Safety Icons
Information Security Organization Chart Ppt PowerPoint Presentation Layouts Design Templates Cpb Pdf
Presenting this set of slides with name information security organization chart ppt powerpoint presentation layouts design templates cpb pdf. This is an editable Powerpoint four stages graphic that deals with topics like information security organization chart to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Security KPI Dashboard With Various Charts And Graphs Ppt Summary Background Image PDF
Persuade your audience using this Security KPI Dashboard With Various Charts And Graphs Ppt Summary Background Image PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Various Charts, Security KPI Dashboard, Graphs. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Proposal For Enterprise Security System Gantt Chart One Pager Sample Example Document
Presenting you an exemplary Proposal For Enterprise Security System Gantt Chart One Pager Sample Example Document. Our one pager comprises all the must have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Proposal For Enterprise Security System Gantt Chart One Pager Sample Example Document brilliant piece now.
Gantt Chart For Home Security Equipment Installation Proposal One Pager Sample Example Document
Presenting you an exemplary Gantt Chart For Home Security Equipment Installation Proposal One Pager Sample Example Document. Our one pager comprises all the must have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Gantt Chart For Home Security Equipment Installation Proposal One Pager Sample Example Document brilliant piece now.
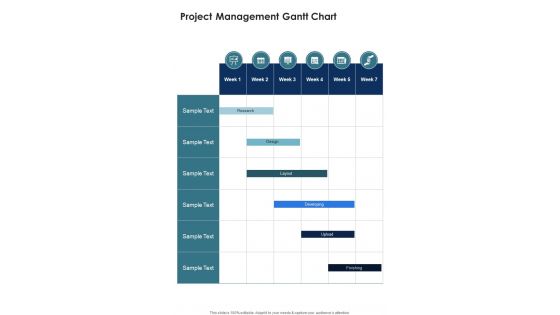
Project Management Gantt Chart Secure Network Construction Proposal One Pager Sample Example Document
Presenting you an exemplary Project Management Gantt Chart Secure Network Construction Proposal One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Project Management Gantt Chart Secure Network Construction Proposal One Pager Sample Example Document brilliant piece now.
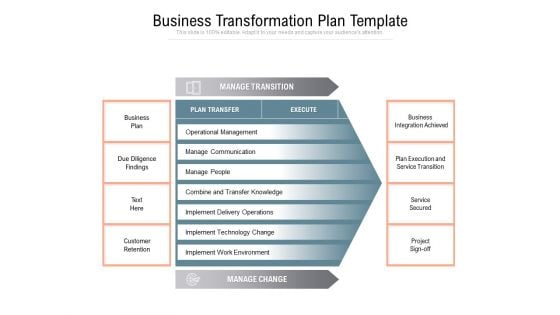
Business Transformation Plan Template Ppt PowerPoint Presentation Show Diagrams
Presenting this set of slides with name business transformation plan template ppt powerpoint presentation show diagrams. The topics discussed in these slides are business plan, due diligence findings, customer retention, business integration achieved, plan execution and service transition, service secured, project sign off. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
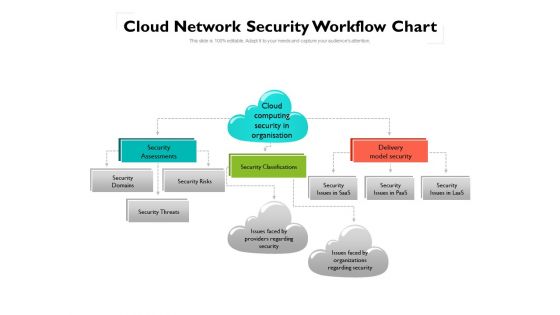
Cloud Network Security Workflow Chart Ppt PowerPoint Presentation Gallery Ideas PDF
This is a cloud network security workflow chart ppt powerpoint presentation gallery ideas pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security, organizations, domains. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
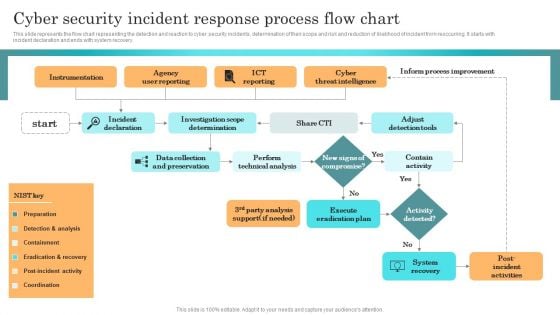
Incident Response Techniques Deployement Cyber Security Incident Response Process Flow Chart Slides PDF
This slide represents the flow chart representing the detection and reaction to cyber security incidents, determination of their scope and risk and reduction of likelihood of incident from reoccurring. It starts with incident declaration and ends with system recovery. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Incident Response Techniques Deployement Cyber Security Incident Response Process Flow Chart Slides PDF from Slidegeeks and deliver a wonderful presentation.
