Safety Icons
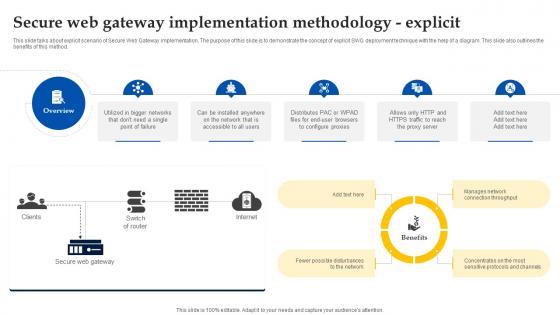
Web Access Control Solution Secure Web Gateway Implementation Methodology Explicit
This slide talks about explicit scenario of Secure Web Gateway implementation. The purpose of this slide is to demonstrate the concept of explicit SWG deployment technique with the help of a diagram. This slide also outlines the benefits of this method. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Web Access Control Solution Secure Web Gateway Implementation Methodology Explicit a try. Our experts have put a lot of knowledge and effort into creating this impeccable Web Access Control Solution Secure Web Gateway Implementation Methodology Explicit. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide talks about explicit scenario of Secure Web Gateway implementation. The purpose of this slide is to demonstrate the concept of explicit SWG deployment technique with the help of a diagram. This slide also outlines the benefits of this method.
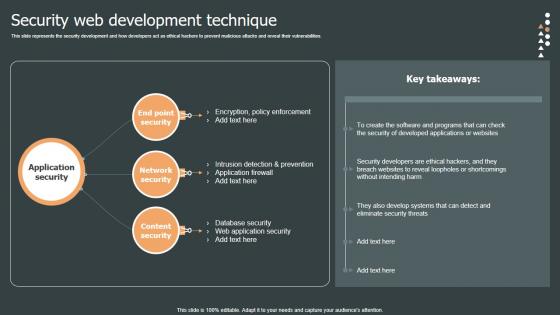
Security Web Development Role Web Designing User Engagement Topics PDF
This slide represents the security development and how developers act as ethical hackers to prevent malicious attacks and reveal their vulnerabilities. Are you searching for a Security Web Development Role Web Designing User Engagement Topics PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Security Web Development Role Web Designing User Engagement Topics PDF from Slidegeeks today. This slide represents the security development and how developers act as ethical hackers to prevent malicious attacks and reveal their vulnerabilities.

Sharing Files Global PowerPoint Templates And PowerPoint Themes 0912
Sharing Files Global PowerPoint Templates And PowerPoint Themes Presentations-Microsoft Powerpoint Templates and Background with laptop computer transferring files securely-Sharing Files Global PowerPoint Templates And PowerPoint Themes Presentations-This PowerPoint template can be used for presentations relating to-Laptop computer transferring files securely, internet, computer, security, communication, shapes Add on the colours with our Sharing Files Global PowerPoint Templates And PowerPoint Themes 0912. Give your views a decorative look.
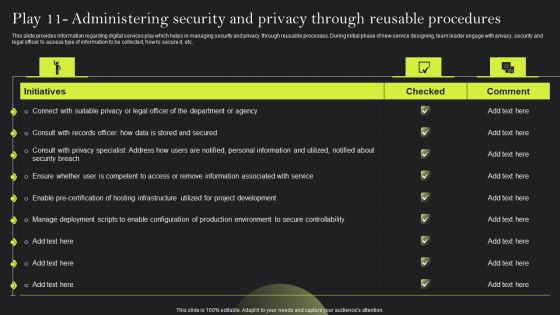
Playbook For Advancing Technology Play 11 Administering Security And Privacy Elements PDF
This slide provides information regarding digital services play which helps in managing security and privacy through reusable processes. During initial phase of new service designing, team leader engage with privacy, security and legal officer to assess type of information to be collected, how to secure it, etc. Retrieve professionally designed Playbook For Advancing Technology Play 11 Administering Security And Privacy Elements PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You dont have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Secure Web Gateway Implementation Methodology Transparent Web Access Control Solution
This slide talks about the transparent scenario of Secure Web Gateway implementation. The purpose of this slide is to demonstrate the concept of transparent SWG deployment technique with the help of a diagram. This slide also outlines the benefits of this method. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Secure Web Gateway Implementation Methodology Transparent Web Access Control Solution for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide talks about the transparent scenario of Secure Web Gateway implementation. The purpose of this slide is to demonstrate the concept of transparent SWG deployment technique with the help of a diagram. This slide also outlines the benefits of this method.

Security Information And Event Management Strategies For Financial Audit And Compliance Table Of Contents Diagrams PDF
This is a security information and event management strategies for financial audit and compliance table of contents diagrams pdf template with various stages. Focus and dispense information on eleven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like company overview, challenges and solutions, services offered, features and benefits, siem architecture. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
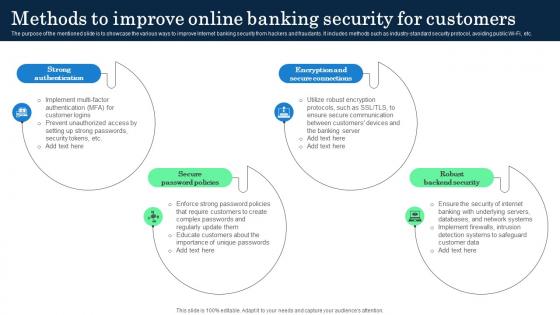
Methods To Improve Online Banking Security Incorporating Banking Operational Growth
The purpose of the mentioned slide is to showcase the various ways to improve Internet banking security from hackers and fraudants. It includes methods such as industry-standard security protocol, avoiding public Wi-Fi, etc. Do you know about Slidesgeeks Methods To Improve Online Banking Security Incorporating Banking Operational Growth These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. The purpose of the mentioned slide is to showcase the various ways to improve Internet banking security from hackers and fraudants. It includes methods such as industry-standard security protocol, avoiding public Wi-Fi, etc.

