Safety Performance

Software Development Life Cycle Planning Software Testing Methodologies Background PDF
This slide covers software testing methodologies such as functional testings including unit, integration, system, acceptance testing, and non functional testing including performance, security, usability and compatibility testing. This Software Development Life Cycle Planning Software Testing Methodologies Background PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
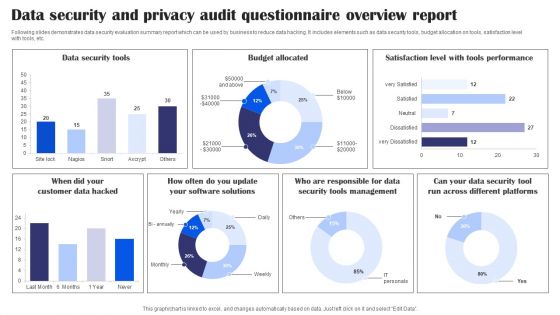
Data Security And Privacy Audit Questionnaire Overview Report Survey SS
Following slides demonstrates data security evaluation summary report which can be used by business to reduce data hacking. It includes elements such as data security tools, budget allocation on tools, satisfaction level with tools, etc. Pitch your topic with ease and precision using this Data Security And Privacy Audit Questionnaire Overview Report Survey SS. This layout presents information on Data Security Tools, Budget Allocated, Tools Performance, Data Security Tools Management. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Multi Cloud Infrastructure Management Types Of Services Offered By Consulting Firm Download PDF
This slide covers the broader services offered by consulting firm such as managing data centres, multi-cloud services, manged security services. This Multi Cloud Infrastructure Management Types Of Services Offered By Consulting Firm Download PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

Information Security And Risk Management User Spending By Segment Cybersecurity Risk Assessment Rules PDF
This slide showcases expenses done by organization in different segments of information security and risk management. Key segments include application security, cloud security, data security, identify access management, infrastructure protection, integrated risk management, security services etc. This Information Security And Risk Management User Spending By Segment Cybersecurity Risk Assessment Rules PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
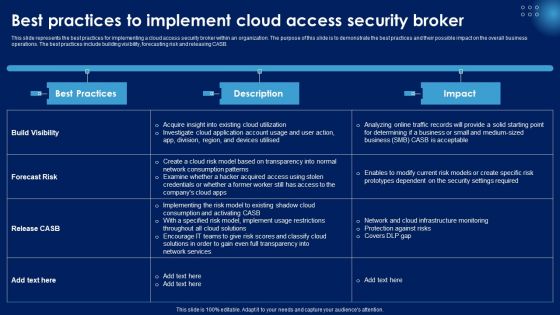
Best Practices To Implement Cloud Access Security Broker Ppt PowerPoint Presentation File Gallery PDF
This slide represents the best practices for implementing a cloud access security broker within an organization. The purpose of this slide is to demonstrate the best practices and their possible impact on the overall business operations. The best practices include building visibility, forecasting risk and releasing CASB. This Best Practices To Implement Cloud Access Security Broker Ppt PowerPoint Presentation File Gallery PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

Security Testing Types Code Review Application Security Testing
This slide outlines the introduction of secure code review in application security for efficient working of an application. This Security Testing Types Code Review Application Security Testing from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide outlines the introduction of secure code review in application security for efficient working of an application.
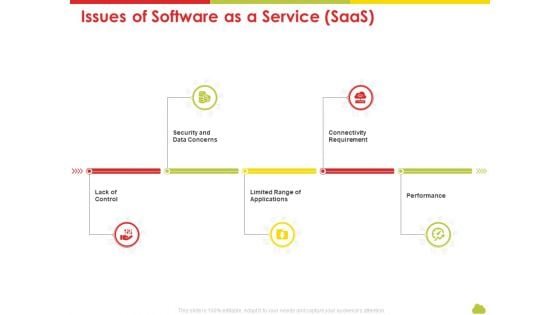
Mesh Computing Technology Hybrid Private Public Iaas Paas Saas Workplan Issues Of Software As A Service Saas Demonstration PDF
This is a mesh computing technology hybrid private public iaas paas saas workplan issues of software as a service saas demonstration pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security and data concerns, lack of control, limited range of applications, connectivity requirement, performance. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
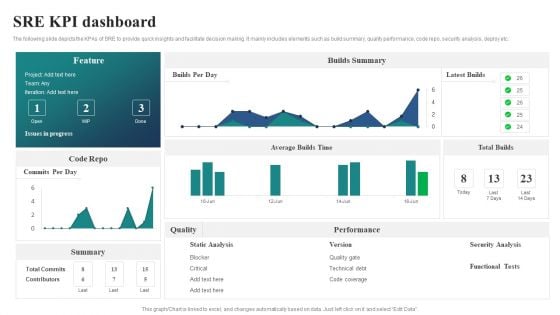
SRE KPI Dashboard Ppt PowerPoint Presentation File Slide Portrait PDF
The following slide depicts the KPAs of SRE to provide quick insights and facilitate decision making. It mainly includes elements such as build summary, quality performance, code repo, security analysis, deploy etc. Showcasing this set of slides titled SRE KPI Dashboard Ppt PowerPoint Presentation File Slide Portrait PDF. The topics addressed in these templates are Builds Summary, Latest Builds, Total Builds. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
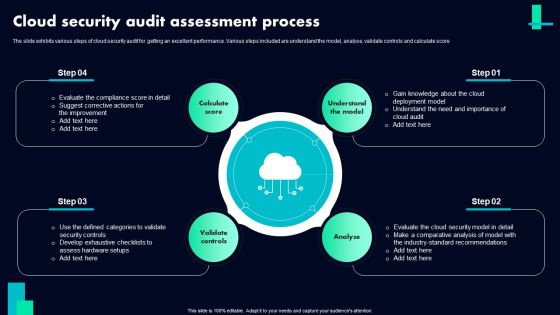
Cloud Security Audit Assessment Process Ppt PowerPoint Presentation Gallery Summary PDF
The slide exhibits various steps of cloud security audit for getting an excellent performance. Various steps included are understand the model, analyse, validate controls and calculate score. Persuade your audience using this Cloud Security Audit Assessment Process Ppt PowerPoint Presentation Gallery Summary PDF. This PPT design covers FOUR stages, thus making it a great tool to use. It also caters to a variety of topics including Calculate Score, Understand The Model, Analyse Validate Controls. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Formulating Money Laundering Key Members Of Financial Security Department Structure PDF
This Formulating Money Laundering Key Members Of Financial Security Department Structure PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

