Risk Template

Business People Clipart 3d Traffic Police Man PowerPoint Slides
We present our business people clipart 3d traffic police man PowerPoint Slides.Use our Cones PowerPoint Templates because Our PowerPoint Templates and Slides has conjured up a web of all you need with the help of our great team. Use them to string together your glistening ideas. Present our Security PowerPoint Templates because It will let you Set new benchmarks with our PowerPoint Templates and Slides. They will keep your prospects well above par. Download and present our Signs PowerPoint Templates because Our PowerPoint Templates and Slides will let your team Walk through your plans. See their energy levels rise as you show them the way. Download our Shapes PowerPoint Templates because Our PowerPoint Templates and Slides will help you be quick off the draw. Just enter your specific text and see your points hit home. Download and present our Technology PowerPoint Templates because Our PowerPoint Templates and Slides will let you Hit the right notes. Watch your audience start singing to your tune.Use these PowerPoint slides for presentations relating to 3d, Alert, Attention, Background, Barrier, Boundary, Caution, Character, Cone, Construct, Construction, Danger, Design, Equipment, Forbidden, Guy, Helmet, Highway, Human, Icon, Idea, Illustration, Marking, Men, Obstacle, Orange, People, Person, Puppets, Reflection, Repair, Road, Safety, Security, Set, Shape, Sign, Signal, Stop, Street, Striped, Symbol, Traffic, Traffic-Coins, Traffic , Transportation, Warning, White, Work, Yellow. The prominent colors used in the PowerPoint template are Green, White, Orange. Our Business People Clipart 3d Traffic Police Man PowerPoint Slides encourage a creative environment. Allow diverse ideas to gain acceptance.
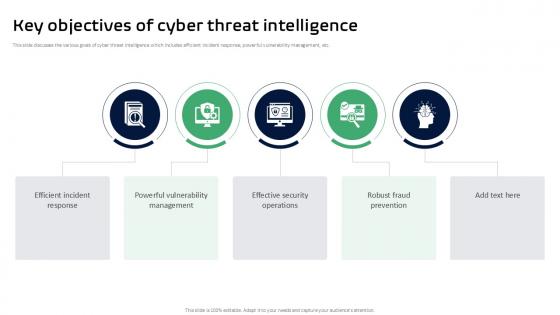
Key Objectives Of Cyber Threat Intelligence Ppt Sample
This slide discusses the various goals of cyber threat intelligence which includes efficient incident response, powerful vulnerability management, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Key Objectives Of Cyber Threat Intelligence Ppt Sample to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide discusses the various goals of cyber threat intelligence which includes efficient incident response, powerful vulnerability management, etc.
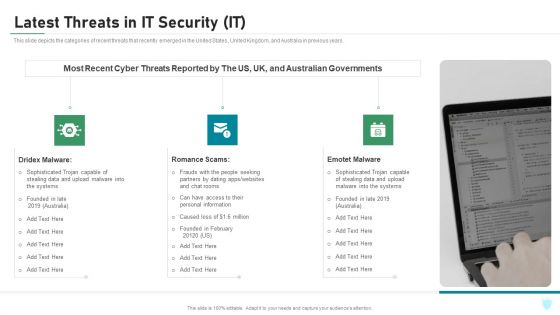
Latest Threats In IT Security IT Ppt Gallery Elements PDF
This slide depicts the categories of recent threats that recently emerged in the United States, United Kingdom, and Australia in previous years. Presenting latest threats in it security it ppt gallery elements pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like dridex malware, romance scams, emotet malware. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
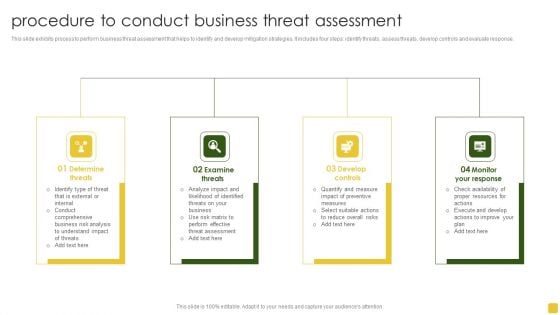
Procedure To Conduct Business Threat Assessment Topics PDF
This slide exhibits process to perform business threat assessment that helps to identify and develop mitigation strategies. It includes four steps identify threats, assess threats, develop controls and evaluate response.Presenting Procedure To Conduct Business Threat Assessment Topics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Determine Threats, Examine Threats, Develop Controls. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Building An Effective Threat Intelligence Framework Icons PDF
This slide showcases steps to create a framework for effective cyber threat intelligence that will help prevent firms from cyber threats. It includes steps such as scope definition, defines specific goals, cyber threat intelligence tools and continuous refinement. Presenting Building An Effective Threat Intelligence Framework Icons PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Scope Definition, Define Specific Goals, Cyber Threat Intelligence Tools. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
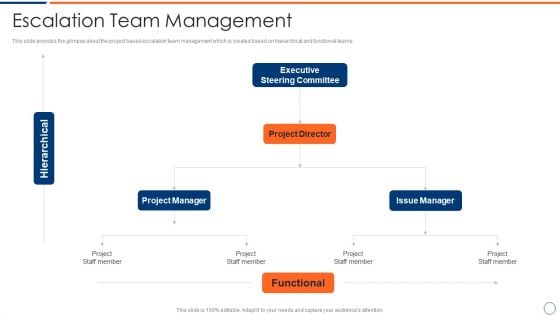
How To Intensify Project Threats Escalation Team Management Slides PDF
This slide provides the glimpse about the project based escalation team management which is created based on hierarchical and functional teams. Presenting how to intensify project threats escalation team management slides pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like project manager, issue manager, functional, project director, executive steering committee. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Swot Analysis Of Adc Cosmetics Company Threats Guidelines PDF
This slide shows some threats that may effect the company in future course of time and impact the company profits. Some potential threats are Intense Competition from Similar Companies , Changes in Consumer Demand and Preferences , Government Regulations and Currency Fluctuations etc. This is a swot analysis of adc cosmetics company threats guidelines pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like intense competition, consumer demand, currency fluctuations, threat. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Techniques Used In Ethical Hacking Ppt Infographics Guide PDF