Prominent Users Of Secure Web Gateway Web Threat Protection System
This slide outlines the various Secure Web Gateway clients. The purpose of this slide is to explain how different users are utilizing SWG in their organizations. These are IT security experts, network administrators, compliance officers, HR managers, etc. Retrieve professionally designed Prominent Users Of Secure Web Gateway Web Threat Protection System to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide outlines the various Secure Web Gateway clients. The purpose of this slide is to explain how different users are utilizing SWG in their organizations. These are IT security experts, network administrators, compliance officers, HR managers, etc.
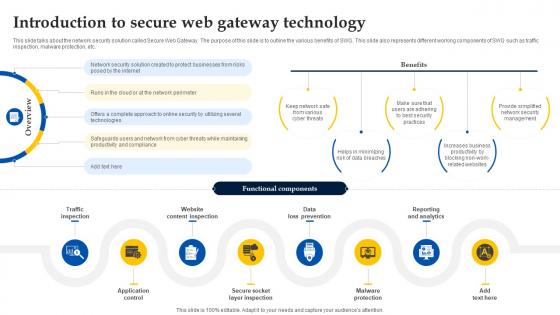
Web Access Control Solution Introduction To Secure Web Gateway Technology
This slide talks about the network security solution called Secure Web Gateway. The purpose of this slide is to outline the various benefits of SWG. This slide also represents different working components of SWG such as traffic inspection, malware protection, etc. Retrieve professionally designed Web Access Control Solution Introduction To Secure Web Gateway Technology to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide talks about the network security solution called Secure Web Gateway. The purpose of this slide is to outline the various benefits of SWG. This slide also represents different working components of SWG such as traffic inspection, malware protection, etc.

Illustration Depicting Brass Key On Laptop PowerPoint Templates Ppt Backgrounds For Slides 0113
We present our Illustration Depicting Brass Key On Laptop PowerPoint Templates PPT Backgrounds For Slides 0113.Download and present our Computer PowerPoint Templates because Our PowerPoint Templates and Slides are designed to help you succeed. They have all the ingredients you need. Present our Technology PowerPoint Templates because It will Raise the bar of your Thoughts. They are programmed to take you to the next level. Download and present our Security PowerPoint Templates because Our PowerPoint Templates and Slides will let you meet your Deadlines. Download and present our Network Diagrams PowerPoint Templates because Our PowerPoint Templates and Slides will Activate the energies of your audience. Get their creative juices flowing with your words. Use our Success PowerPoint Templates because Our PowerPoint Templates and Slides will bullet point your ideas. See them fall into place one by one.Use these PowerPoint slides for presentations relating to A pair of Keys and a Laptop, computer, technology, security, network diagrams, success. The prominent colors used in the PowerPoint template are Blue navy, Black, Red. Professionals tell us our Illustration Depicting Brass Key On Laptop PowerPoint Templates PPT Backgrounds For Slides 0113 are designed to make your presentations professional. PowerPoint presentation experts tell us our and PowerPoint templates and PPT Slides are designed by professionals You can be sure our Illustration Depicting Brass Key On Laptop PowerPoint Templates PPT Backgrounds For Slides 0113 will save the presenter time. PowerPoint presentation experts tell us our and PowerPoint templates and PPT Slides are designed by professionals We assure you our Illustration Depicting Brass Key On Laptop PowerPoint Templates PPT Backgrounds For Slides 0113 will get their audience's attention. PowerPoint presentation experts tell us our technology PowerPoint templates and PPT Slides will impress their bosses and teams. Our Illustration Depicting Brass Key On Laptop PowerPoint Templates Ppt Backgrounds For Slides 0113 are eclectic by nature. They are acceptable to different cultures.
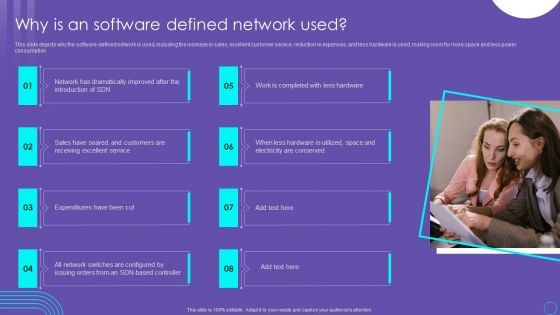
SDN Security Architecture Why Is An Software Defined Network Used Themes PDF
This slide depicts why the software defined network is used, including the increase in sales, excellent customer service, reduction in expenses, and less hardware is used, making room for more space and less power consumption. Present like a pro with SDN Security Architecture Why Is An Software Defined Network Used Themes PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
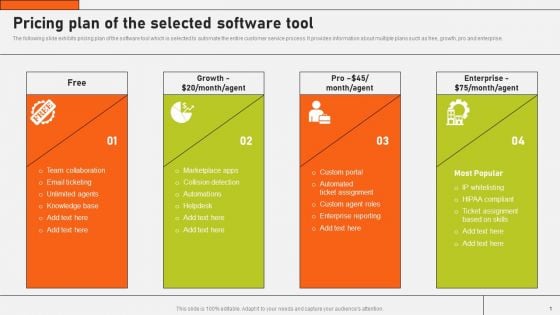
Securing Market Leadership Through Competitive Excellence Pricing Plan Of The Selected Software Tool Themes PDF
The following slide exhibits pricing plan of the software tool which is selected to automate the entire customer service process. It provides information about multiple plans such as free, growth, pro and enterprise. Slidegeeks is here to make your presentations a breeze with Securing Market Leadership Through Competitive Excellence Pricing Plan Of The Selected Software Tool Themes PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Solar Computing IT Improving Security By Green Computing Technology
This slide outlines how green computing can improve security. The purpose of this slide is to showcase the pillars of data security, security concerns and solution, and different antivirus software that can help users to protect their computers and networks. Are you searching for a Solar Computing IT Improving Security By Green Computing Technology that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Solar Computing IT Improving Security By Green Computing Technology from Slidegeeks today. This slide outlines how green computing can improve security. The purpose of this slide is to showcase the pillars of data security, security concerns and solution, and different antivirus software that can help users to protect their computers and networks.

Laptop With Pair Of Keys Security PowerPoint Templates And PowerPoint Themes 0812
Laptop With Pair Of Keys Security PowerPoint Templates And PowerPoint Themes 0812-Microsoft Powerpoint Templates and Background with a pair of keys and a laptop Bet on your assets coming good for you. Sign the cheque with our Laptop With Pair Of Keys Security PowerPoint Templates And PowerPoint Themes 0812.

