Safety Plan
Blockchain Technology Implementation In Various Banking Activities Pictures PDF
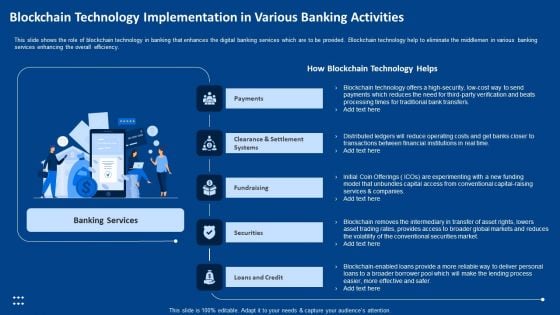
This slide shows the role of blockchain technology in banking that enhances the digital banking services which are to be provided. Blockchain technology help to eliminate the middlemen in various banking services enhancing the overall efficiency. This is a blockchain technology implementation in various banking activities pictures pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like payments, fundraising, securities, loans and credit, clearance and settlement systems. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Analysis And Valuation Of Equity Securities Ppt PowerPoint Presentation Icon Slide Portrait
This is a analysis and valuation of equity securities ppt powerpoint presentation icon slide portrait. This is a one stage process. The stages in this process are business, management, marketing, agenda.
Key Steps To Create Role Specific Cyber Security Training Program Structure PDF
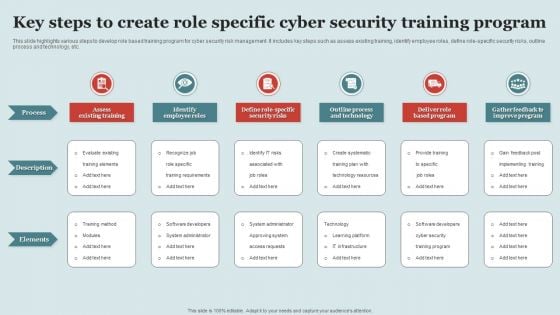
This slide highlights various steps to develop role based training program for cyber security risk management. It includes key steps such as assess existing training, identify employee roles, define role-specific security risks, outline process and technology, etc. Persuade your audience using this Key Steps To Create Role Specific Cyber Security Training Program Structure PDF This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Process, Description, Elements. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Proposal For Corporate Meeting Scope One Pager Sample Example Document
The slide presents the scope of services for the proposal project in terms of catering, internet and audio visual equipment , logistics, security and decor. Presenting you an exemplary Proposal For Corporate Meeting Scope One Pager Sample Example Document. Our one pager comprises all the must have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Proposal For Corporate Meeting Scope One Pager Sample Example Document brilliant piece now.

Scope For Scientific Conference One Pager Sample Example Document
The slide presents the scope of services for the proposal project in terms of catering, internet and audio-visual equipment, logistics, security and decor. Presenting you an exemplary Scope For Scientific Conference One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Scope For Scientific Conference One Pager Sample Example Document brilliant piece now.
Benefits Of Content Management System In Web Development Graphics PDF
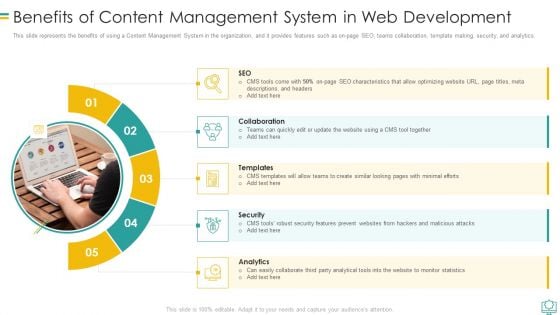
This slide represents the benefits of using a Content Management System in the organization, and it provides features such as on page SEO, teams collaboration, template making, security, and analytics.Presenting Benefits Of Content Management System In Web Development Graphics PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Collaboration, Security, Analytics In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Security For Your Organization Staff Training Schedule With Cost Ppt Visual Aids Slides PDF
Presenting this set of slides with name cyber security for your organization staff training schedule with cost ppt visual aids slides pdf. This is a one stage process. The stages in this process are advanced software training, advanced skills train, training module. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Computer Security Incident Handling Staff Training Schedule With Cost Demonstration PDF
Presenting this set of slides with name computer security incident handling staff training schedule with cost demonstration pdf. The topics discussed in these slides are packages, level 1, level 2. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Types Of Information Leaked In Data Breach Data Breach Prevention Brochure Pdf
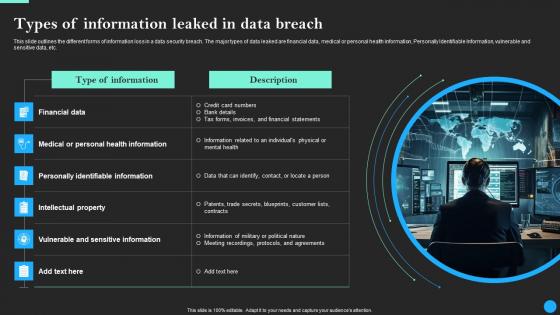
Present like a pro with Types Of Information Leaked In Data Breach Data Breach Prevention Brochure Pdf Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide outlines the different forms of information loss in a data security breach. The major types of data leaked are financial data, medical or personal health information, Personally Identifiable Information, vulnerable and sensitive data, etc.

