Risk
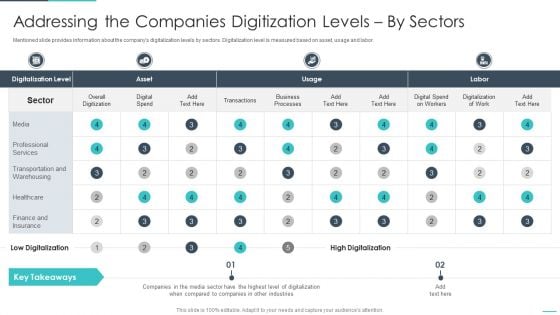
Handling Cyber Threats Digital Era Addressing The Companies Digitization Ppt Portfolio Smartart PDF
Mentioned slide provides information about the companys digitalization levels by sectors. Digitalization level is measured based on asset, usage and labor. Deliver and pitch your topic in the best possible manner with this andling cyber threats digital era addressing the companies digitization ppt portfolio smartart pdf. Use them to share invaluable insights on addressing the companies digitization levels by sectors and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Handling Cyber Threats Digital Era Checklist For Effectively Managing Asset Security Ppt Slides Example File PDF
Following slide displays system management checklist that company will use for effectively managing asset security. It also includes system management activities and frequency of performing them. Deliver an awe inspiring pitch with this creative handling cyber threats digital era checklist for effectively managing asset security ppt slides example file pdf bundle. Topics like checklist for effectively managing asset security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
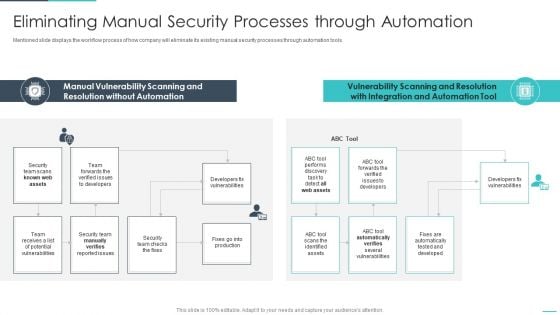
Handling Cyber Threats Digital Era Eliminating Manual Security Processes Ppt Show Influencers PDF
Mentioned slide displays the workflow process of how company will eliminate its existing manual security processes through automation tools. Deliver and pitch your topic in the best possible manner with this handling cyber threats digital era eliminating manual security processes ppt show influencers pdf. Use them to share invaluable insights on eliminating manual security processes through automation and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
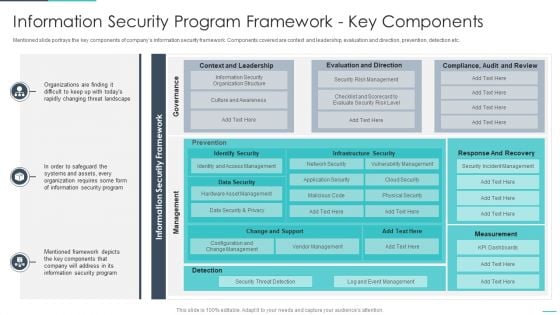
Handling Cyber Threats Digital Era Information Security Program Framework Ppt Model Summary PDF
Mentioned slide portrays the key components of companys information security framework. Components covered are context and leadership, evaluation and direction, prevention, detection etc. Deliver and pitch your topic in the best possible manner with this handling cyber threats digital era information security program framework ppt model summary pdf. Use them to share invaluable insights on information security program framework key components and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Handling Cyber Threats Digital Era Introducing New Incidents Logging Process Ppt Slides Graphic Images PDF
This slide displays the new incident logging process that company will introduce. It covers information of logging process, its description and responsible person details. Deliver an awe inspiring pitch with this creative handling cyber threats digital era introducing new incidents logging process ppt slides graphic images pdf bundle. Topics like introducing new incidents logging process can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
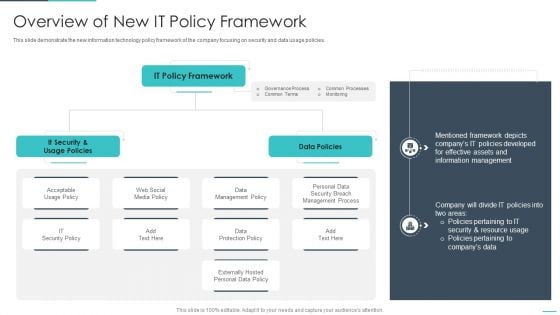
Handling Cyber Threats Digital Era Overview Of New IT Policy Framework Ppt Summary Guidelines PDF
This slide demonstrate the new information technology policy framework of the company focusing on security and data usage policies. Deliver and pitch your topic in the best possible manner with this handling cyber threats digital era overview of new it policy framework ppt summary guidelines pdf. Use them to share invaluable insights on overview of new it policy framework and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
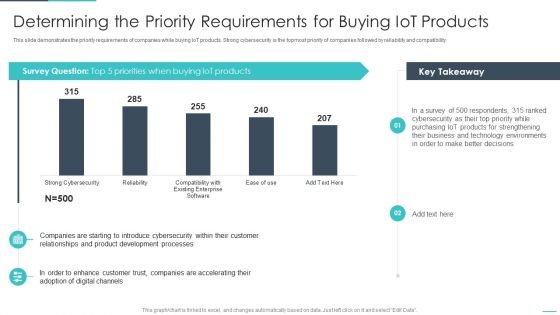
Handling Cyber Threats Digital Era Determining The Priority Requirements Ppt Outline Visual Aids PDF
This slide demonstrates the priority requirements of companies while buying IoT products. Strong cybersecurity is the topmost priority of companies followed by reliability and compatibility. Deliver an awe inspiring pitch with this creative handling cyber threats digital era determining the priority requirements ppt outline visual aids pdf bundle. Topics like determining the priority requirements for buying iot products can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Threat Management At Workplace Addressing Critical Business Functions Recovery Priorities Formats Pdf
