Safety Management Strategy Ppt

RPA As A Integration Factors For Business Processes Portrait PDF
Following Slide Covers Various Factors Associated With Robotic Process Automation As Service. Purpose Of This Slide Is To Understand The Role Of Automation In Business Efficiency And Cost Reduction. It Includes Factors Such As Platforms, Security. Maintenance Etc. With Description And Impact Persuade your audience using this RPA As A Integration Factors For Business Processes Portrait PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Factors, Description, Impact. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
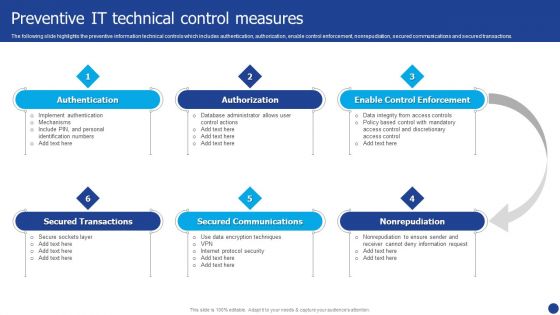
Information Technology Threat Mitigation Methods Preventive IT Technical Control Measures Information PDF
The following slide highlights the preventive information technical controls which includes authentication, authorization, enable control enforcement, nonrepudiation, secured communications and secured transactions. Presenting Information Technology Threat Mitigation Methods Preventive IT Technical Control Measures Information PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Authorization, Secured Communications, Authentication. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
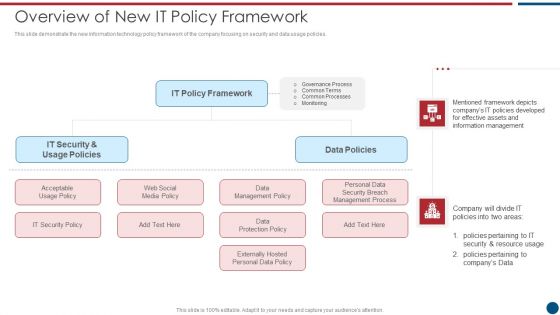
Risk Based Procedures To IT Security Overview Of New IT Policy Framework Guidelines PDF
This slide demonstrate the new information technology policy framework of the company focusing on security and data usage policies. Presenting Risk Based Procedures To IT Security Overview Of New IT Policy Framework Guidelines PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like IT Policy, Data Policies, IT Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
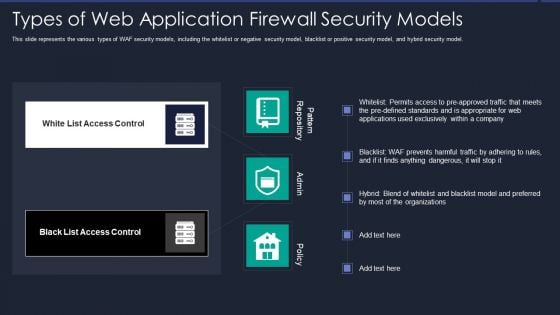
Web App Firewall Services IT Types Of Web Application Firewall Security Models Background PDF
This slide represents the various types of WAF security models, including the whitelist or negative security model, blacklist or positive security model, and hybrid security model. Presenting web app firewall services it types of web application firewall security models background pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like applications, organizations. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
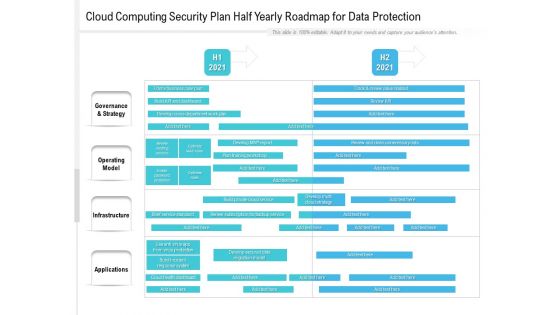
Cloud Computing Security Plan Half Yearly Roadmap For Data Protection Formats
Presenting our innovatively structured cloud computing security plan half yearly roadmap for data protection formats Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.
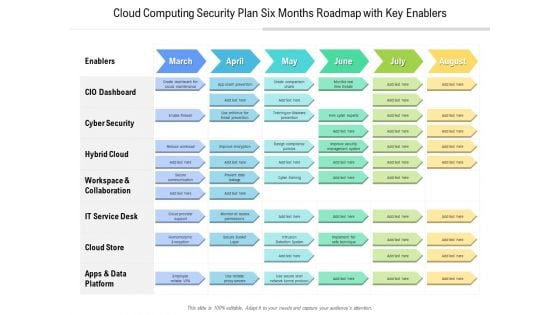
Cloud Computing Security Plan Six Months Roadmap With Key Enablers Ideas
Presenting our innovatively structured cloud computing security plan six months roadmap with key enablers ideas Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.