Risk Management Model For Data Security Online And Onsite Training Schedule For Employee Rules PDF
This slide illustrates employee training schedule. It covers details about employee name, its position, software name, course type, training mode and duration. Deliver an awe inspiring pitch with this creative Risk Management Model For Data Security Online And Onsite Training Schedule For Employee Rules PDF bundle. Topics like Course Type, Training Mode, Training Duration, Employee can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Financing Catalogue For Security Underwriting Agreement Share Allocation Process Clipart PDF
The slide provides the methods of share allocation in different subscription cases oversubscription and under subscription. Key methods include lottery basis, pro rata basis, and combination of both. Presenting financing catalogue for security underwriting agreement share allocation process clipart pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like in case undersubscription, in case of oversubscription. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Strategies To Mitigate Cyber Security Risks Backup Maintenance Selecting Offsite Storage Facility Vendor Ppt Model Graphic Images PDF
Presenting this set of slides with name strategies to mitigate cyber security risks backup maintenance selecting offsite storage facility vendor ppt model graphic images pdf. This is a five stage process. The stages in this process are geographic location, accessibility, security, cost, operational fees, environment. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
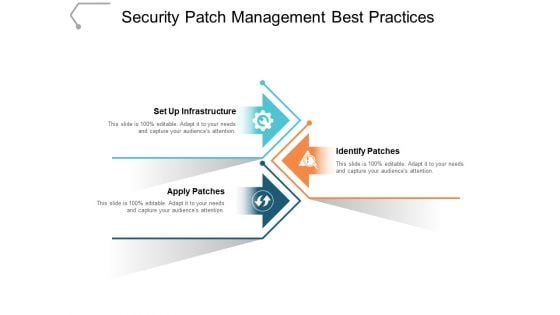
Security Patch Management Best Practices Ppt PowerPoint Presentation Pictures Infographics
This is a security patch management best practices ppt powerpoint presentation pictures infographics. This is a three stage process. The stages in this process are patch management process, patch management procedure, patch management approach.
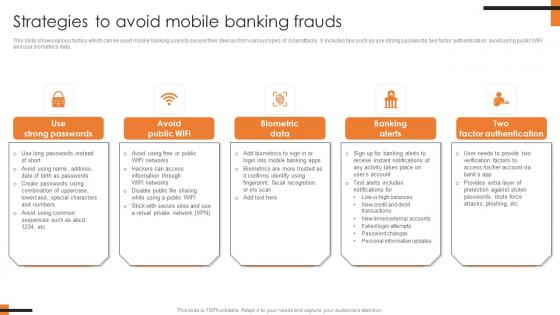
Strategies To Avoid Mobile Banking Frauds Comprehensive Smartphone Banking Slides Pdf
This slide shows various tactics which can be used mobile banking users to secure their devices from various types of cyberattacks. It includes tips such as use strong passwords, two factor authentication, avoid using public WIFI and use biometrics data.This modern and well-arranged Strategies To Avoid Mobile Banking Frauds Comprehensive Smartphone Banking Slides Pdf provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide shows various tactics which can be used mobile banking users to secure their devices from various types of cyberattacks. It includes tips such as use strong passwords, two factor authentication, avoid using public WIFI and use biometrics data.
Business PowerPoint Templates Download Process Circular Flow Network Slides
We present our business powerpoint templates download process Circular Flow Network Slides.Download and present our Globe PowerPoint Templates because You can Be the puppeteer with our PowerPoint Templates and Slides as your strings. Lead your team through the steps of your script. Download and present our Ring Charts PowerPoint Templates because You can Inspire your team with our PowerPoint Templates and Slides. Let the force of your ideas flow into their minds. Download our Circle Charts PowerPoint Templates because this Layout can explain the relevance of the different layers and stages in getting down to your core competence, ability and desired result. Use our Arrows PowerPoint Templates because it shows various choices to be made. Use our Business PowerPoint Templates because you have secured a name for yourself in the domestic market. Now the time is right to spread your reach to other countries.Use these PowerPoint slides for presentations relating to Business, chart, circle,colors, concept, corporate, cycle, data,design, detail, development, diagram,engineering, graphic, ideas, illustration,image, implement, implementation, life,lifecycle, management, model, objects,organization, phase, plan, process,product, professional, project, quality,schema, shape. The prominent colors used in the PowerPoint template are Blue, Yellow, White. You can be sure our business powerpoint templates download process Circular Flow Network Slides will make you look like a winner. PowerPoint presentation experts tell us our circle PowerPoint templates and PPT Slides are designed by professionals Professionals tell us our business powerpoint templates download process Circular Flow Network Slides are Graceful. Presenters tell us our data PowerPoint templates and PPT Slides are the best it can get when it comes to presenting. Professionals tell us our business powerpoint templates download process Circular Flow Network Slides are Whimsical. Customers tell us our corporate PowerPoint templates and PPT Slides are Beautiful. Build teams with our Business PowerPoint Templates Download Process Circular Flow Network Slides. Download without worries with our money back guaranteee.

Protected Dollar Money PowerPoint Templates Ppt Backgrounds For Slides 0313
We present our Protected Dollar Money PowerPoint Templates PPT Backgrounds For Slides 0313.Use our Umbrellas PowerPoint Templates because Our PowerPoint Templates and Slides are topically designed to provide an attractive backdrop to any subject. Download and present our Security PowerPoint Templates because They will bring a lot to the table. Their alluring flavours will make your audience salivate. Download our Shapes PowerPoint Templates because Our PowerPoint Templates and Slides will let you Hit the target. Go the full distance with ease and elan. Download our Signs PowerPoint Templates because Our PowerPoint Templates and Slides offer you the widest possible range of options. Use our Money PowerPoint Templates because Our PowerPoint Templates and Slides are conceived by a dedicated team. Use them and give form to your wondrous ideas.Use these PowerPoint slides for presentations relating to Dollar sign under umbrella, signs, shapes, umbrellas, security, money. The prominent colors used in the PowerPoint template are Red, Gray, Black. Hand your team the perfect strategy with our Protected Dollar Money PowerPoint Templates Ppt Backgrounds For Slides 0313. Try us out and see what a difference our templates make.