This slide provides details regarding business functions recovery as firm needs to retrieve the crucial information based on priorities in various departments and time taken to retrieve the information. Deliver an awe inspiring pitch with this creative threat management at workplace addressing critical business functions recovery priorities formats pdf bundle. Topics like priorities, department, maximum allowable downtime can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Threat Management At Workplace Evaluating Financial Practices In Firm Ideas Pdf
The firm can track the financial performance by looking the financial practices it follows in order to avoid any early signs of financial distress. Deliver an awe inspiring pitch with this creative threat management at workplace evaluating financial practices in firm ideas pdf bundle. Topics like organization prepare cash flow projections, financial statements on a budget, comprehensive operating budget can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
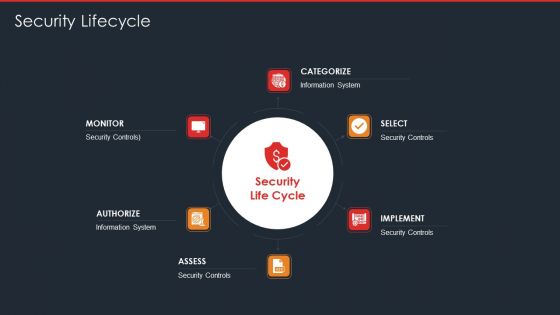
Data Safety Initiatives For Effective IT Security Threats Administration Security Lifecycle Template PDF
This is a data safety initiatives for effective it security threats administration security lifecycle template pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like information system, security controls, monitor, assess, implement, authorize. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Data Safety Initiatives For Effective IT Security Threats Administration Table Of Contents Themes PDF
Presenting data safety initiatives for effective it security threats administration table of contents themes pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like global market insights, gap identification, defining business priorities, about security program, companies digitization levels. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Agenda For Developing Cyber Security Threat Awareness Staff Training Program Inspiration PDF
This is a Agenda For Developing Cyber Security Threat Awareness Staff Training Program Inspiration PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Agenda. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
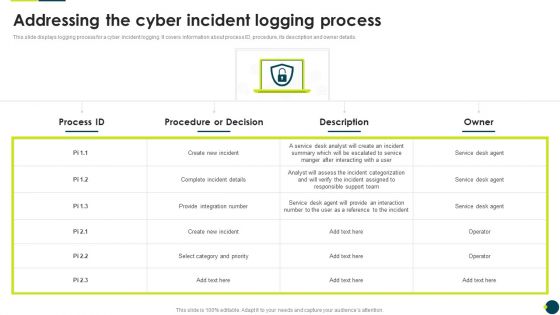
IT Threats Response Playbook Addressing The Cyber Incident Logging Process Introduction PDF
This slide displays logging process for a cyber incident logging. It covers information about process ID, procedure, its description and owner details.Deliver and pitch your topic in the best possible manner with this IT Threats Response Playbook Addressing The Cyber Incident Logging Process Introduction PDF. Use them to share invaluable insights on Provide Integration, Responsible Support, Assess The Incident and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
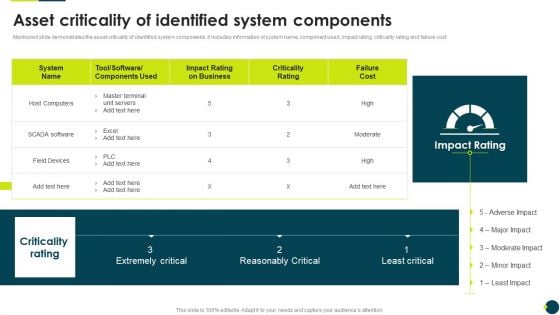
IT Threats Response Playbook Asset Criticality Of Identified System Components Themes PDF
Mentioned slide demonstrates the asset criticality of identified system components. It includes information of system name, component used, impact rating, criticality rating and failure cost.Deliver and pitch your topic in the best possible manner with this IT Threats Response Playbook Asset Criticality Of Identified System Components Themes PDF. Use them to share invaluable insights on Master Terminal, Extremely Critical, Reasonably Critical and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
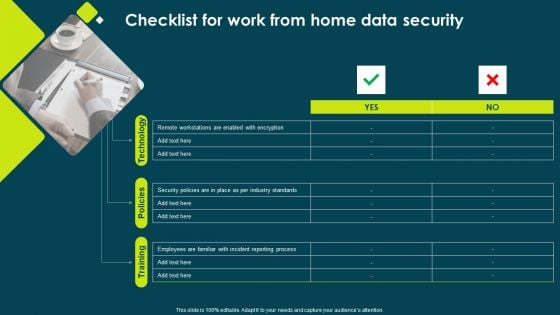
IT Threats Response Playbook Checklist For Work From Home Data Security Inspiration PDF
This is a IT Threats Response Playbook Checklist For Work From Home Data Security Inspiration PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security Policies, Incident Reporting, Remote Workstations. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Threats Response Playbook Classifying Various Security Issues And Attacks Professional PDF
Purpose of this slide is to show the classification of different security issues and attacks. Categories covered are majorly internal as well as external issues and attacks.Deliver and pitch your topic in the best possible manner with this IT Threats Response Playbook Classifying Various Security Issues And Attacks Professional PDF. Use them to share invaluable insights on External Issues, Audio Steganography, Malware Injection and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

IT Threats Response Playbook Communication Plan For Effective Incident Management Formats PDF
