Purpose Slides
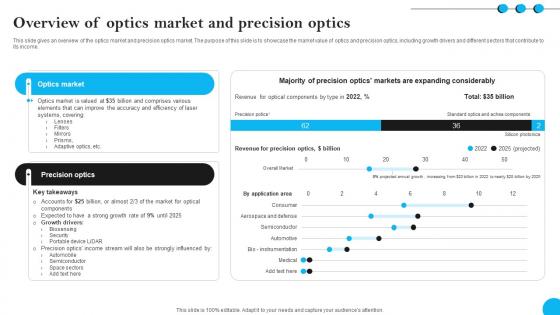
Fibers IT Overview Of Optics Market And Precision Optics
This slide gives an overview of the optics market and precision optics market. The purpose of this slide is to showcase the market value of optics and precision optics, including growth drivers and different sectors that contribute to its income. Do you know about Slidesgeeks Fibers IT Overview Of Optics Market And Precision Optics These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide gives an overview of the optics market and precision optics market. The purpose of this slide is to showcase the market value of optics and precision optics, including growth drivers and different sectors that contribute to its income.
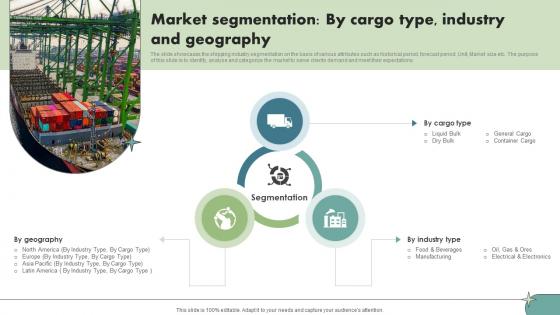
Market Segmentation By Cargo Type Industry And Geography Maritime Shipping Industry IR SS V
The slide showcases the shipping industry segmentation on the basis of various attributes such as historical period, forecast period, Unit, Market size etc. The purpose of this slide is to identify, analyse and categorize the market to serve clients demand and meet their expectations. This Market Segmentation By Cargo Type Industry And Geography Maritime Shipping Industry IR SS V is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Market Segmentation By Cargo Type Industry And Geography Maritime Shipping Industry IR SS V features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today The slide showcases the shipping industry segmentation on the basis of various attributes such as historical period, forecast period, Unit, Market size etc. The purpose of this slide is to identify, analyse and categorize the market to serve clients demand and meet their expectations.
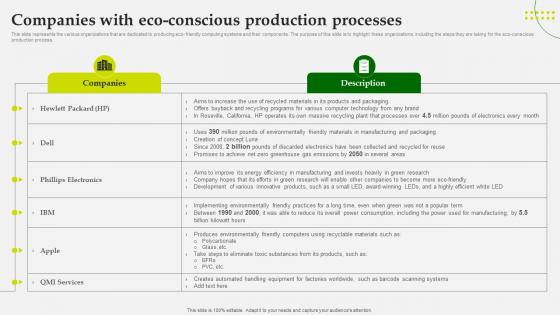
Green Computing Companies With Eco Conscious Production Processes
This slide represents the various organizations that are dedicated to producing eco-friendly computing systems and their components. The purpose of this slide is to highlight these organizations, including the steps they are taking for the eco-conscious production process. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Green Computing Companies With Eco Conscious Production Processes a try. Our experts have put a lot of knowledge and effort into creating this impeccable Green Computing Companies With Eco Conscious Production Processes You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide represents the various organizations that are dedicated to producing eco-friendly computing systems and their components. The purpose of this slide is to highlight these organizations, including the steps they are taking for the eco-conscious production process.

Green Computing Green Cloud Computing Strategy Components
This slide represents the components of a green cloud computing strategy. The purpose of this slide is to showcasethe different components of green computing strategy, including remote work, smart technology, upgrading and rearranging data centers, power down, strategic scheduling, display selection, and so on. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Green Computing Green Cloud Computing Strategy Components and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide represents the components of a green cloud computing strategy. The purpose of this slide is to showcasethe different components of green computing strategy, including remote work, smart technology, upgrading and rearranging data centers, power down, strategic scheduling, display selection, and so on.
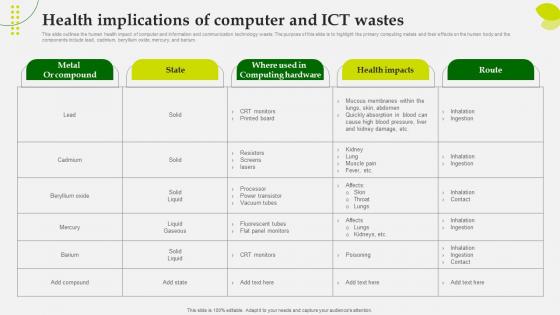
Green Computing Health Implications Of Computer And Ict Wastes
This slide outlines the human health impact of computer and information and communication technology waste. The purpose of this slide is to highlight the primary computing metals and their effects on the human body and the components include lead, cadmium, beryllium oxide, mercury, and barium. This Green Computing Health Implications Of Computer And Ict Wastes is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Green Computing Health Implications Of Computer And Ict Wastes features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide outlines the human health impact of computer and information and communication technology waste. The purpose of this slide is to highlight the primary computing metals and their effects on the human body and the components include lead, cadmium, beryllium oxide, mercury, and barium.
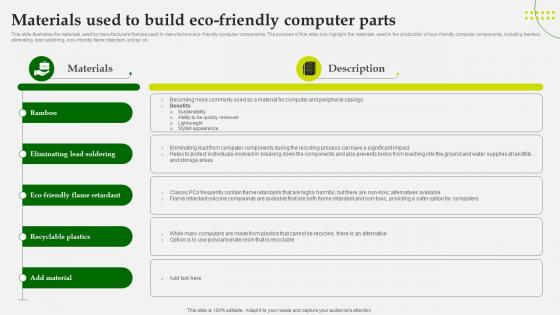
Green Computing Materials Used To Build Eco Friendly Computer Parts
This slide illustrates the materials used by manufacturers that are used to manufacture eco friendly computer components. The purpose of this slide is to highlight the materialsused in the production of eco friendly computer components, including bamboo, eliminating lead soldering, eco friendly flame retardant, and so on. Presenting this PowerPoint presentation, titled Green Computing Materials Used To Build Eco Friendly Computer Parts with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Green Computing Materials Used To Build Eco Friendly Computer Parts Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Green Computing Materials Used To Build Eco Friendly Computer Parts that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide illustrates the materials used by manufacturers that are used to manufacture eco-friendly computer components. The purpose of this slide is to highlight the materialsused in the production of eco-friendly computer components, including bamboo, eliminating lead soldering, eco-friendly flame retardant, and so on.
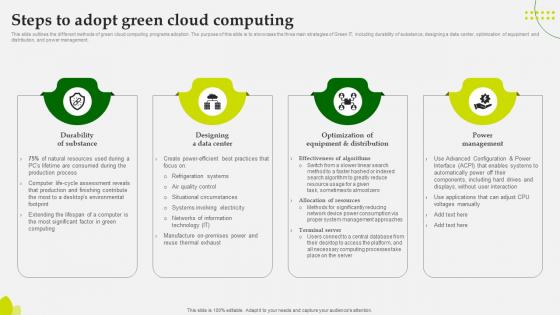
Green Computing Steps To Adopt Green Cloud Computing
This slide outlines the different methods of green cloud computing programs adoption. The purpose of this slide is to showcase the three main strategiesof Green IT, including durability of substance, designing a data center, optimization of equipment and distribution, and power management. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Green Computing Steps To Adopt Green Cloud Computing a try. Our experts have put a lot of knowledge and effort into creating this impeccable Green Computing Steps To Adopt Green Cloud Computing You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide outlines the different methods of green cloud computing programs adoption. The purpose of this slide is to showcase the three main strategiesof Green IT, including durability of substance, designing a data center, optimization of equipment and distribution, and power management.

