Safety Improvement Plan

Ways To Prevent Crypto Phishing Comprehensive Guide To Blockchain Digital Security Structure Pdf
The following slide illustrates some methods to minimize crypto phishing attacks and . It includes elements such as using VPN, cross checking browsers URL, emails, leveraging two factor authentication, avoid usage of protected wi-fi networks, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Ways To Prevent Crypto Phishing Comprehensive Guide To Blockchain Digital Security Structure Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Ways To Prevent Crypto Phishing Comprehensive Guide To Blockchain Digital Security Structure Pdf today and make your presentation stand out from the rest The following slide illustrates some methods to minimize crypto phishing attacks and . It includes elements such as using VPN, cross checking browsers URL, emails, leveraging two factor authentication, avoid usage of protected wi-fi networks, etc.
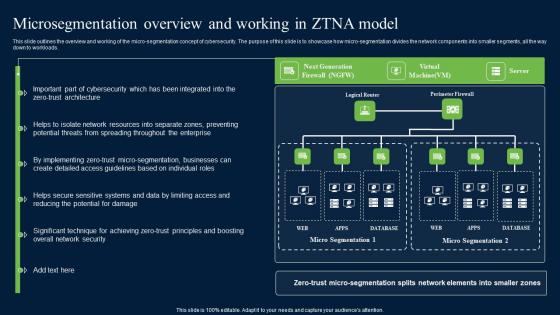
Microsegmentation Overview And Working In ZTNA Zero Trust Network Security Diagrams Pdf
This slide outlines the overview and working of the micro-segmentation concept of cybersecurity. The purpose of this slide is to showcase how micro-segmentation divides the network components into smaller segments, all the way down to workloads. Explore a selection of the finest Microsegmentation Overview And Working In ZTNA Zero Trust Network Security Diagrams Pdf here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Microsegmentation Overview And Working In ZTNA Zero Trust Network Security Diagrams Pdf to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide outlines the overview and working of the micro-segmentation concept of cybersecurity. The purpose of this slide is to showcase how micro-segmentation divides the network components into smaller segments, all the way down to workloads.

Step 6 And 7 Define Operational Changes And Zero Trust Network Security Diagrams Pdf
This slide outlines the sixth and seventh steps for ZTNA implementation, which are defining operational changes and implementing, rinsing and repeating the process. The purpose of this slide is to showcase the following steps in zero trust model deployment. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Step 6 And 7 Define Operational Changes And Zero Trust Network Security Diagrams Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Step 6 And 7 Define Operational Changes And Zero Trust Network Security Diagrams Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide outlines the sixth and seventh steps for ZTNA implementation, which are defining operational changes and implementing, rinsing and repeating the process. The purpose of this slide is to showcase the following steps in zero trust model deployment.
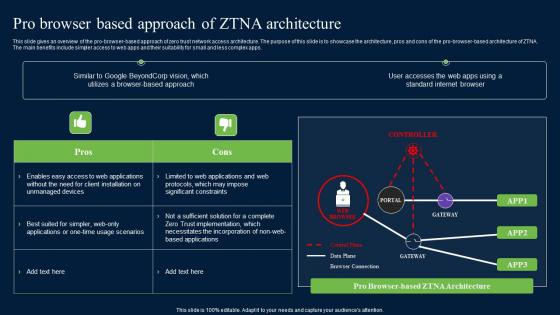
Pro Browser Based Approach Of ZTNA Architecture Zero Trust Network Security Formats Pdf
The main benefits include simpler access to web apps and their suitability for small and less complex apps. Presenting this PowerPoint presentation, titled Pro Browser Based Approach Of ZTNA Architecture Zero Trust Network Security Formats Pdf, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Pro Browser Based Approach Of ZTNA Architecture Zero Trust Network Security Formats Pdf. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Pro Browser Based Approach Of ZTNA Architecture Zero Trust Network Security Formats Pdf that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. The main benefits include simpler access to web apps and their suitability for small and less complex apps.
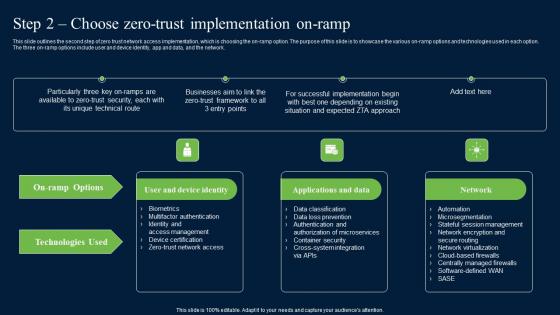
Step 2 Choose Zero Trust Implementation On Ramp Zero Trust Network Security Introduction Pdf
This slide outlines the second step of zero trust network access implementation, which is choosing the on-ramp option. The purpose of this slide is to showcase the various on-ramp options and technologies used in each option. The three on-ramp options include user and device identity, app and data, and the network. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Step 2 Choose Zero Trust Implementation On Ramp Zero Trust Network Security Introduction Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide outlines the second step of zero trust network access implementation, which is choosing the on-ramp option. The purpose of this slide is to showcase the various on-ramp options and technologies used in each option. The three on-ramp options include user and device identity, app and data, and the network.

On Ramp Option 2 Applications And Data Zero Trust Network Security Sample Pdf
This slide describes the second on-ramp option, which is the applications and data of ZTNA implementation. The purpose of this slide is to give an overview of practices and technologies used in this approach, such as data classification, data loss prevention, authentication and authorization of microservices, container security, etc. The On Ramp Option 2 Applications And Data Zero Trust Network Security Sample Pdf is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide describes the second on-ramp option, which is the applications and data of ZTNA implementation. The purpose of this slide is to give an overview of practices and technologies used in this approach, such as data classification, data loss prevention, authentication and authorization of microservices, container security, etc.

Endpoint Initiated Zero Trust Network Topology Zero Trust Network Security Template Pdf
This slide describes the overview of the endpoint-initiated zero trust network topology model of ZTNA deployment. The purpose of this slide is to showcase the conceptual model of the approach along with its benefits and drawbacks. The model components include the end-user device, SDP controller, gateway, and directory. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Endpoint Initiated Zero Trust Network Topology Zero Trust Network Security Template Pdf and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide describes the overview of the endpoint-initiated zero trust network topology model of ZTNA deployment. The purpose of this slide is to showcase the conceptual model of the approach along with its benefits and drawbacks. The model components include the end-user device, SDP controller, gateway, and directory.