Safeguarding Network With SDN Security Ppt PowerPoint Presentation Complete Deck With Slides
You will save yourself your energy and hours of time when you choose to use this impactful PowerPoint Deck. This Safeguarding Network With SDN Security Ppt PowerPoint Presentation Complete Deck With Slides has been tailor-made to your business needs which ensures that you will always be prepared for that next meeting. Worry can not touch you when you present in your area of expertise using this PPT Template Bundle. With a modern design and easy to follow structure, this PowerPoint Presentation has fifty nine slides, which ensures that you can cover you need to without much work. Create your next presentation using this PPT Theme to deliver a memorable performance.

Issues Addressed By Dcaas Elements PDF
This slide brings forth various issues which are addressed by data service centers to provide users a solution in order to improve current business performance. The various issues addressed are data management, hyper converged infrastructure, data security and file storage. Presenting Issues Addressed By Dcaas Elements PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Data Management, Data Security, Converged Infrastructure. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
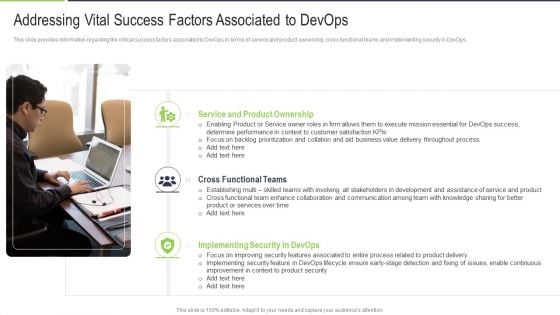
Addressing Vital Success Factors Associated To Devops Summary PDF
This slide provides information regarding the critical success factors associated to DevOps in terms of service and product ownership, cross functional teams and implementing security in DevOps. Presenting addressing vital success factors associated to devops summary pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like teams, product, service, value, performance. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
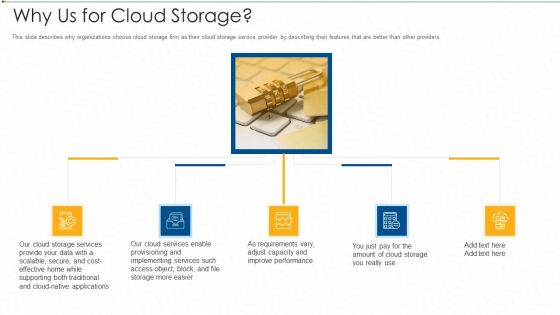
Why Us For Cloud Storage Ppt Infographic Template Graphics Pictures PDF
This slide describes why organizations choose cloud storage firm as their cloud storage service provider by describing their features that are better than other providers.This is a why us for cloud storage ppt infographic template graphics pictures pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like secure, applications, implementing, services, performance. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
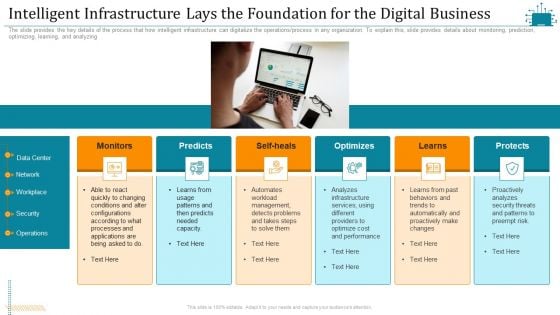
Cloud Intelligence Framework For Application Consumption Intelligent Infrastructure Lays The Foundation For The Digital Business Summary PDF
The slide provides the key details of the process that how intelligent infrastructure can digitalize the operations process in any organization. To explain this, slide provides details about monitoring, prediction, optimizing, learning, and analyzing. Presenting cloud intelligence framework for application consumption intelligent infrastructure lays the foundation for the digital business summary pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like security, operations, proactively analyzes, optimize cost and performance, analyzes infrastructure services. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download
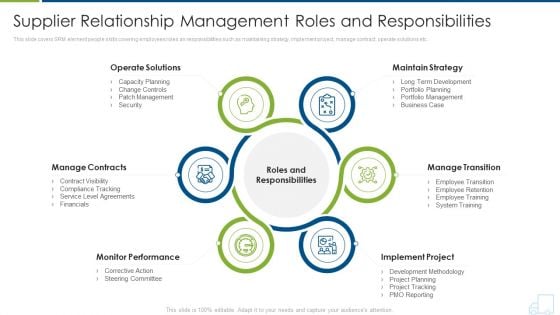
Distributor Strategy Supplier Relationship Management Roles And Responsibilities Structure PDF
This slide covers SRM element people skills covering employees roles an responsibilities such as maintaining strategy, implement project, manage contract, operate solutions etc. Presenting distributor strategy supplier relationship management roles and responsibilities structure pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like management, security, service, financials, performance. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
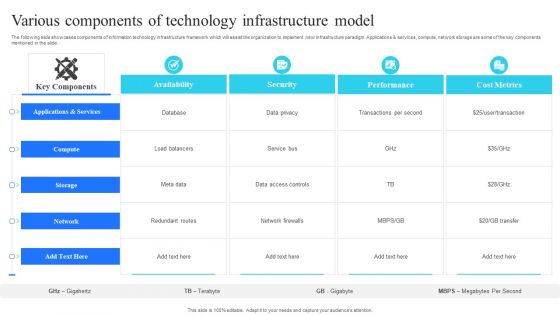
Various Components Of Technology Infrastructure Model Portrait PDF
The following slide showcases components of information technology infrastructure framework which will assist the organization to implement new infrastructure paradigm. Applications and services, compute, network storage are some of the key components mentioned in the slide. Showcasing this set of slides titled Various Components Of Technology Infrastructure Model Portrait PDF. The topics addressed in these templates are Availability, Security, Performance, Cost Metrics. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

