Safety Icons
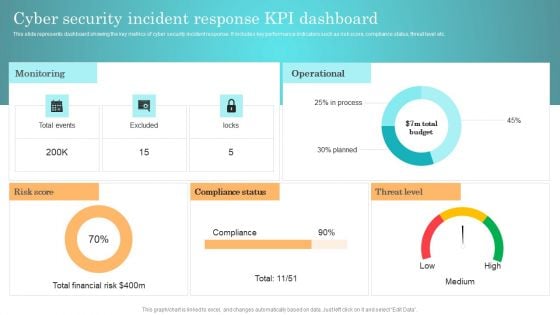
Incident Response Techniques Deployement Cyber Security Incident Response KPI Dashboard Background PDF
This slide represents dashboard showing the key metrics of cyber security incident response. It includes key performance indicators such as risk score, compliance status, threat level etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Incident Response Techniques Deployement Cyber Security Incident Handler Contact Information Guidelines PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
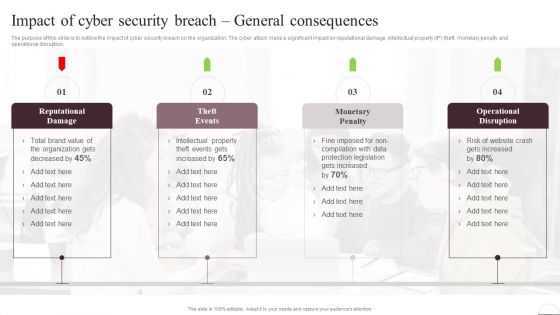
Prevention Of Information Impact Of Cyber Security Breach General Consequences Diagrams PDF
The purpose of this slide is to outline the impact of cyber security breach on the organization. The cyber attack make a significant impact on reputational damage, intellectual property IP theft, monetary penalty and operational disruption. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Prevention Of Information Impact Of Cyber Security Breach General Consequences Diagrams PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
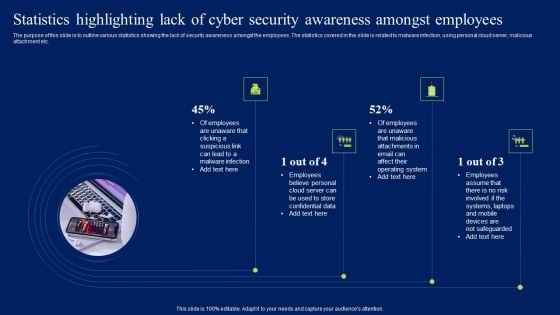
Statistics Highlighting Lack Of Cyber Security Awareness Amongst Employees Diagrams PDF
The purpose of this slide is to outline various statistics showing the lack of security awareness amongst the employees. The statistics covered in the slide is related to malware infection, using personal cloud server, malicious attachment etc. Present like a pro with Statistics Highlighting Lack Of Cyber Security Awareness Amongst Employees Diagrams PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
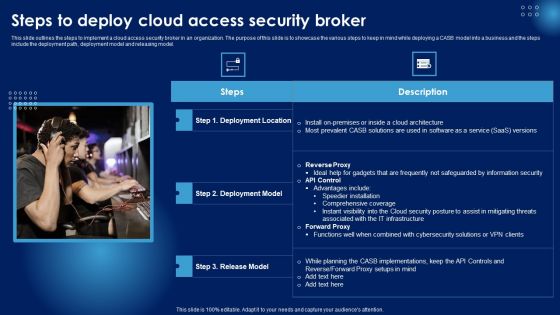
Steps To Deploy Cloud Access Security Broker Ppt PowerPoint Presentation Diagram Images PDF
This slide outlines the steps to implement a cloud access security broker in an organization. The purpose of this slide is to showcase the various steps to keep in mind while deploying a CASB model into a business and the steps include the deployment path, deployment model and releasing model. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Steps To Deploy Cloud Access Security Broker Ppt PowerPoint Presentation Diagram Images PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
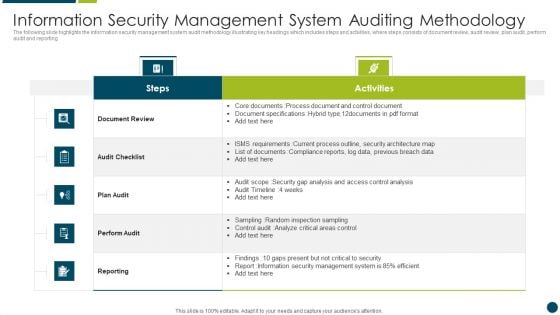
Information Security Management System Auditing Methodology Download PDF
The following slide highlights the information security system audit framework illustrating key headings which includes act, plan, do and check which are used for update and improve isms, establish isms, implement policy and control and monitor and review performance Presenting Information Security Management System Auditing Methodology Download PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Analysis, Data, Risk. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
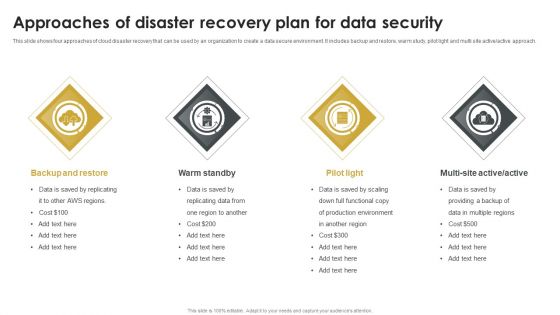
Approaches Of Disaster Recovery Plan For Data Security Topics PDF
This slide shows four approaches of cloud disaster recovery that can be used by an organization to create a data secure environment. It includes backup and restore, warm study, pilot light and multi site active or active approach. Presenting Approaches Of Disaster Recovery Plan For Data Security Topics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Warm Standby, Backup And Restore, Pilot Light. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Five Steps For Cyber IT Security Risk Analysis Graphics PDF
This slide covers the steps for analysis of risk occurring in cyber security to reduce errors and system hacks so that the information of clients remain safe. It includes finding assets, identifying consequences, threats and assessing risk. Presenting Five Steps For Cyber IT Security Risk Analysis Graphics PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Find Valuable Assets, Assess Risk, Identify Potential Consequences. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
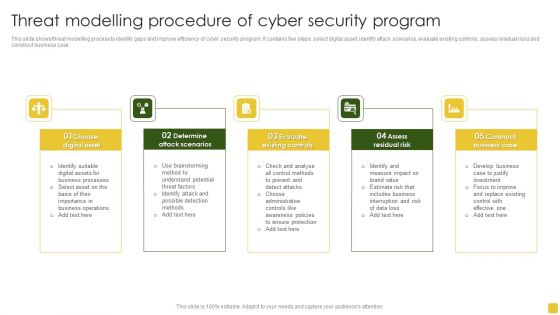
Threat Modelling Procedure Of Cyber Security Program Elements PDF
This slide shows threat modelling process to identify gaps and improve efficiency of cyber security program. It contains five steps select digital asset, identify attack scenarios, evaluate existing controls, assess residual risks and construct business case.Presenting Threat Modelling Procedure Of Cyber Security Program Elements PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Digital Asset, Attack Scenarios, Evaluate Existing. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Information Technology Security Data Breach And Trend Analysis Professional PDF
The following slide reflects some trends in information technology security to assess financial loss occurred to companies due to data breach. It includes average cost and average number of days to determine and report data breach, number of new malware detected per day etc. Presenting Information Technology Security Data Breach And Trend Analysis Professional PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Data Breach, Average Cost, Determine. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
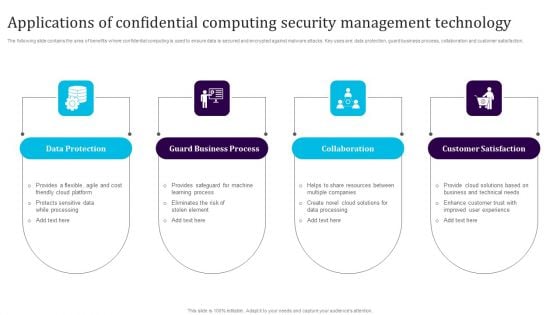
Applications Of Confidential Computing Security Management Technology Sample PDF
The following slide contains the area of benefits where confidential computing is used to ensure data is secured and encrypted against malware attacks. Key uses are data protection, guard business process, collaboration and customer satisfaction. Presenting Applications Of Confidential Computing Security Management Technology Sample PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Data Protection, Guard Business Process, Collaboration, Customer Satisfaction. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Digital Banking Security Management Technology Trends Introduction PDF
The following slide provides the integration of security technology with banking which helps to provide improved and enhanced customer experience. Key components are login protection, artificial intelligence and cloud computing. Presenting Digital Banking Security Management Technology Trends Introduction PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Login Protection, Ai, Cloud Computing. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Country Wise Security Strategies For Digital Terrorism Professional PDF
This slide shows various strategies adopted by different countries to eliminate threat of cyber attacks. It include various risk area covered such as Hostile cyber attacks, International Cyber Attacks etc. Presenting Country Wise Security Strategies For Digital Terrorism Professional PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including National Strategy, Cyber Security, International Cyber. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Smart Phone Device Security Best Practices Structure PDF
This slide shows key practices for protecting business data of mobile. The purpose of this slide is to highlight latest practices that can be used for securing mobile data. It include practices such as enable user authentication, update OS system, etc. Presenting Smart Phone Device Security Best Practices Structure PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Enable User Authentication, Avoid Using Public Wi Fi, Follow BYOD Policy. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
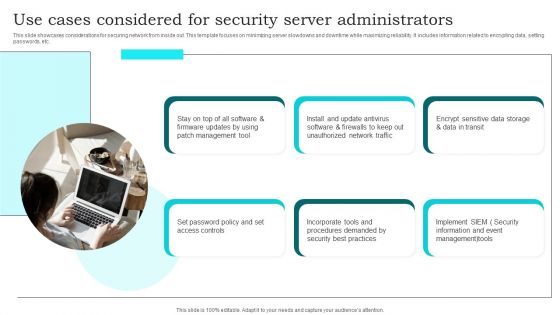
Use Cases Considered For Security Server Administrators Brochure PDF
This slide showcases considerations for securing network from inside out. This template focuses on minimizing server slowdowns and downtime while maximizing reliability. It includes information related to encrypting data, setting passwords, etc. Presenting Use Cases Considered For Security Server Administrators Brochure PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Management Tool, Set Password Policy, Unauthorized Network Traffic. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
