Risk And Compliance
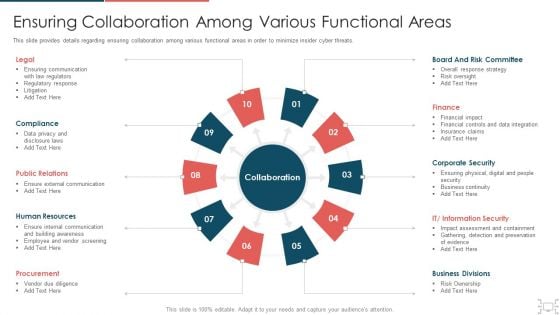
cyber security administration in organization ensuring collaboration among various functional areas brochure pdf
This slide provides details regarding ensuring collaboration among various functional areas in order to minimize insider cyber threats. Presenting cyber security administration in organization ensuring collaboration among various functional areas brochure pdf to provide visual cues and insights. Share and navigate important information on ten stages that need your due attention. This template can be used to pitch topics like communication, compliance, relations, resources, procurement . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security Information And Event Management Services Mockup PDF
This slide covers the SIEM services offered by our company such as data aggregation, correlation, security alerts, dashboards, retention, forensic analysis, IT compliance, threat detection, etc. Presenting security information and event management services mockup pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like data aggregation, data correlation, security alert, dashboards. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
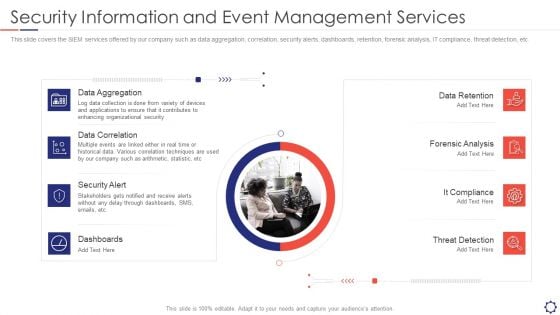
SIEM Security Information And Event Management Services Ppt Ideas Graphics Pictures PDF
This slide covers the SIEM services offered by our company such as data aggregation, correlation, security alerts, dashboards, retention, forensic analysis, IT compliance, threat detection, etc. This is a siem security information and event management services ppt ideas graphics pictures pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Data Aggregation, Data Correlation, Security Alert, Dashboards, Data Retention. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

