Risks And Solution
Strategies To Tackle Operational Risk In Banking Institutions Circular Diagram Pictures PDF
Presenting strategies to tackle in banking institutions need for operational risk management framework portrait pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like circular diagram. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Strategies To Tackle Operational Risk In Banking Institutions Post It Notes Inspiration PDF
Presenting strategies to tackle operational risk in banking institutions post it notes inspiration pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like post it notes. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
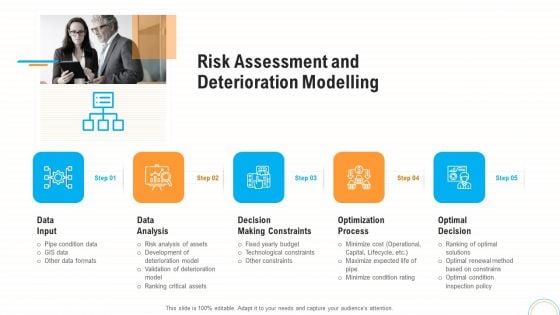
Fiscal And Operational Assessment Risk Assessment And Deterioration Modelling Demonstration PDF
Presenting fiscal and operational assessment risk assessment and deterioration modelling demonstration pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like data analysis, decision making constraints, optimization process. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Case Study 4 Improving Patient Security And Reducing Risk Of Violence Graphics PDF
Presenting case study 4 improving patient security and reducing risk of violence graphics pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like building management, security management, power management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Operational Risk Management Structure In Financial Companies Table Of Contents Pictures PDF
Presenting operational risk management structure in financial companies table of contents pictures pdf to provide visual cues and insights. Share and navigate important information on eleven stages that need your due attention. This template can be used to pitch topics like management, performance, training, budget, cost. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Risk Analysis Strategies For Real Estate Construction Project 30 60 90 Days Plan Background PDF
Presenting risk analysis strategies for real estate construction project 30 60 90 days plan background pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like 30 60 90 days plan. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Risk Analysis Strategies For Real Estate Construction Project Project Conflict Management Strategies Slides PDF
This slides covers project team conflict management strategies to reduce overall conflicts occurring during project. Presenting risk analysis strategies for real estate construction project project conflict management strategies slides pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like post it notes. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Risk Assessment Methods Real Estate Development Project Project Conflict Management Strategies Graphics PDF
This slides covers project team conflict management strategies to reduce overall conflicts occurring during project. Presenting risk assessment methods real estate development project project conflict management strategies graphics pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like project conflict management strategies. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
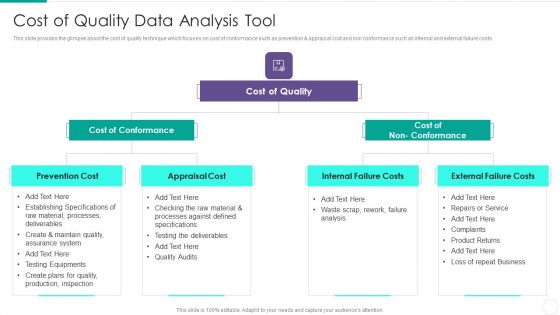
Quantitative Risk Assessment Cost Of Quality Data Analysis Tool Graphics PDF
Presenting Quantitative Risk Assessment Cost Of Quality Data Analysis Tool Graphics PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Cost Of Conformance, Cost Of Quality, Internal Failure Costs, External Failure Costs, Appraisal Cost. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
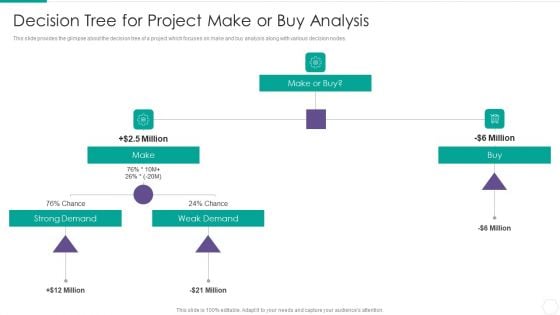
Quantitative Risk Assessment Decision Tree For Project Make Or Buy Analysis Designs PDF
Presenting Quantitative Risk Assessment Decision Tree For Project Make Or Buy Analysis Designs PDF to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like Decision Tree For Project Make Or Buy Analysis. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
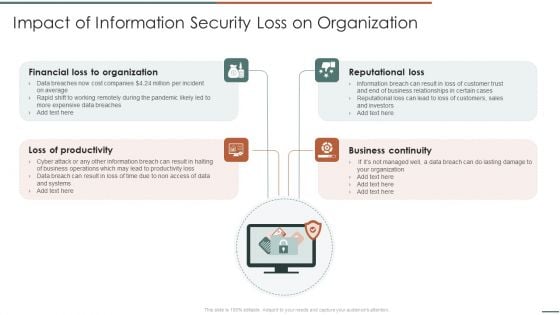
Information Security Risk Evaluation Impact Of Information Security Loss On Organization Structure PDF
