Roles And Responsibility Slides

Key Channels Car Manufacturing Company Business Model BMC SS V
This slide showcases the various points through which the company connects with its customers. It includes channels such as dealership networks, online, mobile, and social media. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Key Channels Car Manufacturing Company Business Model BMC SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide showcases the various points through which the company connects with its customers. It includes channels such as dealership networks, online, mobile, and social media.

Key Partnerships Payment Gateway Company Business Model BMC SS V
This slide covers the important assets required to operate a business successfully. It includes technological infrastructure, brand reputation, partnership and alliances, human capital and data analytics. Present like a pro with Key Partnerships Payment Gateway Company Business Model BMC SS V. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide covers the important assets required to operate a business successfully. It includes technological infrastructure, brand reputation, partnership and alliances, human capital and data analytics.
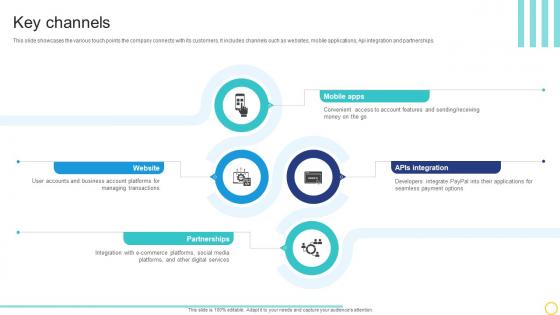
Key Channels Online Transaction Facilitator Business Model BMC SS V
This slide showcases the various touch points the company connects with its customers. It includes channels such as websites, mobile applications, Api integration and partnerships. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Key Channels Online Transaction Facilitator Business Model BMC SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide showcases the various touch points the company connects with its customers. It includes channels such as websites, mobile applications, Api integration and partnerships.

Key Channels Software Development Company Business Model BMC SS V
This slide showcases company primary channels for delivering its products and services such a Google search and Ads, YouTube, maps, Google workspace and play, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Key Channels Software Development Company Business Model BMC SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide showcases company primary channels for delivering its products and services such a Google search and Ads, YouTube, maps, Google workspace and play, etc.
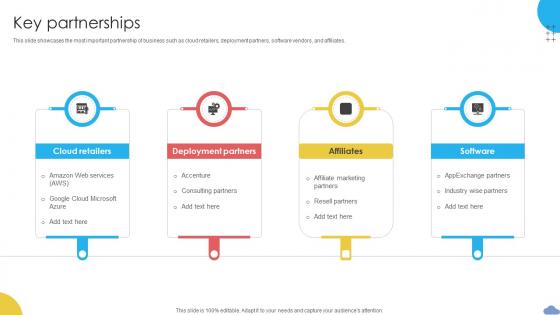
Key Partnerships Cloud Based CRM Business Model BMC SS V
This slide showcases the most important partnership of business such as cloud retailers, deployment partners, software vendors, and affiliates. Present like a pro with Key Partnerships Cloud Based CRM Business Model BMC SS V. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide showcases the most important partnership of business such as cloud retailers, deployment partners, software vendors, and affiliates.
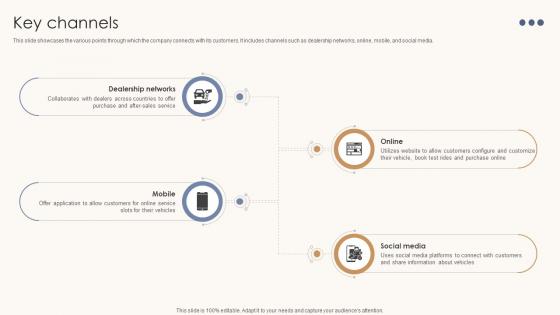
Key Channels Automotive Assembly Business Model BMC SS V
This slide showcases the various points through which the company connects with its customers. It includes channels such as dealership networks, online, mobile, and social media. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Key Channels Automotive Assembly Business Model BMC SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide showcases the various points through which the company connects with its customers. It includes channels such as dealership networks, online, mobile, and social media.
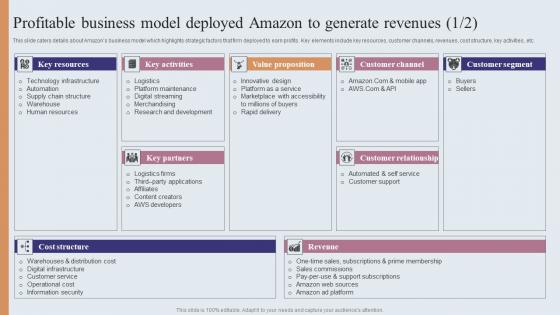
Profitable Business Model Deployed Amazon To Generate Amazons Journey For Becoming Elements PDF
This slide caters details about Amazons business model which highlights strategic factors that firm deployed to earn profits. Key elements include key resources, customer channels, revenues, cost structure, key activities, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Profitable Business Model Deployed Amazon To Generate Amazons Journey For Becoming Elements PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide caters details about Amazons business model which highlights strategic factors that firm deployed to earn profits. Key elements include key resources, customer channels, revenues, cost structure, key activities, etc.
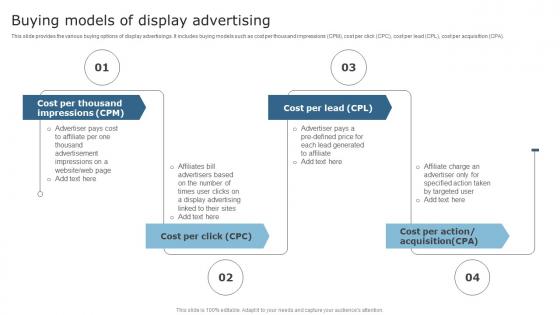
Techniques To Optimize Business Performance Buying Models Of Display Advertising Sample Pdf
This slide provides the various buying options of display advertisings. It includes buying models such as cost per thousand impressions CPM, cost per click CPC, cost per lead CPL, cost per acquisition CPA. Present like a pro with Techniques To Optimize Business Performance Buying Models Of Display Advertising Sample Pdf Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide provides the various buying options of display advertisings. It includes buying models such as cost per thousand impressions CPM, cost per click CPC, cost per lead CPL, cost per acquisition CPA.