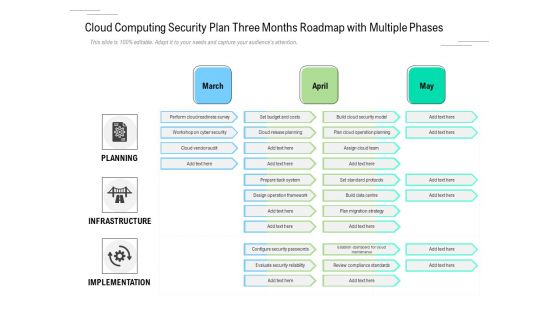
Cloud Computing Security Plan Three Months Roadmap With Multiple Phases Clipart
Presenting our innovatively structured cloud computing security plan three months roadmap with multiple phases clipart Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.

Cyber Security Administration In Organization Evaluating Financial Practices In Firm Rules PDF
The firm can track the financial performance by looking the financial practices it follows in order to avoid any early signs of financial distress. Presenting cyber security administration in organization evaluating financial practices in firm rules pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like evaluating financial practices in firm. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
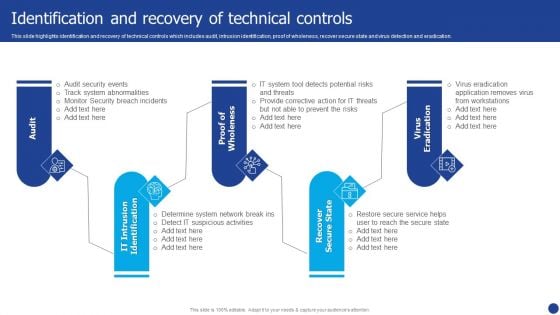
Information Technology Threat Mitigation Methods Identification And Recovery Of Technical Controls Demonstration PDF
This slide highlights identification and recovery of technical controls which includes audit, intrusion identification, proof of wholeness, recover secure state and virus detection and eradication. Presenting Information Technology Threat Mitigation Methods Identification And Recovery Of Technical Controls Demonstration PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Recover Secure State, Virus Eradication, Audit. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
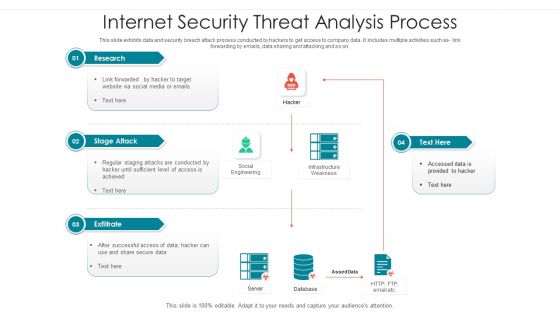
Internet Security Threat Analysis Process Brochure PDF
Following slide showcase how a data breach process is performed by hacker to collect and utilize company data. It includes following activities such as code integration with company software, so on. Showcasing this set of slides titled internet security threat analysis process brochure pdf. The topics addressed in these templates are supply chain attack, execution persistence, defense evasion, exfiltration, keyboard attack. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Weekly Cybersecurity Awareness Training Program Schedule Timeline Guidelines PDF
This slide covers various courses for employees to aware about IT security threats. It includes identification of compliance stands, audit standards, incident trends, organisations security awareness, etc.Showcasing this set of slides titled Weekly Cybersecurity Awareness Training Program Schedule Timeline Guidelines PDF. The topics addressed in these templates are Compliance Standards, Identify Audit Standards, Security Training. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Secure Attachment Psychology In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Secure Attachment Psychology In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Secure Attachment Psychology that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Secure Attachment Psychology In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Cyber Security Milestones In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Cyber Security Milestones In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Cyber Security Milestones that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Cyber Security Milestones In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Firewall Security Audit Checklist In Powerpoint And Google Slides Cpb
Presenting our innovatively-designed set of slides titled Firewall Security Audit Checklist In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Firewall Security Audit Checklist that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well-structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Firewall Security Audit Checklist In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
System Security Diagram In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled System Security Diagram In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits System Security Diagram that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our System Security Diagram In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
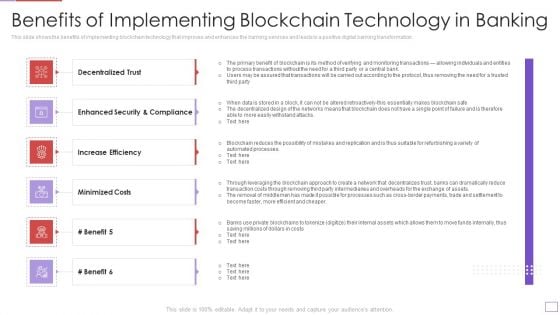
Utilization Of Digital Industry Evolution Methods Benefits Of Implementing Blockchain Technology In Banking Summary PDF
