographic Template PDF
This slide outlines the working process of a cloud access security broker. The purpose of this slide is to showcase the overview and working process steps of CASB. The main steps include discovery, classification, and remediation. Find highly impressive Cloud Access Security Broker Working Process Ppt PowerPoint Presentation File Infographic Template PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Cloud Access Security Broker Working Process Ppt PowerPoint Presentation File Infographic Template PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.
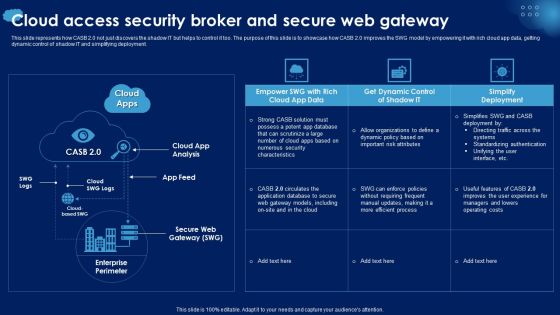
Cloud Access Security Broker And Secure Web Gateway Ppt PowerPoint Presentation Diagram Images PDF
This slide represents how CASB 2.0 not just discovers the shadow IT but helps to control it too. The purpose of this slide is to showcase how CASB 2.0 improves the SWG model by empowering it with rich cloud app data, getting dynamic control of shadow IT and simplifying deployment. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Cloud Access Security Broker And Secure Web Gateway Ppt PowerPoint Presentation Diagram Images PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Cloud Access Security Broker And Secure Web Gateway Ppt PowerPoint Presentation Diagram Images PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.
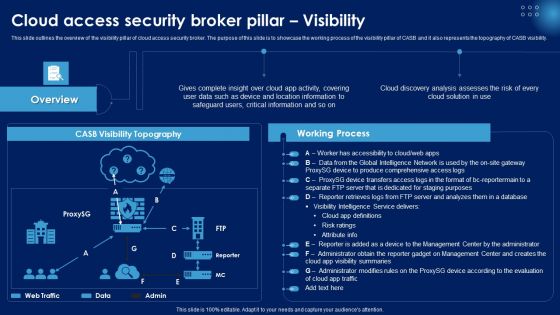
Cloud Access Security Broker Pillar Visibility Ppt PowerPoint Presentation File Infographics PDF
This slide outlines the overview of the visibility pillar of cloud access security broker. The purpose of this slide is to showcase the working process of the visibility pillar of CASB and it also represents the topography of CASB visibility. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Cloud Access Security Broker Pillar Visibility Ppt PowerPoint Presentation File Infographics PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
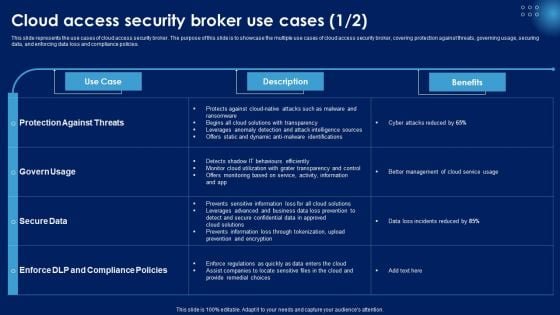
Cloud Access Security Broker Use Cases Ppt PowerPoint Presentation File Background Images PDF
This slide represents the use cases of cloud access security broker. The purpose of this slide is to showcase the multiple use cases of cloud access security broker, covering protection against threats, governing usage, securing data, and enforcing data loss and compliance policies. This Cloud Access Security Broker Use Cases Ppt PowerPoint Presentation File Background Images PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

Primary Types Of Reverse Proxy Server Deployment Ppt PowerPoint Presentation File Gallery PDF
This slide outlines the main types of reverse proxy server deployment, covering regular reverse proxies and load balancers. The purpose of this slide is to showcase how both methods work to manage traffic and offer security features to organizations. Take your projects to the next level with our ultimate collection of Primary Types Of Reverse Proxy Server Deployment Ppt PowerPoint Presentation File Gallery PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest.