Key Partnerships Cloud Computing Services Business Model PPT Sample BMC SS V
This slide showcases the essential relationship a company needs to function effectively in all areas of the business model. It includes partnerships with cloud providers, technology vendors, consulting firms, industry associations. Present like a pro with Key Partnerships Cloud Computing Services Business Model PPT Sample. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide showcases the essential relationship a company needs to function effectively in all areas of the business model. It includes partnerships with cloud providers, technology vendors, consulting firms, industry associations.

Checklist For Affiliate Revenue Model Internet Based Trade Structure Ppt Example
This slide shows detailed checklist for affiliate revenue model to generate income online. It include points such as choosing suitable partner, setting commission structure, etc. Present like a pro with Checklist For Affiliate Revenue Model Internet Based Trade Structure Ppt Example. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide shows detailed checklist for affiliate revenue model to generate income online. It include points such as choosing suitable partner, setting commission structure, etc.
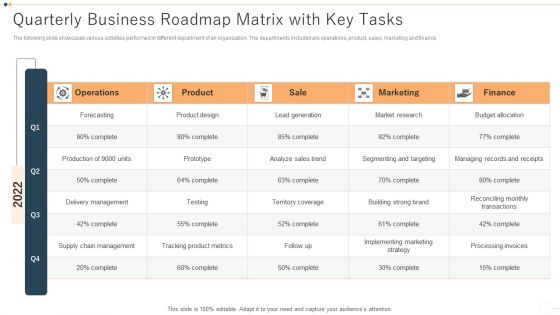
Quarterly Business Roadmap Matrix With Key Tasks Introduction PDF
The following slide showcases various activities performed in different department of an organization. The departments included are operations, product, sales, marketing and finance. Pitch your topic with ease and precision using this Quarterly Business Roadmap Matrix With Key Tasks Introduction PDF. This layout presents information on Sale, Product, Marketing. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
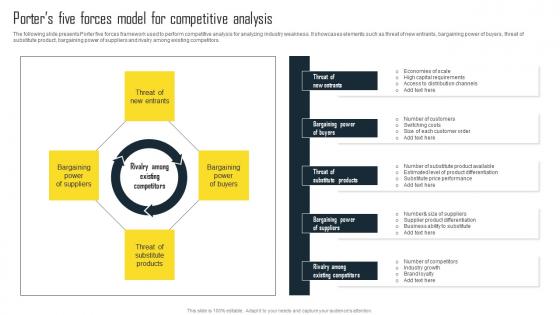
Porters Five Forces Model For Competitive Efficient Plan For Conducting Competitor Infographics Pdf
The following slide presents Porter five forces framework used to perform competitive analysis for analyzing industry weakness. It showcases elements such as threat of new entrants, bargaining power of buyers, threat of substitute product, bargaining power of suppliers and rivalry among existing competitors. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Porters Five Forces Model For Competitive Efficient Plan For Conducting Competitor Infographics Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. The following slide presents Porter five forces framework used to perform competitive analysis for analyzing industry weakness. It showcases elements such as threat of new entrants, bargaining power of buyers, threat of substitute product, bargaining power of suppliers and rivalry among existing competitors.
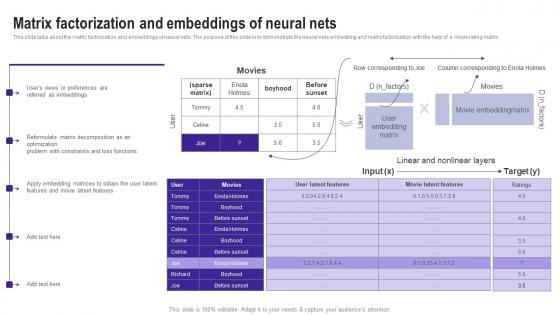
Matrix Factorization And Embeddings Of Neural Nets Use Cases Of Filtering Methods Structure Pdf
This slide talks about the matrix factorization and embeddings of neural nets. The purpose of this slide is to demonstrate the neural nets embedding and matrix factorization with the help of a movie rating matrix. Create an editable Matrix Factorization And Embeddings Of Neural Nets Use Cases Of Filtering Methods Structure Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Matrix Factorization And Embeddings Of Neural Nets Use Cases Of Filtering Methods Structure Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide talks about the matrix factorization and embeddings of neural nets. The purpose of this slide is to demonstrate the neural nets embedding and matrix factorization with the help of a movie rating matrix.
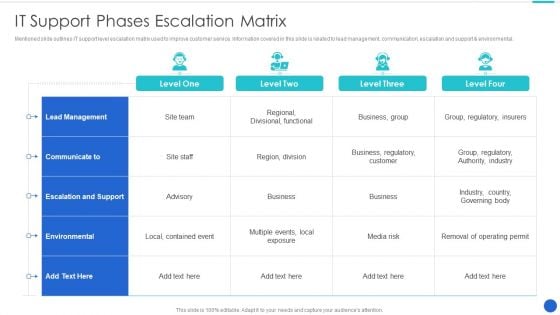
IT Support Phases Escalation Matrix Topics PDF
Mentioned slide outlines IT support level escalation matrix used to improve customer service. Information covered in this slide is related to lead management, communication, escalation and support environmental.Pitch your topic with ease and precision using this IT Support Phases Escalation Matrix Topics PDF This layout presents information on Escalation Support, Communicate, Environmental It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Corporate Communication Strategy Public Relations In Corporate Communication Introduction PDF
This template covers a comparison between business communication and public relations. It also depicts corporate communication is a process through which companies roll out information to internal and external stakeholders. On the other hand, PR is a corporate communication task that works with workers, investors, the authorities, the media, and the general public. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Corporate Communication Strategy Public Relations In Corporate Communication Introduction PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Corporate Communication Strategy Public Relations In Corporate Communication Introduction PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today
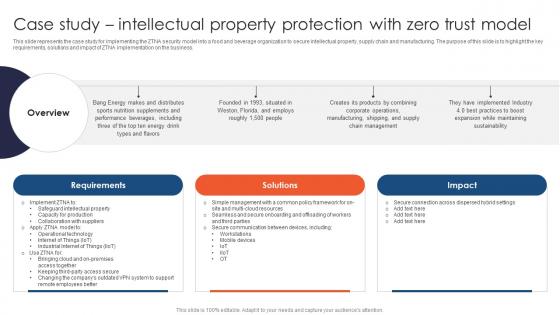
Zero Trust Network Access Case Study Intellectual Property Protection With Zero Trust Model
This slide represents the case study for implementing the ZTNA security model into a food and beverage organization to secure intellectual property, supply chain and manufacturing. The purpose of this slide is to highlight the key requirements, solutions and impact of ZTNA implementation on the business. Make sure to capture your audiences attention in your business displays with our gratis customizable Zero Trust Network Access Case Study Intellectual Property Protection With Zero Trust Model. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide represents the case study for implementing the ZTNA security model into a food and beverage organization to secure intellectual property, supply chain and manufacturing. The purpose of this slide is to highlight the key requirements, solutions and impact of ZTNA implementation on the business.
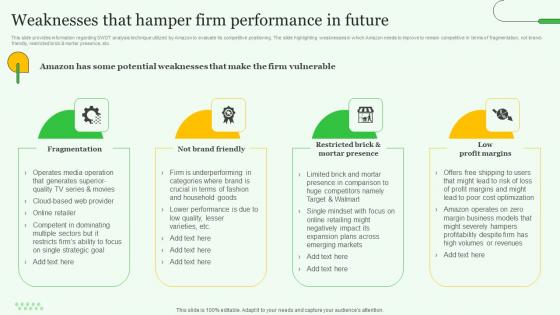
Weaknesses That Hamper Firm Exploring Amazons Global Business Model Growth Pictures Pdf
This slide provides information regarding SWOT analysis technique utilized by Amazon to evaluate its competitive positioning. The slide highlighting weaknesses in which Amazon needs to improve to remain competitive in terms of fragmentation, not brand friendly, restricted brick and mortar presence, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Weaknesses That Hamper Firm Exploring Amazons Global Business Model Growth Pictures Pdf. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide provides information regarding SWOT analysis technique utilized by Amazon to evaluate its competitive positioning. The slide highlighting weaknesses in which Amazon needs to improve to remain competitive in terms of fragmentation, not brand friendly, restricted brick and mortar presence, etc.
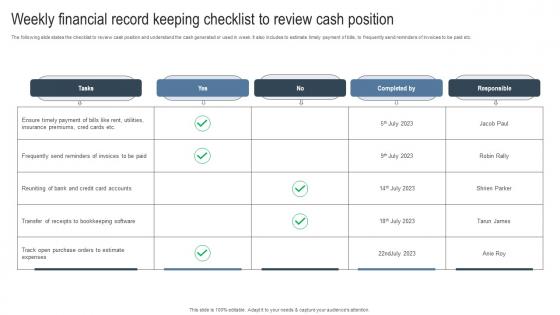
Weekly Financial Record Keeping Checklist To Review Cash Position Portrait Pdf
The following slide states the checklist to review cash position and understand the cash generated or used in week. It also includes to estimate timely payment of bills, to frequently send reminders of invoices to be paid etc. Pitch your topic with ease and precision using this Weekly Financial Record Keeping Checklist To Review Cash Position Portrait Pdf. This layout presents information on Tasks, Completed, Responsible. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. The following slide states the checklist to review cash position and understand the cash generated or used in week. It also includes to estimate timely payment of bills, to frequently send reminders of invoices to be paid etc.
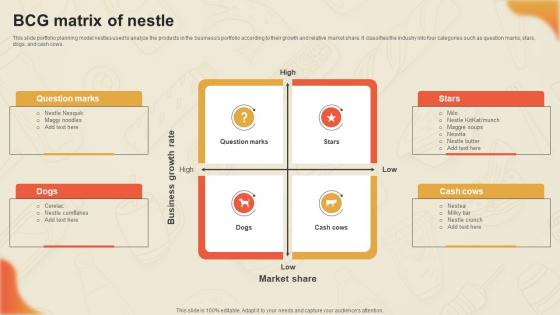
Decoding Nestles Marketing BCG Matrix Of Nestle Strategy SS V
This slide portfolio planning model nestles used to analyze the products in the businesss portfolio according to their growth and relative market share. It classifies the industry into four categories such as question marks, stars, dogs, and cash cows. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Decoding Nestles Marketing BCG Matrix Of Nestle Strategy SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide portfolio planning model nestles used to analyze the products in the businesss portfolio according to their growth and relative market share. It classifies the industry into four categories such as question marks, stars, dogs, and cash cows.