SIEM Services Security Information And Event Management Services Ppt Ideas Design Ideas PDF
This slide covers the SIEM services offered by our company such as data aggregation, correlation, security alerts, dashboards, retention, forensic analysis, IT compliance, threat detection, etc. This is a siem services security information and event management services ppt ideas design ideas pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like data correlation, data aggregation, security alert, dashboards. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
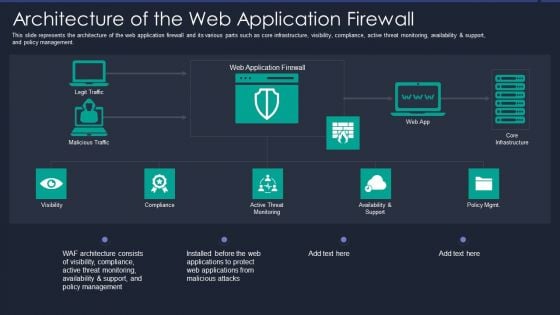
Web App Firewall Services IT Architecture Of The Web Application Firewall Mockup PDF
This slide represents the architecture of the web application firewall and its various parts such as core infrastructure, visibility, compliance, active threat monitoring, availability and support, and policy management. This is a web app firewall services it architecture of the web application firewall mockup pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like management, applications. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
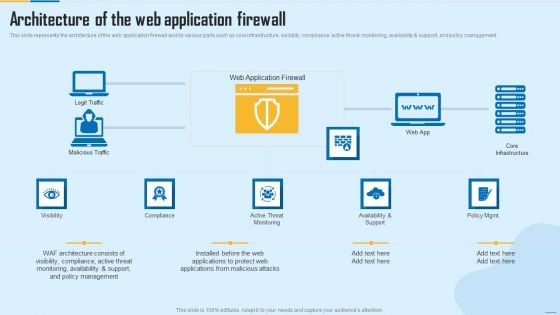
Architecture Of The Web Application Firewall WAF Platform Rules PDF
This slide represents the architecture of the web application firewall and its various parts such as core infrastructure, visibility, compliance, active threat monitoring, availability and support, and policy management. Presenting Architecture Of The Web Application Firewall WAF Platform Rules PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Policy Management, Core Infrastructure, Web Application Firewall. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
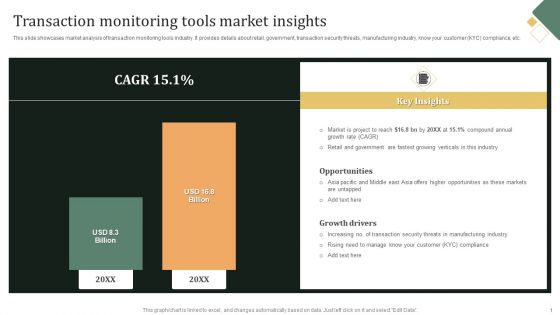
Transaction Monitoring Transaction Monitoring Tools Market Insights Information PDF
This slide showcases market analysis of transaction monitoring tools industry. It provides details about retail, government, transaction security threats, manufacturing industry, know your customer KYC compliance, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Transaction Monitoring Transaction Monitoring Tools Market Insights Information PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
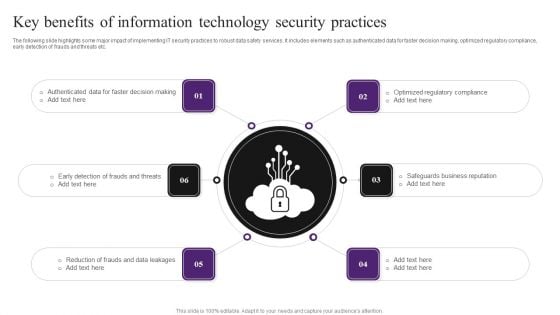
Key Benefits Of Information Technology Security Practices Summary PDF
The following slide highlights some major impact of implementing IT security practices to robust data safety services. It includes elements such as authenticated data for faster decision making, optimized regulatory compliance, early detection of frauds and threats etc. Presenting Key Benefits Of Information Technology Security Practices Summary PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Data Leakages, Reduction Of Frauds, Safeguards Business Reputation. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Requirements For Appropriate Cloud Security Model Ppt PowerPoint Presentation File Gallery PDF
This slide outlines the different prerequisites organizations should consider when choosing a cloud security model and provider. The purpose of this slide is to showcase the various requirements a cloud security provider should possess, including visibility and threat detection, continuous compliance, data encryption and so on. There are so many reasons you need a Requirements For Appropriate Cloud Security Model Ppt PowerPoint Presentation File Gallery PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
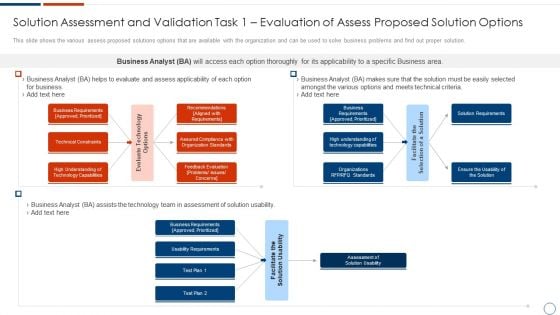
Solution Assessment And Validation Task 1 Evaluation Of Assess Proposed Solution Options Themes PDF
This slide shows the various assess proposed solutions options that are available with the organization and can be used to solve business problems and find out proper solution.Deliver and pitch your topic in the best possible manner with this solution assessment and validation task 1 evaluation of assess proposed solution options themes pdf Use them to share invaluable insights on business analyst, assured compliance, recommendations aligned with requirements and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
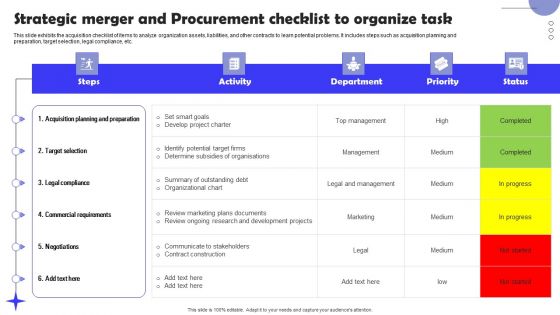
Strategic Merger And Procurement Checklist To Organize Task Diagrams PDF
This slide exhibits the acquisition checklist of items to analyze organization assets, liabilities, and other contracts to learn potential problems. It includes steps such as acquisition planning and preparation, target selection, legal compliance, etc. Pitch your topic with ease and precision using this Strategic Merger And Procurement Checklist To Organize Task Diagrams PDF. This layout presents information on Target Selection, Commercial Requirements, Acquisition Planning And Preparation. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
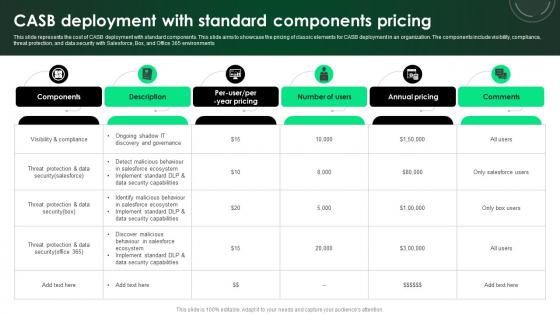
CASB 2 0 IT CASB Deployment With Standard Components Pricing
This slide represents the cost of CASB deployment with standard components. This slide aims to showcase the pricing of classic elements for CASB deployment in an organization. The components include visibility, compliance, threat protection, and data security with Salesforce, Box, and Office 365 environments. Whether you have daily or monthly meetings, a brilliant presentation is necessary. CASB 2 0 IT CASB Deployment With Standard Components Pricing can be your best option for delivering a presentation. Represent everything in detail using CASB 2 0 IT CASB Deployment With Standard Components Pricing and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide represents the cost of CASB deployment with standard components. This slide aims to showcase the pricing of classic elements for CASB deployment in an organization. The components include visibility, compliance, threat protection, and data security with Salesforce, Box, and Office 365 environments
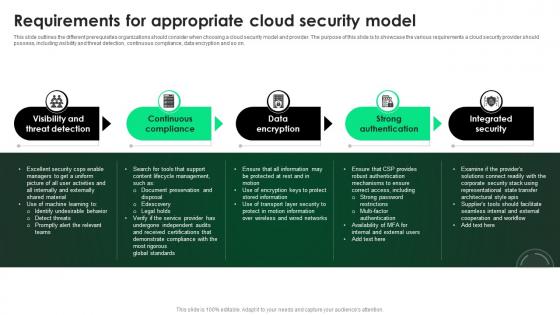
CASB 2 0 IT Requirements For Appropriate Cloud Security Model
This slide outlines the different prerequisites organizations should consider when choosing a cloud security model and provider. The purpose of this slide is to showcase the various requirements a cloud security provider should possess, including visibility and threat detection, continuous compliance, data encryption and so on. Find highly impressive CASB 2 0 IT Requirements For Appropriate Cloud Security Model on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download CASB 2 0 IT Requirements For Appropriate Cloud Security Model for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide outlines the different prerequisites organizations should consider when choosing a cloud security model and provider. The purpose of this slide is to showcase the various requirements a cloud security provider should possess, including visibility and threat detection, continuous compliance, data encryption and so on.
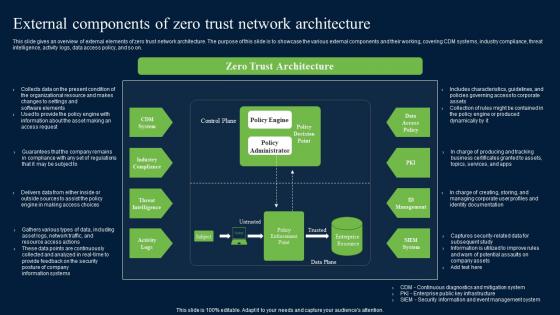
External Components Of Zero Trust Network Security Structure Pdf
This slide gives an overview of external elements of zero trust network architecture. The purpose of this slide is to showcase the various external components and their working, covering CDM systems, industry compliance, threat intelligence, activity logs, data access policy, and so on. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download External Components Of Zero Trust Network Security Structure Pdf and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide gives an overview of external elements of zero trust network architecture. The purpose of this slide is to showcase the various external components and their working, covering CDM systems, industry compliance, threat intelligence, activity logs, data access policy, and so on.

