Safety Inspection
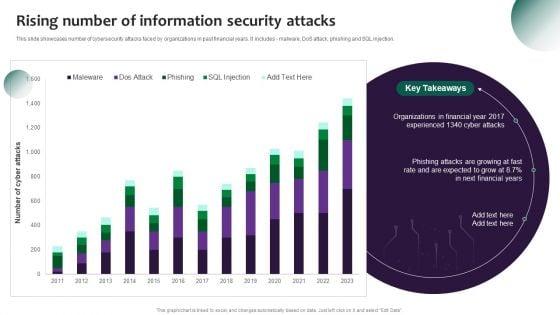
Information Systems Security And Risk Management Plan Rising Number Of Information Security Attacks Information PDF
This slide showcases number of cybersecurity attacks faced by organizations in past financial years. It includes - malware, DoS attack, phishing and SQL injection. Welcome to our selection of the Information Systems Security And Risk Management Plan Rising Number Of Information Security Attacks Information PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.
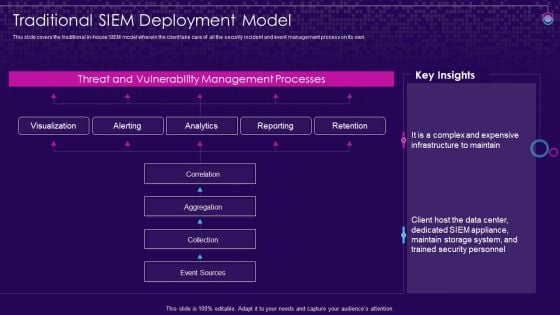
SIEM Services Traditional SIEM Deployment Model Ppt Gallery Layout Ideas PDF
This slide covers the traditional in-house SIEM model wherein the client take care of all the security incident and event management process on its own. Deliver an awe inspiring pitch with this creative siem services traditional siem deployment model ppt gallery layout ideas pdf bundle. Topics like alerting, analytics, reporting, retention can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cybersecurity Operations Cybersecops Roles And Responsibilities Of Socas A Service Ideas PDF
This slide illustrates the roles and responsibilities of the SOC-as-a-Service security model. The purpose of this slide is to highlight the various roles and responsibilities in a SOC as a Service environment. The main roles include SOC manager, security analyst, security architecture, compliance auditor, and SOC coordinator. Explore a selection of the finest Cybersecurity Operations Cybersecops Roles And Responsibilities Of Socas A Service Ideas PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Cybersecurity Operations Cybersecops Roles And Responsibilities Of Socas A Service Ideas PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Our Services Maintenance Company Profile Ppt Summary Graphics PDF
This is a our services maintenance company profile ppt summary graphics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like digital advertising, marketing and analytics, digital care package, security and maintenance. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
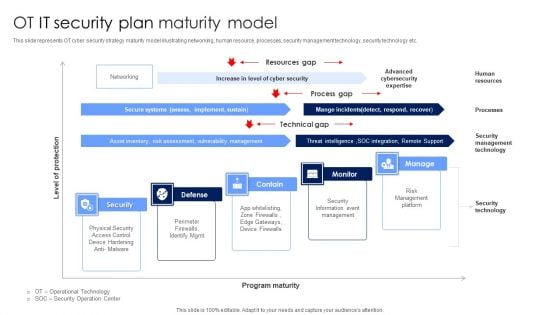
OT IT Security Plan Maturity Model Designs PDF
This slide represents OT cyber security strategy maturity model illustrating networking, human resource, processes, security management technology, security technology etc. Showcasing this set of slides titled OT IT Security Plan Maturity Model Designs PDF. The topics addressed in these templates are Security Information Event Management, Risk Management Platform, Security Technology. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Framework Administration Interdependence Resiliency And Security Ppt Ideas PDF
Presenting framework administration interdependence resiliency and security ppt ideas pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like lifecycle adaptive components of resilience framework, infrastructure resilience wheel. In addition, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.