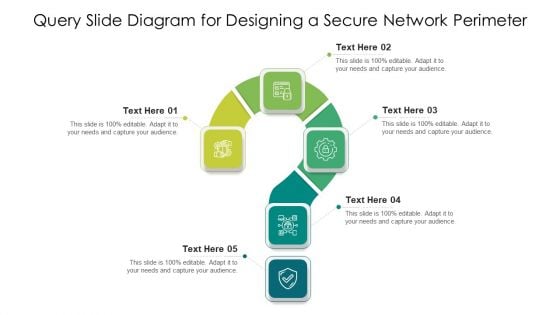
Query Slide Diagram For Designing A Secure Network Perimeter Diagrams PDF
Showcasing this set of slides titled query slide diagram for designing a secure network perimeter diagrams pdf. The topics addressed in these templates are query slide diagram for designing a secure network perimeter. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
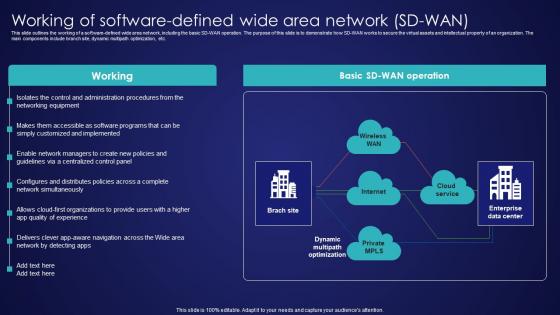
Working Of Software Defined Wide Area Network SD Wan Wide Area Network Services Diagrams Pdf
This slide outlines the working of a software-defined wide area network, including the basic SD-WAN operation. The purpose of this slide is to demonstrate how SD-WAN works to secure the virtual assets and intellectual property of an organization. The main components include branch site, dynamic multipath optimization, etc. Present like a pro with Working Of Software Defined Wide Area Network SD Wan Wide Area Network Services Diagrams Pdf Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide outlines the working of a software-defined wide area network, including the basic SD-WAN operation. The purpose of this slide is to demonstrate how SD-WAN works to secure the virtual assets and intellectual property of an organization. The main components include branch site, dynamic multipath optimization, etc.

Security Control Techniques For Real Estate Project Organizational Chart For Construction Site Designs PDF
There are so many reasons you need a Security Control Techniques For Real Estate Project Organizational Chart For Construction Site Designs PDF. The first reason is you canot spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
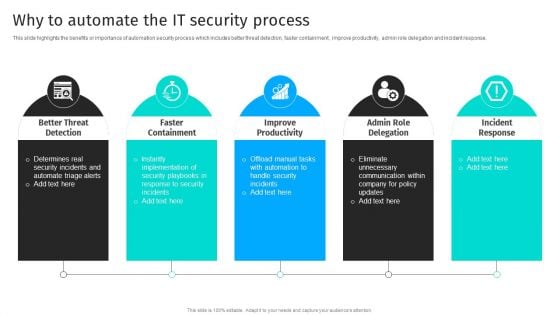
Security Automation To Analyze And Mitigate Cyberthreats Why To Automate The It Security Process Summary PDF
This slide highlights the benefits or importance of automation security process which includes better threat detection, faster containment, improve productivity, admin role delegation and incident response.Are you searching for a Security Automation To Analyze And Mitigate Cyberthreats Why To Automate The It Security Process Summary PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you ve put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Security Automation To Analyze And Mitigate Cyberthreats Why To Automate The It Security Process Summary PDF from Slidegeeks today.
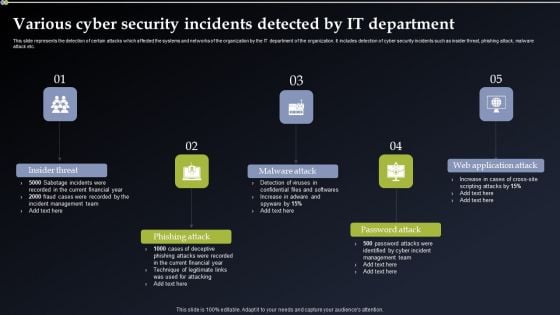
Deploying Cyber Security Incident Response Administration Various Cyber Security Incidents Detected By IT Department Portrait PDF
This slide represents the detection of certain attacks which affected the systems and networks of the organization by the IT department of the organization. It includes detection of cyber security incidents such as insider threat, phishing attack, malware attack etc. Are you searching for a Deploying Cyber Security Incident Response Administration Various Cyber Security Incidents Detected By IT Department Portrait PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Deploying Cyber Security Incident Response Administration Various Cyber Security Incidents Detected By IT Department Portrait PDF from Slidegeeks today.
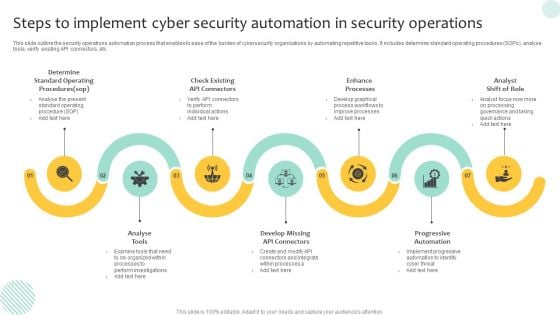
Steps To Implement Cyber Security Automation In Security Operations Demonstration PDF
This slide outline the security operations automation process that enables to ease of the burden of cybersecurity organizations by automating repetitive tasks. It includes determine standard operating procedures SOPs, analyse tools, verify existing API connectors, etc. Presenting Steps To Implement Cyber Security Automation In Security Operations Demonstration PDF to dispense important information. This template comprises seven stages. It also presents valuable insights into the topics including Progressive Automation, Enhance Processes, Analyse Tools. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
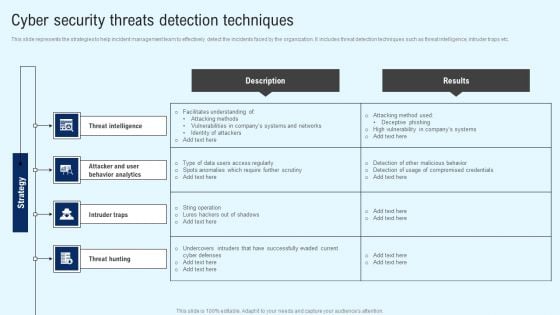
Implementing Cyber Security Incident Cyber Security Threats Detection Techniques Slides PDF
This slide represents the strategies to help incident management team to effectively detect the incidents faced by the organization. It includes threat detection techniques such as threat intelligence, intruder traps etc. Are you searching for a Implementing Cyber Security Incident Cyber Security Threats Detection Techniques Slides PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal. With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Implementing Cyber Security Incident Cyber Security Threats Detection Techniques Slides PDF from Slidegeeks today.
