Safety Management
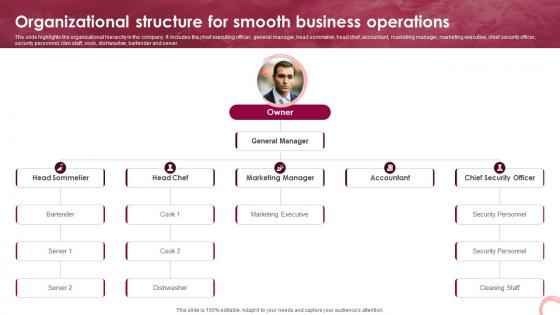
Wine Lounge Business Plan Organizational Structure For Smooth Business Operations BP SS V
The slide highlights the organizational hierarchy in the company. It includes the chief executing officer, general manager, head sommelier, head chef, accountant, marketing manager, marketing executive, chief security officer, security personnel, clen staff, cook, dishwasher, bartender and server. Are you searching for a Wine Lounge Business Plan Organizational Structure For Smooth Business Operations BP SS V that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Wine Lounge Business Plan Organizational Structure For Smooth Business Operations BP SS V from Slidegeeks today. The slide highlights the organizational hierarchy in the company. It includes the chief executing officer, general manager, head sommelier, head chef, accountant, marketing manager, marketing executive, chief security officer, security personnel, clen staff, cook, dishwasher, bartender and server.
Security Officer Wearing Uniform With Badge Image Ppt PowerPoint Presentation Inspiration Microsoft PDF
Presenting this set of slides with name security officer wearing uniform with badge image ppt powerpoint presentation inspiration microsoft pdf. This is a three stage process. The stages in this process are security officer wearing uniform with badge image. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Security Controls To Reduce The Risk Improving Cybersecurity With Incident Pictures PDF
Mentioned slide depicts the incident workflow diagram of a ransomware event along with security controls implemented to mitigate it. The diagram starts with the threat actors entry and ends with the threat actor demanding ransom.Are you searching for a Security Controls To Reduce The Risk Improving Cybersecurity With Incident Pictures PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you ve put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Security Controls To Reduce The Risk Improving Cybersecurity With Incident Pictures PDF from Slidegeeks today.
Confidential Computing Performance Tracking Secure Computing Framework Microsoft Pdf
This slide represents the performance tracking dashboard for confidential computing. The purpose of this slide is to represent the overall performance of the confidential computing cloud environment visually. The main components include overall health, operations, progress, time, cost and workloads. This Confidential Computing Performance Tracking Secure Computing Framework Microsoft Pdf is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Confidential Computing Performance Tracking Secure Computing Framework Microsoft Pdf features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide represents the performance tracking dashboard for confidential computing. The purpose of this slide is to represent the overall performance of the confidential computing cloud environment visually. The main components include overall health, operations, progress, time, cost and workloads.
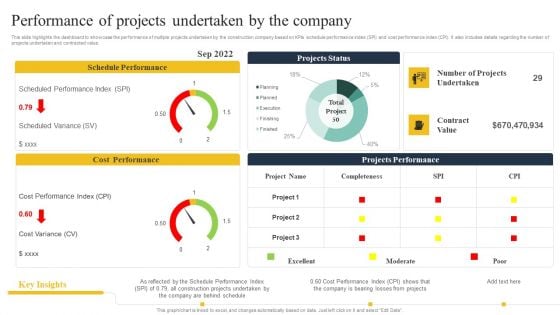
Security Control Techniques For Real Estate Project Performance Of Projects Undertaken By The Company Brochure PDF
Do you have to make sure that everyone on your team knows about any specific topic. I yes, then you should give Security Control Techniques For Real Estate Project Performance Of Projects Undertaken By The Company Brochure PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Security Control Techniques For Real Estate Project Performance Of Projects Undertaken By The Company Brochure PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
Stock Photo Business Strategy Wrench For Loosening Nuts Clipart
Control the fall of the dice with our stock photo business strategy wrench for loosening nuts clipart. Your forecasts will come out correct. Our construction can control fate. The dice will fall as per your call.
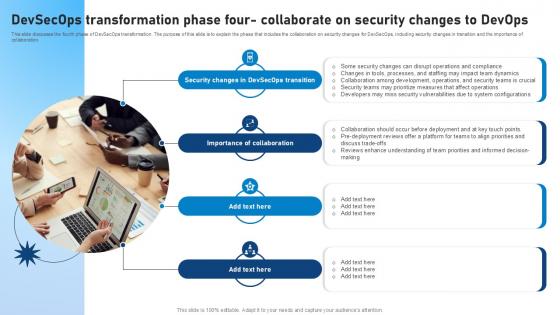
Devsecops Transformation Phase Four Collaborate On Security Role Of Devsecops Ppt Slide
This slide discusses the fourth phase of DevSecOps transformation. The purpose of this slide is to explain the phase that includes the collaboration on security changes for DevSecOps, including security changes in transition and the importance of collaboration. This Devsecops Transformation Phase Four Collaborate On Security Role Of Devsecops Ppt Slide is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Devsecops Transformation Phase Four Collaborate On Security Role Of Devsecops Ppt Slide features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide discusses the fourth phase of DevSecOps transformation. The purpose of this slide is to explain the phase that includes the collaboration on security changes for DevSecOps, including security changes in transition and the importance of collaboration.