This slide shows the benefits of implementing blockchain technology that improves and enhances the banking services and leads to a positive digital banking transformation. Presenting utilization of digital industry evolution methods benefits of implementing blockchain technology in banking summary pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics likedecentralized trust, increase efficiency, minimized costs, enhanced security and compliance. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
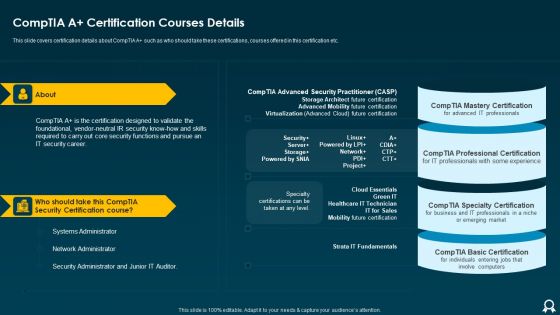
IT Data Services Certification Programs Comptia A Certification Courses Details Formats PDF
Presenting IT Data Services Certification Programs Comptia A Certification Courses Details Formats PDF to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like Security Certification Course, Network Administrator, Systems Administrator. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Business Information Cyber Protection Program For Threat Prevention Background PDF
This slide covers business cyber security program for threat prevention which includes identify, protect, detect, respond and recover.Showcasing this set of slides titled Business Information Cyber Protection Program For Threat Prevention Background PDF. The topics addressed in these templates are Business Environment, Administrative Governance, Evaluating Risk. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
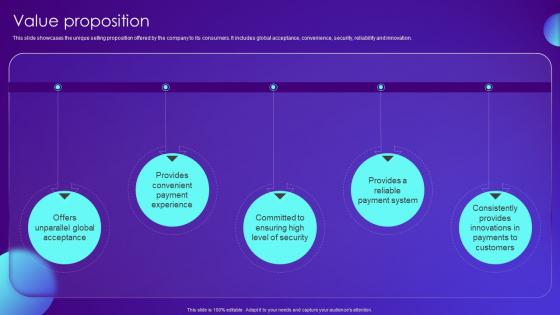
Value Proposition Payment Card Services Business Model BMC SS V
This slide showcases the unique selling proposition offered by the company to its consumers. It includes global acceptance, convenience, security, reliability and innovation. Get a simple yet stunning designed Value Proposition Payment Card Services Business Model BMC SS V. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Value Proposition Payment Card Services Business Model BMC SS V can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide showcases the unique selling proposition offered by the company to its consumers. It includes global acceptance, convenience, security, reliability and innovation.
Workforce Security Realization Coaching Plan Security Awareness Tracking Kpis Inspiration PDF
This slide covers the key performance for security awareness training including compliance, security culture and incident reduction. This is a workforce security realization coaching plan security awareness tracking kpis inspiration pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like compliance, security culture, incident reduction. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Project Security Administration IT Facilities Rendered By Security Centre Implementation Clipart PDF
This slide provides information regarding the various facilities that are offered by successful implementation of security center in the organization in terms if malware detection, phishing detection, investigations by HR, risk mitigation, etc. Presenting project security administration it facilities rendered by security centre implementation clipart pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like malware detection and investigation, phishing detection and prevention, investigations by hr, risk mitigation of left employees. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
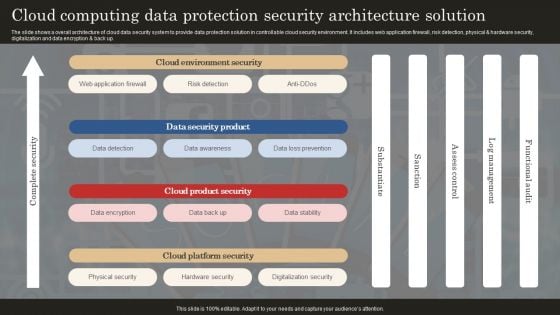
Cloud Computing Data Protection Security Architecture Solution Professional PDF
The slide shows a overall architecture of cloud data security system to provide data protection solution in controllable cloud security environment. It includes web application firewall, risk detection, physical and hardware security, digitalization and data encryption and back up. Showcasing this set of slides titled Cloud Computing Data Protection Security Architecture Solution Professional PDF. The topics addressed in these templates are Web Application Firewall, Data Detection, Data Awareness. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
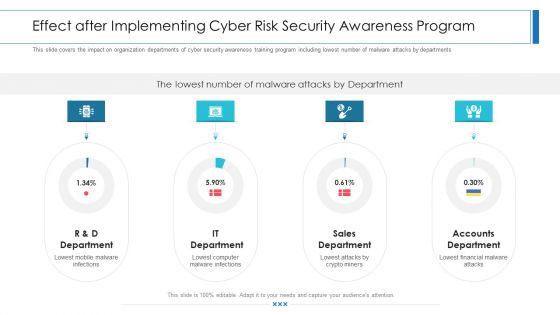
Workforce Security Realization Coaching Plan Effect After Implementing Cyber Risk Security Awareness Program Structure PDF
This slide covers the impact on organization departments of cyber security awareness training program including lowest number of malware attacks by departments. Presenting workforce security realization coaching plan effect after implementing cyber risk security awareness program structure pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like it department, sales department, accounts department. In addition, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.