Database Modeling Relational Data Model Technique In DBMs Template Pdf
This slide shows the overview of relational data modeling technique which represents information in the form of tables. The purpose of this slide is to explain the different constraints of relational data modeling technique. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Database Modeling Relational Data Model Technique In DBMs Template Pdf was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Database Modeling Relational Data Model Technique In DBMs Template Pdf This slide shows the overview of relational data modeling technique which represents information in the form of tables. The purpose of this slide is to explain the different constraints of relational data modeling technique.
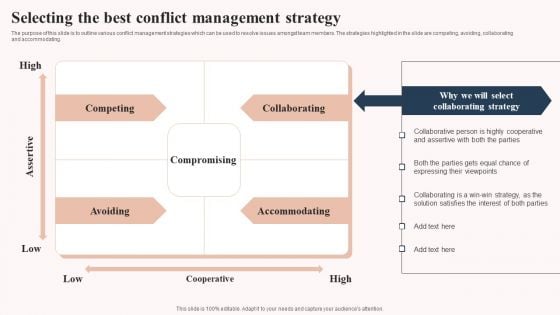
Workplace Conflict Resolution Technqiues Selecting The Best Conflict Inspiration PDF
The purpose of this slide is to outline various conflict management strategies which can be used to resolve issues amongst team members. The strategies highlighted in the slide are competing, avoiding, collaborating and accommodating. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Workplace Conflict Resolution Technqiues Selecting The Best Conflict Inspiration PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Zero Trust Model Working Of Zero Trust Network Access Model
This slide outlines the working of zero trust network access. The purpose of this slide is to demonstrate the workflow of ZTNA, including the principles shared by all ZTNA architectures. The principles include no use of MPLS, hiding the IP addresses, securing devices, IDP and SSO platform, and so on. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Zero Trust Model Working Of Zero Trust Network Access Model to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide outlines the working of zero trust network access. The purpose of this slide is to demonstrate the workflow of ZTNA, including the principles shared by all ZTNA architectures. The principles include no use of MPLS, hiding the IP addresses, securing devices, IDP and SSO platform, and so on.