Verizon Security Report In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Verizon Security Report In Powerpoint And Google Slides Cpb This completely editable PowerPoint graphic exhibits Verizon Security Report that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Verizon Security Report In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Security Playbook Example In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Security Playbook Example In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Security Playbook Example that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Security Playbook Example In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Cyber Deals Security In Powerpoint And Google Slides Cpb
Introducing our well-designed Cyber Deals Security In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Cyber Deals Security. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high-quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Cyber Deals Security In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Secure Shell Protocol In Powerpoint And Google Slides Cpb
Introducing our well designed Secure Shell Protocol In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Secure Shell Protocol. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Secure Shell Protocol In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Network Security Dark Overlord In Powerpoint And Google Slides Cpb
Presenting our innovatively-designed set of slides titled Network Security Dark Overlord In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Network Security Dark Overlord that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well-structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Network Security Dark Overlord In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Information Security Books In Powerpoint And Google Slides Cpb
Introducing our well-designed Information Security Books In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Information Security Books. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high-quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Information Security Books In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Cyber Security Paper Presentation In Powerpoint And Google Slides Cpb
Presenting our innovatively-designed set of slides titled Cyber Security Paper Presentation In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Cyber Security Paper Presentation that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well-structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Cyber Security Paper Presentation In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Smartphones Mobile Security In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Smartphones Mobile Security In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Smartphones Mobile Security that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Smartphones Mobile Security In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
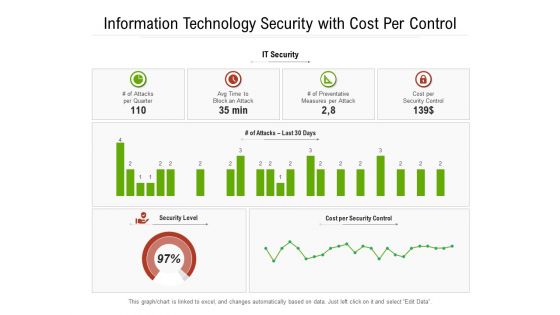
Information Technology Security With Cost Per Control Ppt PowerPoint Presentation Gallery Maker PDF
Presenting this set of slides with name information technology security with cost per control ppt powerpoint presentation gallery maker pdf. The topics discussed in these slides are cost, quarter, measures. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Security Control Techniques For Real Estate Project Organizational Chart For Construction Site Designs PDF
There are so many reasons you need a Security Control Techniques For Real Estate Project Organizational Chart For Construction Site Designs PDF. The first reason is you canot spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
Icon Slide For Security Control Techniques For Real Estate Project Clipart PDF
Presenting our innovatively structured Icon Slide For Security Control Techniques For Real Estate Project Clipart PDF set of slides. The slides contain a hundred percent editable icons. You can replace these icons without any inconvenience. Therefore, pick this set of slides and create a striking presentation.
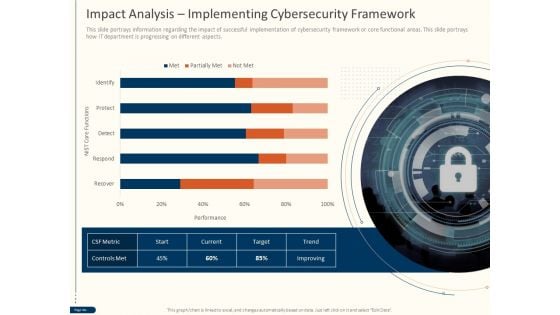
Cyber Security For Your Organization Impact Analysis Implementing Cybersecurity Framework Ppt Model Background PDF
Presenting this set of slides with name cyber security for your organization impact analysis implementing cybersecurity framework ppt model background pdf. This is a one stage process. The stages in this process are csf metric, controls met, trend, target, current, state, performance . This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
In Business PowerPoint Templates Download Process Circular Flow Diagram Slides
We present our in business powerpoint templates download process Circular Flow Diagram Slides.Present our Arrows PowerPoint Templates because this template contains the material to highlight the key issues of your presentation. Download and present our Business PowerPoint Templates because you have secured a name for yourself in the domestic market. Now the time is right to spread your reach to other countries. Download and present our Signs PowerPoint Templates because You can Connect the dots. Fan expectations as the whole picture emerges. Use our Shapes PowerPoint Templates because Your ideas provide food for thought. Our PowerPoint Templates and Slides will help you create a dish to tickle the most discerning palate. Download our Spheres PowerPoint Templates because this diagram has the unique ability to drive home your ideas and show how they mesh to guarantee success.Use these PowerPoint slides for presentations relating to Arrows, Business, Chart, Circular, Commerce, Concept, Contribution, Cycle, Development, Diagram, Global, Idea, Informative, Internet, Join, Making, Manage, Management, Market, Marketing, Partner, Paying, Performance, Plans, Process, Productive, Productivity, Profit, Profitable, Project. The prominent colors used in the PowerPoint template are Green, Black, Gray. Professionals tell us our in business powerpoint templates download process Circular Flow Diagram Slides are designed by professionals You can be sure our Chart PowerPoint templates and PPT Slides are Adorable. Customers tell us our in business powerpoint templates download process Circular Flow Diagram Slides are Classic. Professionals tell us our Contribution PowerPoint templates and PPT Slides are Dazzling. People tell us our in business powerpoint templates download process Circular Flow Diagram Slides are Excellent. People tell us our Cycle PowerPoint templates and PPT Slides are Appealing. Economise on the time you have. Equip yourself with our In Business PowerPoint Templates Download Process Circular Flow Diagram Slides.