This slide portrays communication plan for successfully managing cyber incidents. Sections covered are deliverable info, recipient, delivery method, schedule and responsible person.Deliver an awe inspiring pitch with this creative IT Threats Response Playbook Communication Plan For Effective Incident Management Formats PDF bundle. Topics like Conference Meeting, Incident Information, Various Departments can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
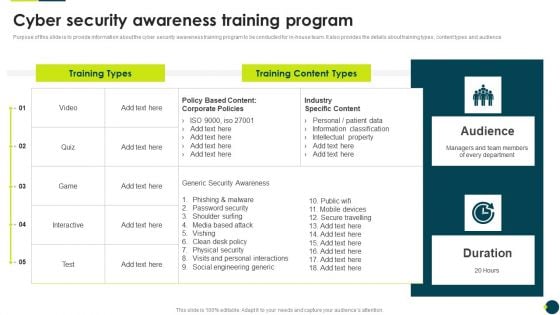
IT Threats Response Playbook Cyber Security Awareness Training Program Graphics PDF
Purpose of this slide is to provide information about the cyber security awareness training program to be conducted for in-house team. It also provides the details about training types, content types and audience.Deliver an awe inspiring pitch with this creative IT Threats Response Playbook Cyber Security Awareness Training Program Graphics PDF bundle. Topics like Phishing Malware, Password Security, Shoulder Surfing can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

IT Threats Response Playbook KPI Dashboard To Track Department Wise Security Incidents Brochure PDF
Mentioned slide portrays KPI dashboard that can be used to monitor department wise security incidents. KPIs covered are new cases, total cases, resolved and pending cases.Deliver an awe inspiring pitch with this creative IT Threats Response Playbook KPI Dashboard To Track Department Wise Security Incidents Brochure PDF bundle. Topics like It Department, Hr Department, Requires Immediate can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
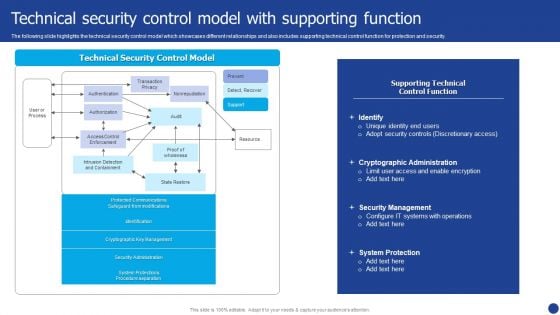
Information Technology Threat Mitigation Methods Technical Security Control Model With Supporting Function Introduction PDF
The following slide highlights the technical security control model which showcases different relationships and also includes supporting technical control function for protection and security. Deliver and pitch your topic in the best possible manner with this Information Technology Threat Mitigation Methods Technical Security Control Model With Supporting Function Introduction PDF. Use them to share invaluable insights on Cryptographic Administration, Security Management, System Protection and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Table Of Contents For Information Technology Threat Mitigation Methods Measures Diagrams PDF
Presenting Table Of Contents For Information Technology Threat Mitigation Methods Measures Diagrams PDF to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like IT Technical Control Measures, Technical Security, System Vulnerabilities. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

G7 Table Of Contents Enhancing Process Improvement By Regularly Managing Real Estate Project Threats Microsoft PDF
Make sure to capture your audiences attention in your business displays with our gratis customizable G7 Table Of Contents Enhancing Process Improvement By Regularly Managing Real Estate Project Threats Microsoft PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Ready To Eat Food Market Analysis General Mills Threats Graphics PDF
If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Ready To Eat Food Market Analysis General Mills Threats Graphics PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates

Agenda For Building Security Awareness Among Workforce To Minimize Cybersecurity Threats Template PDF
Find a pre designed and impeccable Agenda For Building Security Awareness Among Workforce To Minimize Cybersecurity Threats Template PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
Building Security Awareness Among Workforce To Minimize Cybersecurity Threats Table Of Contents Download PDF
Boost your pitch with our creative Building Security Awareness Among Workforce To Minimize Cybersecurity Threats Table Of Contents Download PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Current Trends Enhancing Performance Of Secure Web Gateway Web Threat Protection System
This slide outlines the recent developments for Secure Web Gateway. The purpose of this slide is to briefly explain the top current SWG trends. These include cloud based SWG, advanced threat protection, user behavior analytics, Secure Access Service Edge, etc. Slidegeeks is here to make your presentations a breeze with Current Trends Enhancing Performance Of Secure Web Gateway Web Threat Protection System With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide outlines the recent developments for Secure Web Gateway. The purpose of this slide is to briefly explain the top current SWG trends. These include cloud based SWG, advanced threat protection, user behavior analytics, Secure Access Service Edge, etc.