Zero Trust Model Steps To Implement Zero Trust Network Access Model
This slide outlines the crucial steps to implement the zero trust network access model in an organization. The purpose of this slide is to highlight the key steps to perform to deploy the ZTNA model. The steps include identifying assets, defining protection surface, understanding the businesss security model, etc. Slidegeeks is here to make your presentations a breeze with Zero Trust Model Steps To Implement Zero Trust Network Access Model With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide outlines the crucial steps to implement the zero trust network access model in an organization. The purpose of this slide is to highlight the key steps to perform to deploy the ZTNA model. The steps include identifying assets, defining protection surface, understanding the businesss security model, etc.
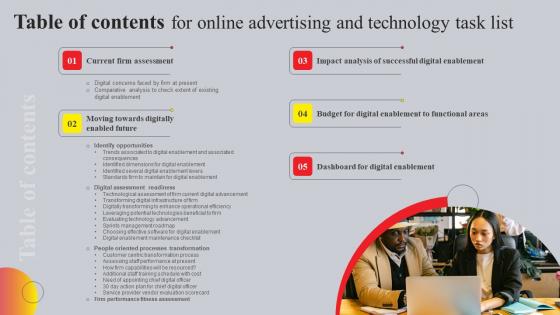
Table Of Contents For Online Advertising And Technology Task List Portrait Pdf
Are you searching for a Table Of Contents For Online Advertising And Technology Task List Portrait Pdf that is uncluttered, straightforward, and original It is easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, it is perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Table Of Contents For Online Advertising And Technology Task List Portrait Pdf from Slidegeeks today. Our Table Of Contents For Online Advertising And Technology Task List Portrait Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
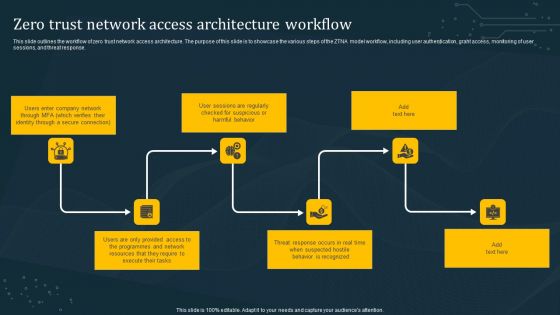
Zero Trust Network Access Architecture Workflow Microsoft PDF
This slide outlines the workflow of zero trust network access architecture. The purpose of this slide is to showcase the various steps of the ZTNA model workflow, including user authentication, grant access, monitoring of user sessions, and threat response. Slidegeeks has constructed Zero Trust Network Access Architecture Workflow Microsoft PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

Zero Trust Model Comparison Between Zero Trust Model SDP And VPN
This slide represents the comparison between the zero trust security model, software-defined perimeter, and virtual private network. The purpose of this slide is to showcase the difference as well as the relationship between three security technologies such as zero trust, SDP and VPN. Find highly impressive Zero Trust Model Comparison Between Zero Trust Model SDP And VPN on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Zero Trust Model Comparison Between Zero Trust Model SDP And VPN for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide represents the comparison between the zero trust security model, software-defined perimeter, and virtual private network. The purpose of this slide is to showcase the difference as well as the relationship between three security technologies such as zero trust, SDP and VPN.

Comprehensive Review Of Nestles BCG Matrix Of Nestle Strategy SS V
This slide portfolio planning model nestles used to analyze the products in the businesss portfolio according to their growth and relative market share. It classifies the industry into four categories such as question marks, stars, dogs, and cash cows. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Comprehensive Review Of Nestles BCG Matrix Of Nestle Strategy SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide portfolio planning model nestles used to analyze the products in the businesss portfolio according to their growth and relative market share. It classifies the industry into four categories such as question marks, stars, dogs, and cash cows.
Editable PowerPoint Template Straight Demonstration Of 6 Stages Business Graphic
We present our editable PowerPoint template straight Demonstration of 6 stages business Graphic.Use our Process and flows PowerPoint Templates because, are the symbols of human growth. Use our shapes PowerPoint Templates because, guaranteed to focus the minds of your team. Use our Signs PowerPoint Templates because, Amplify on your plans to have dedicated sub groups working on related but distinct tasks. Use our Business PowerPoint Templates because; heighten the anticipation of your audience with this slide listing. Use our Arrows PowerPoint Templates because, The Venn graphic comprising interlinking circles geometrically demonstrate how various functions operating independently, to a large extent, are essentially interdependant.Use these PowerPoint slides for presentations relating to Algorithm, arrow, arrow chart, block, block diagram, business, chart, connection, design, development, diagram, direction, element, flow, flow chart, flow diagram, flowchart, graph, linear, linear diagram, management, model, module, motion, process, process arrows, process chart, process diagram, process flow, program, section, segment, set, sign, solution, strategy, symbol, technology, vibrant, workflow, workflow chart, workflow diagram. The prominent colors used in the PowerPoint template are Pink, White, and Gray Our Editable PowerPoint Template Straight Demonstration Of 6 Stages Business Graphic make many a feat feasible. They ease out all difficulties.