This slide represents the techniques of ethical hacking such as port scanning, analyzing and sniffing network traffic, detection of SQL injections, an inspection of patch installation. This is a techniques used in ethical hacking ppt infographics guide pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like systems, methods, analyzing, network, information. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Social Media Marketing With Business Objectives And Kpis Ppt Professional Microsoft PDF
This slide covers Connection between social media branding goals and business objective. It also includes business objective such as increase brand awareness, increase online sales , boost brand loyalty and revenue increase from new product. Presenting social media marketing with business objectives and kpis ppt professional microsoft pdf to dispense important information. This template comprises two stages. It also presents valuable insights into the topics including business, marketing, objectives. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

HR SWOT Analysis For Talent Management Graphics PDF
This slide represents the SWOT analysis of talent management in an organization. It includes strengths such as adaptability to change, weaknesses such as poor work life balance, opportunities such as diverse workshops and threats such as disengaged employees.Presenting HR SWOT Analysis For Talent Management Graphics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Diverse Workshops, Enhanced Career, Planning Programs This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
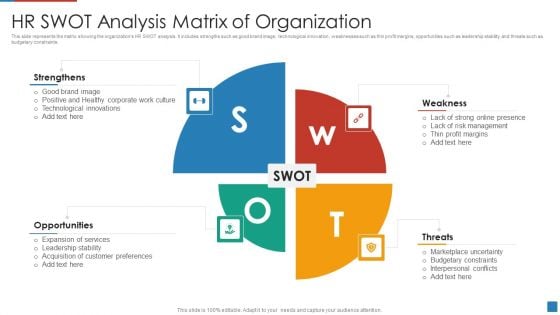
HR SWOT Analysis Matrix Of Organization Designs PDF
This slide represents the matrix showing the organizations HR SWOT analysis. It includes strengths such as good brand image, technological innovation, weaknesses such as thin profit margins, opportunities such as leadership stability and threats such as budgetary constraints.Presenting HR SWOT Analysis Matrix Of Organization Designs PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Marketplace Uncertainty, Budgetary Constraints, Interpersonal Conflicts This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
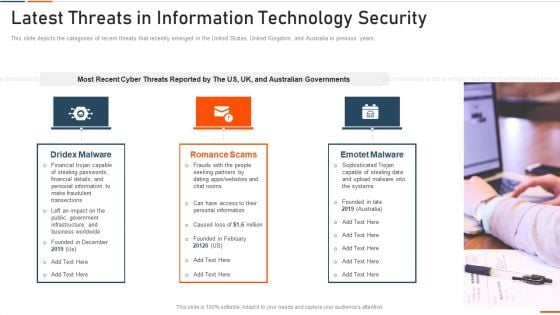
Latest Threats In Information Technology Security Ppt Pictures Designs PDF
This slide represents the different elements of Network security such as application security, network security, information security, etc. This is a latest threats in information technology security ppt pictures designs pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like network security, cloud security, application security, operational security, information security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
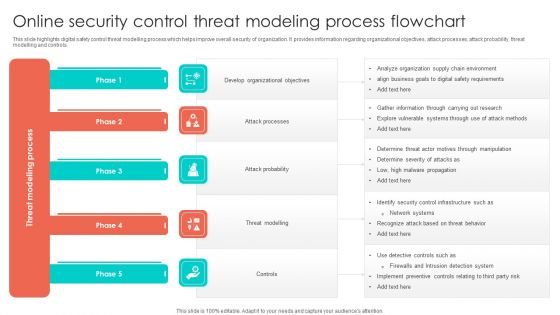
Online Security Control Threat Modeling Process Flowchart Structure PDF
This slide highlights digital safety control threat modelling process which helps improve overall security of organization. It provides information regarding organizational objectives, attack processes, attack probability, threat modelling and controls. Presenting Online Security Control Threat Modeling Process Flowchart Structure PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Develop Organizational Objectives, Attack Probability, Threat Modelling. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
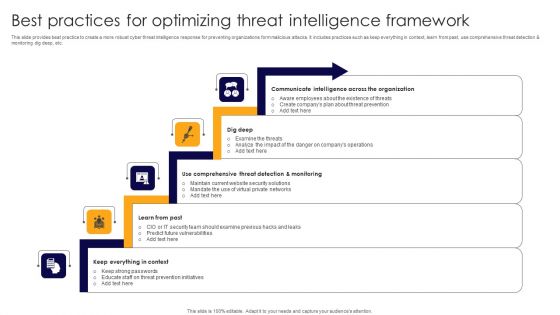
Best Practices For Optimizing Threat Intelligence Framework Formats PDF
This slide provides beat practice to create a more robust cyber threat intelligence response for preventing organizations form malicious attacks. It includes practices such as keep everything in context, learn from past, use comprehensive threat detection and monitoring dig deep, etc. Presenting Best Practices For Optimizing Threat Intelligence Framework Formats PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Communicate Intelligence, Dig Deep, Comprehensive Threat Detection. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
SWOT Analysis Of XYZ Logistics Company Threats Icons PDF
This slide shows some threats that may effect the company in future course of time and impact the company profits. Some potential threats are Rising Fuel Costs, Intense Competition, Government Regulations and Currency Fluctuations etc.Presenting swot analysis of xyz logistics company threats icons pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like intense competition, government regulations and currency fluctuations, rising fuel costs . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
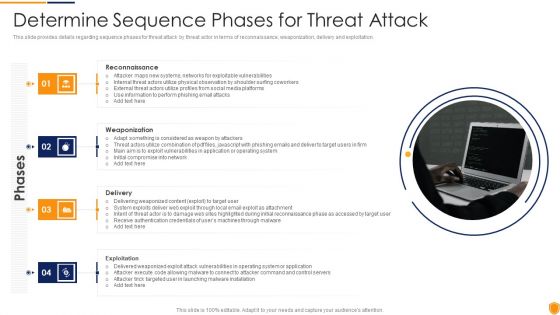
Mitigating Cybersecurity Threats And Vulnerabilities Determine Sequence Phases Elements PDF