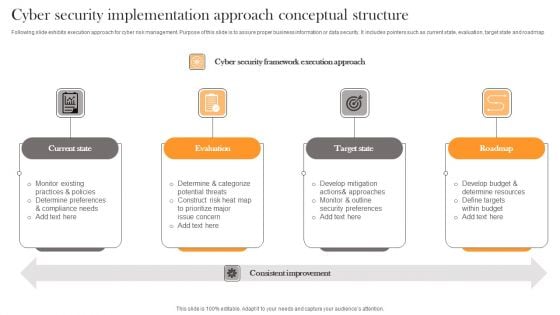
Cyber Security Implementation Approach Conceptual Structure Professional PDF
Following slide exhibits execution approach for cyber risk management. Purpose of this slide is to assure proper business information or data security. It includes pointers such as current state, evaluation, target state and roadmap. Presenting Cyber Security Implementation Approach Conceptual Structure Professional PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Current State, Evaluation, Target State . This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
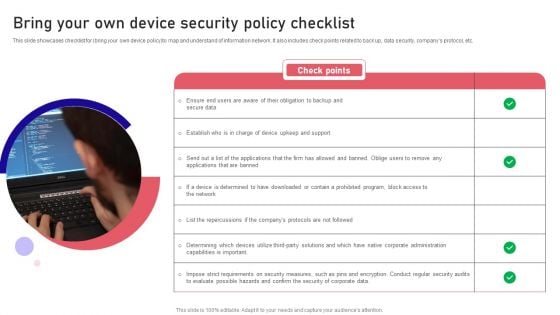
Bring Your Own Device Security Policy Checklist Graphics PDF
This slide showcases checklist for bring your own device policy to map and understand of information network. It also includes check points related to back up, data security, companys protocol, etc. Presenting Bring Your Own Device Security Policy Checklist Graphics PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Check Points, Checklist, Device. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
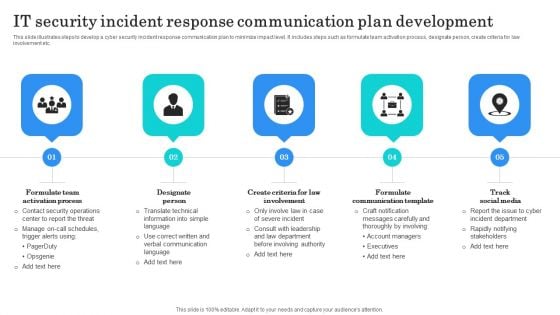
IT Security Incident Response Communication Plan Development Background PDF
This slide illustrates steps to develop a cyber security incident response communication plan to minimize impact level. It includes steps such as formulate team activation process, designate person, create criteria for law involvement etc. Presenting IT Security Incident Response Communication Plan Development Background PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Formulate Team Activation, Designate Person, Formulate Communication Template. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
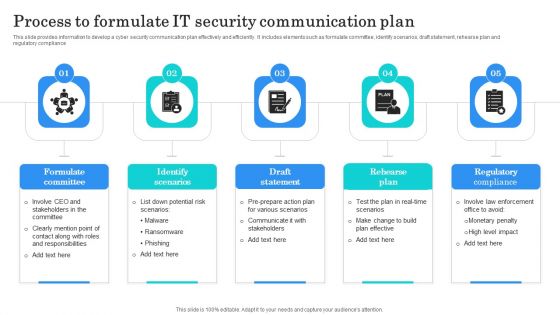
Process To Formulate IT Security Communication Plan Clipart PDF
This slide provides information to develop a cyber security communication plan effectively and efficiently. It includes elements such as formulate committee, identify scenarios, draft statement, rehearse plan and regulatory compliance. Presenting Process To Formulate IT Security Communication Plan Clipart PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Formulate Committee, Identify Scenarios, Draft Statement. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
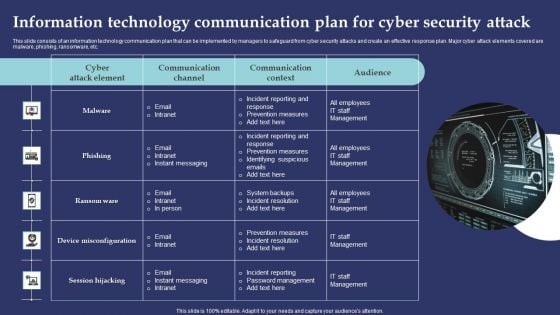
Information Technology Communication Plan For Cyber Security Attack Summary PDF
This slide consists of an information technology communication plan that can be implemented by managers to safeguard from cyber security attacks and create an effective response plan. Major cyber attack elements covered are malware, phishing, ransomware, etc. Presenting Information Technology Communication Plan For Cyber Security Attack Summary PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Incident Reporting Response, Prevention Measures, Incident Reporting. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
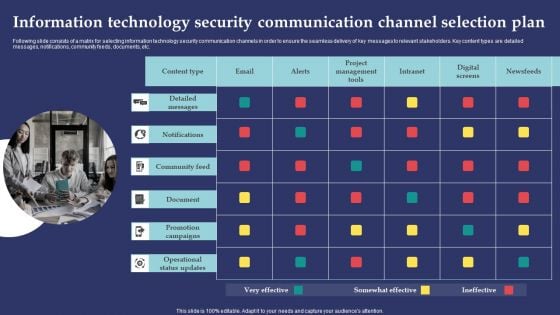
Information Technology Security Communication Channel Selection Plan Template PDF
Following slide consists of a matrix for selecting information technology security communication channels in order to ensure the seamless delivery of key messages to relevant stakeholders. Key content types are detailed messages, notifications, community feeds, documents, etc. Presenting Information Technology Security Communication Channel Selection Plan Template PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Detailed Message, Notifications, Community Feed. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Information Technology Security Crisis Communication Plan Checklist Professional PDF
Following slide presents an information technology security crisis communication plan checklist that can be used by information technology managers to ensure the effective preparation of a communication plan. Key elements covered in the checklist are identifying office protocol, creating a list of IT terms, etc. Presenting Information Technology Security Crisis Communication Plan Checklist Professional PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Communications Team, Internal Communication Plan, Dissemination Information. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
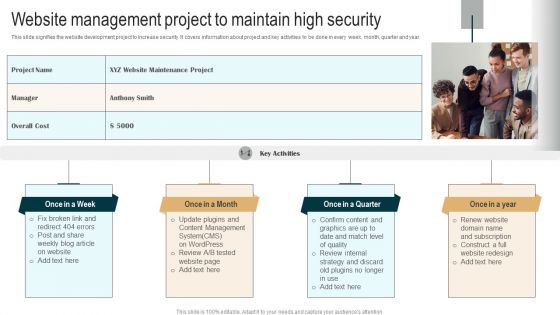
Website Management Project To Maintain High Security Demonstration PDF
This slide signifies the website development project to increase security. It covers information about project and key activities to be done in every week, month, quarter and year. Presenting Website Management Project To Maintain High Security Demonstration PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Fix broken link, Update plugins, Confirm content. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
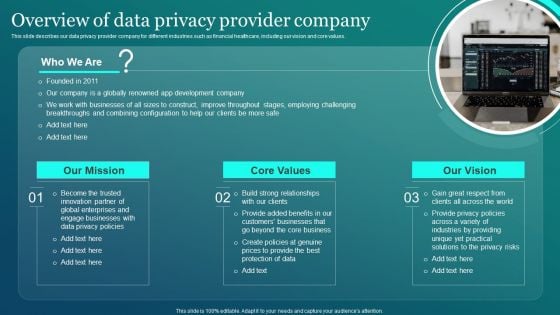
Information Security Overview Of Data Privacy Provider Company Background PDF
This slide describes our data privacy provider company for different industries such as financial healthcare, including our vision and core values. Retrieve professionally designed Information Security Overview Of Data Privacy Provider Company Background PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
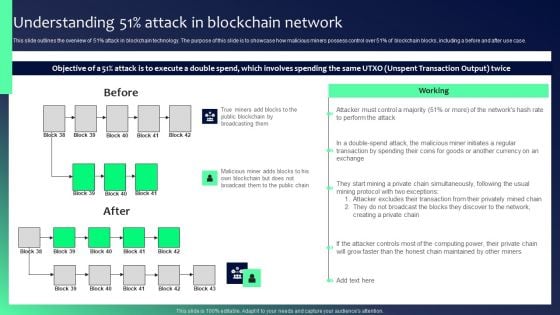
Blockchain Security Solutions Deployment Understanding 51 Percent Attack Sample PDF
This slide outlines the overview of 51 percent attack in blockchain technology. The purpose of this slide is to showcase how malicious miners possess control over 51 percent of blockchain blocks, including a before and after use case. Retrieve professionally designed Blockchain Security Solutions Deployment Understanding 51 Percent Attack Sample PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
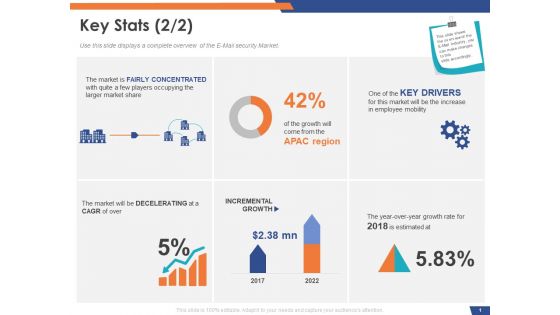
Email Security Market Research Report Key Stats Ppt Gallery Design Inspiration PDF
Presenting this set of slides with name email security market research report key stats ppt gallery design inspiration pdf. The topics discussed in these slides are incremental growth, key drivers, the market is fairly concentrated with quite a few players occupying the larger market share. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

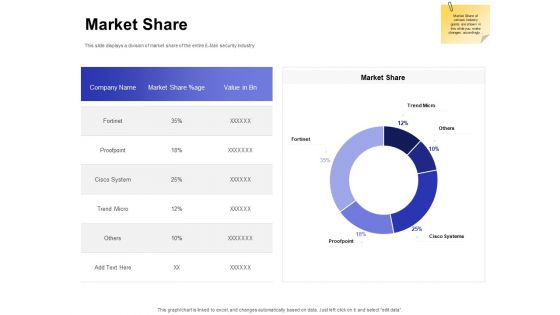
Email Security Market Research Report Market Share Ppt Show Infographics PDF
Presenting this set of slides with name email security market research report market share ppt show infographics pdf. The topics discussed in these slides are company name, market share, value. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
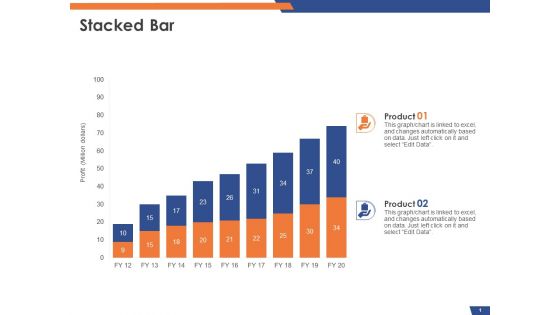
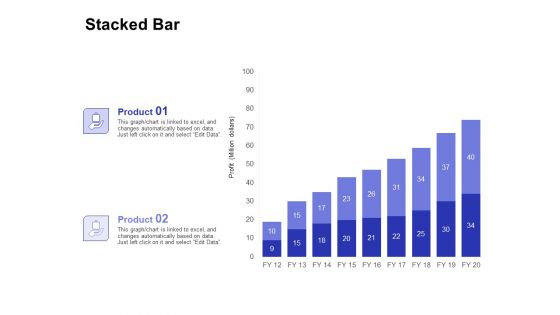
Email Security Market Research Report Stacked Bar Ppt Styles Slide PDF
Presenting this set of slides with name email security market research report stacked bar ppt styles slide pdf. The topics discussed in these slides are product 1, product 2. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Global Cloud Based Email Security Market Market Share Ppt Portfolio Layouts PDF
Presenting this set of slides with name global cloud based email security market market share ppt portfolio layouts pdf. The topics discussed in these slides are company name, market share, value. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Global Cloud Based Email Security Market Stacked Bar Ppt Ideas Infographics PDF
Presenting this set of slides with name global cloud based email security market stacked bar ppt ideas infographics pdf. The topics discussed in these slides are product 1, product 2. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Computer Security Incident Handling Analyzing IT Department On Nist Cybersecurity Framework Introduction PDF
Presenting this set of slides with name computer security incident handling analyzing it department on nist cybersecurity framework introduction pdf. The topics discussed in these slides are identify, detect, protect, respond, recover. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