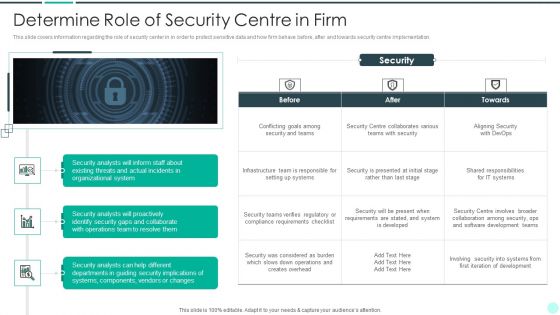
Executing Advance Data Analytics At Workspace Determine Role Of Security Centre In Firm Sample PDF
This slide covers information regarding the role of security center in in order to protect sensitive data and how firm behave before, after and towards security centre implementation. This is a executing advance data analytics at workspace determine role of security centre in firm sample pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like determine role of security centre in firm. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Blockchain Technology For Security In Banking Vector Icon Ppt PowerPoint Presentation Icon Infographic Template PDF
Presenting blockchain technology for security in banking vector icon ppt powerpoint presentation icon infographic template pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including blockchain technology for security in banking vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
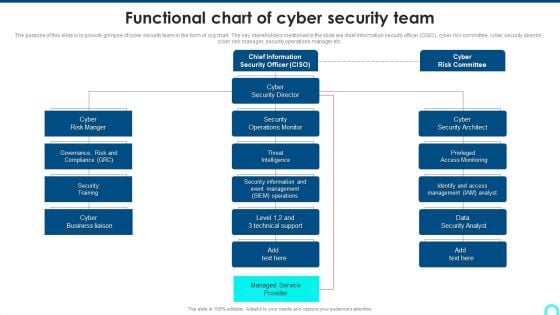
Functional Chart Of Cyber Security Team Diagrams PDF
The purpose of this slide is to provide glimpse of cyber security team in the form of org chart. The key stakeholders mentioned in the slide are chief information security officer CISO, cyber risk committee, cyber security director, cyber risk manager, security operations manager etc.Deliver an awe inspiring pitch with this creative Functional Chart Of Cyber Security Team Diagrams PDF bundle. Topics like Access Monitoring, Security Architect, Security Information can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
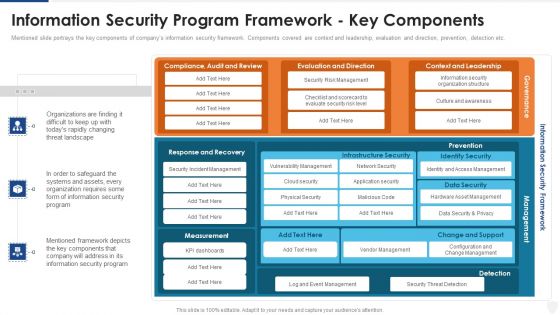
Information Security Program Framework Key Components Ppt Inspiration Ideas PDF
Mentioned slide portrays the key components of companys information security framework. Components covered are context and leadership, evaluation and direction, prevention, detection etc. Deliver and pitch your topic in the best possible manner with this information security program framework key components ppt inspiration ideas pdf. Use them to share invaluable insights on network security, application security, vendor management, data security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Framework Of Information IT Security Action Program Slides PDF
This slide focuses on information security action program framework which covers governance plan, security standards, stakeholder engagement and operational management to manage risks, handling threat, data security management, etc.Showcasing this set of slides titled Framework Of Information IT Security Action Program Slides PDF The topics addressed in these templates are Security Standards, Data Protection, Response Structure All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

IT Security Hacker Interview Schedule For New Professionals Portrait PDF
This slide represents the interview schedule for new employees, including ethical hackers, security consultants, and IT security analysts to be hired to prevent hacking.Deliver and pitch your topic in the best possible manner with this IT Security Hacker Interview Schedule For New Professionals Portrait PDF. Use them to share invaluable insights on Ethical Hacker, Security Consultant, Security Analyst and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
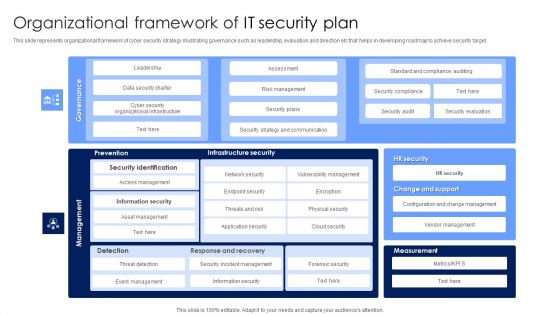
Organizational Framework Of IT Security Plan Microsoft PDF
This slide represents organizational framework of cyber security strategy illustrating governance such as leadership, evaluation and direction etc that helps in developing roadmap to achieve security target. Showcasing this set of slides titled Organizational Framework Of IT Security Plan Microsoft PDF. The topics addressed in these templates are Infrastructure Security, Management, Information Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
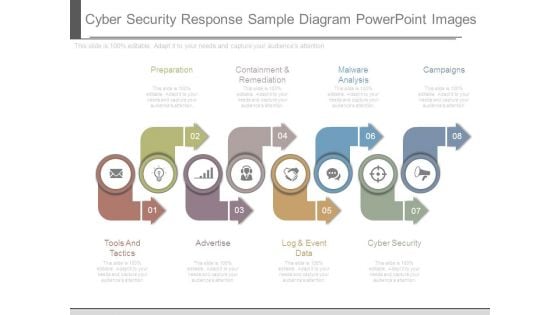
Cyber Security Response Sample Diagram Powerpoint Images
This is a cyber security response sample diagram powerpoint images. This is a eight stage process. The stages in this process are preparation, containment and remediation, malware analysis, campaigns, cyber security, log and event data, advertise, tools and tactics.
