Real Estate Network
Group Social Network Ppt PowerPoint Slides And Ppt Diagram Templates
Group Social Network PPT PowerPoint Slides And PPT Diagram Templates-These high quality, editable pre-designed powerpoint slides have been carefully created by our professional team to help you impress your audience. Each graphic in every slide is vector based and is 100% editable in powerpoint. Each and every property of any slide - color, size, shading etc can be modified to build an effective powerpoint presentation. Use these slides to convey complex business concepts in a simplified manner. Any text can be entered at any point in the powerpoint slide. Simply DOWNLOAD, TYPE and PRESENT! Your thought process will never falter. Our Group Social Network Ppt PowerPoint Slides And Ppt Diagram Templates will steer them along correctly.
Mind Map Network Diagram PowerPoint Slides Map Nodes Ppt
Mind Map Network Diagram PowerPoint Slides Map Nodes PPT-These high quality powerpoint pre-designed slides and powerpoint templates have been carefully created by our professional team to help you impress your audience. All slides have been created and are 100% editable in powerpoint. Each and every property of any graphic - color, size, orientation, shading, outline etc. can be modified to help you build an effective powerpoint presentation. Any text can be entered at any point in the powerpoint template or slide. Simply DOWNLOAD, TYPE and PRESENT!-These slides can be used for presentation themes relating to-Brain, brainstorming, business, clearance, communications, decision, discharging, graphic, leadership, making, management, map, mapping, mind, mind-map, option, problem, problem-solving, process, project, question, red, solutions, solve, solving, technique, think, training, why Don't let it drag with our Mind Map Network Diagram PowerPoint Slides Map Nodes Ppt. They help you keep it crisp and concise.
Network Diagram Mind Map PowerPoint Templates Ppt Slides
Network Diagram Mind Map PowerPoint templates PPT Slides-These high quality powerpoint pre-designed slides and powerpoint templates have been carefully created by our professional team to help you impress your audience. All slides have been created and are 100% editable in powerpoint. Each and every property of any graphic - color, size, orientation, shading, outline etc. can be modified to help you build an effective powerpoint presentation. Any text can be entered at any point in the powerpoint template or slide. Simply DOWNLOAD, TYPE and PRESENT!-These slides can be used for presentation themes relating to-Brain, brainstorming, business, clearance, communications, decision, discharging, graphic, leadership, making, management, map, mapping, mind, mind-map, option, problem, problem-solving, process, project, question, red, solutions, solve, solving, technique, think, training, why Our Network Diagram Mind Map PowerPoint Templates Ppt Slides will channel your creativity. They place your ideas at the forefront.
Sales Network Clustering 2d PowerPoint Slides And Ppt Diagram Templates
Sales Network Clustering 2D PowerPoint Slides And PPT Diagram Templates-These high quality powerpoint pre-designed slides and powerpoint templates have been carefully created by our professional team to help you impress your audience. All slides have been created and are 100% editable in powerpoint. Each and every property of any graphic - color, size, orientation, shading, outline etc. can be modified to help you build an effective powerpoint presentation. Any text can be entered at any point in the powerpoint template or slide. Simply DOWNLOAD, TYPE and PRESENT! Our Sales Network Clustering 2d PowerPoint Slides And Ppt Diagram Templates have a festive effect. The audience will celebrate your ideas.
Teamwork Social Network 2 PowerPoint Slides And Ppt Diagram Templates
Teamwork Social Network 2 PowerPoint Slides And PPT Diagram Templates-These high quality powerpoint pre-designed slides and powerpoint templates have been carefully created by our professional team to help you impress your audience. All slides have been created and are 100% editable in powerpoint. Each and every property of any graphic - color, size, orientation, shading, outline etc. can be modified to help you build an effective powerpoint presentation. Any text can be entered at any point in the powerpoint template or slide. Simply DOWNLOAD, TYPE and PRESENT! Acquire a flourish with our Teamwork Social Network 2 PowerPoint Slides And Ppt Diagram Templates. Your thoughts will begin to flower.

Render Human Connection Networking PowerPoint Templates And PowerPoint Backgrounds 0511
Microsoft PowerPoint Template and Background with 3D render human connections around the world Overcome resistance with our Render Human Connection Networking PowerPoint Templates And PowerPoint Backgrounds 0511. You will come out on top.

Render Human Connection Networking PowerPoint Themes And PowerPoint Slides 0511
Microsoft PowerPoint Slide and Theme with 3D render human connections around the world Our Render Human Connection Networking PowerPoint Themes And PowerPoint Slides 0511 cover a broad ambit. They help you articulate on an array of aspects.

Our Proposed Network Architecture For Firewall Migration Proposal
This slide represents the proposed network architecture for the firewall migration proposal. It shows the network architecture after migrating to a new firewall solution, and its components include workstation PCs, internal switch, directory server, internet, internal and external firewalls, etc.Power up your presentations with our Our Proposed Network Architecture For Firewall Migration Proposal single-slide PPT template. Our visually-stunning template will help you deliver your message with confidence. With easy-to-use editing options and fully customizable features, you can create polished and captivating presentations in no time. Say goodbye to boring slides and hello to impactful presentations with our top-quality template. Download now and get ready to wow your audience. singles This slide represents the proposed network architecture for the firewall migration proposal. It shows the network architecture after migrating to a new firewall solution, and its components include workstation PCs, internal switch, directory server, internet, internal and external firewalls, etc.