Zero Trust Model Technologies Used In Zero Trust Network Access
This slide represents the techniques used in the zero-trust network access model. The purpose of this slide is to showcase the multiple technologies used in the ZTNA model, including their functions and the network protection they offer. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Zero Trust Model Technologies Used In Zero Trust Network Access. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Zero Trust Model Technologies Used In Zero Trust Network Access today and make your presentation stand out from the rest This slide represents the techniques used in the zero-trust network access model. The purpose of this slide is to showcase the multiple technologies used in the ZTNA model, including their functions and the network protection they offer.
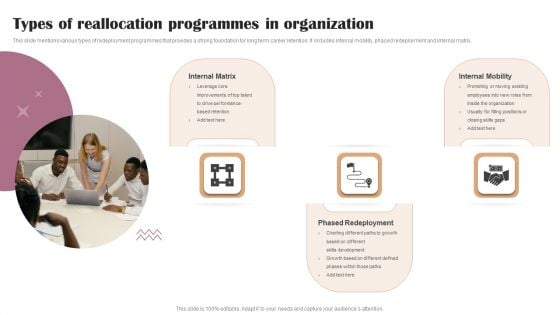
Types Of Reallocation Programmes In Organization Brochure PDF
This slide mentions various types of redeployment programmes that provides a strong foundation for long term career retention. It includes internal mobility, phased redeployment and internal matrix.
Ppt Theme Continous Way To Show 3 Practice PowerPoint Macro Steps Workflow 4 Image
We present our PPT Theme continuous way to show 3 practices PowerPoint macro steps workflow 4 Image. Use our Arrows PowerPoint Templates because, Many a core idea has various enveloping layers. Use our Symbol PowerPoint Templates because, Corporate Ladder:- The graphic is a symbol of growth and success. Use our Business PowerPoint Templates because, Present your views using our innovative slides and be assured of leaving a lasting impression. Use our Process and Flows PowerPoint Templates because, Will surely see the all making the grade. Use our Marketing PowerPoint Templates because; enlighten them with your brilliant understanding of mental health. Use these PowerPoint slides for presentations relating to Abstract, Algorithm, Arrow, Business, Chart, Color, Connection, Design, Development, Direction, Element, Flow, Graph, Linear, Management, Model, Organization, Plan, Process, Program, Section, Segment, Set, Sign, Solution, Strategy, Symbol, Technology. The prominent colors used in the PowerPoint template are Green, Gray, and Black Enter into a contract with our Ppt Theme Continous Way To Show 3 Practice PowerPoint Macro Steps Workflow 4 Image. Your signature thoughts will get approval.
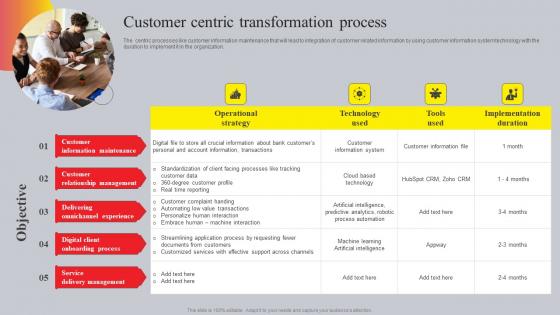
Online Advertising And Technology Task Customer Centric Transformation Process Diagrams Pdf
The centric processes like customer information maintenance that will lead to integration of customer related information by using customer information system technology with the duration to implement it in the organization. Present like a pro with Online Advertising And Technology Task Customer Centric Transformation Process Diagrams Pdf Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. The centric processes like customer information maintenance that will lead to integration of customer related information by using customer information system technology with the duration to implement it in the organization.

Chatgpt In Web Applications For Enhanced User Interactions Transformer Neural Network Architecture Of Chatgpt Sample PDF
This slide demonstrates the architecture diagram of ChatGPT. The purpose of this slide is to represent how ChatGPT uses transformer model to create cohesive responses. The main components self-attention layers, feed-forward layers, residual connections etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Chatgpt In Web Applications For Enhanced User Interactions Transformer Neural Network Architecture Of Chatgpt Sample PDF can be your best option for delivering a presentation. Represent everything in detail using Chatgpt In Web Applications For Enhanced User Interactions Transformer Neural Network Architecture Of Chatgpt Sample PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Zero Trust Model Timeline To Implement Zero Trust Network Access
This slide showcases the timeline for implementing the ZTNA security model. This slide highlights the various steps organizations will take while deploying the ZTNA system, forming a dedicated team, choosing zero-trust implementation on-ramp, assessing the environment and so on. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Zero Trust Model Timeline To Implement Zero Trust Network Access can be your best option for delivering a presentation. Represent everything in detail using Zero Trust Model Timeline To Implement Zero Trust Network Access and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide showcases the timeline for implementing the ZTNA security model. This slide highlights the various steps organizations will take while deploying the ZTNA system, forming a dedicated team, choosing zero-trust implementation on-ramp, assessing the environment and so on.

Smart Phone Launch Event Management Tasks Event Tasks And Activity Management Timeline Pictures PDF
This slide showcases event activity timeline. It includes strategies covered in pre, during and post event which are create budget plan, vendor booking, live polling, thank you emails, feedback survey, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Smart Phone Launch Event Management Tasks Event Tasks And Activity Management Timeline Pictures PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Zero Trust Model Key Characteristics Of Modern ZTNA Solution
This slide outlines the top features that a modern ZTNA model should include. This slide highlights the characteristics of modern ZTNA solutions, including data loss prevention, scalable performance, granular visibility and reporting, BYOD deployment options, advanced threat protection, and SASE offering. Welcome to our selection of the Zero Trust Model Key Characteristics Of Modern ZTNA Solution. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. This slide outlines the top features that a modern ZTNA model should include. This slide highlights the characteristics of modern ZTNA solutions, including data loss prevention, scalable performance, granular visibility and reporting, BYOD deployment options, advanced threat protection, and SASE offering.
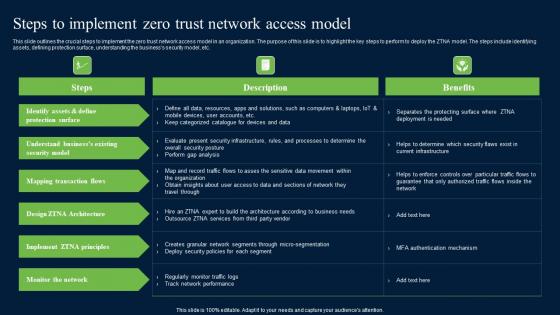
Steps To Implement Zero Trust Network Access Model Zero Trust Network Security Inspiration Pdf
This slide outlines the crucial steps to implement the zero trust network access model in an organization. The purpose of this slide is to highlight the key steps to perform to deploy the ZTNA model. The steps include identifying assets, defining protection surface, understanding the businesss security model, etc. Get a simple yet stunning designed Steps To Implement Zero Trust Network Access Model Zero Trust Network Security Inspiration Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Steps To Implement Zero Trust Network Access Model Zero Trust Network Security Inspiration Pdf can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide outlines the crucial steps to implement the zero trust network access model in an organization. The purpose of this slide is to highlight the key steps to perform to deploy the ZTNA model. The steps include identifying assets, defining protection surface, understanding the businesss security model, etc.