Factors Influencing Software Defined Networking SDN Adoption Evolution Of SDN Controllers Slides Pdf
This slide represents the factors influencing SDN adoption, including cultural change, security risks, interoperability, scalability, performance, and reliability. SDN is appealing regarding network simplicity and investment, and operational cost savings. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Factors Influencing Software Defined Networking SDN Adoption Evolution Of SDN Controllers Slides Pdf and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide represents the factors influencing SDN adoption, including cultural change, security risks, interoperability, scalability, performance, and reliability. SDN is appealing regarding network simplicity and investment, and operational cost savings.

Ecommerce Payment Gateway System Evaluation And Deployment Of Enhanced Portrait Pdf
This slide represents the architecture showing the ways in which payment gateway validates consumers card details securely and ensures availability of funds and eventually enables merchants to get paid. Find highly impressive Ecommerce Payment Gateway System Evaluation And Deployment Of Enhanced Portrait Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Ecommerce Payment Gateway System Evaluation And Deployment Of Enhanced Portrait Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now. This slide represents the architecture showing the ways in which payment gateway validates consumers card details securely and ensures availability of funds and eventually enables merchants to get paid.

Optimizing Business Integration Key Trends That Drive The Industry Information Pdf
Mentioned slide shows various key trends that are driving many industries. Trends covered in the slide are IoT, smarter business system with AI, cyber security and improved employee engagement through technology. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Optimizing Business Integration Key Trends That Drive The Industry Information Pdf and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. Mentioned slide shows various key trends that are driving many industries. Trends covered in the slide are IoT, smarter business system with AI, cyber security and improved employee engagement through technology.

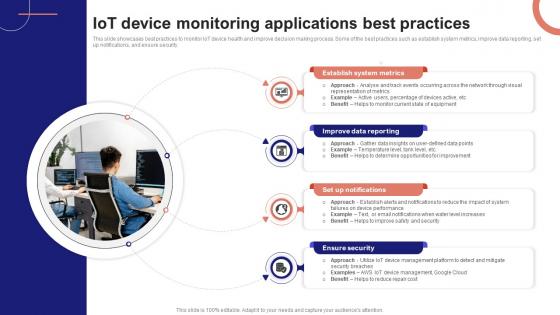
Iot Device Monitoring Applications Best Practices Iot Device Management Infographics Pdf
This slide showcases best practices to monitor IoT device health and improve decision making process. Some of the best practices such as establish system metrics, improve data reporting, set up notifications, and ensure security. Slidegeeks is here to make your presentations a breeze with Iot Device Monitoring Applications Best Practices Iot Device Management Infographics Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide showcases best practices to monitor IoT device health and improve decision making process. Some of the best practices such as establish system metrics, improve data reporting, set up notifications, and ensure security.
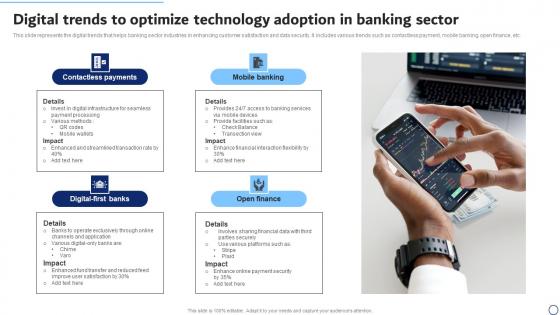
Digital Trends To Optimize Technology Adoption In Banking Sector Themes Pdf
This slide represents the digital trends that helps banking sector industries in enhancing customer satisfaction and data security. It includes various trends such as contactless payment, mobile banking, open finance, etc. Showcasing this set of slides titled Digital Trends To Optimize Technology Adoption In Banking Sector Themes Pdf. The topics addressed in these templates are Contactless Payments, Mobile Banking, Open Finance. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide represents the digital trends that helps banking sector industries in enhancing customer satisfaction and data security. It includes various trends such as contactless payment, mobile banking, open finance, etc.
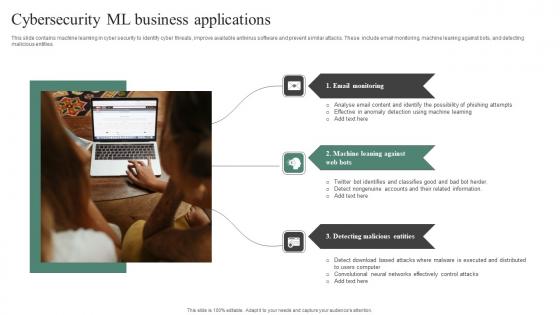
Cybersecurity ML Business Applications Sample Pdf
This slide contains machine learning in cyber security to identify cyber threats, improve available antivirus software and prevent similar attacks. These include email monitoring, machine leaning against bots, and detecting malicious entities. Pitch your topic with ease and precision using this Cybersecurity ML Business Applications Sample Pdf. This layout presents information on Email Monitoring, Machine Leaning, Detecting Malicious Entities. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide contains machine learning in cyber security to identify cyber threats, improve available antivirus software and prevent similar attacks. These include email monitoring, machine leaning against bots, and detecting malicious entities.

