Safety Plan

Improving Customer Satisfaction Essential Personnel Required For Digital Transformation
The following slide outlines key personnel required to develop digital transformation team for converting insurer traditional to technology based. Team consists of members which are technologists, security and compliance specialists, business technology liaisons, project managers, financial stakeholders, marketers, implementation leads and evangelists. This Improving Customer Satisfaction Essential Personnel Required For Digital Transformation is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Improving Customer Satisfaction Essential Personnel Required For Digital Transformation features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today The following slide outlines key personnel required to develop digital transformation team for converting insurer traditional to technology based. Team consists of members which are technologists, security and compliance specialists, business technology liaisons, project managers, financial stakeholders, marketers, implementation leads and evangelists.
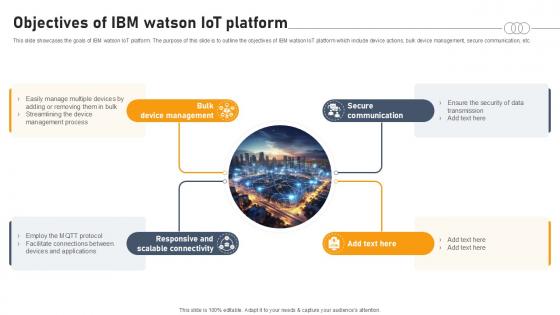
Objectives Of Ibm Watson IOT Platform Aws IOT Platform Ppt Slide
This slide showcases the goals of IBM watson IoT platform. The purpose of this slide is to outline the objectives of IBM watson IoT platform which include device actions, bulk device management, secure communication, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Objectives Of Ibm Watson IOT Platform Aws IOT Platform Ppt Slide to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide showcases the goals of IBM watson IoT platform. The purpose of this slide is to outline the objectives of IBM watson IoT platform which include device actions, bulk device management, secure communication, etc.

Zero Trust Model Zero Trust Network Access Architectural Models
This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption. This Zero Trust Model Zero Trust Network Access Architectural Models is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Zero Trust Model Zero Trust Network Access Architectural Models features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption.

Comprehensive Manual For Blockchain Best Practices For Effectively Using BCT SS V
This slide covers tips to develop private network based blockchain platform. It includes practices such as identifying the participants or stakeholders ensuring their commitments, selecting appropriate consensus mechanism, regularly updating and monitoring security measures, conducting thorough testing and quality assurance, implementing effective communication, etc. Get a simple yet stunning designed Comprehensive Manual For Blockchain Best Practices For Effectively Using BCT SS V. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Comprehensive Manual For Blockchain Best Practices For Effectively Using BCT SS V can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide covers tips to develop private network based blockchain platform. It includes practices such as identifying the participants or stakeholders ensuring their commitments, selecting appropriate consensus mechanism, regularly updating and monitoring security measures, conducting thorough testing and quality assurance, implementing effective communication, etc.
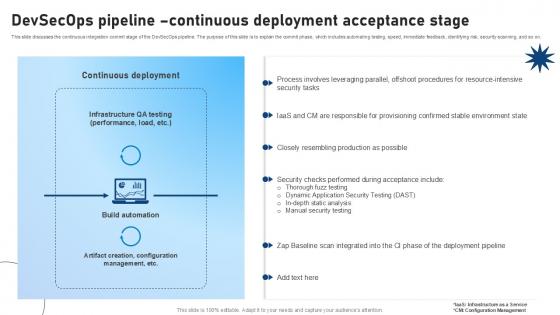
Devsecops Pipeline Continuous Deployment Acceptance Stage Role Of Devsecops Ppt Example
This slide discusses the continuous integration commit stage of the DevSecOps pipeline. The purpose of this slide is to explain the commit phase, which includes automating testing, speed, immediate feedback, identifying risk, security scanning, and so on. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Devsecops Pipeline Continuous Deployment Acceptance Stage Role Of Devsecops Ppt Example template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Devsecops Pipeline Continuous Deployment Acceptance Stage Role Of Devsecops Ppt Example that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide discusses the continuous integration commit stage of the DevSecOps pipeline. The purpose of this slide is to explain the commit phase, which includes automating testing, speed, immediate feedback, identifying risk, security scanning, and so on.