Overview Subscription Based Business Model DT SS V
This slide presents an overview of subscription based business model. It includes overview, framework, need and impact such as customer convenience, revenue prediction, customer attraction, low customer acquisition costs, and stronger customer relationships.Take your projects to the next level with our ultimate collection of Overview Subscription Based Business Model DT SS V. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest This slide presents an overview of subscription based business model. It includes overview, framework, need and impact such as customer convenience, revenue prediction, customer attraction, low customer acquisition costs, and stronger customer relationships.
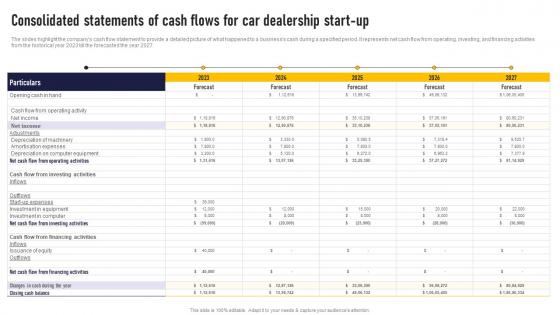
Consolidated Statements Of Cash Flows For Car Dealership Auto Dealership Business Plan Formats Pdf
The slides highlight the companys cash flow statement to provide a detailed picture of what happened to a businesss cash during a specified period. It represents net cash flow from operating, investing, and financing activities from the historical year 2023 till the forecasted the year 2027. Take your projects to the next level with our ultimate collection of Consolidated Statements Of Cash Flows For Car Dealership Auto Dealership Business Plan Formats Pdf Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they well make your projects stand out from the rest. The slides highlight the companys cash flow statement to provide a detailed picture of what happened to a businesss cash during a specified period. It represents net cash flow from operating, investing, and financing activities from the historical year 2023 till the forecasted the year 2027.

Features Of Zero Trust Network Access Security Model Background Pdf
This slide represents the main features of ZTNA. The purpose of this slide is to showcase the various features of zero trust network access, including safeguarding private apps, connecting security controls to apps more closely, restriction of access, recognizing internal app use, and so on. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Features Of Zero Trust Network Access Security Model Background Pdf template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Features Of Zero Trust Network Access Security Model Background Pdf that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide represents the main features of ZTNA. The purpose of this slide is to showcase the various features of zero trust network access, including safeguarding private apps, connecting security controls to apps more closely, restriction of access, recognizing internal app use, and so on.

Zero Trust Model Benefits Of Zero Trust Network Access ZTNA
This slide represents the benefits of zero trust network access, a component of SASE technology. The purpose of this slide is to demonstrate the multiple benefits of ZTNA to businesses and users. It also caters to the security benefits such as increased control and visibility, invisible infrastructure, and simple app segmentation. Get a simple yet stunning designed Zero Trust Model Benefits Of Zero Trust Network Access ZTNA. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Zero Trust Model Benefits Of Zero Trust Network Access ZTNA can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide represents the benefits of zero trust network access, a component of SASE technology. The purpose of this slide is to demonstrate the multiple benefits of ZTNA to businesses and users. It also caters to the security benefits such as increased control and visibility, invisible infrastructure, and simple app segmentation.
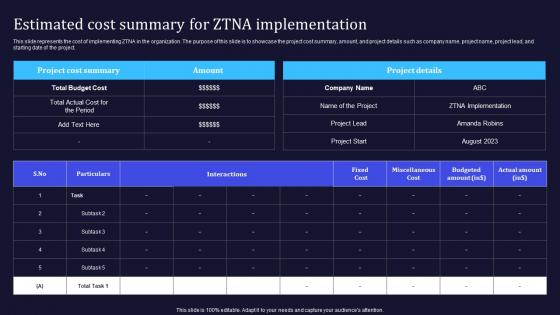
Zero Trust Model Estimated Cost Summary For ZTNA Implementation
This slide represents the cost of implementing ZTNA in the organization. The purpose of this slide is to showcase the project cost summary, amount, and project details such as company name, project name, project lead, and starting date of the project. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Zero Trust Model Estimated Cost Summary For ZTNA Implementation was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Zero Trust Model Estimated Cost Summary For ZTNA Implementation This slide represents the cost of implementing ZTNA in the organization. The purpose of this slide is to showcase the project cost summary, amount, and project details such as company name, project name, project lead, and starting date of the project.

Zero Trust Model Step 3 Assess The Environment
This slide outlines the third step of ZTNA deployment, which is assessing the environment. The purpose of this slide is to highlight the questions that should be answered to evaluate the ecosystem and the questions include knowing the security controls, knowledge gaps and so on. Get a simple yet stunning designed Zero Trust Model Step 3 Assess The Environment. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Zero Trust Model Step 3 Assess The Environment can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide outlines the third step of ZTNA deployment, which is assessing the environment. The purpose of this slide is to highlight the questions that should be answered to evaluate the ecosystem and the questions include knowing the security controls, knowledge gaps and so on.
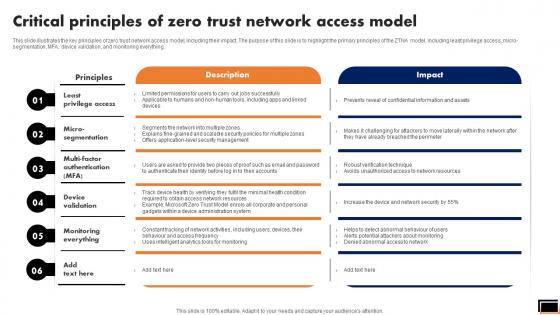
Critical Principles Of Zero Trust Network Access Model Software Defined Perimeter SDP
This slide illustrates the key principles of zero trust network access model, including their impact. The purpose of this slide is to highlight the primary principles of the ZTNA model, including least privilege access, micro-segmentation, MFA, device validation, and monitoring everything. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Critical Principles Of Zero Trust Network Access Model Software Defined Perimeter SDP. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Critical Principles Of Zero Trust Network Access Model Software Defined Perimeter SDP today and make your presentation stand out from the rest This slide illustrates the key principles of zero trust network access model, including their impact. The purpose of this slide is to highlight the primary principles of the ZTNA model, including least privilege access, micro-segmentation, MFA, device validation, and monitoring everything.
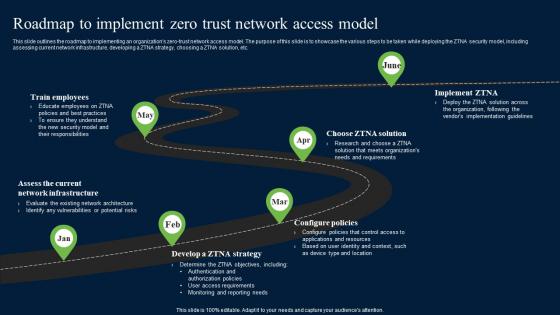
Roadmap To Implement Zero Trust Network Access Model Zero Trust Network Security Graphics Pdf
This slide outlines the roadmap to implementing an organizations zero-trust network access model. The purpose of this slide is to showcase the various steps to be taken while deploying the ZTNA security model, including assessing current network infrastructure, developing a ZTNA strategy, choosing a ZTNA solution, etc. This Roadmap To Implement Zero Trust Network Access Model Zero Trust Network Security Graphics Pdf from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide outlines the roadmap to implementing an organizations zero-trust network access model. The purpose of this slide is to showcase the various steps to be taken while deploying the ZTNA security model, including assessing current network infrastructure, developing a ZTNA strategy, choosing a ZTNA solution, etc.