Key Drivers For Encouraging Adoption Of Complete Roadmap To Blockchain BCT SS V
This slide covers critical factors that encourages widespread adoption of blockchain technology across various industries. It includes drivers such as efficiency and cost savings, security and data integrity, disintermediation and decentralization, etc. This Key Drivers For Encouraging Adoption Of Complete Roadmap To Blockchain BCT SS V from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide covers critical factors that encourages widespread adoption of blockchain technology across various industries. It includes drivers such as efficiency and cost savings, security and data integrity, disintermediation and decentralization, etc.
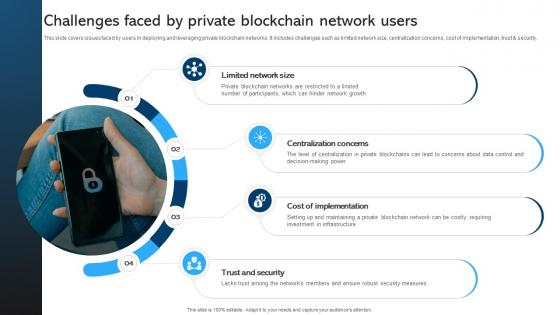
Comprehensive Manual For Challenges Faced By Private Blockchain Network Users BCT SS V
This slide covers issues faced by users in deploying and leveraging private blockchain networks. It includes challenges such as limited network size, centralization concerns, cost of implementation, trust and security. Boost your pitch with our creative Comprehensive Manual For Challenges Faced By Private Blockchain Network Users BCT SS V. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide covers issues faced by users in deploying and leveraging private blockchain networks. It includes challenges such as limited network size, centralization concerns, cost of implementation, trust and security.
IoT Device Management Fundamentals IoT Device Monitoring Applications Best Practices IoT Ss V
This slide showcases best practices to monitor IoT device health and improve decision making process. Some of the best practices such as establish system metrics, improve data reporting, set up notifications, and ensure security. Present like a pro with IoT Device Management Fundamentals IoT Device Monitoring Applications Best Practices IoT SS V. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide showcases best practices to monitor IoT device health and improve decision making process. Some of the best practices such as establish system metrics, improve data reporting, set up notifications, and ensure security.

IoT Device Management Fundamentals Key Factors For Selecting Right IoT Device Management IoT Ss V
This slide exhibits specific factors to consider for selecting an IoT device management platform. These factors include connectivity management, scalability, security, and ability to adapt technological changes. The IoT Device Management Fundamentals Key Factors For Selecting Right IoT Device Management IoT SS V is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide exhibits specific factors to consider for selecting an IoT device management platform. These factors include connectivity management, scalability, security, and ability to adapt technological changes.
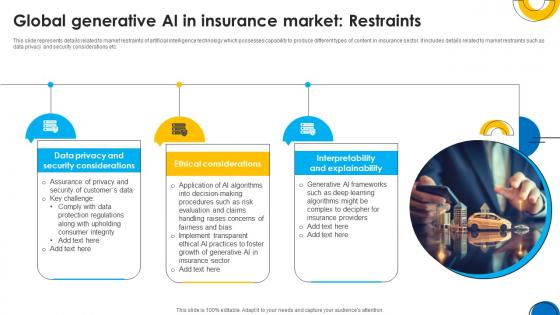
A101 Implementing ChatGpt In Insurance Global Generative Ai In Insurance ChatGpt SS V
This slide represents details related to market restraints of artificial intelligence technology which possesses capability to produce different types of content in insurance sector. It includes details related to market restraints such as data privacy and security considerations etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate A101 Implementing ChatGpt In Insurance Global Generative Ai In Insurance ChatGpt SS V for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide represents details related to market restraints of artificial intelligence technology which possesses capability to produce different types of content in insurance sector. It includes details related to market restraints such as data privacy and security considerations etc.
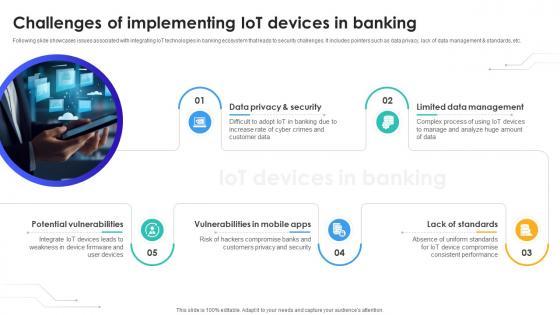
Challenges Of Implementing IoT Devices In Banking IoT In Banking For Digital Future IoT SS V
Following slide showcases issues associated with integrating IoT technologies in banking ecosystem that leads to security challenges. It includes pointers such as data privacy, lack of data management and standards, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Challenges Of Implementing IoT Devices In Banking IoT In Banking For Digital Future IoT SS V for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. Following slide showcases issues associated with integrating IoT technologies in banking ecosystem that leads to security challenges. It includes pointers such as data privacy, lack of data management and standards, etc.
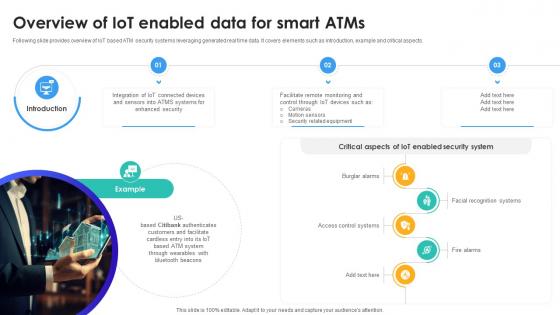
Overview Of IoT Enabled Data For Smart Atms IoT In Banking For Digital Future IoT SS V
Following slide provides overview of IoT based ATM security systems leveraging generated real time data. It covers elements such as introduction, example and critical aspects. Retrieve professionally designed Overview Of IoT Enabled Data For Smart Atms IoT In Banking For Digital Future IoT SS V to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. Following slide provides overview of IoT based ATM security systems leveraging generated real time data. It covers elements such as introduction, example and critical aspects.

Performance Analysis Of Current Automated Regression Testing And Achieving PPT Slide
The purpose of this slide is to indicate the performance analysis of the organizations current security infrastructure. The key components include where we are, the gap, where we want to be, and recommended solutions. Find highly impressive Performance Analysis Of Current Automated Regression Testing And Achieving PPT Slide on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Performance Analysis Of Current Automated Regression Testing And Achieving PPT Slide for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now The purpose of this slide is to indicate the performance analysis of the organizations current security infrastructure. The key components include where we are, the gap, where we want to be, and recommended solutions.