Presenting Information Security Risk Evaluation Impact Of Information Security Loss On Organization Structure PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Financial Organization, Loss Of Productivity, Reputational Loss. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Table Of Contents For Information Security Risk Evaluation And Administration Plan Formats PDF
Presenting Table Of Contents For Information Security Risk Evaluation And Administration Plan Formats PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Scenario Assessment, Security Capabilities, Overview Of Information. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Table Of Contents Information Security Risk Evaluation And Administration Plan Slide Slides PDF
Presenting Table Of Contents Information Security Risk Evaluation And Administration Plan Slide Slides PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Process Formulate, Management Plan, Mitigating Information. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Table Of Contents For IT Spend Management Priorities By Cios Risk Template PDF
Presenting Table Of Contents For IT Spend Management Priorities By Cios Risk Template PDF to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like Cloud Management To Optimize, Containerization Technologies, Transformation Measures. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
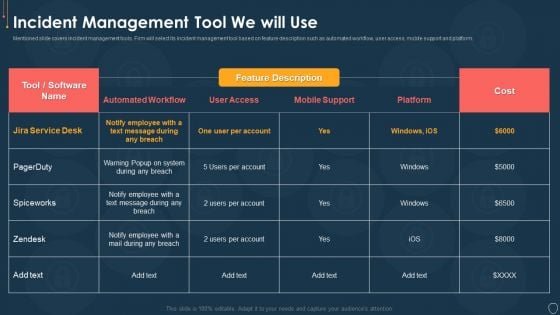
Cyber Security Risk Management Plan Incident Management Tool We Will Use Mockup PDF
Mentioned slide covers incident management tools. Firm will select its incident management tool based on feature description such as automated workflow, user access, mobile support and platform. Deliver an awe inspiring pitch with this creative cyber security risk management plan incident management tool we will use mockup pdf bundle. Topics like incident management tool we will use can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Effective IT Risk Management Process Incident Management Tool We Will Use Professional PDF
Mentioned slide covers incident management tools. Firm will select its incident management tool based on feature description such as automated workflow, user access, mobile support and platform. Deliver an awe inspiring pitch with this creative effective it risk management process incident management tool we will use professional pdf bundle. Topics like incident management tool we will use can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
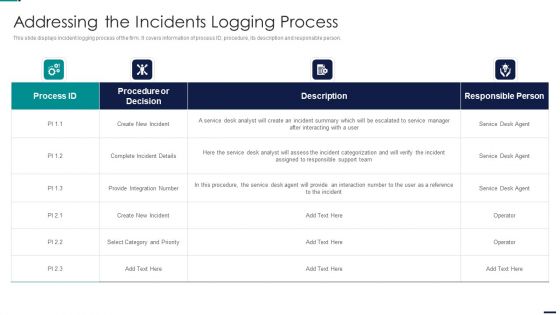
Risk Management Model For Data Security Addressing The Incidents Logging Process Professional PDF
This slide displays incident logging process of the firm. It covers information of process ID, procedure, its description and responsible person. Deliver an awe inspiring pitch with this creative Risk Management Model For Data Security Addressing The Incidents Logging Process Professional PDF bundle. Topics like Procedure or Decision, Create New Incident, Integration Number can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
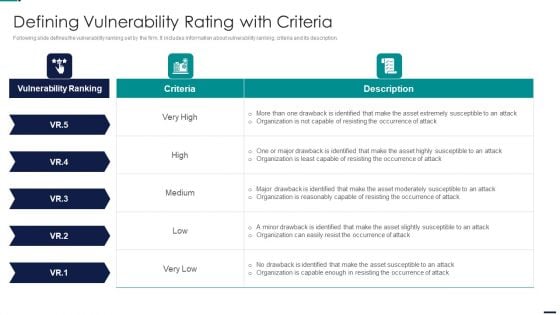
Risk Management Model For Data Security Defining Vulnerability Rating With Criteria Mockup PDF
Following slide defines the vulnerability ranking set by the firm. It includes information about vulnerability ranking, criteria and its description. Deliver and pitch your topic in the best possible manner with this Risk Management Model For Data Security Defining Vulnerability Rating With Criteria Mockup PDF. Use them to share invaluable insights on Vulnerability Ranking, High, LOW, MEDIUM, Attack Organization, Occurrence Attack and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
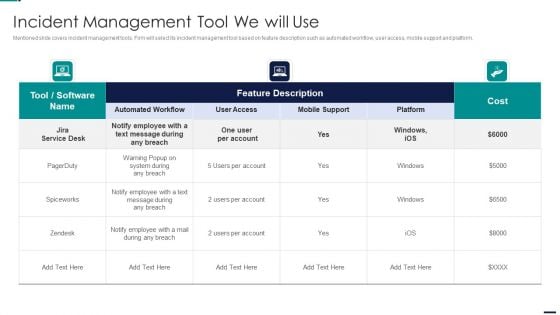
Risk Management Model For Data Security Incident Management Tool We Will Use Diagrams PDF
Mentioned slide covers incident management tools. Firm will select its incident management tool based on feature description such as automated workflow, user access, mobile support and platform. Deliver an awe inspiring pitch with this creative Risk Management Model For Data Security Incident Management Tool We Will Use Diagrams PDFbundle. Topics like Cost, Employee, Mobile Support, Automated Workflow, User Access can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Risk Management Model For Data Security Setting Scenario For Security Control Designs PDF