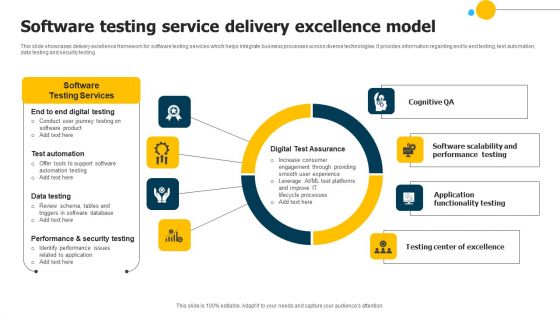
Software Testing Service Delivery Excellence Model Mockup PDF
This slide showcases delivery excellence framework for software testing services which helps integrate business processes across diverse technologies. It provides information regarding end to end testing, test automation, data testing and security testing. Showcasing this set of slides titled Software Testing Service Delivery Excellence Model Mockup PDF. The topics addressed in these templates are Performance Testing, Digital Test Assurance, Security Testing. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
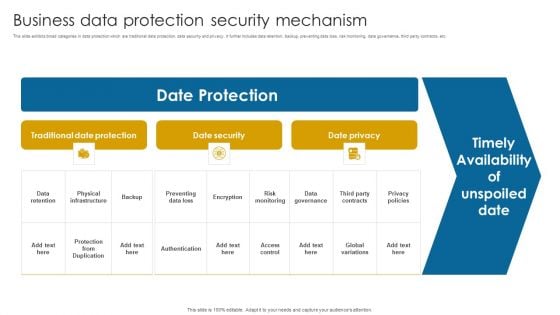
Business Data Protection Security Mechanism Portrait PDF
This slide exhibits broad categories in data protection which are traditional data protection, data security and privacy. It further includes data retention, backup, preventing data loss, risk monitoring, data governance, third party contracts, etc.Showcasing this set of slides titled Business Data Protection Security Mechanism Portrait PDF. The topics addressed in these templates are Data Retention, Physical Infrastructure, Date Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
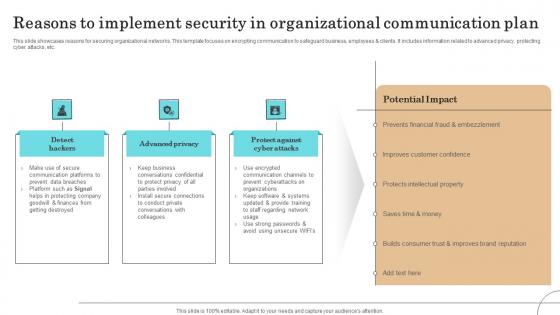
Reasons To Implement Security In Organizational Communication Plan Sample Pdf
This slide showcases reasons for securing organizational networks. This template focuses on encrypting communication to safeguard business, employees clients. It includes information related to advanced privacy, protecting cyber attacks, etc.Showcasing this set of slides titled Reasons To Implement Security In Organizational Communication Plan Sample Pdf The topics addressed in these templates are Communication Platforms, Protecting Company, Improves Customer Confidence All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcases reasons for securing organizational networks. This template focuses on encrypting communication to safeguard business, employees clients. It includes information related to advanced privacy, protecting cyber attacks, etc.
Human Rights Policies Of The Company Icons PDF
This slide shows the human rights policies that are followed by the company for the betterment of community and employees such as stakeholder engagement, diversity and inclusion, safe and healthy workplace, workplace security, work hours, wages and benefits etc. Presenting human rights policies of the company icons pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like community and stakeholder engagement, diversity and inclusion, safe and healthy workplace. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
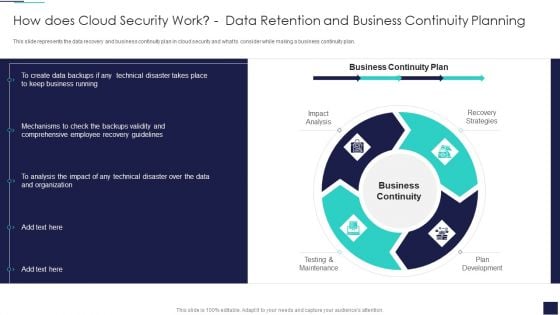
Cloud Information Security How Does Cloud Security Work Data Retention And Business Summary PDF
This slide represents the data recovery and business continuity plan in cloud security and what to consider while making a business continuity plan. This is a Cloud Information Security How Does Cloud Security Work Data Retention And Business Summary PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Business Continuity, Recovery Strategies, Plan Development. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Digital Bookkeeping And Finance Automation Benefits Structure PDF
The following slide highlights benefits of accounting automation limiting invoice traffic jams. It includes benefits such as automate, real time access, visibility, security, productivity, improve decision making, security, compliance, remote access, scalability, cut costs etc. Persuade your audience using this Digital Bookkeeping And Finance Automation Benefits Structure PDF. This PPT design covers ten stages, thus making it a great tool to use. It also caters to a variety of topics including Productivity, Scalability, Cut Costs. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
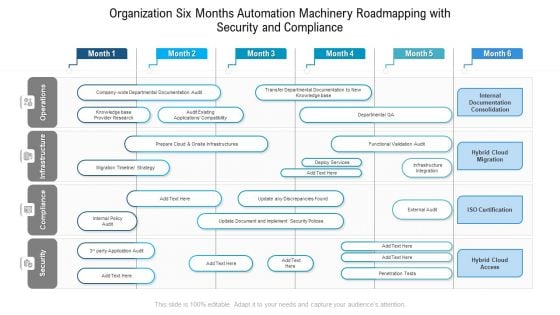
Organization Six Months Automation Machinery Roadmapping With Security And Compliance Summary
Presenting our innovatively structured organization six months automation machinery roadmapping with security and compliance summary Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.