Computer Folder With Key Security PowerPoint Templates And PowerPoint Themes 0912
Computer Folder With Key Security PowerPoint Templates And PowerPoint Themes 0912-Microsoft Powerpoint Templates and Background with folder with key Our Computer Folder With Key Security PowerPoint Templates And PowerPoint Themes 0912 get you a promotion. With our money back guarantee you have nothing to lose.
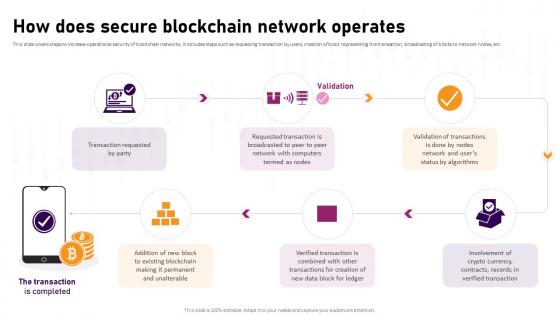
How Does Secure Blockchain Network Operates Complete Roadmap To Blockchain BCT SS V
This slide covers steps to increase operational security of blockchain networks. It includes steps such as requesting transaction by users, creation of block representing the transaction, broadcasting of blocks to network nodes, etc. Retrieve professionally designed How Does Secure Blockchain Network Operates Complete Roadmap To Blockchain BCT SS V to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide covers steps to increase operational security of blockchain networks. It includes steps such as requesting transaction by users, creation of block representing the transaction, broadcasting of blocks to network nodes, etc.
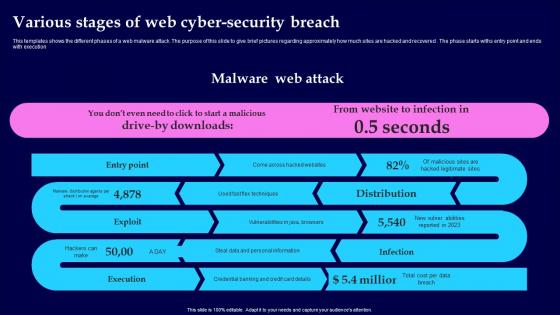
Various Stages Of Web Cyber Security Breach Introduction Pdf
This templates shows the different phases of a web malware attack. The purpose of this slide to give brief pictures regarding approximately how much sites are hacked and recovered. The phase starts withs entry point and ends with execution Pitch your topic with ease and precision using this Various Stages Of Web Cyber Security Breach Introduction Pdf This layout presents information on Malware Web Attack, Various Stages, Cyber Security Breach It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This templates shows the different phases of a web malware attack. The purpose of this slide to give brief pictures regarding approximately how much sites are hacked and recovered. The phase starts withs entry point and ends with execution
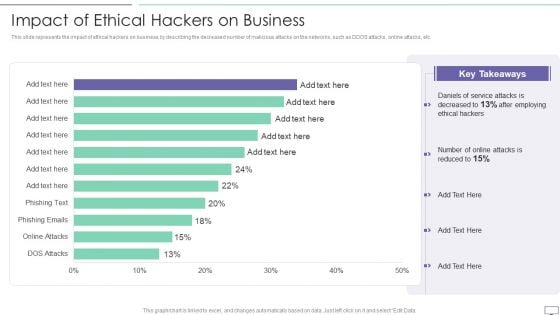
IT Security Hacker Impact Of Ethical Hackers On Business Slides PDF
This slide represents the impact of ethical hackers on business by describing the decreased number of malicious attacks on the networks, such as DDOS attacks, online attacks, etc.Deliver an awe inspiring pitch with this creative IT Security Hacker Impact Of Ethical Hackers On Business Slides PDF bundle. Topics like Key Takeaways, Daniels Of Service, After Employing can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Key With Welcome Home Security PowerPoint Templates And PowerPoint Themes 1112
Key With Welcome Home Security PowerPoint Templates And PowerPoint Themes 1112-Use this awesome PowerPoint template for property and ownership concept. This template features golden key with welcome home text. It portrays the concept of home, happiness, investment, mortgage, ownership, property, residence, security etc. This image has been conceived to enable you to emphatically communicate your ideas in your Real Estate PPT presentations. Our PPT images are so ideally designed that it reveals the very basis of our PPT template are an effective tool to make your clients understand.-Key With Welcome Home Security PowerPoint Templates And PowerPoint Themes 1112-This PowerPoint template can be used for presentations relating to-Gold Key With Welcome Home, Security, Business, Technology, Design, Metaphor Flood your audience with great slides with our Key With Welcome Home Security PowerPoint Templates And PowerPoint Themes 1112. Try us out and see what a difference our templates make.

Browser Favourites PowerPoint Templates And PowerPoint Themes 1012
Browser Favourites PowerPoint Templates And PowerPoint Themes 1012-By using this PowerPoint Template you can teach the Browser and networking configuration. It imitates richness, security, stocks and bonds, store, substance, substantiality, treasure, velvet, worth. Our PPT images are so ideally designed that it reveals the very basis of our PPT Template are an effective tool to make your clients understand.-Browser Favourites PowerPoint Templates And PowerPoint Themes 1012-This PowerPoint template can be used for presentations relating to-Browser favourites, technology, business, internet, success, stars Make an exhibition characteristic of you. Display your effectiveness on our Browser Favourites PowerPoint Templates And PowerPoint Themes 1012.

Key Security Considerations For 5G For Threat Handling 5G Network Architecture Instructions Diagrams PDF
This slide provides details regarding key security considerations associated to 5G in order to handle threats such as data breach, denial of service, unauthorized activities, etc. Deliver and pitch your topic in the best possible manner with this Key Security Considerations For 5G For Threat Handling 5G Network Architecture Instructions Diagrams PDF. Use them to share invaluable insights on Nodes Authentication, Rule Consistency, Policy Enforcement and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Table Of Contents For Global Data Security Industry Report IR SS V
Retrieve professionally designed Table Of Contents For Global Data Security Industry Report IR SS V to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. Our Table Of Contents For Global Data Security Industry Report IR SS V are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

SWOT Analysis To Understand The Global Security Industry PPT Slide IR SS V
Retrieve professionally designed SWOT Analysis To Understand The Global Security Industry PPT Slide IR SS V to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. Our SWOT Analysis To Understand The Global Security Industry PPT Slide IR SS V are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
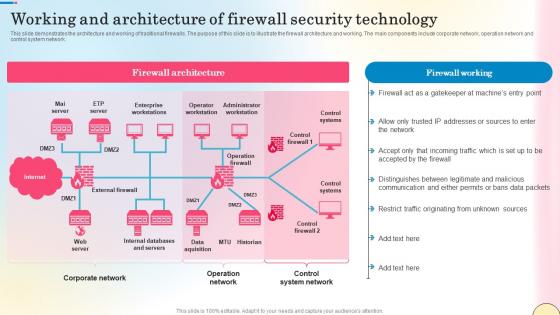
Working And Architecture Of Firewall Security Technology Network Security Summary Pdf
This slide demonstrates the architecture and working of traditional firewalls. The purpose of this slide is to illustrate the firewall architecture and working. The main components include corporate network, operation network and control system network. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Working And Architecture Of Firewall Security Technology Network Security Summary Pdf can be your best option for delivering a presentation. Represent everything in detail using Working And Architecture Of Firewall Security Technology Network Security Summary Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide demonstrates the architecture and working of traditional firewalls. The purpose of this slide is to illustrate the firewall architecture and working. The main components include corporate network, operation network and control system network.