Zero Trust Network Access System Use Cases Themes Pdf
This slide outlines the workflow of zero trust network access architecture. The purpose of this slide is to showcase the various steps of the ZTNA model workflow, including user authentication, grant access, monitoring of user sessions, and threat response. Present like a pro with Zero Trust Network Access System Use Cases Themes Pdf Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide outlines the workflow of zero trust network access architecture. The purpose of this slide is to showcase the various steps of the ZTNA model workflow, including user authentication, grant access, monitoring of user sessions, and threat response.
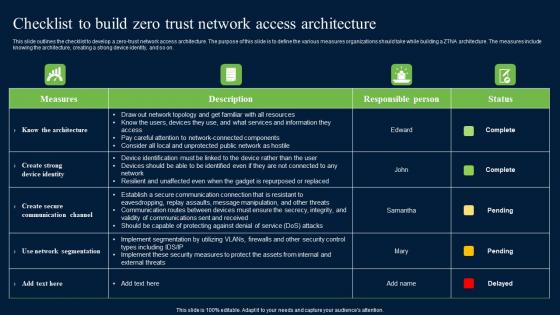
Checklist To Build Zero Trust Network Access Security Structure Pdf
This slide outlines the checklist to develop a zero-trust network access architecture. The purpose of this slide is to define the various measures organizations should take while building a ZTNA architecture. The measures include knowing the architecture, creating a strong device identity, and so on. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Checklist To Build Zero Trust Network Access Security Structure Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Checklist To Build Zero Trust Network Access Security Structure Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide outlines the checklist to develop a zero-trust network access architecture. The purpose of this slide is to define the various measures organizations should take while building a ZTNA architecture. The measures include knowing the architecture, creating a strong device identity, and so on.

Fibers IT 5g Transport Network Architecture And Photonic Systems
This slide represents the relationship between 5g transport network architecture and the photonics system. The purpose of this slide is to showcase the transformation of transform network architecture through three stages such as traditional RBS, main remote system and centralized RAN. There are so many reasons you need a Fibers IT 5g Transport Network Architecture And Photonic Systems. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide represents the relationship between 5g transport network architecture and the photonics system. The purpose of this slide is to showcase the transformation of transform network architecture through three stages such as traditional RBS, main remote system and centralized RAN.
5g Transport Network Silicon Photonics SiPh It Ppt Example
This slide represents the relationship between 5g transport network architecture and the photonics system. The purpose of this slide is to showcase the transformation of transform network architecture through three stages such as traditional RBS, main remote system and centralized RAN.Find a pre-designed and impeccable 5g Transport Network Silicon Photonics SiPh It Ppt Example. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide represents the relationship between 5g transport network architecture and the photonics system. The purpose of this slide is to showcase the transformation of transform network architecture through three stages such as traditional RBS, main remote system and centralized RAN.

Zero Trust Model Zero Trust Network Access Architectural Models
This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption. This Zero Trust Model Zero Trust Network Access Architectural Models is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Zero Trust Model Zero Trust Network Access Architectural Models features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption.
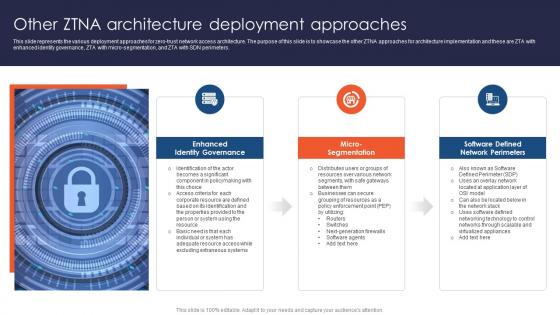
Zero Trust Network Access Other ZTNA Architecture Deployment Approaches
This slide represents the various deployment approaches for zero-trust network access architecture. The purpose of this slide is to showcase the other ZTNA approaches for architecture implementation and these are ZTA with enhanced identity governance, ZTA with micro-segmentation, and ZTA with SDN perimeters. Create an editable Zero Trust Network Access Other ZTNA Architecture Deployment Approaches that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Zero Trust Network Access Other ZTNA Architecture Deployment Approaches is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide represents the various deployment approaches for zero-trust network access architecture. The purpose of this slide is to showcase the other ZTNA approaches for architecture implementation and these are ZTA with enhanced identity governance, ZTA with micro-segmentation, and ZTA with SDN perimeters.
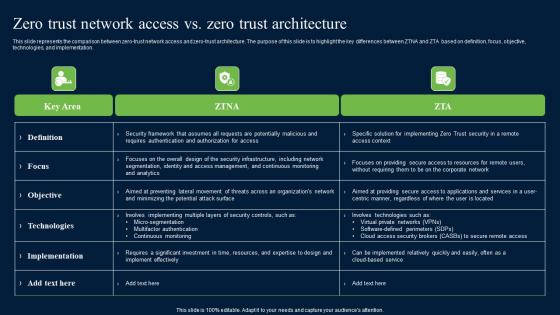
Zero Trust Network Access Vs Zero Trust Architecture Diagrams Pdf
This slide represents the comparison between zero-trust network access and zero-trust architecture. The purpose of this slide is to highlight the key differences between ZTNA and ZTA based on definition, focus, objective, technologies, and implementation. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Zero Trust Network Access Vs Zero Trust Architecture Diagrams Pdf can be your best option for delivering a presentation. Represent everything in detail using Zero Trust Network Access Vs Zero Trust Architecture Diagrams Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide represents the comparison between zero-trust network access and zero-trust architecture. The purpose of this slide is to highlight the key differences between ZTNA and ZTA based on definition, focus, objective, technologies, and implementation.
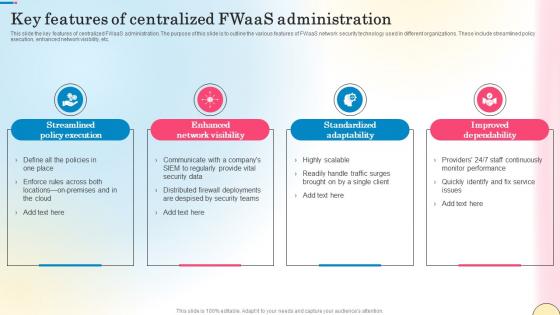
Key Features Of Centralized Fwaas Administration Network Security Introduction Pdf
This slide the key features of centralized FWaaS administration. The purpose of this slide is to outline the various features of FWaaS network security technology used in different organizations. These include streamlined policy execution, enhanced network visibility, etc. Slidegeeks has constructed Key Features Of Centralized Fwaas Administration Network Security Introduction Pdf after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide the key features of centralized FWaaS administration. The purpose of this slide is to outline the various features of FWaaS network security technology used in different organizations. These include streamlined policy execution, enhanced network visibility, etc.