Comparative Assessment Of ZTNA Version 10 And 20 Zero Trust Network Security Infographics Pdf
This slide represents the comparison between zero trust network access versions 1.0 and 2.0. The purpose of this slide is to demonstrate the overview of both versions, including differences. It also includes the architecture of both versions of zero-trust network access. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Comparative Assessment Of ZTNA Version 10 And 20 Zero Trust Network Security Infographics Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide represents the comparison between zero trust network access versions 1.0 and 2.0. The purpose of this slide is to demonstrate the overview of both versions, including differences. It also includes the architecture of both versions of zero-trust network access.
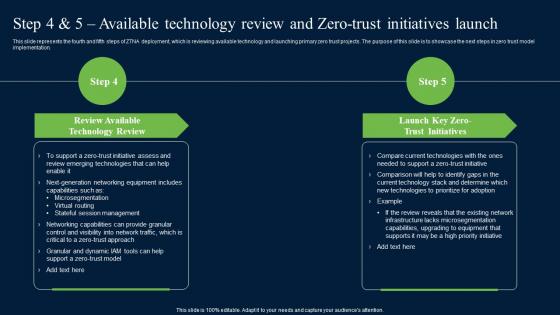
Step 4 And 5 Available Technology Review And Zero Trust Network Security Professional Pdf
This slide represents the fourth and fifth steps of ZTNA deployment, which is reviewing available technology and launching primary zero trust projects. The purpose of this slide is to showcase the next steps in zero trust model implementation. There are so many reasons you need a Step 4 And 5 Available Technology Review And Zero Trust Network Security Professional Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide represents the fourth and fifth steps of ZTNA deployment, which is reviewing available technology and launching primary zero trust projects. The purpose of this slide is to showcase the next steps in zero trust model implementation.

Problem Statement FMCG Products Investor Funding Ppt Sample
This slide showcases identified problems that consumers commonly face during product purchase. Challenges are convenience, quality and performance, safety and affordability. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Problem Statement FMCG Products Investor Funding Ppt Sample was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Problem Statement FMCG Products Investor Funding Ppt Sample This slide showcases identified problems that consumers commonly face during product purchase. Challenges are convenience, quality and performance, safety and affordability.

Problem Statement Personal Care Company Investor Ppt Slides
This slide showcases identified problems that consumers commonly face during product purchase. Challenges are convenience, quality and performance, safety and affordability. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Problem Statement Personal Care Company Investor Ppt Slides was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Problem Statement Personal Care Company Investor Ppt Slides This slide showcases identified problems that consumers commonly face during product purchase. Challenges are convenience, quality and performance, safety and affordability.
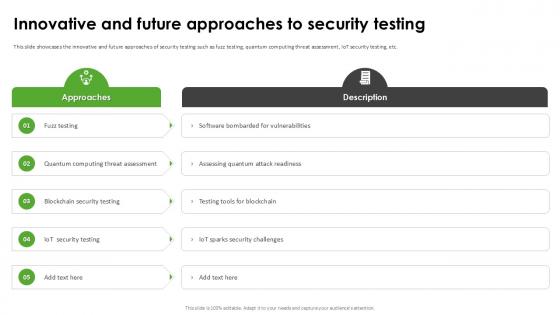
Innovative And Future Approaches Harnessing The World Of Ethical Ppt Slide
This slide showcases the innovative and future approaches of security testing such as fuzz testing, quantum computing threat assessment, IoT security testing, etc. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Innovative And Future Approaches Harnessing The World Of Ethical Ppt Slide and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide showcases the innovative and future approaches of security testing such as fuzz testing, quantum computing threat assessment, IoT security testing, etc.
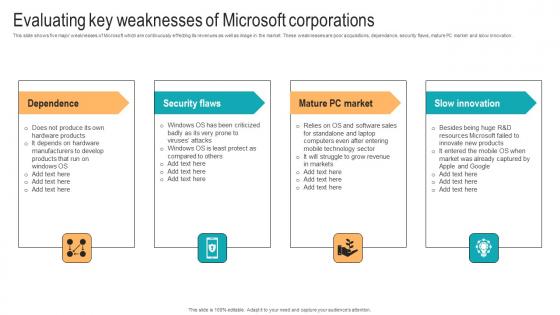
Evaluating Key Weaknesses Of Microsoft Strategic Advancements By Microsofts Microsoft Pdf
This slide shows five major weaknesses of Microsoft which are continuously effecting its revenues as well as image in the market. These weaknesses are poor acquisitions, dependance, security flaws, mature PC market and slow innovation. If you are looking for a format to display your unique thoughts, then the professionally designed Evaluating Key Weaknesses Of Microsoft Strategic Advancements By Microsofts Microsoft Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Evaluating Key Weaknesses Of Microsoft Strategic Advancements By Microsofts Microsoft Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide shows five major weaknesses of Microsoft which are continuously effecting its revenues as well as image in the market. These weaknesses are poor acquisitions, dependance, security flaws, mature PC market and slow innovation.
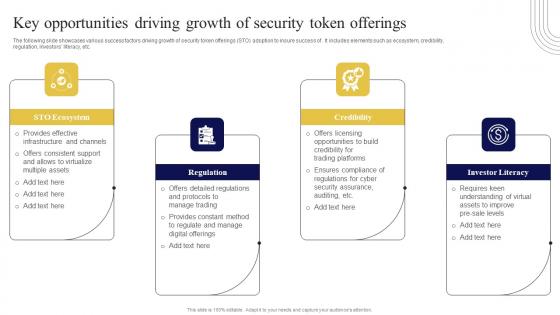
Key Opportunities Driving Growth Exploring Investment Opportunities Structure Pdf
The following slide showcases various success factors driving growth of security token offerings STO adoption to insure success of . It includes elements such as ecosystem, credibility, regulation, investors literacy, etc. Retrieve professionally designed Key Opportunities Driving Growth Exploring Investment Opportunities Structure Pdf to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. The following slide showcases various success factors driving growth of security token offerings STO adoption to insure success of . It includes elements such as ecosystem, credibility, regulation, investors literacy, etc.