Shadow IT Management Lifecycle Overview Ppt PowerPoint Presentation Diagram PDF
This slide outlines the lifecycle of shadow IT management for safely adopting cloud apps. The purpose of this slide is to showcase the various stages of the lifecycle, such as discovering shadow IT, knowing the risk level of apps, evaluating compliance, analyzing usage, governing cloud apps, and continuous monitoring. Get a simple yet stunning designed Shadow IT Management Lifecycle Overview Ppt PowerPoint Presentation Diagram PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Shadow IT Management Lifecycle Overview Ppt PowerPoint Presentation Diagram PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
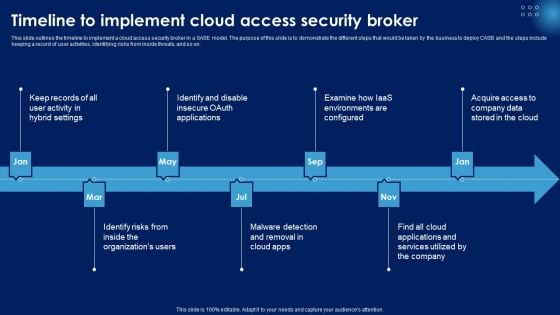
Timeline To Implement Cloud Access Security Broker Ppt PowerPoint Presentation File Styles PDF
This slide outlines the timeline to implement a cloud access security broker in a SASE model. The purpose of this slide is to demonstrate the different steps that would be taken by the business to deploy CASB and the steps include keeping a record of user activities, identifying risks from inside threats, and so on. Slidegeeks is here to make your presentations a breeze with Timeline To Implement Cloud Access Security Broker Ppt PowerPoint Presentation File Styles PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
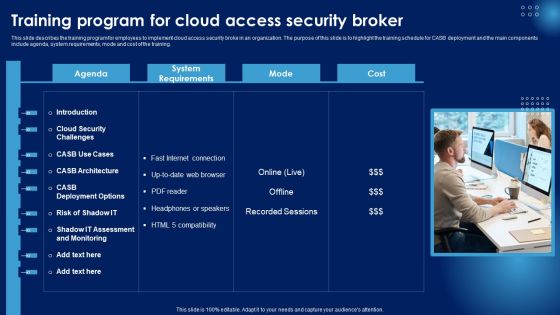
Training Program For Cloud Access Security Broker Ppt PowerPoint Presentation File Show PDF
This slide describes the training program for employees to implement cloud access security broke in an organization. The purpose of this slide is to highlight the training schedule for CASB deployment and the main components include agenda, system requirements, mode and cost of the training. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Training Program For Cloud Access Security Broker Ppt PowerPoint Presentation File Show PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Training Program For Cloud Access Security Broker Ppt PowerPoint Presentation File Show PDF today and make your presentation stand out from the rest.
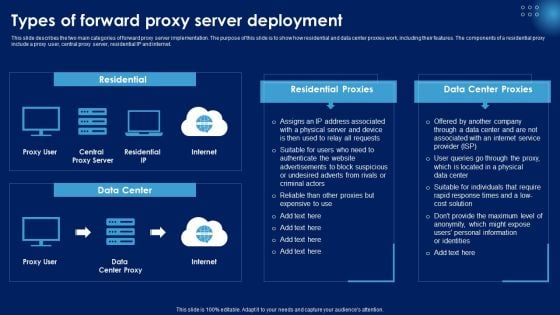
Types Of Forward Proxy Server Deployment Ppt PowerPoint Presentation File Styles PDF
This slide describes the two main categories of forward proxy server implementation. The purpose of this slide is to show how residential and data center proxies work, including their features. The components of a residential proxy include a proxy user, central proxy server, residential IP and internet. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Types Of Forward Proxy Server Deployment Ppt PowerPoint Presentation File Styles PDF can be your best option for delivering a presentation. Represent everything in detail using Types Of Forward Proxy Server Deployment Ppt PowerPoint Presentation File Styles PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
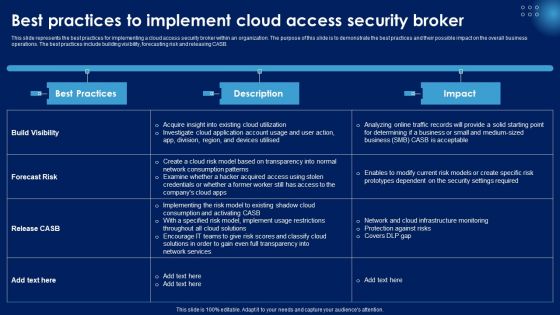
Best Practices To Implement Cloud Access Security Broker Ppt PowerPoint Presentation File Gallery PDF