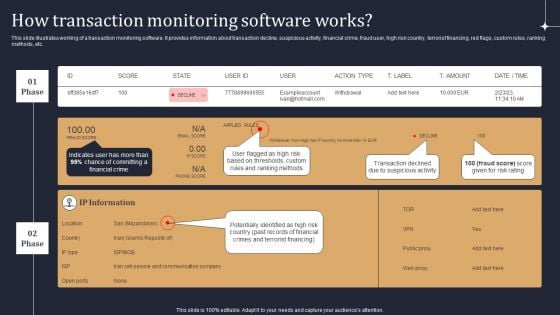
KYC Transaction Monitoring System Business Security How Transaction Monitoring Software Works Themes PDF
This slide illustrates working of a transaction monitoring software. It provides information about transaction decline, suspicious activity, financial crime, fraud user, high risk country, terrorist financing, red flags, custom rules, ranking methods, etc. Are you searching for a KYC Transaction Monitoring System Business Security How Transaction Monitoring Software Works Themes PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download KYC Transaction Monitoring System Business Security How Transaction Monitoring Software Works Themes PDF from Slidegeeks today.

Three Level Business Continuity Diagram Ppt Slides
This is a three level business continuity diagram ppt slides. This is a three stage process. The stages in this process are business continuity planning, security management, disaster recovery, technology, roles, testing, risk management, data assessment, coordination, communicating plan, policy, technology, services, procedures, incident response.
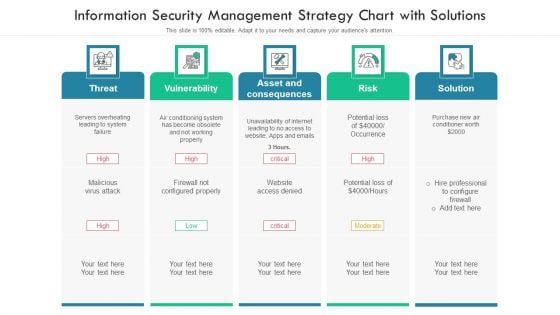
Information Security Management Strategy Chart With Solutions Ppt PowerPoint Presentation File Slides PDF
Persuade your audience using this information security management strategy chart with solutions ppt powerpoint presentation file slides pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including threat, vulnerability, risk, solution. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Key Techniques In Phishing Attacks Awareness Training Program Themes PDF
This slide covers strategies to consider in phishing awareness training program. It involves strategies such as verify email address, consider every email as phishing attempt and update security software. Presenting Key Techniques In Phishing Attacks Awareness Training Program Themes PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Implement, Secure Network Connectivity, Payment Service. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
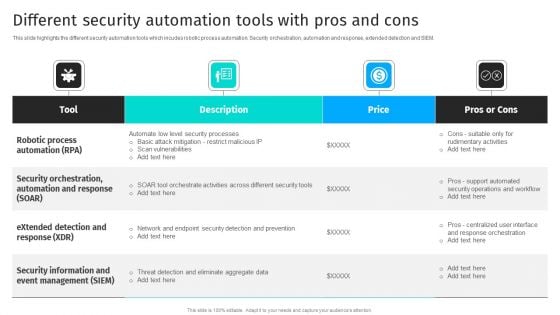
Security Automation To Analyze And Mitigate Cyberthreats Different Security Automation Tools Information PDF
This slide highlights the different security automation tools which incudes robotic process automation. Security orchestration, automation and response, extended detection and SIEM.Whether you have daily or monthly meetings, a brilliant presentation is necessary. Security Automation To Analyze And Mitigate Cyberthreats Different Security Automation Tools Information PDF can be your best option for delivering a presentation. Represent everything in detail using Security Automation To Analyze And Mitigate Cyberthreats Different Security Automation Tools Information PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
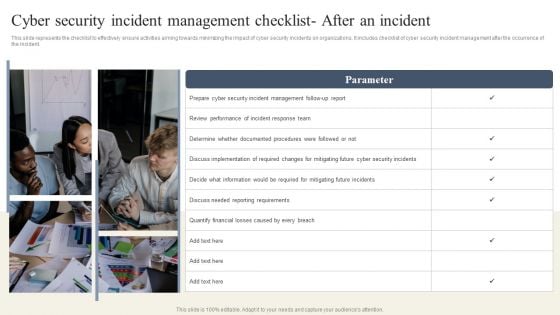
CYBER Security Breache Response Strategy Cyber Security Incident Management Checklist After An Incident Summary PDF
This slide represents the checklist to effectively ensure activities aiming towards minimizing the impact of cyber security incidents on organizations. It includes checklist of cyber security incident management after the occurrence of the incident. Whether you have daily or monthly meetings, a brilliant presentation is necessary. CYBER Security Breache Response Strategy Cyber Security Incident Management Checklist After An Incident Summary PDF can be your best option for delivering a presentation. Represent everything in detail using CYBER Security Breache Response Strategy Cyber Security Incident Management Checklist After An Incident Summary PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
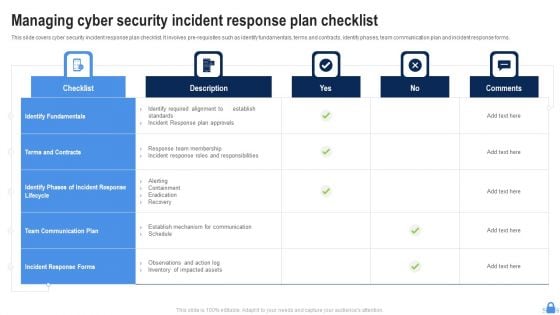
Managing Cyber Security Incident Response Plan Checklist Ppt Picture PDF
This slide covers cyber security incident response plan checklist. It involves pre-requisites such as identify fundamentals, terms and contracts, identify phases, team communication plan and incident response forms. Showcasing this set of slides titled Managing Cyber Security Incident Response Plan Checklist Ppt Picture PDF. The topics addressed in these templates are Identify Fundamentals, Checklist, Terms And Contracts. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Security Analysis Ppt PowerPoint Presentation File Format Ideas
This is a security analysis ppt powerpoint presentation file format ideas. This is a one stage process. The stages in this process are security analysis, growth, strategy, management, business.