Agile Threat Modeling Overview About Duration Process Crafting A Sustainable Company Designs Pdf
This slide provides information regarding agile threat modeling as a risk-based approach that helps develop secure systems. The approach is suitable for business analysts, product managers, security teams, technical and non-technical professionals, etc. Create an editable Agile Threat Modeling Overview About Duration Process Crafting A Sustainable Company Designs Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Agile Threat Modeling Overview About Duration Process Crafting A Sustainable Company Designs Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide provides information regarding agile threat modeling as a risk-based approach that helps develop secure systems. The approach is suitable for business analysts, product managers, security teams, technical and non-technical professionals, etc.
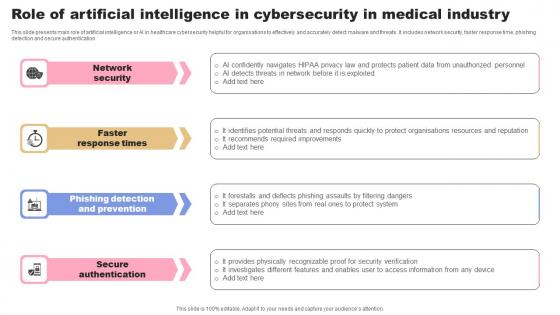
Role Of Artificial Intelligence In Cybersecurity In Medical Industry Background Pdf
This slide presents main role of artificial intelligence or AI in healthcare cybersecurity helpful for organisations to effectively and accurately detect malware and threats. It includes network security, faster response time, phishing detection and secure authentication Showcasing this set of slides titled Role Of Artificial Intelligence In Cybersecurity In Medical Industry Background Pdf. The topics addressed in these templates are Network Security, Response Times, Prevention. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide presents main role of artificial intelligence or AI in healthcare cybersecurity helpful for organisations to effectively and accurately detect malware and threats. It includes network security, faster response time, phishing detection and secure authentication
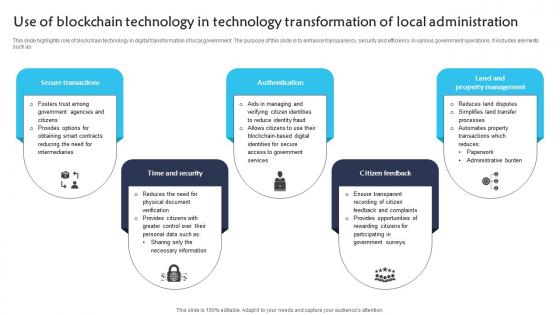
Use Of Blockchain Technology In Technology Transformation Of Local Administration Infographics pdf
This slide highlights role of blockchain technology in digital transformation of local government. The purpose of this slide is to enhance transparency, security and efficiency in various government operations. It includes elements such as. Showcasing this set of slides titled Use Of Blockchain Technology In Technology Transformation Of Local Administration Infographics pdf. The topics addressed in these templates are Secure Transactions, Authentication, Citizen Feedback, Time And Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide highlights role of blockchain technology in digital transformation of local government. The purpose of this slide is to enhance transparency, security and efficiency in various government operations. It includes elements such as.
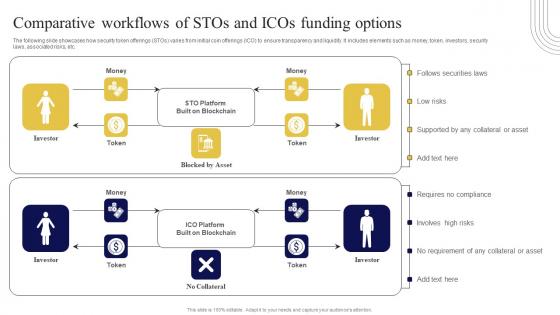
Comparative Workflows Of Stos And Icos Exploring Investment Opportunities Professional Pdf
The following slide showcases how security token offerings STOs varies from initial coin offerings ICO to ensure transparency and liquidity. It includes elements such as money, token, investors, security laws, associated risks, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Comparative Workflows Of Stos And Icos Exploring Investment Opportunities Professional Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Comparative Workflows Of Stos And Icos Exploring Investment Opportunities Professional Pdf today and make your presentation stand out from the rest The following slide showcases how security token offerings STOs varies from initial coin offerings ICO to ensure transparency and liquidity. It includes elements such as money, token, investors, security laws, associated risks, etc.
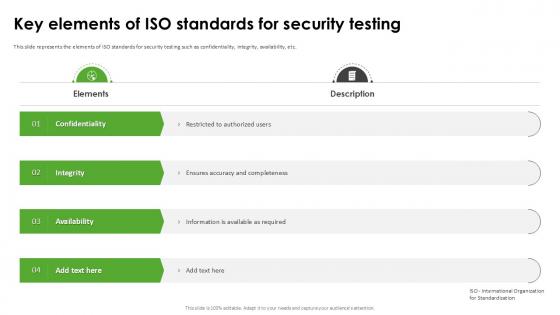
Key Elements Of Iso Standards Harnessing The World Of Ethical Ppt Presentation
This slide represents the elements of ISO standards for security testing such as confidentiality, integrity, availability, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Key Elements Of Iso Standards Harnessing The World Of Ethical Ppt Presentation and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide represents the elements of ISO standards for security testing such as confidentiality, integrity, availability, etc.

Tokenization Process Activities In A Cloud Based System PPT Template
This slide highlights the key functions within a cloud-based system in data security. The purpose of this slide is to outline the Process activities in a cloud-based system which include gathering, creating, retrieving data, etc. Boost your pitch with our creative Tokenization Process Activities In A Cloud Based System PPT Template. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide highlights the key functions within a cloud-based system in data security. The purpose of this slide is to outline the Process activities in a cloud-based system which include gathering, creating, retrieving data, etc.

Zero Trust Network Access Architectural Models Ideas Pdf
This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption. There are so many reasons you need a Zero Trust Network Access Architectural Models Ideas Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption.

Key AI Trends Associated With Financial Sector Applications And Impact Themes Pdf
This slide represents key artificial intelligence tools related to financial sector. It includes huperautomation, AI-powered advisory, financial security and personalized offering. Find a pre-designed and impeccable Key AI Trends Associated With Financial Sector Applications And Impact Themes Pdf. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide represents key artificial intelligence tools related to financial sector. It includes huperautomation, AI-powered advisory, financial security and personalized offering.
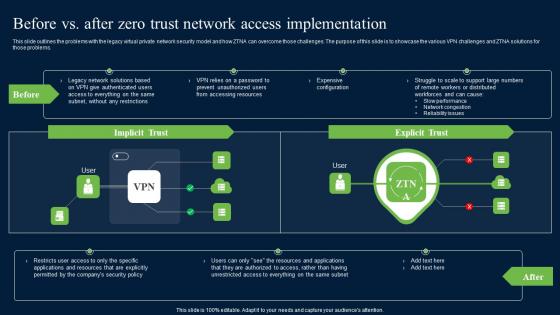
Before Vs After Zero Trust Network Access Brochure Pdf
This slide outlines the problems with the legacy virtual private network security model and how ZTNA can overcome those challenges. The purpose of this slide is to showcase the various VPN challenges and ZTNA solutions for those problems. Create an editable Before Vs After Zero Trust Network Access Brochure Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Before Vs After Zero Trust Network Access Brochure Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide outlines the problems with the legacy virtual private network security model and how ZTNA can overcome those challenges. The purpose of this slide is to showcase the various VPN challenges and ZTNA solutions for those problems.