Cloud Recruitment Technology Enhancing Recruitment Process PPT Template
This slide showcases overview of cloud based recruitment technology which can guide HR professionals in streamlining hiring process. It also provides details about remote work, workflows, security, efficiency, e-recruitment, connectivity, operational costs, etc. Get a simple yet stunning designed Cloud Recruitment Technology Enhancing Recruitment Process PPT Template. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Cloud Recruitment Technology Enhancing Recruitment Process PPT Template can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide showcases overview of cloud based recruitment technology which can guide HR professionals in streamlining hiring process. It also provides details about remote work, workflows, security, efficiency, e-recruitment, connectivity, operational costs, etc.
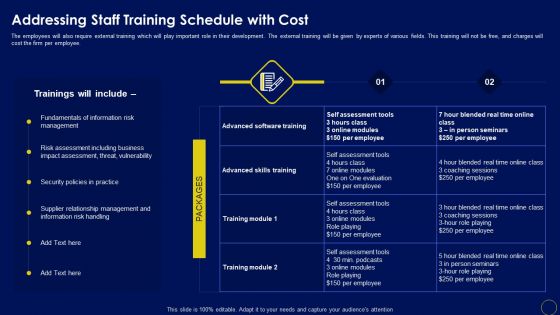
Addressing Staff Training Schedule With Cost Business Mobile Device Security Management And Mitigation Diagrams PDF
The employees will also require external training which will play important role in their development. The external training will be given by experts of various fields. This training will not be free, and charges will cost the firm per employee. This Addressing Staff Training Schedule With Cost Business Mobile Device Security Management And Mitigation Diagrams PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Addressing Staff Training Schedule With Cost Business Mobile Device Security Management And Mitigation Diagrams PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today.
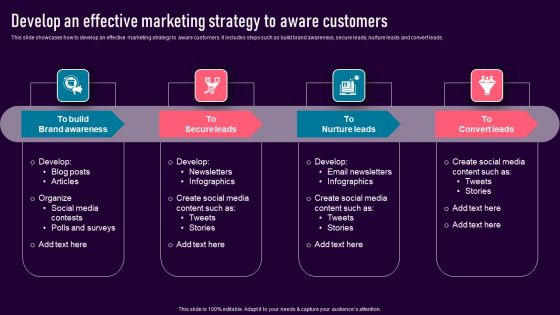
Develop An Effective Marketing Strategy To Aware Customers Elements PDF
This slide showcases how to develop an effective marketing strategy to aware customers. It includes steps such as build brand awareness, secure leads, nurture leads and convert leads. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Develop An Effective Marketing Strategy To Aware Customers Elements PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Develop An Effective Marketing Strategy To Aware Customers Elements PDF
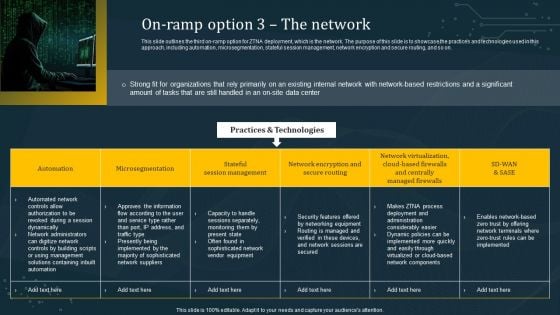
On Ramp Option 3 The Network Structure PDF
This slide outlines the third on-ramp option for ZTNA deployment, which is the network. The purpose of this slide is to showcase the practices and technologies used in this approach, including automation, microsegmentation, stateful session management, network encryption and secure routing, and so on. Do you know about Slidesgeeks On Ramp Option 3 The Network Structure PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
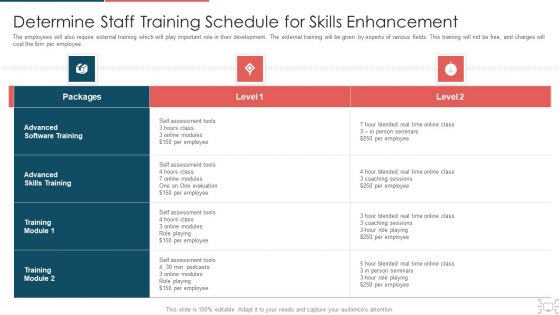
Cyber Security Administration In Organization Determine Staff Training Schedule For Skills Diagrams PDF
The employees will also require external training which will play important role in their development. The external training will be given by experts of various fields. This training will not be free, and charges will cost the firm per employee. Deliver an awe inspiring pitch with this creative cyber security administration in organization determine staff training schedule for skills diagrams pdf bundle. Topics like determine staff training schedule for skills enhancement can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Stakeholder Management Assessment Business Fundamentals Human Rights Policies Of The Company Background PDF
This slide shows the human rights policies that are followed by the company for the betterment of community and employees such as stakeholder engagement, diversity and inclusion, safe and healthy workplace, workplace security, work hours, wages and benefits etc. This is a stakeholder management assessment business fundamentals human rights policies of the company background pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like stakeholder engagement, workplace security, wages and benefits, human rights. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
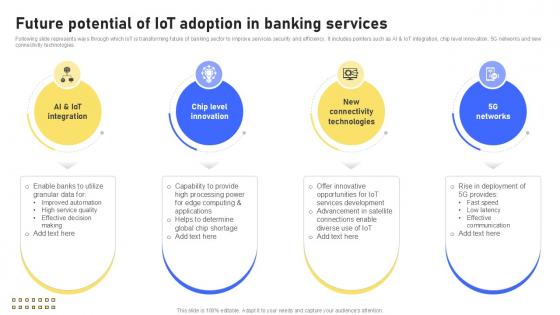
Future Potential Of IoT Adoption Banking Future With IoT Ppt Presentation IoT SS V
Following slide represents ways through which IoT is transforming future of banking sector to improve services security and efficiency. It includes pointers such as AI and IoT integration, chip level innovation, 5G networks and new connectivity technologies. There are so many reasons you need a Future Potential Of IoT Adoption Banking Future With IoT Ppt Presentation IoT SS V. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. Following slide represents ways through which IoT is transforming future of banking sector to improve services security and efficiency. It includes pointers such as AI and IoT integration, chip level innovation, 5G networks and new connectivity technologies.
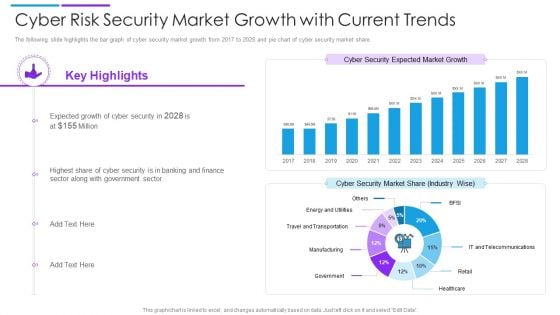
Cyber Risk Security Market Growth With Current Trends Summary PDF
The following slide highlights the bar graph of cyber security market growth from 2017 to 2028 and pie chart of cyber security market share. Showcasing this set of slides titled cyber risk security market growth with current trends summary pdf. The topics addressed in these templates are cyber security market share, cyber security expected market growth, banking and finance. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
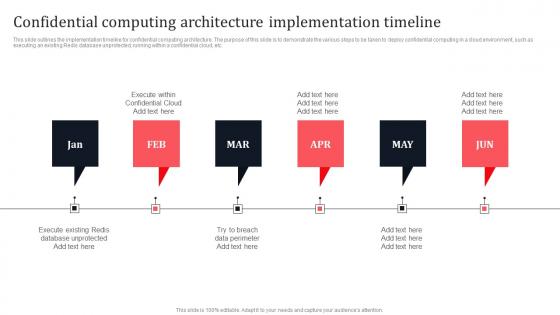
Confidential Computing Architecture Implementation Timeline Secure Multi Party Demonstration Pdf
This slide outlines the implementation timeline for confidential computing architecture. The purpose of this slide is to demonstrate the various steps to be taken to deploy confidential computing in a cloud environment, such as executing an existing Redis database unprotected, running within a confidential cloud, etc. Find highly impressive Confidential Computing Architecture Implementation Timeline Secure Multi Party Demonstration Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Confidential Computing Architecture Implementation Timeline Secure Multi Party Demonstration Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now. This slide outlines the implementation timeline for confidential computing architecture. The purpose of this slide is to demonstrate the various steps to be taken to deploy confidential computing in a cloud environment, such as executing an existing Redis database unprotected, running within a confidential cloud, etc.