Integrating Data Privacy System Data Privacy Vs Data Security Ppt Icon Guidelines PDF
This slide compares data privacy with data security, indicating that security is concerned with safeguarding data, and privacy is about responsible data usage. Make sure to capture your audiences attention in your business displays with our gratis customizable Integrating Data Privacy System Data Privacy Vs Data Security Ppt Icon Guidelines PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
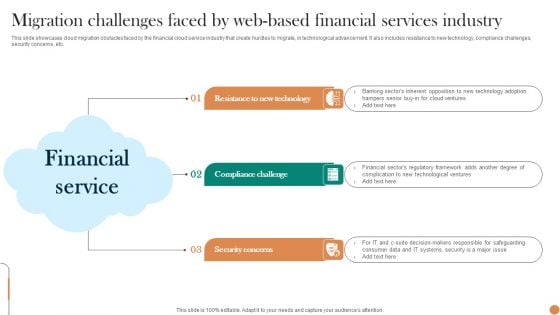
Migration Challenges Faced By Web Based Financial Services Industry Professional PDF
This slide showcases cloud migration obstacles faced by the financial cloud service industry that create hurdles to migrate, in technological advancement. It also includes resistance to new technology, compliance challenges, security concerns, etc. Presenting Migration Challenges Faced By Web Based Financial Services Industry Professional PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Resistance To New Technology, Compliance Challenge, Security Concerns. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
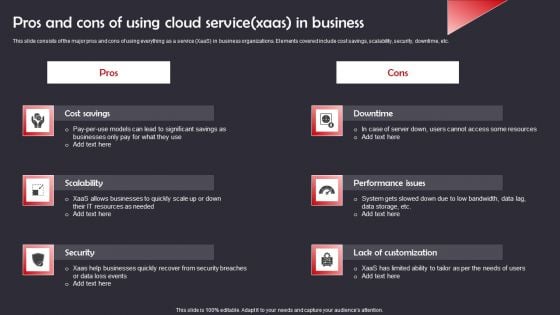
Pros And Cons Of Using Cloud Service Xaas In Business Formats PDF
This slide consists of the major pros and cons of using everything as a service XaaS in business organizations. Elements covered include cost savings, scalability, security, downtime, etc. Presenting Pros And Cons Of Using Cloud Service Xaas In Business Formats PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Cost Savings, Scalability, Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Saas Application Cloud Security Infrastructure Icon Ppt PowerPoint Presentation Gallery Introduction PDF
Persuade your audience using this Saas Application Cloud Security Infrastructure Icon Ppt PowerPoint Presentation Gallery Introduction PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Saas Application, Cloud Security, Infrastructure Icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
IT Managing Cyber Security Incident Response Icon Ppt Portfolio Model PDF
Persuade your audience using this IT Managing Cyber Security Incident Response Icon Ppt Portfolio Model PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including IT Managing, Cyber Security, Incident Response, Icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
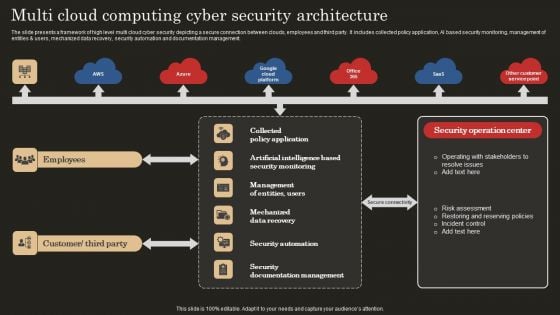
Multi Cloud Computing Cyber Security Architecture Microsoft PDF
The slide presents a framework of high level multi cloud cyber security depicting a secure connection between clouds, employees and third party. It includes collected policy application, AI based security monitoring, management of entities and users, mechanized data recovery, security automation and documentation management. Showcasing this set of slides titled Multi Cloud Computing Cyber Security Architecture Microsoft PDF. The topics addressed in these templates are Mechanized Data Recovery, Security Automation, Employees. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Types Of Cloud Security Solutions Cloud Computing Security IT Ppt Layouts Example PDF
This slide represents the cloud security solutions such as hybrid cloud security solutions, SMB cloud security solutions, and enterprise cloud security solutions. This is a types of cloud security solutions cloud computing security it ppt layouts example pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like hybrid cloud security solutions, smb cloud security solutions, enterprise cloud security solutions. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Essential Pillars Of Cloud Security Cloud Computing Security IT Ppt Design Ideas PDF
This slide shows the four essential pillars of cloud security, namely visibility and consistency, process-based security, network security, and identity security. Presenting essential pillars of cloud security cloud computing security it ppt design ideas pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like visibility and consistency, process based security, network security, identity security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
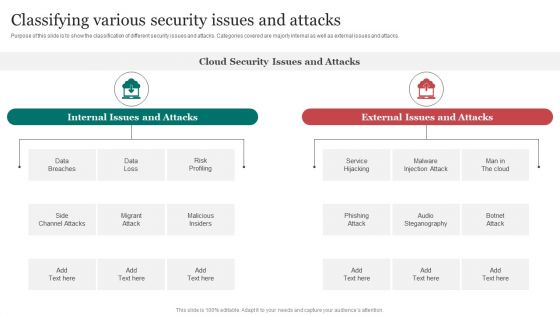
Classifying Various Security Issues And Attacks Improving Cybersecurity Incident Elements PDF