Blue Computer Folder Internet PowerPoint Templates And PowerPoint Themes 0912
Blue Computer Folder Internet PowerPoint Templates And PowerPoint Themes 0912-Microsoft Powerpoint Templates and Background with computer folder with document-Computer folder with document, internet, marketing, computer, security, business Experience craftsmanship with our Blue Computer Folder Internet PowerPoint Templates And PowerPoint Themes 0912. They are designed by excellent artisans.
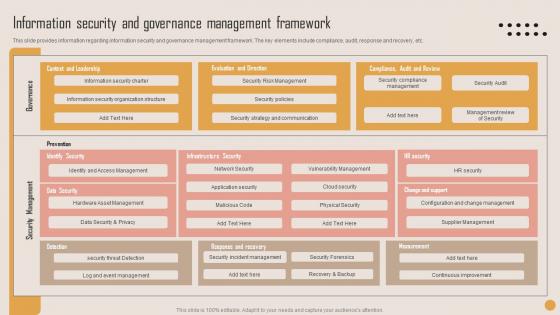
Information Security Governance Playbook For Strategic Actions To Improve IT Performance Themes Pdf
This slide provides information regarding information security and governance management framework. The key elements include compliance, audit, response and recovery, etc. This Information Security Governance Playbook For Strategic Actions To Improve IT Performance Themes Pdf is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Information Security Governance Playbook For Strategic Actions To Improve IT Performance Themes Pdf features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide provides information regarding information security and governance management framework. The key elements include compliance, audit, response and recovery, etc.

Umbrella With Laptop PowerPoint Templates And PowerPoint Themes 1012
Umbrella With Laptop PowerPoint Templates And PowerPoint Themes 1012-Microsoft Powerpoint Templates and Background with laptop and umbrella-Umbrella With Laptop PowerPoint Templates And PowerPoint Themes 1012-This PowerPoint template can be used for presentations relating to-Laptop and umbrella, computer, technology, security, internet, business Make interesting presentations no matter what the topic with our Umbrella With Laptop PowerPoint Templates And PowerPoint Themes 1012. Dont waste time struggling with PowerPoint. Let us do it for you.
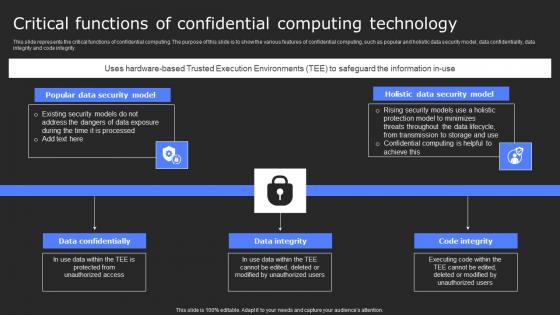
Critical Functions Of Confidential Computing Secure Computing Framework Microsoft Pdf
This slide represents the critical functions of confidential computing. The purpose of this slide is to show the various features of confidential computing, such as popular and holistic data security model, data confidentiality, data integrity and code integrity. Are you searching for a Critical Functions Of Confidential Computing Secure Computing Framework Microsoft Pdf that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Critical Functions Of Confidential Computing Secure Computing Framework Microsoft Pdf from Slidegeeks today. This slide represents the critical functions of confidential computing. The purpose of this slide is to show the various features of confidential computing, such as popular and holistic data security model, data confidentiality, data integrity and code integrity.
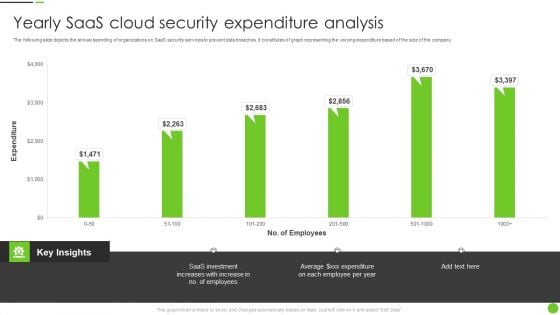
Yearly Saas Cloud Security Expenditure Analysis Ppt PowerPoint Presentation File Deck PDF
The following slide depicts the annual spending of organizations on SaaS security services to prevent data breaches. It constitutes of graph representing the varying expenditure based of the size of the company. Pitch your topic with ease and precision using this Yearly Saas Cloud Security Expenditure Analysis Ppt PowerPoint Presentation File Deck PDF. This layout presents information on Saas Investment, Employees. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
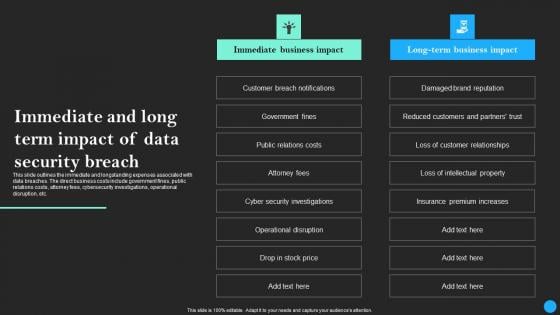
Immediate And Long Term Impact Of Data Security Breach Data Breach Prevention Topics Pdf
This slide outlines the immediate and longstanding expenses associated with data breaches. The direct business costs include government fines, public relations costs, attorney fees, cybersecurity investigations, operational disruption, etc. Retrieve professionally designed Immediate And Long Term Impact Of Data Security Breach Data Breach Prevention Topics Pdf to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide outlines the immediate and longstanding expenses associated with data breaches. The direct business costs include government fines, public relations costs, attorney fees, cybersecurity investigations, operational disruption, etc.