5G Evolution Architectural Technology Identifying Success Factors Associated To 5G Handsets Guidelines PDF
This slide provides details regarding success factors associated to 5G handsets with better battery capacity, performance and safety performance. Deliver an awe inspiring pitch with this creative 5G Evolution Architectural Technology Identifying Success Factors Associated To 5G Handsets Guidelines PDF bundle. Topics like Telecom Is Catered, Effective Scale, Premises Equipment can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
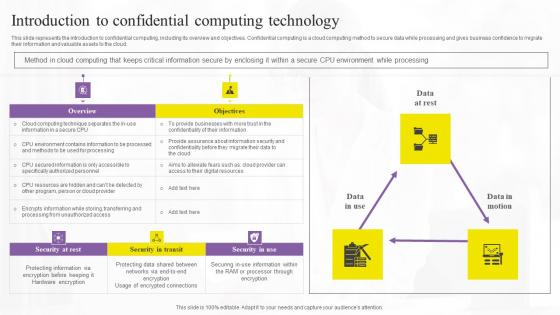
Introduction To Confidential Computing Technology Structure Pdf
This slide represents the introduction to confidential computing, including its overview and objectives. Confidential computing is a cloud computing method to secure data while processing and gives business confidence to migrate their information and valuable assets to the cloud. Boost your pitch with our creative Introduction To Confidential Computing Technology Structure Pdf. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide represents the introduction to confidential computing, including its overview and objectives. Confidential computing is a cloud computing method to secure data while processing and gives business confidence to migrate their information and valuable assets to the cloud.
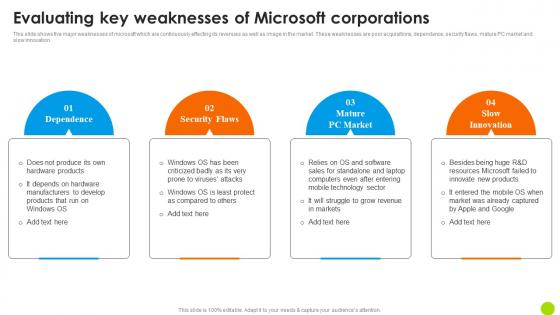
Evaluating Key Weaknesses Of Microsoft Corporations Microsoft Long Term Business Guidelines PDF
This slide shows five major weaknesses of microsoft which are continuously effecting its revenues as well as image in the market. These weaknesses are poor acquisitions, dependance, security flaws, mature PC market and slow innovation. If you are looking for a format to display your unique thoughts, then the professionally designed Evaluating Key Weaknesses Of Microsoft Corporations Microsoft Long Term Business Guidelines PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Evaluating Key Weaknesses Of Microsoft Corporations Microsoft Long Term Business Guidelines PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide shows five major weaknesses of microsoft which are continuously effecting its revenues as well as image in the market. These weaknesses are poor acquisitions, dependance, security flaws, mature PC market and slow innovation.

Interoperability Challenges In IOT Manufacturing Devices Streamlining Production Ppt Presentation
This slide aims to analyze interoperability challenges faced by organizations in IoT ecosystem of manufacturing devices. It includes lack of standardization, fragmentation of communication protocols, security and privacy concerns, etc. Do you know about Slidesgeeks Interoperability Challenges In IOT Manufacturing Devices Streamlining Production Ppt Presentation These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide aims to analyze interoperability challenges faced by organizations in IoT ecosystem of manufacturing devices. It includes lack of standardization, fragmentation of communication protocols, security and privacy concerns, etc.
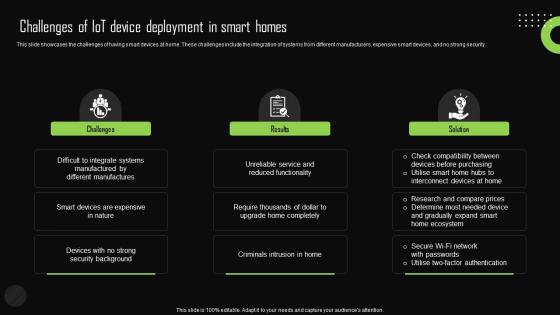
Challenges Of Iot Device Deployment In Smart Iot Device Management Guidelines Pdf
This slide showcases the challenges of having smart devices at home. These challenges include the integration of systems from different manufacturers, expensive smart devices, and no strong security. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Challenges Of Iot Device Deployment In Smart Iot Device Management Guidelines Pdf can be your best option for delivering a presentation. Represent everything in detail using Challenges Of Iot Device Deployment In Smart Iot Device Management Guidelines Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide showcases the challenges of having smart devices at home. These challenges include the integration of systems from different manufacturers, expensive smart devices, and no strong security.
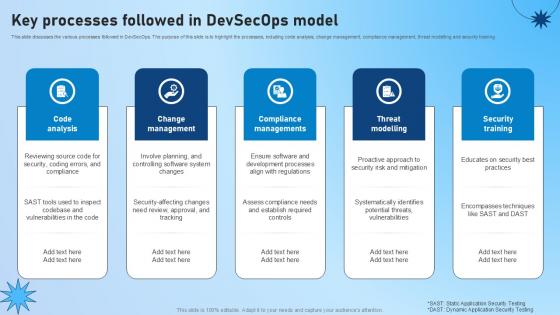
Key Processes Followed In Devsecops Model Role Of Devsecops Ppt Powerpoint
This slide discusses the various processes followed in DevSecOps. The purpose of this slide is to highlight the processes, including code analysis, change management, compliance management, threat modelling and security training. Boost your pitch with our creative Key Processes Followed In Devsecops Model Role Of Devsecops Ppt Powerpoint Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide discusses the various processes followed in DevSecOps. The purpose of this slide is to highlight the processes, including code analysis, change management, compliance management, threat modelling and security training.
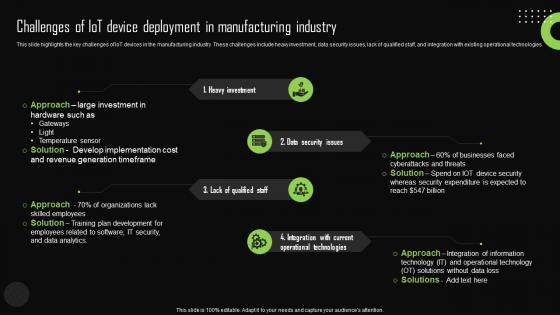
Challenges Of Iot Device Deployment In Iot Device Management Guidelines Pdf
This slide highlights the key challenges of IoT devices in the manufacturing industry. These challenges include heavy investment, data security issues, lack of qualified staff, and integration with existing operational technologies. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Challenges Of Iot Device Deployment In Iot Device Management Guidelines Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Challenges Of Iot Device Deployment In Iot Device Management Guidelines Pdf today and make your presentation stand out from the rest This slide highlights the key challenges of IoT devices in the manufacturing industry. These challenges include heavy investment, data security issues, lack of qualified staff, and integration with existing operational technologies.
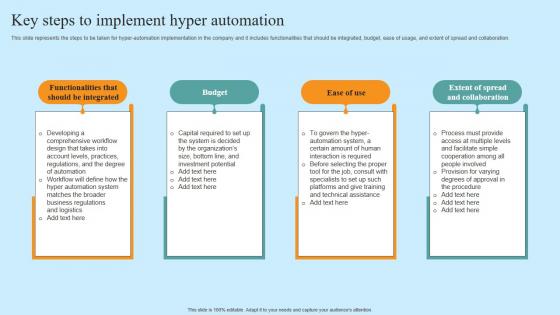
Key Steps To Implement Hyper Automation Hyper Automation Solutions Graphics Pdf
This slide represents the applications of machine learning algorithms in different areas such as banking and finance, fraud detection, data security, the retail sector, and the healthcare industry. It also includes how these business operations the technology and its impact. Take your projects to the next level with our ultimate collection of Key Steps To Implement Hyper Automation Hyper Automation Solutions Graphics Pdf. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest This slide represents the applications of machine learning algorithms in different areas such as banking and finance, fraud detection, data security, the retail sector, and the healthcare industry. It also includes how these business operations the technology and its impact.