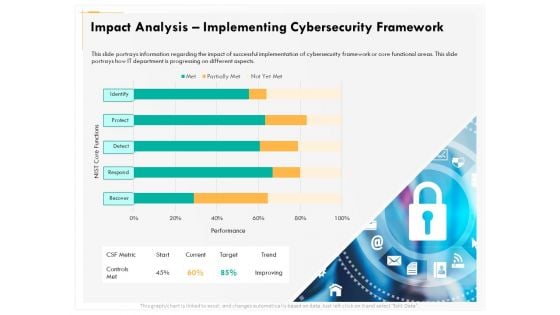
Computer Security Incident Handling Impact Analysis Implementing Cybersecurity Framework Designs PDF
Presenting this set of slides with name computer security incident handling impact analysis implementing cybersecurity framework designs pdf. The topics discussed in these slides are recover, detect, respond, protect, identify. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
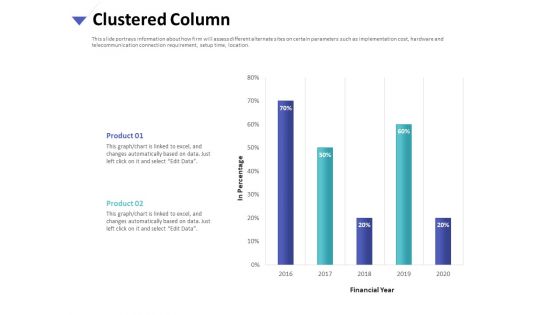
Strategies To Mitigate Cyber Security Risks Clustered Column Ppt Inspiration Example PDF
Presenting this set of slides with name strategies to mitigate cyber security risks clustered column ppt inspiration example pdf. The topics discussed in these slide is clustered column. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Strategies To Mitigate Cyber Security Risks Dashboard Ppt File Brochure PDF
Presenting this set of slides with name strategies to mitigate cyber security risks dashboard ppt file brochure pdf. The topics discussed in these slide is dashboard. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
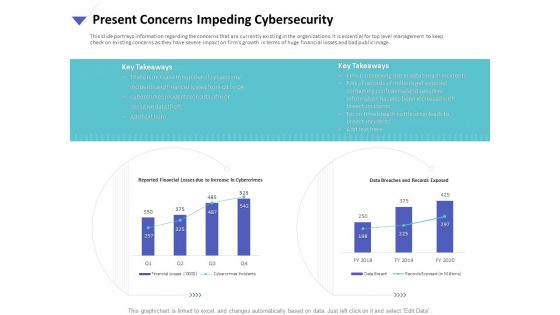
Strategies To Mitigate Cyber Security Risks Present Concerns Impeding Cybersecurity Ppt Show Objects PDF
Presenting this set of slides with name strategies to mitigate cyber security risks present concerns impeding cybersecurity ppt show objects pdf. The topics discussed in these slides are reported financial losses due increase cybercrimes, data breaches and records exposed, key takeaways. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
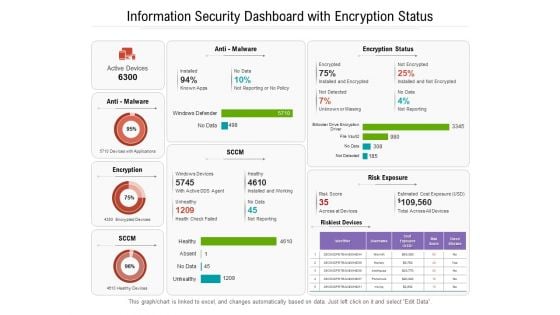
Information Security Dashboard With Encryption Status Ppt PowerPoint Presentation Gallery Pictures PDF
Presenting this set of slides with name information security dashboard with encryption status ppt powerpoint presentation gallery pictures pdf. The topics discussed in these slides are devices, cost, malware. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
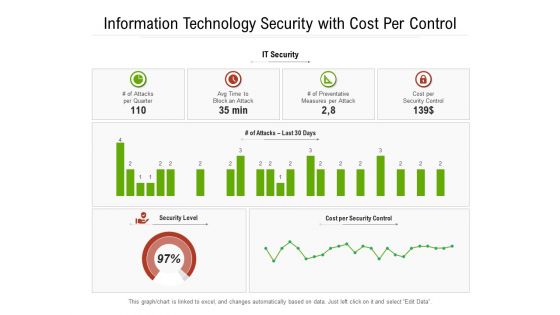
Information Technology Security With Cost Per Control Ppt PowerPoint Presentation Gallery Maker PDF
Presenting this set of slides with name information technology security with cost per control ppt powerpoint presentation gallery maker pdf. The topics discussed in these slides are cost, quarter, measures. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
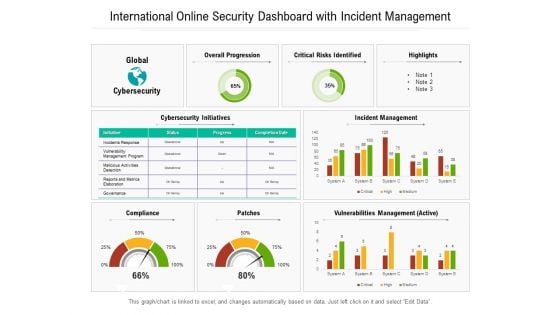
International Online Security Dashboard With Incident Management Ppt PowerPoint Presentation File Background PDF
Presenting this set of slides with name international online security dashboard with incident management ppt powerpoint presentation file background pdf. The topics discussed in these slides are management, vulnerabilities, cybersecurity. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
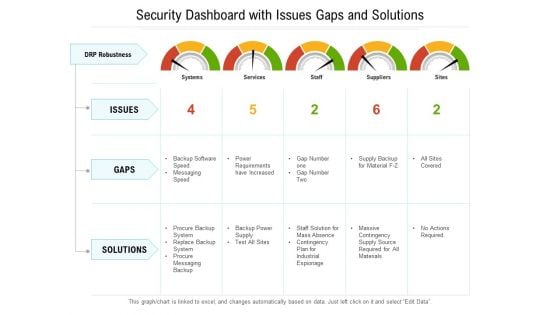
Security Dashboard With Issues Gaps And Solutions Ppt PowerPoint Presentation File Structure PDF
Presenting this set of slides with name security dashboard with issues gaps and solutions ppt powerpoint presentation file structure pdf. The topics discussed in these slides are issues, gaps, solutions. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
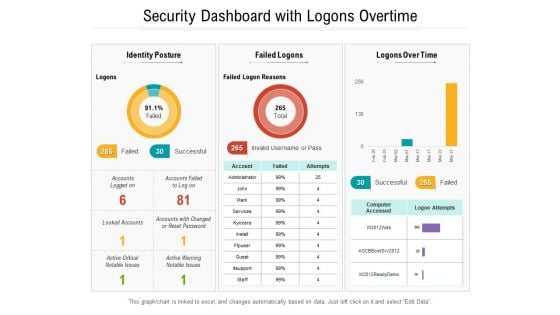
Security Dashboard With Logons Overtime Ppt PowerPoint Presentation Gallery Graphics Design PDF
Presenting this set of slides with name security dashboard with logons overtime ppt powerpoint presentation gallery graphics design pdf. The topics discussed in these slides are identity posture, failed logons, logons over time. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security Implementation Framework Dashboard Cyber Risk Management Ppt Outline Structure PDF
Presenting this set of slides with name cyber security implementation framework dashboard cyber risk management ppt outline structure pdf. The topics discussed in these slides are risk rating breakdown, risk analysis progress, average risk threshold, response progress for risks. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security Implementation Framework Impact Analysis Implementing Cybersecurity Framework Ppt Show Graphics PDF
Presenting this set of slides with name cyber security implementation framework impact analysis implementing cybersecurity framework ppt show graphics pdf. The topics discussed in these slides are csf metric, controls met, nist core functions, target, trend. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
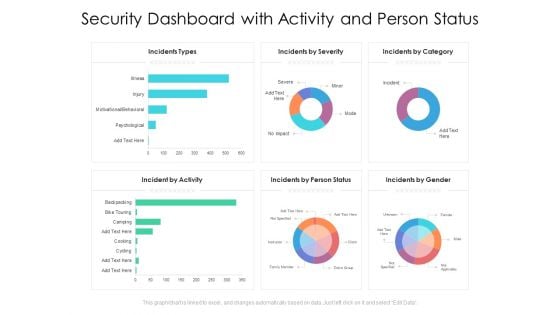
Security Dashboard With Activity And Person Status Ppt PowerPoint Presentation File Shapes PDF
Presenting this set of slides with name security dashboard with activity and person status ppt powerpoint presentation file shapes pdf. The topics discussed in these slides are incidents types, incidents by severity, incidents by category, incident by activity, incidents by person status, incidents by gender. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
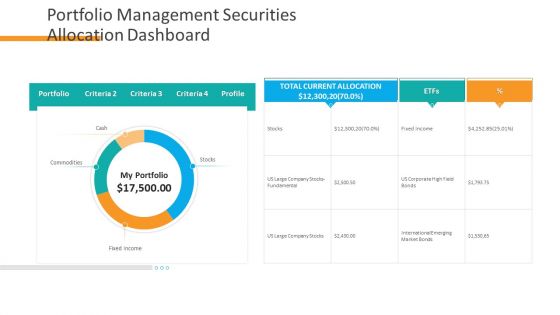
Organizational Financial Assets Assessment Portfolio Management Securities Allocation Dashboard Brochure PDF
Deliver and pitch your topic in the best possible manner with this organizational financial assets assessment portfolio management securities allocation dashboard brochure pdf. Use them to share invaluable insights on portfolio, commodities and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
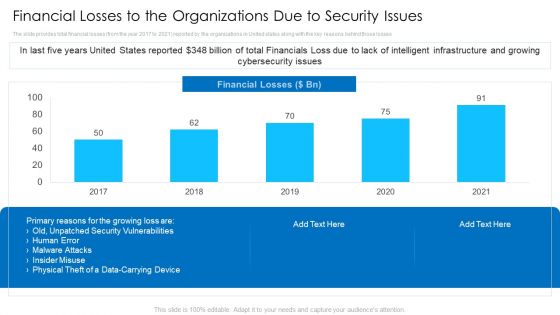
Financial Losses To The Organizations Due To Security Issues Mockup PDF
Deliver an awe inspiring pitch with this creative financial losses to the organizations due to security issues mockup pdf bundle. Topics like physical theft of a data carrying device, malware attacks, insider misuse can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
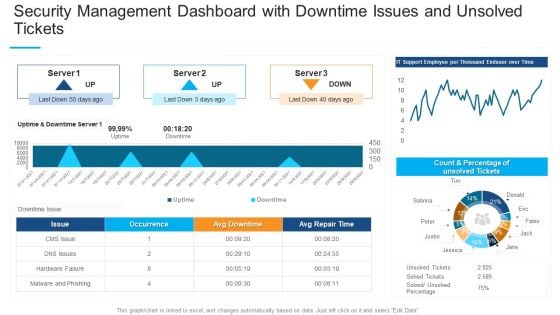
Security Management Dashboard With Downtime Issues And Unsolved Tickets Professional PDF
Deliver and pitch your topic in the best possible manner with this security management dashboard with downtime issues and unsolved tickets professional pdf. Use them to share invaluable insights on occurrence, malware and phishing, count and percentage and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
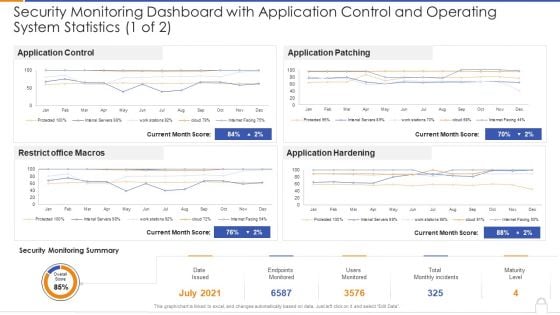
Security Monitoring Dashboard With Application Control And Operating System Statistics 1 Of 2 Ideas PDF
Deliver and pitch your topic in the best possible manner with thissecurity monitoring dashboard with application control and operating system statistics 1 of 2 ideas pdf Use them to share invaluable insights on security monitoring dashboard with application control and operating system statistics and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
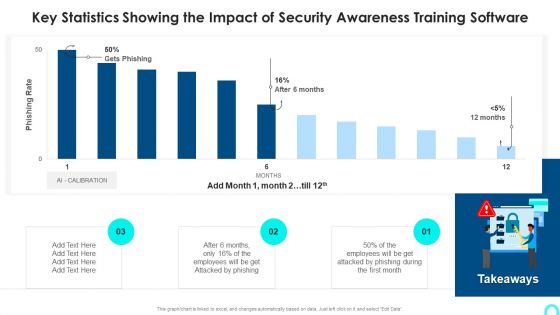
Key Statistics Showing The Impact Of Security Awareness Training Software Information PDF
Deliver an awe inspiring pitch with this creative Key Statistics Showing The Impact Of Security Awareness Training Software Information PDF bundle. Topics like Attacked Phishing, Employees Will, Phishing During can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
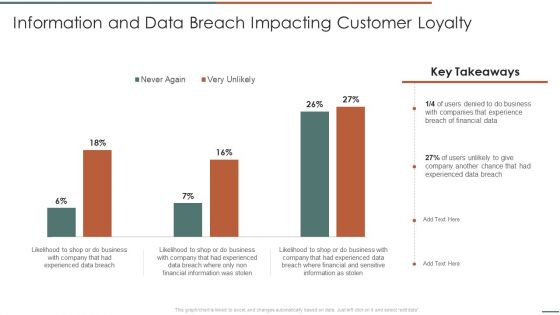
Information Security Risk Evaluation Information And Data Breach Impacting Customer Loyalty Structure PDF
Deliver an awe inspiring pitch with this creative Information Security Risk Evaluation Information And Data Breach Impacting Customer Loyalty Structure PDF bundle. Topics like Companies Experience, Financial Information, Breach Of Financial can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Managing Cyber Security In Manufacturing 30 Days Plan Portrait PDF
This slide describes the first 30 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. Are you searching for a Managing Cyber Security In Manufacturing 30 Days Plan Portrait PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Managing Cyber Security In Manufacturing 30 Days Plan Portrait PDF from Slidegeeks today.