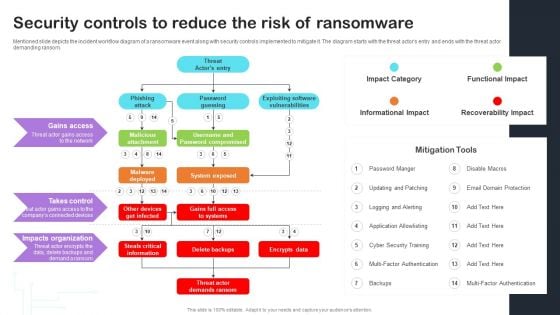
Cyber Risks And Incident Response Playbook Security Controls To Reduce The Risk Of Ransomware Themes PDF
Mentioned slide depicts the incident workflow diagram of a ransomware event along with security controls implemented to mitigate it. The diagram starts with the threat actors entry and ends with the threat actor demanding ransom. Take your projects to the next level with our ultimate collection of Cyber Risks And Incident Response Playbook Security Controls To Reduce The Risk Of Ransomware Themes PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors theyll make your projects stand out from the rest.
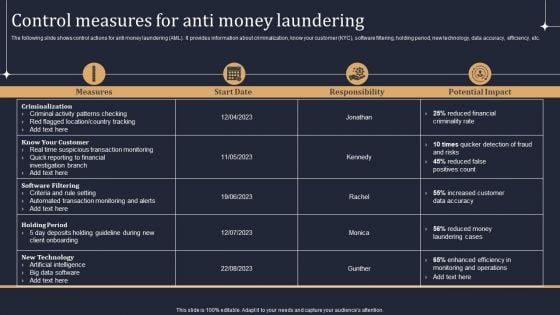
KYC Transaction Monitoring System Business Security Control Measures For Anti Money Laundering Ideas PDF
The following slide shows control actions for anti money laundering AML. It provides information about criminalization, know your customer KYC, software filtering, holding period, new technology, data accuracy, efficiency, etc. The following slide shows control actions for anti money laundering AML. It provides information about criminalization, know your customer KYC, software filtering, holding period, new technology, data accuracy, efficiency, etc. This modern and well arranged KYC Transaction Monitoring System Business Security Control Measures For Anti Money Laundering Ideas PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
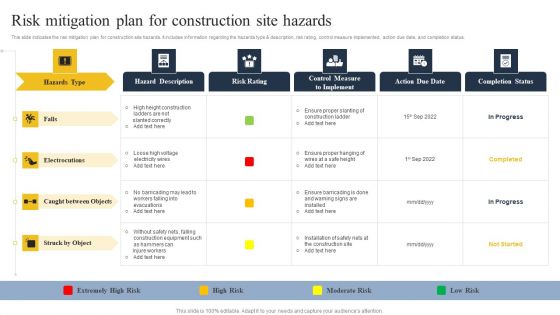
Security Control Techniques For Real Estate Project Risk Mitigation Plan For Construction Site Hazards Microsoft PDF
From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Security Control Techniques For Real Estate Project Risk Mitigation Plan For Construction Site Hazards Microsoft PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Table Of Contents For Security Control Techniques For Real Estate Project Download PDF
If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Table Of Contents For Security Control Techniques For Real Estate Project Download PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates

Security Control Techniques For Real Estate Project Dashboard To Monitor Construction Site Injuries Diagrams PDF
The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Security Control Techniques For Real Estate Project Dashboard To Monitor Construction Site Injuries Diagrams PDF from Slidegeeks and deliver a wonderful presentation.

Global Data Security Industry Report Pestle Analysis Of Global Cybersecurity Industry IR SS V
The slide depicts PESTLE analysis which companies can use to evaluate the external factors that impact the industrys growth and profitability. It enables companies to make informed decisions and strategic planning in a dynamic business environment. Key components include political, legal, economic, social, technological and environmental aspects. This Global Data Security Industry Report Pestle Analysis Of Global Cybersecurity Industry IR SS V is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Global Data Security Industry Report Pestle Analysis Of Global Cybersecurity Industry IR SS V features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today The slide depicts PESTLE analysis which companies can use to evaluate the external factors that impact the industrys growth and profitability. It enables companies to make informed decisions and strategic planning in a dynamic business environment. Key components include political, legal, economic, social, technological and environmental aspects.