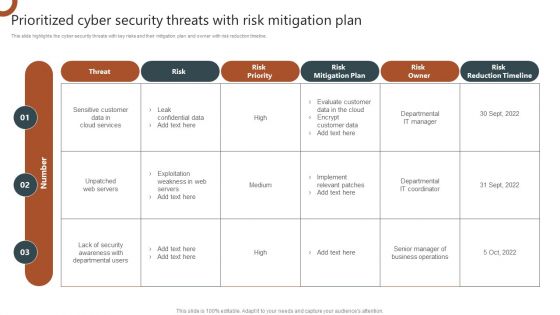
Organizations Risk Management And IT Security Prioritized Cyber Security Threats With Risk Mitigation Plan Demonstration PDF
This slide highlights the cyber security threats with key risks and their mitigation plan and owner with risk reduction timeline. Are you searching for a Organizations Risk Management And IT Security Risk Assessment Table With Actions And Escalation Level Background PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Organizations Risk Management And IT Security Risk Assessment Table With Actions And Escalation Level Background PDF from Slidegeeks today.
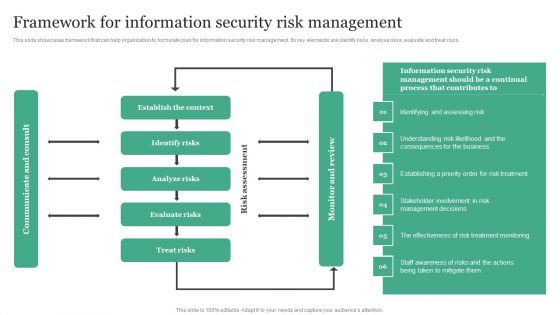
Framework For Information Security Risk Management Information Security Risk Administration Clipart PDF
This slide showcases framework that can help organization to formulate plan for information security risk management. Its key elements are identify risks, analyse risks, evaluate and treat risks.Whether you have daily or monthly meetings, a brilliant presentation is necessary. Framework For Information Security Risk Management Information Security Risk Administration Clipart PDF can be your best option for delivering a presentation. Represent everything in detail using Framework For Information Security Risk Management Information Security Risk Administration Clipart PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
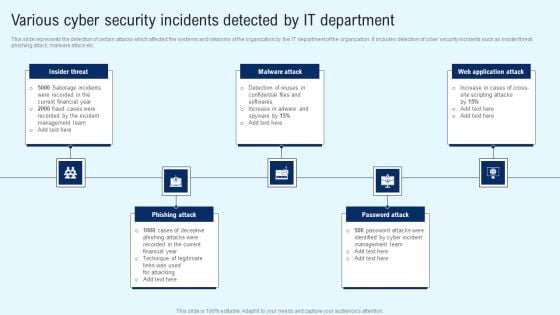
Implementing Cyber Security Incident Various Cyber Security Incidents Detected Elements PDF
This slide represents the detection of certain attacks which affected the systems and networks of the organization by the IT department of the organization. It includes detection of cyber security incidents such as insider threat, phishing attack, malware attack etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Implementing Cyber Security Incident Various Cyber Security Incidents Detected Elements PDF can be your best option for delivering a presentation. Represent everything in detail using Implementing Cyber Security Incident Various Cyber Security Incidents Detected Elements PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
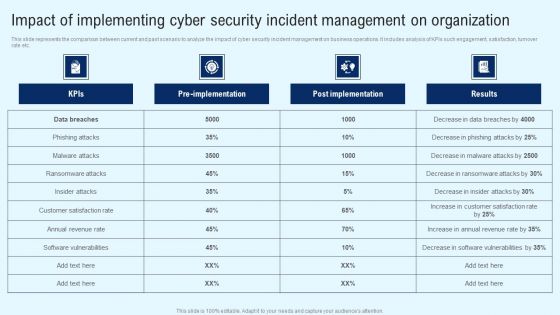
Implementing Cyber Security Incident Impact Of Implementing Cyber Security Incident Mockup PDF
This slide represents the comparison between current and past scenario to analyze the impact of cyber security incident management on business operations. It includes analysis of KPIs such engagement, satisfaction, turnover rate etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Implementing Cyber Security Incident Impact Of Implementing Cyber Security Incident Mockup PDF can be your best option for delivering a presentation. Represent everything in detail using Implementing Cyber Security Incident Impact Of Implementing Cyber Security Incident Mockup PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
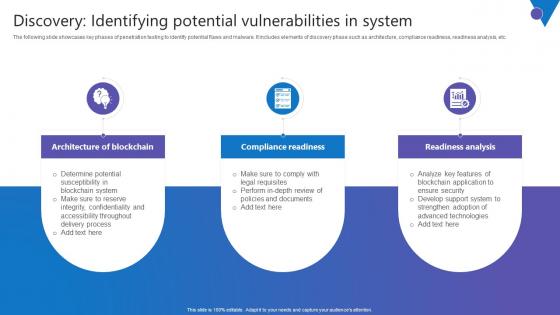
Discovery Identifying Potential Comprehensive Guide To Blockchain Digital Security Information Pdf
The following slide showcases key phases of penetration testing to identify potential flaws and malware. It includes elements of discovery phase such as architecture, compliance readiness, readiness analysis, etc. There are so many reasons you need a Discovery Identifying Potential Comprehensive Guide To Blockchain Digital Security Information Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. The following slide showcases key phases of penetration testing to identify potential flaws and malware. It includes elements of discovery phase such as architecture, compliance readiness, readiness analysis, etc.