Purpose of this slide is to show the classification of different security issues and attacks. Categories covered are majorly internal as well as external issues and attacks.Slidegeeks is here to make your presentations a breeze with Classifying Various Security Issues And Attacks Improving Cybersecurity Incident Elements PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you Are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
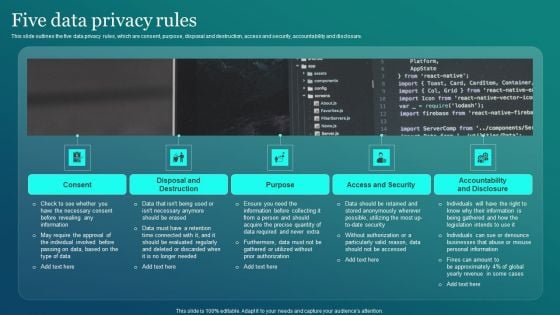
Information Security Five Data Privacy Rules Ppt PowerPoint Presentation File Deck PDF
This slide outlines the five data privacy rules, which are consent, purpose, disposal and destruction, access and security, accountability and disclosure. Slidegeeks is here to make your presentations a breeze with Information Security Five Data Privacy Rules Ppt PowerPoint Presentation File Deck PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
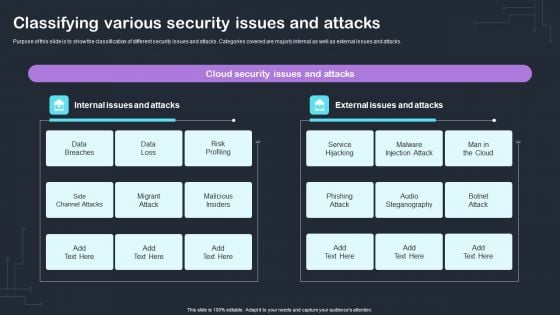
Cyber Risks And Incident Response Playbook Classifying Various Security Issues And Attacks Microsoft PDF
Purpose of this slide is to show the classification of different security issues and attacks. Categories covered are majorly internal as well as external issues and attacks. Slidegeeks is here to make your presentations a breeze with Cyber Risks And Incident Response Playbook Classifying Various Security Issues And Attacks Microsoft PD With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, youre sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether youre giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
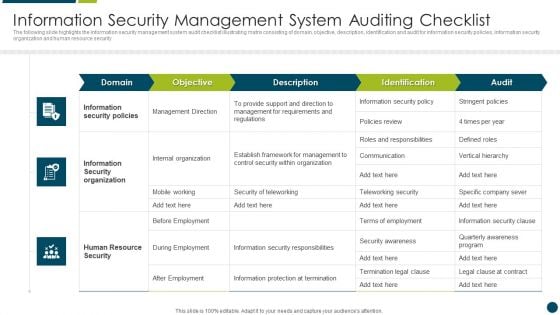
Information Security Management System Auditing Brochure PDF
The following slide highlights the information security management system audit process illustrating information security system details, information collection, statement o applicability review, audit scope, risk management analysis, gap analysis, business continuity and contingency plan review, mitigation strategy and compliance audit activities PresentingInformation Security Management System Auditing Brochure PDF to dispense important information. This template comprises eight stages. It also presents valuable insights into the topics including Risk Management Analysis, Information Collection, Mitigation Strategy. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully
Measures And Ways To Mitigate Security Management Challenges Icons PDF
This slide provides information about the ways and measures through which the company and IT security managers can overcome the problems and issues related to Security Management. Deliver and pitch your topic in the best possible manner with this measures and ways to mitigate security management challenges icons pdf. Use them to share invaluable insights on information, security training, implementing, technologies and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
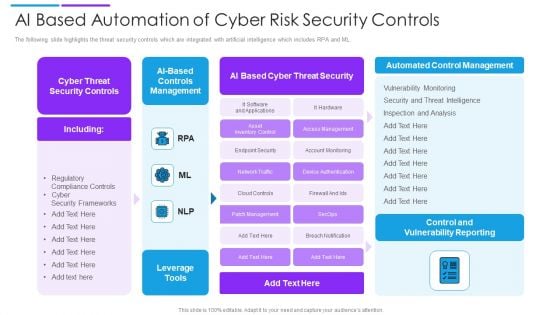
AI Based Automation Of Cyber Risk Security Controls Summary PDF
The following slide highlights the threat security controls which are integrated with artificial intelligence which includes RPA and ML. Showcasing this set of slides titled ai based automation of cyber risk security controls summary pdf. The topics addressed in these templates are controls management, cyber threat security controls, ai based cyber threat security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

IT Security Hacker Ethical Hackers Roles And Responsibilities Background PDF
This slide depicts why organizations recruit ethical hackers, including effective security measures, protecting customer information, raising security awareness, and so on.Deliver and pitch your topic in the best possible manner with this IT Security Hacker Ethical Hackers Roles And Responsibilities Background PDF. Use them to share invaluable insights on Effective Preventative, Information Systems, Security Consciousness and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Various Strategies For Cloud Computing Security Brochure PDF
This slide shows strategies which can be used by organizations for cloud computing security. These strategies are end to end data encryption, secure data transfers, local data backups, etc. Showcasing this set of slides titled Various Strategies For Cloud Computing Security Brochure PDF. The topics addressed in these templates are Various Strategies, For Cloud, Computing Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