This slide provides details regarding sequence phases for threat attack by threat actor in terms of reconnaissance, weaponization, delivery and exploitation. This is a mitigating cybersecurity threats and vulnerabilities determine sequence phases elements pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like reconnaissance, weaponization, delivery, exploitation. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
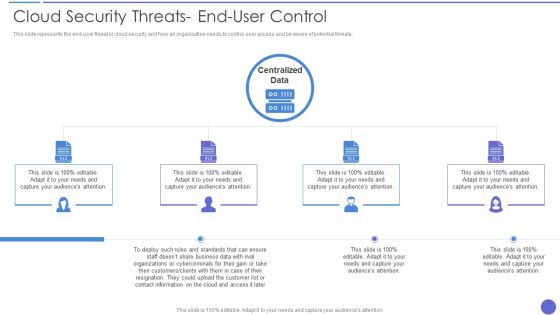
Cloud Security Threats End User Control Themes PDF
This slide represents the end user threat in cloud security and how an organization needs to control user access and be aware of potential threats. This is a Cloud Security Threats End User Control Themes PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Centralized Data, Customer, Contact Information. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information Technology Security Threats And Key Performance Indicators Formats PDF
This slide covers the information related to the various types of cyber threats and the key performance indicators used by the organization for dealing with these security breaches. Presenting Information Technology Security Threats And Key Performance Indicators Formats PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Threats Reported, Security Incidents, Intrusion Attempts. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cloud Network Security Threats And Solutions Infographics PDF
The slide showcases threats occurred due to data flowing between cloud service providers and organizations with their solutions. It includes lack of cloud security architecture and tactics, account hijacking , weak control plane , inadequate of identity, credentials, etc. Presenting Cloud Network Security Threats And Solutions Infographics PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Threats, Description, Solutions. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
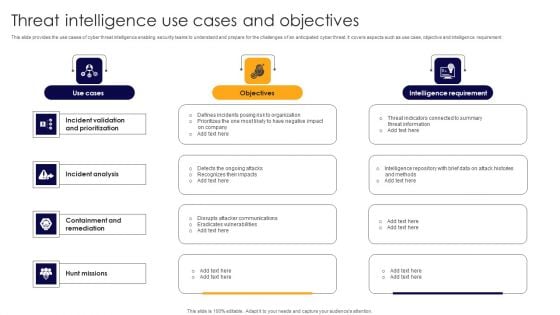
Threat Intelligence Use Cases And Objectives Demonstration PDF
This slide provides the use cases of cyber threat intelligence enabling security teams to understand and prepare for the challenges of an anticipated cyber threat. It covers aspects such as use case, objective and intelligence requirement. Presenting Threat Intelligence Use Cases And Objectives Demonstration PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Incident Analysis, Containment Remediation, Hunt Missions. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Successful Business Men Team Work To Solve The Problem PowerPoint Slides
We present our successful business men team work to solve the problem PowerPoint Slides.Download our People PowerPoint Templates because These PowerPoint Templates and Slides will give the updraft to your ideas. See them soar to great heights with ease. Download our Puzzles or Jigsaws PowerPoint Templates because Our PowerPoint Templates and Slides will generate and maintain the level of interest you desire. They will create the impression you want to imprint on your audience. Use our Shapes PowerPoint Templates because our PowerPoint Templates and Slides will give your ideas the shape. Download and present our Business PowerPoint Templates because our PowerPoint Templates and Slides are the string of your bow. Fire of your ideas and conquer the podium. Use our Marketing PowerPoint Templates because you should Whip up a frenzy with our PowerPoint Templates and Slides. They will fuel the excitement of your team.Use these PowerPoint slides for presentations relating to team, work, partnership, seo, puzzle, human, collective, assemble, challenge, implementation, business, concept, assembly, unity, success, decisions, teamwork, fit, character, match, cooperation, join, search engine, people, opposite, idea, four, support, figure, togetherness, piece, connection, solve, strategy, humorous, holding, solution, problem, group, color, making, colorful, person, connect, jigsaw, answer, solved, part, build. The prominent colors used in the PowerPoint template are Red, Blue navy, Green. Sharpen your point with our Successful Business Men Team Work To Solve The Problem PowerPoint Slides. You will come out on top.

SWOT Analysis Threats Luxury Automobile Vehicles PPT Sample CP SS V
This slide focuses on strengths, weakness, opportunities and threats to evaluate competitive position of company. It assists business to determine internal and external factors affecting growth and development. Get a simple yet stunning designed SWOT Analysis Threats Luxury Automobile Vehicles PPT Sample CP SS V. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit SWOT Analysis Threats Luxury Automobile Vehicles PPT Sample CP SS V can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide focuses on strengths, weakness, opportunities and threats to evaluate competitive position of company. It assists business to determine internal and external factors affecting growth and development.