CASB 2 0 IT Cloud Security Standards And Control Frameworks
This slide provides an overview of the cloud security protocols and control frameworks. The purpose of this slide is to showcase the various information security standards and control frameworks, including ISO-27001, ISO-27017, ISO-27018, GDPR, SOC reporting, PCI DSS, and HIPAA. This CASB 2 0 IT Cloud Security Standards And Control Frameworks from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide provides an overview of the cloud security protocols and control frameworks. The purpose of this slide is to showcase the various information security standards and control frameworks, including ISO-27001, ISO-27017, ISO-27018, GDPR, SOC reporting, PCI DSS, and HIPAA.
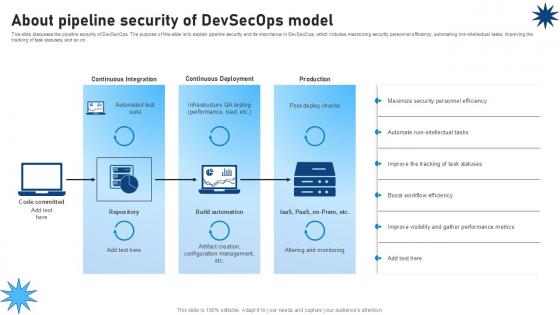
About Pipeline Security Of Devsecops Model Role Of Devsecops Ppt Powerpoint
This slide discusses the pipeline security of DevSecOps. The purpose of this slide is to explain pipeline security and its importance in DevSecOps, which includes maximizing security personnel efficiency, automating non-intellectual tasks, improving the tracking of task statuses, and so on. This About Pipeline Security Of Devsecops Model Role Of Devsecops Ppt Powerpoint from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide discusses the pipeline security of DevSecOps. The purpose of this slide is to explain pipeline security and its importance in DevSecOps, which includes maximizing security personnel efficiency, automating non-intellectual tasks, improving the tracking of task statuses, and so on.

Key Characteristics Of Modern ZTNA Solution Zero Trust Network Security Formats Pdf
This slide outlines the top features that a modern ZTNA model should include. This slide highlights the characteristics of modern ZTNA solutions, including data loss prevention, scalable performance, granular visibility and reporting, BYOD deployment options, advanced threat protection, and SASE offering. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Key Characteristics Of Modern ZTNA Solution Zero Trust Network Security Formats Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide outlines the top features that a modern ZTNA model should include. This slide highlights the characteristics of modern ZTNA solutions, including data loss prevention, scalable performance, granular visibility and reporting, BYOD deployment options, advanced threat protection, and SASE offering.

Help In Information Search Education PowerPoint Templates And PowerPoint Themes 1112
We present our Help In Information Search Education PowerPoint Templates And PowerPoint Themes 1112.Use our Education PowerPoint Templates because, A, B, C, is where it all starts. Use our Future PowerPoint Templates because, Leadership Template:- Show them the way, be Captain of the ship and lead them to new shores. Use our Security PowerPoint Templates because, Churn the mixture to the right degree and pound home your views and expectations in a spectacularly grand and virtuoso fluid performance. Use our Success PowerPoint Templates because,have always been a source of inspiration for us all. Use our Business PowerPoint Templates because,Marketing Strategy Business Template:- Maximising sales of your product is the intended destination.Use these PowerPoint slides for presentations relating to Help in information search, education, future, security, success, business. The prominent colors used in the PowerPoint template are Red, White, Maroon Publicize your views with our Help In Information Search Education PowerPoint Templates And PowerPoint Themes 1112. Download without worries with our money back guaranteee.
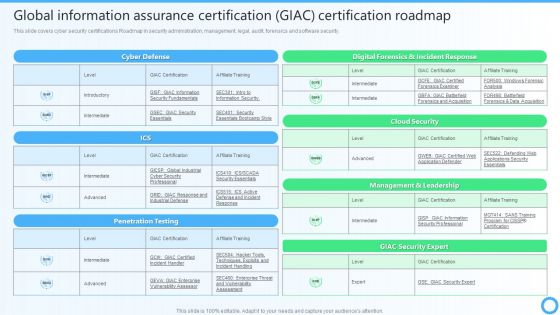
Global Information Assurance Certification GIAC Certification Roadmap IT Certifications To Enhance Template PDF
This slide covers cyber security certifications Roadmap in security administration, management, legal, audit, forensics and software security.This Global Information Assurance Certification GIAC Certification Roadmap IT Certifications To Enhance Template PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