Zero Trust Model External Components Of Zero Trust Network Architecture
This slide gives an overview of external elements of zero trust network architecture. The purpose of this slide is to showcase the various external components and their working, covering CDM systems, industry compliance, threat intelligence, activity logs, data access policy, and so on. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Zero Trust Model External Components Of Zero Trust Network Architecture to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide gives an overview of external elements of zero trust network architecture. The purpose of this slide is to showcase the various external components and their working, covering CDM systems, industry compliance, threat intelligence, activity logs, data access policy, and so on.

External Components Of Zero Trust Network Architecture Software Defined Perimeter SDP
This slide gives an overview of external elements of zero trust network architecture. The purpose of this slide is to showcase the various external components and their working, covering CDM systems, industry compliance, threat intelligence, activity logs, data access policy, and so on. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download External Components Of Zero Trust Network Architecture Software Defined Perimeter SDP and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide gives an overview of external elements of zero trust network architecture. The purpose of this slide is to showcase the various external components and their working, covering CDM systems, industry compliance, threat intelligence, activity logs, data access policy, and so on.

Zero Trust Network Access External Components Of Zero Trust Network Architecture
This slide gives an overview of external elements of zero trust network architecture. The purpose of this slide is to showcase the various external components and their working, covering CDM systems, industry compliance, threat intelligence, activity logs, data access policy, and so on. Retrieve professionally designed Zero Trust Network Access External Components Of Zero Trust Network Architecture to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide gives an overview of external elements of zero trust network architecture. The purpose of this slide is to showcase the various external components and their working, covering CDM systems, industry compliance, threat intelligence, activity logs, data access policy, and so on.