Green Computing Types Of Green Data Centers Waste Management
This slide represents the overview of waste management types of green data centers. The purpose of this slide is to showcase the total percentage of e-waste landfill and how e-waste can be reduced using circular economy principles and dynamic UPS systems. If you are looking for a format to display your unique thoughts, then the professionally designed Green Computing Types Of Green Data Centers Waste Management is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Green Computing Types Of Green Data Centers Waste Management and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide represents the overview of waste management types of green data centers. The purpose of this slide is to showcase the total percentage of e-waste landfill and how e-waste can be reduced using circular economy principles and dynamic UPS systems.

Sustainable Certifications And Education In Green Cloud Computing
This slide outlines the overview of certifications and education in green cloud computing. The purpose of this slide is to showcase the various initiative and accreditations for green cloud computing. The green initiatives include ICT sustainability, Green ICT approaches, and so on. If you are looking for a format to display your unique thoughts, then the professionally designed Sustainable Certifications And Education In Green Cloud Computing is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Sustainable Certifications And Education In Green Cloud Computing and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide outlines the overview of certifications and education in green cloud computing. The purpose of this slide is to showcase the various initiative and accreditations for green cloud computing. The green initiatives include ICT sustainability, Green ICT approaches, and so on.

Sustainable Checklist To Implement Green Cloud Computing
This slide describes the checklist to implementing green cloud computing in a company. The purpose of this slide is to showcase the different strategies to implement green IT, including knowing when to use the cloud, offsetting carbon emissions, green cloud architecture, and choosing the right cloud service. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Sustainable Checklist To Implement Green Cloud Computing and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide describes the checklist to implementing green cloud computing in a company. The purpose of this slide is to showcase the different strategies to implement green IT, including knowing when to use the cloud, offsetting carbon emissions, green cloud architecture, and choosing the right cloud service.
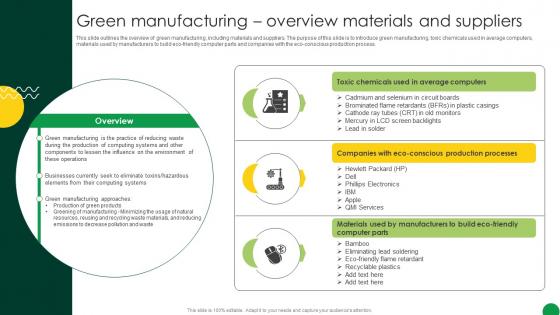
Sustainable Green Manufacturing Overview Materials And Suppliers
This slide outlines the overview of green manufacturing, including materials and suppliers. The purpose of this slide is to introduce green manufacturing, toxic chemicals used in average computers, materials used by manufacturers to build eco-friendly computer parts and companies with the eco-conscious production process. Presenting this PowerPoint presentation, titled Sustainable Green Manufacturing Overview Materials And Suppliers, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Sustainable Green Manufacturing Overview Materials And Suppliers. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Sustainable Green Manufacturing Overview Materials And Suppliers that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide outlines the overview of green manufacturing, including materials and suppliers. The purpose of this slide is to introduce green manufacturing, toxic chemicals used in average computers, materials used by manufacturers to build eco-friendly computer parts and companies with the eco-conscious production process.
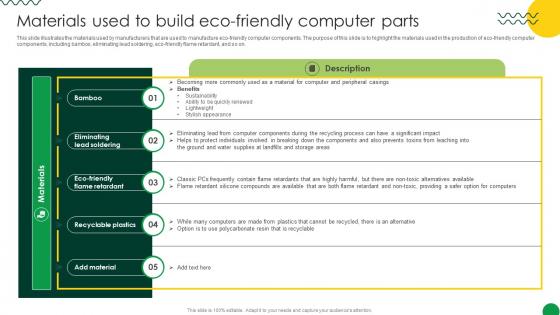
Sustainable Materials Used To Build Eco Friendly Computer Parts
This slide illustrates the materials used by manufacturers that are used to manufacture eco-friendly computer components. The purpose of this slide is to highlight the materials used in the production of eco-friendly computer components, including bamboo, eliminating lead soldering, eco-friendly flame retardant, and so on. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Sustainable Materials Used To Build Eco Friendly Computer Parts a try. Our experts have put a lot of knowledge and effort into creating this impeccable Sustainable Materials Used To Build Eco Friendly Computer Parts. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide illustrates the materials used by manufacturers that are used to manufacture eco-friendly computer components. The purpose of this slide is to highlight the materials used in the production of eco-friendly computer components, including bamboo, eliminating lead soldering, eco-friendly flame retardant, and so on.
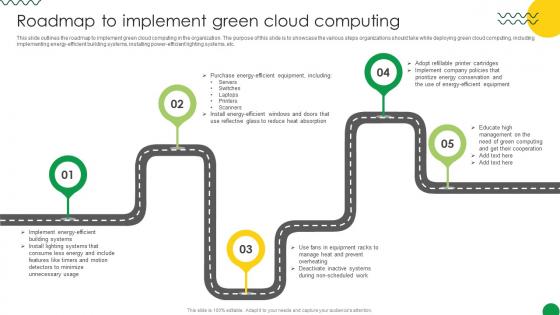
Sustainable Roadmap To Implement Green Cloud Computing
This slide outlines the roadmap to implement green cloud computing in the organization. The purpose of this slide is to showcase the various steps organizations should take while deploying green cloud computing, including implementing energy-efficient building systems, installing power-efficient lighting systems, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Sustainable Roadmap To Implement Green Cloud Computing is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Sustainable Roadmap To Implement Green Cloud Computing and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide outlines the roadmap to implement green cloud computing in the organization. The purpose of this slide is to showcase the various steps organizations should take while deploying green cloud computing, including implementing energy-efficient building systems, installing power-efficient lighting systems, etc.
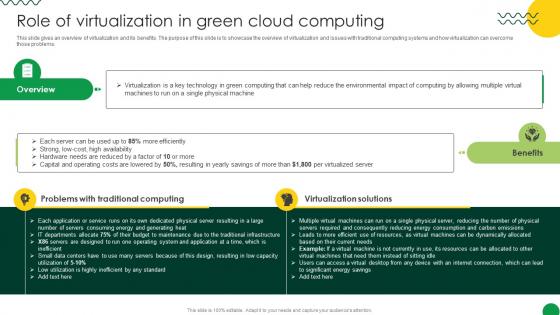
Sustainable Role Of Virtualization In Green Cloud Computing
This slide gives an overview of virtualization and its benefits. The purpose of this slide is to showcase the overview of virtualization and issues with traditional computing systems and how virtualization can overcome those problems. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Sustainable Role Of Virtualization In Green Cloud Computing and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide gives an overview of virtualization and its benefits. The purpose of this slide is to showcase the overview of virtualization and issues with traditional computing systems and how virtualization can overcome those problems.