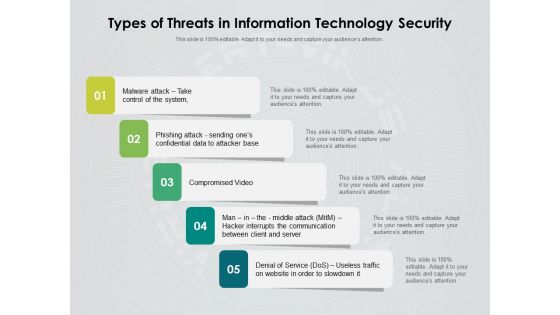
Types Of Threats In Information Technology Security Ppt PowerPoint Presentation Inspiration Rules PDF
Persuade your audience using this types of threats in information technology security ppt powerpoint presentation inspiration rules pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including malware attack take control of the system, phishing attack sending ones confidential data to attacker base, compromised video, man in the middle attack hacker interrupts the communication between client and server, denial of service dos, useless traffic on website in order to slowdown it. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
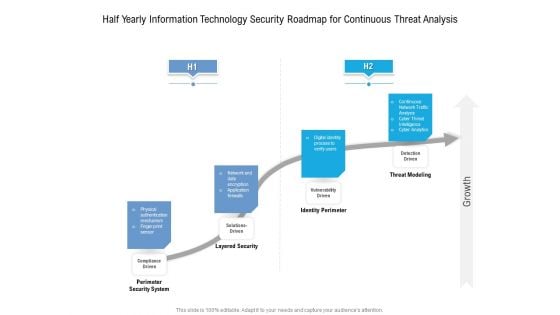
Half Yearly Information Technology Security Roadmap For Continuous Threat Analysis Rules
Presenting the half yearly information technology security roadmap for continuous threat analysis rules. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
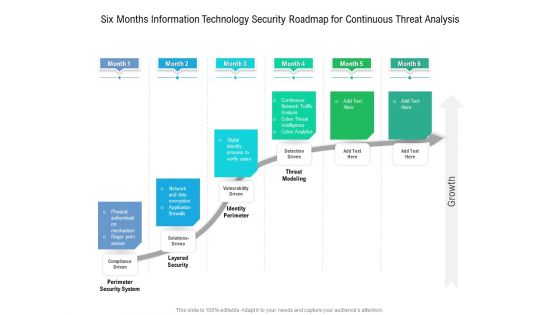
Six Months Information Technology Security Roadmap For Continuous Threat Analysis Microsoft
Presenting the six months information technology security roadmap for continuous threat analysis microsoft. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
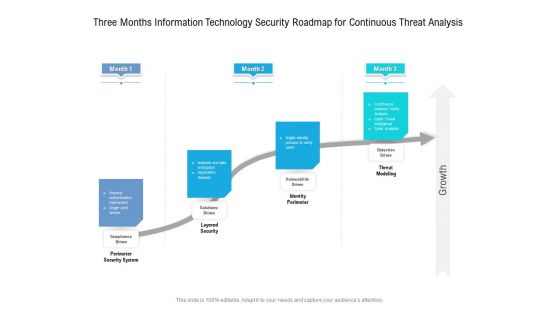
Three Months Information Technology Security Roadmap For Continuous Threat Analysis Professional
Presenting the three months information technology security roadmap for continuous threat analysis professional. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
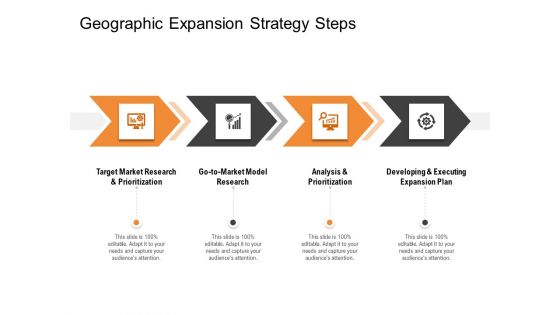
Opportunities And Threats For Penetrating In New Market Segments Geographic Expansion Strategy Steps Introduction PDF
This is a opportunities and threats for penetrating in new market segments geographic expansion strategy steps introduction pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like target market research and prioritization, go to market model research, analysis and prioritization, developing and executing expansion plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
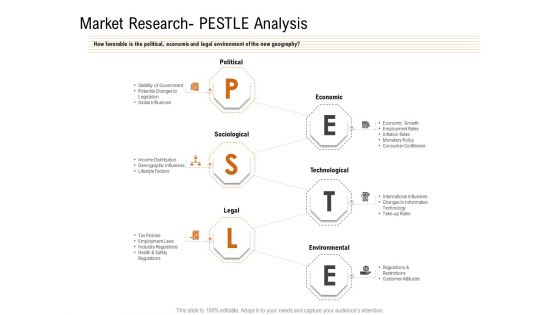
Opportunities And Threats For Penetrating In New Market Segments Market Research PESTLE Analysis Download PDF
How favorable is the political, economic and legal environment of the new geography. This is a opportunities and threats for penetrating in new market segments market research pestle analysis download pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like political, economic, sociological, technological, legal. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
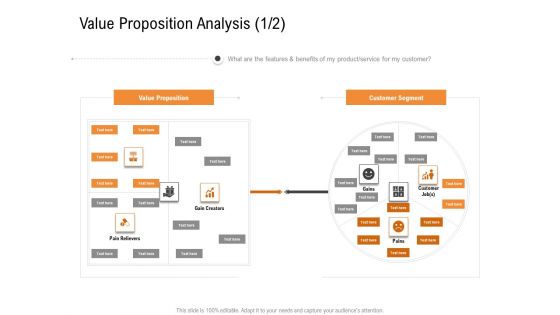
Opportunities And Threats For Penetrating In New Market Segments Value Proposition Analysis Customer Sample PDF
What are the features and benefits of my product or service for my customer. This is a opportunities and threats for penetrating in new market segments value proposition analysis customer sample pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like value proposition, customer segment. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Security Threats Shared Vulnerabilities Cloud Computing Security IT Ppt Slides Picture PDF
This slide describes how organizations and providers share vulnerabilities of a system, so each party must take precautions to protect data. Presenting cloud security threats shared vulnerabilities cloud computing security it ppt slides picture pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like organizations, cloud service, responsibility, cloud data security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

How To Intensify Project Threats Participants Roles And Responsibilities For Issue Template PDF