Understanding Real World Use Cases Of Secure Web Gateway Web Threat Protection System
This slide outlines the prominent features of Secure Web Gateway which provide protection to organizations from severe cyber threats. The purpose of this slide is to define the use cases of SWG such as real time web traffic surveillance, access management, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Understanding Real World Use Cases Of Secure Web Gateway Web Threat Protection System is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Understanding Real World Use Cases Of Secure Web Gateway Web Threat Protection System and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide outlines the prominent features of Secure Web Gateway which provide protection to organizations from severe cyber threats. The purpose of this slide is to define the use cases of SWG such as real time web traffic surveillance, access management, etc.

IAC Security For Protecting Cloud IAC Tools For Performance Analysis PPT Slide
This slide showcases the security of Infrastructure as Code for protecting cloud infrastructure. The purpose of this slide is to highlight the importance of IaC security such as consistency and predictability, early detection and prevention, reduced human error, etc. Retrieve professionally designed IAC Security For Protecting Cloud IAC Tools For Performance Analysis PPT Slide to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide showcases the security of Infrastructure as Code for protecting cloud infrastructure. The purpose of this slide is to highlight the importance of IaC security such as consistency and predictability, early detection and prevention, reduced human error, etc.

Cryptographic Algorithms Used In Cloud Data Security Using Cryptography Themes Pdf
This slide talks about algorithms used for implementing cryptography in data security. The purpose of this slide is to explain the different implementation steps. The techniques discussed are RSA Rivest, Shamir, Adleman cryptographic algorithm and Data Encryption Standard algorithm. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Cryptographic Algorithms Used In Cloud Data Security Using Cryptography Themes Pdf from Slidegeeks and deliver a wonderful presentation. This slide talks about algorithms used for implementing cryptography in data security. The purpose of this slide is to explain the different implementation steps. The techniques discussed are RSA Rivest, Shamir, Adleman cryptographic algorithm and Data Encryption Standard algorithm.