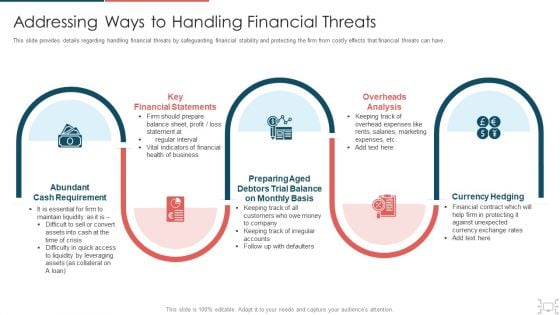
cyber security administration in organization addressing ways to handling financial threats summary pdf
This slide provides details regarding handling financial threats by safeguarding financial stability and protecting the firm from costly effects that financial threats can have. This is a cyber security administration in organization addressing ways to handling financial threats summary pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like financial, statements, requirement, preparing, balance . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
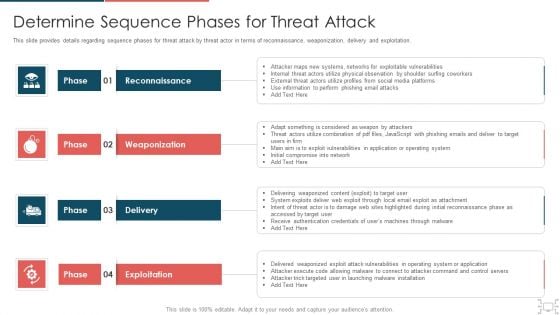
cyber security administration in organization determine sequence phases for threat attack infographics pdf
This slide provides details regarding sequence phases for threat attack by threat actor in terms of reconnaissance, weaponization, delivery and exploitation. This is a cyber security administration in organization determine sequence phases for threat attack infographics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like internal, threat, perform, phishing, combination . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
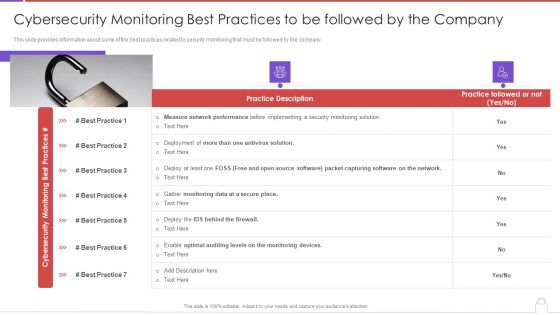
Methods To Develop Cybersecurity Monitoring Best Practices To Be Followed By The Company Demonstration PDF
This slide provides information about some of the best practices related to security monitoring that must be followed by the company. Presenting methods to develop cybersecurity monitoring best practices to be followed by the company demonstration pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like practice description, gather monitoring data. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
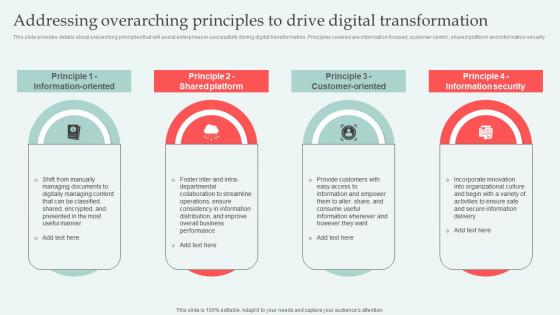
Addressing Overarching Principles Digital Approaches To Increase Business Growth Topics Pdf
This slide provides details about overarching principles that will assist enterprises in successfully driving digital transformation. Principles covered are information focused, customer centric, shared platform and information security. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Addressing Overarching Principles Digital Approaches To Increase Business Growth Topics Pdf from Slidegeeks and deliver a wonderful presentation. This slide provides details about overarching principles that will assist enterprises in successfully driving digital transformation. Principles covered are information focused, customer centric, shared platform and information security.