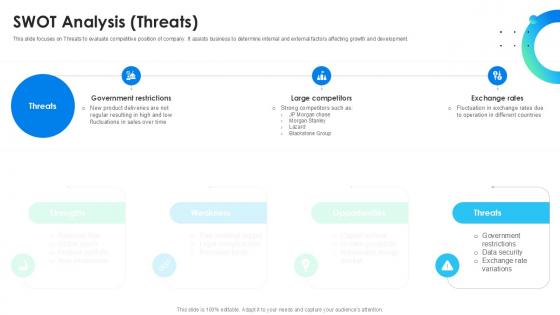
SWOT Analysis Threats Global Energy Company Profile PPT Presentation CP SS V
This slide focuses on Threats to evaluate competitive position of company. It assists business to determine internal and external factors affecting growth and development. Get a simple yet stunning designed SWOT Analysis Threats Global Energy Company Profile PPT Presentation CP SS V. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit SWOT Analysis Threats Global Energy Company Profile PPT Presentation CP SS V can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide focuses on Threats to evaluate competitive position of company. It assists business to determine internal and external factors affecting growth and development.
SWOT Analysis Of ABC Software Company Threats Icons PDF
This slide shows the Threats related to ABC Software Company which includes Liability Laws, Lawsuits, Shortage of skilled workforce etc. Presenting swot analysis of abc software company threats icons pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like liability laws, intense competition, shortage of skilled workforce. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
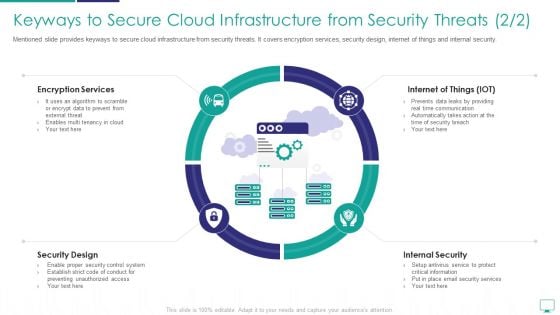
Keyways To Secure Cloud Infrastructure From Security Threats Formats PDF
Mentioned slide provides keyways to secure cloud infrastructure from security threats. It covers encryption services, security design, internet of things and internal security.This is a keyways to secure cloud infrastructure from security threats formats pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like encryption services, internet of things, security design. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
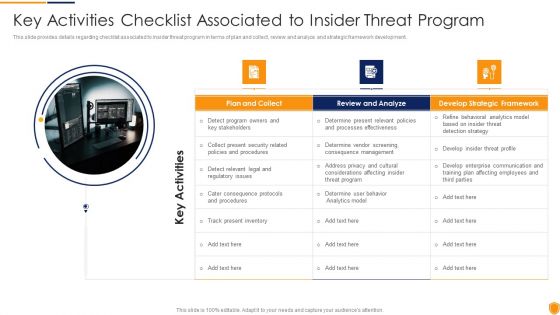
Mitigating Cybersecurity Threats And Vulnerabilities Key Activities Checklist Diagrams PDF
This slide provides details regarding checklist associated to insider threat program in terms of plan and collect, review and analyze and strategic framework development. This is a mitigating cybersecurity threats and vulnerabilities key activities checklist diagrams pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like plan and collect, review and analyze, develop strategic framework. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
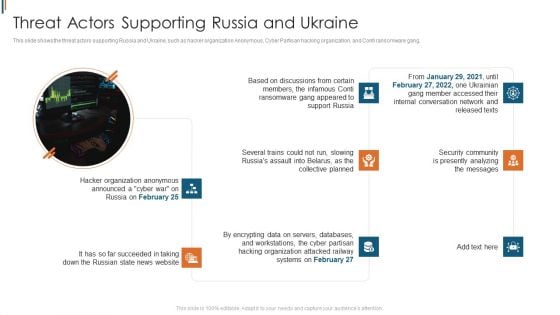
Ukraine Cyberwarfare Threat Actors Supporting Russia And Ukraine Graphics Pdf
This slide shows the threat actors supporting Russia and Ukraine, such as hacker organization Anonymous, Cyber Partisan hacking organization, and Conti ransomware gang. This is a ukraine cyberwarfare threat actors supporting russia and ukraine graphics pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security community is presently analyzing the messages, hacker organization anonymous announced, several trains could not run, slowing russias assault. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Security Threats Loss Of Data Guidelines PDF
This slide represents the data loss threat of cloud security it is essential to secure organization data and create backups. This is a Cloud Security Threats Loss Of Data Guidelines PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Strategies, Service Provider, Organization. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
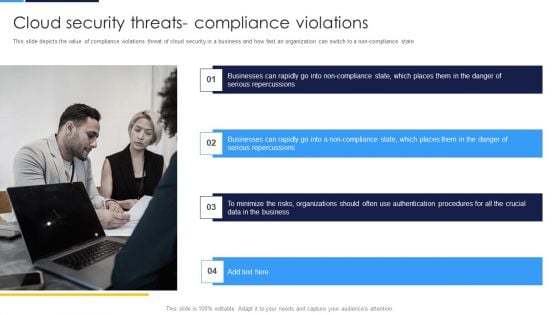
Cloud Security Assessment Cloud Security Threats Compliance Violations Mockup PDF
This slide depicts the value of compliance violations threat of cloud security in a business and how fast an organization can switch to a non compliance state.This is a Cloud Security Assessment Cloud Security Threats Compliance Violations Mockup PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Serious Repercussions, Data In The Business, Organizations Should You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Security Assessment Cloud Security Threats Malware Attacks Inspiration PDF