Sustainable Types Of Green Data Centers Water And Wastewater Management
This slide gives an overview of the water and wastewater management types of green data centers. The purpose of this slide is to showcase the essential water-related green data center initiatives and water withdrawal breakdown of Facebook. If you are looking for a format to display your unique thoughts, then the professionally designed Sustainable Types Of Green Data Centers Water And Wastewater Management is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Sustainable Types Of Green Data Centers Water And Wastewater Management and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide gives an overview of the water and wastewater management types of green data centers. The purpose of this slide is to showcase the essential water-related green data center initiatives and water withdrawal breakdown of Facebook.
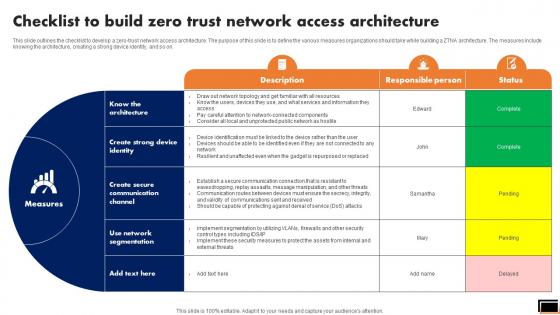
Checklist To Build Zero Trust Network Access Architecture Software Defined Perimeter SDP
This slide outlines the checklist to develop a zero-trust network access architecture. The purpose of this slide is to define the various measures organizations should take while building a ZTNA architecture. The measures include knowing the architecture, creating a strong device identity, and so on. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Checklist To Build Zero Trust Network Access Architecture Software Defined Perimeter SDP a try. Our experts have put a lot of knowledge and effort into creating this impeccable Checklist To Build Zero Trust Network Access Architecture Software Defined Perimeter SDP. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide outlines the checklist to develop a zero-trust network access architecture. The purpose of this slide is to define the various measures organizations should take while building a ZTNA architecture. The measures include knowing the architecture, creating a strong device identity, and so on.
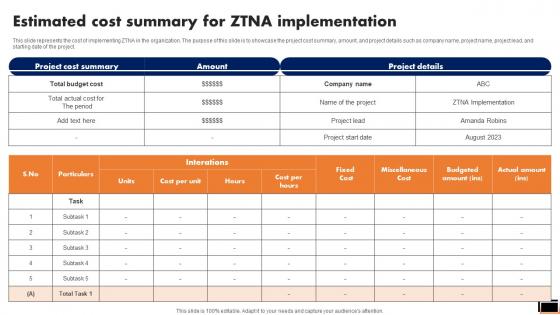
Estimated Cost Summary For Ztna Implementation Software Defined Perimeter SDP
This slide represents the cost of implementing ZTNA in the organization. The purpose of this slide is to showcase the project cost summary, amount, and project details such as company name, project name, project lead, and starting date of the project. If you are looking for a format to display your unique thoughts, then the professionally designed Estimated Cost Summary For Ztna Implementation Software Defined Perimeter SDP is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Estimated Cost Summary For Ztna Implementation Software Defined Perimeter SDP and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide represents the cost of implementing ZTNA in the organization. The purpose of this slide is to showcase the project cost summary, amount, and project details such as company name, project name, project lead, and starting date of the project.

External Components Of Zero Trust Network Architecture Software Defined Perimeter SDP
This slide gives an overview of external elements of zero trust network architecture. The purpose of this slide is to showcase the various external components and their working, covering CDM systems, industry compliance, threat intelligence, activity logs, data access policy, and so on. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download External Components Of Zero Trust Network Architecture Software Defined Perimeter SDP and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide gives an overview of external elements of zero trust network architecture. The purpose of this slide is to showcase the various external components and their working, covering CDM systems, industry compliance, threat intelligence, activity logs, data access policy, and so on.
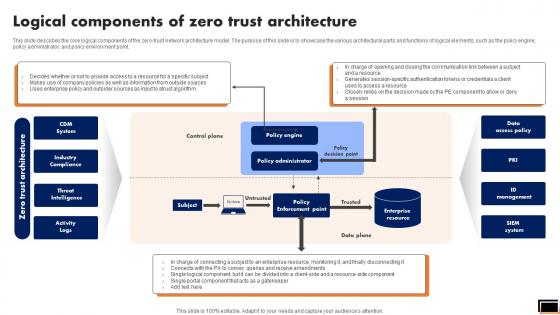
Logical Components Of Zero Trust Architecture Software Defined Perimeter SDP
This slide describes the core logical components of the zero-trust network architecture model. The purpose of this slide is to showcase the various architectural parts and functions of logical elements, such as the policy engine, policy administrator, and policy environment point. This Logical Components Of Zero Trust Architecture Software Defined Perimeter SDP is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Logical Components Of Zero Trust Architecture Software Defined Perimeter SDP features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide describes the core logical components of the zero-trust network architecture model. The purpose of this slide is to showcase the various architectural parts and functions of logical elements, such as the policy engine, policy administrator, and policy environment point.
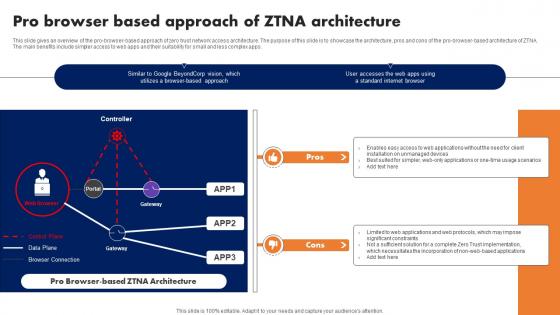
Pro Browser Based Approach Of Ztna Architecture Software Defined Perimeter SDP
This slide gives an overview of the pro-browser-based approach of zero trust network access architecture. The purpose of this slide is to showcase the architecture, pros and cons of the pro-browser-based architecture of ZTNA. The main benefits include simpler access to web apps and their suitability for small and less complex apps. Presenting this PowerPoint presentation, titled Pro Browser Based Approach Of Ztna Architecture Software Defined Perimeter SDP, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Pro Browser Based Approach Of Ztna Architecture Software Defined Perimeter SDP. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Pro Browser Based Approach Of Ztna Architecture Software Defined Perimeter SDP that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide gives an overview of the pro-browser-based approach of zero trust network access architecture. The purpose of this slide is to showcase the architecture, pros and cons of the pro-browser-based architecture of ZTNA. The main benefits include simpler access to web apps and their suitability for small and less complex apps.
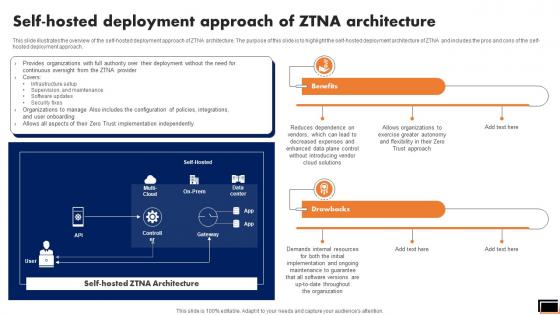
Self-Hosted Deployment Approach Of Ztna Architecture Software Defined Perimeter SDP
This slide talks about the ways in which ZTNA improves the business operations and security. The purpose of this slide is to showcase the various domains that zero trust network access improves, including increased user experience, remote workforce protection, improve data protection, and network visibility. Do you know about Slidesgeeks Self-Hosted Deployment Approach Of Ztna Architecture Software Defined Perimeter SDP These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide illustrates the overview of the self-hosted deployment approach of ZTNA architecture. The purpose of this slide is to highlight the self-hosted deployment architecture of ZTNA and includes the pros and cons of the self-hosted deployment approach.