Following slide shows the current security management capabilities of the firm. It covers details about core functions, its description, key enablers, required and actual standard ratings. Deliver an awe inspiring pitch with this creative Risk Management Model For Data Security Setting Scenario For Security Control Designs PDF bundle. Topics like Identify, Protect, Detect, Response, Recovery can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cybersecurity Risk Administration Plan Present Security Management Capabilities Of The Firm Rules PDF
Following slide shows the current security management capabilities of the firm. It covers details about core functions, its description, key enablers, required and actual standard ratings.Deliver and pitch your topic in the best possible manner with this Cybersecurity Risk Administration Plan Present Security Management Capabilities Of The Firm Rules PDF Use them to share invaluable insights on Assessing Information Security, Safeguarding Valuable, Vulnerability Intelligence and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
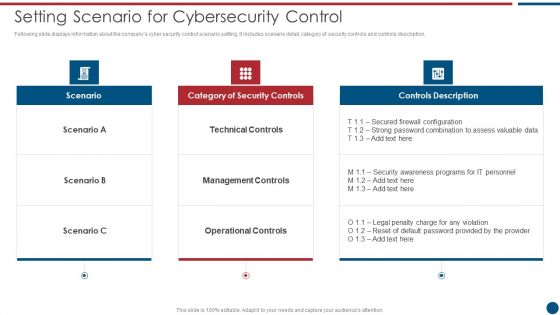
Risk Based Procedures To IT Security Setting Scenario For Cybersecurity Control Professional PDF
Following slide displays information about the companys cyber security control scenario setting. It includes scenario detail, category of security controls and controls description. Deliver an awe inspiring pitch with this creative Risk Based Procedures To IT Security Setting Scenario For Cybersecurity Control Professional PDF bundle. Topics like Technical Controls, Management Controls, Operational Controls can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
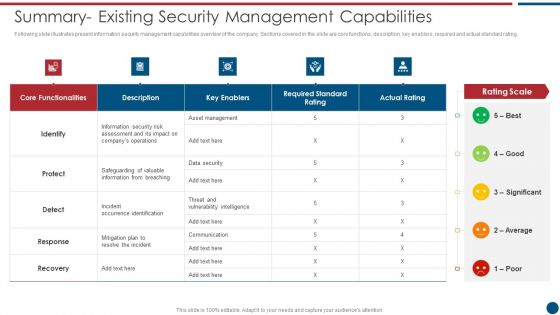
Risk Based Procedures To IT Security Summary Existing Security Management Capabilities Topics PDF
Following slide illustrates present information security management capabilities overview of the company. Sections covered in the slide are core functions, description, key enablers, required and actual standard rating. Deliver an awe inspiring pitch with this creative Risk Based Procedures To IT Security Summary Existing Security Management Capabilities Topics PDF bundle. Topics like Asset Management, Key Enablers, Communication Plan can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
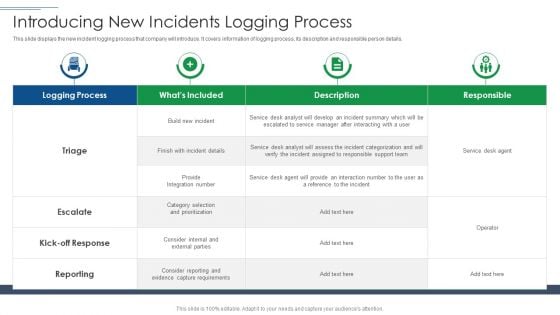
IT Security Risk Management Approach Introduction Introducing New Incidents Logging Process Slides PDF
This slide displays the new incident logging process that company will introduce. It covers information of logging process, its description and responsible person details. Deliver and pitch your topic in the best possible manner with this IT Security Risk Management Approach Introduction Introducing New Incidents Logging Process Slides PDF. Use them to share invaluable insights on Logging Process, Capture Requirements, Service Desk Agent and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
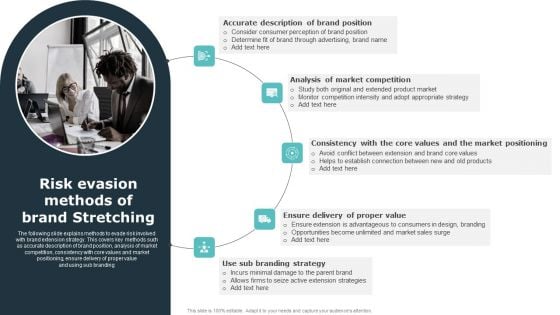
Risk Evasion Methods Of Brand Stretching Ppt PowerPoint Presentation File Display PDF
The following slide explains methods to evade risk involved with brand extension strategy. This covers key methods such as accurate description of brand position, analysis of market competition, consistency with core values and market positioning, ensure delivery of proper value and using sub branding . This modern and well-arranged Risk Evasion Methods Of Brand Stretching Ppt PowerPoint Presentation File Display PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
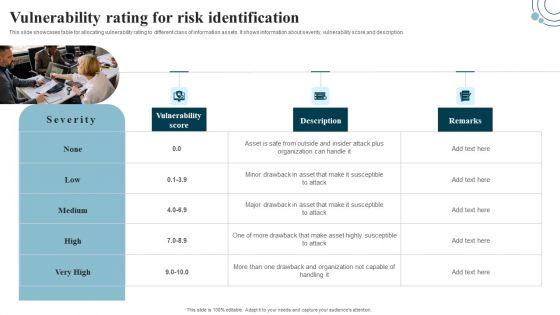
Developing IT Security Strategy Vulnerability Rating For Risk Identification Topics PDF
This slide showcases table for allocating vulnerability rating to different class of information assets. It shows information about severity, vulnerability score and description. Are you searching for a Developing IT Security Strategy Vulnerability Rating For Risk Identification Topics PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Developing IT Security Strategy Vulnerability Rating For Risk Identification Topics PDF from Slidegeeks today.