This slide provides the glimpse about the roles and responsibilities for participants involved in issue and escalation process such as project staff members, issue manager, project manager, project director and executive steering committee. Presenting how to intensify project threats participants roles and responsibilities for issue template pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like project staff members, issue manager, project manager, project director, executive steering committee. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
How To Intensify Project Threats Issue And Escalation Process Flow Chart Icons PDF
This slide provides the glimpse about the issue and escalation process flowchart which covers various steps involved in this process. Presenting how to intensify project threats issue and escalation process flow chart icons pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like analysis, validation and prioritization, tracking and reporting, escalation, resolution and closure. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
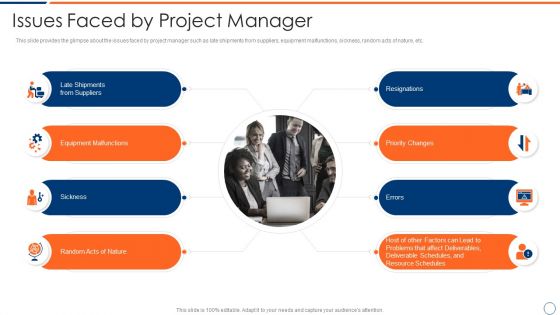
How To Intensify Project Threats Issues Faced By Project Manager Elements PDF
This slide provides the glimpse about the issues faced by project manager such as late shipments from suppliers, equipment malfunctions, sickness, random acts of nature, etc. This is a how to intensify project threats issues faced by project manager elements pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like priority changes, sickness, random acts of nature, equipment malfunctions, resignations. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

How To Intensify Project Threats Project Management Challenges And Solutions Guidelines PDF
This slide provides the glimpse about the challenges faced during project management such as unclear goals, inadequate communication, misestimating expenses along with the solutions. This is a how to intensify project threats project management challenges and solutions guidelines pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like challenges, solutions. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
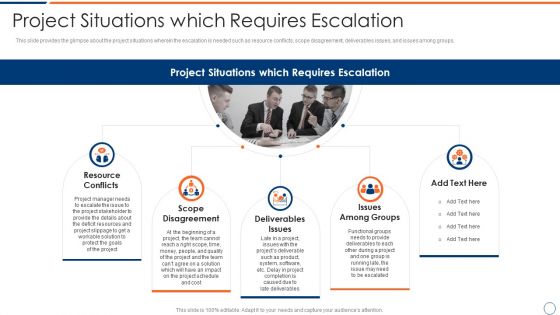
How To Intensify Project Threats Project Situations Which Requires Escalation Summary PDF
This slide provides the glimpse about the project situations wherein the escalation is needed such as resource conflicts, scope disagreement, deliverables issues, and issues among groups. Presenting how to intensify project threats project situations which requires escalation summary pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like resource conflicts, scope disagreement, deliverables issues, issues among groups. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

How To Intensify Project Threats Why It Is Difficult To Escalate Mockup PDF
This slide provides the glimpse about the reasons why it is difficult to escalate the issues such as clash creator, fear of backlash, avoiding escalation against experienced members, and deceived perception. This is a how to intensify project threats why it is difficult to escalate mockup pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like clash creator, fear of backlash, avoiding escalation against experienced members, deceived perception. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
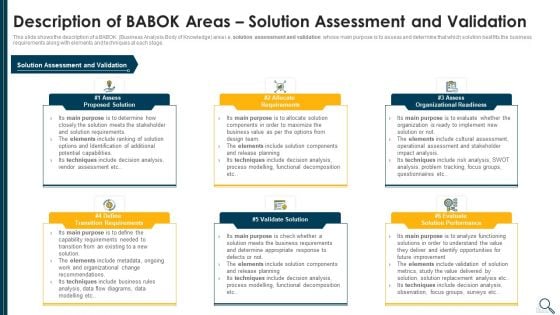
Solution Evaluation Criteria Assessment And Threat Impact Matrix Description Of Babok Slides PDF
This slide shows the description of a BABOK Business Analysis Body of Knowledge area i.e. solution assessment and validation whose main purpose is to assess and determine that which solution best fits the business requirements along with elements and techniques at each stage. Presenting solution evaluation criteria assessment and threat impact matrix description of babok slides pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like requirements, organizational readiness, validate solution, potential. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