Cyber Security Administration In Organization Addressing Threat Management Team Training Schedule Inspiration PDF
The threat management team needs to have strong critical and creative thinking skills so that they become capable in taking key decisions without complete or conflicting information under immense tensed situations. The team will be trained by experts who will also use scenario based activities and costing will be per employee basis. Deliver and pitch your topic in the best possible manner with this cyber security administration in organization addressing threat management team training schedule inspiration pdf. Use them to share invaluable insights on probing, unexpected, decision, skills, managerial and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
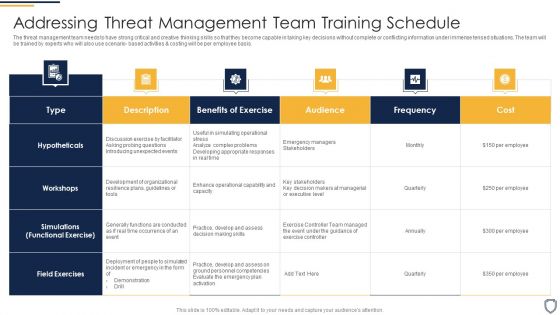
Corporate Security And Risk Management Addressing Threat Management Team Training Schedule Clipart PDF
The threat management team needs to have strong critical and creative thinking skills so that they become capable in taking key decisions without complete or conflicting information under immense tensed situations. The team will be trained by experts who will also use scenario- based activities and costing will be per employee basis. Deliver an awe inspiring pitch with this creative corporate security and risk management addressing threat management team training schedule clipart pdf bundle. Topics like benefits of exercise, audience, frequency, cost can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
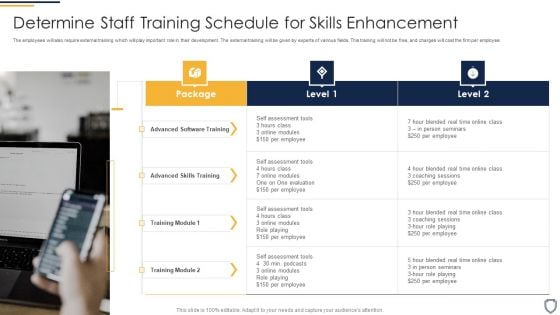
Corporate Security And Risk Management Determine Staff Training Schedule For Skills Enhancement Inspiration PDF
The employees will also require external training which will play important role in their development. The external training will be given by experts of various fields. This training will not be free, and charges will cost the firm per employee. Presenting corporate security and risk management determine staff training schedule for skills enhancement inspiration pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like advanced software training, advanced skills training. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
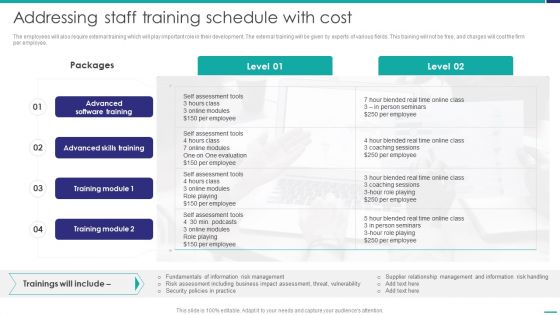
Addressing Staff Training Schedule With Cost Mobile Device Security Management Diagrams PDF
The employees will also require external training which will play important role in their development. The external training will be given by experts of various fields. This training will not be free, and charges will cost the firm per employee. Deliver an awe inspiring pitch with this creative Addressing Staff Training Schedule With Cost Mobile Device Security Management Diagrams PDF bundle. Topics like Advanced Skills, Coaching Sessions, Assessment Tools can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Security Awareness Tracking Kpis Ppt Slides Shapes PDF
This slide covers the key performance for security awareness training including compliance, security culture and incident reduction. Deliver and pitch your topic in the best possible manner with this security awareness tracking kpis ppt slides shapes pdf. Use them to share invaluable insights on security awareness tracking kpis and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
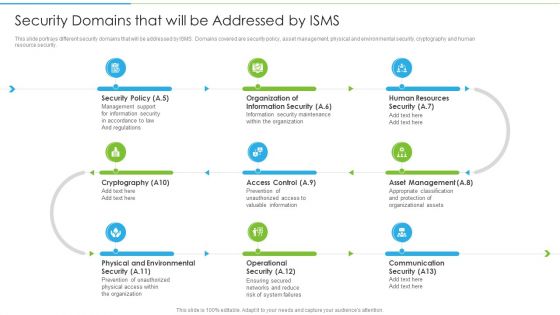
Ways To Accomplish ISO 27001 Accreditation Security Domains That Will Be Addressed By Isms Topics PDF
This slide portrays different security domains that will be addressed by ISMS. Domains covered are security policy, asset management, physical and environmental security, cryptography and human resource security. This is a Ways To Accomplish ISO 27001 Accreditation Security Domains That Will Be Addressed By Isms Topics PDF template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security Policy, Organization Information, Human Resources. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
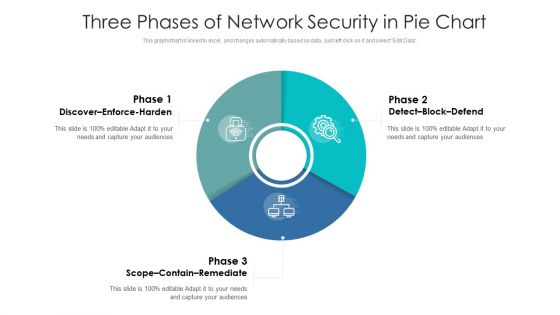
Three Phases Of Network Security In Pie Chart Ppt PowerPoint Presentation Gallery Graphics Download PDF
Pitch your topic with ease and precision using this three phases of network security in pie chart ppt powerpoint presentation gallery graphics download pdf. This layout presents information on discover enforce harden, detect block defend, scope contain remediate. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Challenges And Opportunities For Online Money Transfer Service Provider Ppt Professional Files PDF
The following slide highlights some major challenges and opportunities fund transfer service providers to grab the advantage. It includes elements such as low profit margin, reliability, security etc. Showcasing this set of slides titled Challenges And Opportunities For Online Money Transfer Service Provider Ppt Professional Files PDF. The topics addressed in these templates are Challenges, Opportunities, Traditional Providers. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