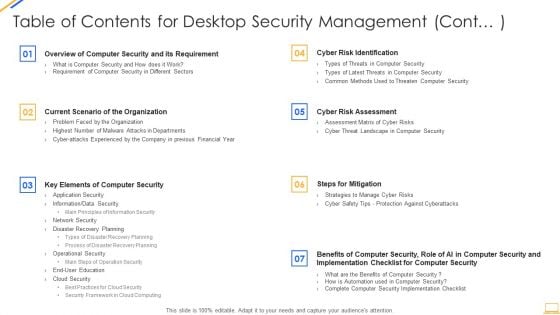
Table Of Contents For Desktop Security Management Cont Ideas PDF
Deliver an awe inspiring pitch with this creative table of contents for desktop security management cont ideas pdf bundle. Topics like security implementation, security budget, dashboards, communication can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cloud Computing Services Disadvantages Of Iaas Cloud Computing Layer Introduction PDF
This slide shows the disadvantages of the IaaS cloud computing layer based on security, maintenance and upgrade, and interoperability issues. This is a Cloud Computing Services Disadvantages Of Iaas Cloud Computing Layer Introduction PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Maintenance And Upgrade, Security, Interoperability Issues. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
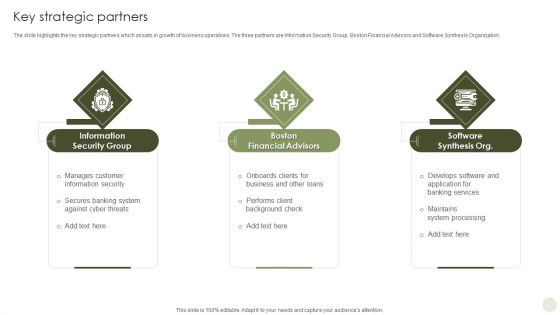
Commercial Bank Financial Services Company Profile Key Strategic Partners Template PDF
The slide highlights the key strategic partners which assists in growth of business operations. The three partners are Information Security Group, Boston Financial Advisors and Software Synthesis Organization. Presenting Commercial Bank Financial Services Company Profile Key Strategic Partners Template PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Information Security Group, Boston Financial Advisors, Software Synthesis Org. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Cloud Distribution Service Models Disadvantages Of Iaas Cloud Computing Layer Icons PDF
This slide shows the disadvantages of the IaaS cloud computing layer based on security, maintenance and upgrade, and interoperability issues. This is a Cloud Distribution Service Models Disadvantages Of Iaas Cloud Computing Layer Icons PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security, Interoperability Issues, Maintenance And Upgrade. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
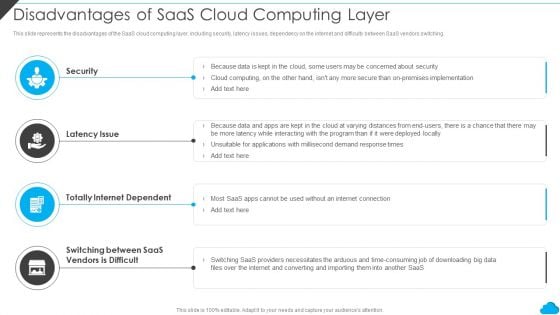
Cloud Distribution Service Models Disadvantages Of Saas Cloud Computing Layer Sample PDF
This slide represents the disadvantages of the SaaS cloud computing layer, including security, latency issues, dependency on the internet and difficulty between SaaS vendors switching. This is a Cloud Distribution Service Models Disadvantages Of Saas Cloud Computing Layer Sample PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Totally Internet Dependent, Latency Issue, Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
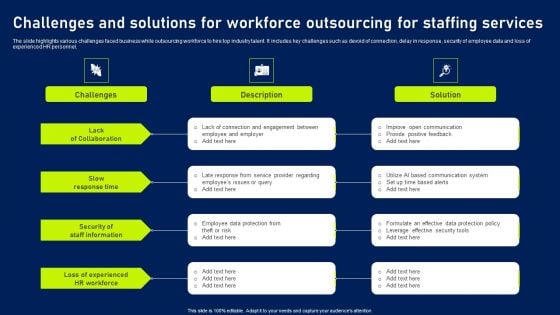
Challenges And Solutions For Workforce Outsourcing For Staffing Services Diagrams PDF
The slide highlights various challenges faced business while outsourcing workforce to hire top industry talent. It includes key challenges such as devoid of connection, delay in response, security of employee data and loss of experienced HR personnel. Presenting Challenges And Solutions For Workforce Outsourcing For Staffing Services Diagrams PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Lack Collaboration, Slow Response Time, Security Staff Information. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
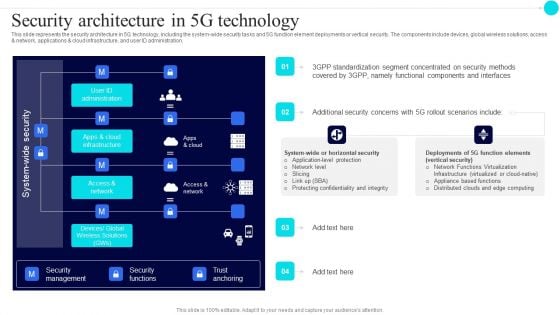
Security Architecture In 5G Technology 5G Functional Architecture Topics PDF
This slide represents the security architecture in 5G technology, including the system-wide security tasks and 5G function element deployments or vertical security. The components include devices, global wireless solutions, access and network, applications and cloud infrastructure, and user ID administration.Deliver an awe inspiring pitch with this creative Security Architecture In 5G Technology 5G Functional Architecture Topics PDF bundle. Topics like Standardization Segment, Concentrated Security, Components Interfaces can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
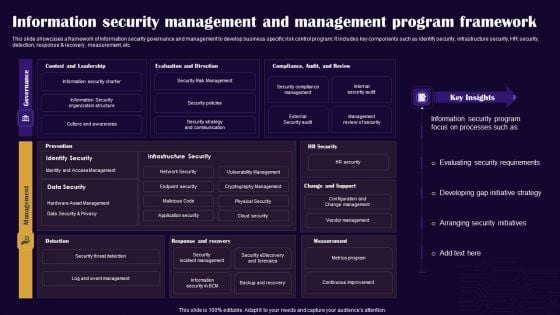
Information Security Management And Management Program Framework Inspiration PDF