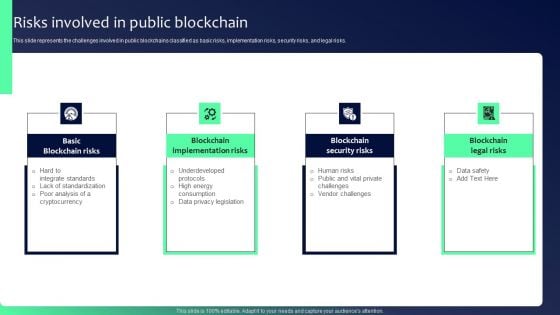
Blockchain Security Solutions Deployment Risks Involved In Public Rules PDF
This slide represents the challenges involved in public blockchains classified as basic risks, implementation risks, security risks, and legal risks. Are you searching for a Blockchain Security Solutions Deployment Risks Involved In Public Rules PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Blockchain Security Solutions Deployment Risks Involved In Public Rules PDF from Slidegeeks today.
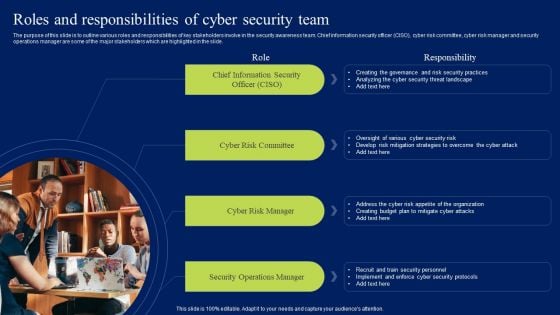
Roles And Responsibilities Of Cyber Security Team Ppt Portfolio
The purpose of this slide is to outline various roles and responsibilities of key stakeholders involve in the security awareness team. Chief information security officer CISO, cyber risk committee, cyber risk manager and security operations manager are some of the major stakeholders which are highlighted in the slide. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Roles And Responsibilities Of Cyber Security Team Ppt Portfolio can be your best option for delivering a presentation. Represent everything in detail using Roles And Responsibilities Of Cyber Security Team Ppt Portfolio and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
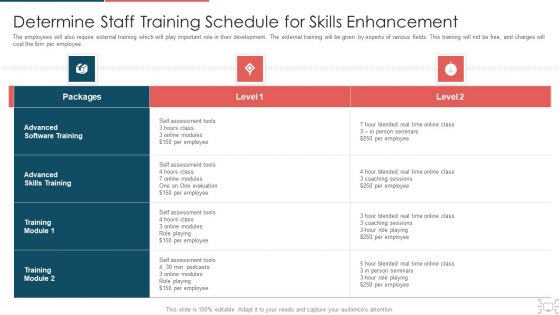
Cyber Security Administration In Organization Determine Staff Training Schedule For Skills Diagrams PDF
The employees will also require external training which will play important role in their development. The external training will be given by experts of various fields. This training will not be free, and charges will cost the firm per employee. Deliver an awe inspiring pitch with this creative cyber security administration in organization determine staff training schedule for skills diagrams pdf bundle. Topics like determine staff training schedule for skills enhancement can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
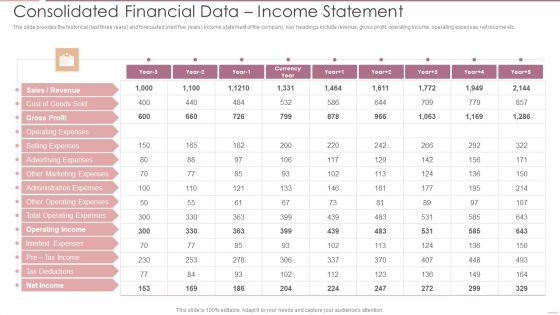
Investment Banking Security Underwriting Pitchbook Consolidated Financial Data Income Statement Diagrams PDF
The slide provides the historical last three years and forecasted next five years income statement of the company. Key headings include revenue, gross profit, operating income, operating expenses, net income etc.Deliver and pitch your topic in the best possible manner with this Investment Banking Security Underwriting Pitchbook Consolidated Financial Data Income Statement Diagrams PDF Use them to share invaluable insights on Gross Profit, Operating Expenses, Advertising Expenses and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
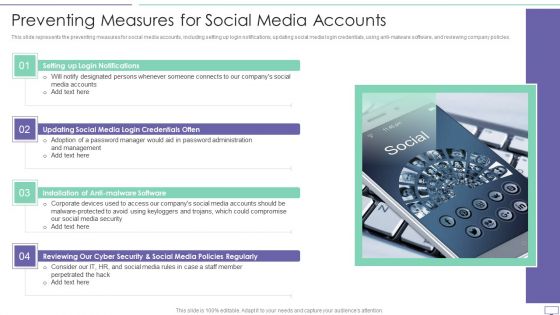
IT Security Hacker Preventing Measures For Social Media Accounts Diagrams PDF
This slide represents the preventing measures for social media accounts, including setting up login notifications, updating social media login credentials, using anti-malware software, and reviewing company policies.Presenting IT Security Hacker Preventing Measures For Social Media Accounts Diagrams PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Login Notifications, Malware Software, Policies Regularly. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
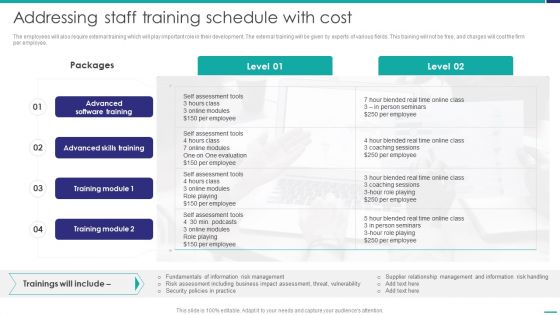
Addressing Staff Training Schedule With Cost Mobile Device Security Management Diagrams PDF
The employees will also require external training which will play important role in their development. The external training will be given by experts of various fields. This training will not be free, and charges will cost the firm per employee. Deliver an awe inspiring pitch with this creative Addressing Staff Training Schedule With Cost Mobile Device Security Management Diagrams PDF bundle. Topics like Advanced Skills, Coaching Sessions, Assessment Tools can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Organizing Security Awareness Various Techniques To Successfully Prevent Business Email Diagrams PDF
The purpose of this slide is to outline different techniques which can be used to protect organization from business email compromise attack. The techniques covered in the slide are sender policy framework SPF, using strong password policy and process for wire transfers. Find a pre-designed and impeccable Organizing Security Awareness Various Techniques To Successfully Prevent Business Email Diagrams PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Table Of Contents Security Automation To Analyze And Mitigate Cyberthreats Diagrams PDF
Slidegeeks has constructed Table Of Contents Security Automation To Analyze And Mitigate Cyberthreats Diagrams PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.
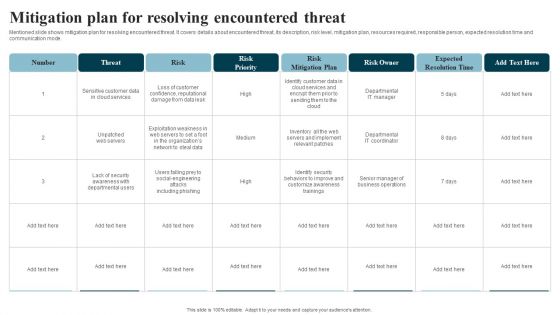
Developing IT Security Strategy Mitigation Plan For Resolving Encountered Threat Diagrams PDF
Mentioned slide shows mitigation plan for resolving encountered threat. It covers details about encountered threat, its description, risk level, mitigation plan, resources required, responsible person, expected resolution time and communication mode. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Developing IT Security Strategy Mitigation Plan For Resolving Encountered Threat Diagrams PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.
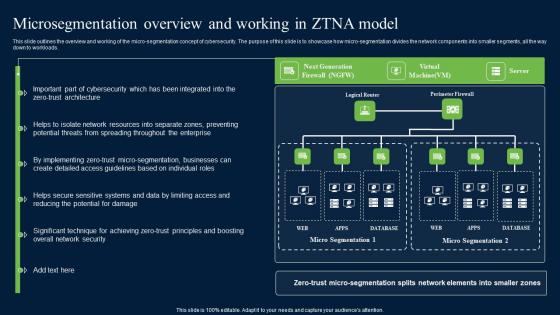
Microsegmentation Overview And Working In ZTNA Zero Trust Network Security Diagrams Pdf
This slide outlines the overview and working of the micro-segmentation concept of cybersecurity. The purpose of this slide is to showcase how micro-segmentation divides the network components into smaller segments, all the way down to workloads. Explore a selection of the finest Microsegmentation Overview And Working In ZTNA Zero Trust Network Security Diagrams Pdf here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Microsegmentation Overview And Working In ZTNA Zero Trust Network Security Diagrams Pdf to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide outlines the overview and working of the micro-segmentation concept of cybersecurity. The purpose of this slide is to showcase how micro-segmentation divides the network components into smaller segments, all the way down to workloads.

Step 6 And 7 Define Operational Changes And Zero Trust Network Security Diagrams Pdf
This slide outlines the sixth and seventh steps for ZTNA implementation, which are defining operational changes and implementing, rinsing and repeating the process. The purpose of this slide is to showcase the following steps in zero trust model deployment. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Step 6 And 7 Define Operational Changes And Zero Trust Network Security Diagrams Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Step 6 And 7 Define Operational Changes And Zero Trust Network Security Diagrams Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide outlines the sixth and seventh steps for ZTNA implementation, which are defining operational changes and implementing, rinsing and repeating the process. The purpose of this slide is to showcase the following steps in zero trust model deployment.
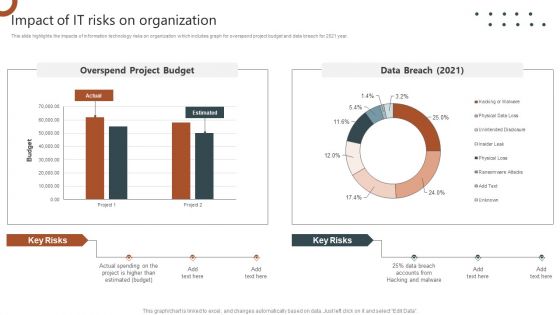
Organizations Risk Management And IT Security Impact Of IT Risks On Organization Structure PDF
This slide highlights the impacts of information technology risks on organization which includes graph for overspend project budget and data breach for 2021 year. Explore a selection of the finest Organizations Risk Management And IT Security Impact Of IT Risks On Organization Structure PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Organizations Risk Management And IT Security Impact Of IT Risks On Organization Structure PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Certified Information Systems Security Professional CISSP Examination Details IT Certifications To Enhance Pictures PDF
This slide covers information about CISSP Examination such as weight of each domain in exams, prep courses details, qualification details etc.Find highly impressive Certified Information Systems Security Professional CISSP Examination Details IT Certifications To Enhance Pictures PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Certified Information Systems Security Professional CISSP Examination Details IT Certifications To Enhance Pictures PDF for your upcoming presentation. All the presentation templates are 100 precent editable and you can change the color and personalize the content accordingly. Download now.