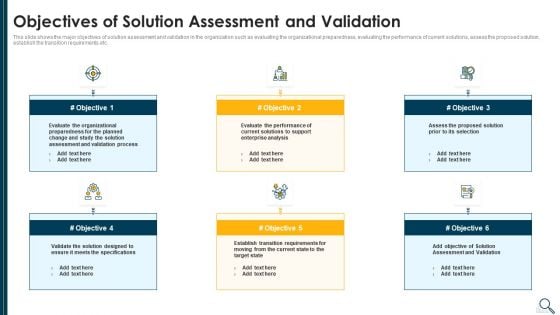
Solution Evaluation Criteria Assessment And Threat Impact Matrix Objectives Of Solution Assessment Rules PDF
This slide shows the major objectives of solution assessment and validation in the organization such as evaluating the organizational preparedness, evaluating the performance of current solutions, assess the proposed solution, establish the transition requirements etc. This is a solution evaluation criteria assessment and threat impact matrix objectives of solution assessment rules pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like organizational, process, enterprise analysis, performance, evaluate. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
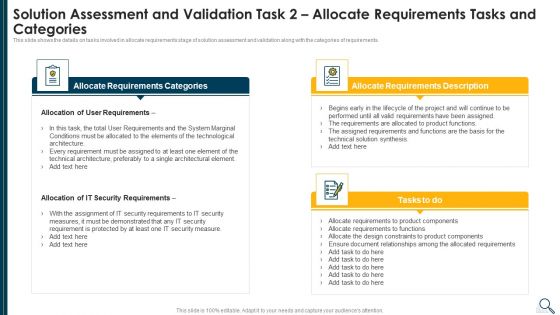
Solution Evaluation Criteria Assessment And Threat Impact Matrix Solution Assessment And Validation Task Ideas PDF
This slide shows the solution assessment and validation model or framework which helps to assess and determine that which solution best fits the business requirements along with the model inputs and outputs. Deliver and pitch your topic in the best possible manner with this solution evaluation criteria assessment and threat impact matrix solution assessment and validation task ideas pdf. Use them to share invaluable insights on solution assessment and validation model of the company and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
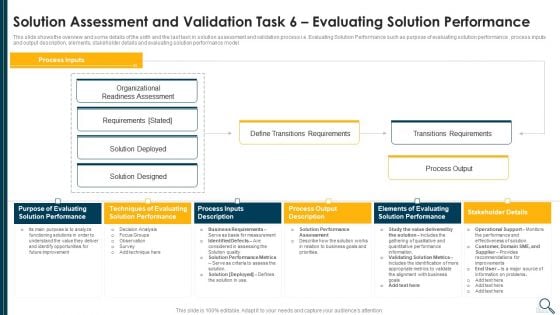
Solution Evaluation Criteria Assessment And Threat Impact Matrix Solution Assessment And Validation Information PDF
This slide shows the overview and some details of the sixth and the last task in solution assessment and validation process i.e. Evaluating Solution Performance such as purpose of evaluating solution performance , process inputs and output description, elements, stakeholder details and evaluating solution performance model. Deliver an awe inspiring pitch with this creative solution evaluation criteria assessment and threat impact matrix solution assessment and validation information pdf bundle. Topics like evaluating, performance, organizational, process output can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Solution Evaluation Criteria Assessment And Threat Impact Matrix Assess Organizational Readiness Icons PDF
This slide explains the various elements of force field analysis framework such as proposed change, pushing forces, forces resisting change etc. along with the benefits of force field analysis tool. This is a solution evaluation criteria assessment and threat impact matrix assess organizational readiness icons pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like reduce issues, execution. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
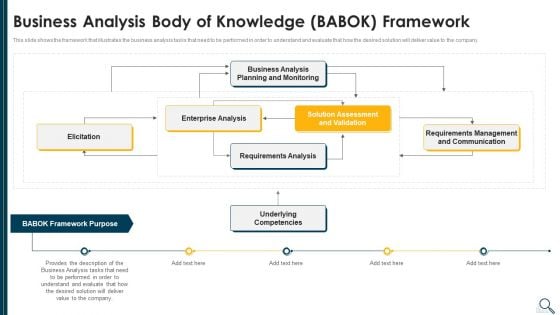
Solution Evaluation Criteria Assessment And Threat Impact Matrix Business Analysis Body Introduction PDF
This slide shows the framework that illustrates the business analysis tasks that need to be performed in order to understand and evaluate that how the desired solution will deliver value to the company. Deliver an awe inspiring pitch with this creative solution evaluation criteria assessment and threat impact matrix business analysis body introduction pdf bundle. Topics like enterprise analysis, requirements analysis, communication, requirements management, business analysis can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Solution Evaluation Criteria Assessment And Threat Impact Matrix Importance Of Solution Assessment Clipart PDF