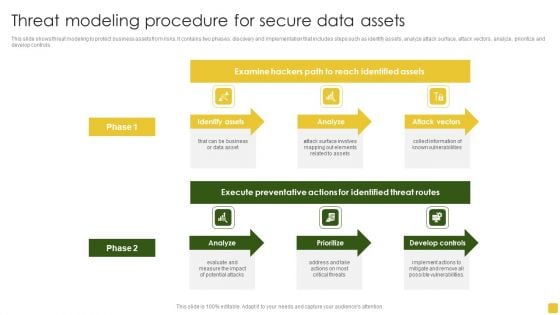
Threat Modeling Procedure For Secure Data Assets Formats PDF
This slide shows threat modeling to protect business assets from risks. It contains two phases discovery and implementation that includes steps such as identify assets, analyze attack surface, attack vectors, analyze, prioritize and develop controls. Pitch your topic with ease and precision using this Threat Modeling Procedure For Secure Data Assets Formats PDF. This layout presents information on Execute Preventative, Identified Threat, Develop Controls. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Cash Flow Chart Invests Security Ppt PowerPoint Presentation Complete Deck With Slides
Improve your presentation delivery using this cash flow chart invests security ppt powerpoint presentation complete deck with slides. Support your business vision and objectives using this well-structured PPT deck. This template offers a great starting point for delivering beautifully designed presentations on the topic of your choice. Comprising twelve this professionally designed template is all you need to host discussion and meetings with collaborators. Each slide is self-explanatory and equipped with high-quality graphics that can be adjusted to your needs. Therefore, you will face no difficulty in portraying your desired content using this PPT slideshow. This PowerPoint slideshow contains every important element that you need for a great pitch. It is not only editable but also available for immediate download and utilization. The color, font size, background, shapes everything can be modified to create your unique presentation layout. Therefore, download it now.

Stock Photo Ball With Big Data Text For Data Protection Concept PowerPoint Slide
Graphic of ball with big data text has been used to craft this power point template. This image template contains the concept of data protection. Use this image for data security related topics in any presentation.

Organizing Security Awareness Recognizing The Cyber Security Gaps Faced By Key Mockup PDF
The purpose of this slide is to outline the different cyber security gaps which are faced by employees, line and senior managers. Information covered in this slide is related to ransomware, password attack, crypto-jacking, iot-based attack, malware etc. Do you know about Slidesgeeks Organizing Security Awareness Recognizing The Cyber Security Gaps Faced By Key Mockup PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.

Current Information And Data Security Capabilities Of Firm Information Security Risk Administration Designs PDF
This slide showcases current capabilities of organization regarding information and data security. Its key component are risk management functions, required standard rating and actual standard rating.Do you know about Slidesgeeks Current Information And Data Security Capabilities Of Firm Information Security Risk Administration Designs PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.

CYBER Security Breache Response Strategy Strategies To Analyze Cyber Security Incidents Inspiration PDF
This slide represents the techniques to be used by the organizations to analyze the impact of cyber security incidents on business operations. It includes strategies for analyzing cyber incidents such as profile network and systems etc. Do you know about Slidesgeeks CYBER Security Breache Response Strategy Strategies To Analyze Cyber Security Incidents Inspiration PDF. These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
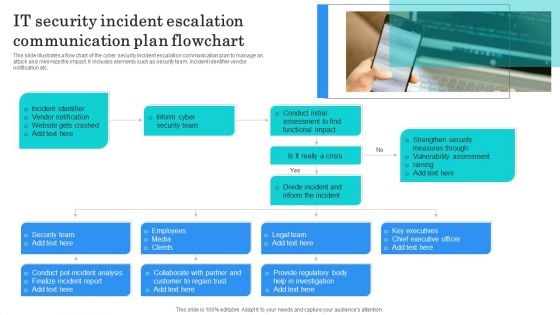
IT Security Incident Escalation Communication Plan Flowchart Structure PDF
This slide illustrates a flow chart of the cyber security incident escalation communication plan to manage an attack and minimize the impact. It includes elements such as security team, incident identifier vendor notification etc. Presenting IT Security Incident Escalation Communication Plan Flowchart Structure PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Incident Identifier, Vendor Notification, Website Gets Crashed. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Key To Success Security PowerPoint Templates And PowerPoint Backgrounds 0311
Microsoft PowerPoint Template and Background with a key and stock charts Respond to feedback with our Key To Success Security PowerPoint Templates And PowerPoint Backgrounds 0311. Download without worries with our money back guaranteee.