Data Transfer Business PowerPoint Templates And PowerPoint Themes 1112
We present our Data Transfer Business PowerPoint Templates And PowerPoint Themes 1112.Use our Security PowerPoint Templates because, Present your views using our innovative slides and be assured of leaving a lasting impression. Use our Arrows PowerPoint Templates because, Help them develop their thoughts along the way. Use our Business PowerPoint Templates because, Emphasise the process of your business/corporate growth. Use our Computer PowerPoint Templates because, Clarity of thought has been the key to your growth. Use our Internet PowerPoint Templates because, Transmit this concern to your staff using our halpful slides.Use these PowerPoint slides for presentations relating to Data transfer, inetrnet, computer, business, arrows, security. The prominent colors used in the PowerPoint template are Yellow, Blue, Green Put up the facts and figures on our Data Transfer Business PowerPoint Templates And PowerPoint Themes 1112. Display the data for everyone's consumption.
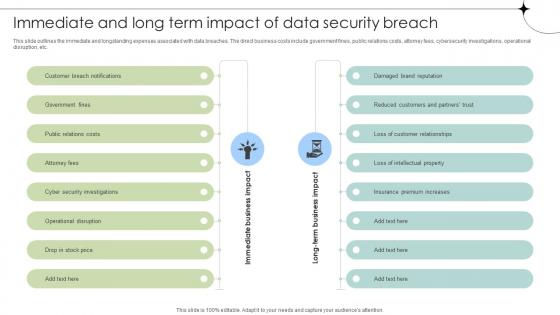
Immediate And Long Term Impact Of Data Security Breach Data Fortification Strengthening Defenses
This slide outlines the immediate and longstanding expenses associated with data breaches. The direct business costs include government fines, public relations costs, attorney fees, cybersecurity investigations, operational disruption, etc. Are you searching for a Immediate And Long Term Impact Of Data Security Breach Data Fortification Strengthening Defenses that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Immediate And Long Term Impact Of Data Security Breach Data Fortification Strengthening Defenses from Slidegeeks today. This slide outlines the immediate and longstanding expenses associated with data breaches. The direct business costs include government fines, public relations costs, attorney fees, cybersecurity investigations, operational disruption, etc.
Stock Photo Yellow Folders And Server On It For Data Storage Image Graphics For PowerPoint Slide
This image slide displays yellow folder with computer server for technology. This image slide has been designed with graphic of computer server on yellow data folder. Use this image, in your presentations to express views on client server, computing, data storage and backup. This image will enhance the quality of your presentations.
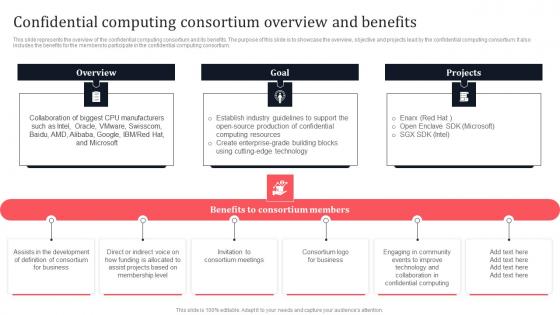
Confidential Computing Consortium Overview And Benefits Secure Multi Party Demonstration Pdf
This slide represents the overview of the confidential computing consortium and its benefits. The purpose of this slide is to showcase the overview, objective and projects lead by the confidential computing consortium. It also includes the benefits for the members to participate in the confidential computing consortium. If you are looking for a format to display your unique thoughts, then the professionally designed Confidential Computing Consortium Overview And Benefits Secure Multi Party Demonstration Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Confidential Computing Consortium Overview And Benefits Secure Multi Party Demonstration Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide represents the overview of the confidential computing consortium and its benefits. The purpose of this slide is to showcase the overview, objective and projects lead by the confidential computing consortium. It also includes the benefits for the members to participate in the confidential computing consortium.
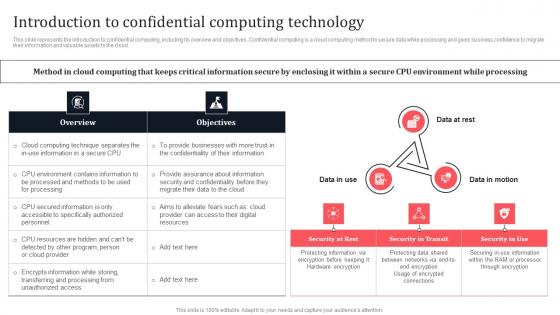
Introduction To Confidential Computing Technology Secure Multi Party Download Pdf
This slide represents the introduction to confidential computing, including its overview and objectives. Confidential computing is a cloud computing method to secure data while processing and gives business confidence to migrate their information and valuable assets to the cloud. Do you know about Slidesgeeks Introduction To Confidential Computing Technology Secure Multi Party Download Pdf These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide represents the introduction to confidential computing, including its overview and objectives. Confidential computing is a cloud computing method to secure data while processing and gives business confidence to migrate their information and valuable assets to the cloud.
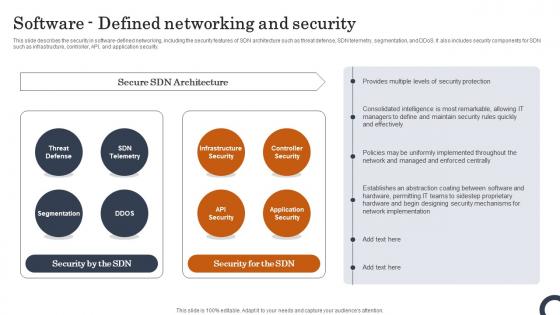
Software Defined Networking And Security Evolution Of SDN Controllers Inspiration Pdf
This slide describes the security in software-defined networking, including the security features of SDN architecture such as threat defense, SDN telemetry, segmentation, and DDoS. It also includes security components for SDN such as infrastructure, controller, API, and application security. Do you know about Slidesgeeks Software Defined Networking And Security Evolution Of SDN Controllers Inspiration Pdf These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide describes the security in software-defined networking, including the security features of SDN architecture such as threat defense, SDN telemetry, segmentation, and DDoS. It also includes security components for SDN such as infrastructure, controller, API, and application security.
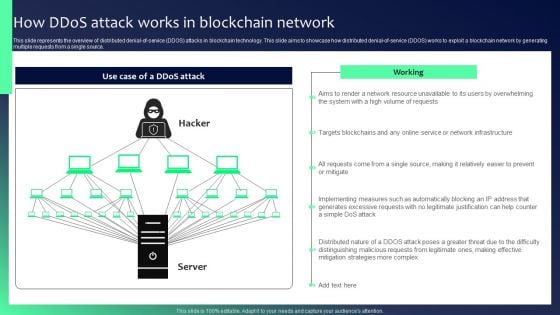
Blockchain Security Solutions Deployment How Ddos Attack Works In Blockchain Network Diagrams PDF
This slide represents the overview of distributed denial-of-service DDOS attacks in blockchain technology. This slide aims to showcase how distributed denial-of-service DDOS works to exploit a blockchain network by generating multiple requests from a single source. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Blockchain Security Solutions Deployment How Ddos Attack Works In Blockchain Network Diagrams PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Key To Success Business PowerPoint Templates And PowerPoint Themes 1012
Key To Success Business PowerPoint Templates And PowerPoint Themes 1012-Create dynamic Microsoft office PPT Presentations with our professional Templates containing a graphic of a golden key written Success on it. This image has been professionally designed to emphasize the concept of achievement, accomplishment, victory, triumph, feat, realization, attainment, hit, winner, sensation, star, triumph, success story etc. This image has been conceived to enable you to emphatically communicate your ideas in your Business, Financial, Global and Social PPT presentation.-Key To Success Business PowerPoint Templates And PowerPoint Themes 1012-This PowerPoint template can be used for presentations relating to-Key To Success, Security, Success, Business, Shapes, Real Estate Acquire the endorsement of the audience. The use of our Key To Success Business PowerPoint Templates And PowerPoint Themes 1012 will go in your favour.
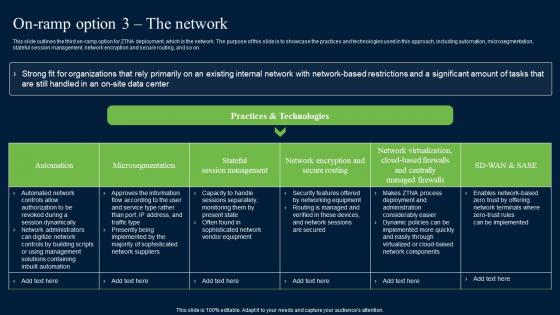
On Ramp Option 3 The Network Zero Trust Network Security Information Pdf
This slide outlines the third on-ramp option for ZTNA deployment, which is the network. The purpose of this slide is to showcase the practices and technologies used in this approach, including automation, microsegmentation, stateful session management, network encryption and secure routing, and so on. Are you searching for a On Ramp Option 3 The Network Zero Trust Network Security Information Pdf that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download On Ramp Option 3 The Network Zero Trust Network Security Information Pdf from Slidegeeks today. This slide outlines the third on-ramp option for ZTNA deployment, which is the network. The purpose of this slide is to showcase the practices and technologies used in this approach, including automation, microsegmentation, stateful session management, network encryption and secure routing, and so on.
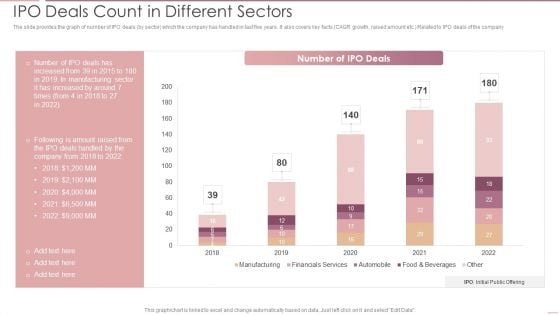
Investment Banking Security Underwriting Pitchbook IPO Deals Count In Different Sectors Mockup PDF
The slide provides the graph of number of IPO deals by sector which the company has handled in last five years. It also covers key facts CAGR growth, raised amount etc. Related to IPO deals of the company.Deliver and pitch your topic in the best possible manner with this Investment Banking Security Underwriting Pitchbook IPO Deals Count In Different Sectors Mockup PDF Use them to share invaluable insights on Manufacturing, Automobile, Financials Services and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Ppt PowerPoint Graphics Arrows Assembled To Form Square Templates
PPT powerpoint graphics arrows assembled to form square Templates-This PowerPoint Diagram shows four curved arrows combined together to form a square. It is helpful to describe interrelated issues, Approaches or Methods. This can be used to explain comparative approaches also.-Can be used for presentations on arrow, background, bio, care, circle, clean, conservation, curve, cycle, design, eco, ecological, ecology, element, environment, environmental, friendly, garbage, global, graphic, green, icon, illustration, image, isolated, life, modern, motion, natural, nature, object, painting, pattern, pollution, protection, recycle, recycling, reduce, renew, responsibility, return, reuse, save, shape, sign, single, symbol, vector, waste, white-PPT powerpoint graphics arrows assembled to form square Templates Add emphasis to your ideas with our Ppt PowerPoint Graphics Arrows Assembled To Form Square Templates. Lend greater credence to your expression.