Market Trends Reshaping The Defense Global Security Industry PPT Slide IR SS V
The slide determines the attributes on the basis of major trends in the Defense market. The purpose of this slide is to aware about the different areas where Defense is reshaping the market. It capture the information related to upcoming trends offered in the industry. This Market Trends Reshaping The Defense Global Security Industry PPT Slide IR SS V is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Market Trends Reshaping The Defense Global Security Industry PPT Slide IR SS V features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today The slide determines the attributes on the basis of major trends in the Defense market. The purpose of this slide is to aware about the different areas where Defense is reshaping the market. It capture the information related to upcoming trends offered in the industry..

Searching Password Security PowerPoint Backgrounds And Templates 1210
Microsoft PowerPoint Template and Background with the metallic magnifying glass hovering in front of a flat panel computer display monitor with a large brass metallic key on it on a black reflective surface Conduct yourself creditably with our Searching Password Security PowerPoint Backgrounds And Templates 1210. They will let you dominate the dais.
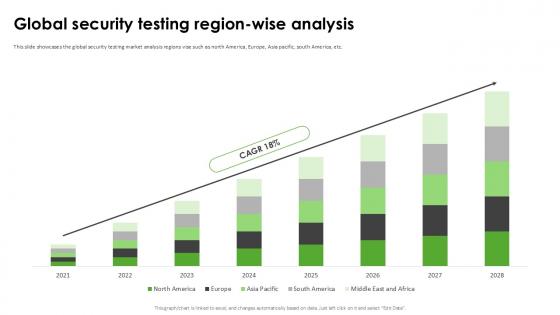
Global Security Testing Region Harnessing The World Of Ethical Ppt Example
This slide showcases the global security testing market analysis regions vise such as north America, Europe, Asia pacific, south America, etc. Find highly impressive Global Security Testing Region Harnessing The World Of Ethical Ppt Example on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Global Security Testing Region Harnessing The World Of Ethical Ppt Example for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide showcases the global security testing market analysis regions vise such as north America, Europe, Asia pacific, south America, etc.
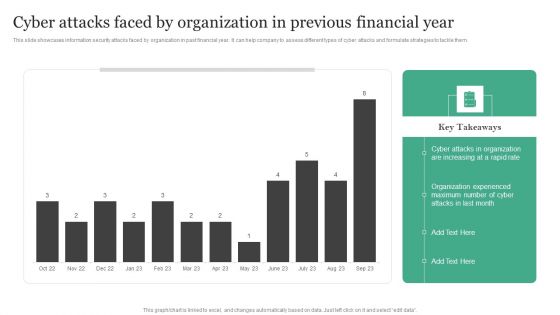
Cyber Attacks Faced By Organization In Previous Financial Year Information Security Risk Administration Topics PDF
This slide showcases information security attacks faced by organization in past financial year. It can help company to assess different types of cyber attacks and formulate strategies to tackle them.Create an editable Cyber Attacks Faced By Organization In Previous Financial Year Information Security Risk Administration Topics PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Cyber Attacks Faced By Organization In Previous Financial Year Information Security Risk Administration Topics PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Security Control Techniques For Real Estate Project Checklist For Construction Site Hazard Identification Introduction PDF
Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Security Control Techniques For Real Estate Project Checklist For Construction Site Hazard Identification Introduction PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
Security Control Techniques For Real Estate Project Hazard Impact Analysis For Construction Site Icons PDF
The Security Control Techniques For Real Estate Project Hazard Impact Analysis For Construction Site Icons PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Table Of Contents Of Security Control Techniques For Real Estate Project Portrait PDF
Slidegeeks has constructed Table Of Contents Of Security Control Techniques For Real Estate Project Portrait PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