This slide represents the best practices for implementing a cloud access security broker within an organization. The purpose of this slide is to demonstrate the best practices and their possible impact on the overall business operations. The best practices include building visibility, forecasting risk and releasing CASB. This Best Practices To Implement Cloud Access Security Broker Ppt PowerPoint Presentation File Gallery PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
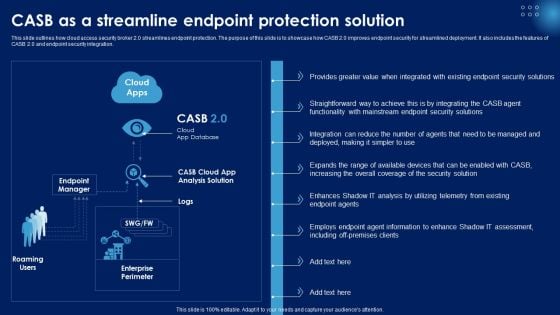
CASB As A Streamline Endpoint Protection Solution Ppt PowerPoint Presentation File Layouts PDF
This slide outlines how cloud access security broker 2.0 streamlines endpoint protection. The purpose of this slide is to showcase how CASB 2.0 improves endpoint security for streamlined deployment. It also includes the features of CASB 2.0 and endpoint security integration. Take your projects to the next level with our ultimate collection of CASB As A Streamline Endpoint Protection Solution Ppt PowerPoint Presentation File Layouts PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest.
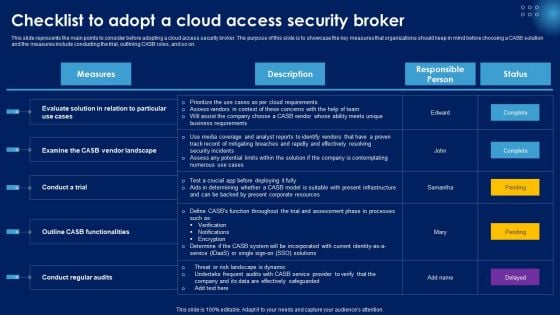
Checklist To Adopt A Cloud Access Security Broker Ppt PowerPoint Presentation File Portfolio PDF
This slide represents the main points to consider before adopting a cloud access security broker. The purpose of this slide is to showcase the key measures that organizations should keep in mind before choosing a CASB solution and the measures include conducting the trial, outlining CASB roles, and so on. Get a simple yet stunning designed Checklist To Adopt A Cloud Access Security Broker Ppt PowerPoint Presentation File Portfolio PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Checklist To Adopt A Cloud Access Security Broker Ppt PowerPoint Presentation File Portfolio PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Emerging Cloud Security Risks And Threats Ppt PowerPoint Presentation File Diagrams PDF
This slide represents the emerging cloud security risks, and threats organizations can encounter. The purpose of this slide is to highlight the various threats that CASB deployment can help overcome, including VPNs, system misconfiguration, non-zero security permissions, and so on. Slidegeeks is here to make your presentations a breeze with Emerging Cloud Security Risks And Threats Ppt PowerPoint Presentation File Diagrams PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
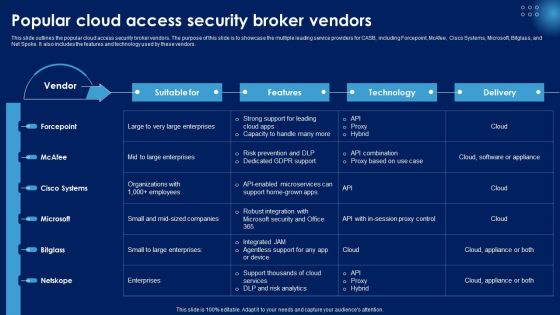
Popular Cloud Access Security Broker Vendors Ppt PowerPoint Presentation File Example PDF
This slide outlines the popular cloud access security broker vendors. The purpose of this slide is to showcase the multiple leading service providers for CASB, including Forcepoint, McAfee, Cisco Systems, Microsoft, Bitglass, and Net Spoke. It also includes the features and technology used by these vendors. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Popular Cloud Access Security Broker Vendors Ppt PowerPoint Presentation File Example PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Popular Cloud Access Security Broker Vendors Ppt PowerPoint Presentation File Example PDF today and make your presentation stand out from the rest.