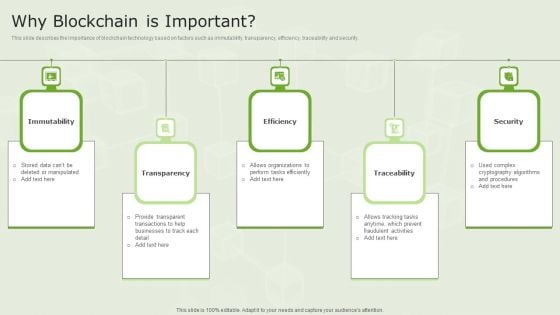
Managed Blockchain Service Why Blockchain Is Important Template PDF
This slide describes the importance of blockchain technology based on factors such as immutability, transparency, efficiency, traceability and security. Are you searching for a Managed Blockchain Service Why Blockchain Is Important Template PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Managed Blockchain Service Why Blockchain Is Important Template PDF from Slidegeeks today.
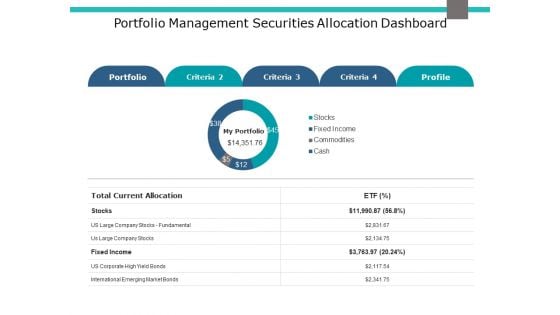
Portfolio Management Securities Allocation Dashboard Ppt PowerPoint Presentation Pictures Objects
This is a portfolio management securities allocation dashboard ppt powerpoint presentation pictures objects. This is a five stage process. The stages in this process are finance, marketing, management, investment.
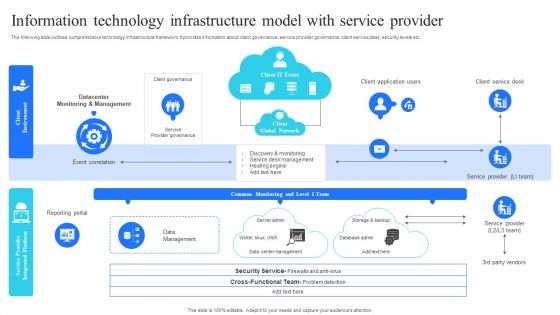
Information Technology Infrastructure Model With Service Provider Graphics PDF
The following slide outlines comprehensive technology infrastructure framework. It provides information about client governance, service provider governance, client service desk, security levels etc. Presenting Information Technology Infrastructure Model With Service Provider Graphics PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Datacenter, Monitoring And Management, Data Management, Client Service Desk, Service Provider. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
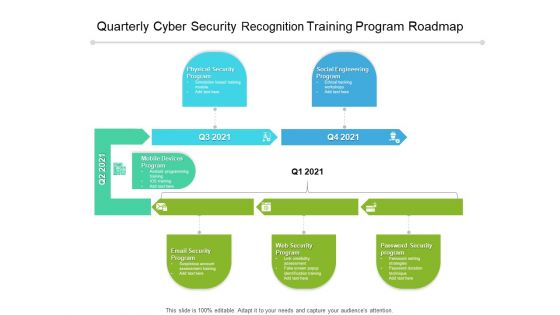
Quarterly Cyber Security Recognition Training Program Roadmap Elements
We present our quarterly cyber security recognition training program roadmap elements. This PowerPoint layout is easy-to-edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well-researched quarterly cyber security recognition training program roadmap elements in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
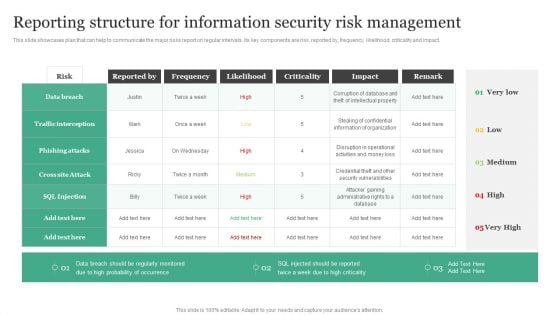
Reporting Structure For Information Security Risk Management Information Security Risk Administration Elements PDF
This slide showcases plan that can help to communicate the major risks report on regular intervals. Its key components are risk, reported by, frequency, likelihood, criticality and impact.Do you know about Slidesgeeks Reporting Structure For Information Security Risk Management Information Security Risk Administration Elements PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
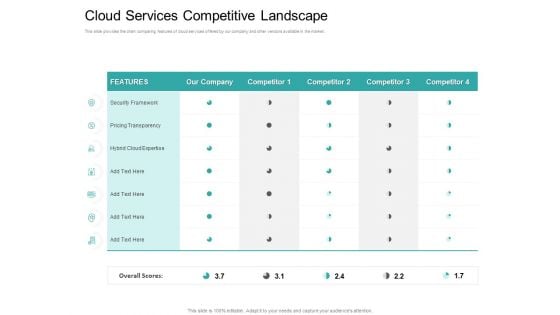
Cloud Based Marketing Cloud Services Competitive Landscape Ppt PowerPoint Presentation Summary PDF
This slide provides the chart comparing features of cloud services offered by our company and other vendors available in the market. Deliver an awe-inspiring pitch with this creative cloud based marketing cloud services competitive landscape ppt powerpoint presentation summary pdf bundle. Topics like security framework, pricing transparency, hybrid cloud expertise, overall scores can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Service Architecture And Delivery Process For Business Transformation Topics PDF
This slide includes the service architecture process enabling the development of applications that are easier to handle and more secure. These steps help to make software components reusable and efficient. Presenting Service Architecture And Delivery Process For Business Transformation Topics PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Govern Plan Service Products, Direct Plan Resources, Supply Service. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Five Year Cyber Data Security Career Growth Roadmap Formats