Roadmap To Implement Zero Trust Network Access Model Software Defined Perimeter SDP
This slide outlines the roadmap to implementing an organizations zero-trust network access model. The purpose of this slide is to showcase the various steps to be taken while deploying the ZTNA security model, including assessing current network infrastructure, developing a ZTNA strategy, choosing a ZTNA solution, etc. This Roadmap To Implement Zero Trust Network Access Model Software Defined Perimeter SDP from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide outlines the roadmap to implementing an organizations zero-trust network access model. The purpose of this slide is to showcase the various steps to be taken while deploying the ZTNA security model, including assessing current network infrastructure, developing a ZTNA strategy, choosing a ZTNA solution, etc.

Zero Trust Model Checklist To Build Zero Trust Network Access
This slide outlines the checklist to develop a zero-trust network access architecture. The purpose of this slide is to define the various measures organizations should take while building a ZTNA architecture. The measures include knowing the architecture, creating a strong device identity, and so on. Slidegeeks is here to make your presentations a breeze with Zero Trust Model Checklist To Build Zero Trust Network Access With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide outlines the checklist to develop a zero-trust network access architecture. The purpose of this slide is to define the various measures organizations should take while building a ZTNA architecture. The measures include knowing the architecture, creating a strong device identity, and so on.

Zero Trust Model Overview Of Zero Trust Solution Categories
This slide represents the overview of zero-trust solution categories, including MFA, SSO, identity and access management, zero-trust network access and secure access service edge. The purpose of this slide is to give an overview of zero-trust technologies and their benefits. This Zero Trust Model Overview Of Zero Trust Solution Categories from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide represents the overview of zero-trust solution categories, including MFA, SSO, identity and access management, zero-trust network access and secure access service edge. The purpose of this slide is to give an overview of zero-trust technologies and their benefits.

Zero Trust Model Solutions To Overcome ZTNA Implementation Challenges
This slide talks about the various solutions to overcome the ZTNA deployment challenges. The purpose of this slide is to showcase the remedies to overcome ZTNA obstacles. The leading solutions include running zero-trust trials, starting small, scaling slowly, and keeping people and zero trust in mind. Want to ace your presentation in front of a live audience Our Zero Trust Model Solutions To Overcome ZTNA Implementation Challenges can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide talks about the various solutions to overcome the ZTNA deployment challenges. The purpose of this slide is to showcase the remedies to overcome ZTNA obstacles. The leading solutions include running zero-trust trials, starting small, scaling slowly, and keeping people and zero trust in mind.

Zero Trust Model Zero Trust Network Access Architecture Overview
This slide gives an overview of zero trust network access architecture. The purpose of this slide is to showcase the ZTNA architecture and its benefits, covering granting safe and fast access, protecting reliable remote access, protecting sensitive data and apps, stopping insider threats, and so on. Welcome to our selection of the Zero Trust Model Zero Trust Network Access Architecture Overview. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. This slide gives an overview of zero trust network access architecture. The purpose of this slide is to showcase the ZTNA architecture and its benefits, covering granting safe and fast access, protecting reliable remote access, protecting sensitive data and apps, stopping insider threats, and so on.
Deploying XP Practices To Enhance Operational Efficiency Collective Code Ownership Practice Icons PDF
This slide depicts collective code ownership as a practice of extreme programming which allows programmer within the team to make changes in the code.Make sure to capture your audiences attention in your business displays with our gratis customizable Deploying XP Practices To Enhance Operational Efficiency Collective Code Ownership Practice Icons PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
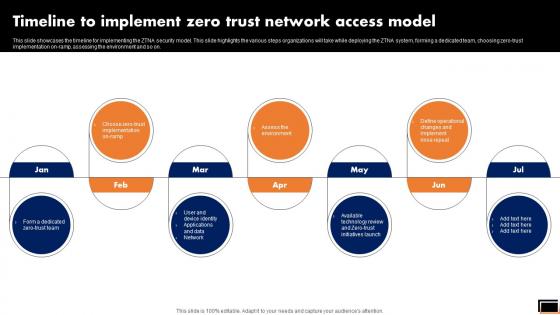
Timeline To Implement Zero Trust Network Access Model Software Defined Perimeter SDP
This slide showcases the timeline for implementing the ZTNA security model. This slide highlights the various steps organizations will take while deploying the ZTNA system, forming a dedicated team, choosing zero-trust implementation on-ramp, assessing the environment and so on. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Timeline To Implement Zero Trust Network Access Model Software Defined Perimeter SDP can be your best option for delivering a presentation. Represent everything in detail using Timeline To Implement Zero Trust Network Access Model Software Defined Perimeter SDP and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide showcases the timeline for implementing the ZTNA security model. This slide highlights the various steps organizations will take while deploying the ZTNA system, forming a dedicated team, choosing zero-trust implementation on-ramp, assessing the environment and so on.