Cloud Assessment Tools And Techniques Ppt PowerPoint Presentation Gallery Picture PDF
The slide highlights various tools of cloud audit to guide and improve the vendors performance. Various tools and techniques included are cloud controls matrix, STAR questionnaire and CSA best practices. Persuade your audience using this Cloud Assessment Tools And Techniques Ppt PowerPoint Presentation Gallery Picture PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Cloud Controls Matrix, Security, Trust, Assurance, Risk Security Questionnaire. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Operational Process Improvement Plan Steps In Detail Monitoring And Optimization Demonstration PDF
This slide provides information about the seventh and the foremost step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e., Monitoring and Optimization. Presenting operational process improvement plan steps in detail monitoring and optimization demonstration pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like process improvement, performance, team. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
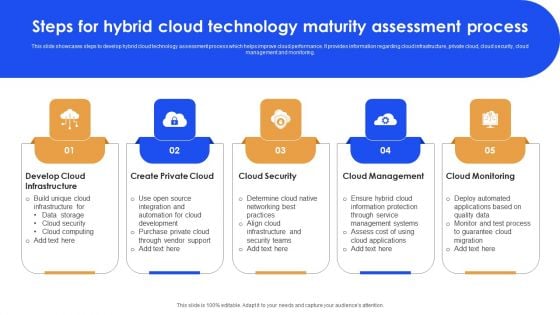
Steps For Hybrid Cloud Technology Maturity Assessment Process Microsoft PDF
This slide showcases steps to develop hybrid cloud technology assessment process which helps improve cloud performance. It provides information regarding cloud infrastructure, private cloud, cloud security, cloud management and monitoring. Persuade your audience using this Steps For Hybrid Cloud Technology Maturity Assessment Process Microsoft PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Develop Cloud Infrastructure, Cloud Security, Cloud Monitoring. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
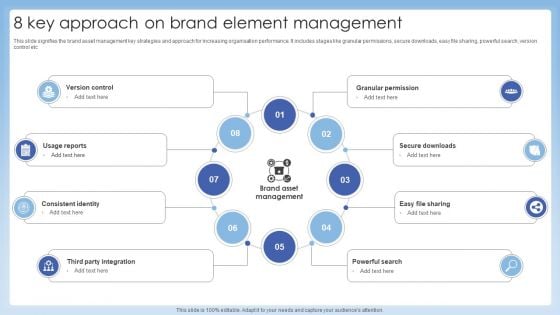
8 Key Approach On Brand Element Management Rules PDF
This slide signifies the brand asset management key strategies and approach for increasing organisation performance. It includes stages like granular permissions, secure downloads, easy file sharing, powerful search, version control etc. Presenting 8 Key Approach On Brand Element Management Rules PDF to dispense important information. This template comprises eight stages. It also presents valuable insights into the topics including Version Control, Granular Permission, Secure Downloads. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
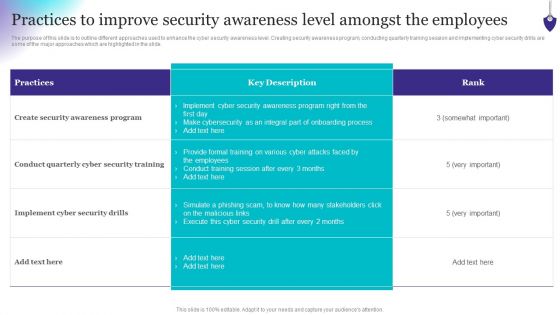
Organizing Security Awareness Practices To Improve Security Awareness Level Amongst Demonstration PDF
The purpose of this slide is to outline different approaches used to enhance the cyber security awareness level. Creating security awareness program, conducting quarterly training session and implementing cyber security drills are some of the major approaches which are highlighted in the slide. This Organizing Security Awareness Practices To Improve Security Awareness Level Amongst Demonstration PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

Challenges And Solutions In Information Security Risk Management Information Security Risk Administration Template PDF
This slide showcases challenges involved in formulating risk management program for information security. It also shows solutions to tackle the challenges and impact of implementing them.This Challenges And Solutions In Information Security Risk Management Information Security Risk Administration Template PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
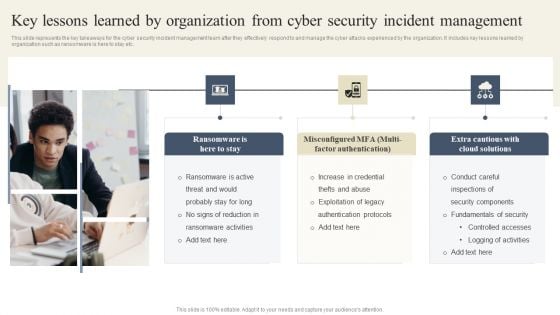
CYBER Security Breache Response Strategy Key Lessons Learned By Organization From Cyber Security Incident Graphics PDF
This slide represents the key takeaways for the cyber security incident management team after they effectively respond to and manage the cyber attacks experienced by the organization. It includes key lessons learned by organization such as ransomware is here to stay etc. This CYBER Security Breache Response Strategy Key Lessons Learned By Organization From Cyber Security Incident Graphics PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
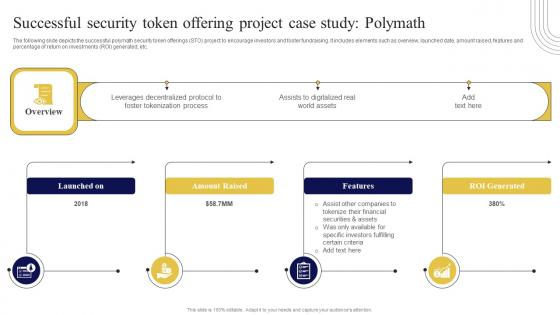
Successful Security Token Offering Project Case Exploring Investment Opportunities Summary Pdf
The following slide depicts the successful polymath security token offerings STO project to encourage investors and foster fundraising. It includes elements such as overview, launched date, amount raised, features and percentage of return on investments ROI generated, etc. This Successful Security Token Offering Project Case Exploring Investment Opportunities Summary Pdf from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. The following slide depicts the successful polymath security token offerings STO project to encourage investors and foster fundraising. It includes elements such as overview, launched date, amount raised, features and percentage of return on investments ROI generated, etc.
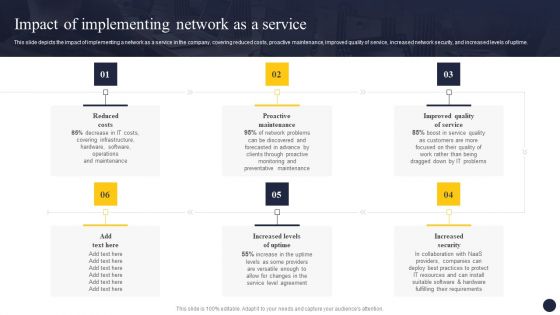
Integrating Naas Service Model To Enhance Impact Of Implementing Network As A Service Portrait PDF
This slide depicts the impact of implementing a network as a service in the company, covering reduced costs, proactive maintenance, improved quality of service, increased network security, and increased levels of uptime. This Integrating Naas Service Model To Enhance Impact Of Implementing Network As A Service Portrait PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
Inclavare Confidential Containers Architecture In Tee Secure Multi Party Icons Pdf
This slide represents the architecture of inclavare confidential containers in the TEE environment. The purpose of this slide is to showcase the various components and features of inclavare containers. The primary components include Kubelet, containerd, shim-rune, rune, PAL API, Pod and so on. This Inclavare Confidential Containers Architecture In Tee Secure Multi Party Icons Pdf from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide represents the architecture of inclavare confidential containers in the TEE environment. The purpose of this slide is to showcase the various components and features of inclavare containers. The primary components include Kubelet, containerd, shim-rune, rune, PAL API, Pod and so on.
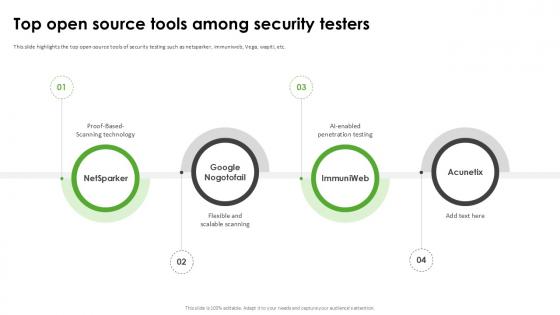
Top Open Source Tools Harnessing The World Of Ethical Ppt Slide
This slide highlights the top open-source tools of security testing such as netsparker, immuniweb, Vega, wapiti, etc. This Top Open Source Tools Harnessing The World Of Ethical Ppt Slide from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide highlights the top open-source tools of security testing such as netsparker, immuniweb, Vega, wapiti, etc.