Zero Trust Network Access Architectural Models Ideas Pdf
This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption. There are so many reasons you need a Zero Trust Network Access Architectural Models Ideas Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption.
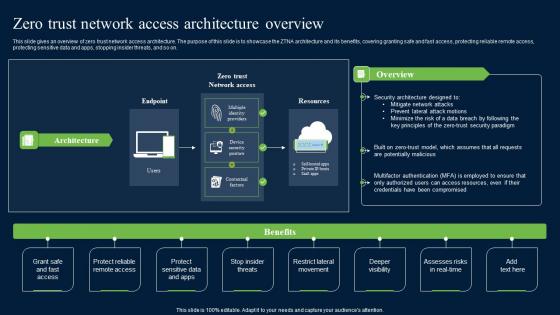
Zero Trust Network Security Access Architecture Overview Graphics Pdf
This slide gives an overview of zero trust network access architecture. The purpose of this slide is to showcase the ZTNA architecture and its benefits, covering granting safe and fast access, protecting reliable remote access, protecting sensitive data and apps, stopping insider threats, and so on. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Zero Trust Network Security Access Architecture Overview Graphics Pdf and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide gives an overview of zero trust network access architecture. The purpose of this slide is to showcase the ZTNA architecture and its benefits, covering granting safe and fast access, protecting reliable remote access, protecting sensitive data and apps, stopping insider threats, and so on.
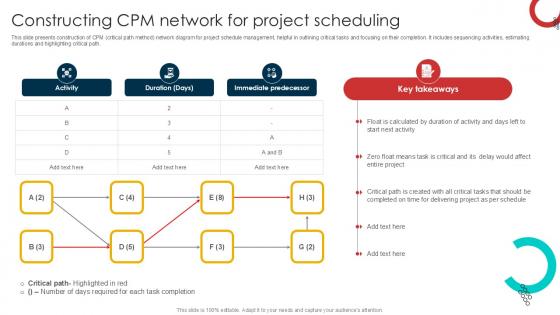
Constructing CPM Network For Schedule Management Techniques PPT Presentation
This slide presents construction of CPM critical path method network diagram for project schedule management, helpful in outlining critical tasks and focusing on their completion. It includes sequencing activities, estimating durations and highlighting critical path. Get a simple yet stunning designed Constructing CPM Network For Schedule Management Techniques PPT Presentation. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Constructing CPM Network For Schedule Management Techniques PPT Presentation can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide presents construction of CPM critical path method network diagram for project schedule management, helpful in outlining critical tasks and focusing on their completion. It includes sequencing activities, estimating durations and highlighting critical path.

Zero Trust Model Zero Trust Network Access Architecture Overview
This slide gives an overview of zero trust network access architecture. The purpose of this slide is to showcase the ZTNA architecture and its benefits, covering granting safe and fast access, protecting reliable remote access, protecting sensitive data and apps, stopping insider threats, and so on. Welcome to our selection of the Zero Trust Model Zero Trust Network Access Architecture Overview. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. This slide gives an overview of zero trust network access architecture. The purpose of this slide is to showcase the ZTNA architecture and its benefits, covering granting safe and fast access, protecting reliable remote access, protecting sensitive data and apps, stopping insider threats, and so on.