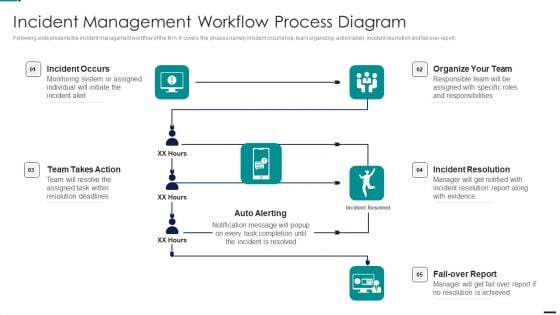
Risk Management Model For Data Security Incident Management Workflow Process Diagram Topics PDF
Following slide presents the incident management workflow of the firm. It covers five phases namely incident occurrence, team organizing, action taken, incident resolution and fail over report. Presenting Risk Management Model For Data Security Incident Management Workflow Process Diagram Topics PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Incident Occurs, Organize Team, Incident Resolution, Fail Over Report, Auto Alerting, Team Takes Action. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cybersecurity Risk Administration Plan Setting Scenario For Security Control Topics PDF
Following slide displays security control scenario setting. It includes scenario detail, category of security controls and controls description.Presenting Cybersecurity Risk Administration Plan Setting Scenario For Security Control Topics PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Category Of Security Controls, Controls Description, Secured Firewall Configuration In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Performing Sales Risk Analysis To Increase Revenue Ppt PowerPoint Presentation Complete Deck With Slides
In business, sometimes the end result can be completely different from what stakeholders visualized. This Performing Sales Risk Analysis To Increase Revenue Ppt PowerPoint Presentation Complete Deck With Slides details the study of enterprise and problem solving as a fundamental area of getting the desired outcomes. Stakeholders need to be convinced of how to proceed and change through this wonderful PPT presentation. The idea guiding this complete deck of fifty one presentation slides is to ensure that dealing with change and unexpected results becomes easy. The area of focus for this change can be customized with the 100 percent editable and customizable nature of each of the slides in our presentation. Download now.
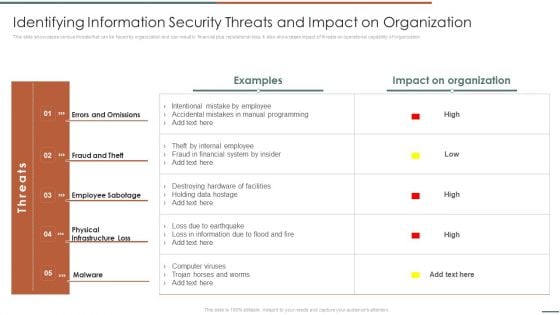
Information Security Risk Evaluation Identifying Information Security Threats And Impact On Organization Sample PDF
This slide showcases various threats that can be faced by organization and can result in financial plus reputational loss. It also showcases impact of threats on operational capability of organization.Deliver an awe inspiring pitch with this creative Information Security Risk Evaluation Identifying Information Security Threats And Impact On Organization Sample PDF bundle. Topics like Errors And Omissions, Fraud And Theft, Employee Sabotage can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Risk Assessment And Mitigation Plan Strategies To Overcome Labor Shortages Ppt Portfolio Shapes PDF
This slide shows key strategies to overcome labor shortages. It covers expanding recruitment drive, labor safety improvement, process automation and other financial incentives to enhance labor retention. Presenting risk assessment and mitigation plan strategies to overcome labor shortages ppt portfolio shapes pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like construction material, prioritize labor safety, offer financial incentives, expand recruitment drive, automate processes, increase connectivity, better retention. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Effective IT Risk Management Process Setting Scenario For Security Control Sample PDF
Following slide displays security control scenario setting. It includes scenario detail, category of security controls and controls description. Presenting effective it risk management process setting scenario for security control sample pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like technical controls, management controls, operational controls. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Risk Based Procedures To IT Security Communication Plan For Cyber Breaches Structure PDF
Mentioned slide portrays communication plan that company will use for effectively managing cyber breaches. Sections covered here are what to communicate, description, delivery method, frequency and responsible. Presenting Risk Based Procedures To IT Security Communication Plan For Cyber Breaches Structure PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Sprint Report, Delivery Method, Frequency Responsible. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Risk Management For Organization Essential Assets Addressing Various Ways To Handle Icons PDF