Devsecops Pipeline Production Post Deployment Stage Role Of Devsecops Ppt Powerpoint
This slide discusses the production post-deployment stage of the DevSecOps pipeline. The purpose of this slide is to explain the post-deployment phase and the responsibility of the security team, which includes continuous monitoring, implementing runtime application self-protraction, and so on. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Devsecops Pipeline Production Post Deployment Stage Role Of Devsecops Ppt Powerpoint to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide discusses the production post-deployment stage of the DevSecOps pipeline. The purpose of this slide is to explain the post-deployment phase and the responsibility of the security team, which includes continuous monitoring, implementing runtime application self-protraction, and so on.
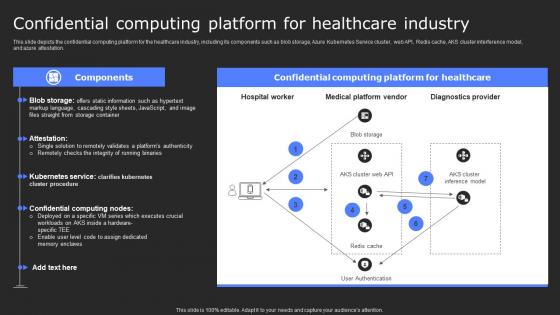
Confidential Computing Platform For Healthcare Secure Computing Framework Structure Pdf
This slide depicts the confidential computing platform for the healthcare industry, including its components such as blob storage, Azure Kubernetes Service cluster, web API, Redis cache, AKS cluster interference model, and azure attestation. Welcome to our selection of the Confidential Computing Platform For Healthcare Secure Computing Framework Structure Pdf. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today This slide depicts the confidential computing platform for the healthcare industry, including its components such as blob storage, Azure Kubernetes Service cluster, web API, Redis cache, AKS cluster interference model, and azure attestation.
Traffic Cones Around Road Powerpoint Templates
Traffic cones around road have been used to design this power point template. Use this diagram to display traffic rules and safety. Download this diagram to display information in visual manner.
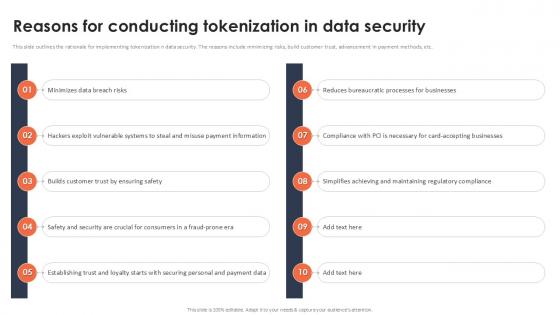
Reasons For Conducting Tokenization In Data Security Securing Your Data Ppt Presentation