Zero Trust Network Access Architectural Models Software Defined Perimeter SDP
This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption. This Zero Trust Network Access Architectural Models Software Defined Perimeter SDP is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Zero Trust Network Access Architectural Models Software Defined Perimeter SDP features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption.
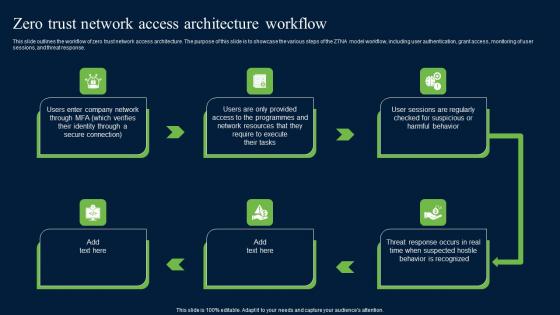
Zero Trust Network Access Architecture Workflow Themes Pdf
This slide outlines the workflow of zero trust network access architecture. The purpose of this slide is to showcase the various steps of the ZTNA model workflow, including user authentication, grant access, monitoring of user sessions, and threat response. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Zero Trust Network Access Architecture Workflow Themes Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Zero Trust Network Access Architecture Workflow Themes Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide outlines the workflow of zero trust network access architecture. The purpose of this slide is to showcase the various steps of the ZTNA model workflow, including user authentication, grant access, monitoring of user sessions, and threat response.
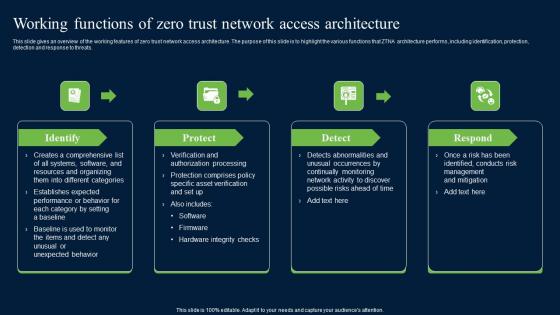
Working Functions Of Zero Trust Network Access Security Infographics Pdf
This slide gives an overview of the working features of zero trust network access architecture. The purpose of this slide is to highlight the various functions that ZTNA architecture performs, including identification, protection, detection and response to threats. Create an editable Working Functions Of Zero Trust Network Access Security Infographics Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Working Functions Of Zero Trust Network Access Security Infographics Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide gives an overview of the working features of zero trust network access architecture. The purpose of this slide is to highlight the various functions that ZTNA architecture performs, including identification, protection, detection and response to threats.
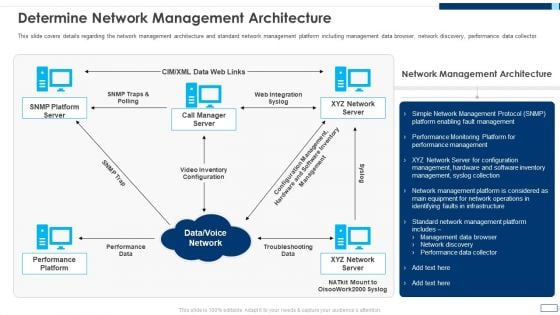
Evolving BI Infrastructure Determine Network Management Architecture Elements PDF
This slide covers details regarding the network management architecture and standard network management platform including management data browser, network discovery, performance data collector. This is a evolving bi infrastructure determine network management architecture elements pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like web integration syslog, performance data, troubleshooting data, network management architecture. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
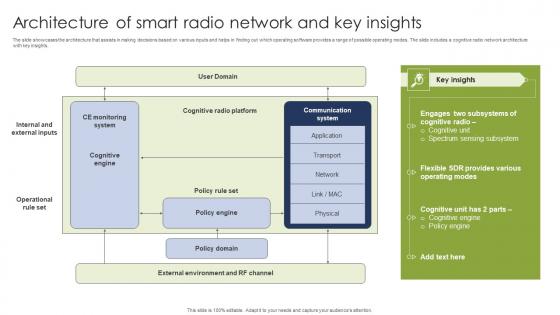
Architecture Of Smart Radio Network And Key Insights Clipart Pdf
The slide showcases the architecture that assists in making decisions based on various inputs and helps in finding out which operating software provides a range of possible operating modes. The slide includes a cognitive radio network architecture with key insights. Pitch your topic with ease and precision using this Architecture Of Smart Radio Network And Key Insights Clipart Pdf. This layout presents information on Policy Engine, Policy Domain, Cognitive Unit. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. The slide showcases the architecture that assists in making decisions based on various inputs and helps in finding out which operating software provides a range of possible operating modes. The slide includes a cognitive radio network architecture with key insights.

Zero Trust Network Access Architecture Overview Software Defined Perimeter SDP
This slide gives an overview of zero trust network access architecture. The purpose of this slide is to showcase the ZTNA architecture and its benefits, covering granting safe and fast access, protecting reliable remote access, protecting sensitive data and apps, stopping insider threats, and so on. Welcome to our selection of the Zero Trust Network Access Architecture Overview Software Defined Perimeter SDP. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. This slide gives an overview of zero trust network access architecture. The purpose of this slide is to showcase the ZTNA architecture and its benefits, covering granting safe and fast access, protecting reliable remote access, protecting sensitive data and apps, stopping insider threats, and so on.

Zero Trust Model Zero Trust Network Access Architecture Workflow
This slide outlines the workflow of zero trust network access architecture. The purpose of this slide is to showcase the various steps of the ZTNA model workflow, including user authentication, grant access, monitoring of user sessions, and threat response. Explore a selection of the finest Zero Trust Model Zero Trust Network Access Architecture Workflow here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Zero Trust Model Zero Trust Network Access Architecture Workflow to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide outlines the workflow of zero trust network access architecture. The purpose of this slide is to showcase the various steps of the ZTNA model workflow, including user authentication, grant access, monitoring of user sessions, and threat response.

Zero Trust Network Access Architecture Workflow Software Defined Perimeter SDP
This slide outlines the workflow of zero trust network access architecture. The purpose of this slide is to showcase the various steps of the ZTNA model workflow, including user authentication, grant access, monitoring of user sessions, and threat response. Explore a selection of the finest Zero Trust Network Access Architecture Workflow Software Defined Perimeter SDP here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Zero Trust Network Access Architecture Workflow Software Defined Perimeter SDP to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide outlines the workflow of zero trust network access architecture. The purpose of this slide is to showcase the various steps of the ZTNA model workflow, including user authentication, grant access, monitoring of user sessions, and threat response.