Network Access Computer PowerPoint Themes And PowerPoint Slides 0411
Microsoft PowerPoint Theme and Slide with network access of computer Put in our Network Access Computer PowerPoint Themes And PowerPoint Slides 0411 as the catalyst. Churn out new equations with your ideas.

Anti Virus Computer PowerPoint Themes And PowerPoint Slides 0211
Microsoft PowerPoint Theme and Slide with modern mouse connected to word Anti-Virus Award yourself with our Anti Virus Computer PowerPoint Themes And PowerPoint Slides 0211. Your thoughts deserve the distinction.

Internet Browser Travel PowerPoint Themes And PowerPoint Slides 0211
Microsoft PowerPoint Theme and Slide with a metallic lock dial inside window of internet browser The corporate world can be fiercely competitive. Battle it out with our Internet Browser Travel PowerPoint Themes And PowerPoint Slides 0211.

Golden Key Idea Business PowerPoint Themes And PowerPoint Slides 0611
Microsoft PowerPoint Theme and Slide with golden key idea Our Golden Key Idea Business PowerPoint Themes And PowerPoint Slides 0611 are never far from you. They will come to your assistance in a click.

Data Recovery Internet PowerPoint Themes And PowerPoint Slides 0511
Microsoft PowerPoint Theme and Slide with lifesaver floating in a binary data sea Acquire a feel for it all with our Data Recovery Internet PowerPoint Themes And PowerPoint Slides 0511. They put you in your comfort zone.

Computer Assistance Concept Success PowerPoint Templates And PowerPoint Themes 0812
Computer Assistance Concept Success PowerPoint Templates And PowerPoint Themes 0812-Microsoft Powerpoint Templates and Background with computer assistance concept Put your faith in our Computer Assistance Concept Success PowerPoint Templates And PowerPoint Themes 0812. You will soon become a believer.
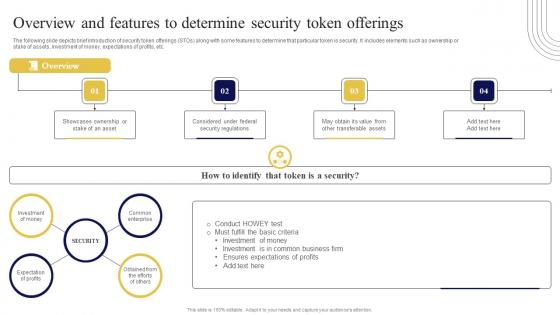
Overview And Features To Determine Security Exploring Investment Opportunities Slides Pdf
The following slide depicts brief introduction of security token offerings STOs along with some features to determine that particular token is security. It includes elements such as ownership or stake of assets, investment of money, expectations of profits, etc. Do you know about Slidesgeeks Overview And Features To Determine Security Exploring Investment Opportunities Slides Pdf These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. The following slide depicts brief introduction of security token offerings STOs along with some features to determine that particular token is security. It includes elements such as ownership or stake of assets, investment of money, expectations of profits, etc.

Abstract Clear On Keyboard PowerPoint Templates And PowerPoint Themes 0912
Abstract Clear On Keyboard PowerPoint Templates And PowerPoint Themes Presentations-Microsoft Powerpoint Templates and Background with image of a keyboard with the copyright symbol. This template is for use of IPR (Intellectual Property rights) presentations and campaings against online piracy.-Abstract Clear On Keyboard PowerPoint Templates And PowerPoint Themes PresentationsThis PPT can be used for presentations relating to-Copyright, piracy, IPR, intellectual property rights Your effort has brought you along. Go further with our Abstract Clear On Keyboard PowerPoint Templates And PowerPoint Themes 0912.

Application Of Internet Security In Operational Technology Pictures Pdf
This slide showcase operational technology cyber risk strategy mapping to different project lifecycles from strategy, architecture, implementation, and operations phases to prevent, predict, detect and response adaptative security model.Showcasing this set of slides titled Application Of Internet Security In Operational Technology Pictures Pdf The topics addressed in these templates are Consequence Driven Scenarios, Execute Prioritized, Risk Identified All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcase operational technology cyber risk strategy mapping to different project lifecycles from strategy, architecture, implementation, and operations phases to prevent, predict, detect and response adaptative security model.
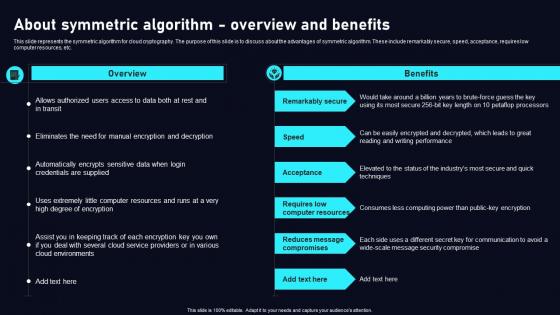
About Symmetric Algorithm Overview Cloud Data Security Using Cryptography Microsoft Pdf
This slide represents the symmetric algorithm for cloud cryptography. The purpose of this slide is to discuss about the advantages of symmetric algorithm. These include remarkably secure, speed, acceptance, requires low computer resources, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. About Symmetric Algorithm Overview Cloud Data Security Using Cryptography Microsoft Pdf can be your best option for delivering a presentation. Represent everything in detail using About Symmetric Algorithm Overview Cloud Data Security Using Cryptography Microsoft Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide represents the symmetric algorithm for cloud cryptography. The purpose of this slide is to discuss about the advantages of symmetric algorithm. These include remarkably secure, speed, acceptance, requires low computer resources, etc.
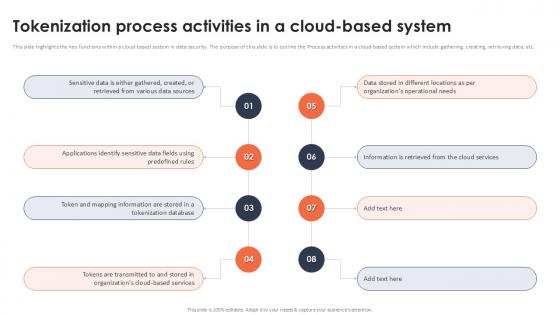
Tokenization Process Activities In A Cloud Based System Securing Your Data Ppt Powerpoint
This slide highlights the key functions within a cloud-based system in data security. The purpose of this slide is to outline the Process activities in a cloud-based system which include gathering, creating, retrieving data, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Tokenization Process Activities In A Cloud Based System Securing Your Data Ppt Powerpoint can be your best option for delivering a presentation. Represent everything in detail using Tokenization Process Activities In A Cloud Based System Securing Your Data Ppt Powerpoint and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide highlights the key functions within a cloud-based system in data security. The purpose of this slide is to outline the Process activities in a cloud-based system which include gathering, creating, retrieving data, etc.
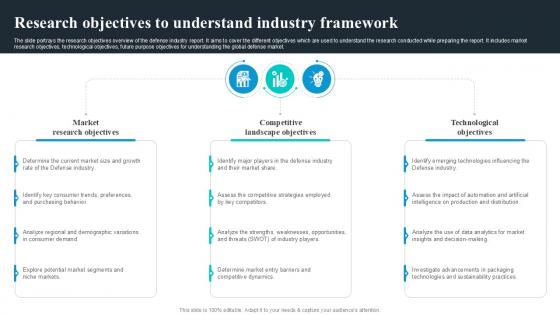
Research Objectives To Understand Global Security Industry PPT Template IR SS V
The slide highlights the SWOT analysis of Defense industry. The main purpose of this side is to understand and measure the comprehensive assessment of defense market. It further helps in mitigating the potential risks. Key components include strengths, weakness opportunities and threats. The slide portrays the research objectives overview of the defense industry report. It aims to cover the different objectives which are used to understand the research conducted while preparing the report. It includes market research objectives, technological objectives, future purpose objectives for understanding the global defense market. Are you searching for a Research Objectives To Understand Global Security Industry PPT Template IR SS V that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Research Objectives To Understand Global Security Industry PPT Template IR SS V from Slidegeeks today. The slide highlights the SWOT analysis of Defense industry. The main purpose of this side is to understand and measure the comprehensive assessment of defense market. It further helps in mitigating the potential risks. Key components include strengths, weakness opportunities and threats.