This slide provides details regarding various ways to handle insider cyber threats in terms of active remediation implementation, deactivating orphaned user accounts, etc. Presenting risk management for organization essential assets addressing various ways to handle icons pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like develop strict access management policies, deactivate orphaned user accounts, implement active remediation, investigate remote access policies. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
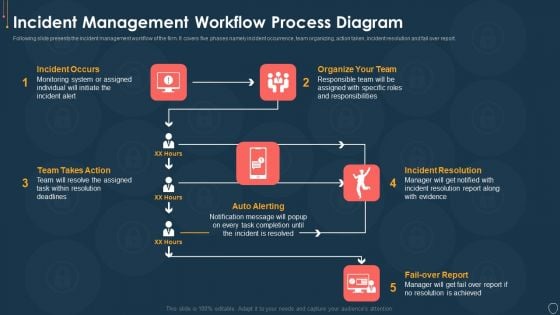
Cyber Security Risk Management Plan Incident Management Workflow Process Diagram Infographics PDF
Following slide presents the incident management workflow of the firm. It covers five phases namely incident occurrence, team organizing, action taken, incident resolution and fail over report. Presenting cyber security risk management plan incident management workflow process diagram infographics pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like fail over report, incident resolution, organize your team, incident occurs, team takes action. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
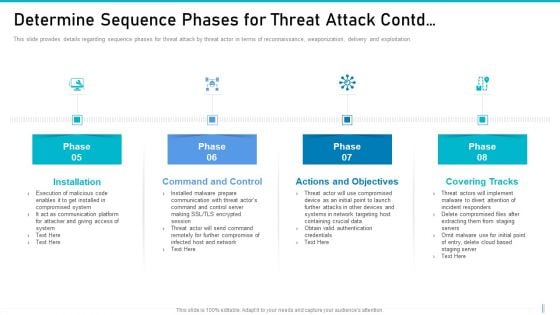
Risk Management For Organization Essential Assets Determine Sequence Phases For Threat Professional PDF
This slide provides details regarding sequence phases for threat attack by threat actor in terms of reconnaissance, weaponization, delivery and exploitation. Presenting risk management for organization essential assets determine sequence phases for threat professional pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like installation, command and control, actions and objectives, covering tracks. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Corporate Security And Risk Management Addressing Internal And External Sources Of Threat Data Gathering Template PDF
This slide provides details regarding internal and external sources of threat data gathering with threat intelligence category. Presenting corporate security and risk management addressing internal and external sources of threat data gathering template pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like targeted intelligence, malware intelligence, reputation intelligence . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Corporate Security And Risk Management Addressing Ways To Handling Financial Threats Ideas PDF
This slide provides details regarding handling financial threats by safeguarding financial stability and protecting the firm from costly effects that financial threats can have. Presenting corporate security and risk management addressing ways to handling financial threats ideas pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like abundant cash requirement, key financial statements, overheads analysis, currency hedging, preparing aged debtors trial balance on monthly basis. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
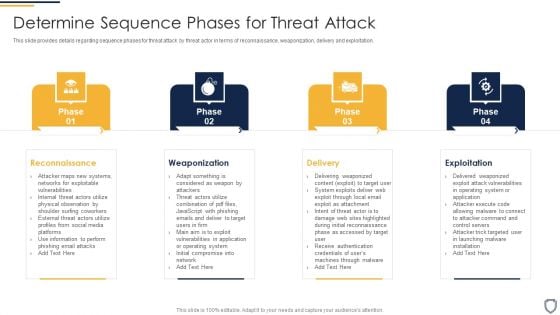
Corporate Security And Risk Management Determine Sequence Phases For Threat Attack Ideas PDF
This slide provides details regarding sequence phases for threat attack by threat actor in terms of reconnaissance, weaponization, delivery and exploitation. Presenting corporate security and risk management determine sequence phases for threat attack ideas pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like reconnaissance, weaponization, delivery, exploitation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Corporate Security And Risk Management Various Types Of Workplace Violence And Threats Designs PDF
This slide provides details regarding various types of workplace violence threats created by people in terms of stalking, physical assault, harassment or intimidation, etc. Presenting corporate security and risk management various types of workplace violence and threats designs pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like threats or threatening behavior, physical assault, property damage, stalking, harassment or intimidation . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
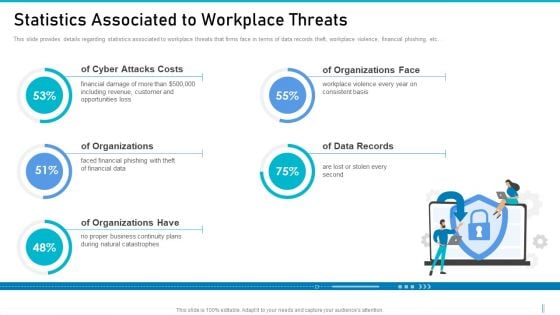
Risk Management For Organization Essential Assets Statistics Associated To Workplace Threats Structure PDF