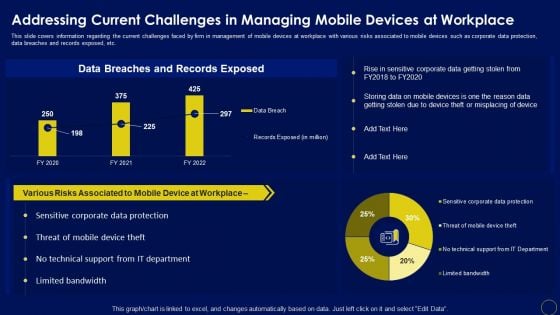
Addressing Current Challenges In Managing Business Mobile Device Security Management Summary PDF
This slide covers information regarding the current challenges faced by firm in management of mobile devices at workplace with various risks associated to mobile devices such as corporate data protection, data breaches and records exposed, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Addressing Current Challenges In Managing Business Mobile Device Security Management Summary PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Addressing Current Challenges In Managing Business Mobile Device Security Management Summary PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.
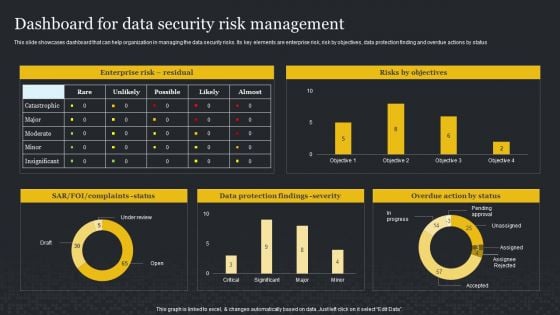
Dashboard For Data Security Risk Management Cybersecurity Risk Assessment Template PDF
This slide showcases dashboard that can help organization in managing the data security risks. Its key elements are enterprise risk, risk by objectives, data protection finding and overdue actions by status. Welcome to our selection of the Dashboard For Data Security Risk Management Cybersecurity Risk Assessment Template PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 parcent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.
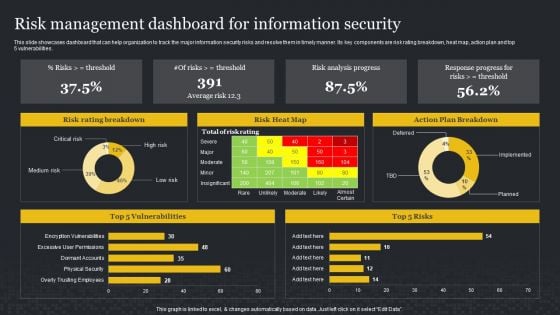
Risk Management Dashboard For Information Security Cybersecurity Risk Assessment Sample PDF
This slide showcases dashboard that can help organization to track the major information security risks and resolve them in timely manner. Its key components are risk rating breakdown, heat map, action plan and top 5 vulnerabilities. This Risk Management Dashboard For Information Security Cybersecurity Risk Assessment Sample PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
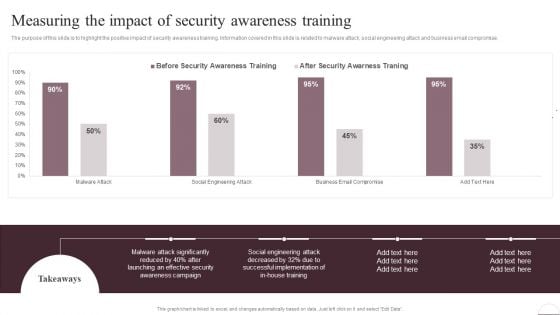
Prevention Of Information Measuring The Impact Of Security Awareness Training Ideas PDF
The purpose of this slide is to highlight the positive impact of security awareness training. Information covered in this slide is related to malware attack, social engineering attack and business email compromise. The Prevention Of Information Measuring The Impact Of Security Awareness Training Ideas PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
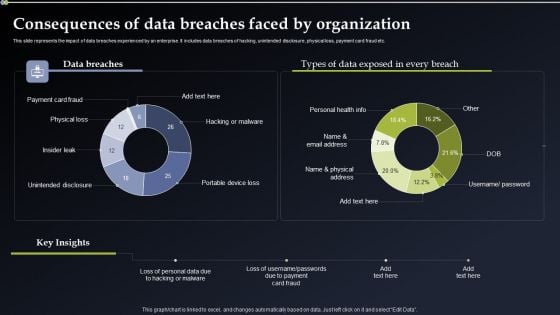
Deploying Cyber Security Incident Response Administration Consequences Of Data Breaches Portrait PDF
This slide represents the impact of data breaches experienced by an enterprise. It includes data breaches of hacking, unintended disclosure, physical loss, payment card fraud etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Deploying Cyber Security Incident Response Administration Consequences Of Data Breaches Portrait PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Deploying Cyber Security Incident Response Administration Consequences Of Data Breaches Portrait PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
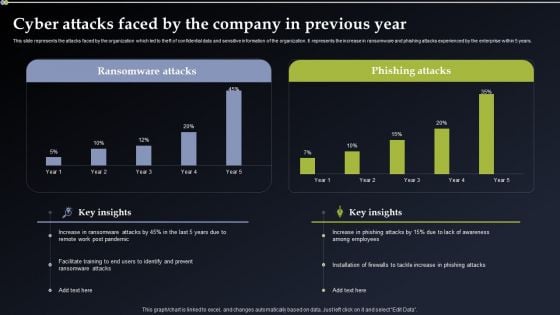
Deploying Cyber Security Incident Response Administration Cyber Attacks Faced By The Company Sample PDF
This slide represents the attacks faced by the organization which led to theft of confidential data and sensitive information of the organization. It represents the increase in ransomware and phishing attacks experienced by the enterprise within 5 years. Get a simple yet stunning designed Deploying Cyber Security Incident Response Administration Cyber Attacks Faced By The Company Sample PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Deploying Cyber Security Incident Response Administration Cyber Attacks Faced By The Company Sample PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

KYC Transaction Monitoring System Business Security Analyzing Impact On Key Operations Ideas PDF
This slide showcases assessing impact on major operations and workflows. It provides information about customer understanding, knowledge, data management, financial risk management, customer relationship management, client onboarding, etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download KYC Transaction Monitoring System Business Security Analyzing Impact On Key Operations Ideas PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the KYC Transaction Monitoring System Business Security Analyzing Impact On Key Operations Ideas PDF.
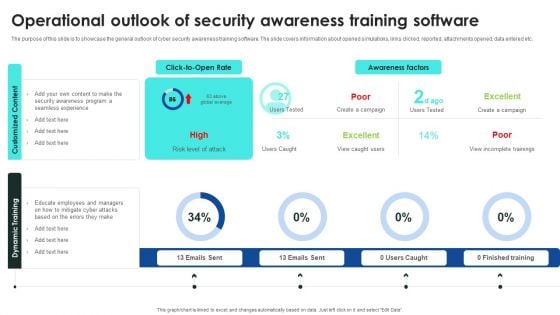
Implementing Cybersecurity Awareness Program To Prevent Attacks Operational Outlook Of Security Awareness Elements PDF
The purpose of this slide is to showcase the general outlook of cyber security awareness training software. The slide covers information about opened simulations, links clicked, reported, attachments opened, data entered etc. Slidegeeks has constructed Implementing Cybersecurity Awareness Program To Prevent Attacks Operational Outlook Of Security Awareness Elements PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.

Incident Response Techniques Deployement Cyber Security Systems Monitoring Report Microsoft PDF
This slide represents the report to effectively monitor the networks and systems of the organization. It includes kpis such as total intrusion attempts, mean detect team, mean resolve time etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Incident Response Techniques Deployement Cyber Security Systems Monitoring Report Microsoft PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Incident Response Techniques Deployement Cyber Security Systems Monitoring Report Microsoft PDF today and make your presentation stand out from the rest.
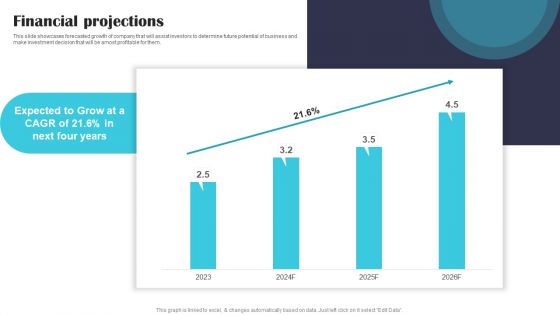
Security Software Company Investor Funding Pitch Deck Financial Projections Information PDF
This slide showcases forecasted growth of company that will assist investors to determine future potential of business and make investment decision that will be amost profitable for them. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Security Software Company Investor Funding Pitch Deck Financial Projections Information PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Security Software Company Investor Funding Pitch Deck Financial Projections Information PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.
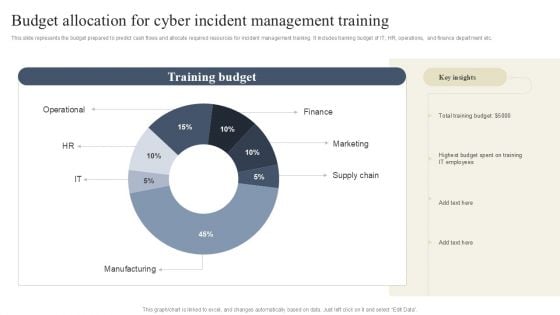
CYBER Security Breache Response Strategy Budget Allocation For Cyber Incident Management Training Topics PDF
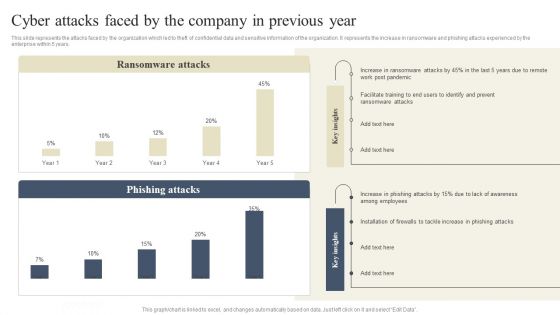
CYBER Security Breache Response Strategy Cyber Attacks Faced By The Company In Previous Year Information PDF
This slide represents the attacks faced by the organization which led to theft of confidential data and sensitive information of the organization. It represents the increase in ransomware and phishing attacks experienced by the enterprise within 5 years. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give CYBER Security Breache Response Strategy Cyber Attacks Faced By The Company In Previous Year Information PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable CYBER Security Breache Response Strategy Cyber Attacks Faced By The Company In Previous Year Information PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
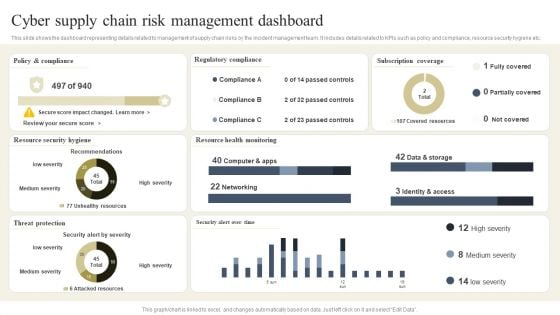
CYBER Security Breache Response Strategy Cyber Supply Chain Risk Management Dashboard Inspiration PDF
This slide shows the dashboard representing details related to management of supply chain risks by the incident management team. It includes details related to KPIs such as policy and compliance, resource security hygiene etc. The CYBER Security Breache Response Strategy Cyber Supply Chain Risk Management Dashboard Inspiration PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
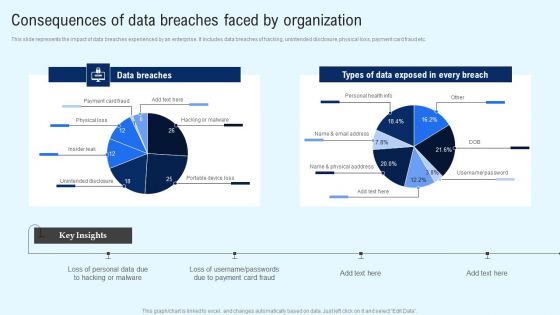
Implementing Cyber Security Incident Consequences Of Data Breaches Faced By Organization Infographics PDF
This slide represents the impact of data breaches experienced by an enterprise. It includes data breaches of hacking, unintended disclosure, physical loss, payment card fraud etc. Create an editable Implementing Cyber Security Incident Consequences Of Data Breaches Faced By Organization Infographics PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre designed presentation templates help save time. Implementing Cyber Security Incident Consequences Of Data Breaches Faced By Organization Infographics PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