This slide represents the malware threat of cloud security and how it can affect data stored on the cloud, further leading to company loss.This is a Cloud Security Assessment Cloud Security Threats Malware Attacks Inspiration PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Cloud Administrations, Information Exfiltration, Protection Frameworks. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
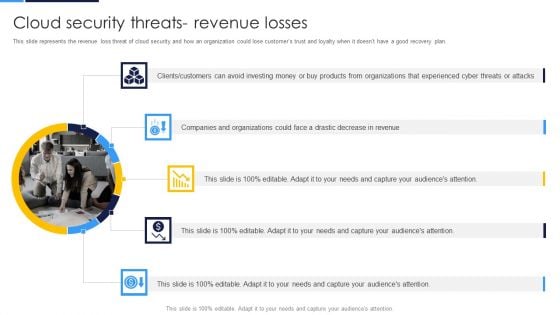
Cloud Security Assessment Cloud Security Threats Revenue Losses Introduction PDF
This slide represents the revenue loss threat of cloud security and how an organization could lose customers trust and loyalty when it doesnt have a good recovery plan.Presenting Cloud Security Assessment Cloud Security Threats Revenue Losses Introduction PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Clients Or Customers, Companies And Organizations, Organizations That Experienced. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Keyways To Secure Cloud Infrastructure From Security Threats Inspiration PDF
Mentioned slide provides keyways to secure cloud infrastructure from security threats. It covers encryption services, security design, internet of things and internal security.Presenting Keyways To Secure Cloud Infrastructure From Security Threats Inspiration PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Encryption Services, Internal Security, Security Design. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
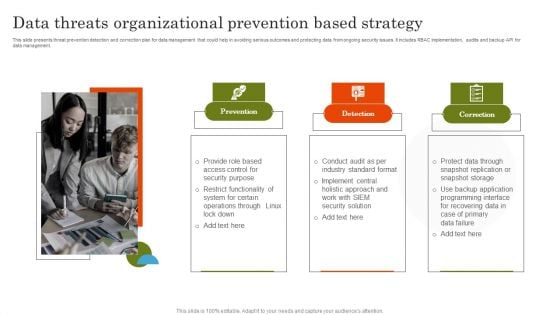
Data Threats Organizational Prevention Based Strategy Infographics PDF
This slide presents threat prevention detection and correction plan for data management that could help in avoiding serious outcomes and protecting data from ongoing security issues. It includes RBAC implementation, audits and backup API for data management. Increase audience engagement and knowledge by dispensing information using Data Threats Organizational Prevention Based Strategy Infographics PDF. This template helps you present information on three stages. You can also present information on Prevention, Detection, Correction using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.

SWOT Analysis Of HCL Plus Logistics Company Threats Rules PDF
This slide shows some threats that may effect the company in future course of time and impact the company profits. Some potential threats are Intense Competition from Rivalries , Rising Fuel Costs , Government Regulations and Currency Fluctuations etc. Deliver and pitch your topic in the best possible manner with this swot analysis of hcl plus logistics company threats rules pdf. Use them to share invaluable insights on technologies, market, technology, costs, customer and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
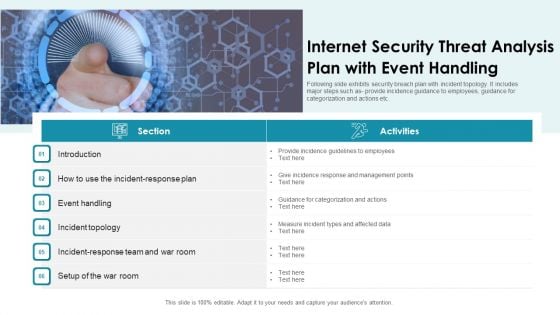
Internet Security Threat Analysis Plan With Event Handling Summary PDF
Following slide exhibits security breach plan with incident topology. It includes major steps such as- provide incidence guidance to employees, guidance for categorization and actions etc. Presenting internet security threat analysis plan with event handling summary pdf to dispense important information. This template comprises one stage. It also presents valuable insights into the topics including internet security threat analysis plan with event handling. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
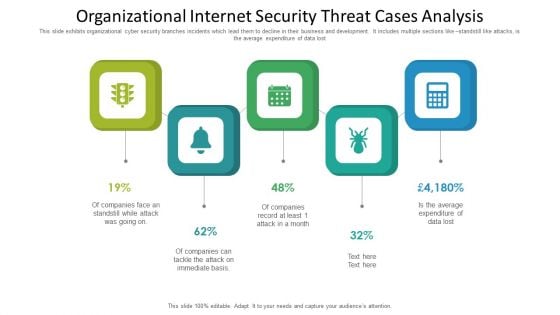
Organizational Internet Security Threat Cases Analysis Information PDF
This slide exhibits organizational cyber security branches incidents which lead them to decline in their business and development. It includes multiple sections like standstill like attacks, is the average expenditure of data lost. Presenting organizational internet security threat cases analysis information pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including organizational internet security threat cases analysis. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
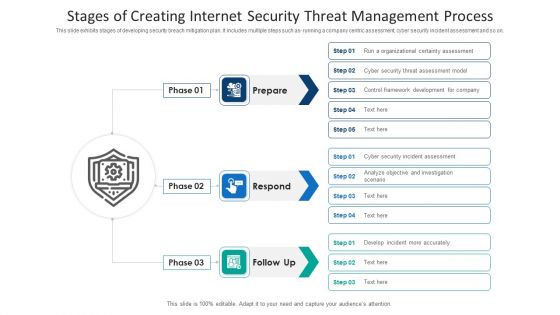
Stages Of Creating Internet Security Threat Management Process Information PDF