Proxy Based Vs API Based Deployment Of CASB Ppt PowerPoint Presentation File Pictures PDF
This slide represents the comparison between proxy-based and API-based deployment of the CASB model. The purpose of this slide is to highlight the key differences between proxy-based and API-based deployment of cloud access security broker. Find highly impressive Proxy Based Vs API Based Deployment Of CASB Ppt PowerPoint Presentation File Pictures PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Proxy Based Vs API Based Deployment Of CASB Ppt PowerPoint Presentation File Pictures PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.

Blockchain Security Solutions Deployment Blockchain Hashing SHA 256 Algorithm Formats PDF
This slide talks about the hashing SHA-256 algorithm used in blockchain technology, including its properties. The purpose of this slide is to give an overview of hashing and its properties, such as collision resistance, deterministic, quick, and irreversible. Create an editable Blockchain Security Solutions Deployment Blockchain Hashing SHA 256 Algorithm Formats PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Blockchain Security Solutions Deployment Blockchain Hashing SHA 256 Algorithm Formats PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Blockchain Security Solutions Deployment How Blockchain Prevents Fraud And Data Theft Themes PDF
This slide describes the different methods used by blockchain technology to prevent data from fraud and stealing. The purpose of this slide is to showcase the various techniques and technologies used in blockchain technology to prevent fraud and data theft. Get a simple yet stunning designed Blockchain Security Solutions Deployment How Blockchain Prevents Fraud And Data Theft Themes PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Blockchain Security Solutions Deployment How Blockchain Prevents Fraud And Data Theft Themes PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Blockchain Security Solutions Deployment How Organizations Maintaining Blockchain Mockup PDF
This slide represents the various organizations that are taking security measures to prevent cyberattacks on blockchain network. The purpose of this slide is to highlight the various steps taken by US based organizations to prevent blockchain from cyber attacks and frauds. Slidegeeks is here to make your presentations a breeze with Blockchain Security Solutions Deployment How Organizations Maintaining Blockchain Mockup PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first
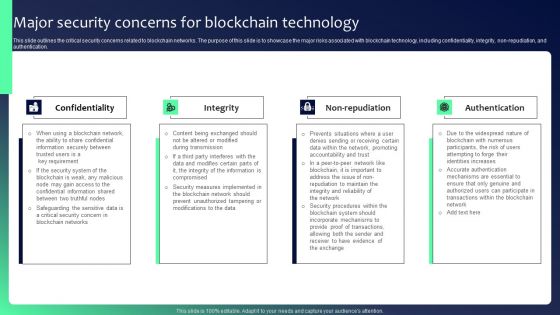
Blockchain Security Solutions Deployment Major Security Concerns For Blockchain Graphics PDF
This slide outlines the critical security concerns related to blockchain networks. The purpose of this slide is to showcase the major risks associated with blockchain technology, including confidentiality, integrity, non-repudiation, and authentication. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Blockchain Security Solutions Deployment Major Security Concerns For Blockchain Graphics PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Blockchain Security Solutions Deployment Major Security Concerns For Blockchain Graphics PDF today and make your presentation stand out from the rest