Top Rated Outdoor Security Lights In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Top Rated Outdoor Security Lights In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Top Rated Outdoor Security Lights that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Top Rated Outdoor Security Lights In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Table Of Contents For Secure Multi Party Computation SMPC Elements Pdf
Find highly impressive Table Of Contents For Secure Multi Party Computation SMPC Elements Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Table Of Contents For Secure Multi Party Computation SMPC Elements Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now. Our Table Of Contents For Secure Multi Party Computation SMPC Elements Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
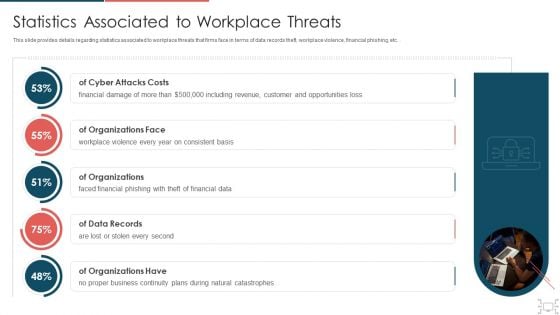
Cyber Security Administration In Organization Statistics Associated To Workplace Threats Microsoft PDF
This slide provides details regarding statistics associated to workplace threats that firms face in terms of data records theft, workplace violence, financial phishing, etc.. Deliver an awe inspiring pitch with this creative cyber security administration in organization statistics associated to workplace threats microsoft pdf bundle. Topics like organizations, consistent, financial, business, catastrophes can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
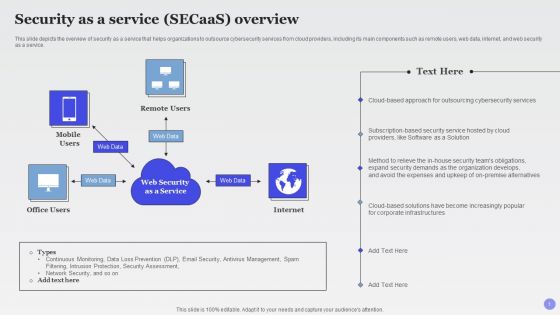
Security As A Service Secaas Overview Xaas Cloud Computing Models Ppt PowerPoint Presentation Outline Slide Download PDF
This slide depicts the overview of security as a service that helps organizations to outsource cybersecurity services from cloud providers, including its main components such as remote users, web data, internet, and web security as a service.Deliver and pitch your topic in the best possible manner with this Security As A Service Secaas Overview Xaas Cloud Computing Models Ppt PowerPoint Presentation Outline Slide Download PDF. Use them to share invaluable insights on Outsourcing Cybersecurity, Software Solution, Expenses Upkeep and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
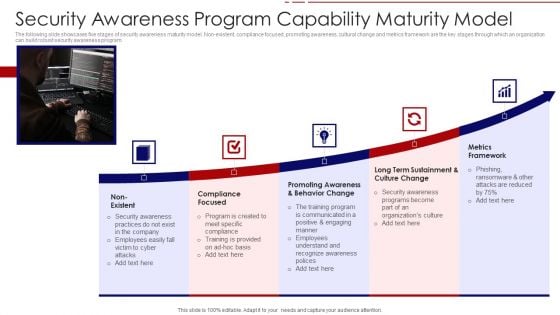
Security Awareness Program Capability Maturity Model Ppt PowerPoint Presentation File Portfolio PDF
The following slide showcases five stages of security awareness maturity model. Non-existent, compliance focused, promoting awareness, cultural change and metrics framework are the key stages through which an organization can build robust security awareness program. Persuade your audience using this security awareness program capability maturity model ppt powerpoint presentation file portfolio pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including non existent, compliance focused, promoting awareness and behavior change, long term sustainment and culture change, metrics framework. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Global Market Analysis Of Secure Web Gateway Web Threat Protection System
This slide depicts the industry analysis and forecast for Secure Web Gateway. The purpose of this slide is to illustrate the market of SWG security technology. The components covered are market size, regional analysis and component segment overview. If you are looking for a format to display your unique thoughts, then the professionally designed Global Market Analysis Of Secure Web Gateway Web Threat Protection System is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Global Market Analysis Of Secure Web Gateway Web Threat Protection System and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide depicts the industry analysis and forecast for Secure Web Gateway. The purpose of this slide is to illustrate the market of SWG security technology. The components covered are market size, regional analysis and component segment overview.