CASB 2 0 IT Cloud Access Security Broker Pillar Overview
This slide represents the four major pillars of cloud access security broker. The purpose of this slide is to showcase the main pillars of implementing a cloud access security broker. The pillars include compliance, visibility, threat protection, and data security. Are you searching for a CASB 2 0 IT Cloud Access Security Broker Pillar Overview that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download CASB 2 0 IT Cloud Access Security Broker Pillar Overview from Slidegeeks today. This slide represents the four major pillars of cloud access security broker. The purpose of this slide is to showcase the main pillars of implementing a cloud access security broker. The pillars include compliance, visibility, threat protection, and data security.
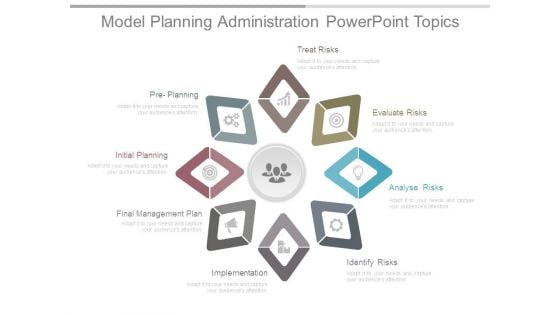
Model Planning Administration Powerpoint Topics
This is a model planning administration powerpoint topics. This is a eight stage process. The stages in this process are treat risks, evaluate risks, analyse risks, identify risks, implementation, final management plan, initial planning, pre planning.

Electronic Game Pitch Deck What Video Game Experience Challenges Are Faced By Prospect Topics PDF
This slide caters details about key business challenges are faced by prospects in terms of security threats, regulatory compliances. Deliver an awe inspiring pitch with this creative electronic game pitch deck what video game experience challenges are faced by prospect topics pdf bundle. Topics like security threats, regulatory compliances, systems information breach can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Computerized Game Pitch Deck What Video Game Experience Challenges Are Faced By Prospect Download PDF
This slide caters details about key business challenges are faced by prospects in terms of security threats, regulatory compliances. Deliver and pitch your topic in the best possible manner with this computerized game pitch deck what video game experience challenges are faced by prospect download pdf. Use them to share invaluable insights on regulatory compliances, security threats and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

WAF Introduction Architecture Of The Web Application Firewall Download PDF
This slide represents the architecture of the web application firewall and its various parts such as core infrastructure, visibility, compliance, active threat monitoring, availability and support, and policy management. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download WAF Introduction Architecture Of The Web Application Firewall Download PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
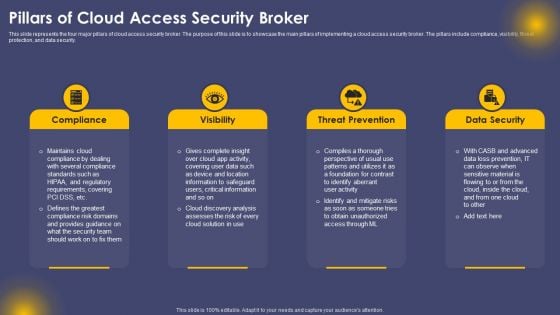
Pillars Of Cloud Access Security Broker Ppt Show Background PDF
This slide represents the four major pillars of cloud access security broker. The purpose of this slide is to showcase the main pillars of implementing a cloud access security broker. The pillars include compliance, visibility, threat protection, and data security. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Pillars Of Cloud Access Security Broker Ppt Show Background PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Pillars Of Cloud Access Security Broker Ppt Show Background PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

External Components Of Zero Trust Network Architecture Information PDF
This slide gives an overview of external elements of zero trust network architecture. The purpose of this slide is to showcase the various external components and their working, covering CDM systems, industry compliance, threat intelligence, activity logs, data access policy, and so on. Welcome to our selection of the External Components Of Zero Trust Network Architecture Information PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today

Cloud Access Security Broker Pillar Overview Ppt PowerPoint Presentation File Infographics PDF
This slide represents the four major pillars of cloud access security broker. The purpose of this slide is to showcase the main pillars of implementing a cloud access security broker. The pillars include compliance, visibility, threat protection, and data security. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Cloud Access Security Broker Pillar Overview Ppt PowerPoint Presentation File Infographics PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Cloud Access Security Broker Pillar Overview Ppt PowerPoint Presentation File Infographics PDF today and make your presentation stand out from the rest.