Top Rising Virtual Security Hazards In 2023 Elements Pdf
This slide illustrates top threats which are emerging in the field of cyber security from the year 2023 onwards. The cyber security risks as covered in this template are crypto jacking, IoT attacks, smart medical devices, connected cars and third party attacks Showcasing this set of slides titled Top Rising Virtual Security Hazards In 2023 Elements Pdf. The topics addressed in these templates are Crypto Jacking, Attacks, Medical Devices. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide illustrates top threats which are emerging in the field of cyber security from the year 2023 onwards. The cyber security risks as covered in this template are crypto jacking, IoT attacks, smart medical devices, connected cars and third party attacks

Internet Security Framework For Data Security Summary Pdf
This slide showcase frame to handle cyber security threats and risk faced by organisation. It include identifying risk, protection, delete , respond and recover.Showcasing this set of slides titled Internet Security Framework For Data Security Summary Pdf The topics addressed in these templates are Policies And Standard, Data Collection, Establish Firewall All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcase frame to handle cyber security threats and risk faced by organisation. It include identifying risk, protection, delete , respond and recover.
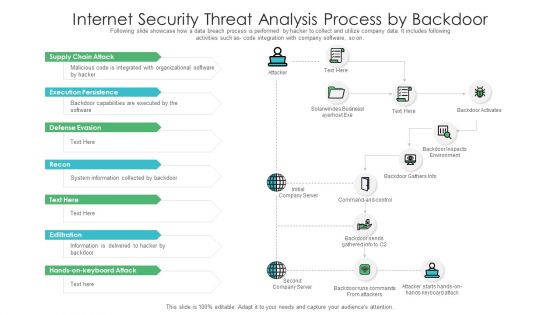
Internet Security Threat Analysis Process By Backdoor Graphics PDF
This slide exhibits data and security breach attack process conducted by hackers to get access to company data. It includes multiple activities such as link forwarding by emails, data sharing and attacking and so on. Showcasing this set of slides titled internet security threat analysis process by backdoor graphics pdf. The topics addressed in these templates are exfiltrate, stage attack, research. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
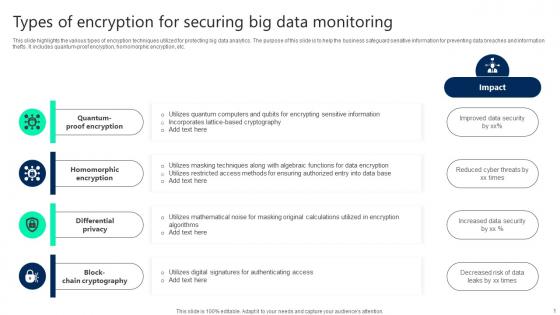
Types Of Encryption For Securing Big Data Monitoring Topics pdf
This slide highlights the various types of encryption techniques utilized for protecting big data analytics. The purpose of this slide is to help the business safeguard sensitive information for preventing data breaches and information thefts. It includes quantum-proof encryption, homomorphic encryption, etc. Showcasing this set of slides titled Types Of Encryption For Securing Big Data Monitoring Topics pdf. The topics addressed in these templates are Quantum Proof Encryption, Homomorphic Encryption, Differential Privacy. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide highlights the various types of encryption techniques utilized for protecting big data analytics. The purpose of this slide is to help the business safeguard sensitive information for preventing data breaches and information thefts. It includes quantum-proof encryption, homomorphic encryption, etc.