Step 4 And 5 Available Technology Review And Zero Trust Initiatives Launch Software Defined Perimeter SDP
This slide represents the fourth and fifth steps of ZTNA deployment, which is reviewing available technology and launching primary zero trust projects. The purpose of this slide is to showcase the next steps in zero trust model implementation. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Step 4 And 5 Available Technology Review And Zero Trust Initiatives Launch Software Defined Perimeter SDP a try. Our experts have put a lot of knowledge and effort into creating this impeccable Step 4 And 5 Available Technology Review And Zero Trust Initiatives Launch Software Defined Perimeter SDP. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide represents the fourth and fifth steps of ZTNA deployment, which is reviewing available technology and launching primary zero trust projects. The purpose of this slide is to showcase the next steps in zero trust model implementation.
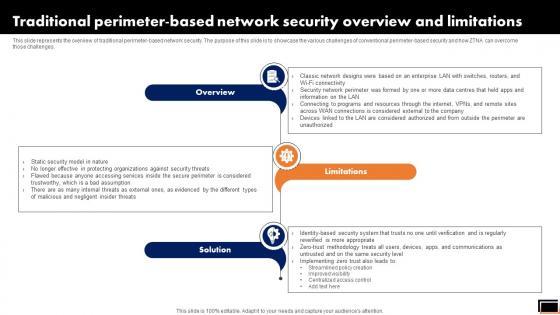
Traditional Perimeter-Based Network Security Overview And Limitations Software Defined Perimeter SDP
This slide represents the overview of traditional perimeter-based network security. The purpose of this slide is to showcase the various challenges of conventional perimeter-based security and how ZTNA can overcome those challenges. If you are looking for a format to display your unique thoughts, then the professionally designed Traditional Perimeter-Based Network Security Overview And Limitations Software Defined Perimeter SDP is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Traditional Perimeter-Based Network Security Overview And Limitations Software Defined Perimeter SDP and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide represents the overview of traditional perimeter-based network security. The purpose of this slide is to showcase the various challenges of conventional perimeter-based security and how ZTNA can overcome those challenges.
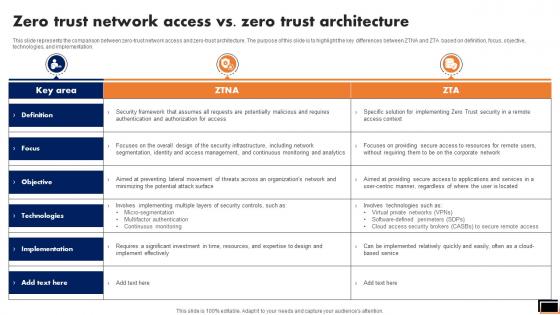
Zero Trust Network Access Vs Zero Trust Architecture Software Defined Perimeter SDP
This slide represents the comparison between zero-trust network access and zero-trust architecture. The purpose of this slide is to highlight the key differences between ZTNA and ZTA based on definition, focus, objective, technologies, and implementation. Presenting this PowerPoint presentation, titled Zero Trust Network Access Vs Zero Trust Architecture Software Defined Perimeter SDP, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Zero Trust Network Access Vs. Zero Trust Architecture Software Defined Perimeter SDP. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Zero Trust Network Access Vs. Zero Trust Architecture Software Defined Perimeter SDP that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide represents the comparison between zero-trust network access and zero-trust architecture. The purpose of this slide is to highlight the key differences between ZTNA and ZTA based on definition, focus, objective, technologies, and implementation.
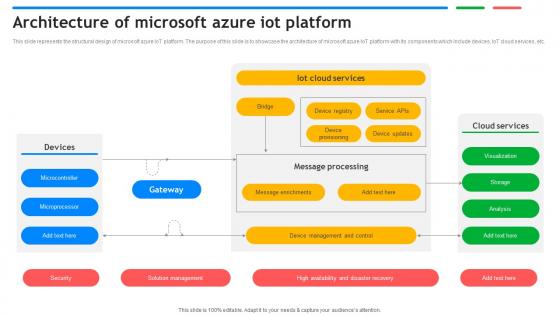
Architecture Of Microsoft Azure IoT Platform Exploring Google Cloud IoT Platform
This slide represents the structural design of microsoft azure IoT platform. The purpose of this slide is to showcase the architecture of microsoft azure IoT platform with its components which include devices, IoT cloud services, etc.Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Architecture Of Microsoft Azure IoT Platform Exploring Google Cloud IoT Platform a try. Our experts have put a lot of knowledge and effort into creating this impeccable Architecture Of Microsoft Azure IoT Platform Exploring Google Cloud IoT Platform You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide represents the structural design of microsoft azure IoT platform. The purpose of this slide is to showcase the architecture of microsoft azure IoT platform with its components which include devices, IoT cloud services, etc.
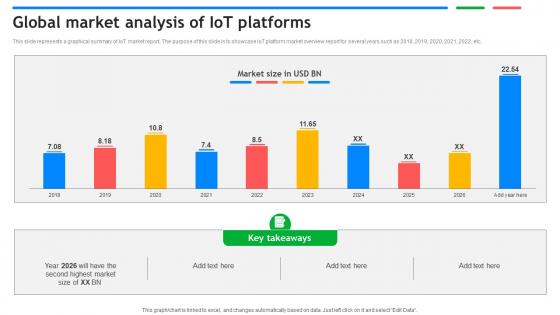
Global Market Analysis Of IoT Platforms Exploring Google Cloud IoT Platform
This slide represents a graphical summary of IoT market report. The purpose of this slide is to showcase IoT platform market overview report for several years such as 2018, 2019, 2020, 2021, 2022, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Global Market Analysis Of IoT Platforms Exploring Google Cloud IoT Platform and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide represents a graphical summary of IoT market report. The purpose of this slide is to showcase IoT platform market overview report for several years such as 2018, 2019, 2020, 2021, 2022, etc.

Key Benefits Of Using IoT Platforms Exploring Google Cloud IoT Platform
This slide outlines the various advantages of IoT platform utilization. The purpose of this slide is to showcase the key benefits of using IoT platforms which include scalability, security, cost saving, etc. Presenting this PowerPoint presentation, titled Key Benefits Of Using IoT Platforms Exploring Google Cloud IoT Platform with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Key Benefits Of Using IoT Platforms Exploring Google Cloud IoT Platform Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Key Benefits Of Using IoT Platforms Exploring Google Cloud IoT Platform that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide outlines the various advantages of IoT platform utilization. The purpose of this slide is to showcase the key benefits of using IoT platforms which include scalability, security, cost saving, etc.