Key Characteristics Of Modern ZTNA Solution Portrait PDF
This slide outlines the top features that a modern ZTNA model should include. This slide highlights the characteristics of modern ZTNA solutions, including data loss prevention, scalable performance, granular visibility and reporting, BYOD deployment options, advanced threat protection, and SASE offering. Are you searching for a Key Characteristics Of Modern ZTNA Solution Portrait PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Key Characteristics Of Modern ZTNA Solution Portrait PDF from Slidegeeks today.
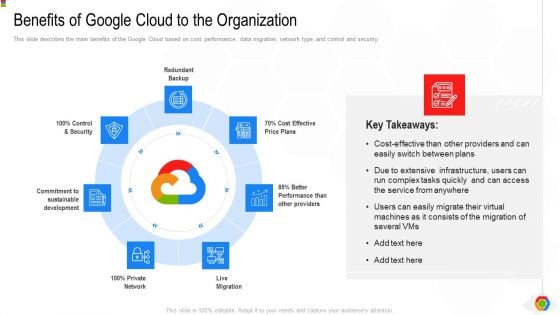
Google Cloud Console IT Benefits Of Google Cloud To The Organization Ppt Styles Templates PDF
This slide describes the main benefits of the Google Cloud based on cost, performance, data migration, network type, and control and security. Presenting google cloud console it benefits of google cloud to the organization ppt styles templates pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like cost effective price plans, live migration, private network. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
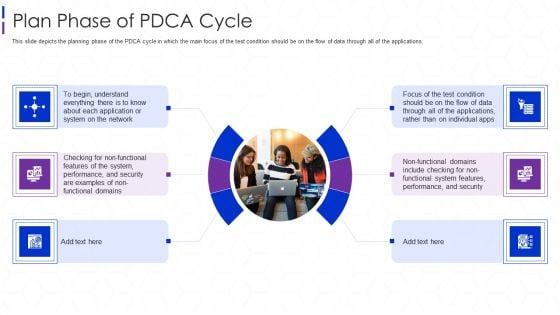
Software Interoperability Examination IT Plan Phase Of PDCA Cycle Clipart PDF
This slide depicts the planning phase of the PDCA cycle in which the main focus of the test condition should be on the flow of data through all of the applications. This is a software interoperability examination it plan phase of pdca cycle clipart pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like network, system, security, performance. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
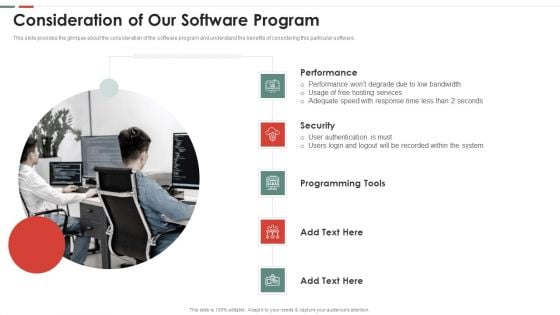
Feasibility Analysis Template Different Projects Consideration Of Our Software Program Infographics PDF
This slide provides the glimpse about the consideration of the software program and understand the benefits of considering this particular software. This is a feasibility analysis template different projects consideration of our software program infographics pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like performance, security, programming tools. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
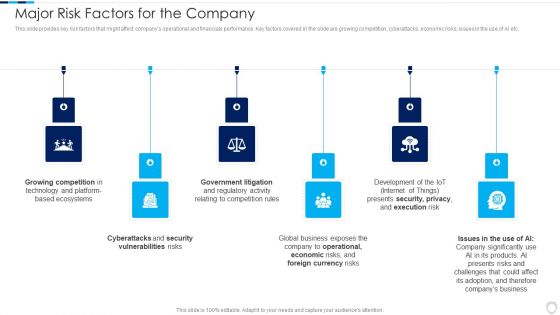
Financial Report Of An IT Firm Major Risk Factors For The Company Demonstration PDF
This slide provides key risk factors that might affect companys operational and financials performance. Key factors covered in the slide are growing competition, cyberattacks, economic risks, issues in the use of AI etc.This is a Financial Report Of An IT Firm Major Risk Factors For The Company Demonstration PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Growing Competition, Government Litigation, Cyberattacks Security You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