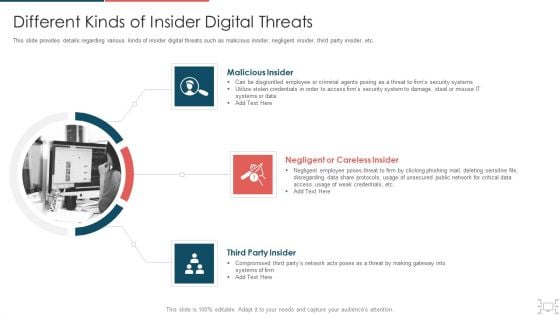
Cyber Security Administration In Organization Different Kinds Of Insider Digital Threats Microsoft PDF
This slide provides details regarding various kinds of insider digital threats such as malicious insider, negligent insider, third party insider, etc. This is a cyber security administration in organization different kinds of insider digital threats microsoft pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like disgruntled, employee, criminal, agents, damage, security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
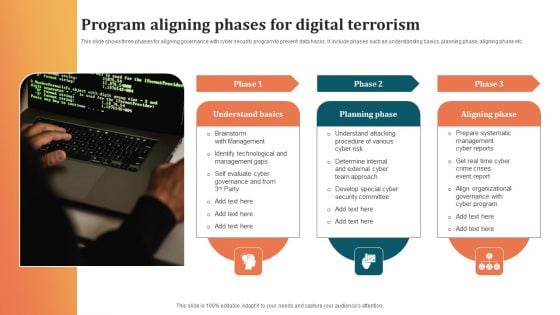
Program Aligning Phases For Digital Terrorism Infographics PDF
This slide shows three phases for aligning governance with cyber security program to prevent data hacks. It include phases such as understanding basics, planning phase, aligning phase etc. Persuade your audience using this Program Aligning Phases For Digital Terrorism Infographics PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Planning Phase, Aligning Phase, Understand Basics. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Satisfying Consumers Through Strategic Product Building Plan Emerging Trends Shaping Information PDF
This slide describes the emerging trends shaping the product development future such as data-driven development, digital product ecosystem, distributed teams, security awareness, etc. Presenting satisfying consumers through strategic product building plan emerging trends shaping information pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like data driven development, digital product ecosystem, distributed teams, security awareness, execution and technical background. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Security Administration In Organization Addressing Several Financial Scenarios And Signs Threat Template PDF
This slide provides information regarding the various financial scenarios that pose a threat to firm profitability and determine signs of financial distress. Presenting cyber security administration in organization addressing several financial scenarios and signs threat template pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like insolvency, scenario, bankruptcy, situation, fluctuations. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
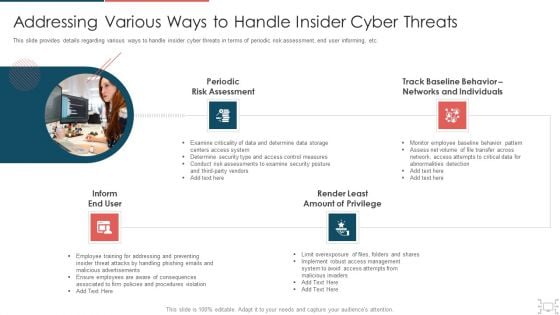
Cyber Security Administration In Organization Addressing Various Ways To Handle Insider Cyber Threats Designs PDF
This slide provides details regarding various ways to handle insider cyber threats in terms of periodic risk assessment, end user informing, etc. This is a cyber security administration in organization addressing various ways to handle insider cyber threats designs pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like assessment, networks, individuals, determine. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
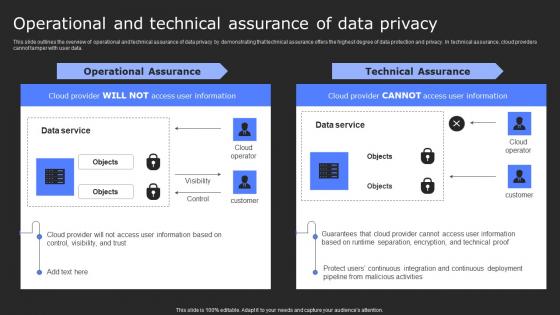
Operational And Technical Assurance Of Data Privacy Secure Computing Framework Mockup Pdf
This slide outlines the overview of operational and technical assurance of data privacy by demonstrating that technical assurance offers the highest degree of data protection and privacy. In technical assurance, cloud providers cannot tamper with user data. Get a simple yet stunning designed Operational And Technical Assurance Of Data Privacy Secure Computing Framework Mockup Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Operational And Technical Assurance Of Data Privacy Secure Computing Framework Mockup Pdf can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide outlines the overview of operational and technical assurance of data privacy by demonstrating that technical assurance offers the highest degree of data protection and privacy. In technical assurance, cloud providers cannot tamper with user data.