Budget For Social Media Analytics Tools Training Cracking The Code Of Social Media
This slide shows the cost breakup of a Social Media Analytics awareness and mitigation training program. The purpose of this slide is to highlight the estimated cost of various training components, such as instructors cost, training material cost, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Budget For Social Media Analytics Tools Training Cracking The Code Of Social Media a try. Our experts have put a lot of knowledge and effort into creating this impeccable Budget For Social Media Analytics Tools Training Cracking The Code Of Social Media. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide shows the cost breakup of a Social Media Analytics awareness and mitigation training program. The purpose of this slide is to highlight the estimated cost of various training components, such as instructors cost, training material cost, etc.
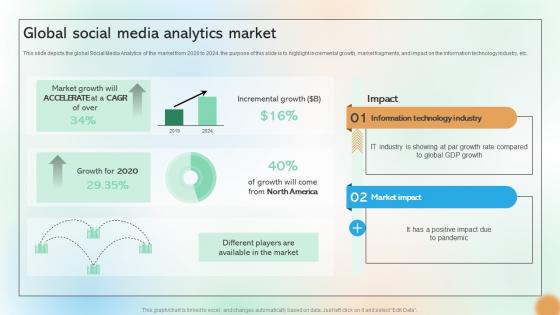
Global Social Media Analytics Market Cracking The Code Of Social Media
This slide depicts the global Social Media Analytics of the market from 2020 to 2024. the purpose of this slide is to highlight incremental growth, market fragments, and impact on the information technology industry, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Global Social Media Analytics Market Cracking The Code Of Social Media a try. Our experts have put a lot of knowledge and effort into creating this impeccable Global Social Media Analytics Market Cracking The Code Of Social Media. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide depicts the global Social Media Analytics of the market from 2020 to 2024. the purpose of this slide is to highlight incremental growth, market fragments, and impact on the information technology industry, etc.
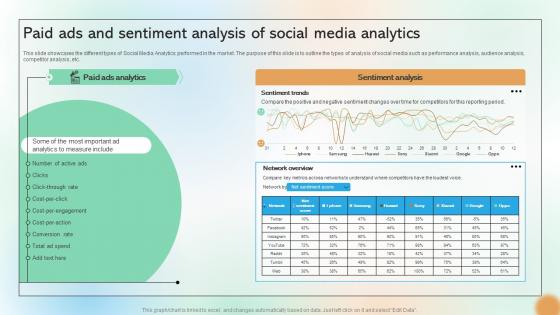
Paid Ads And Sentiment Analysis Of Social Media Analytics Cracking The Code Of Social Media
This slide showcases the different types of Social Media Analytics performed in the market. The purpose of this slide is to outline the types of analysis of social media such as performance analysis, audience analysis, competitor analysis, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Paid Ads And Sentiment Analysis Of Social Media Analytics Cracking The Code Of Social Media a try. Our experts have put a lot of knowledge and effort into creating this impeccable Paid Ads And Sentiment Analysis Of Social Media Analytics Cracking The Code Of Social Media. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide showcases the different types of Social Media Analytics performed in the market. The purpose of this slide is to outline the types of analysis of social media such as performance analysis, audience analysis, competitor analysis, etc.

Global Market Analysis Of Secure Web Gateway Web Threat Protection System
This slide depicts the industry analysis and forecast for Secure Web Gateway. The purpose of this slide is to illustrate the market of SWG security technology. The components covered are market size, regional analysis and component segment overview. If you are looking for a format to display your unique thoughts, then the professionally designed Global Market Analysis Of Secure Web Gateway Web Threat Protection System is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Global Market Analysis Of Secure Web Gateway Web Threat Protection System and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide depicts the industry analysis and forecast for Secure Web Gateway. The purpose of this slide is to illustrate the market of SWG security technology. The components covered are market size, regional analysis and component segment overview.
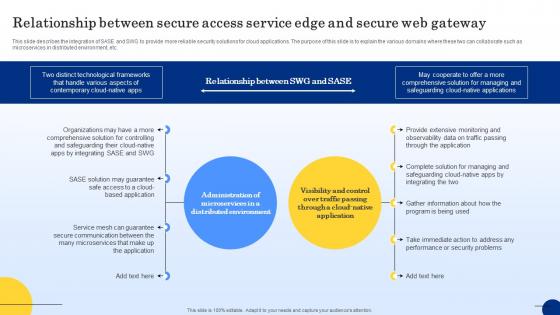
Relationship Between Secure Access Service Edge Web Threat Protection System
This slide describes the integration of SASE and SWG to provide more reliable security solutions for cloud applications. The purpose of this slide is to explain the various domains where these two can collaborate such as microservices in distributed environment, etc. Presenting this PowerPoint presentation, titled Relationship Between Secure Access Service Edge Web Threat Protection System, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Relationship Between Secure Access Service Edge Web Threat Protection System. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Relationship Between Secure Access Service Edge Web Threat Protection System that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide describes the integration of SASE and SWG to provide more reliable security solutions for cloud applications. The purpose of this slide is to explain the various domains where these two can collaborate such as microservices in distributed environment, etc.

Secure Web Gateway For Remote And On Site Workers Web Threat Protection System
This slide represents the on-premise and cloud based SWG technology solution for organizations. The purpose of this slide is to provide visualization of Secure Web Gateway structure enabling encrypted web surfing for both on-site and remote employees. Do you know about Slidesgeeks Secure Web Gateway For Remote And On Site Workers Web Threat Protection System These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide represents the on-premise and cloud based SWG technology solution for organizations. The purpose of this slide is to provide visualization of Secure Web Gateway structure enabling encrypted web surfing for both on-site and remote employees.

Secure Web Gateway Set Up Ongoing Maintenance Web Threat Protection System
This slide represents the procedure for implementing Secure Web Gateway in network. The purpose of this slide is to explain the ongoing maintenance phase of SWG set-up. The key points included are inspect web gateway, examine security policies, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Secure Web Gateway Set Up Ongoing Maintenance Web Threat Protection System a try. Our experts have put a lot of knowledge and effort into creating this impeccable Secure Web Gateway Set Up Ongoing Maintenance Web Threat Protection System. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide represents the procedure for implementing Secure Web Gateway in network. The purpose of this slide is to explain the ongoing maintenance phase of SWG set-up. The key points included are inspect web gateway, examine security policies, etc.

Understanding Real World Use Cases Of Secure Web Gateway Web Threat Protection System
This slide outlines the prominent features of Secure Web Gateway which provide protection to organizations from severe cyber threats. The purpose of this slide is to define the use cases of SWG such as real time web traffic surveillance, access management, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Understanding Real World Use Cases Of Secure Web Gateway Web Threat Protection System is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Understanding Real World Use Cases Of Secure Web Gateway Web Threat Protection System and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide outlines the prominent features of Secure Web Gateway which provide protection to organizations from severe cyber threats. The purpose of this slide is to define the use cases of SWG such as real time web traffic surveillance, access management, etc.

Working Components Of Secure Web Gateway Architecture Web Threat Protection System
This slide represents the key elements involved in the working of Secure Web Gateway. The purpose of this slide is to explain the different components of SWG. These include traffic inspection, URL filtering, application control, website content inspection, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Working Components Of Secure Web Gateway Architecture Web Threat Protection System and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide represents the key elements involved in the working of Secure Web Gateway. The purpose of this slide is to explain the different components of SWG. These include traffic inspection, URL filtering, application control, website content inspection, etc.

Community Engagement Tools To Outreach Building A Winning Community Outreach Strategy SS V
This slide covers tools to increase engagement of community for particular cause or goals. The purpose oft this slide covers formal and informal ways to communicate with community, checking communication progress and integration, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Community Engagement Tools To Outreach Building A Winning Community Outreach Strategy SS V a try. Our experts have put a lot of knowledge and effort into creating this impeccable Community Engagement Tools To Outreach Building A Winning Community Outreach Strategy SS V. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide covers tools to increase engagement of community for particular cause or goals. The purpose oft this slide covers formal and informal ways to communicate with community, checking communication progress and integration, etc.
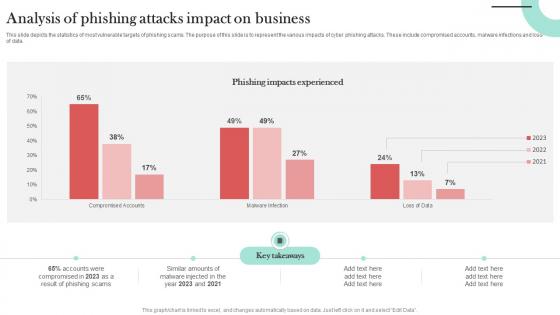
Analysis Of Phishing Attacks Impact Man In The Middle Phishing IT
This slide depicts the statistics of most vulnerable targets of phishing scams. The purpose of this slide is to represent the various impacts of cyber phishing attacks. These include compromised accounts, malware infections and loss of data. If you are looking for a format to display your unique thoughts, then the professionally designed Analysis Of Phishing Attacks Impact Man In The Middle Phishing IT is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Analysis Of Phishing Attacks Impact Man In The Middle Phishing IT and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide depicts the statistics of most vulnerable targets of phishing scams. The purpose of this slide is to represent the various impacts of cyber phishing attacks. These include compromised accounts, malware infections and loss of data.