This slide exhibits stages of developing security breach mitigation plan. It includes multiple steps such as- running a company centric assessment, cyber security incident assessment and so on. Presenting stages of creating internet security threat management process information pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including stages of creating internet security threat management process. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Safety And Security Threat Report With Action Plan Mockup PDF
This slide shows report which can be used by an organization to prepare server security threat report. It includes date, time, description, action plan and remarks related to incident. Presenting Safety And Security Threat Report With Action Plan Mockup PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Action Plan, Remarks, Diagnostic. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
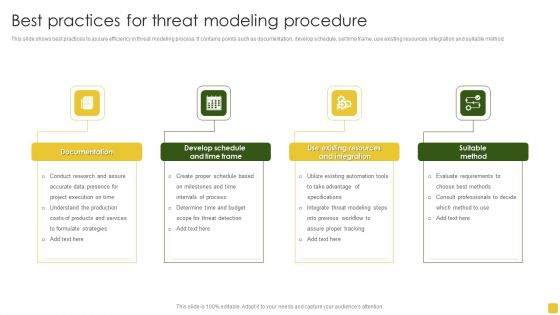
Best Practices For Threat Modeling Procedure Themes PDF
This slide shows best practices to assure efficiency in threat modeling process. It contains points such as documentation, develop schedule, set time frame, use existing resources, integration and suitable method.Presenting Best Practices For Threat Modeling Procedure Themes PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Project Execution, Determine Budget, Existing Resources. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
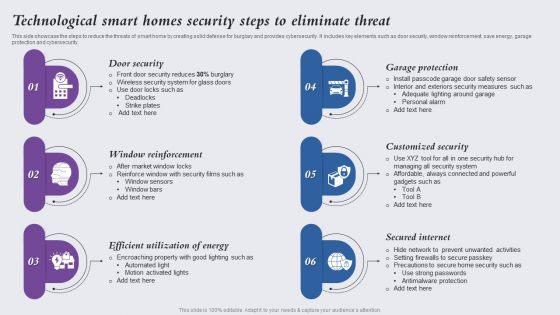
Technological Smart Homes Security Steps To Eliminate Threat Themes PDF
This side showcase the steps to reduce the threats of smart home by creating solid defense for burglary and provides cybersecurity. It includes key elements such as door security, window reinforcement, save energy, garage protection and cybersecurity. Presenting Technological Smart Homes Security Steps To Eliminate Threat Themes PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Door Security, Window Reinforcement, Efficient Utilization Energy. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
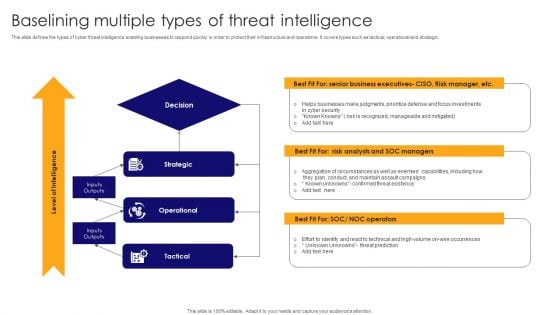
Baselining Multiple Types Of Threat Intelligence Pictures PDF
This slide defines the types of cyber threat intelligence enabling businesses to respond quickly in order to protect their infrastructure and operations. It covers types such as tactical, operational and strategic. Presenting Baselining Multiple Types Of Threat Intelligence Pictures PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Strategic, Operational, Tactical . This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
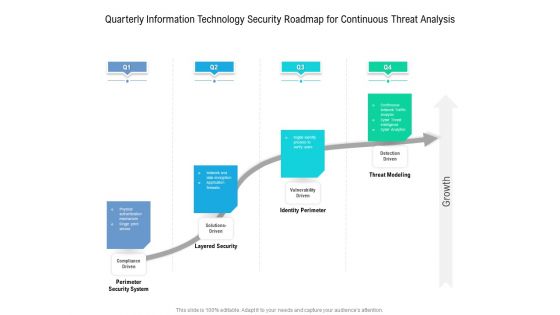
Quarterly Information Technology Security Roadmap For Continuous Threat Analysis Download
Presenting the quarterly information technology security roadmap for continuous threat analysis download. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
Ppt Background Continual Seven Stages Linear Flow Communication Skills PowerPoint 5 Image
We present our PPT Background continual seven stages linear flow communication skills PowerPoint 5 Image. Use our Business PowerPoint Templates because, you are buzzing with ideas. Use our Design PowerPoint Templates because; Grab the attention of your team with this eye catching template signifying. Use our Arrows PowerPoint Templates because, you know the path so show the way. Use our Shapes PowerPoint Templates because, Weak Links & Chains: - Chain reactions and the element of teamwork add value to your efforts. Use our Process and Flows PowerPoint Templates because, Heighten the anticipation of your audience with this slide listing .Use these PowerPoint slides for presentations relating to advertising, arrow, background, banner, bookmark, choice, concept, creative, design, direction, flow, label, layout, manual, marketing, modern, process, product, promotion, sequence, simple, special, step, symbol, tab, tag, turquoise, tutorial, two, vector, . The prominent colors used in the PowerPoint template are Red, Gray, and Black Resolve problems with our Ppt Background Continual Seven Stages Linear Flow Communication Skills PowerPoint 5 Image. Download without worries with our money back guaranteee.