VID Managing End User Computing In The Company Infographics PDF
This slide represents how we will manage to end user computing and it includes to adopt centralized application deployment, preparation for changing job roles, know users and so on.Presenting VID Managing End User Computing In The Company Infographics PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Security Implications, Application Performance, Endeavor And Metrics. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
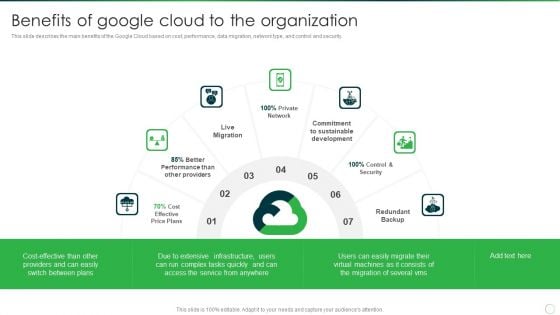
Google Cloud Computing System Benefits Of Google Cloud To The Organization Mockup PDF
This slide describes the main benefits of the Google Cloud based on cost, performance, data migration, network type, and control and security. This is a Google Cloud Computing System Benefits Of Google Cloud To The Organization Mockup PDF template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Live Migration, Private Network, Redundant Backup. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
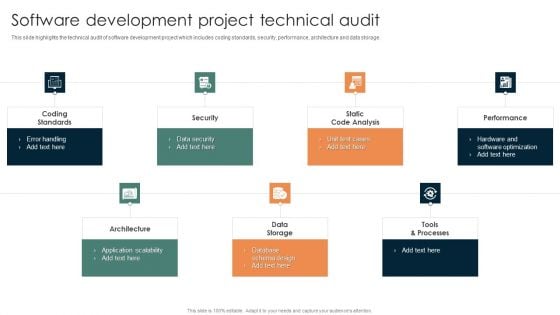
Online Mechanism For Site Software Development Project Technical Audit Introduction PDF
This slide highlights the technical audit of software development project which includes coding standards, security, performance, architecture and data storage. Want to ace your presentation in front of a live audience Our Online Mechanism For Site Software Development Project Technical Audit Introduction PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.
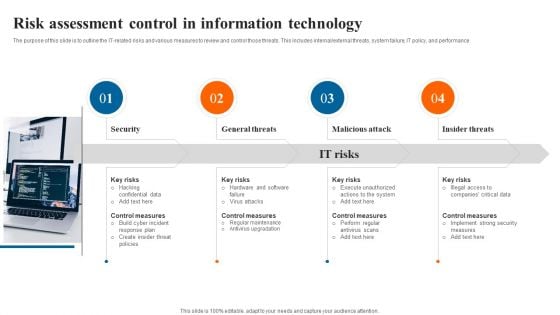
Risk Assessment Control In Information Technology Download PDF
The purpose of this slide is to outline the IT related risks and various measures to review and control those threats. This includes internal or external threats, system failure, IT policy, and performance. Presenting Risk Assessment Control In Information Technology Download PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including General Threats, Malicious Attack, Insider Threats, Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
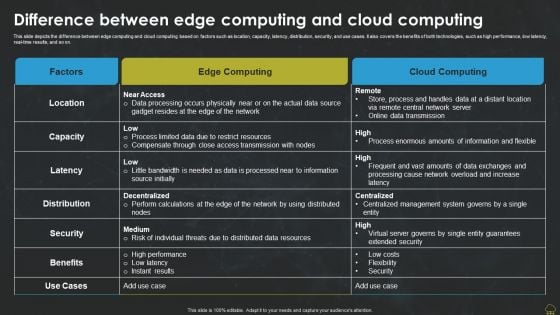
Difference Between Edge Computing And Cloud Computing Professional PDF
This slide depicts the difference between edge computing and cloud computing based on factors such as location, capacity, latency, distribution, security, and use cases. It also covers the benefits of both technologies, such as high performance, low latency, real-time results, and so on. Find a pre designed and impeccable Difference Between Edge Computing And Cloud Computing Professional PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
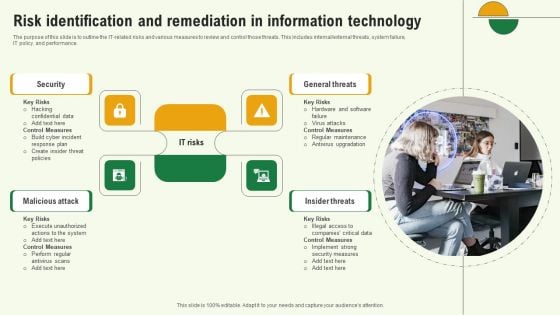
Risk Identification And Remediation In Information Technology Template PDF
The purpose of this slide is to outline the IT related risks and various measures to review and control those threats. This includes internal or external threats, system failure, IT policy, and performance. Persuade your audience using this Risk Identification And Remediation In Information Technology Template PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Insider Threats, General Threats, Security. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
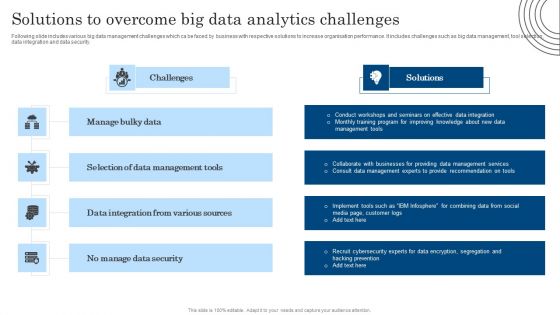
Solutions To Overcome Big Data Analytics Challenges Download PDF
Following slide includes various big data management challenges which ca be faced by business with respective solutions to increase organisation performance. It includes challenges such as big data management, tool selection, data integration and data security. Showcasing this set of slides titled Solutions To Overcome Big Data Analytics Challenges Download PDF. The topics addressed in these templates are Data Management Tools, Data Integration, Various Sources. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
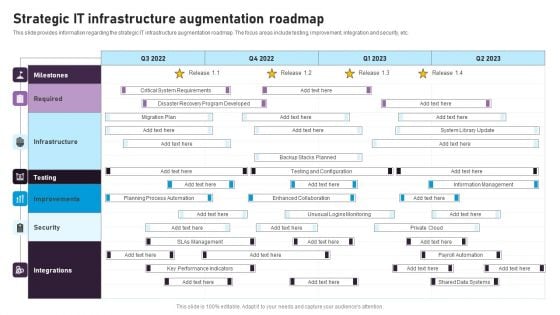
Strategic IT Infrastructure Augmentation Roadmap Microsoft PDF
This slide provides information regarding the strategic IT infrastructure augmentation roadmap. The focus areas include testing, improvement, integration and security, etc. This Strategic IT Infrastructure Augmentation Roadmap Microsoft PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