This slide showcases a framework of information security governance and management to develop business specific risk control program. It includes key components such as identify security, infrastructure security, HR security, detection, response and recovery, measurement, etc. Showcasing this set of slides titled Information Security Management And Management Program Framework Inspiration PDF. The topics addressed in these templates are Governance, Management, Key Insights All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
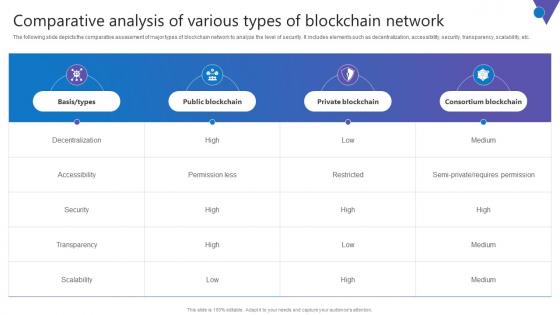
Comparative Analysis Of Various Comprehensive Guide To Blockchain Digital Security Slides Pdf
The following slide depicts the comparative assessment of major types of blockchain network to analyze the level of security. It includes elements such as decentralization, accessibility, security, transparency, scalability, etc. Find a pre designed and impeccable Comparative Analysis Of Various Comprehensive Guide To Blockchain Digital Security Slides Pdf. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. The following slide depicts the comparative assessment of major types of blockchain network to analyze the level of security. It includes elements such as decentralization, accessibility, security, transparency, scalability, etc.

Organizational Security Solutions Table Of Contents Summary PDF
Deliver an awe inspiring pitch with this creative organizational security solutions table of contents summary pdf bundle. Topics like management, implementation, analysis, technologies can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security And Process Integration Table Of Contents Designs PDF
Deliver an awe inspiring pitch with this creative security and process integration table of contents designs pdf bundle. Topics like management, implementation, analysis, technologies can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
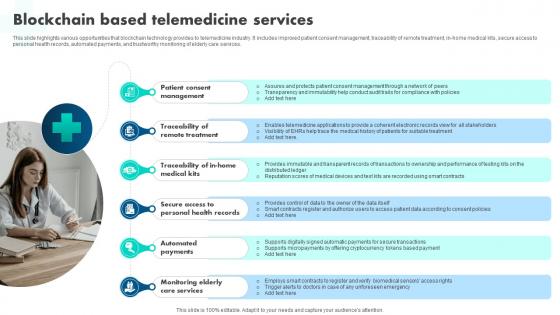
A55 How Blockchain Is Reshaping Blockchain Based Telemedicine Services BCT SS V
This slide highlights various opportunities that blockchain technology provides to telemedicine industry. It includes improved patient consent management, traceability of remote treatment, in-home medical kits, secure access to personal health records, automated payments, and trustworthy monitoring of elderly care services. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate A55 How Blockchain Is Reshaping Blockchain Based Telemedicine Services BCT SS V for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide highlights various opportunities that blockchain technology provides to telemedicine industry. It includes improved patient consent management, traceability of remote treatment, in-home medical kits, secure access to personal health records, automated payments, and trustworthy monitoring of elderly care services.

Incorporating HIS To Enhance Healthcare Services Comparative Analysis Of Health Management Information System Tools Summary PDF
This slide covers comparative assessment of health management information tool to select suitable one. It involves features such as clinical database, data compliance, enhanced security and healthcare analytics. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Incorporating HIS To Enhance Healthcare Services Comparative Analysis Of Health Management Information System Tools Summary PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Incorporating HIS To Enhance Healthcare Services Comparative Analysis Of Health Management Information System Tools Summary PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
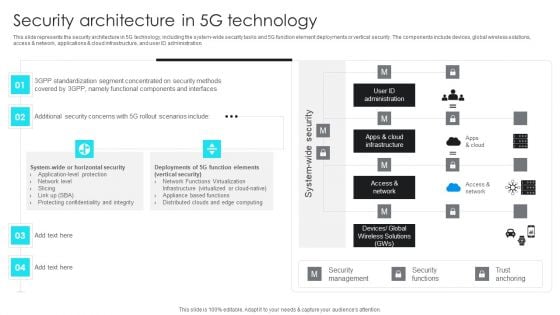
5G Network Operations Security Architecture In 5G Technology Inspiration PDF
This slide represents the security architecture in 5G technology, including the system-wide security tasks and 5G function element deployments or vertical security. The components include devices, global wireless solutions, access and network, applications cloud infrastructure, and user ID administration. Presenting this PowerPoint presentation, titled 5G Network Operations Security Architecture In 5G Technology Inspiration PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this 5G Network Operations Security Architecture In 5G Technology Inspiration PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable 5G Network Operations Security Architecture In 5G Technology Inspiration PDFthat is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.