About Sidechain Blockchain Network Different Architectures Of Blockchain Guidelines Pdf
This slide highlights the overview and examples of sidechain blockchain networks. The purpose of this slide is to give an overview of the sidechain, including its workflow and examples. The examples cater to parachain, plasma, and rootstock. This About Sidechain Blockchain Network Different Architectures Of Blockchain Guidelines Pdf from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide highlights the overview and examples of sidechain blockchain networks. The purpose of this slide is to give an overview of the sidechain, including its workflow and examples. The examples cater to parachain, plasma, and rootstock.
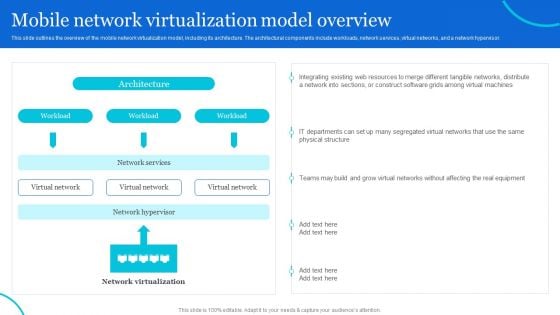
Naas Architectural Framework Mobile Network Virtualization Model Overview Background PDF
This slide outlines the overview of the mobile network virtualization model, including its architecture. The architectural components include workloads, network services, virtual networks, and a network hypervisor. Make sure to capture your audiences attention in your business displays with our gratis customizable Naas Architectural Framework Mobile Network Virtualization Model Overview Background PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
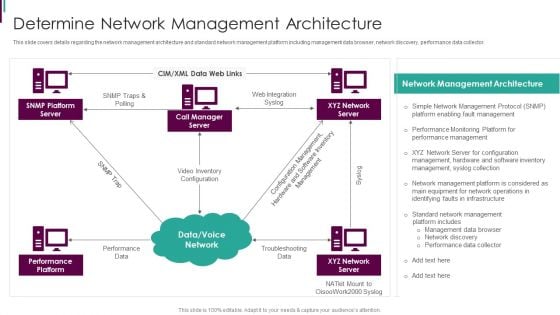
Developing Business Analytics Framework Determine Network Management Architecture Designs PDF
This slide covers details regarding the network management architecture and standard network management platform including management data browser, network discovery, performance data collector. Presenting Developing Business Analytics Framework Determine Network Management Architecture Designs PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Platform Server, Manager Server, Network Server In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
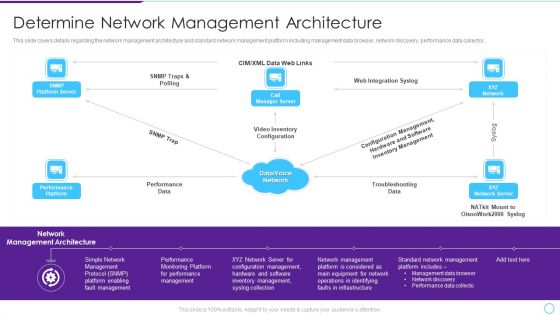
Intelligent Infrastructure Determine Network Management Architecture Formats PDF
This slide covers details regarding the network management architecture and standard network management platform including management data browser, network discovery, performance data collector. Presenting Intelligent Infrastructure Determine Network Management Architecture Formats PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Performance, Data, SNMP Trap, Web Integration Syslog, XYZ Network Server. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Features Of Zero Trust Network Access Security Model Background Pdf
This slide represents the main features of ZTNA. The purpose of this slide is to showcase the various features of zero trust network access, including safeguarding private apps, connecting security controls to apps more closely, restriction of access, recognizing internal app use, and so on. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Features Of Zero Trust Network Access Security Model Background Pdf template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Features Of Zero Trust Network Access Security Model Background Pdf that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide represents the main features of ZTNA. The purpose of this slide is to showcase the various features of zero trust network access, including safeguarding private apps, connecting security controls to apps more closely, restriction of access, recognizing internal app use, and so on.

Zero Trust Model Traditional Perimeter Based Network Security Overview
This slide represents the overview of traditional perimeter-based network security. The purpose of this slide is to showcase the various challenges of conventional perimeter-based security and how ZTNA can overcome those challenges. If you are looking for a format to display your unique thoughts, then the professionally designed Zero Trust Model Traditional Perimeter Based Network Security Overview is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Zero Trust Model Traditional Perimeter Based Network Security Overview and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide represents the overview of traditional perimeter-based network security. The purpose of this slide is to showcase the various challenges of conventional perimeter-based security and how ZTNA can overcome those challenges.

Zero Trust Network Access Logical Components Of Zero Trust Architecture
This slide describes the core logical components of the zero-trust network architecture model. The purpose of this slide is to showcase the various architectural parts and functions of logical elements, such as the policy engine, policy administrator, and policy environment point. Take your projects to the next level with our ultimate collection of Zero Trust Network Access Logical Components Of Zero Trust Architecture. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest This slide describes the core logical components of the zero-trust network architecture model. The purpose of this slide is to showcase the various architectural parts and functions of logical elements, such as the policy engine, policy administrator, and policy environment point.
Pairing 5G Network For Smart Logistics Icons PDF
This slide shows pairing 5G network for smart logistics. It provides information about supply chain risk management, latency reduction, self driven vehicles, device connections, network usage, downtime, etc. Deliver and pitch your topic in the best possible manner with this Pairing 5G Network For Smart Logistics Icons PDF. Use them to share invaluable insights on Mitigating Supply Chain Risks, Network, Synchronization and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Data Center Network Architecture Model Icon Ppt Layouts Smartart PDF
Pitch your topic with ease and precision using this Data Center Network Architecture Model Icon Ppt Layouts Smartart PDF. This layout presents information on Data Center Network, Architecture Model, Icon. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Home Security Network Icon Ppt PowerPoint Presentation Portfolio Ideas
Presenting this set of slides with name home security network icon ppt powerpoint presentation portfolio ideas. The topics discussed in these slides are communication, teamwork, build network. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Zero Trust Model Service Initiated Zero Trust Network Topology Model
This slide provides an overview of service initiated zero-trust network topology model. The purpose of this slide is to showcase its architecture, benefits, and disadvantages. The architectural components include a user device, controller, broker proxy, and connector. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Zero Trust Model Service Initiated Zero Trust Network Topology Model for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide provides an overview of service initiated zero-trust network topology model. The purpose of this slide is to showcase its architecture, benefits, and disadvantages. The architectural components include a user device, controller, broker proxy, and connector.