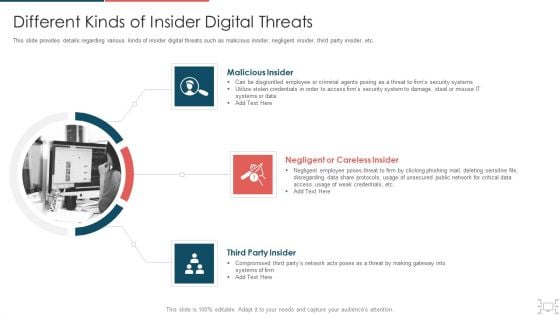
Cyber Security Administration In Organization Different Kinds Of Insider Digital Threats Microsoft PDF
This slide provides details regarding various kinds of insider digital threats such as malicious insider, negligent insider, third party insider, etc. This is a cyber security administration in organization different kinds of insider digital threats microsoft pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like disgruntled, employee, criminal, agents, damage, security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
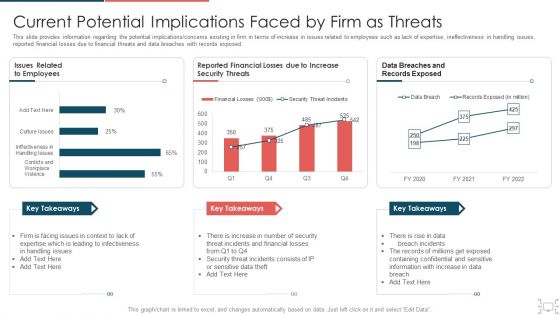
Cyber Security Administration In Organization Current Potential Implications Faced By Firm As Threats Clipart PDF
This slide provides information regarding the potential implications concerns existing in firm in terms of increase in issues related to employees such as lack of expertise, ineffectiveness in handling issues, reported financial losses due to financial threats and data breaches with records exposed. Deliver and pitch your topic in the best possible manner with this cyber security administration in organization current potential implications faced by firm as threats clipart pdf. Use them to share invaluable insights on infectiveness, expertise, issues, security, increase and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Table Of Contents Cyber Security Administration In Organization Assets Background PDF
Presenting table of contents cyber security administration in organization assets background pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like handling, assets, digital, workplace, violence. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
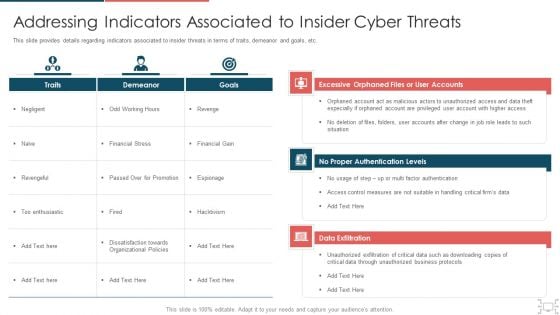
Cyber Security Administration In Organization Addressing Indicators Associated To Insider Cyber Threats Themes PDF
This slide provides details regarding indicators associated to insider threats in terms of traits, demeanor and goals, etc. Deliver and pitch your topic in the best possible manner with this cyber security administration in organization addressing indicators associated to insider cyber threats themes pdf. Use them to share invaluable insights on unauthorized, privileged, measures, authentication and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
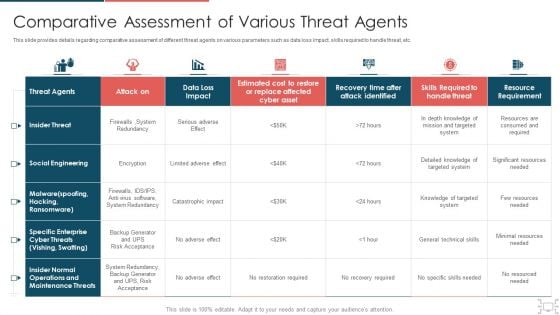
Cyber Security Administration In Organization Comparative Assessment Of Various Threat Agents Infographics PDF
This slide provides details regarding comparative assessment of different threat agents on various parameters such as data loss impact, skills required to handle threat, etc. Deliver and pitch your topic in the best possible manner with this cyber security administration in organization comparative assessment of various threat agents infographics pdf. Use them to share invaluable insights on social engineering, operations, maintenance, redundancy and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Security Administration In Organization Contingency Plan For Cyber Threat Handling Brochure PDF
This slide portrays information contingency plan for handling threats with the help of technical equipment that assist contingency solution and considerations Deliver an awe inspiring pitch with this creative cyber security administration in organization contingency plan for cyber threat handling brochure pdf bundle. Topics like contingency, implementation, components, documentation, technologies can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Cyber Security Administration In Organization Financial Performance Tracking Dashboard Microsoft PDF
This slide presents the dashboard which will help firm in tracking the fiscal performance. This dashboard displays revenues and expenses trends and payment received analysis. Deliver and pitch your topic in the best possible manner with this cyber security administration in organization financial performance tracking dashboard microsoft pdf. Use them to share invaluable insights on financial performance tracking dashboard and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
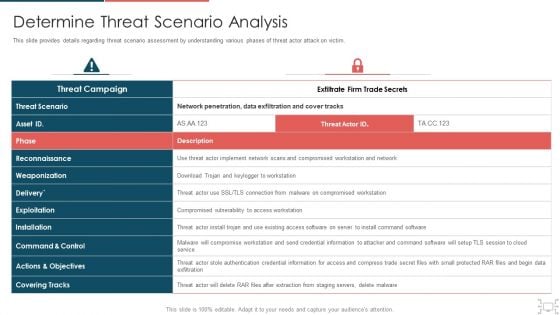
Cyber Security Administration In Organization Determine Threat Scenario Analysis Introduction PDF
This slide provides details regarding threat scenario assessment by understanding various phases of threat actor attack on victim. Deliver an awe inspiring pitch with this creative cyber security administration in organization determine threat scenario analysis introduction pdf bundle. Topics like determine threat scenario analysis can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Security Administration In Organization Incident Reporting By Different Departments Download PDF