Concerns Faced Due To Ineffective Product Delivery Management Ideas PDF
This slide provides information regarding issues faced by firm while implementing product delivery in terms of value risk, usability risk, feasibility risk, etc. Deliver and pitch your topic in the best possible manner with this concerns faced due to ineffective product delivery management ideas pdf. Use them to share invaluable insights on value risk, usability risk, feasibility risk, business viability risk, product management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Security Analysis Ppt PowerPoint Presentation Guidelines
This is a security analysis ppt powerpoint presentation guidelines. This is a one stage process. The stages in this process are high risk, low risk.
Service Marketing Fundraising What Business Challenges Are Faced By Prospect Icons PDF
This slide caters details about key business challenges are faced by prospects in context to services such as high IT cost, poor business agility, regulatory compliances, etc. Presenting service marketing fundraising what business challenges are faced by prospect icons pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like poor business agility, regulatory compliances, security threats, infrastructure silos. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Services Marketing Sales What Business Challenges Are Faced By Prospect Ppt Icon Diagrams PDF
This slide caters details about key business challenges are faced by prospects in context to services such as high IT cost, poor business agility, regulatory compliances, etc. This is a services marketing sales what business challenges are faced by prospect ppt icon diagrams pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like humongous it cost, infrastructure silos, security threats, regulatory compliances, poor business agility. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
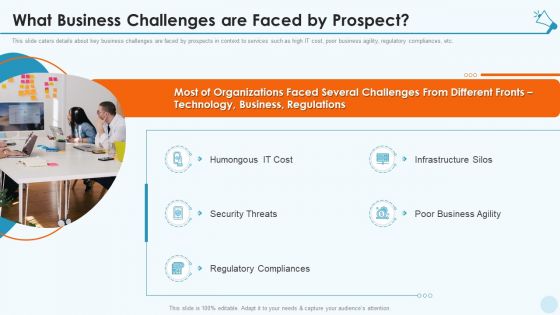
Services Promotion Investor Financing Elevator What Business Challenges Are Faced By Prospect Designs PDF
This slide caters details about key business challenges are faced by prospects in context to services such as high IT cost, poor business agility, regulatory compliances, etc. Presenting services promotion investor financing elevator what business challenges are faced by prospect designs pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like humongous it cost, security threats, regulatory compliances, infrastructure silos, poor business agility. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
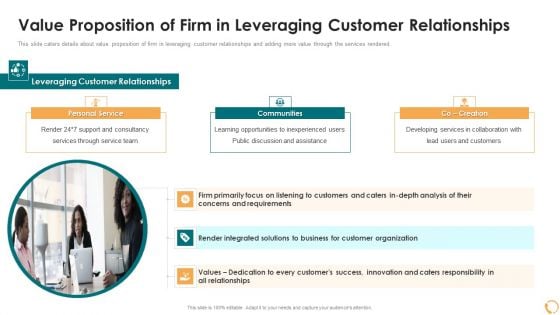
Services Sales Capital Investment Pitch Deck Value Proposition Of Firm In Leveraging Customer Relationships Background PDF
This slide caters details about key business challenges are faced by prospects in context to services such as high IT cost, poor business agility, regulatory compliances, etc. This is a services sales capital investment pitch deck what business challenges are faced by prospect icons pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like humongous it cost, infrastructure silos, security threats, regulatory compliances, poor business agilit. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Stakeholder Deck Presentation Services What Business Challenges Are Faced By Prospect Diagrams PDF
This slide caters details about key business challenges are faced by prospects in context to services such as high IT cost, poor business agility, regulatory compliances, etc. This is a Stakeholder Deck Presentation Services What Business Challenges Are Faced By Prospect Diagrams PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Humongous IT Cost, Regulatory Compliances, Security Threats, Infrastructure Silos, Poor Business Agility. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
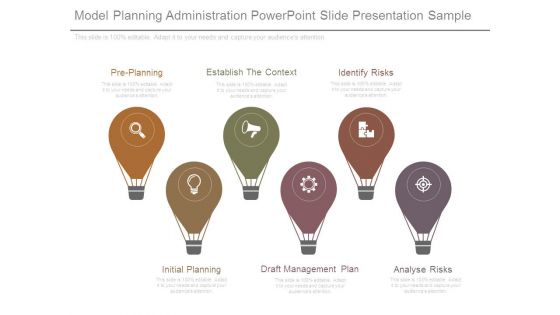
Model Planning Administration Powerpoint Slide Presentation Sample
This is a model planning administration powerpoint slide presentation sample. This is a six stage process. The stages in this process are pre planning, establish the context, identify risks, initial planning, draft management plan, analyse risks.
Developing Product Planning Strategies Product Roadmap Plan Ppt PowerPoint Presentation Icon Visual Aids PDF
Presenting this set of slides with name developing product planning strategies product roadmap plan ppt powerpoint presentation icon visual aids pdf. The topics discussed in these slides are high risk, med risk, low risk, development, press launch, celebrity partnership, ongoing marketing. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
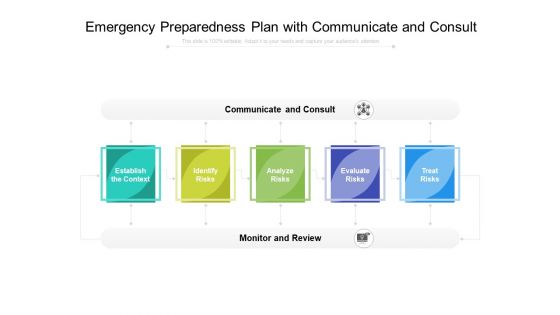
Emergency Preparedness Plan With Communicate And Consult Ppt PowerPoint Presentation Gallery Ideas PDF
Presenting this set of slides with name emergency preparedness plan with communicate and consult ppt powerpoint presentation gallery ideas pdf. This is a five stage process. The stages in this process are communicate and consult, monitor and review, establish the context, identify risks, analyze risks, evaluate risks, treat risks. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