Zero Trust Model Working Functions Of Zero Trust Network Access
This slide gives an overview of the working features of zero trust network access architecture. The purpose of this slide is to highlight the various functions that ZTNA architecture performs, including identification, protection, detection and response to threats. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Zero Trust Model Working Functions Of Zero Trust Network Access was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Zero Trust Model Working Functions Of Zero Trust Network Access. This slide gives an overview of the working features of zero trust network access architecture. The purpose of this slide is to highlight the various functions that ZTNA architecture performs, including identification, protection, detection and response to threats.
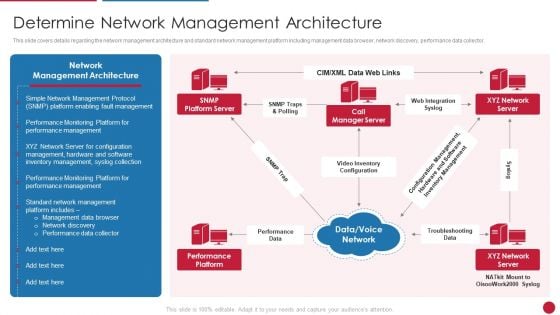
Facilitating IT Intelligence Architecture Determine Network Management Architecture Infographics PDF
This slide covers details regarding the network management architecture and standard network management platform including management data browser, network discovery, performance data collector. Presenting Facilitating IT Intelligence Architecture Determine Network Management Architecture Infographics PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Performance Platform, Configuration Management, Inventory Management In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
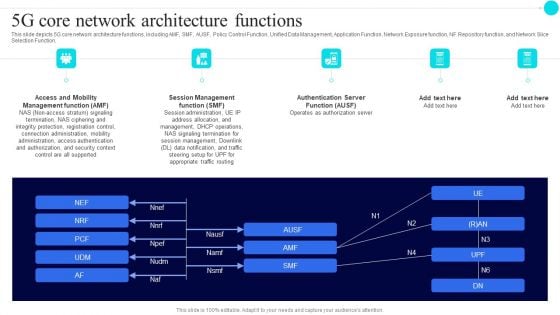
5G Core Network Architecture Functions 5G Functional Architecture Background PDF
This slide depicts 5G core network architecture functions, including AMF, SMF, AUSF, Policy Control Function, Unified Data Management, Application Function, Network Exposure function, NF Repository function, and Network Slice Selection Function.Presenting 5G Core Network Architecture Functions 5G Functional Architecture Background PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like session management, authentication server, management function. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Zero Trust Model Checklist To Build Zero Trust Network Access
This slide outlines the checklist to develop a zero-trust network access architecture. The purpose of this slide is to define the various measures organizations should take while building a ZTNA architecture. The measures include knowing the architecture, creating a strong device identity, and so on. Slidegeeks is here to make your presentations a breeze with Zero Trust Model Checklist To Build Zero Trust Network Access With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide outlines the checklist to develop a zero-trust network access architecture. The purpose of this slide is to define the various measures organizations should take while building a ZTNA architecture. The measures include knowing the architecture, creating a strong device identity, and so on.
Connected Devices Network Icon For Smart Homes Introduction PDF
Presenting Connected Devices Network Icon For Smart Homes Introduction PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Connected Devices Network Icon, Smart Homes. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Architecture Of Content Delivery Network Ppt Gallery Infographic Template PDF
This slide explains the content delivery network architecture in which point of presence and regional data Centre is the basic foundation of CDN systems. Deliver an awe inspiring pitch with this creative architecture of content delivery network ppt gallery infographic template pdf bundle. Topics like architecture of content delivery network can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
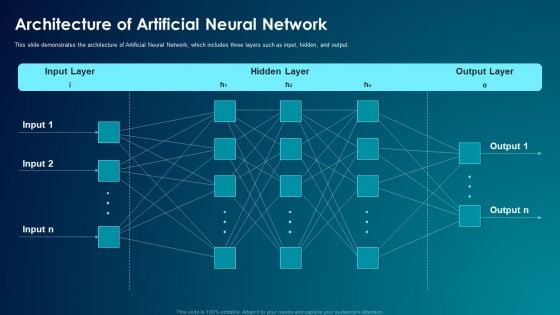
ANN System Architecture Of Artificial Neural Network Inspiration PDF
This slide demonstrates the architecture of Artificial Neural Network, which includes three layers such as input, hidden, and output. Deliver an awe inspiring pitch with this creative ANN System Architecture Of Artificial Neural Network Inspiration PDF bundle. Topics like Architecture, Artificial Neural Network can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
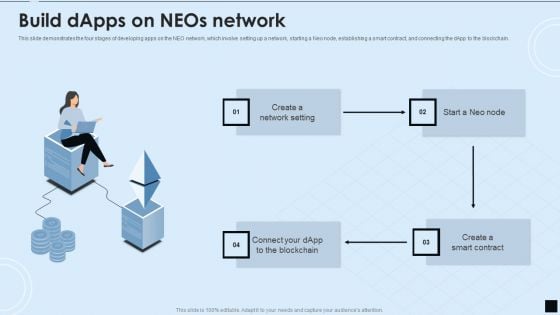
Decentralized Applications IT Build Dapps On Neos Network Demonstration PDF
This slide demonstrates the four stages of developing apps on the NEO network, which involve setting up a network, starting a Neo node, establishing a smart contract, and connecting the dApp to the blockchain. Presenting Decentralized Applications IT Build Dapps On Neos Network Demonstration PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Neos Network, Build Dapps. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
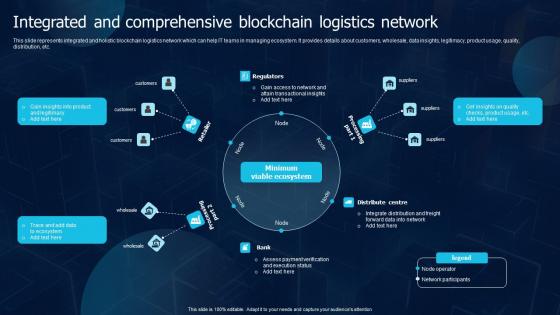
Integrated And Comprehensive Blockchain Logistics Network Blockchain Transportation Formats Pdf
This slide represents integrated and holistic blockchain logistics network which can help IT teams in managing ecosystem. It provides details about customers, wholesale, data insights, legitimacy, product usage, quality, distribution, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Integrated And Comprehensive Blockchain Logistics Network Blockchain Transportation Formats Pdf and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide represents integrated and holistic blockchain logistics network which can help IT teams in managing ecosystem. It provides details about customers, wholesale, data insights, legitimacy, product usage, quality, distribution, etc.
Gaming Platform Network Structure Framework Ppt Summary Icons PDF
This slide represents the API architecture for gaming applications including availability of network, gaming API, gaming engine etc. Showcasing this set of slides titled gaming platform network structure framework ppt summary icons pdf. The topics addressed in these templates are gaming app, gaming engine, network, gaming server, database. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
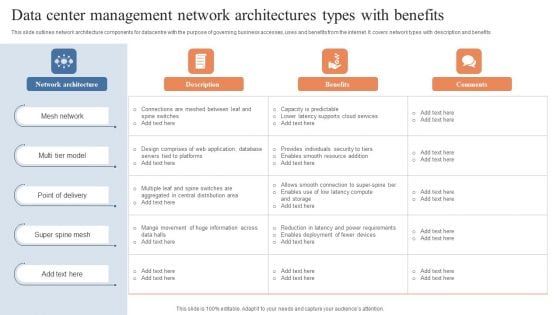
Data Center Management Network Architectures Types With Benefits Brochure PDF
This slide outlines network architecture components for datacentre with the purpose of governing business accesses, uses and benefits from the internet. It covers network types with description and benefits. Showcasing this set of slides titled Data Center Management Network Architectures Types With Benefits Brochure PDF. The topics addressed in these templates are Mesh Network, Point Delivery, Super Spine Mesh. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
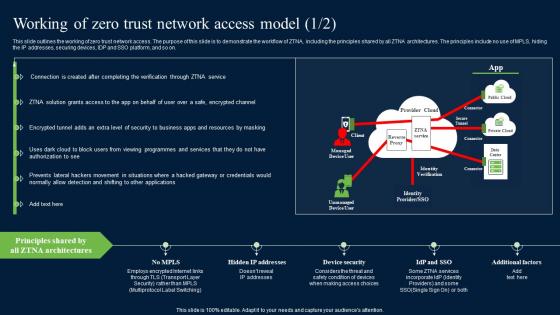
Working Of Zero Trust Network Access Model Security Pictures Pdf
This slide outlines the working of zero trust network access. The purpose of this slide is to demonstrate the workflow of ZTNA, including the principles shared by all ZTNA architectures. The principles include no use of MPLS, hiding the IP addresses, securing devices, IDP and SSO platform, and so on. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Working Of Zero Trust Network Access Model Security Pictures Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide outlines the working of zero trust network access. The purpose of this slide is to demonstrate the workflow of ZTNA, including the principles shared by all ZTNA architectures. The principles include no use of MPLS, hiding the IP addresses, securing devices, IDP and SSO platform, and so on.