SWOT Analysis Of XYZ Logistics Company Weakness Icons PDF
This slide shows the weaknesses of XYZ Logistics Company that it must overcome such as Lack of optimum Technology, High Operating Costs, Limited Scope for Differentiation etc.This is a swot analysis of xyz logistics company weakness icons pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like limited technology, high operating costs, limited scope for differentiation . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
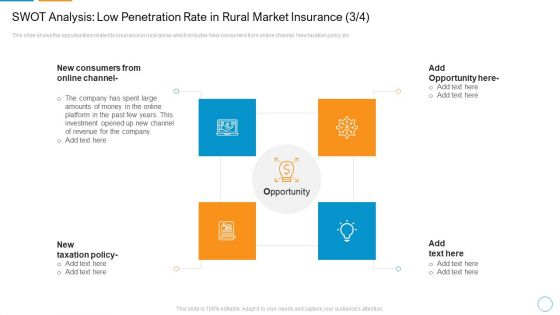
SWOT Analysis Low Penetration Rate In Rural Market Insurance Policy Mockup PDF
This slide shows the opportunities related to insurance in rural areas which includes New consumers from online channel, New taxation policy etc.Presenting swot analysis low penetration rate in rural market insurance policy mockup pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like new consumers from online channel, opportunity here, taxation policy In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
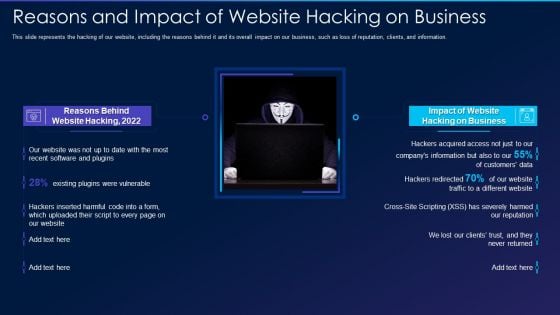
Cyber Exploitation IT Reasons And Impact Of Website Hacking On Business Elements PDF
This slide represents the hacking of our website, including the reasons behind it and its overall impact on our business, such as loss of reputation, clients, and information. Presenting cyber exploitation it reasons and impact of website hacking on business elements pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like reasons behind website hacking, 2022, impact of website hacking on business. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Global Cyber Terrorism Incidents On The Rise IT How To Protect Company From Trojan Attacks Summary PDF
This slide explains how to protect the company from trojan attacks which include procedures such as installing advanced antivirus software. This is a global cyber terrorism incidents on the rise it how to protect company from trojan attacks summary pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like install a good antivirus programm, web application firewall waf, stick to reliable sources, avoid third party downloads. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

How To Intensify Project Threats Project Closure Report Mockup PDF
This slide provides the glimpse about the final step of issue and escalation process which covers the project closure report along with the details such as project information, benefits, key metrics, project deliverables, controls in place, shortfalls, etc. This is a how to intensify project threats project closure report mockup pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like project information, benefits, key metrics, project deliverables, controls in place, shortfalls. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
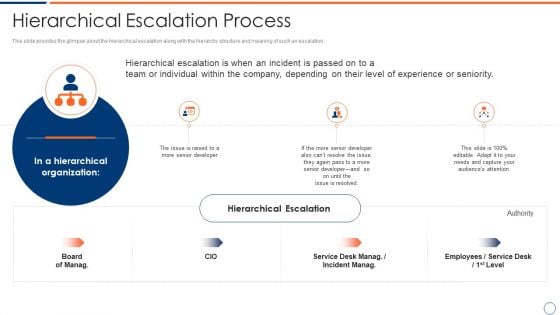
How To Intensify Project Threats Hierarchical Escalation Process Summary PDF
This slide provides the glimpse about the hierarchical escalation along with the hierarchy structure and meaning of such an escalation. This is a how to intensify project threats hierarchical escalation process summary pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like developer, service, hierarchical, organization. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
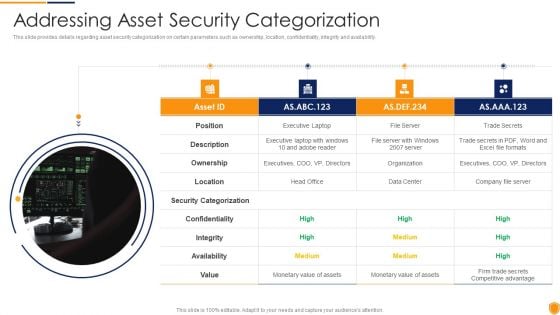
Mitigating Cybersecurity Threats And Vulnerabilities Addressing Asset Security Elements PDF
This slide provides details regarding asset security categorization on certain parameters such as ownership, location, confidentiality, integrity and availability. This is a mitigating cybersecurity threats and vulnerabilities addressing asset security elements pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like ownership, location, integrity, security categorization. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
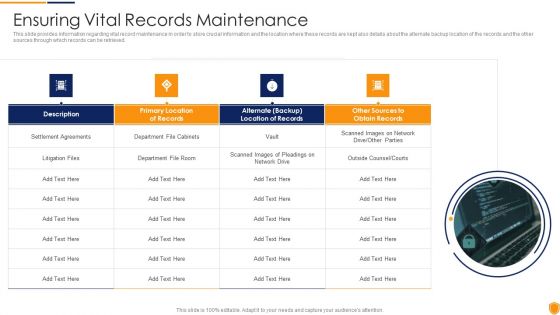
Mitigating Cybersecurity Threats And Vulnerabilities Ensuring Vital Records Inspiration PDF
This slide provides information regarding vital record maintenance in order to store crucial information and the location where these records are kept also details about the alternate backup location of the records and the other sources through which records can be retrieved. This is a mitigating cybersecurity threats and vulnerabilities ensuring vital records inspiration pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like ensuring vital records maintenance. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Mitigating Cybersecurity Threats And Vulnerabilities Incident Reporting Themes PDF