Technologies Used To Protect Data In Confidential Computing Technologies Guidelines Pdf
This slide depicts the related technologies used to protect the information in processing. The purpose of this slide is to showcase the technologies and comparison between these technologies based on security and scalability. The technologies include homomorphic encryption, multi-party computation, and so on. Present like a pro with Technologies Used To Protect Data In Confidential Computing Technologies Guidelines Pdf Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide depicts the related technologies used to protect the information in processing. The purpose of this slide is to showcase the technologies and comparison between these technologies based on security and scalability. The technologies include homomorphic encryption, multi-party computation, and so on.
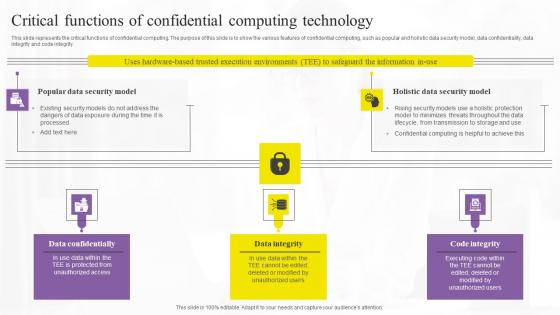
Critical Functions Of Confidential Computing Technology Demonstration Pdf
This slide represents the critical functions of confidential computing. The purpose of this slide is to show the various features of confidential computing, such as popular and holistic data security model, data confidentiality, data integrity and code integrity. Presenting this PowerPoint presentation, titled Critical Functions Of Confidential Computing Technology Demonstration Pdf, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Critical Functions Of Confidential Computing Technology Demonstration Pdf. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Critical Functions Of Confidential Computing Technology Demonstration Pdf that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide represents the critical functions of confidential computing. The purpose of this slide is to show the various features of confidential computing, such as popular and holistic data security model, data confidentiality, data integrity and code integrity.
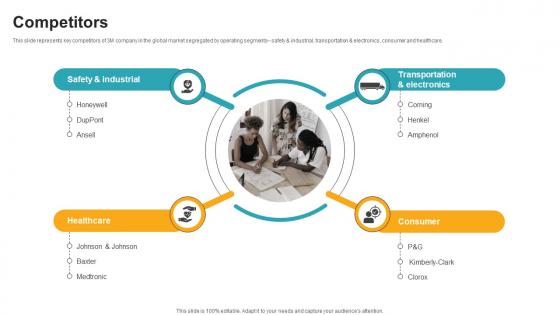
Competitors Innovative Industrial Solutions Company Profile CP SS V
This slide represents key competitors of 3M company in the global market segregated by operating segments safety and industrial, transportation and electronics, consumer and healthcare. Want to ace your presentation in front of a live audience Our Competitors Innovative Industrial Solutions Company Profile CP SS V can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide represents key competitors of 3M company in the global market segregated by operating segments safety and industrial, transportation and electronics, consumer and healthcare.
Best Practices Effective Management Maximizing Efficiency Asset Tracking Solutions Mockup Pdf
This slide covers best practice for managing inventory more efficiently and boost productivity. It involves approaches such as track product information, invest in inventory management technology and analyze supplier performance. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Best Practices Effective Management Maximizing Efficiency Asset Tracking Solutions Mockup Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Best Practices Effective Management Maximizing Efficiency Asset Tracking Solutions Mockup Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide covers key features and components of Bluetooth low energy technique for effective asset tracking. It involves real time tracking, cloud based security, email and messages notifications.This slide covers best practice for managing inventory more efficiently and boost productivity. It involves approaches such as track product information, invest in inventory management technology and analyze supplier performance.