Examples Of Clone Phishing Cyber Scams Man In The Middle Phishing IT
This slide demonstrates the various examples of clone phishing cyber scams. The purpose of this slide is to illustrate different types of clone phishing emails targeting different individuals. These include customer support scams, fake virus scams and refund scams. This Examples Of Clone Phishing Cyber Scams Man In The Middle Phishing IT is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Examples Of Clone Phishing Cyber Scams Man In The Middle Phishing IT features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide demonstrates the various examples of clone phishing cyber scams. The purpose of this slide is to illustrate different types of clone phishing emails targeting different individuals. These include customer support scams, fake virus scams and refund scams.
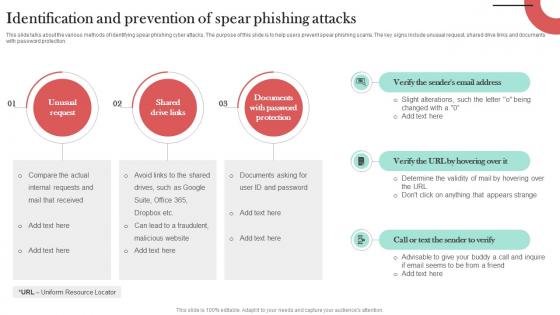
Identification And Prevention Of Spear Man In The Middle Phishing IT
This slide talks about the various methods of identifying spear phishing cyber attacks. The purpose of this slide is to help users prevent spear phishing scams. The key signs include unusual request, shared drive links and documents with password protection. Presenting this PowerPoint presentation, titled Identification And Prevention Of Spear Man In The Middle Phishing IT, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Identification And Prevention Of Spear Man In The Middle Phishing IT. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Identification And Prevention Of Spear Man In The Middle Phishing IT that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide talks about the various methods of identifying spear phishing cyber attacks. The purpose of this slide is to help users prevent spear phishing scams. The key signs include unusual request, shared drive links and documents with password protection.
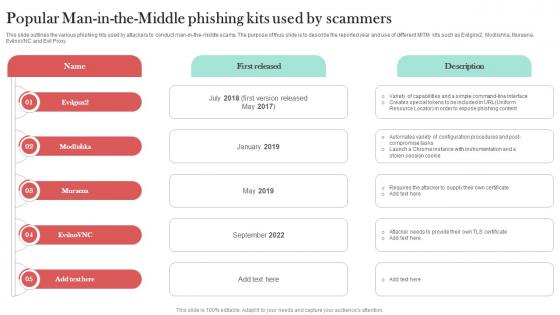
Popular Man In The Middle Phishing Kits Man In The Middle Phishing IT
This slide outlines the various phishing kits used by attackers to conduct man-in-the-middle scams. The purpose of thus slide is to describe the reported year and use of different MITM kits such as Evilginx2, Modlishka, Muraena, EvilnoVNC and Evil Proxy. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Popular Man In The Middle Phishing Kits Man In The Middle Phishing IT a try. Our experts have put a lot of knowledge and effort into creating this impeccable Popular Man In The Middle Phishing Kits Man In The Middle Phishing IT. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide outlines the various phishing kits used by attackers to conduct man-in-the-middle scams. The purpose of thus slide is to describe the reported year and use of different MITM kits such as Evilginx2, Modlishka, Muraena, EvilnoVNC and Evil Proxy.
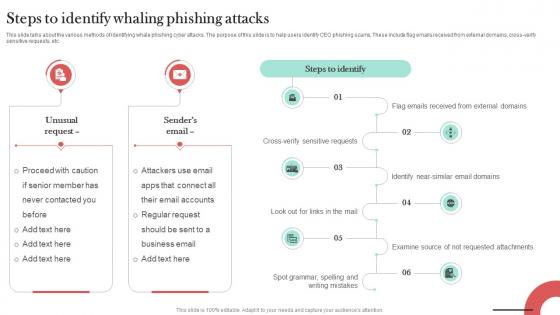
Steps To Identify Whaling Phishing Attacks Man In The Middle Phishing IT
This slide talks about the various methods of identifying whale phishing cyber attacks. The purpose of this slide is to help users identify CEO phishing scams. These include flag emails received from external domains, cross-verify sensitive requests, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Steps To Identify Whaling Phishing Attacks Man In The Middle Phishing IT is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Steps To Identify Whaling Phishing Attacks Man In The Middle Phishing IT and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide talks about the various methods of identifying whale phishing cyber attacks. The purpose of this slide is to help users identify CEO phishing scams. These include flag emails received from external domains, cross-verify sensitive requests, etc.
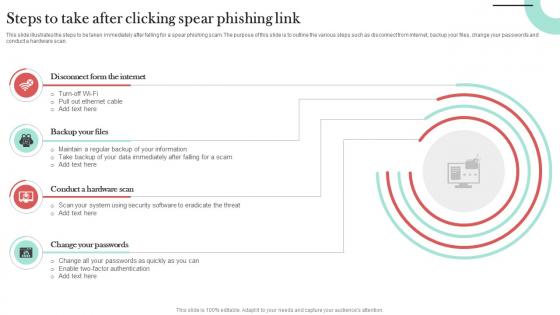
Steps To Take After Clicking Spear Phishing Link Man In The Middle Phishing IT
This slide illustrates the steps to be taken immediately after falling for a spear phishing scam. The purpose of this slide is to outline the various steps such as disconnect from internet, backup your files, change your passwords and conduct a hardware scan. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Steps To Take After Clicking Spear Phishing Link Man In The Middle Phishing IT and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide illustrates the steps to be taken immediately after falling for a spear phishing scam. The purpose of this slide is to outline the various steps such as disconnect from internet, backup your files, change your passwords and conduct a hardware scan.
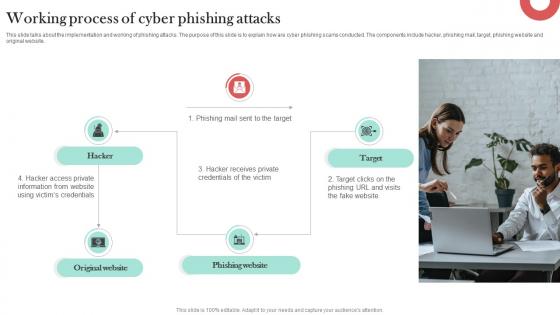
Working Process Of Cyber Phishing Attacks Man In The Middle Phishing IT
This slide talks about the implementation and working of phishing attacks. The purpose of this slide is to explain how are cyber phishing scams conducted. The components include hacker, phishing mail, target, phishing website and original website. Do you know about Slidesgeeks Working Process Of Cyber Phishing Attacks Man In The Middle Phishing IT These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide talks about the implementation and working of phishing attacks. The purpose of this slide is to explain how are cyber phishing scams conducted. The components include hacker, phishing mail, target, phishing website and original website.
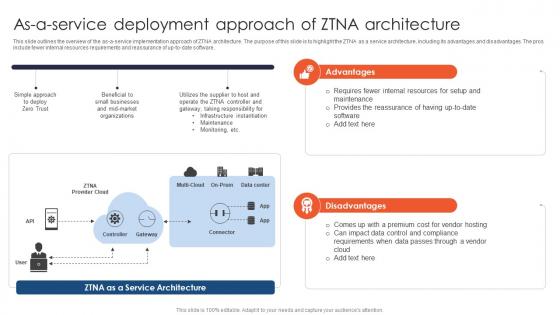
Zero Trust Network Access As A Service Deployment Approach Of ZTNA Architecture
This slide outlines the overview of the as-a-service implementation approach of ZTNA architecture. The purpose of this slide is to highlight the ZTNA as a service architecture, including its advantages and disadvantages. The pros include fewer internal resources requirements and reassurance of up-to-date software. If you are looking for a format to display your unique thoughts, then the professionally designed Zero Trust Network Access As A Service Deployment Approach Of ZTNA Architecture is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Zero Trust Network Access As A Service Deployment Approach Of ZTNA Architecture and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide outlines the overview of the as-a-service implementation approach of ZTNA architecture. The purpose of this slide is to highlight the ZTNA as a service architecture, including its advantages and disadvantages. The pros include fewer internal resources requirements and reassurance of up-to-date software.
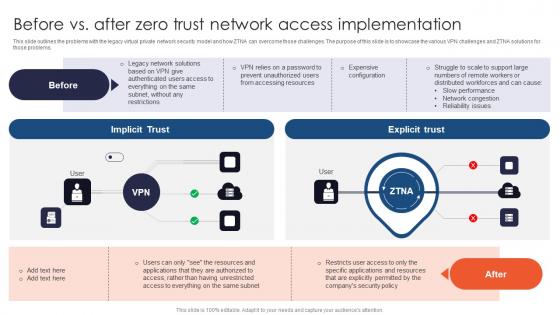
Zero Trust Network Access Before Vs After Zero Trust Network Access Implementation
This slide outlines the problems with the legacy virtual private network security model and how ZTNA can overcome those challenges. The purpose of this slide is to showcase the various VPN challenges and ZTNA solutions for those problems. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Zero Trust Network Access Before Vs After Zero Trust Network Access Implementation and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide outlines the problems with the legacy virtual private network security model and how ZTNA can overcome those challenges. The purpose of this slide is to showcase the various VPN challenges and ZTNA solutions for those problems.