This slide will help in providing an overview of the various reported incidents, average cost per incident and number of people involved in the various incidents across different departments. Deliver an awe inspiring pitch with this creative cyber security administration in organization incident reporting by different departments download pdf bundle. Topics like incident reporting by different departments can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
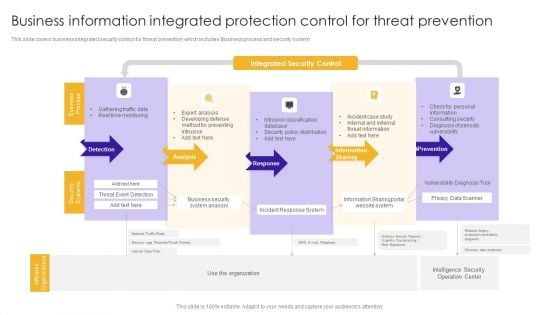
Business Information Integrated Protection Control For Threat Prevention Graphics PDF
This slide covers business integrated security control for threat prevention which includes Business process and security system.Pitch your topic with ease and precision using this Business Information Integrated Protection Control For Threat Prevention Graphics PDF. This layout presents information on Incident Response, Security Policy Distribution, Threat Information. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Security Control Laptop Access Ppt PowerPoint Presentation Complete Deck With Slides
If designing a presentation takes a lot of your time and resources and you are looking for a better alternative, then this security control laptop access ppt powerpoint presentation complete deck with slides is the right fit for you. This is a prefabricated set that can help you deliver a great presentation on the topic. All the eleven slides included in this sample template can be used to present a birds-eye view of the topic. These slides are also fully editable, giving you enough freedom to add specific details to make this layout more suited to your business setting. Apart from the content, all other elements like color, design, theme are also replaceable and editable. This helps in designing a variety of presentations with a single layout. Not only this, you can use this PPT design in formats like PDF, PNG, and JPG once downloaded. Therefore, without any further ado, download and utilize this sample presentation as per your liking.

Organizing Security Awareness Key Stakeholders Of Cyber Security Awareness Training Guidelines PDF
Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Organizing Security Awareness Key Stakeholders Of Cyber Security Awareness Training Guidelines PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Organizing Security Awareness Key Stakeholders Of Cyber Security Awareness Training Guidelines PDF.

Financial Impact Of Information Security Attacks Information Security Risk Administration Slides PDF
This slide showcases financial impact of different cyber security attacks on organizations. Its key elements are business disruption, information loss, revenue loss, equipment damage and total cost by attack type.Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Financial Impact Of Information Security Attacks Information Security Risk Administration Slides PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Financial Impact Of Information Security Attacks Information Security Risk Administration Slides PDF today and make your presentation stand out from the rest.
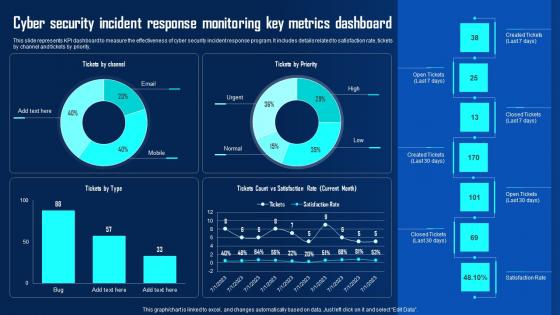
Cyber Security Incident Response Monitoring Key Ppt Powerpoint Presentation File Example File Pdf
This slide represents KPI dashboard to measure the effectiveness of cyber security incident response program. It includes details related to satisfaction rate, tickets by channel and tickets by priority. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Cyber Security Incident Response Monitoring Key Ppt Powerpoint Presentation File Example File Pdf was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Cyber Security Incident Response Monitoring Key Ppt Powerpoint Presentation File Example File Pdf This slide represents KPI dashboard to measure the effectiveness of cyber security incident response program. It includes details related to satisfaction rate, tickets by channel and tickets by priority.
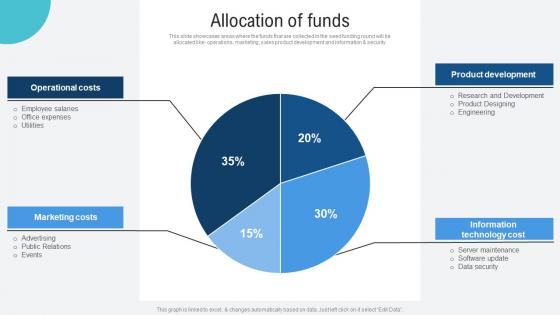
Allocation Of Funds Voice Assistance Security Platform Investor Funding Presentation Professional Pdf
This slide showcases areas where the funds that are collected in the seed funding round will be allocated like operations, marketing, sales product development and information and security. If you are looking for a format to display your unique thoughts, then the professionally designed Allocation Of Funds Voice Assistance Security Platform Investor Funding Presentation Professional Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Allocation Of Funds Voice Assistance Security Platform Investor Funding Presentation Professional Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide showcases areas where the funds that are collected in the seed funding round will be allocated like operations, marketing, sales product development and information and security.