5G Network Technology Identifying Success Factors Associated To 5G Handsets Ppt Model Graphics Template PDF
This slide provides details regarding success factors associated to 5G handsets with better battery capacity, performance and safety performance. Deliver an awe inspiring pitch with this creative 5g network technology identifying success factors associated to 5g handsets ppt model graphics template pdf bundle. Topics like performance, economies, financial, development, strategies can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
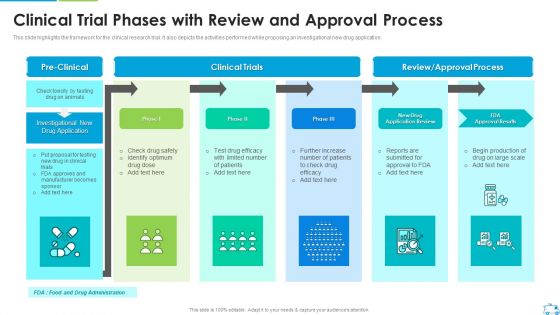
Clinical Trial Phases With Review And Approval Process Microsoft PDF
This slide highlights the framework for the clinical research trial. It also depicts the activities performed while proposing an investigational new drug application.Deliver and pitch your topic in the best possible manner with this Clinical Trial Phases With Review And Approval Process Microsoft PDF Use them to share invaluable insights on Safety Identify Optimum, Further Increase, Review Or Approval Process and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
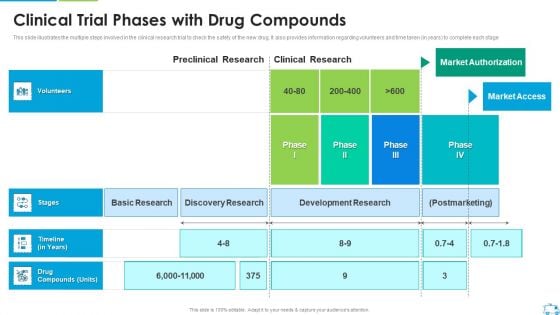
Clinical Trial Phases With Drug Compounds Download PDF
This slide illustrates the multiple steps involved in the clinical research trial to check the safety of the new drug. It also provides information regarding volunteers and time taken in years to complete each stageDeliver an awe inspiring pitch with this creative Clinical Trial Phases With Drug Compounds Download PDF bundle. Topics like Basic Research, Discovery Research, Development Research can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
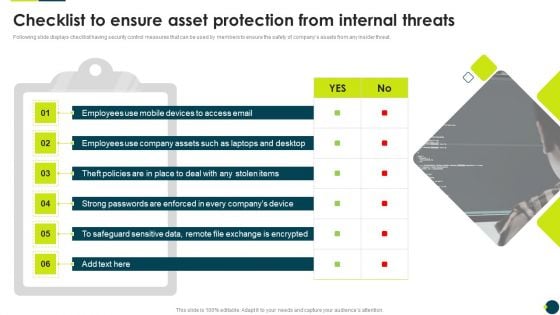
IT Threats Response Playbook Checklist To Ensure Asset Protection From Internal Threats Information PDF
Following slide displays checklist having security control measures that can be used by members to ensure the safety of companys assets from any insider threat.Deliver an awe inspiring pitch with this creative IT Threats Response Playbook Checklist To Ensure Asset Protection From Internal Threats Information PDF bundle. Topics like Safeguard Sensitive, Strong Passwords, Exchange Encrypted can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Community Social Wellbeing Development Strategy Download PDF
This slide presents social wellbeing action plan for community development, helpful in planning out goals and resources. It includes reducing litter, improving pedestrian safety and increasing access to fresh produce. Present the topic in a bit more detail with this Community Social Wellbeing Development Strategy Download PDF. Use it as a tool for discussion and navigation on Trash Bags, Gloves And Pickers, Land, Gardening Tools. This template is free to edit as deemed fit for your organization. Therefore download it now.
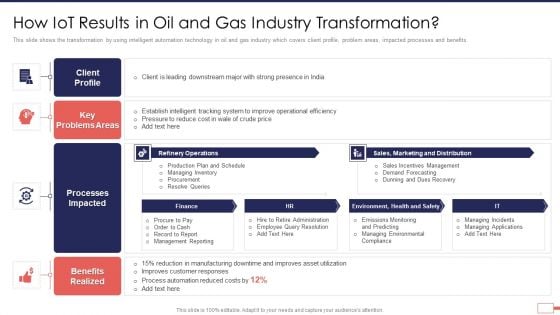
Iot Digital Twin Technology Post Covid Expenditure Management How Iot Results Ideas PDF
This slide shows the transformation by using intelligent automation technology in oil and gas industry which covers client profile, problem areas, impacted processes and benefits. Deliver and pitch your topic in the best possible manner with this iot digital twin technology post covid expenditure management how iot results ideas pdf Use them to share invaluable insights on downstream, intelligent, operational, marketing, environment, safety and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
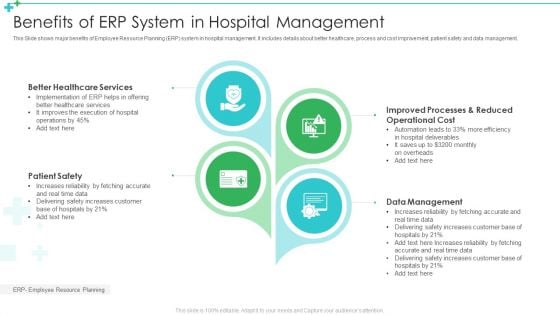
Benefits Of ERP System In Hospital Management Ppt Layouts Deck PDF
This Slide shows major benefits of Employee Resource Planning ERP system in hospital management. It includes details about better healthcare, process and cost improvement, patient safety and data management. Presenting Benefits Of ERP System In Hospital Management Ppt Layouts Deck PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Better Healthcare Services, Patient Safety, Data Management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
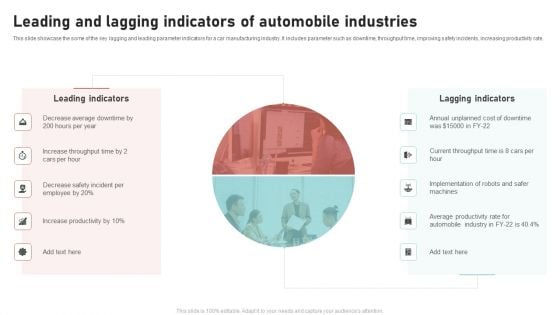
Leading And Lagging Indicators Of Automobile Industries Professional PDF
This slide showcase the some of the key lagging and leading parameter indicators for a car manufacturing industry. It includes parameter such as downtime, throughput time, improving safety incidents, increasing productivity rate. Pitch your topic with ease and precision using this Leading And Lagging Indicators Of Automobile Industries Professional PDF. This layout presents information on Leading Indicators, Lagging Indicators. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
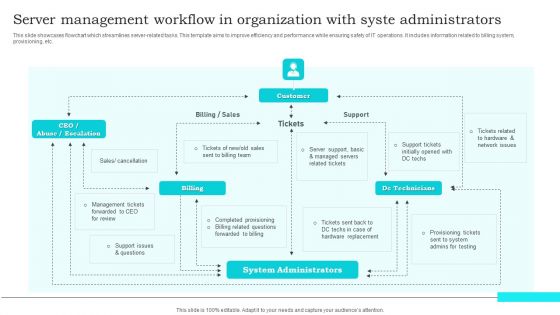
Server Management Workflow In Organization With Syste Administrators Mockup PDF
This slide showcases flowchart which streamlines server-related tasks. This template aims to improve efficiency and performance while ensuring safety of IT operations. It includes information related to billing system, provisioning, etc. Showcasing this set of slides titled Server Management Workflow In Organization With Syste Administrators Mockup PDF. The topics addressed in these templates are Management Tickets, Forwarded CEO, Review. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
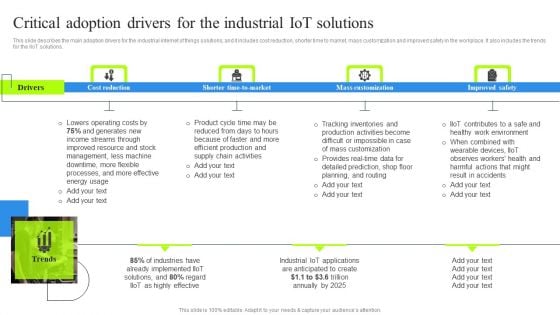
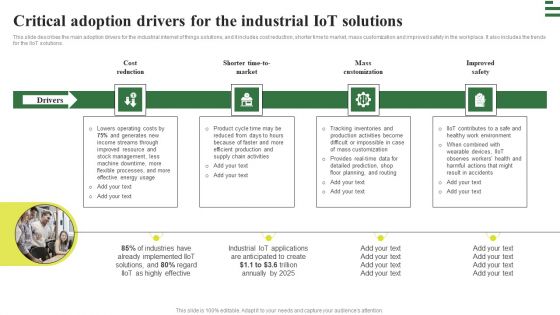
Critical Adoption Drivers For The Industrial Iot Solutions Microsoft PDF
This slide describes the main adoption drivers for the industrial internet of things solutions, and it includes cost reduction, shorter time to market, mass customization and improved safety in the workplace. It also includes the trends for the IIoT solutions. Retrieve professionally designed Critical Adoption Drivers For The Industrial Iot Solutions Microsoft PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
Transforming Manufacturing With Automation Critical Adoption Drivers Industrial Rules PDF
This slide describes the main adoption drivers for the industrial internet of things solutions, and it includes cost reduction, shorter time to market, mass customization and improved safety in the workplace. It also includes the trends for the IIoT solutions. If you are looking for a format to display your unique thoughts, then the professionally designed Transforming Manufacturing With Automation Critical Adoption Drivers Industrial Rules PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Transforming Manufacturing With Automation Critical Adoption Drivers Industrial Rules PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
Iot Integration In Manufacturing Critical Adoption Drivers For The Industrial Iot Solutions Icons PDF
This slide describes the main adoption drivers for the industrial internet of things solutions, and it includes cost reduction, shorter time to market, mass customization and improved safety in the workplace. It also includes the trends for the IIoT solutions. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Iot Integration In Manufacturing Critical Adoption Drivers For The Industrial Iot Solutions Icons PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Iot Integration In Manufacturing Critical Adoption Drivers For The Industrial Iot Solutions Icons PDF today and make your presentation stand out from the rest