This slide outlines the rationale for implementing tokenization n data security. The reasons include minimizing risks, build customer trust, advancement in payment methods, etc. Do you know about Slidesgeeks Reasons For Conducting Tokenization In Data Security Securing Your Data Ppt Presentation These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide outlines the rationale for implementing tokenization n data security. The reasons include minimizing risks, build customer trust, advancement in payment methods, etc.
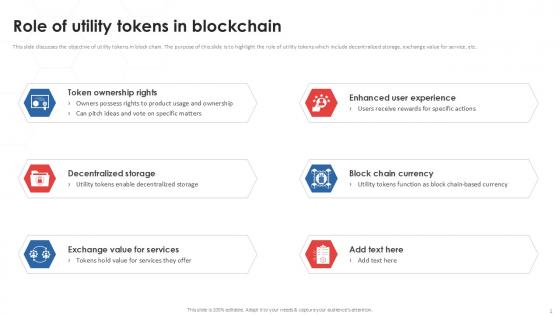
Role Of Utility Tokenization Strategies For Data Security PPT Presentation
This slide discusses the objective of utility tokens in block chain. The purpose of this slide is to highlight the role of utility tokens which include decentralized storage, exchange value for service, etc. Find a pre-designed and impeccable Role Of Utility Tokenization Strategies For Data Security PPT Presentation. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide discusses the objective of utility tokens in block chain. The purpose of this slide is to highlight the role of utility tokens which include decentralized storage, exchange value for service, etc.
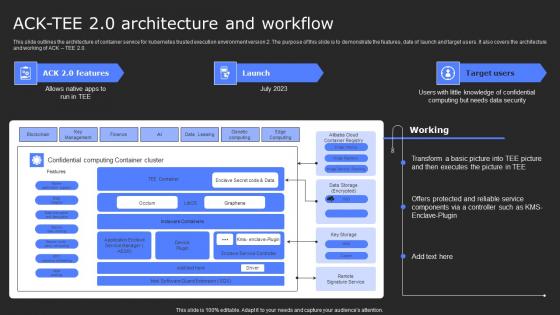
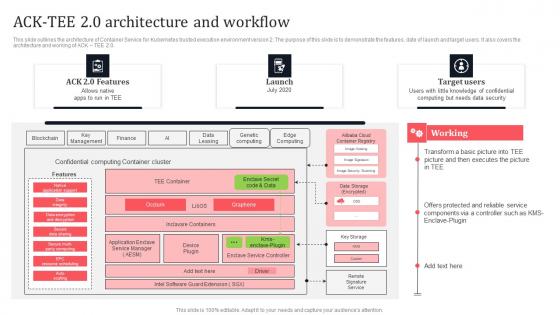
Acktee 20 Architecture And Workflow Secure Computing Framework Guidelines Pdf
This slide outlines the architecture of container service for kubernetes trusted execution environment version 2. The purpose of this slide is to demonstrate the features, date of launch and target users. It also covers the architecture and working of ACK TEE 2.0. Boost your pitch with our creative Acktee 20 Architecture And Workflow Secure Computing Framework Guidelines Pdf. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide outlines the architecture of container service for kubernetes trusted execution environment version 2. The purpose of this slide is to demonstrate the features, date of launch and target users. It also covers the architecture and working of ACK TEE 2.0.