We present our five year cyber data security career growth roadmap formats. This PowerPoint layout is easy-to-edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well-researched five year cyber data security career growth roadmap formats in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
Half Yearly Data Sharing Security Network Career Roadmap Rules
We present our half yearly data sharing security network career roadmap rules. This PowerPoint layout is easy-to-edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well-researched half yearly data sharing security network career roadmap rules in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
Five Year Organization Product Development Roadmap With Advanced Security Sample
We present our five year organization product development roadmap with advanced security sample. This PowerPoint layout is easy-to-edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well-researched five year organization product development roadmap with advanced security sample in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
Five Years Engineering Roadmap With Security And Compliance Clipart
We present our five years engineering roadmap with security and compliance clipart. This PowerPoint layout is easy-to-edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well-researched five years engineering roadmap with security and compliance clipart in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
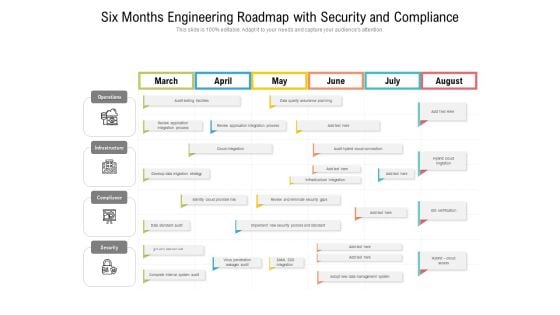
Six Months Engineering Roadmap With Security And Compliance Clipart
We present our six months engineering roadmap with security and compliance clipart. This PowerPoint layout is easy-to-edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well-researched six months engineering roadmap with security and compliance clipart in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
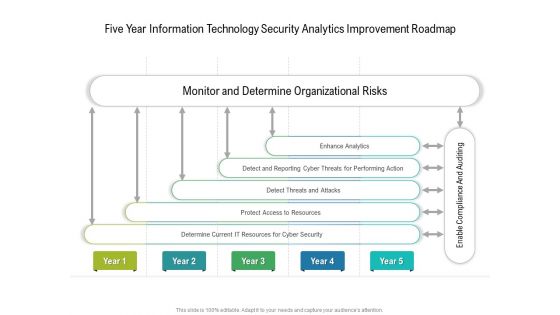
Five Year Information Technology Security Analytics Improvement Roadmap Infographics
We present our five year information technology security analytics improvement roadmap infographics. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched five year information technology security analytics improvement roadmap infographics in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
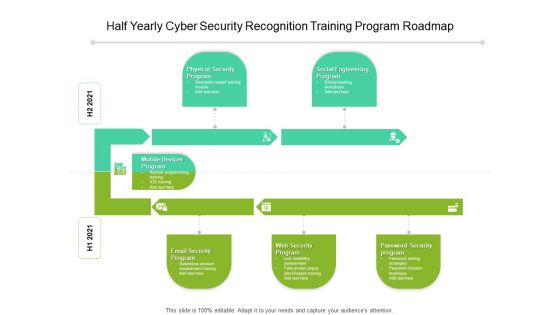
Half Yearly Cyber Security Recognition Training Program Roadmap Elements
We present our half yearly cyber security recognition training program roadmap elements. This PowerPoint layout is easy-to-edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well-researched half yearly cyber security recognition training program roadmap elements in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
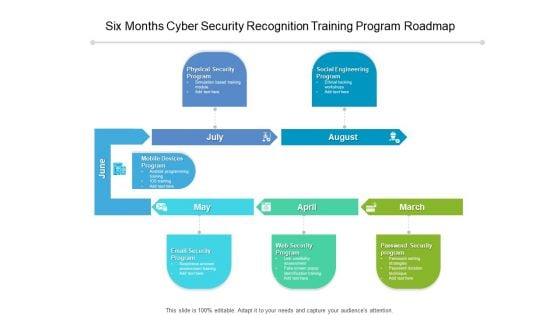
Six Months Cyber Security Recognition Training Program Roadmap Introduction
We present our six months cyber security recognition training program roadmap introduction. This PowerPoint layout is easy-to-edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well-researched six months cyber security recognition training program roadmap introduction in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
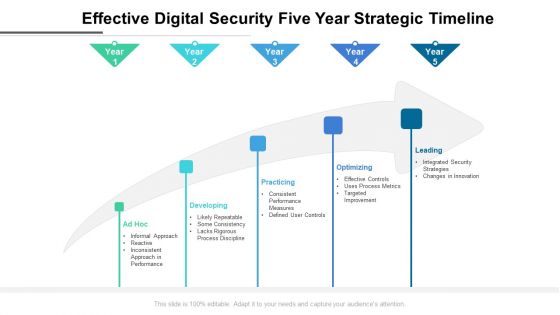