IoT Solutions For Oil IoT Technology Adoption Benefits In Oil And Gas Industry IoT SS V
This slide highlights benefits of IoT technology in oil and gas industry that helps to predict equipment failure and improve safety measurers. It includes benefits such as improved operational efficiency, reduced maintenance costs, hazard management, and process automation. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download IoT Solutions For Oil IoT Technology Adoption Benefits In Oil And Gas Industry IoT SS V to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the IoT Solutions For Oil IoT Technology Adoption Benefits In Oil And Gas Industry IoT SS V. This slide highlights benefits of IoT technology in oil and gas industry that helps to predict equipment failure and improve safety measurers. It includes benefits such as improved operational efficiency, reduced maintenance costs, hazard management, and process automation.

Overview Of Warehouse Performance Management Strategies Clipart PDF
This slide presents an overview of strategy, including tactics to optimize warehouse performance. It includes addressing areas such as accuracy dimension, resource optimization, financial dimension, responsiveness and priority dimension, safety compliance and automation. Present like a pro with Overview Of Warehouse Performance Management Strategies Clipart PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
Ensure Employee Guests And Vendor Health Screening And Training Icons PDF
This slide provides information on the health screening and training criteria that must be ensured for employee, guests and vendor during an event in order to ensure safety and run the event smoothly amidst COVID 19.Deliver an awe inspiring pitch with this creative ensure employee guests and vendor health screening and training icons pdf bundle. Topics like screening protocol, improvements to event, frequently as per industry standards can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
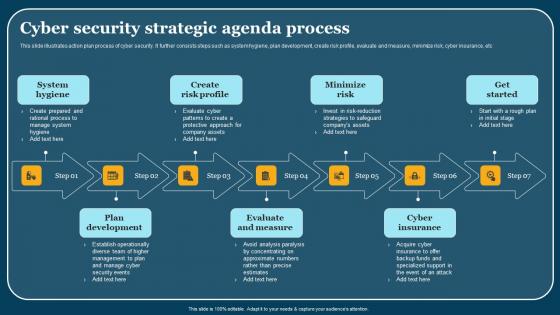
Cyber Security Strategic Agenda Process Demonstration Pdf
This slide illustrates action plan process of cyber security. It further consists steps such as system hygiene, plan development, create risk profile, evaluate and measure, minimize risk, cyber insurance, etc. Showcasing this set of slides titled Cyber Security Strategic Agenda Process Demonstration Pdf. The topics addressed in these templates are System Hygiene, Plan Development, Evaluate And Measure. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide illustrates action plan process of cyber security. It further consists steps such as system hygiene, plan development, create risk profile, evaluate and measure, minimize risk, cyber insurance, etc.

Steps To Perform Vulnerability Analysis For Network Security Pictures Pdf
This slide showcase vulnerability assessment process that help organization to identify security vulnerabilities in network system and prioritize them to plan mitigation action plan. It includes steps such as identifying, scanning, identify type of scan, configure scan etc.Showcasing this set of slides titled Steps To Perform Vulnerability Analysis For Network Security Pictures Pdf The topics addressed in these templates are Evaluate Possible Risk, Interpret Scan Results, Create Mitigation Plan All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcase vulnerability assessment process that help organization to identify security vulnerabilities in network system and prioritize them to plan mitigation action plan. It includes steps such as identifying, scanning, identify type of scan, configure scan etc.