IT Project Roadmap Of Product Delivery Ppt PowerPoint Presentation Summary Graphics Design PDF
Presenting this set of slides with name it project roadmap of product delivery ppt powerpoint presentation summary graphics design pdf. The topics discussed in these slides are delivery, security, inception, promotion stream, continuous improvement, low risk, medium risk, high risk. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Means Of Communication During Disaster Management Crisis Action Plan Summary Ppt Portfolio Graphics PDF
Presenting this set of slides with name means of communication during disaster management crisis action plan summary ppt portfolio graphics pdf. This is a three stage process. The stages in this process are team, person, action, highest risk, moderate risk, lower risk. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
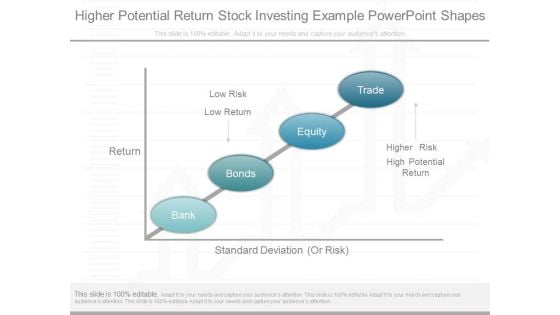
Higher Potential Return Stock Investing Example Powerpoint Shapes
This is a higher potential return stock investing example powerpoint shapes. This is a four stage process. The stages in this process are return, low risk, low return, high potential return, higher risk, high potential return, standard deviation or risk, bank, bonds, equity, trade.\n\n\n\n\n
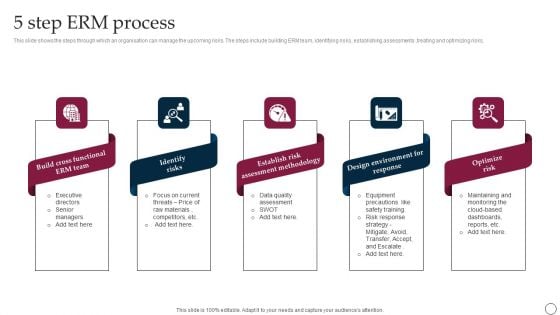
5 Step ERM Process Ppt PowerPoint Presentation File Styles PDF
This slide shows the steps through which an organisation can manage the upcoming risks. The steps include building ERM team, identifying risks, establishing assessments ,treating and optimizing risks. Persuade your audience using this 5 Step ERM Process Ppt PowerPoint Presentation File Styles PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Design Environment For Response, Optimize Risk, Identify Risks. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Administration Enhancement Template Presentation Slides
This is a administration enhancement template presentation slides. This is a five stage process. The stages in this process are risk, achievement, quality, growth, change.
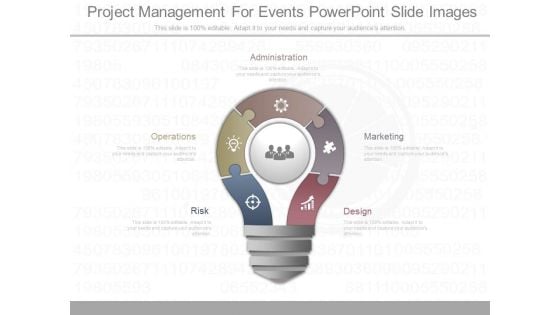
Project Management For Events Powerpoint Slide Images
This is a project management for events powerpoint slide images. This is a five stage process. The stages in this process are administration, marketing, design, risk, operations.