Challenges And Solutions Of Headless Content Management Strategy With Description Topics PDF
The slide showcases main obstacles that developers need to address when using a headless content management system. It covers aspects like challenges, description and solutions offered by third party platforms. Showcasing this set of slides titled Challenges And Solutions Of Headless Content Management Strategy With Description Topics PDF. The topics addressed in these templates are Performance, Preview, Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
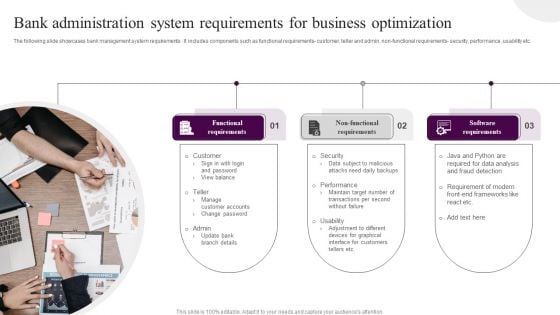
Bank Administration System Requirements For Business Optimization Rules PDF
The following slide showcases bank management system requirements . It includes components such as functional requirements- customer, teller and admin, non-functional requirements- security, performance, usability etc. Presenting Bank Administration System Requirements For Business Optimization Rules PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Functional Requirements, Non Functional Requirements, Software Requirements . This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
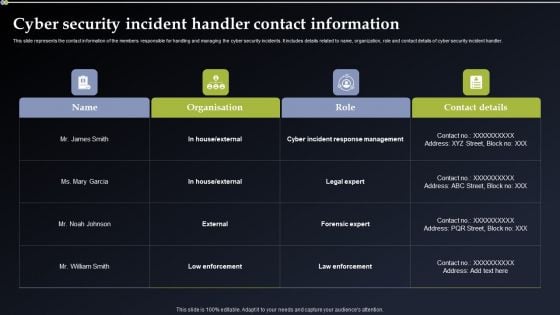
Cyber Security Incident Handler Contact Information Summary PDF
This slide represents the contact information of the members responsible for handling and managing the cyber security incidents. It includes details related to name, organization, role and contact details of cyber security incident handler. This Cyber Security Incident Handler Contact Information Summary PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
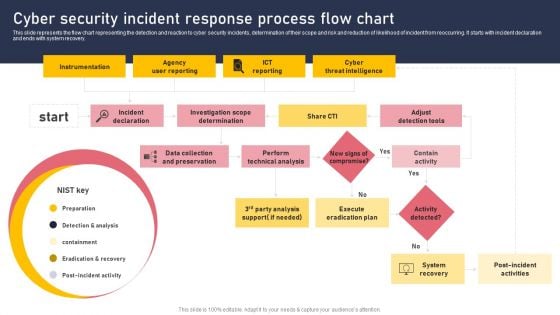
Cyber Security Incident Response Process Flow Chart Download PDF
This slide represents the flow chart representing the detection and reaction to cyber security incidents, determination of their scope and risk and reduction of likelihood of incident from reoccurring. It starts with incident declaration and ends with system recovery. This Cyber Security Incident Response Process Flow Chart Download PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
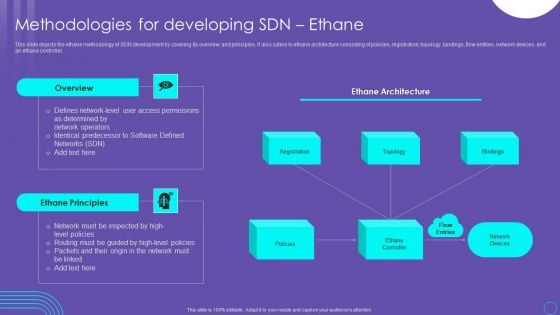
SDN Security Architecture Methodologies For Developing SDN Ethane Infographics PDF
This slide depicts the ethane methodology of SDN development by covering its overview and principles. It also caters to ethane architecture consisting of policies, registration, topology, bindings, flow entities, network devices, and an ethane controller. This SDN Security Architecture Methodologies For Developing SDN Ethane Infographics PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
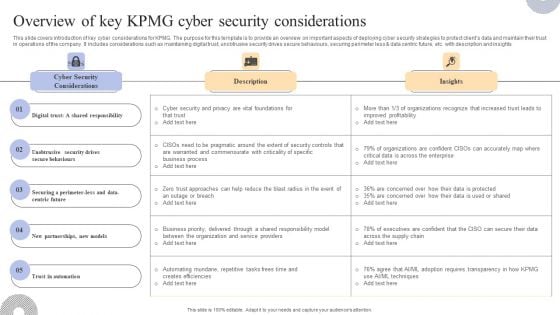
Overview Of Key KPMG Cyber Security Considerations Inspiration PDF
This slide covers an introduction to KPMG company ESG strategy to improve reporting to stakeholders. The purpose of this template is to provide overview on introducing ESG strategy, benefits along with reporting insights. It includes benefits such as helping organization assess and improve sustainable performance, establishing strong reputation and trust, attracting investors and customers, etc. Welcome to our selection of the Overview Of Key KPMG Cyber Security Considerations Inspiration PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today
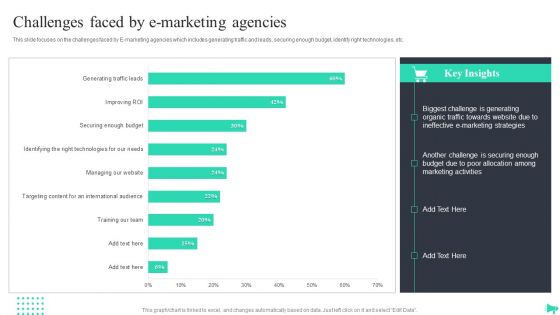
Implementing Ecommerce Marketing Services Plan Challenges Faced By E Marketing Agencies Professional PDF
This slide focuses on the challenges faced by E marketing agencies which includes generating traffic and leads, securing enough budget, identify right technologies, etc. This Implementing Ecommerce Marketing Services Plan Challenges Faced By E Marketing Agencies Professional PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

Secure Web Gateway Architecture And Working Web Threat Protection System
This slide demonstrates the working process of Secure Web Gateway by providing a visualization of its various components. The purpose of this slide is to explain how SWG works. Key points included are offices, private data centres, interface, etc. This Secure Web Gateway Architecture And Working Web Threat Protection System from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide demonstrates the working process of Secure Web Gateway by providing a visualization of its various components. The purpose of this slide is to explain how SWG works. Key points included are offices, private data centres, interface, etc.