Training Program For Zero Trust Network Access Model Software Defined Perimeter SDP
This slide outlines the training program for implementing the zero-trust network access model in the organization. The purpose of this slide is to highlight the training agenda, objectives, system requirements, mode of training and cost of the training. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Training Program For Zero Trust Network Access Model Software Defined Perimeter SDP template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Training Program For Zero Trust Network Access Model Software Defined Perimeter SDP that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide outlines the training program for implementing the zero-trust network access model in the organization. The purpose of this slide is to highlight the training agenda, objectives, system requirements, mode of training and cost of the training.
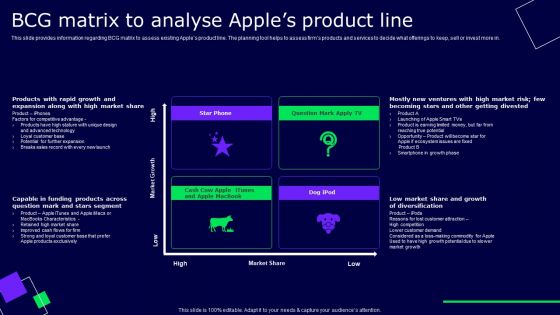
BCG Matrix To Analyse Apples Product Line Ppt Good PDF
This slide provides information regarding BCG matrix to assess existing Apples product line. The planning tool helps to assess firms products and services to decide what offerings to keep, sell or invest more in. Make sure to capture your audiences attention in your business displays with our gratis customizable BCG Matrix To Analyse Apples Product Line Ppt Good PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
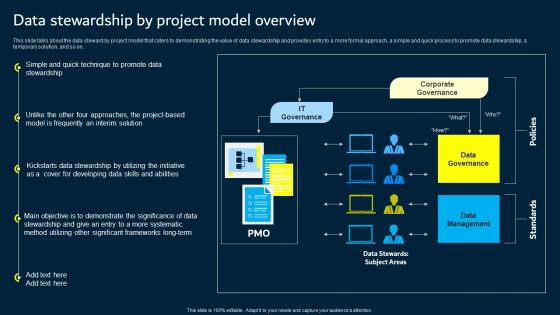
Data Stewardship By Project Model Overview Data Custodianship Pictures Pdf
This slide talks about the data steward by project model that caters to demonstrating the value of data stewardship and provides entry to a more formal approach, a simple and quick process to promote data stewardship, a temporary solution, and so on. Take your projects to the next level with our ultimate collection of Data Stewardship By Project Model Overview Data Custodianship Pictures Pdf. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest This slide talks about the data steward by project model that caters to demonstrating the value of data stewardship and provides entry to a more formal approach, a simple and quick process to promote data stewardship, a temporary solution, and so on.
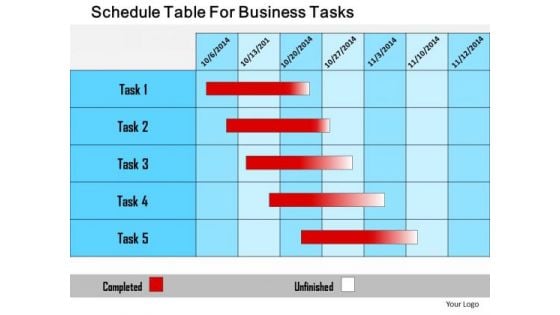
Business Diagram Schedule Table For Business Tasks Presentation Template
Our above slide displays schedule table for business tasks. Download our above diagram to express information in a visual way. Use this diagram to get good comments from viewers

Zero Trust Network Access Comparison Between Zero Trust Model SDP And VPN
This slide represents the comparison between the zero trust security model, software-defined perimeter, and virtual private network. The purpose of this slide is to showcase the difference as well as the relationship between three security technologies such as zero trust, SDP and VPN. Welcome to our selection of the Zero Trust Network Access Comparison Between Zero Trust Model SDP And VPN. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. This slide represents the comparison between the zero trust security model, software-defined perimeter, and virtual private network. The purpose of this slide is to showcase the difference as well as the relationship between three security technologies such as zero trust, SDP and VPN.

CASB 2 0 IT Future Use Of Emerging Technologies In CASB Model
This slide gives an overview of the technologies that can be used in the cloud access security broker model in the future. The purpose of this slide is to showcase the various emerging technologies that can help CASB to grow in the future. The technologies include AI, ML, CSPM, data privacy and protection, etc. Want to ace your presentation in front of a live audience Our CASB 2 0 IT Future Use Of Emerging Technologies In CASB Model can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide gives an overview of the technologies that can be used in the cloud access security broker model in the future. The purpose of this slide is to showcase the various emerging technologies that can help CASB to grow in the future. The technologies include AI, ML, CSPM, data privacy and protection, etc.
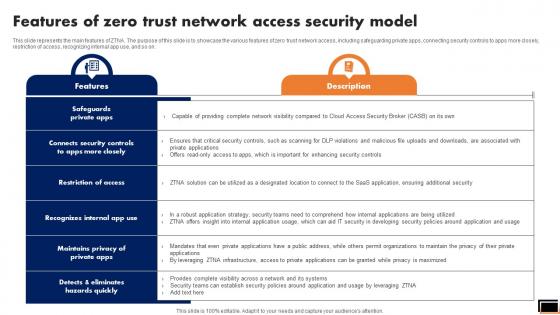
Features Of Zero Trust Network Access Security Model Software Defined Perimeter SDP
This slide represents the main features of ZTNA. The purpose of this slide is to showcase the various features of zero trust network access, including safeguarding private apps, connecting security controls to apps more closely, restriction of access, recognizing internal app use, and so on. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Features Of Zero Trust Network Access Security Model Software Defined Perimeter SDP template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Features Of Zero Trust Network Access Security Model Software Defined Perimeter SDP that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide represents the main features of ZTNA. The purpose of this slide is to showcase the various features of zero trust network access, including safeguarding private apps, connecting security controls to apps more closely, restriction of access, recognizing internal app use, and so on.
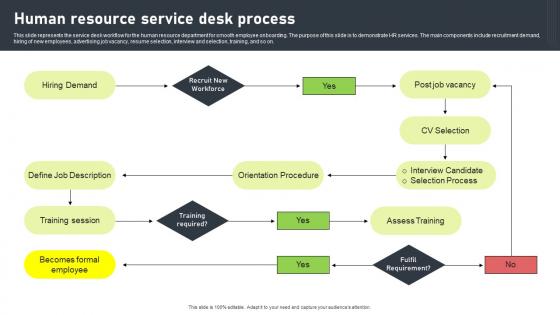
Human Resource Service Desk Process Pictures Pdf
This slide represents the service desk workflow for the human resource department for smooth employee onboarding. The purpose of this slide is to demonstrate HR services. The main components include recruitment demand, hiring of new employees, advertising job vacancy, resume selection, interview and selection, training, and so on. Pitch your topic with ease and precision using this Human Resource Service Desk Process Pictures Pdf. This layout presents information on Hiring Demand, Define Job Description, Training Session. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide represents the service desk workflow for the human resource department for smooth employee onboarding. The purpose of this slide is to demonstrate HR services. The main components include recruitment demand, hiring of new employees, advertising job vacancy, resume selection, interview and selection, training, and so on.


 Continue with Email
Continue with Email

 Home
Home


