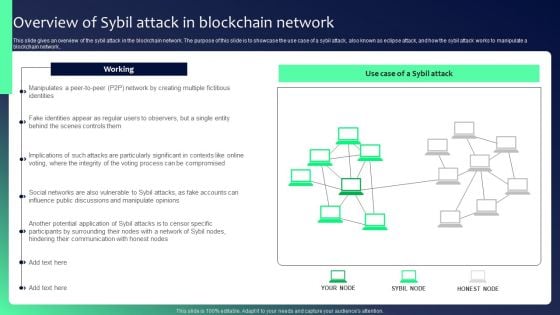
Blockchain Security Solutions Deployment Overview Of Sybil Attack In Blockchain Summary PDF
This slide gives an overview of the sybil attack in the blockchain network. The purpose of this slide is to showcase the use case of a sybil attack, also known as eclipse attack, and how the sybil attack works to manipulate a blockchain network.. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Blockchain Security Solutions Deployment Overview Of Sybil Attack In Blockchain Summary PDF can be your best option for delivering a presentation. Represent everything in detail using Blockchain Security Solutions Deployment Overview Of Sybil Attack In Blockchain Summary PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
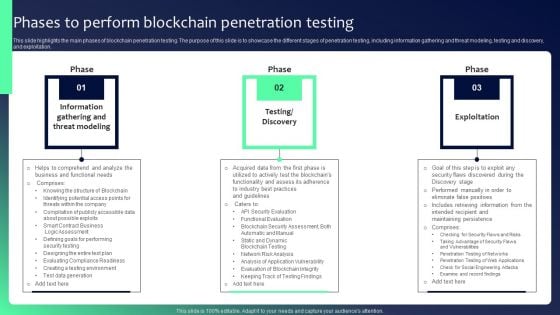
Blockchain Security Solutions Deployment Phases To Perform Blockchain Penetration Graphics PDF
This slide highlights the main phases of blockchain penetration testing. The purpose of this slide is to showcase the different stages of penetration testing, including information gathering and threat modeling, testing and discovery, and exploitation. Find highly impressive Blockchain Security Solutions Deployment Phases To Perform Blockchain Penetration Graphics PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Blockchain Security Solutions Deployment Phases To Perform Blockchain Penetration Graphics PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now
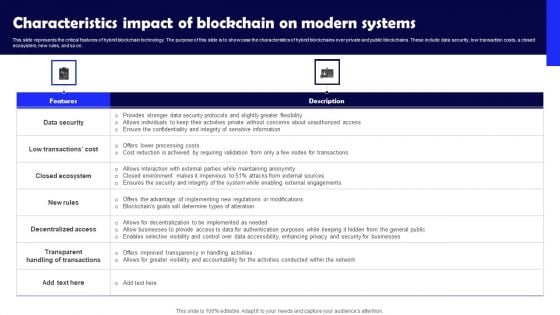
Characteristics Impact Of Blockchain On Modern Systems Introduction PDF
This slide represents the critical features of hybrid blockchain technology. The purpose of this slide is to showcase the characteristics of hybrid blockchains over private and public blockchains. These include data security, low transaction costs, a closed ecosystem, new rules, and so on. Boost your pitch with our creative Characteristics Impact Of Blockchain On Modern Systems Introduction PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
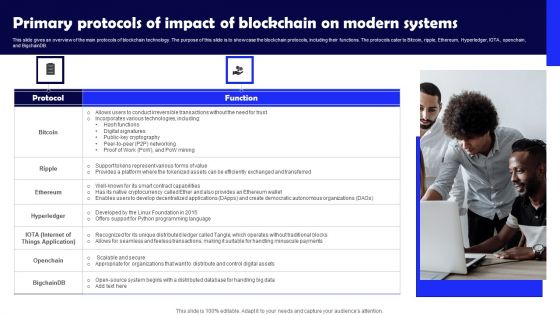
Primary Protocols Of Impact Of Blockchain On Modern Systems Themes PDF
This slide gives an overview of the main protocols of blockchain technology. The purpose of this slide is to showcase the blockchain protocols, including their functions. The protocols cater to Bitcoin, ripple, Ethereum, Hyperledger, IOTA, openchain, and BigchainDB. Slidegeeks is here to make your presentations a breeze with Primary Protocols Of Impact Of Blockchain On Modern Systems Themes PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first
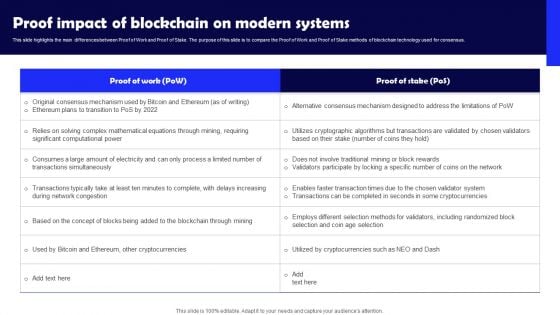
Proof Impact Of Blockchain On Modern Systems Background PDF
This slide highlights the main differences between Proof of Work and Proof of Stake. The purpose of this slide is to compare the Proof of Work and Proof of Stake methods of blockchain technology used for consensus. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Proof Impact Of Blockchain On Modern Systems Background PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Proof Impact Of Blockchain On Modern Systems Background PDF today and make your presentation stand out from the rest