New Product Launch Concerns Faced Due To Ineffective Product Development Mockup PDF
This slide provides information regarding issues faced by firm while developing new product in terms of value risk, usability risk, feasibility risk, etc. Deliver an awe inspiring pitch with this creative new product launch concerns faced due to ineffective product development mockup pdf bundle. Topics like engineering and development, insufficient details about market, internal communication can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
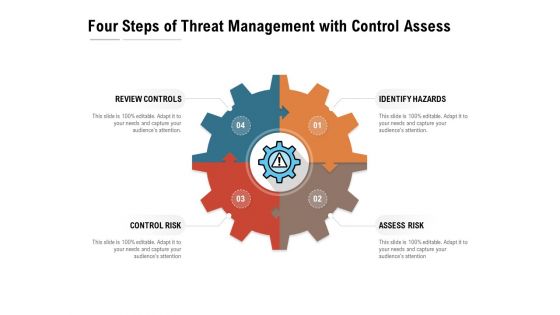
Four Steps Of Threat Management With Control Assess Ppt PowerPoint Presentation Pictures Show
Presenting this set of slides with name four steps of threat management with control assess ppt powerpoint presentation pictures show. This is a four stage process. The stages in this process are review controls, identify hazards, assess risk, control risk. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Moral Hazard Problem Arises In Powerpoint And Google Slides Cpb
Presenting our innovatively-designed set of slides titled Moral Hazard Problem Arises In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Moral Hazard Problem Arises that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well-structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Moral Hazard Problem Arises In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
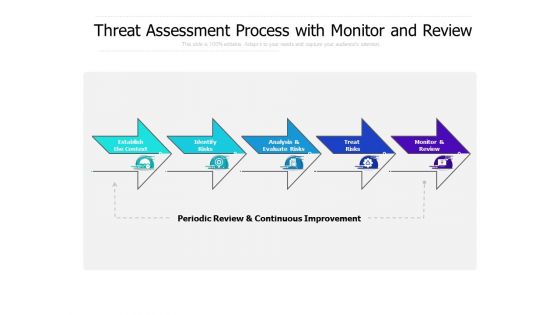
Threat Assessment Process With Monitor And Review Ppt PowerPoint Presentation Slides Templates PDF
Presenting this set of slides with name threat assessment process with monitor and review ppt powerpoint presentation slides templates pdf. This is a five stage process. The stages in this process are establish the context, identify risks, analysis and evaluate risks, treat risks, monitor and review. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
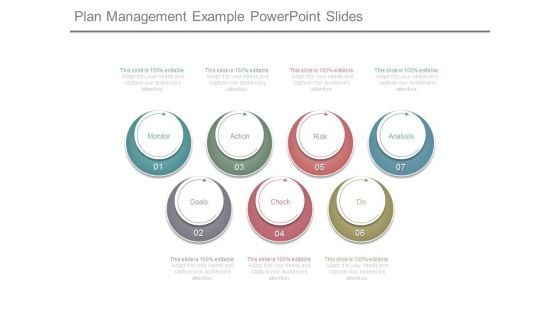
Plan Management Example Powerpoint Slides
This is a plan management example powerpoint slides. This is a seven stage process. The stages in this process are monitor, action, risk, analysis, goals, check, doing.
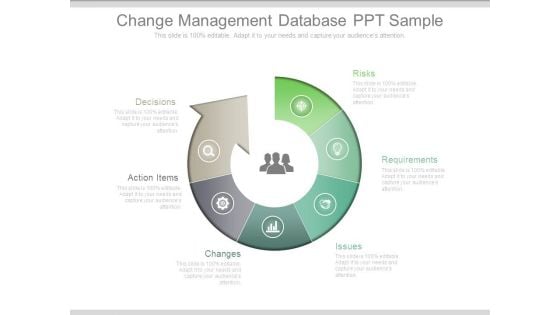
Change Management Database Ppt Sample
This is a change management database ppt sample. This is a six stage process. The stages in this process are risks, requirements, issues, changes, action items, decisions.
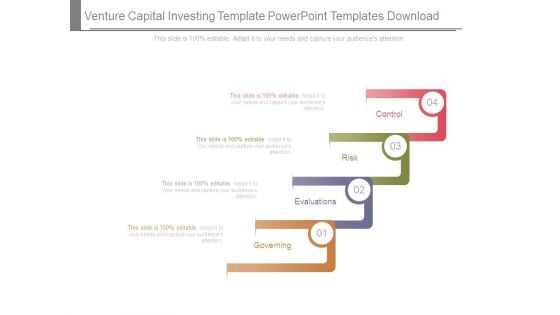
Venture Capital Investing Template Powerpoint Templates Download
This is a venture capital investing template powerpoint templates download. This is a four stage process. The stages in this process are control, risk, evaluations, governing.
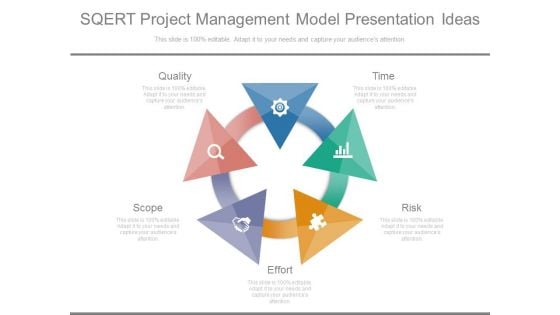
Sqert Project Management Model Presentation Ideas
This is a sqert project management model presentation ideas. This is a five stage process. The stages in this process are quality, time, risk, effort, scope.