4 Best Practices Of Data Management Ethics In Organizations Ppt Infographics Grid PDF
This slide shows the various data practices that organizations can use in data collection. It includes having clear policies, get employees buy-in, secure IT systems and be transparent. Persuade your audience using this 4 Best Practices Of Data Management Ethics In Organizations Ppt Infographics Grid PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Clear Policies, Get Employees, Buy In, Secure IT Systems, Be Transparent. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
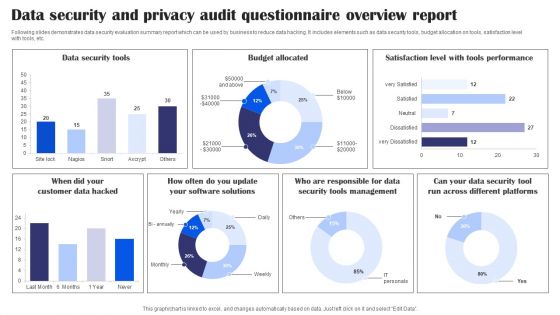
Data Security And Privacy Audit Questionnaire Overview Report Survey SS
Following slides demonstrates data security evaluation summary report which can be used by business to reduce data hacking. It includes elements such as data security tools, budget allocation on tools, satisfaction level with tools, etc. Pitch your topic with ease and precision using this Data Security And Privacy Audit Questionnaire Overview Report Survey SS. This layout presents information on Data Security Tools, Budget Allocated, Tools Performance, Data Security Tools Management. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Computer Security Incident Handling Analyzing IT Department On Nist Cybersecurity Framework Introduction PDF
Presenting this set of slides with name computer security incident handling analyzing it department on nist cybersecurity framework introduction pdf. The topics discussed in these slides are identify, detect, protect, respond, recover. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
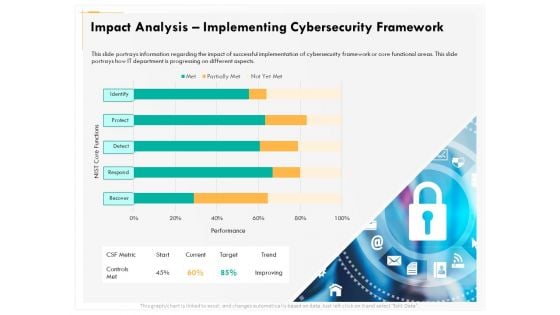
Computer Security Incident Handling Impact Analysis Implementing Cybersecurity Framework Designs PDF
Presenting this set of slides with name computer security incident handling impact analysis implementing cybersecurity framework designs pdf. The topics discussed in these slides are recover, detect, respond, protect, identify. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Current State Of Security Automation With Projected Development Icons PDF
This slide highlights the current state of security automation in the pie chart format. It includes projected development of security automation and state of security automation.Want to ace your presentation in front of a live audience Our Current State Of Security Automation With Projected Development Icons PDF can help you do that by engaging all the users towards you.. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.