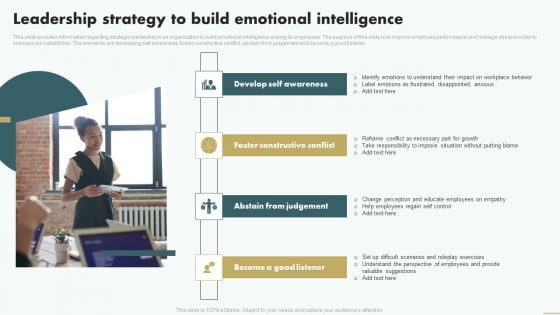
Leadership Strategy To Build Emotional Intelligence Ideas PDF
This slide provides information regarding strategic leadership in an organization to build emotional intelligence among its employees. The purpose of this slide is to improve employee performance and manage stress in order to increase job satisfaction. The elements are developing self awareness, foster constructive conflict, abstain from judgement and become a good listener. Persuade your audience using this Leadership Strategy To Build Emotional Intelligence Ideas PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Develop Self Awareness, Foster Constructive Conflict, Abstain From Judgement. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
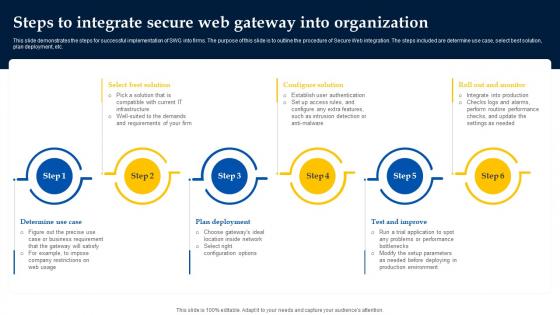
Web Access Control Solution Steps To Integrate Secure Web Gateway Into Organization
Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Web Access Control Solution Steps To Integrate Secure Web Gateway Into Organization. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Web Access Control Solution Steps To Integrate Secure Web Gateway Into Organization today and make your presentation stand out from the rest This slide demonstrates the steps for successful implementation of SWG into firms. The purpose of this slide is to outline the procedure of Secure Web integration. The steps included are determine use case, select best solution, plan deployment, etc.
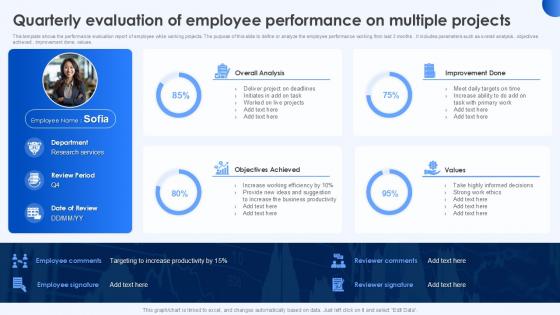
Quarterly Evaluation Of Employee Performance On Multiple Projects
Create an editable Quarterly Evaluation Of Employee Performance On Multiple Projects that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Quarterly Evaluation Of Employee Performance On Multiple Projects is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide shows the performance evaluation report of employees while working on projects. The purpose of this slide is to define or analyze the employee performance from the last 3 months. It includes parameters such as overall analysis, objectives achieved, improvement done, values
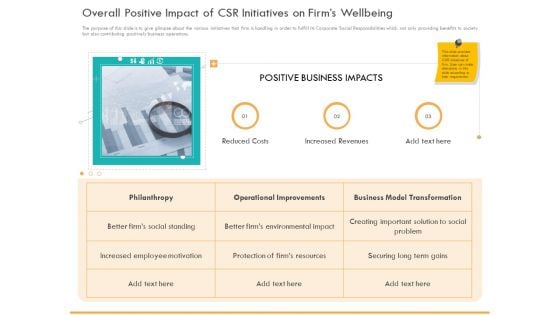
Business Planning And Strategy Playbook Overall Positive Impact Of CSR Initiatives On Firms Wellbeing Background PDF
The purpose of this slide is to give glimpse about the various initiatives that firm is handling in order to fulfill its Corporate Social Responsibilities which not only providing benefits to society but also contributing positively business operations. This is a business planning and strategy playbook overall positive impact of csr initiatives on firms wellbeing background pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like reduced costs, increased revenues, operational improvements, business model transformation, philanthropy. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Employee Recognition Award Best Employee Selection Timeline Ppt PowerPoint Presentation Inspiration Topics PDF