Zero Trust Network Access Comparative Assessment Of ZTNA Version 1 0 And 2 0
This slide represents the comparison between zero trust network access versions 1.0 and 2.0. The purpose of this slide is to demonstrate the overview of both versions, including differences. It also includes the architecture of both versions of zero-trust network access. This Zero Trust Network Access Comparative Assessment Of ZTNA Version 1 0 And 2 0 is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Zero Trust Network Access Comparative Assessment Of ZTNA Version 1 0 And 2 0 features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide represents the comparison between zero trust network access versions 1.0 and 2.0. The purpose of this slide is to demonstrate the overview of both versions, including differences. It also includes the architecture of both versions of zero-trust network access.

Zero Trust Network Access Future And Emerging Trends In ZTNA Model
This slide outlines the future outlook and emerging trends in the zero trust network architecture model. The purpose of this slide is to showcase the various emerging future trends in the ZTNA model, including artificial intelligence, SASE, edge computing, the Internet of Things, and so on. Presenting this PowerPoint presentation, titled Zero Trust Network Access Future And Emerging Trends In ZTNA Model, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Zero Trust Network Access Future And Emerging Trends In ZTNA Model. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Zero Trust Network Access Future And Emerging Trends In ZTNA Model that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide outlines the future outlook and emerging trends in the zero trust network architecture model. The purpose of this slide is to showcase the various emerging future trends in the ZTNA model, including artificial intelligence, SASE, edge computing, the Internet of Things, and so on.

Zero Trust Network Access Main Pillars Of Zero Network Trust Access
This slide outlines the critical pillars of the zero network trust access model. The purpose of this slide is to showcase the primary pillars of ZTNA, including users, devices, networks, infrastructure, applications, data, visibility and analytics, and orchestration and automation. Do you know about Slidesgeeks Zero Trust Network Access Main Pillars Of Zero Network Trust Access These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide outlines the critical pillars of the zero network trust access model. The purpose of this slide is to showcase the primary pillars of ZTNA, including users, devices, networks, infrastructure, applications, data, visibility and analytics, and orchestration and automation.

Zero Trust Network Access Step 4 And 5 Available Technology Review And Zero Trust Initiatives Launch
This slide represents the fourth and fifth steps of ZTNA deployment, which is reviewing available technology and launching primary zero trust projects. The purpose of this slide is to showcase the next steps in zero trust model implementation. If you are looking for a format to display your unique thoughts, then the professionally designed Zero Trust Network Access Step 4 And 5 Available Technology Review And Zero Trust Initiatives Launch is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Zero Trust Network Access Step 4 And 5 Available Technology Review And Zero Trust Initiatives Launch and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide represents the fourth and fifth steps of ZTNA deployment, which is reviewing available technology and launching primary zero trust projects. The purpose of this slide is to showcase the next steps in zero trust model implementation.
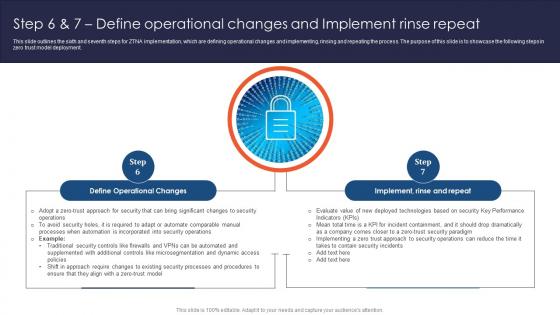
Zero Trust Network Access Step 6 And 7 Define Operational Changes And Implement Rinse Repeat
This slide outlines the sixth and seventh steps for ZTNA implementation, which are defining operational changes and implementing, rinsing and repeating the process. The purpose of this slide is to showcase the following steps in zero trust model deployment. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Zero Trust Network Access Step 6 And 7 Define Operational Changes And Implement Rinse Repeat and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide outlines the sixth and seventh steps for ZTNA implementation, which are defining operational changes and implementing, rinsing and repeating the process. The purpose of this slide is to showcase the following steps in zero trust model deployment.

Zero Trust Network Access Working Of Zero Trust Network Access Model
This slide outlines the working of zero trust network access. The purpose of this slide is to demonstrate the workflow of ZTNA, including the principles shared by all ZTNA architectures. The principles include no use of MPLS, hiding the IP addresses, securing devices, IDP and SSO platform, and so on. Presenting this PowerPoint presentation, titled Zero Trust Network Access Working Of Zero Trust Network Access Model, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Zero Trust Network Access Working Of Zero Trust Network Access Model. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Zero Trust Network Access Working Of Zero Trust Network Access Model that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide outlines the working of zero trust network access. The purpose of this slide is to demonstrate the workflow of ZTNA, including the principles shared by all ZTNA architectures. The principles include no use of MPLS, hiding the IP addresses, securing devices, IDP and SSO platform, and so on.