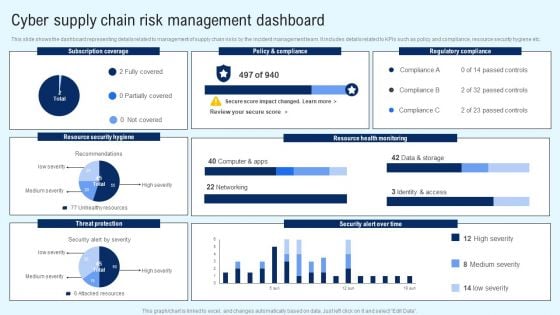
Implementing Cyber Security Incident Cyber Supply Chain Risk Dashboard Download PDF
This slide shows the dashboard representing details related to management of supply chain risks by the incident management team. It includes details related to KPIs such as policy and compliance, resource security hygiene etc. Slidegeeks is here to make your presentations a breeze with Implementing Cyber Security Incident Cyber Supply Chain Risk Dashboard Download PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
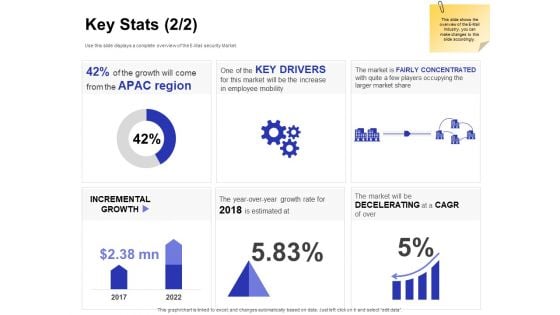
Global Cloud Based Email Security Market Key Stats Drivers Ppt Professional Background PDF
Presenting this set of slides with name global cloud based email security market key stats drivers ppt professional background pdf. The topics discussed in these slides are incremental growth, key drivers, the market is fairly concentrated with quite a few players occupying the larger market share. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
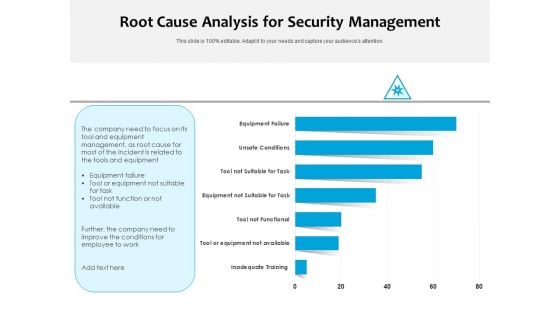
Root Cause Analysis For Security Management Ppt PowerPoint Presentation Slides Grid PDF
Pitch your topic with ease and precision using this root cause analysis for security management ppt powerpoint presentation slides grid pdf. This layout presents information on inadequate training, tool or equipment not available, tool not functional, equipment not suitable for task, tool not suitable for task, unsafe conditions, equipment failure. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Detail Impact Security Awareness Training Can Reduce The Risk Of A Data Breach Professional PDF
This slide covers the impact of data breaching threats such as phishing breakdown, network intrusion breakdown, system misconfiguration, stolen or lost devices or records and inadvertent disclosure. Deliver an awe-inspiring pitch with this creative detail impact security awareness training can reduce the risk of a data breach professional pdf bundle. Topics like phishing breakdown, network intrusion breakdown can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Detail Impact Security Awareness Training Can Reduce The Risk Of A Data Breach Information PDF
This slide covers the impact of data breaching threats such as phishing breakdown, network intrusion breakdown, system misconfiguration, stolen or lost devices or records and inadvertent disclosure. Deliver an awe-inspiring pitch with this creative detail impact security awareness training can reduce the risk of a data breach information pdf bundle. Topics like phishing breakdown, network intrusion breakdown, system misconfiguration can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
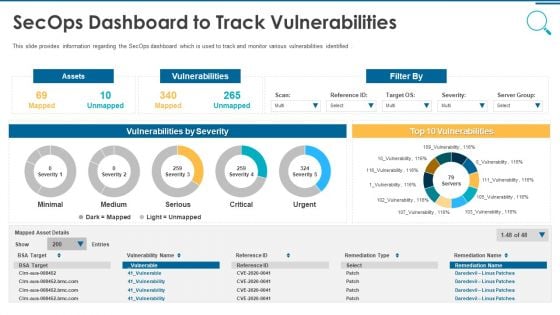
Information And Technology Security Operations Secops Dashboard To Track Vulnerabilities Information PDF
This slide provides information regarding the SecOps dashboard which is used to track and monitor various vulnerabilities identified. Deliver and pitch your topic in the best possible manner with this information and technology security operations secops dashboard to track vulnerabilities information pdf. Use them to share invaluable insights on assets, vulnerabilities, severity and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
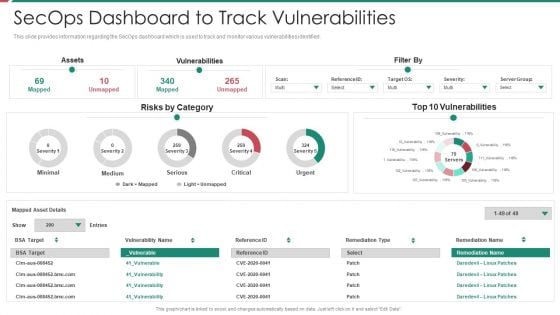
Security And Process Integration Secops Dashboard To Track Vulnerabilities Mockup PDF
This slide provides information regarding the SecOps dashboard which is used to track and monitor various vulnerabilities identified. Deliver and pitch your topic in the best possible manner with this security and process integration secops dashboard to track vulnerabilities mockup pdf. Use them to share invaluable insights on assets, vulnerabilities, severity and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
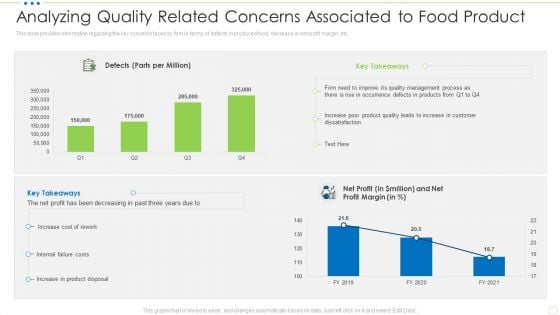
Analyzing Quality Related Concerns Associated To Food Product Food Security Excellence Ppt Infographic Template Picture PDF
This slide provides information regarding the key concerns faced by firm in terms of defects in produced food, decrease in net profit margin, etc. Deliver an awe inspiring pitch with this creative analyzing quality related concerns associated to food product food security excellence ppt infographic template picture pdf bundle. Topics like management, process, net profit margin can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
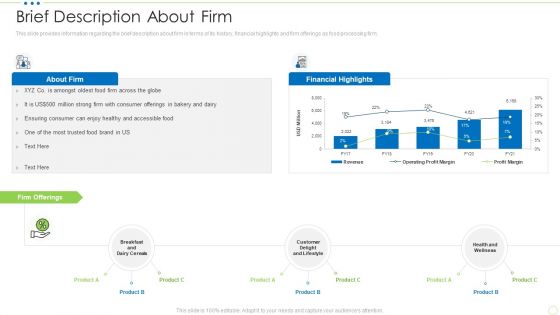
Brief Description About Firm Food Security Excellence Ppt Pictures Rules V
This slide provides information regarding the brief description about firm in terms of its history, financial highlights and firm offerings as food processing firm. Deliver and pitch your topic in the best possible manner with this brief description about firm food security excellence ppt pictures rules v. Use them to share invaluable insights on financial, lifestyle, health and wellness and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
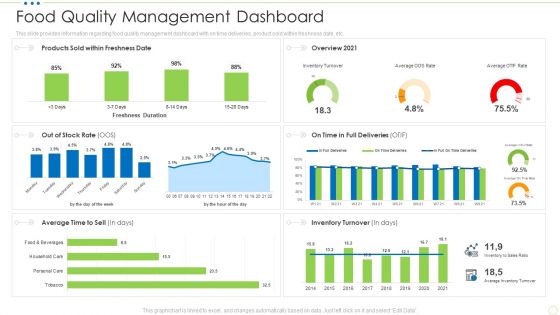
Food Quality Management Dashboard Food Security Excellence Ppt Infographic Template Graphics Pictures PDF
This slide provides information regarding food quality management dashboard with on time deliveries, product sold within freshness date, etc. Deliver and pitch your topic in the best possible manner with this food quality management dashboard food security excellence ppt infographic template graphics pictures pdf. Use them to share invaluable insights on inventory, sales, time to sell and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
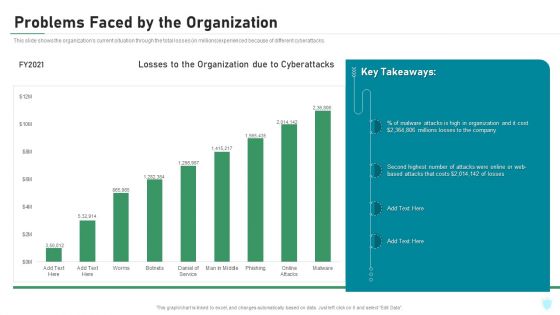
Problems Faced By The Organization IT Security IT Ppt Infographics Graphics PDF
This slide shows the organizations current situation through the total losses in millions experienced because of different cyberattacks. Deliver and pitch your topic in the best possible manner with this problems faced by the organization it security it ppt infographics graphics pdf. Use them to share invaluable insights on problems faced by the organization and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
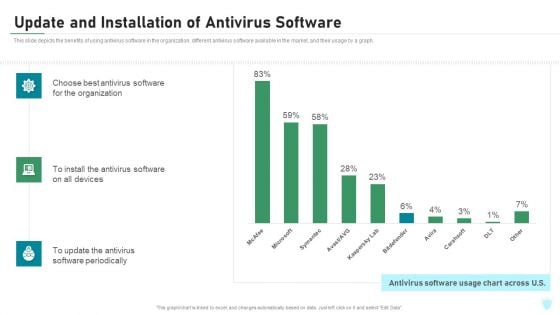
Update And Installation Of Antivirus Software IT Security IT Ppt Information PDF
This slide depicts the benefits of using antivirus software in the organization, different antivirus software available in the market, and their usage by a graph. Deliver and pitch your topic in the best possible manner with this update and installation of antivirus software it security it ppt information pdf. Use them to share invaluable insights on organization, devices, antivirus software, software periodically and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
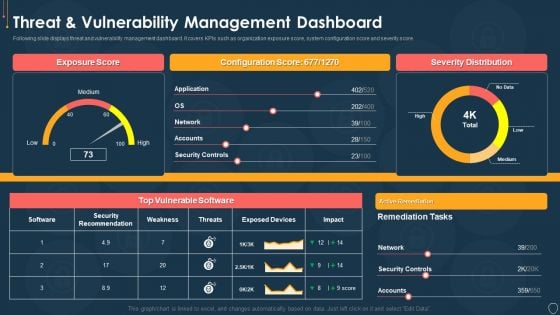
Cyber Security Risk Management Plan Threat And Vulnerability Management Dashboard Portrait PDF
Following slide displays threat and vulnerability management dashboard. It covers KPIs such as organization exposure score, system configuration score and severity score. Deliver and pitch your topic in the best possible manner with this cyber security risk management plan threat and vulnerability management dashboard portrait pdf. Use them to share invaluable insights on exposure score, configuration score, severity distribution, vulnerable software and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
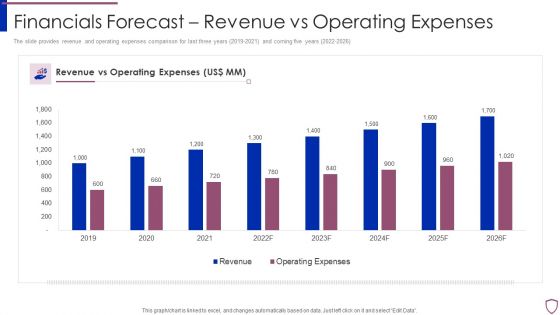
Financing Catalogue For Security Underwriting Agreement Financials Forecast Revenue Vs Operating Demonstration PDF
The slide provides revenue and operating expenses comparison for last three years 2019-2021 and coming five years 2022-2026. Deliver and pitch your topic in the best possible manner with this financing catalogue for security underwriting agreement financials forecast revenue vs operating demonstration pdf. Use them to share invaluable insights on revenue, operating expenses and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Project Security Administration IT Project Management Activities Tracking Dashboard Structure PDF