Zero Trust Model Working Of Zero Trust Network Access Model
This slide outlines the working of zero trust network access. The purpose of this slide is to demonstrate the workflow of ZTNA, including the principles shared by all ZTNA architectures. The principles include no use of MPLS, hiding the IP addresses, securing devices, IDP and SSO platform, and so on. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Zero Trust Model Working Of Zero Trust Network Access Model to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide outlines the working of zero trust network access. The purpose of this slide is to demonstrate the workflow of ZTNA, including the principles shared by all ZTNA architectures. The principles include no use of MPLS, hiding the IP addresses, securing devices, IDP and SSO platform, and so on.
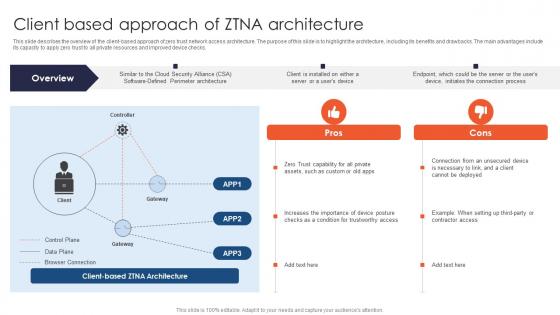
Zero Trust Network Access Client Based Approach Of ZTNA Architecture
This slide describes the overview of the client-based approach of zero trust network access architecture. The purpose of this slide is to highlight the architecture, including its benefits and drawbacks. The main advantages include its capacity to apply zero trust to all private resources and improved device checks. This modern and well-arranged Zero Trust Network Access Client Based Approach Of ZTNA Architecture provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide describes the overview of the client-based approach of zero trust network access architecture. The purpose of this slide is to highlight the architecture, including its benefits and drawbacks. The main advantages include its capacity to apply zero trust to all private resources and improved device checks.