CRM Implementation Strategy CRM Training Program For Employees Infographics PDF
This slide highlights the CRM training Program for employees which includes overview training, lead management session, customization and data security session.This is a CRM Implementation Strategy CRM Training Program For Employees Infographics PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Management Session, Customization Session, Overview Training You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Implementing Cybersecurity Awareness Program To Prevent Attacks Security Awareness Training Program Challenges Introduction PDF
The purpose of this slide is to exhibit biggest cyber security awareness challenges which is faced by the organization. Outdated content, burden on administrators, low employee participation rate and employees losing interest are some of the key challenges which are highlighted in the slide. Want to ace your presentation in front of a live audience Our Implementing Cybersecurity Awareness Program To Prevent Attacks Security Awareness Training Program Challenges Introduction PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.
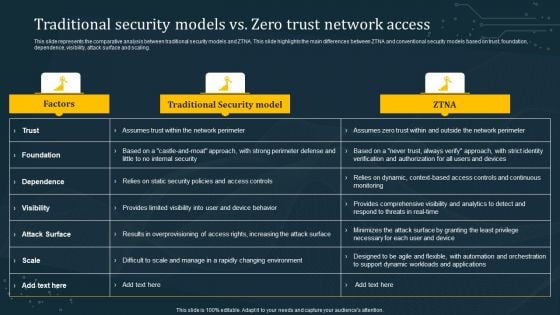
Traditional Security Models Vs Zero Trust Network Access Summary PDF
This slide represents the comparative analysis between traditional security models and ZTNA. This slide highlights the main differences between ZTNA and conventional security models based on trust, foundation, dependence, visibility, attack surface and scaling. This modern and well-arranged Traditional Security Models Vs Zero Trust Network Access Summary PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
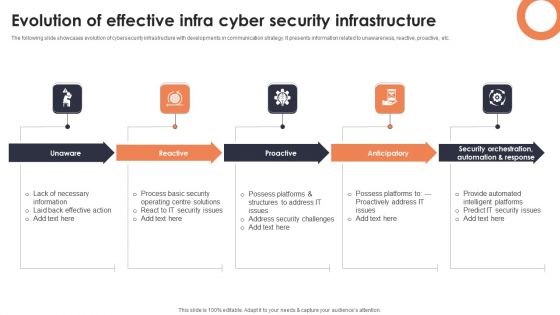
Evolution Of Effective Infra Cyber Security Infrastructure Infographics PDF
The following slide showcases evolution of cybersecurity infrastructure with developments in communication strategy. It presents information related to unawareness, reactive, proactive, etc. Presenting Evolution Of Effective Infra Cyber Security Infrastructure Infographics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Unaware, Reactive, Proactive. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
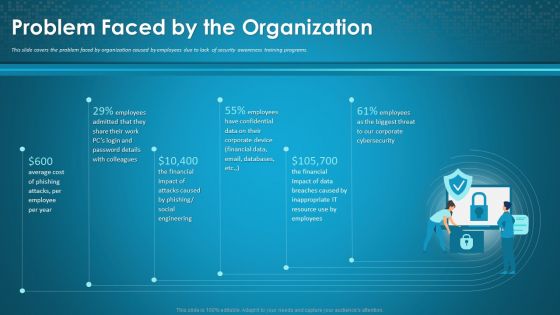
Organizational Network Staff Learning Problem Faced By The Organization Topics PDF
This slide covers the problem faced by organization caused by employees due to lack of security awareness training programs. This is a organizational network staff learning problem faced by the organization topics pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity, financial data, resource use by employees. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
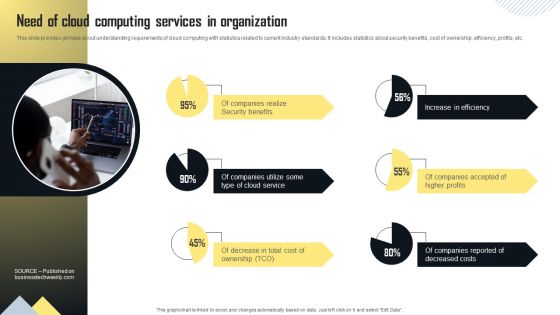
Need Of Cloud Computing Services In Organization Information PDF
This slide provides glimpse about understanding requirements of cloud computing with statistics related to current industry standards. It includes statistics about security benefits, cost of ownership, efficiency, profits, etc. Do you know about Slidesgeeks Need Of Cloud Computing Services In Organization Information PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
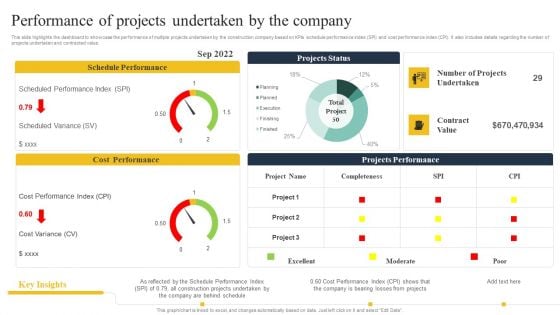
Security Control Techniques For Real Estate Project Performance Of Projects Undertaken By The Company Brochure PDF
Do you have to make sure that everyone on your team knows about any specific topic. I yes, then you should give Security Control Techniques For Real Estate Project Performance Of Projects Undertaken By The Company Brochure PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Security Control Techniques For Real Estate Project Performance Of Projects Undertaken By The Company Brochure PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Security Control Techniques For Real Estate Project Workers Injuries Incurred At Construction Site Infographics PDF
Find highly impressive Security Control Techniques For Real Estate Project Workers Injuries Incurred At Construction Site Infographics PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Security Control Techniques For Real Estate Project Workers Injuries Incurred At Construction Site Infographics PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.


 Continue with Email
Continue with Email

 Home
Home


