This slide provides information regarding the dashboard which will help team in managing different activities associated to projects and keep track on the time, cost spent. Deliver an awe inspiring pitch with this creativeproject security administration it project management activities tracking dashboard structure pdf bundle. Topics like time, cost, team cost breakdown, workload, spent time on projects, progress can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
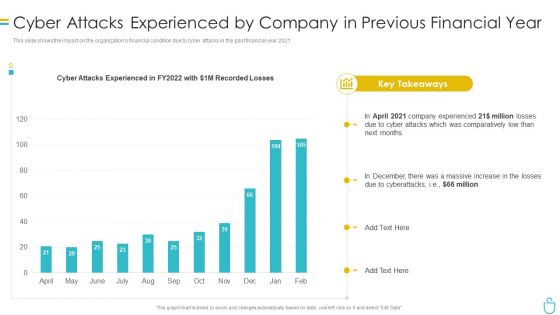
Information Security Cyber Attacks Experienced By Company In Previous Financial Year Ppt Summary Samples PDF
This slide shows the impact on the organizations financial condition due to cyber attacks in the past financial year 2021. Deliver and pitch your topic in the best possible manner with this information security cyber attacks experienced by company in previous financial year ppt summary samples pdf. Use them to share invaluable insights on cyber attacks experienced by company in previous financial year and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
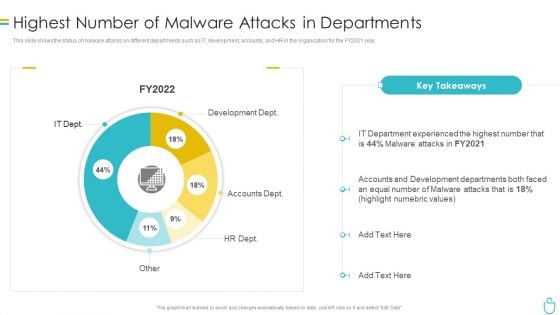
Information Security Highest Number Of Malware Attacks In Departments Ppt Pictures Samples PDF
This slide shows the status of malware attacks on different departments such as IT, development, accounts, and HR in the organization for the FY2021 year. Deliver an awe inspiring pitch with this creative information security highest number of malware attacks in departments ppt pictures samples pdf bundle. Topics like accounts, development, departments can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Information Security Prepare And Deploy Strong IT Policies Ppt Gallery Images PDF
This slide represents the value of having strong IT policies within an organization regarding software, hardware, passwords, and data transfer. Deliver an awe inspiring pitch with this creative information security prepare and deploy strong it policies ppt gallery images pdf bundle. Topics like management, network, device, data can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
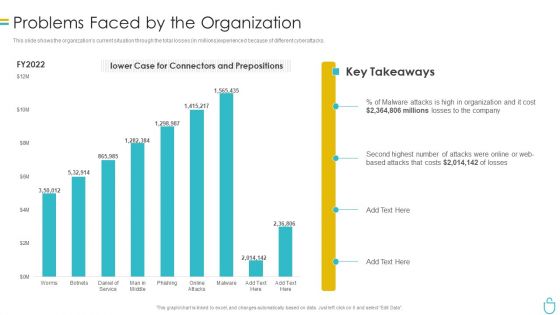
Information Security Problems Faced By The Organization Ppt Layouts Images PDF
This slide shows the organizations current situation through the total losses in millions experienced because of different cyberattacks. Deliver and pitch your topic in the best possible manner with this information security problems faced by the organization ppt layouts images pdf. Use them to share invaluable insights on organization, cost and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
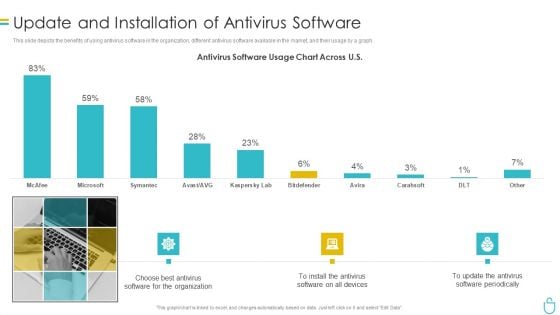
Information Security Update And Installation Of Antivirus Software Ppt Professional Information PDF
This slide depicts the benefits of using antivirus software in the organization, different antivirus software available in the market, and their usage by a graph. Deliver and pitch your topic in the best possible manner with this information security update and installation of antivirus software ppt professional information pdf. Use them to share invaluable insights on organization, devices and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Cyber Security Administration In Organization Financial Performance Tracking Dashboard Microsoft PDF
This slide presents the dashboard which will help firm in tracking the fiscal performance. This dashboard displays revenues and expenses trends and payment received analysis. Deliver and pitch your topic in the best possible manner with this cyber security administration in organization financial performance tracking dashboard microsoft pdf. Use them to share invaluable insights on financial performance tracking dashboard and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
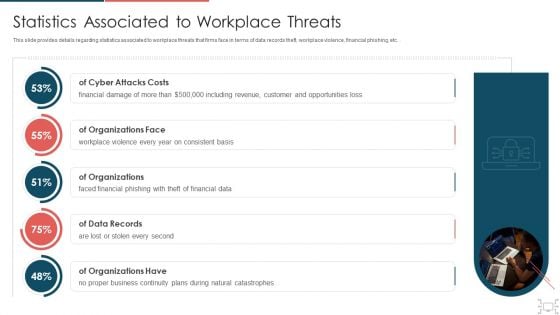
Cyber Security Administration In Organization Statistics Associated To Workplace Threats Microsoft PDF
This slide provides details regarding statistics associated to workplace threats that firms face in terms of data records theft, workplace violence, financial phishing, etc.. Deliver an awe inspiring pitch with this creative cyber security administration in organization statistics associated to workplace threats microsoft pdf bundle. Topics like organizations, consistent, financial, business, catastrophes can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
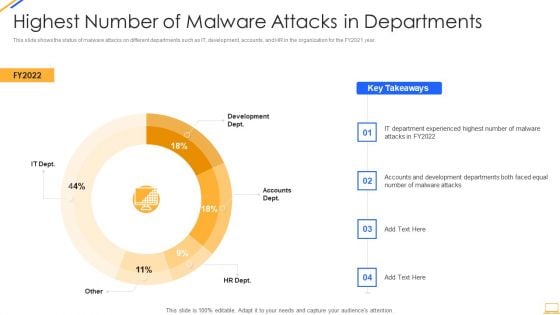
Desktop Security Management Highest Number Of Malware Attacks In Departments Inspiration PDF
This slide shows the status of malware attacks on different departments such as IT, development, accounts, and HR in the organization for the FY2021 year. Deliver an awe inspiring pitch with this creative desktop security management highest number of malware attacks in departments inspiration pdf bundle. Topics like highest number of malware attacks in departments can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
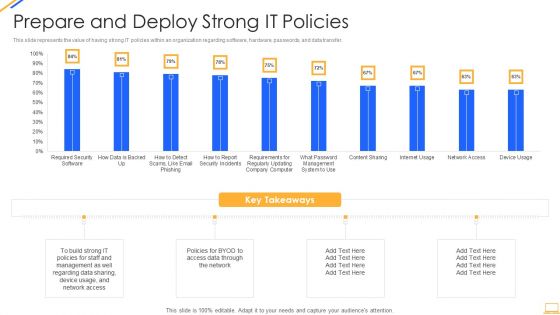
Desktop Security Management Prepare And Deploy Strong It Policies Template PDF
This slide represents the value of having strong IT policies within an organization regarding software, hardware, passwords, and data transfer. Deliver and pitch your topic in the best possible manner with this desktop security management prepare and deploy strong it policies template pdf. Use them to share invaluable insights on management, data, network and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
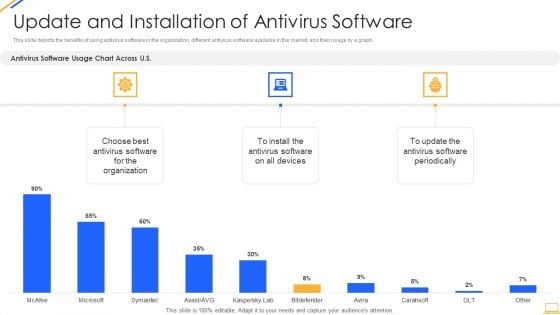
Desktop Security Management Update And Installation Of Antivirus Software Microsoft PDF
This slide depicts the benefits of using antivirus software in the organization, different antivirus software available in the market, and their usage by a graph. Deliver an awe inspiring pitch with this creative desktop security management update and installation of antivirus software microsoft pdf bundle. Topics like organization, devices can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
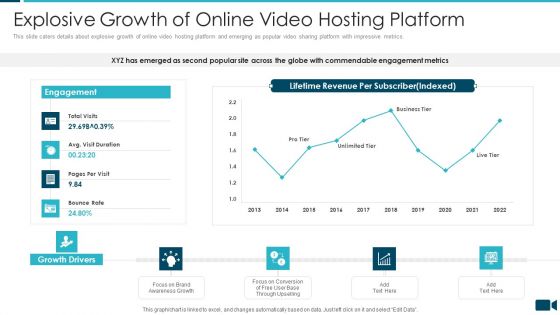
Secured Video Hosting Platform Investor Capital Funding Explosive Growth Of Online Video Hosting Platform Demonstration PDF
This slide caters details about explosive growth of online video hosting platform and emerging as popular video sharing platform with impressive metrics. Deliver an awe inspiring pitch with this creative secured video hosting platform investor capital funding explosive growth of online video hosting platform demonstration pdf bundle. Topics like explosive growth of online video hosting platform can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Corporate Security And Risk Management Financial Performance Tracking Dashboard Introduction PDF
This slide presents the dashboard which will help firm in tracking the fiscal performance. This dashboard displays revenues and expenses trends and payment received analysis. Deliver an awe inspiring pitch with this creative corporate security and risk management financial performance tracking dashboard introduction pdf bundle. Topics like revenue and expense trends, receivables analysis can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
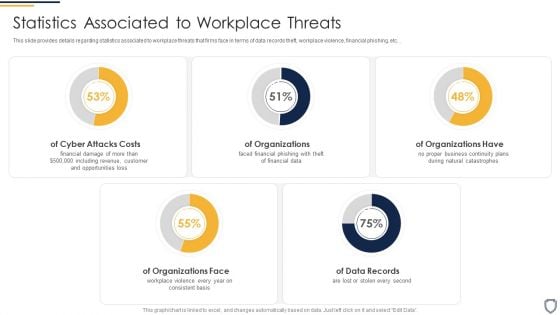
Corporate Security And Risk Management Statistics Associated To Workplace Threats Template PDF
This slide provides details regarding statistics associated to workplace threats that firms face in terms of data records theft, workplace violence, financial phishing, etc. . Deliver an awe inspiring pitch with this creative corporate security and risk management statistics associated to workplace threats template pdf bundle. Topics like cyber attacks costs, organizations, organizations have, organizations face, data records can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
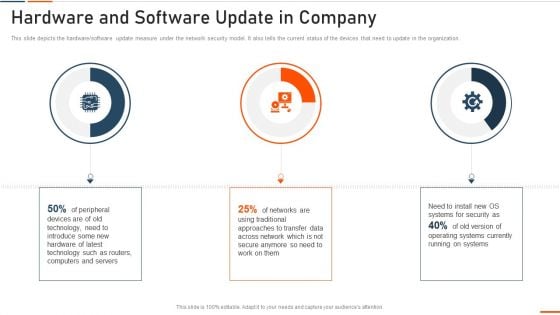
Information Technology Security Hardware And Software Update In Company Ppt Infographic Template Outfit PDF
This slide shows the status of malware attacks on different departments such as IT, development, accounts, and HR in the organization for the FY2022 year. Deliver an awe inspiring pitch with this creative information technology security hardware and software update in company ppt infographic template outfit pdf bundle. Topics like highest number of malware attacks in departments can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
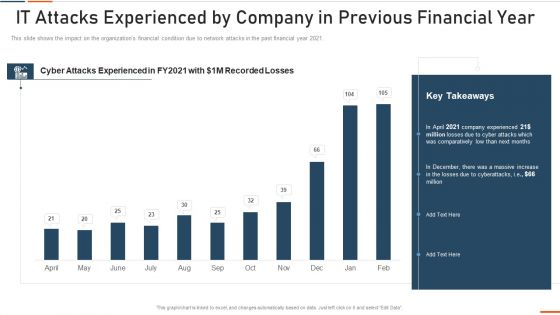
Information Technology Security IT Attacks Experienced By Company Ppt Show Grid PDF