Zero Trust Model External Components Of Zero Trust Network Architecture
This slide gives an overview of external elements of zero trust network architecture. The purpose of this slide is to showcase the various external components and their working, covering CDM systems, industry compliance, threat intelligence, activity logs, data access policy, and so on. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Zero Trust Model External Components Of Zero Trust Network Architecture to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide gives an overview of external elements of zero trust network architecture. The purpose of this slide is to showcase the various external components and their working, covering CDM systems, industry compliance, threat intelligence, activity logs, data access policy, and so on.
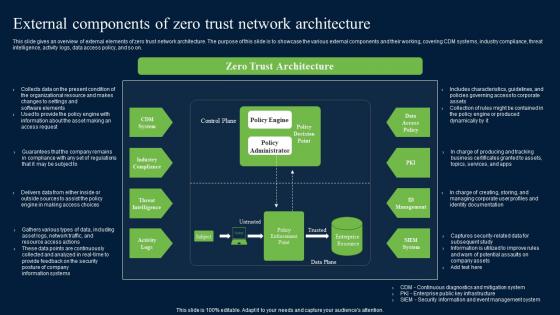
External Components Of Zero Trust Network Security Structure Pdf
This slide gives an overview of external elements of zero trust network architecture. The purpose of this slide is to showcase the various external components and their working, covering CDM systems, industry compliance, threat intelligence, activity logs, data access policy, and so on. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download External Components Of Zero Trust Network Security Structure Pdf and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide gives an overview of external elements of zero trust network architecture. The purpose of this slide is to showcase the various external components and their working, covering CDM systems, industry compliance, threat intelligence, activity logs, data access policy, and so on.
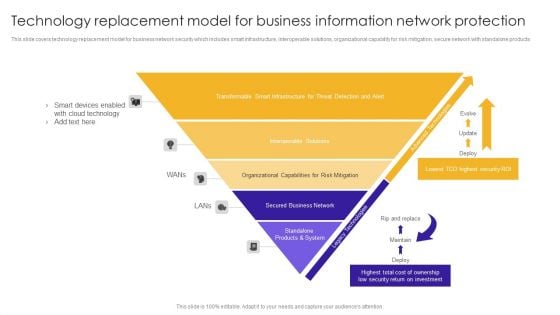
Technology Replacement Model For Business Information Network Protection Structure PDF
This slide covers technology replacement model for business network security which includes smart infrastructure, interoperable solutions, organizational capability for risk mitigation, secure network with standalone products.Showcasing this set of slides titled Technology Replacement Model For Business Information Network Protection Structure PDF. The topics addressed in these templates are Smart Devices, Cloud Technology, Transformable Smart. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Architecture Of Network Load Balancer NLB Ppt File Demonstration PDF
This slide represents the architecture of the network load balancer and its two further designs, such as backend service based or target pool based NLB. This is a architecture of network load balancer nlb ppt file demonstration pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like service, network. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Network Load Balancers Performance Tracker Dashboard Ppt Information PDF
This slide shows the dashboard for tracking the network load balancers performance by covering details of balancer status, balancer session, balancer throughput, etc. Deliver and pitch your topic in the best possible manner with this network load balancers performance tracker dashboard ppt information pdf. Use them to share invaluable insights on network load balancers performance tracker dashboard and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
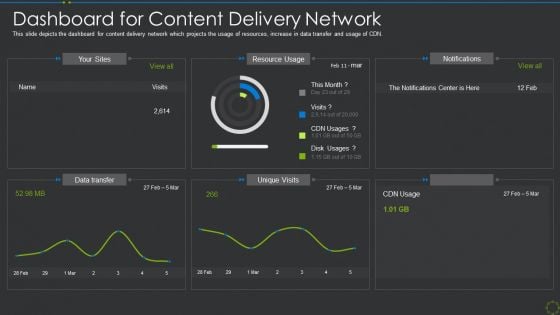
Dashboard For Content Delivery Network Ppt Gallery Show PDF
This slide depicts the dashboard for content delivery network which projects the usage of resources, increase in data transfer and usage of CDN. Deliver and pitch your topic in the best possible manner with this dashboard for content delivery network ppt gallery show pdf. Use them to share invaluable insights on dashboard for content delivery network and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Career With Cisco Certified Network Associate CCNA Professional PDF
This slide covers details about Cisco Certified Network Associate CCNA certification including career with CCNA, salary expectations, job responsibilities etc. Deliver and pitch your topic in the best possible manner with this Career With Cisco Certified Network Associate CCNA Professional PDF. Use them to share invaluable insights on Network Fundamentals, Security Fundamentals, Automation Programmability and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.


 Continue with Email
Continue with Email

 Home
Home


