This slide will help in providing an overview of the various reported incidents, average cost per incident and number of people involved in the various incidents across different departments. Presenting mitigating cybersecurity threats and vulnerabilities incident reporting themes pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like incident reporting by different departments. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
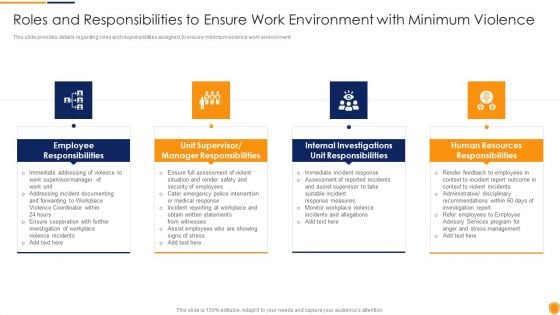
Mitigating Cybersecurity Threats And Vulnerabilities Roles And Responsibilities Introduction PDF
This slide provides details regarding roles and responsibilities assigned to ensure minimum violence work environment. This is a mitigating cybersecurity threats and vulnerabilities roles and responsibilities introduction pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like employee responsibilities, manager responsibilities, unit responsibilities, human resources responsibilities. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Cloud Security Assessment Cloud Security Threats Shared Vulnerabilities Icons PDF
This slide describes how organizations and providers share vulnerabilities of a system, so each party must take precautions to protect data.This is a Cloud Security Assessment Cloud Security Threats Shared Vulnerabilities Icons PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security Standards, Authorization Restrictions, Providers Already. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Business Problems And Their Solutions Icons PDF
This slide provides the business problems Delivery in bad weather, Odd time delivery, uncertainty etc. and their solutions like delivery by car, 24 or 7 delivery etc. This is a business problems and their solutions icons pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like problem, solution. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Strategic Promotional Guide For Restaurant Business Advertising Swot Analysis Demonstration PDF
Get a simple yet stunning designed Strategic Promotional Guide For Restaurant Business Advertising Swot Analysis Demonstration PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Strategic Promotional Guide For Restaurant Business Advertising Swot Analysis Demonstration PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
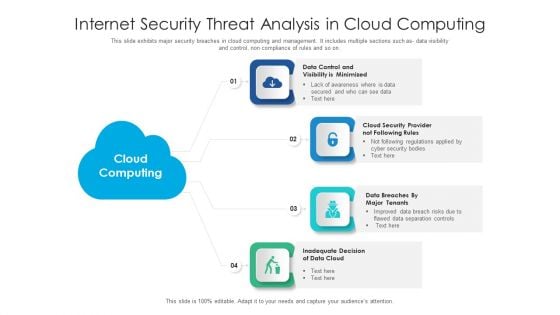
Internet Security Threat Analysis In Cloud Computing Information PDF
This slide exhibits major security breaches in cloud computing and management. It includes multiple sections such as- data visibility and control, non compliance of rules and so on. Presenting internet security threat analysis in cloud computing information pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including data cloud, cloud security, data control. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
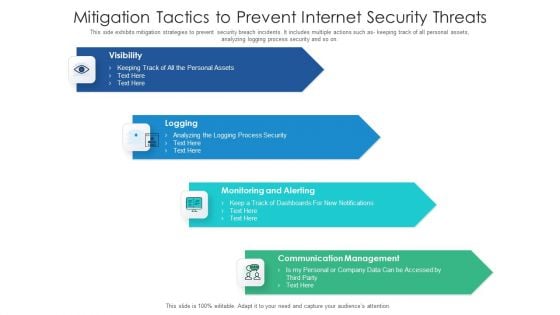
Mitigation Tactics To Prevent Internet Security Threats Formats PDF
This side exhibits mitigation strategies to prevent security breach incidents. It includes multiple actions such as keeping track of all personal assets, analyzing logging process security and so on. Presenting mitigation tactics to prevent internet security threats formats pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including communication management, monitoring and alerting, logging, visibility. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
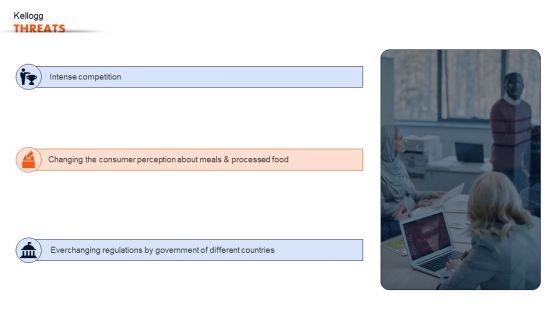
Ready To Eat Food Market Analysis Kellogg Threats Guidelines PDF
Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Ready To Eat Food Market Analysis Kellogg Threats Guidelines PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Smart Phone Security Tools For Preventing Threats Topics PDF
This slide shows latest security tools for managing phone security model. The purpose of this slide is to highlight various tools names with description for selecting most suitable tool. It include tools such as data loss prevention, identify and access management, etc. Presenting Smart Phone Security Tools For Preventing Threats Topics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Data Loss Prevention, Identity Access Management, Security Event Management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.


 Continue with Email
Continue with Email

 Home
Home


