Project Management Budget Plan Ppt Example
This is a project management budget plan ppt example. This is a six stage process. The stages in this process are scope, quality, schedule, budget, resource, risk.

Management Communication Model Ppt Example File
This is a management communication model ppt example file. This is a five stage process. The stages in this process are baseline, risks, resources, tasks, quality.

Template For Project Management Presentation Deck
This is a template for project management presentation deck. This is a six stage process. The stages in this process are resourcing, schedule, budget, risks, benefit, issue.

Project Management Schedule Sample Powerpoint Graphics
This is a project management schedule sample powerpoint graphics. This is a one stage process. The stages in this process are opportunity, risk, review, exposure.

Plan Scope Management Template Ppt Inspiration
This is a plan scope management template ppt inspiration. This is a six stage process. The stages in this process are scope, budget, quality, resources, risk, schedule.

Successful Product Inauguration Management Concerns Faced Due To Ineffective Guidelines PDF
This slide provides information regarding issues faced by firm while developing new product in terms of value risk, usability risk, feasibility risk, etc. Deliver an awe inspiring pitch with this creative successful product inauguration management concerns faced due to ineffective guidelines pdf bundle. Topics like requirements, customer, market, communication can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
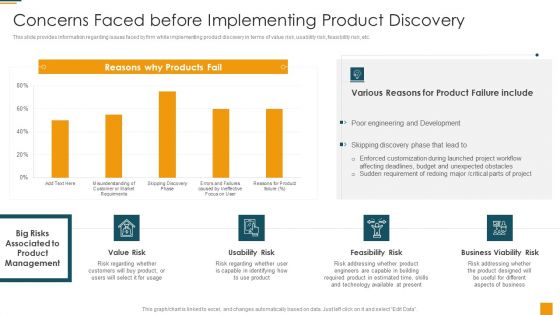
Managing Initial Stage Of Product Design And Development Concerns Faced Before Implementing Professional PDF
This slide provides information regarding issues faced by firm while implementing product discovery in terms of value risk, usability risk, feasibility risk, etc. Deliver an awe inspiring pitch with this creative managing initial stage of product design and development concerns faced before implementing professional pdf bundle. Topics like concerns faced before implementing product discovery can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Information Security Program Strategic Agenda Process Microsoft Pdf
This slide represents action plan process for information security programs. It consists of steps such as make information security team, manage assets and inventory, evaluate risk, manage risk, create incident recovery plan, etc. Showcasing this set of slides titled Information Security Program Strategic Agenda Process Microsoft Pdf. The topics addressed in these templates are Assets And Inventory, Evaluate Risk, Manage Risk. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide represents action plan process for information security programs. It consists of steps such as make information security team, manage assets and inventory, evaluate risk, manage risk, create incident recovery plan, etc.

Management Skills For New Supervisors Template Presentation Powerpoint
This is a management skills for new supervisors template presentation powerpoint. This is a three stage process. The stages in this process are results, feedback, assess risk.
Asset Allocation Ppt PowerPoint Presentation Icon Slides
This is a asset allocation ppt powerpoint presentation icon slides. This is a two stage process. The stages in this process are reward, risk.
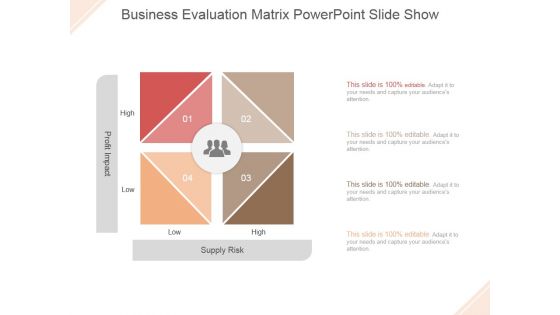
Business Evaluation Matrix Ppt PowerPoint Presentation Professional
This is a business evaluation matrix ppt powerpoint presentation professional. This is a four stage process. The stages in this process are profit impact, supply risk, low, high.


 Continue with Email
Continue with Email

 Home
Home


