The purpose of this slide is to provide the glimpse of the best employee selection timeline wherein a visual representation of a sequence of activities to be performed is provided along with the date of implementation. This is a employee recognition award best employee selection timeline ppt powerpoint presentation inspiration topics pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like introducing recognition programs department, creating budget plan, preparing nominators list, evaluating nominators performance, preparing employees result, presenting award best suitable employee. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

SCR For Market Importance Of Wallet Share Product And Services Guidelines PDF
The purpose of this slide is to provide information regarding the significance of wallet share for firms wellness. This is a SCR for market importance of wallet share product and services guidelines pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like a concrete measure of customers spending for a brand that is measured over a fixed time interval, businesses in improving respective performance that results in accumulation of more profit, concept of wallet share aids firms in retaining customers by improving product and services. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
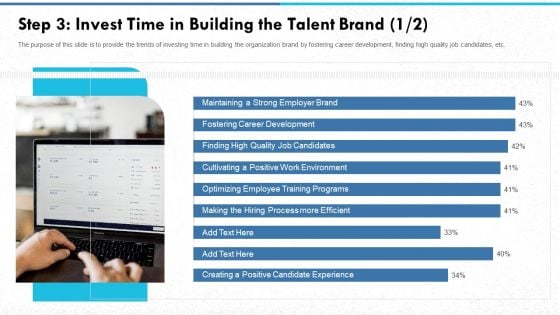
Step 3 Invest Time In Building The Talent Brand Process Clipart PDF
The purpose of this slide is to provide the trends of investing time in building the organization brand by fostering career development, finding high quality job candidates, etc. This is a step 3 invest time in building the talent brand process clipart pdf. template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like fostering career development, finding high quality job candidates, cultivating a positive work environment, optimizing employee training programs, making the hiring process more efficient. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Mhealth Investor Funding Elevator Pitch Deck The Current Investment Environment For Digital Health Industry Icons PDF
Purpose of following slide is to highlight the major investors who have invested into the organization, the provided map displays the key regions where investment can be done and the provided table displays the list of major investors and the total funds raised from each.This is a mhealth investor funding elevator pitch deck the current investment environment for digital health industry icons pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like the current investment environment for digital health industry. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
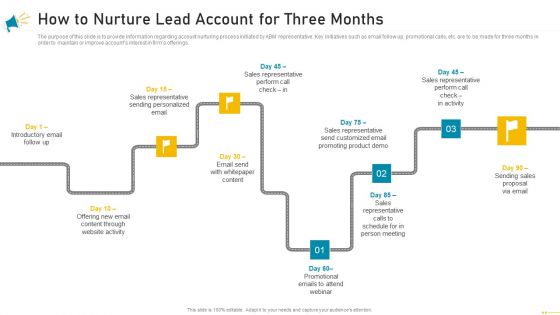
Key Account Marketing Approach How To Nurture Lead Account For Three Months Portrait PDF
The purpose of this slide is to provide information regarding account nurturing process initiated by ABM representative. Key initiatives such as email follow up, promotional calls, etc. are to be made for three months in order to maintain or improve accounts interest in firms offerings. This is a key account marketing approach how to nurture lead account for three months portrait pdf template with various stages. Focus and dispense information on ten stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like how to nurture lead account for three months. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.


 Continue with Email
Continue with Email

 Home
Home


