This slide shows the importance of solution assessment and validation process with details such as assessment details, customer needs, validation details, product component and product requirement details, alternative solutions etc. Deliver and pitch your topic in the best possible manner with this solution evaluation criteria assessment and threat impact matrix importance of solution assessment clipart pdf. Use them to share invaluable insights on requirements development, product integration, customer, product components and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Executing Advance Data Analytics At Workspace Contingency Plan For Threat Handling Slides PDF
This slide covers details regarding the network optimization capabilities in terms of advanced caching capabilities, TCP layer optimization, global balancing of load, etc. This is a executing advance data analytics at workspace contingency plan for threat handling slides pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like caching capabilities, routing optimization, layer optimization, distributed. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Estimating Total Cost Of Ownership Of SIEM Real Time Assessment Of Security Threats Infographics PDF
This slide covers the cost breakdown of SIEM solution based on initial expenses, recurring expenses and amount saved by the client if they choose our company. Deliver and pitch your topic in the best possible manner with this estimating total cost of ownership of siem real time assessment of security threats infographics pdf. Use them to share invaluable insights on ongoing expenses, cost breakdown, siem solution and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Real Time Assessment Of Security Threats What Our Clients Say About Us Portrait PDF
This slide covers the client testimonials and what our customers have to say about our company and its services to understand the companys market reputation. This is a real time assessment of security threats what our clients say about us portrait pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like what our clients say about us. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
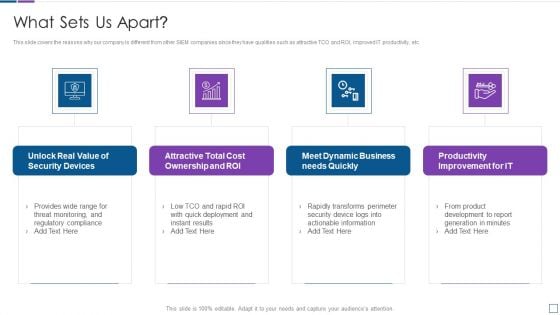
Real Time Assessment Of Security Threats What Sets Us Apart Microsoft PDF
This slide covers the reasons why our company is different from other SIEM companies since they have qualities such as attractive TCO and ROI, improved IT productivity, etc. Presenting real time assessment of security threats what sets us apart microsoft pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like security devices, cost ownership and roi, dynamic business, productivity improvement. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
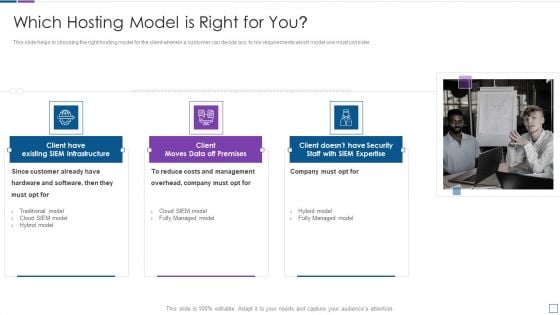
Real Time Assessment Of Security Threats Which Hosting Model Is Right For You Clipart PDF
This slide helps in choosing the right hosting model for the client wherein a customer can decide acc. to his requirements which model one must consider. This is a real time assessment of security threats which hosting model is right for you clipart pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like costs and management, company, hardware and software. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
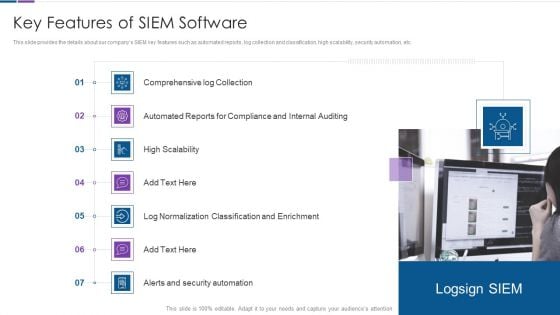
Real Time Assessment Of Security Threats Key Features Of SIEM Software Inspiration PDF
This slide provides the details about our companys SIEM key features such as automated reports, log collection and classification, high scalability, security automation, etc. Presenting real time assessment of security threats key features of siem software inspiration pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like compliance and internal auditing, high scalability, classification and enrichment, security automation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Real Time Assessment Of Security Threats Need For SIEM Software In Your Company Template PDF