Enhanced Protection Corporate Event Administration Role Of Security Operations Centre In Security Operations Brochure PDF
This slide portrays information regarding the role of security operations center in SecOps and how firm behave before, after and towards SecOps implementation. Presenting enhanced protection corporate event administration role of security operations centre in security operations brochure pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like organizational, collaborate, security, analysts. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
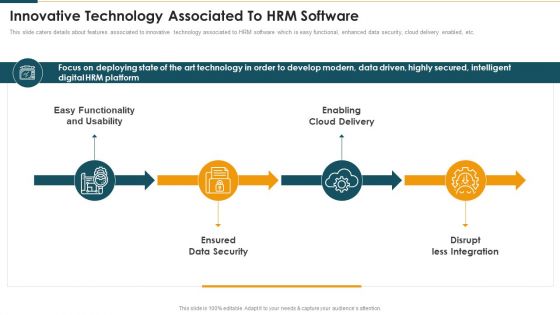
Innovative Technology Associated To Hrm Software Mockup PDF
This slide caters details about features associated to innovative technology associated to HRM software which is easy functional, enhanced data security, cloud delivery enabled, etc. This is a Innovative Technology Associated To Hrm Software Mockup PDF template with various stages. Focus and dispense information on fourstages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Functionality And Usability, Enabling Cloud Delivery, Ensured Data Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Security Icon In Powerpoint And Google Slides Cpb
Introducing our well designed Security Icon In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Security Icon. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Security Icon In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Email Security Industry Report In Powerpoint And Google Slides Cpb
Introducing our well-designed Email Security Industry Report In Powerpoint And Google Slides Cpb This PowerPoint design presents information on topics like Email Security Industry Report As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high-quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Email Security Industry Report In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Secure Streaming Essentials In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Secure Streaming Essentials In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Secure Streaming Essentials that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Secure Streaming Essentials In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Protection Technology Security In Powerpoint And Google Slides Cpb
Introducing our well-designed Protection Technology Security In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Protection Technology Security. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high-quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Protection Technology Security In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Cryptographic Algorithms Used In Cloud Data Security Using Cryptography Themes Pdf
This slide talks about algorithms used for implementing cryptography in data security. The purpose of this slide is to explain the different implementation steps. The techniques discussed are RSA Rivest, Shamir, Adleman cryptographic algorithm and Data Encryption Standard algorithm. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Cryptographic Algorithms Used In Cloud Data Security Using Cryptography Themes Pdf from Slidegeeks and deliver a wonderful presentation. This slide talks about algorithms used for implementing cryptography in data security. The purpose of this slide is to explain the different implementation steps. The techniques discussed are RSA Rivest, Shamir, Adleman cryptographic algorithm and Data Encryption Standard algorithm.
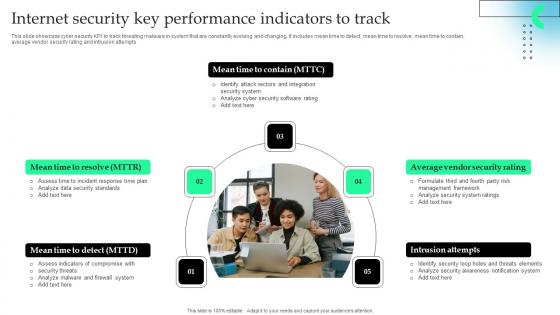
Internet Security Key Performance Indicators To Track Microsoft Pdf
This slide showcase cyber security KPI to track threating malware in system that are constantly evolving and changing. It includes mean time to detect, mean time to resolve, mean time to contain, average vendor security rating and intrusion attempts.Showcasing this set of slides titled Internet Security Key Performance Indicators To Track Microsoft Pdf The topics addressed in these templates are Firewall System, Security Standards, Identify Attack All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcase cyber security KPI to track threating malware in system that are constantly evolving and changing. It includes mean time to detect, mean time to resolve, mean time to contain, average vendor security rating and intrusion attempts.

Way To Overcome Security Monitoring Challenges Setting Up An Advanced Cybersecurity Monitoring Plan Professional PDF
Presenting way to overcome security monitoring challenges setting up an advanced cybersecurity monitoring plan professional pdf to provide visual cues and insights. Share and navigate important information on nine stages that need your due attention. This template can be used to pitch topics like monitoring all systems, monitoring network traffic, monitoring user activity. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Security Playbook Example In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Security Playbook Example In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Security Playbook Example that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Security Playbook Example In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Cyber Deals Security In Powerpoint And Google Slides Cpb
Introducing our well-designed Cyber Deals Security In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Cyber Deals Security. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high-quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Cyber Deals Security In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Secure Shell Protocol In Powerpoint And Google Slides Cpb
Introducing our well designed Secure Shell Protocol In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Secure Shell Protocol. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Secure Shell Protocol In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Network Security Dark Overlord In Powerpoint And Google Slides Cpb
Presenting our innovatively-designed set of slides titled Network Security Dark Overlord In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Network Security Dark Overlord that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well-structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Network Security Dark Overlord In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Information Security Books In Powerpoint And Google Slides Cpb
Introducing our well-designed Information Security Books In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Information Security Books. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high-quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Information Security Books In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Smartphones Mobile Security In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Smartphones Mobile Security In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Smartphones Mobile Security that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Smartphones Mobile Security In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
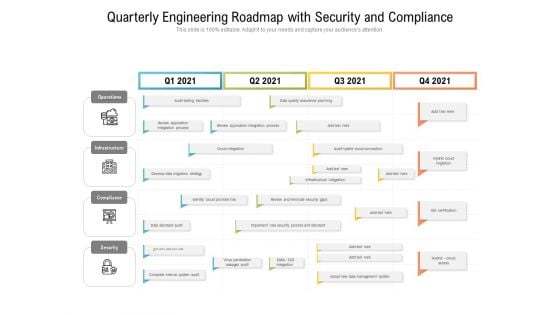
Quarterly Engineering Roadmap With Security And Compliance Template
Presenting our innovatively structured quarterly engineering roadmap with security and compliance template Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.


 Continue with Email
Continue with Email

 Home
Home


