Effective Digital Security Five Year Strategic Timeline Formats
We present our effective digital security five year strategic timeline formats. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched effective digital security five year strategic timeline formats in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
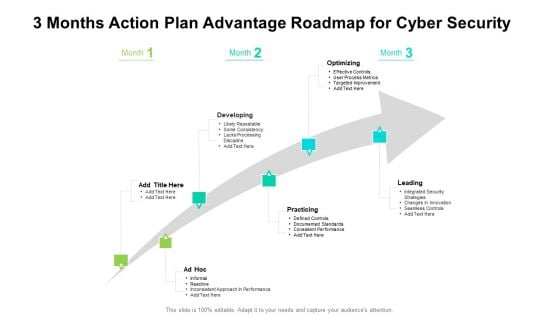
3 Months Action Plan Advantage Roadmap For Cyber Security Inspiration
We present our 3 months action plan advantage roadmap for cyber security inspiration. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched 3 months action plan advantage roadmap for cyber security inspiration in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
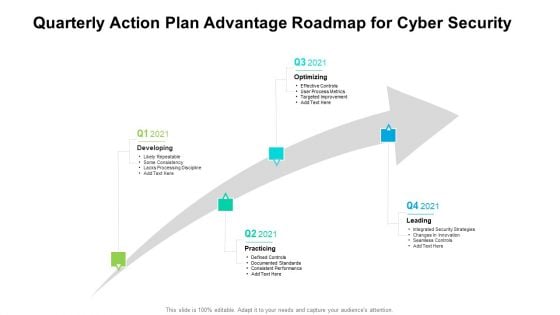
Quarterly Action Plan Advantage Roadmap For Cyber Security Sample
We present our quarterly action plan advantage roadmap for cyber security sample. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched quarterly action plan advantage roadmap for cyber security sample in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
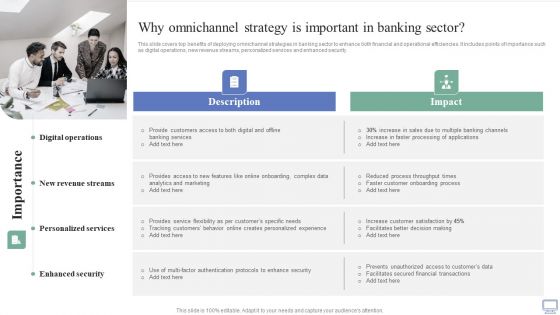
Omnichannel Banking Services Platform Why Omnichannel Strategy Is Important In Banking Sector Diagrams PDF
This slide covers top benefits of deploying omnichannel strategies in banking sector to enhance both financial and operational efficiencies. It includes points of importance such as digital operations, new revenue streams, personalized services and enhanced security. Are you searching for a Omnichannel Banking Services Platform Why Omnichannel Strategy Is Important In Banking Sector Diagrams PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Omnichannel Banking Services Platform Why Omnichannel Strategy Is Important In Banking Sector Diagrams PDF from Slidegeeks today.
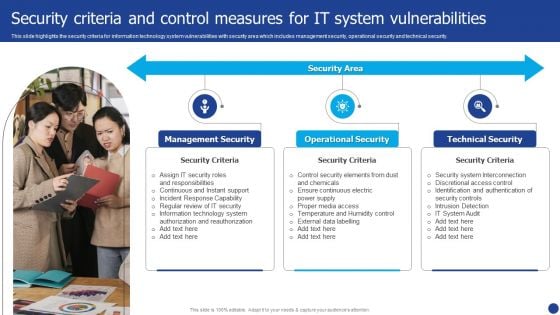
Information Technology Threat Mitigation Methods Security Criteria And Control Measures For IT System Vulnerabilities Themes PDF
This slide highlights the security criteria for information technology system vulnerabilities with security area which includes management security, operational security and technical security. Presenting Information Technology Threat Mitigation Methods Security Criteria And Control Measures For IT System Vulnerabilities Themes PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Management Security, Operational Security, Technical Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
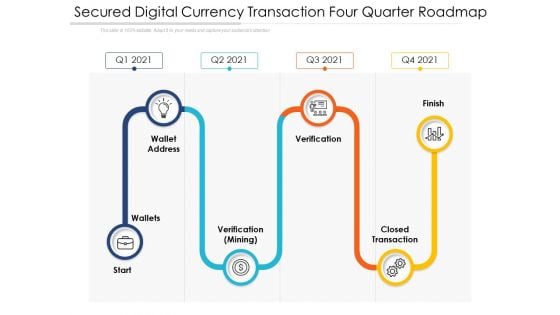
Secured Digital Currency Transaction Four Quarter Roadmap Slides
Presenting our innovatively structured secured digital currency transaction four quarter roadmap slides Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.
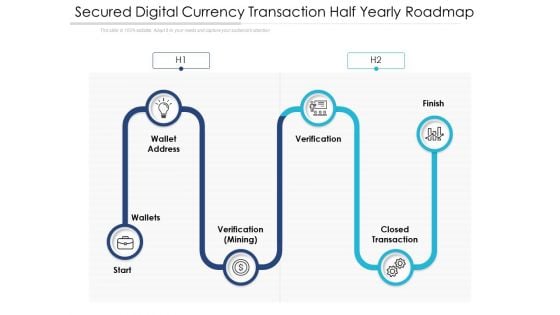
Secured Digital Currency Transaction Half Yearly Roadmap Portrait
Introducing our secured digital currency transaction half yearly roadmap portrait. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.
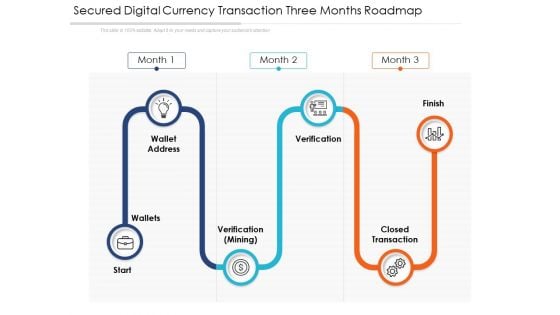
Secured Digital Currency Transaction Three Months Roadmap Graphics
Presenting our jaw dropping secured digital currency transaction three months roadmap graphics. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.

Five Year Data Sharing Security Network Career Roadmap Clipart
Introducing our five year data sharing security network career roadmap clipart. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.

 Home
Home