This slide provides details regarding statistics associated to workplace threats that firms face in terms of data records theft, workplace violence, financial phishing, etc. Presenting risk management for organization essential assets statistics associated to workplace threats structure pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like organizations, cyber attacks costs, data records. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
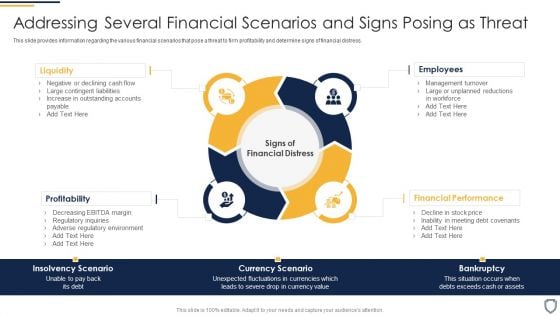
Corporate Security And Risk Management Addressing Several Financial Scenarios And Signs Posing As Threat Pictures PDF
This slide provides information regarding the various financial scenarios that pose a threat to firm profitability and determine signs of financial distress. Presenting corporate security and risk management addressing several financial scenarios and signs posing as threat pictures pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like profitability, liquidity, employees, financial performance . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Corporate Security And Risk Management Addressing Various Ways To Handle Insider Cyber Threats Contd Guidelines PDF
This slide provides details regarding various ways to handle insider cyber threats in terms of active remediation implementation, deactivating orphaned user accounts, etc. Presenting corporate security and risk management addressing various ways to handle insider cyber threats contd guidelines pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like develop strict access management policies, deactivate orphaned user accounts, implement active remediation, investigate remote access policies. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
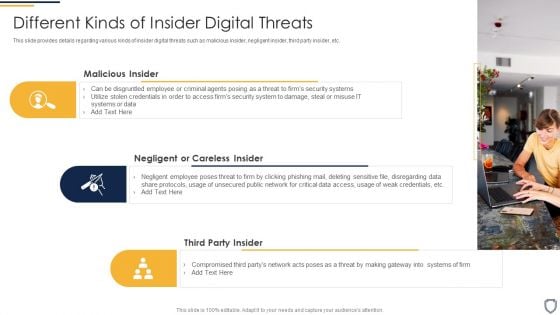
Corporate Security And Risk Management Different Kinds Of Insider Digital Threats Themes PDF
This slide provides details regarding various kinds of insider digital threats such as malicious insider, negligent insider, third party insider, etc. Presenting corporate security and risk management different kinds of insider digital threats themes pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like malicious insider, negligent or careless insider, third party insider . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Risk Management Model For Data Security Defining Categories Of Information Security Threats Graphics PDF
This slide shows the categorization of information security threats. Categories covered are human error, natural disaster, software attacks and environmental control failures. Presenting Risk Management Model For Data Security Defining Categories Of Information Security Threats Graphics PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Human Error, Natural Disaster, Deliberate Software Attacks, Environmental Control Failures. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
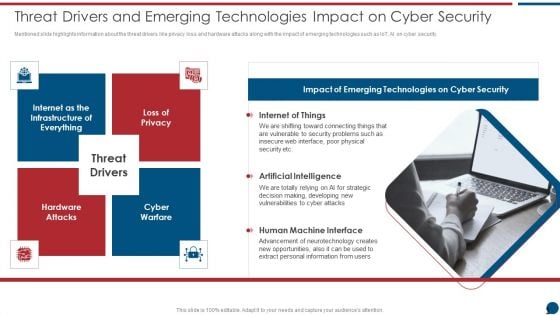
Risk Based Procedures To IT Security Threat Drivers And Emerging Technologies Impact On Information PDF
Mentioned slide highlights information about the threat drivers like privacy loss and hardware attacks along with the impact of emerging technologies such as IoT, AI on cyber security. Presenting Risk Based Procedures To IT Security Threat Drivers And Emerging Technologies Impact On Information PDF to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like Internet Of Things, Artificial Intelligence, Human Machine. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
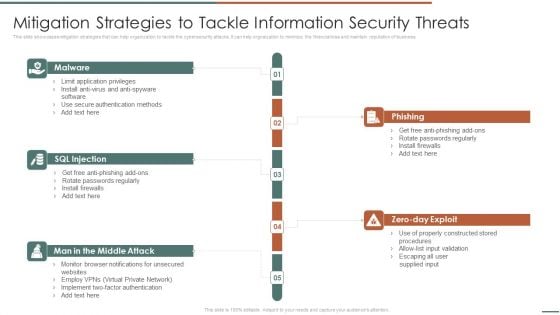
Information Security Risk Evaluation Mitigation Strategies To Tackle Information Security Threats Designs PDF
This slide showcases mitigation strategies that can help organization to tackle the cybersecurity attacks. It can help orgnaization to minimize the financial loss and maintain reputation of business.Presenting Information Security Risk Evaluation Mitigation Strategies To Tackle Information Security Threats Designs PDF to provide visual cues and insights. Share and navigate important information on fivestages that need your due attention. This template can be used to pitch topics like Phishing, Rotate Passwords, Install Firewalls. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
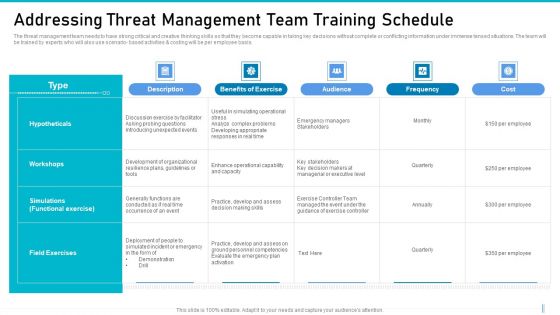