This slide shows the impact on the organizations financial condition due to network attacks in the past financial year 2021. Deliver an awe inspiring pitch with this creative information technology security it attacks experienced by company ppt show grid pdf bundle. Topics like it attacks experienced by company in previous financial year can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Information Technology Security Problems Faced By The Organization Ppt Ideas Visuals PDF
This slide shows the organizations current situation through the total losses ins millionsexperienced because of different cyberattacks. Deliver an awe inspiring pitch with this creative information technology security problems faced by the organization ppt ideas visuals pdf bundle. Topics like problems faced by the organization can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
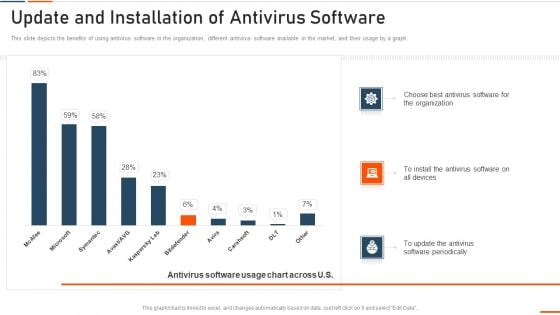
Information Technology Security Update And Installation Of Antivirus Software Ppt Professional Example File PDF
This slide depicts the benefits of using antivirus software in the organization, different antivirus software available in the market, and their usage by a graph. Deliver and pitch your topic in the best possible manner with this information technology security update and installation of antivirus software ppt professional example file pdf. Use them to share invaluable insights on update and installation of antivirus software and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
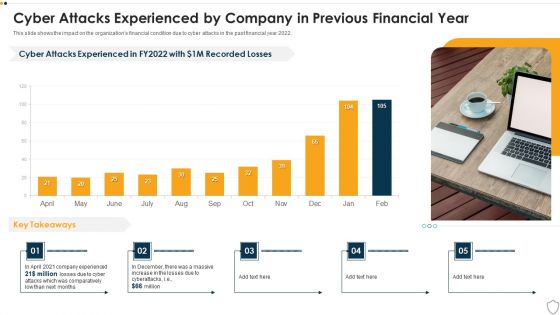
IT Security Cyber Attacks Experienced By Company In Previous Financial Year Ppt Outline Gallery PDF
This slide shows the impact on the organizations financial condition due to cyber attacks in the past financial year 2022. Deliver and pitch your topic in the best possible manner with this it security cyber attacks experienced by company in previous financial year ppt outline gallery pdf. Use them to share invaluable insights on cyber attacks experienced by company in previous financial year and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

IT Security Highest Number Of Malware Attacks In Departments Ppt Layouts Designs Download PDF
This slide shows the status of malware attacks on different departments such as IT, development, accounts, and HR in the organization for the FY2022 year. Deliver an awe inspiring pitch with this creative it security highest number of malware attacks in departments ppt layouts designs download pdf bundle. Topics like it, development, accounts, hr can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

IT Security Problems Faced By The Organization Ppt Model Professional PDF
This slide shows the organizations current situation through the total losses in millionsexperienced because of different cyberattacks. Deliver and pitch your topic in the best possible manner with this it security problems faced by the organization ppt model professional pdf. Use them to share invaluable insights on problems faced by the organization and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
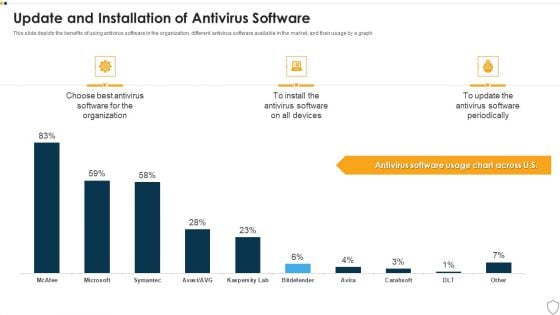
IT Security Update And Installation Of Antivirus Software Ppt Outline Sample PDF
This slide depicts the benefits of using antivirus software in the organization, different antivirus software available in the market, and their usage by a graph. Deliver and pitch your topic in the best possible manner with this it security update and installation of antivirus software ppt outline sample pdf. Use them to share invaluable insights on update and installation of antivirus software and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
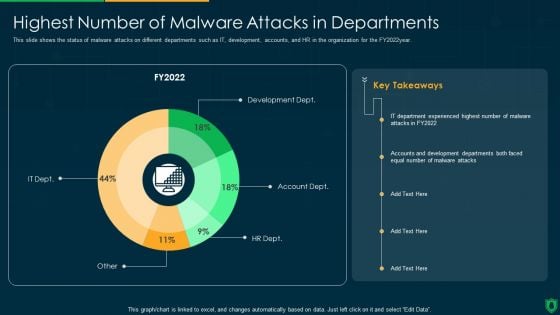
Info Security Highest Number Of Malware Attacks In Departments Ppt PowerPoint Presentation Gallery Format PDF
This slide shows the status of malware attacks on different departments such as IT, development, accounts, and HR in the organization for the FY2022year. Deliver an awe inspiring pitch with this creative info security highest number of malware attacks in departments ppt powerpoint presentation gallery format pdf bundle. Topics like development dept, account dept, hr dept, it dept can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
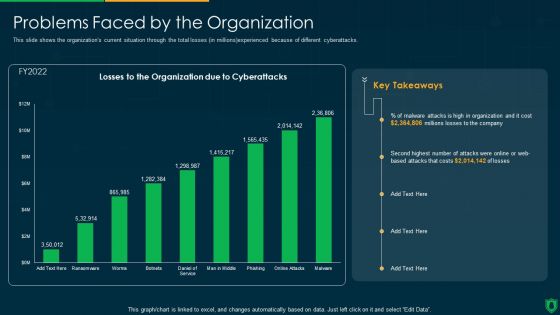
Info Security Problems Faced By The Organization Ppt PowerPoint Presentation File Slide PDF
This slide shows the organizations current situation through the total losses in millions experienced because of different cyberattacks. Deliver and pitch your topic in the best possible manner with this info security problems faced by the organization ppt powerpoint presentation file slide pdf. Use them to share invaluable insights on losses organization, due cyberattacks, cost and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
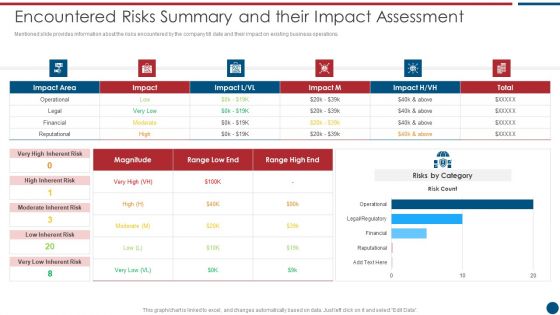
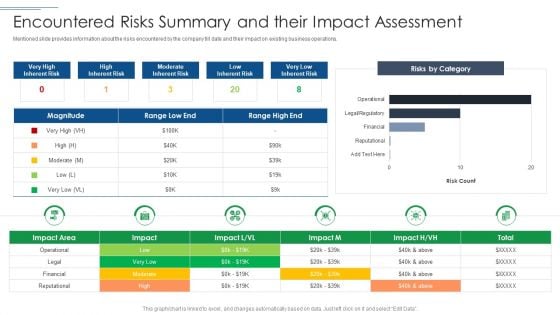
Risk Based Procedures To IT Security Encountered Risks Summary And Their Impact Assessment Topics PDF
Mentioned slide provides information about the risks encountered by the company till date and their impact on existing business operations. Deliver and pitch your topic in the best possible manner with this Risk Based Procedures To IT Security Encountered Risks Summary And Their Impact Assessment Topics PDF. Use them to share invaluable insights on Risks Category, High Inherent, Risk Magnitude and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
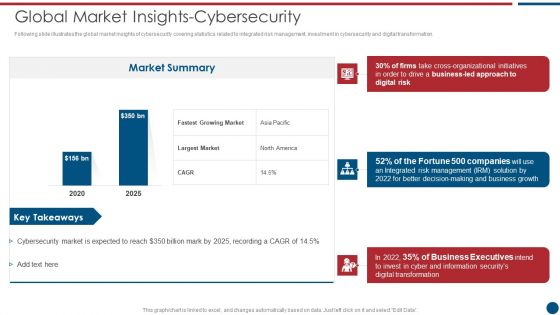
Risk Based Procedures To IT Security Global Market Insights Cybersecurity Ppt PowerPoint Presentation Gallery Clipart PDF
Following slide illustrates the global market insights of cybersecurity covering statistics related to integrated risk management, investment in cybersecurity and digital transformation. Deliver an awe inspiring pitch with this creative Risk Based Procedures To IT Security Global Market Insights Cybersecurity Ppt PowerPoint Presentation Gallery Clipart PDF bundle. Topics like Market Summary, Largest Market, Business Led can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
IT Security Risk Management Approach Introduction Encountered Risks Summary And Their Impact Assessment Professional PDF
Mentioned slide provides information about the risks encountered by the company till date and their impact on existing business operations. Deliver and pitch your topic in the best possible manner with this IT Security Risk Management Approach Introduction Encountered Risks Summary And Their Impact Assessment Professional PDF. Use them to share invaluable insights on Moderate Inherent Risk, Risks By Category, Financial and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
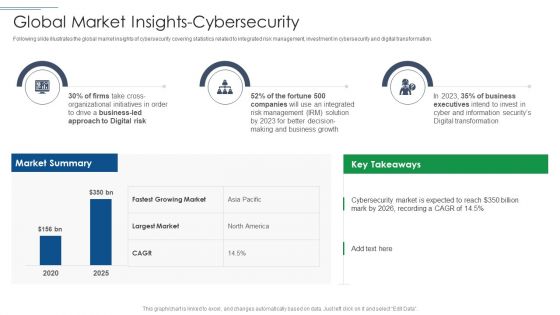
IT Security Risk Management Approach Introduction Global Market Insights Cybersecurity Rules PDF
Following slide illustrates the global market insights of cybersecurity covering statistics related to integrated risk management, investment in cybersecurity and digital transformation. Deliver an awe inspiring pitch with this creative IT Security Risk Management Approach Introduction Global Market Insights Cybersecurity Rules PDF bundle. Topics like Business Growth, Risk Management, Organizational Initiatives can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

IT Security Risk Management Approach Introduction Risk Management KPI Dashboard With Loss Events Brochure PDF
Following slide illustrates a risk management KPI dashboard. KPIs covered are top ten risks, loss events, actions, key risk indicators and compliance. Deliver an awe inspiring pitch with this creative IT Security Risk Management Approach Introduction Risk Management KPI Dashboard With Loss Events Brochure PDF bundle. Topics like Key Risk Indicators, Risk Management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
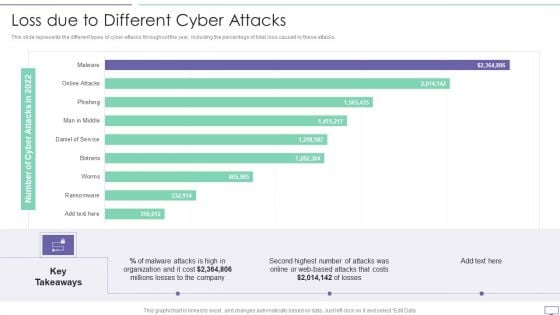
IT Security Hacker Loss Due To Different Cyber Attacks Rules PDF
This slide represents the different types of cyber-attacks throughout the year, including the percentage of total loss caused by these attacks.Deliver an awe inspiring pitch with this creative IT Security Hacker Loss Due To Different Cyber Attacks Rules PDF bundle. Topics like Malware Attacks, Millions Losses, Based Attacks can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

 Home
Home