This slide covers the need for the SIEM software which focuses on detecting incidents, compliance regulations, and incident management. Presenting real time assessment of security threats need for siem software in your company template pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like detecting incidents, compliance with regulations, efficient incident management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
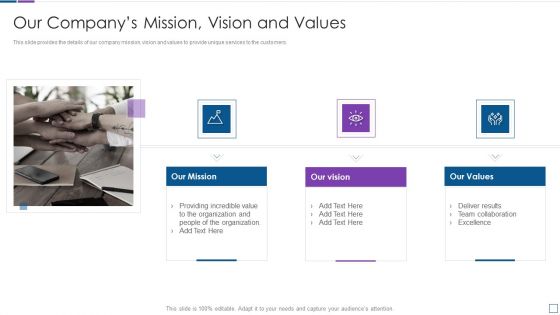
Real Time Assessment Of Security Threats Our Companys Mission Vision And Values Rules PDF
This slide provides the details of our company mission, vision and values to provide unique services to the customers. Presenting real time assessment of security threats our companys mission vision and values rules pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like our mission, our vision, our values. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
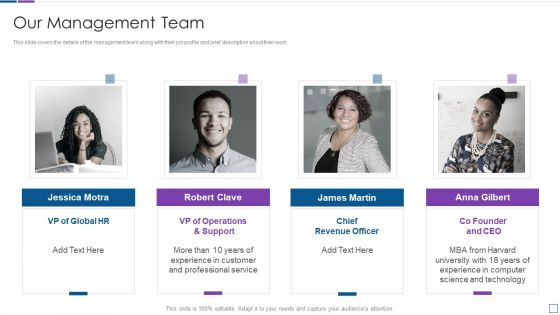
Real Time Assessment Of Security Threats Our Management Team Graphics PDF
This slide covers the details of the management team along with their job profile and brief description about their work. This is a real time assessment of security threats our management team graphics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like our management team. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
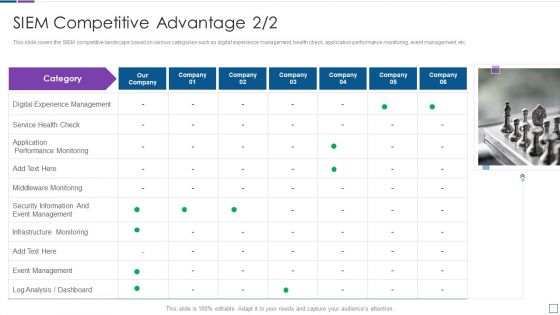
Real Time Assessment Of Security Threats SIEM Competitive Advantage Service Structure PDF
This slide covers the SIEM competitive landscape based on various categories such as digital experience management, health check, application performance monitoring, event management, etc. Presenting real time assessment of security threats siem competitive advantage service structure pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like digital experience management, service health check, application performance monitoring. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
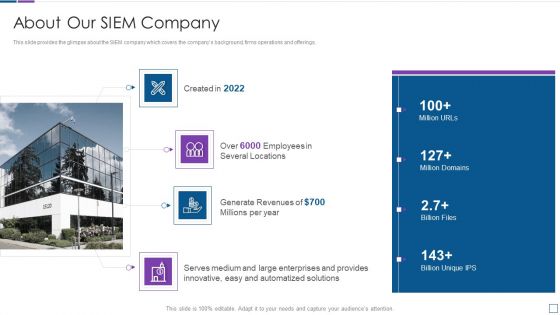
Real Time Assessment Of Security Threats About Our SIEM Company Structure PDF
This slide provides the glimpse about the SIEM company which covers the companys background, firms operations and offerings. This is a real time assessment of security threats about our siem company structure pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like about our siem company. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
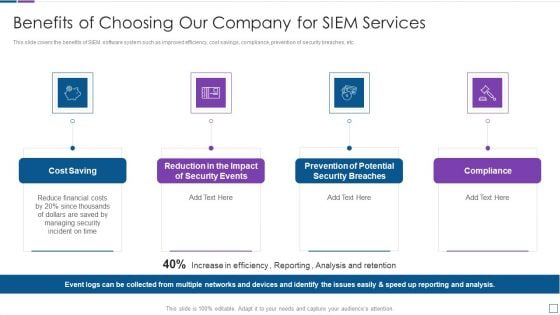
Real Time Assessment Of Security Threats Benefits Of Choosing Our Company For SIEM Services Introduction PDF
This slide covers the benefits of SIEM software system such as improved efficiency, cost savings, compliance, prevention of security breaches, etc. This is a real time assessment of security threats benefits of choosing our company for siem services introduction pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cost saving, security events, compliance. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
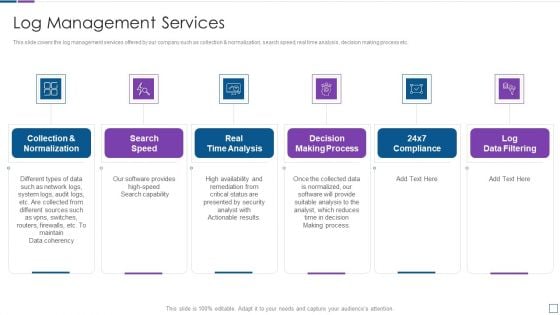
Real Time Assessment Of Security Threats Log Management Services Information PDF
This slide covers the log management services offered by our company such as collection and normalization, search speed, real time analysis, decision making process etc. Presenting real time assessment of security threats log management services information pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like collection and normalization, real time analysis, decision making process, log data filtering. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.


 Continue with Email
Continue with Email

 Home
Home


