Risk Management For Organization Essential Assets Addressing Threat Management Team Portrait PDF
The threat management team needs to have strong critical and creative thinking skills so that they become capable in taking key decisions without complete or conflicting information under immense tensed situations. The team will be trained by experts who will also use scenario- based activities and costing will be per employee basis. Deliver an awe inspiring pitch with this creative risk management for organization essential assets addressing threat management team portrait pdf bundle. Topics like description, benefits of exercise, audience, frequency, cost can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
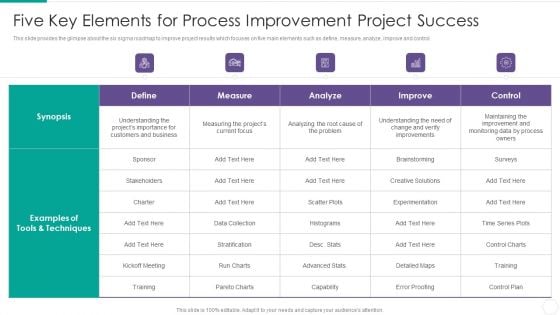
Quantitative Risk Assessment Five Key Elements For Process Improvement Project Success Summary PDF
This slide provides the glimpse about the six sigma roadmap to improve project results which focuses on five main elements such as define, measure, analyze, improve and control. Deliver and pitch your topic in the best possible manner with this Quantitative Risk Assessment Five Key Elements For Process Improvement Project Success Summary PDF. Use them to share invaluable insights on Customers, Business, Techniques, Analyze, Capability and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Quantitative Risk Assessment Steps Required In Planning Project Focus Group Structure PDF
This slide provides the glimpse about the phases required in focus group planning project which covers planning focus group study, conducting focus group discussion and analyzing and reporting results. Deliver and pitch your topic in the best possible manner with this Quantitative Risk Assessment Steps Required In Planning Project Focus Group Structure PDF. Use them to share invaluable insights on Steps Required In Planning Project Focus Group and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
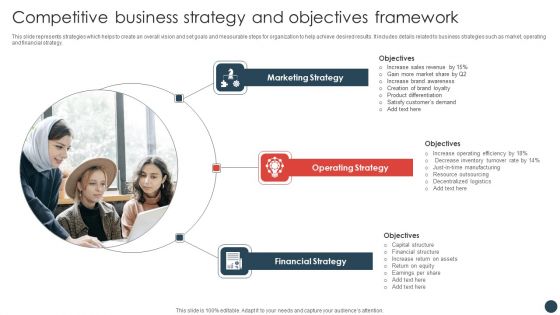
Strategic Risk Management Plan Competitive Business Strategy And Objectives Framework Formats PDF
This slide represents strategies which helps to create an overall vision and set goals and measurable steps for organization to help achieve desired results. It includes details related to business strategies such as market, operating and financial strategy.your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Strategic Risk Management Plan Competitive Business Strategy And Objectives Framework Formats PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.

Performing Sales Risk Analysis Procedure Ppt PowerPoint Presentation Complete Deck With Slides
Our Performing Sales Risk Analysis Procedure Ppt PowerPoint Presentation Complete Deck With Slides replete with visuals, whether of date or creative business images, will help you visualize important performance metrics. It contains business information around all the hot-button topics of today that an engaged audience will like to listen to, This PPT template is easy to edit and fully customizable. So download this stunning design right away and reap the harvests of well-presented business knowledge to an appreciative business. Over time, an increase is your proportion of wins per sales effort is the only result that will make you get amazing brand recall for business and your own self on a personal level.
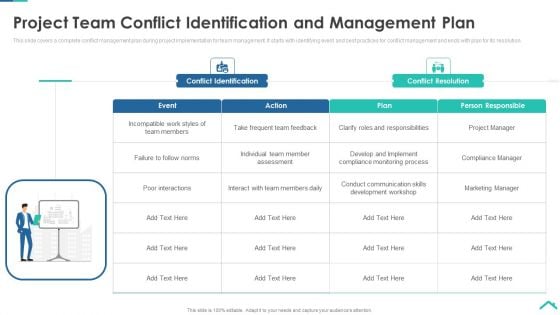
Risk Analysis Strategies For Real Estate Construction Project Project Team Conflict Identification Microsoft PDF
This slide covers a complete conflict management plan during project implementation for team management. It starts with identifying event and best practices for conflict management and ends with plan for its resolution. Deliver and pitch your topic in the best possible manner with this risk analysis strategies for real estate construction project project team conflict identification microsoft pdf. Use them to share invaluable insights on conflict identification, conflict resolution and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
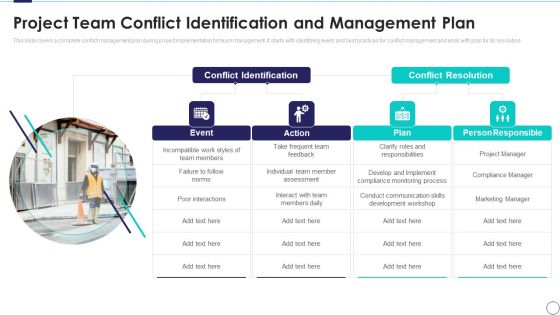
Risk Assessment And Mitigation Plan Project Team Conflict Identification And Management Plan Elements PDF