Secure Internet Connection Security PowerPoint Templates And PowerPoint Themes 0712
Secure Internet Connection Security PowerPoint Templates And PowerPoint Themes 0712-Microsoft Powerpoint Templates and Background with secure internet connection Put your attributes on display with our Secure Internet Connection Security PowerPoint Templates And PowerPoint Themes 0712. They make any exhibition an excellent one.
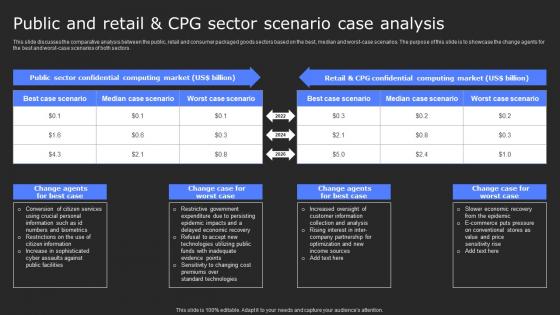
Public And Retail And Cpg Sector Scenario Case Analysis Secure Computing Framework Portrait Pdf
This slide discusses the comparative analysis between the public, retail and consumer packaged goods sectors based on the best, median and worst-case scenarios. The purpose of this slide is to showcase the change agents for the best and worst-case scenarios of both sectors. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Public And Retail And Cpg Sector Scenario Case Analysis Secure Computing Framework Portrait Pdf can be your best option for delivering a presentation. Represent everything in detail using Public And Retail And Cpg Sector Scenario Case Analysis Secure Computing Framework Portrait Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide discusses the comparative analysis between the public, retail and consumer packaged goods sectors based on the best, median and worst-case scenarios. The purpose of this slide is to showcase the change agents for the best and worst-case scenarios of both sectors.
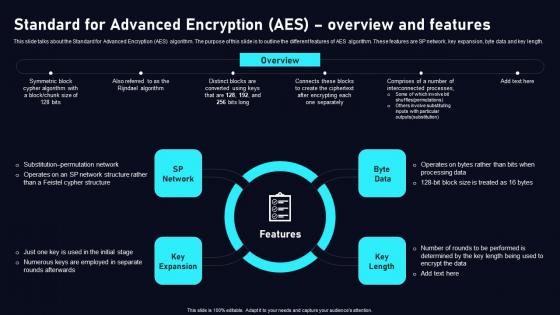
Standard For Advanced Encryption AES Cloud Data Security Using Cryptography Template Pdf
This slide talks about the Standard for Advanced Encryption AES algorithm. The purpose of this slide is to outline the different features of AES algorithm. These features are SP network, key expansion, byte data and key length. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Standard For Advanced Encryption AES Cloud Data Security Using Cryptography Template Pdf can be your best option for delivering a presentation. Represent everything in detail using Standard For Advanced Encryption AES Cloud Data Security Using Cryptography Template Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide talks about the Standard for Advanced Encryption AES algorithm. The purpose of this slide is to outline the different features of AES algorithm. These features are SP network, key expansion, byte data and key length.
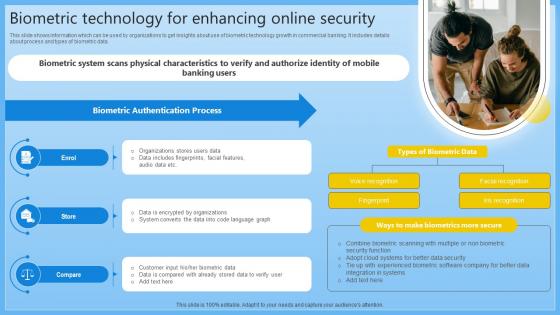
Biometric Technology For Enhancing Online Security Complete Guide On Managing Banking Fin SS V
This slide shows information which can be used by organizations to get insights about use of biometric technology growth in commercial banking. It includes details about process and types of biometric data. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Biometric Technology For Enhancing Online Security Complete Guide On Managing Banking Fin SS V can be your best option for delivering a presentation. Represent everything in detail using Biometric Technology For Enhancing Online Security Complete Guide On Managing Banking Fin SS V and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide shows information which can be used by organizations to get insights about use of biometric technology growth in commercial banking. It includes details about process and types of biometric data.

 Home
Home