Overview Need For Implementing Data Security Across Optimizing Retail Operations With Digital DT SS V
This slide analyses the need of implementing data security initiatives to address key customer data challenges in retail industry. It also mentions types of customer data collected such as account, location, browsing, and profile.Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Overview Need For Implementing Data Security Across Optimizing Retail Operations With Digital DT SS V was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Overview Need For Implementing Data Security Across Optimizing Retail Operations With Digital DT SS V. This slide analyses the need of implementing data security initiatives to address key customer data challenges in retail industry. It also mentions types of customer data collected such as account, location, browsing, and profile.
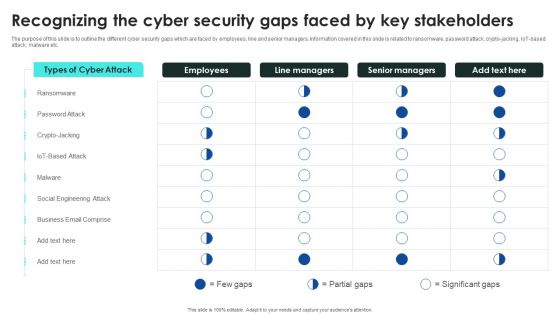
Implementing Cybersecurity Awareness Program To Prevent Attacks Recognizing The Cyber Security Gaps Faced By Key Elements PDF
The purpose of this slide is to outline the different cyber security gaps which are faced by employees, line and senior managers. Information covered in this slide is related to ransomware, password attack, crypto-jacking, IoT-based attack, malware etc. Find a pre designed and impeccable Implementing Cybersecurity Awareness Program To Prevent Attacks Recognizing The Cyber Security Gaps Faced By Key Elements PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
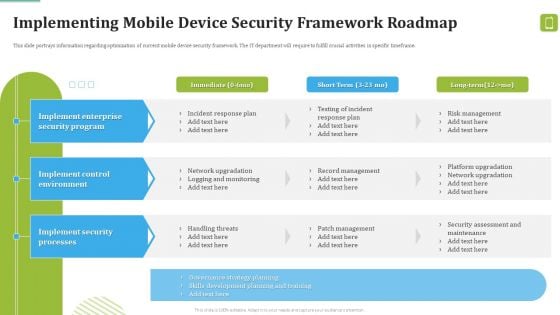
MDM Strategies At Office Implementing Mobile Device Security Framework Roadmap Rules PDF
This slide portrays information regarding optimization of current mobile device security framework. The IT department will require to fulfill crucial activities in specific timeframe. Deliver an awe inspiring pitch with this creative MDM Strategies At Office Implementing Mobile Device Security Framework Roadmap Rules PDF bundle. Topics like Implement Enterprise, Security Program, Implement Control can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
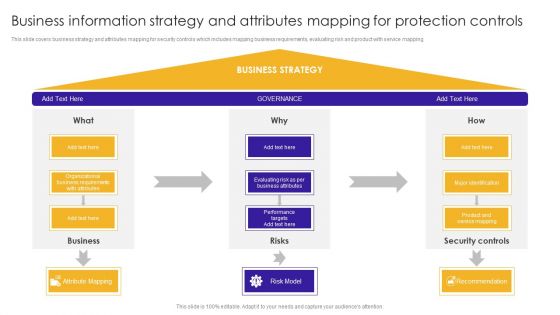
Business Information Strategy And Attributes Mapping For Protection Controls Portrait PDF
This slide covers business strategy and attributes mapping for security controls which includes mapping business requirements, evaluating risk and product with service mapping. Showcasing this set of slides titled Business Information Strategy And Attributes Mapping For Protection Controls Portrait PDF. The topics addressed in these templates are Major Identification, Service Mapping, Recommendation. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cyber Security Administration In Organization Addressing Several Financial Scenarios And Signs Threat Template PDF
This slide provides information regarding the various financial scenarios that pose a threat to firm profitability and determine signs of financial distress. Presenting cyber security administration in organization addressing several financial scenarios and signs threat template pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like insolvency, scenario, bankruptcy, situation, fluctuations. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
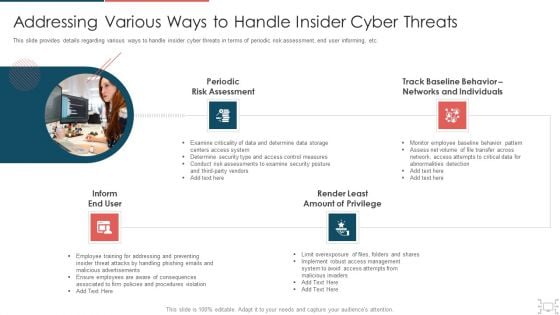
Cyber Security Administration In Organization Addressing Various Ways To Handle Insider Cyber Threats Designs PDF
This slide provides details regarding various ways to handle insider cyber threats in terms of periodic risk assessment, end user informing, etc. This is a cyber security administration in organization addressing various ways to handle insider cyber threats designs pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like assessment, networks, individuals, determine. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.


 Continue with Email
Continue with Email

 Home
Home


