Best Techniques For Inventory And Materials Manufacturing Strategy Driving Industry 4 0
The following slide illustrates some best practices to manage inventory and reduce blockage of financial resources . It includes elements such as just in time inventory management, safety stock, cycle counting etc. Present like a pro with Best Techniques For Inventory And Materials Manufacturing Strategy Driving Industry 4 0. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. The following slide illustrates some best practices to manage inventory and reduce blockage of financial resources . It includes elements such as just in time inventory management, safety stock, cycle counting etc.
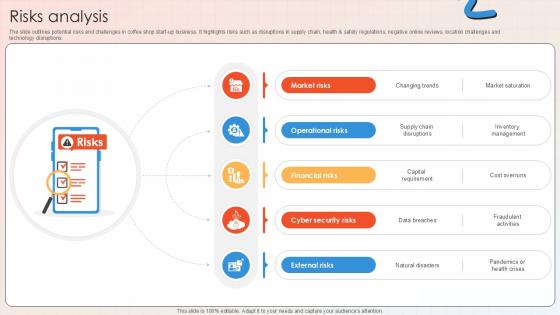
Risks Analysis Apparel And Shoes E Commerce Market PPT Example GTM SS V
The slide outlines potential risks and challenges in coffee shop start-up business. It highlights risks such as disruptions in supply chain, health and safety regulations, negative online reviews, location challenges and technology disruptions. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Risks Analysis Apparel And Shoes E Commerce Market PPT Example GTM SS V to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. The slide outlines potential risks and challenges in coffee shop start-up business. It highlights risks such as disruptions in supply chain, health and safety regulations, negative online reviews, location challenges and technology disruptions.
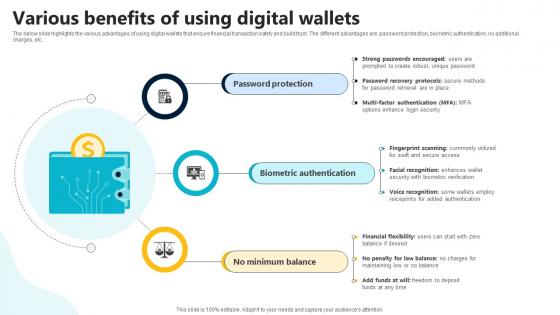
Various Benefits Of Using Digital Wallets In Depth Guide To Digital Wallets Fin SS V
The below slide highlights the various advantages of using digital wallets that ensure financial transaction safety and build trust. The different advantages are password protection, biometric authentication, no additional charges, etc. The Various Benefits Of Using Digital Wallets In Depth Guide To Digital Wallets Fin SS V is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. The below slide highlights the various advantages of using digital wallets that ensure financial transaction safety and build trust. The different advantages are password protection, biometric authentication, no additional charges, etc.
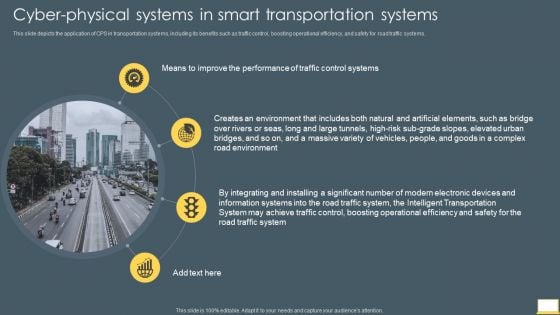
Cyber Intelligent Computing System Cyber Physical Systems In Smart Transportation Systems Themes PDF
This slide depicts the application of CPS in transportation systems, including its benefits such as traffic control, boosting operational efficiency, and safety for road traffic systems. Deliver an awe inspiring pitch with this creative Cyber Intelligent Computing System Cyber Physical Systems In Smart Transportation Systems Themes PDF bundle. Topics like Environment, Traffic Control Systems, Information Systems can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Physical Systems In Smart Transportation Systems Ppt Layouts Maker PDF
This slide depicts the application of CPS in transportation systems, including its benefits such as traffic control, boosting operational efficiency, and safety for road traffic systems. Deliver and pitch your topic in the best possible manner with this Cyber Physical Systems In Smart Transportation Systems Ppt Layouts Maker PDF. Use them to share invaluable insights on Information Systems, Environment, Control Systems and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
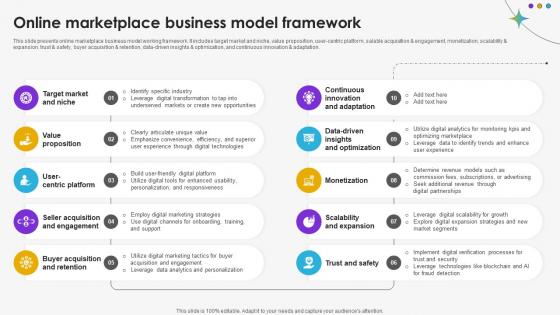
Online Marketplace Business Model Framework DT SS V
This slide presents online marketplace business model working framework. It includes target market and niche, value proposition, user-centric platform, salable acquisition and engagement, monetization, scalability and expansion, trust and safety, buyer acquisition and retention, data-driven insights and optimization, and continuous innovation and adaptation.Make sure to capture your audiences attention in your business displays with our gratis customizable Online Marketplace Business Model Framework DT SS V. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide presents online marketplace business model working framework. It includes target market and niche, value proposition, user-centric platform, salable acquisition and engagement, monetization, scalability and expansion, trust and safety, buyer acquisition and retention, data-driven insights and optimization, and continuous innovation and adaptation.

Products And Services Offered Investor Oriented Urbanlogiq Fundraising Deck
This slide includes services offered by company to integrate and visualize data. It includes services for transportation data, economic development, and fire safety. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Products And Services Offered Investor Oriented Urbanlogiq Fundraising Deck to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide includes services offered by company to integrate and visualize data. It includes services for transportation data, economic development, and fire safety.

Key Aspects Of Legal And Regulatory Compliance Successful Launch Ppt Slide
The following slide showcases legal and regulatory compliance for organic cosmetic series to ensure product safety, transparency, and trustworthiness. It outlines elements such as ingredient safety, labeling requirements, product claims, allergen information, microbial safety, packaging and sustainability, transparency, etc. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Key Aspects Of Legal And Regulatory Compliance Successful Launch Ppt Slide from Slidegeeks and deliver a wonderful presentation. The following slide showcases legal and regulatory compliance for organic cosmetic series to ensure product safety, transparency, and trustworthiness. It outlines elements such as ingredient safety, labeling requirements, product claims, allergen information, microbial safety, packaging and sustainability, transparency, etc.


 Continue with Email
Continue with Email

 Home
Home


