Various CSR Initiatives Taken Global Security Industry PPT Presentation IR SS V
The slide highlights csr initiatives taken in Defense sector. It is to ensure market stability, consumer protection and foster innovation while mitigating risks. It includes financial education and literacy, supporting vulnerable communities, disaster relief and preparedness. This Various CSR Initiatives Taken Global Security Industry PPT Presentation IR SS V from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. The slide highlights csr initiatives taken in Defense sector. It is to ensure market stability, consumer protection and foster innovation while mitigating risks. It includes financial education and literacy, supporting vulnerable communities, disaster relief and preparedness.
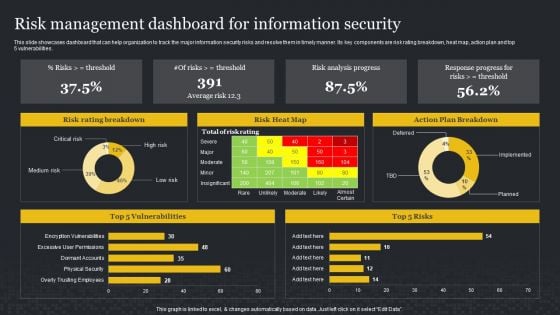
Risk Management Dashboard For Information Security Cybersecurity Risk Assessment Sample PDF
This slide showcases dashboard that can help organization to track the major information security risks and resolve them in timely manner. Its key components are risk rating breakdown, heat map, action plan and top 5 vulnerabilities. This Risk Management Dashboard For Information Security Cybersecurity Risk Assessment Sample PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
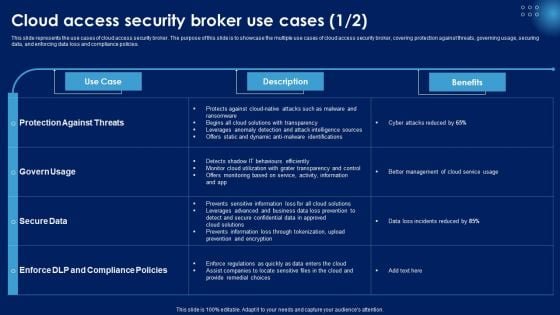
Cloud Access Security Broker Use Cases Ppt PowerPoint Presentation File Background Images PDF
This slide represents the use cases of cloud access security broker. The purpose of this slide is to showcase the multiple use cases of cloud access security broker, covering protection against threats, governing usage, securing data, and enforcing data loss and compliance policies. This Cloud Access Security Broker Use Cases Ppt PowerPoint Presentation File Background Images PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
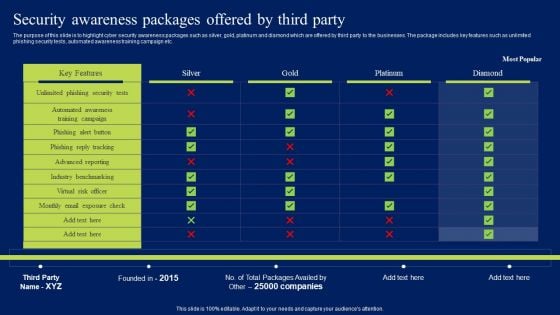
Security Awareness Packages Offered By Third Party Ppt Layouts Topics PDF
The purpose of this slide is to highlight cyber security awareness packages such as silver, gold, platinum and diamond which are offered by third party to the businesses. The package includes key features such as unlimited phishing security tests, automated awareness training campaign etc. This Security Awareness Packages Offered By Third Party Ppt Layouts Topics PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
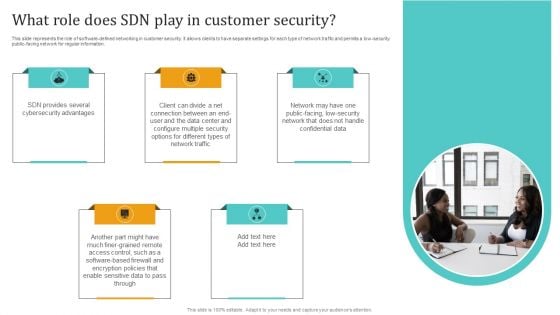
Empowering Network Agility Through SDN What Role Does SDN Play In Customer Security Professional PDF
This slide represents the role of software defined networking in customer security. It allows clients to have separate settings for each type of network traffic and permits a low security public facing network for regular information. This Empowering Network Agility Through SDN What Role Does SDN Play In Customer Security Professional PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
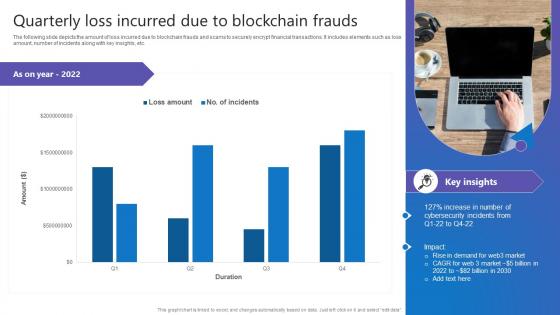
Quarterly Loss Incurred Due Comprehensive Guide To Blockchain Digital Security Themes Pdf
The following slide depicts the amount of loss incurred due to blockchain frauds and scams to securely encrypt financial transactions. It includes elements such as loss amount, number of incidents along with key insights, etc. This Quarterly Loss Incurred Due Comprehensive Guide To Blockchain Digital Security Themes Pdf from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. The following slide depicts the amount of loss incurred due to blockchain frauds and scams to securely encrypt financial transactions. It includes elements such as loss amount, number of incidents along with key insights, etc.


 Continue with Email
Continue with Email

 Home
Home


