This slide covers a complete conflict management plan during project implementation for team management. It starts with identifying event and best practices for conflict management and ends with plan for its resolution. Deliver and pitch your topic in the best possible manner with this risk assessment and mitigation plan project team conflict identification and management plan elements pdf. Use them to share invaluable insights on conflict identification, conflict resolution, poor interactions, individual team member assessment and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Risk Evaluation And Mitigation Project Team Conflict Identification And Management Plan Designs PDF
This slide covers a complete conflict management plan during project implementation for team management. It starts with identifying event and best practices for conflict management and ends with plan for its resolution. Deliver an awe inspiring pitch with this creative Risk Evaluation And Mitigation Project Team Conflict Identification And Management Plan Designs PDF bundle. Topics like Conflict Identification, Conflict Resolution, Person Responsible can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
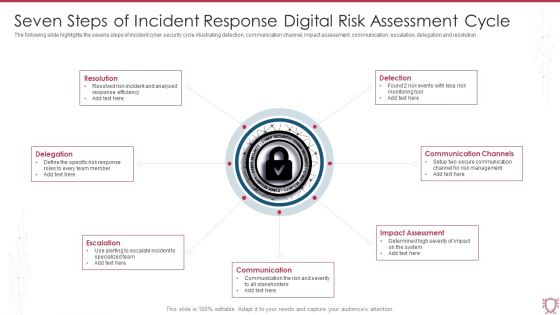
Seven Steps Of Incident Response Digital Risk Assessment Cycle Ppt Portfolio Introduction PDF
The following slide highlights the sevens steps of incident cyber security cycle illustrating detection, communication channel, impact assessment, communication, escalation, delegation and resolution, Persuade your audience using this Seven Steps Of Incident Response Digital Risk Assessment Cycle Ppt Portfolio Introduction PDF. This PPT design covers seven stages, thus making it a great tool to use. It also caters to a variety of topics including Resolution, Detection, Communication Channels, Impact Assessment. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cyber Security Risk Management Plan Present Security Management Capabilities Of The Firm Template PDF
Following slide shows the current security management capabilities of the firm. It covers details about core functions, its description, key enablers, required and actual standard ratings. Deliver and pitch your topic in the best possible manner with this cyber security risk management plan present security management capabilities of the firm template pdf. Use them to share invaluable insights on actual standard rating, required standard rating, key enablers, description, core functions and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
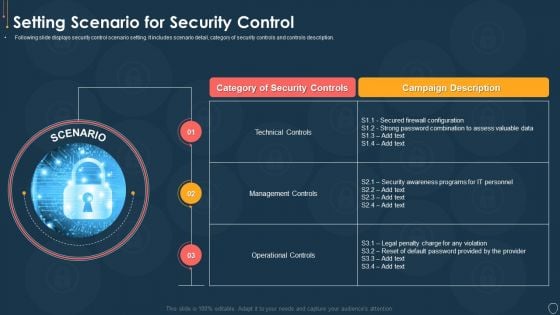
Cyber Security Risk Management Plan Setting Scenario For Security Control Microsoft PDF
Following slide displays security control scenario setting. It includes scenario detail, category of security controls and controls description. This is a cyber security risk management plan setting scenario for security control microsoft pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like category of security controls, campaign description, technical controls, management controls, operational controls. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
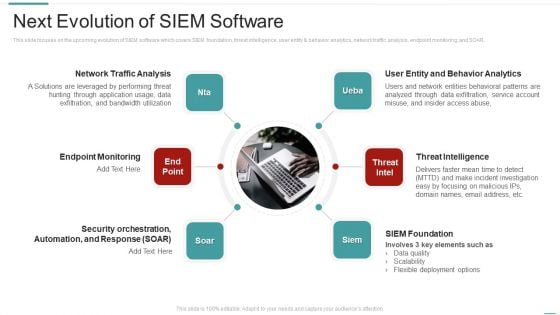
Risk Recognition Automation Next Evolution Of Siem Software Ppt Ideas Objects PDF
This slide focuses on the upcoming evolution of SIEM software which covers SIEM foundation, threat intelligence, user entity and behavior analytics, network traffic analysis, endpoint monitoring, and SOAR. Presenting risk recognition automation next evolution of siem software ppt ideas objects pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like endpoint monitoring, network traffic analysis, threat intelligence, siem foundation, user entity and behavior analytics. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
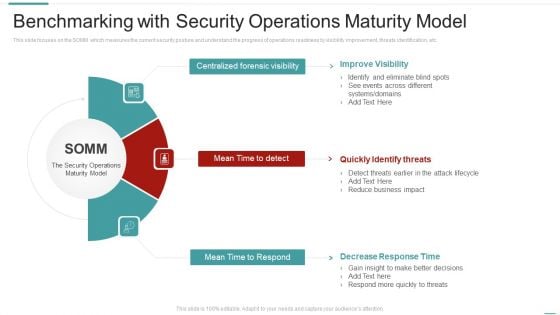
Risk Recognition Automation Benchmarking With Security Operations Maturity Model Ppt Pictures Infographic Template PDF
This slide focuses on the SOMM which measures the current security posture and understand the progress of operations readiness by visibility improvement, threats identification, etc. Presenting risk recognition automation benchmarking with security operations maturity model ppt pictures infographic template pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like improve visibility, quickly identify threats, decrease response time. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.


 Continue with Email
Continue with Email

 Home
Home


