IT Security Automation Systems Guide Domain Security Controls That Can Be Automated Sample PDF
This slide highlights the domain security controls that can be automated which includes security policy, asset management, human resources security, communications and operations management and access control domain. There are so many reasons you need a IT Security Automation Systems Guide Domain Security Controls That Can Be Automated Sample PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
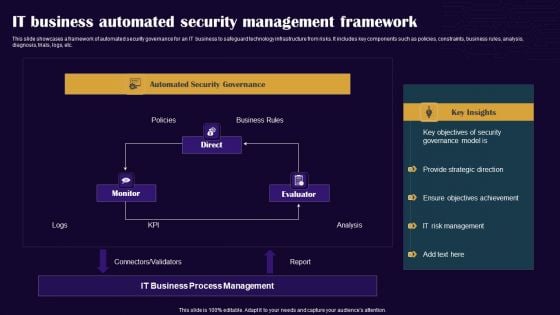
IT Business Automated Security Management Framework Professional PDF
This slide showcases a framework of automated security governance for an IT business to safeguard technology infrastructure from risks. It includes key components such as policies, constraints, business rules, analysis, diagnosis, trials, logs, etc. Showcasing this set of slides titled IT Business Automated Security Management Framework Professional PDF. The topics addressed in these templates are Monitor, Direct, Evaluator. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
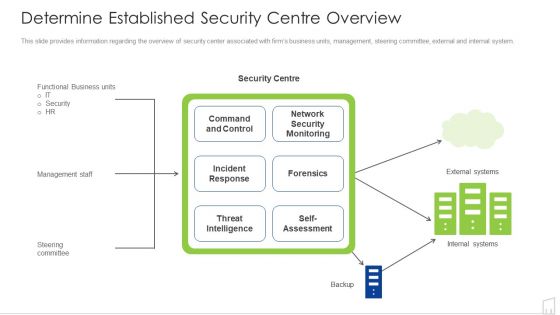
Determine Established Security Centre Overview Ppt Show Visual Aids PDF
This slide provides information regarding the overview of security center associated with firms business units, management, steering committee, external and internal system. Deliver an awe inspiring pitch with this creative determine established security centre overview ppt show visual aids pdf bundle. Topics like security, network, systems, management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
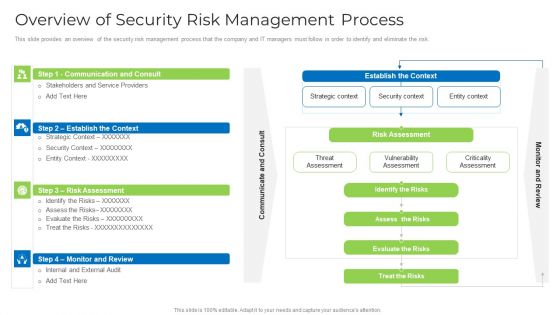
Overview Of Security Risk Management Process Formats PDF
This slide provides an overview of the security risk management process that the company and IT managers must follow in order to identify and eliminate the risk. Deliver an awe inspiring pitch with this creative overview of security risk management process formats pdf bundle. Topics like strategic context, vulnerability assessment, security context, risks can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Security Camera System Company Profile Awards And Accolades Portrait PDF
This slide highlights the awards and allocates received by security company which includes best smart home security systems, best leak and smoke detectors, and innovative product of the year.Deliver an awe inspiring pitch with this creative Security Camera System Company Profile Awards And Accolades Portrait PDF bundle. Topics like Digital Trends, Consumer Technology, Technology Association can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Manpower Corporate Security Business Profile Crisis Management Team Rules PDF
This slide highlights the security company crisis management team which includes general manager, guard supervisor, mobile response team manpower and equipment Deliver an awe inspiring pitch with this creative Manpower Corporate Security Business Profile Crisis Management Team Rules PDF bundle. Topics like Team Driver, Security Guards, Equipment can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cryptocurrency Ledger Is Blockchain Technology Secure Slides PDF
This slide defines the security of blockchain technology and how hash codes are helpful to maintain data integrity and security in blockchain. Deliver an awe inspiring pitch with this creative Cryptocurrency Ledger Is Blockchain Technology Secure Slides PDF bundle. Topics like Digital Data, Blockchain Networks, Technology can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
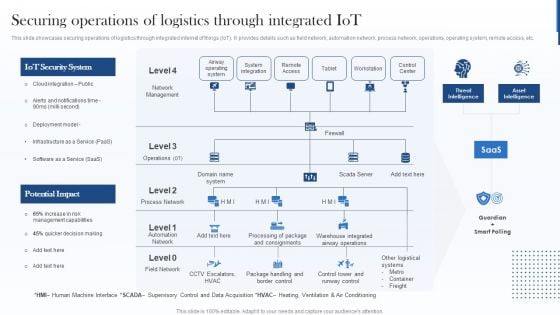
Securing Operations Of Logistics Through Integrated Iot Guidelines PDF
This slide showcases securing operations of logistics through integrated internet of things IoT. It provides details such as field network, automation network, process network, operations, operating system, remote access, etc. Deliver and pitch your topic in the best possible manner with this Securing Operations Of Logistics Through Integrated Iot Guidelines PDF. Use them to share invaluable insights on Iot Security System, Potential Impact, Warehouse and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