CASB 2 0 IT Benefits Of Cloud Access Security Broker 2 0
This slide represents the advantages of cloud access security broker version 2.0. The purpose of this slide is to highlight the main benefits of CASB 2.0, including comprehensive coverage, cost-effectiveness, enhanced security efficacy, improved visibility, app database, and so on. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give CASB 2 0 IT Benefits Of Cloud Access Security Broker 2 0 a try. Our experts have put a lot of knowledge and effort into creating this impeccable CASB 2 0 IT Benefits Of Cloud Access Security Broker 2 0. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide represents the advantages of cloud access security broker version 2.0. The purpose of this slide is to highlight the main benefits of CASB 2.0, including comprehensive coverage, cost-effectiveness, enhanced security efficacy, improved visibility, app database, and so on.
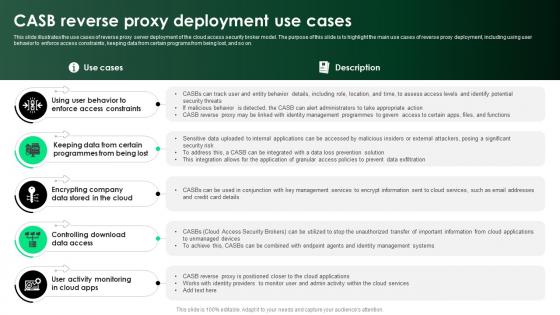
CASB 2 0 IT CASB Reverse Proxy Deployment Use Cases
This slide illustrates the use cases of reverse proxy server deployment of the cloud access security broker model. The purpose of this slide is to highlight the main use cases of reverse proxy deployment, including using user behavior to enforce access constraints, keeping data from certain programs from being lost, and so on. If you are looking for a format to display your unique thoughts, then the professionally designed CASB 2 0 IT CASB Reverse Proxy Deployment Use Cases is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download CASB 2 0 IT CASB Reverse Proxy Deployment Use Cases and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide illustrates the use cases of reverse proxy server deployment of the cloud access security broker model. The purpose of this slide is to highlight the main use cases of reverse proxy deployment, including using user behavior to enforce access constraints, keeping data from certain programs from being lost, and so on.
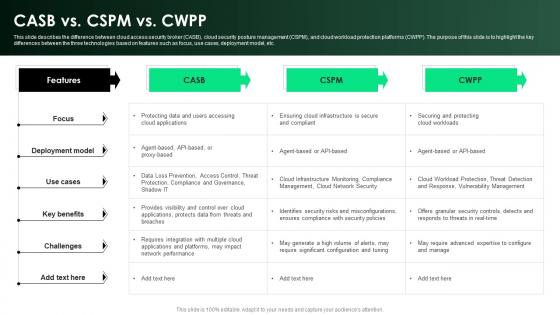
CASB 2 0 IT CASB Vs CSPM Vs CWPP Ppt Diagram Graph Charts
This slide describes the difference between cloud access security broker CASB , cloud security posture management CSPM , and cloud workload protection platforms CWPP . The purpose of this slide is to highlight the key differences between the three technologies based on features such as focus, use cases, deployment model, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download CASB 2 0 IT CASB Vs CSPM Vs CWPP Ppt Diagram Graph Charts and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide describes the difference between cloud access security broker CASB , cloud security posture management CSPM , and cloud workload protection platforms CWPP . The purpose of this slide is to highlight the key differences between the three technologies based on features such as focus, use cases, deployment model, etc.
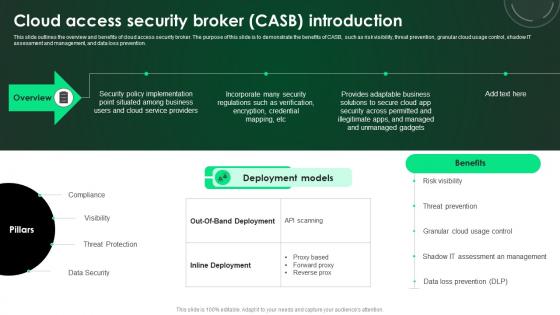
CASB 2 0 IT Cloud Access Security Broker CASB Introduction
This slide outlines the overview and benefits of cloud access security broker. The purpose of this slide is to demonstrate the benefits of CASB, such as risk visibility, threat prevention, granular cloud usage control, shadow IT assessment and management, and data loss prevention. This CASB 2 0 IT Cloud Access Security Broker CASB Introduction is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The CASB 2 0 IT Cloud Access Security Broker CASB Introduction features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide outlines the overview and benefits of cloud access security broker. The purpose of this slide is to demonstrate the benefits of CASB, such as risk visibility, threat prevention, granular cloud usage control, shadow IT assessment and management, and data loss prevention.
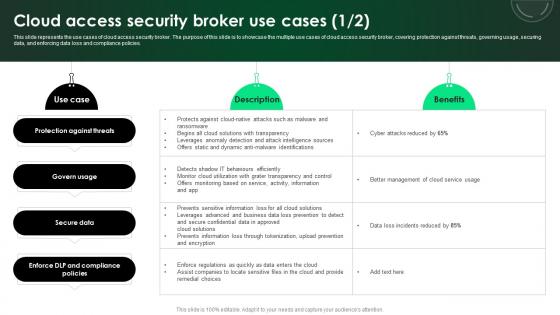
CASB 2 0 IT Cloud Access Security Broker Use Cases
This slide represents the use cases of cloud access security broker. The purpose of this slide is to showcase the multiple use cases of cloud access security broker, covering protection against threats, governing usage, securing data, and enforcing data loss and compliance policies. Presenting this PowerPoint presentation, titled CASB 2 0 IT Cloud Access Security Broker Use Cases, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this CASB 2 0 IT Cloud Access Security Broker Use Cases. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable CASB 2 0 IT Cloud Access Security Broker Use Cases that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide represents the use cases of cloud access security broker. The purpose of this slide is to showcase the multiple use cases of cloud access security broker, covering protection against threats, governing usage, securing data, and enforcing data loss and compliance policies.

CASB 2 0 IT Comparison Between Reverse Proxy And Load Balancer
This slide represents the difference between reverse proxy and load balancer. The purpose of this slide is to highlight the main differences between reverse proxy server and load balancer based on how they respond to client request, number of servers required, and so on. Do you know about Slidesgeeks CASB 2 0 IT Comparison Between Reverse Proxy And Load Balancer These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide represents the difference between reverse proxy and load balancer. The purpose of this slide is to highlight the main differences between reverse proxy server and load balancer based on how they respond to client request, number of servers required, and so on.

CASB 2 0 IT Overview Of CASB Deployment Models
This slide talks about the implementation models of cloud access security broker. The purpose of this slide is to demonstrate the two types of CASB deployment, such as out-of-band and inline. The CASB deployment models include API scanning and forward and reverse proxy. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give CASB 2 0 IT Overview Of CASB Deployment Models a try. Our experts have put a lot of knowledge and effort into creating this impeccable CASB 2 0 IT Overview Of CASB Deployment Models. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide talks about the implementation models of cloud access security broker. The purpose of this slide is to demonstrate the two types of CASB deployment, such as out-of-band and inline. The CASB deployment models include API scanning and forward and reverse proxy.

CASB 2 0 IT Shadow It Management Lifecycle Overview
This slide outlines the lifecycle of shadow IT management for safely adopting cloud apps. The purpose of this slide is to showcase the various stages of the lifecycle, such as discovering shadow IT, knowing the risk level of apps, evaluating compliance, analyzing usage, governing cloud apps, and continuous monitoring. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download CASB 2 0 IT Shadow It Management Lifecycle Overview and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide outlines the lifecycle of shadow IT management for safely adopting cloud apps. The purpose of this slide is to showcase the various stages of the lifecycle, such as discovering shadow IT, knowing the risk level of apps, evaluating compliance, analyzing usage, governing cloud apps, and continuous monitoring.


 Continue with Email
Continue with Email

 Home
Home


