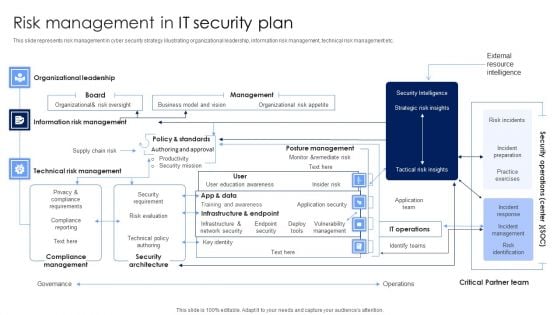
Risk Management In IT Security Plan Rules PDF
This slide represents risk management in cyber security strategy illustrating organizational leadership, information risk management, technical risk management etc. Pitch your topic with ease and precision using this Risk Management In IT Security Plan Rules PDF. This layout presents information on Security Architecture, Compliance Management, Technical Risk Management. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
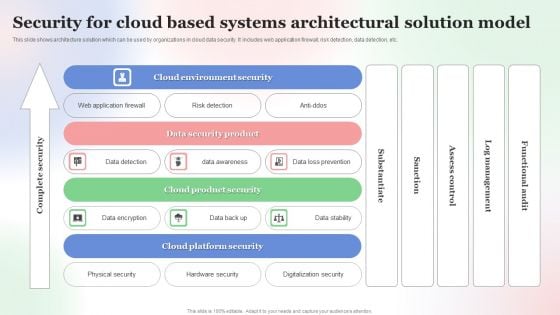
Security For Cloud Based Systems Architectural Solution Model Background PDF
This slide shows architecture solution which can be used by organizations in cloud data security. It includes web application firewall, risk detection, data detection, etc. Showcasing this set of slides titled Security For Cloud Based Systems Architectural Solution Model Background PDF. The topics addressed in these templates are Security For Cloud Based, Systems Architectural Solution Model. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cloud Computing Application Security Architecture Framework Elements PDF
The slide shows a framework describing security architecture to meet organizational unique requirements. It includes setting goals, determining process, constructing architecture and reviewing and revising security model. Showcasing this set of slides titled Cloud Computing Application Security Architecture Framework Elements PDF. The topics addressed in these templates are Set Goals, Determine Process, Construct Architecture. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
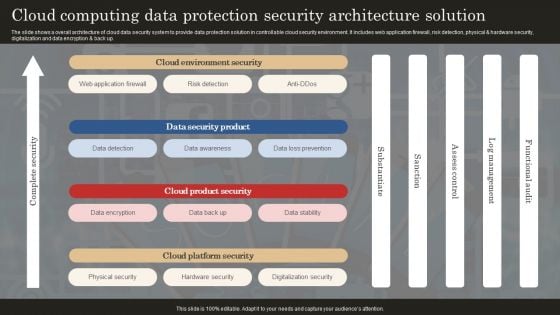
Cloud Computing Data Protection Security Architecture Solution Professional PDF
The slide shows a overall architecture of cloud data security system to provide data protection solution in controllable cloud security environment. It includes web application firewall, risk detection, physical and hardware security, digitalization and data encryption and back up. Showcasing this set of slides titled Cloud Computing Data Protection Security Architecture Solution Professional PDF. The topics addressed in these templates are Web Application Firewall, Data Detection, Data Awareness. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
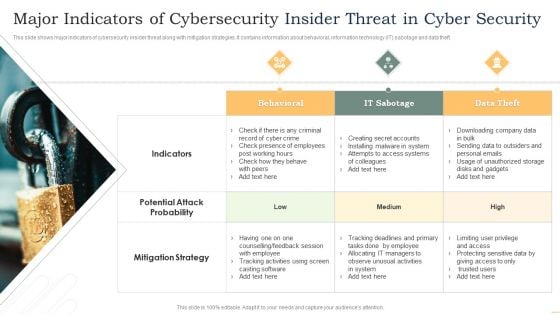
Major Indicators Of Cybersecurity Insider Threat In Cyber Security Microsoft PDF
This slide shows major indicators of cybersecurity insider threat along with mitigation strategies. It contains information about behavioral, information technology IT sabotage and data theft. Presenting Major Indicators Of Cybersecurity Insider Threat In Cyber Security Microsoft PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Behavioral, IT Sabotage, Data Theft. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Data Warehouse Security Mechanism And Procedure Icon Demonstration PDF
Showcasing this set of slides titled Data Warehouse Security Mechanism And Procedure Icon Demonstration PDF. The topics addressed in these templates are Data Warehouse, Security Mechanism, Procedure Icon. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Cyber Security Certification Career Roadmap Icon Pictures PDF
Showcasing this set of slides titled Cyber Security Certification Career Roadmap Icon Pictures PDF. The topics addressed in these templates are Career Roadmap Icon, Cyber Security Certification. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
IT Security Plan Icon Depicting Biometric Identification Topics PDF
Showcasing this set of slides titled IT Security Plan Icon Depicting Biometric Identification Topics PDF. The topics addressed in these templates are IT Security Plan Icon, Depicting Biometric Identification. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.


 Continue with Email
Continue with Email

 Home
Home


