Technical Stack For Evaluating Confidential Secure Computing Framework Information Pdf
This slide depicts the technical stack while assessing confidential computing solutions. The stack divides these solutions into four levels, including application software vendors, infrastructure providers, hardware vendors, and cryptographic building blocks. Want to ace your presentation in front of a live audience Our Technical Stack For Evaluating Confidential Secure Computing Framework Information Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide depicts the technical stack while assessing confidential computing solutions. The stack divides these solutions into four levels, including application software vendors, infrastructure providers, hardware vendors, and cryptographic building blocks.

Internet Security Challenges And Solutions In Banking Industry Download Pdf
This slide showcase cyber security challenges in digital banking and tactics to mitigate data risk. It include challenges like malware, spoofing, phishing, third part service.Showcasing this set of slides titled Internet Security Challenges And Solutions In Banking Industry Download Pdf The topics addressed in these templates are Installing Intergraded, Introducing Firewall, Learning Algorisms All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcase cyber security challenges in digital banking and tactics to mitigate data risk. It include challenges like malware, spoofing, phishing, third part service.

Global Data Security Industry Report Key Considerations Assumptions Of Cybersecurity Industry Report IR SS V
The slide represents key considerations and limitations while building the cybersecurity industry report. The purpose of this slide is to provide framework and context for analysis and projections in addition to acknowledging uncertainties and potential risks in the future. Make sure to capture your audiences attention in your business displays with our gratis customizable Global Data Security Industry Report Key Considerations Assumptions Of Cybersecurity Industry Report IR SS V. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. The slide represents key considerations and limitations while building the cybersecurity industry report. The purpose of this slide is to provide framework and context for analysis and projections in addition to acknowledging uncertainties and potential risks in the future.
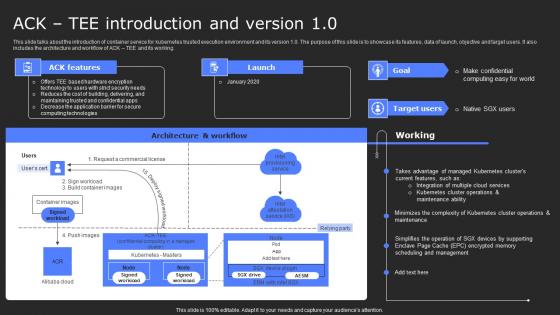
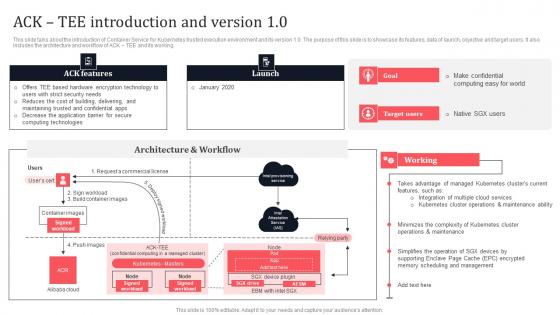
ACK Tee Introduction And Version 10 Secure Computing Framework Slides Pdf
This slide talks about the introduction of container service for kubernetes trusted execution environment and its version 1.0. The purpose of this slide is to showcase its features, data of launch, objective and target users. It also includes the architecture and workflow of ACK TEE and its working. Find a pre-designed and impeccable ACK Tee Introduction And Version 10 Secure Computing Framework Slides Pdf. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide talks about the introduction of container service for kubernetes trusted execution environment and its version 1.0. The purpose of this slide is to showcase its features, data of launch, objective and target users. It also includes the architecture and workflow of ACK TEE and its working.
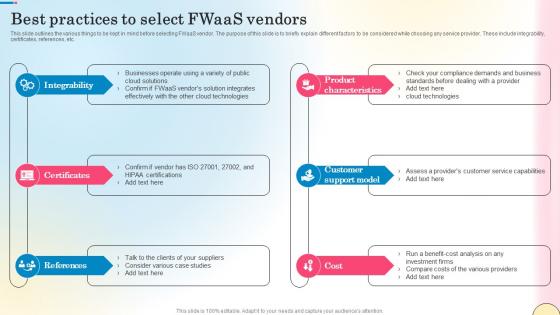
Best Practices To Select Fwaas Vendors Network Security Ideas Pdf
This slide outlines the various things to be kept in mind before selecting FWaaS vendor. The purpose of this slide is to briefly explain different factors to be considered while choosing any service provider. These include integrability, certificates, references, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Best Practices To Select Fwaas Vendors Network Security Ideas Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Best Practices To Select Fwaas Vendors Network Security Ideas Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide outlines the various things to be kept in mind before selecting FWaaS vendor. The purpose of this slide is to briefly explain different factors to be considered while choosing any service provider. These include integrability, certificates, references, etc.

Process Of Using Intel Sgx Based Trusted Applications Secure Computing Framework Sample Pdf
This slide outlines the process of using intel sgx-based trusted applications. The purpose of this slide is to demonstrate the procedure of utilizing intel sgx-based trusted applications. The main components include applying for a key, installing the environment, developing, computing and building, and executing. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Process Of Using Intel Sgx Based Trusted Applications Secure Computing Framework Sample Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Process Of Using Intel Sgx Based Trusted Applications Secure Computing Framework Sample Pdf today and make your presentation stand out from the rest This slide outlines the process of using intel sgx-based trusted applications. The purpose of this slide is to demonstrate the procedure of utilizing intel sgx-based trusted applications. The main components include applying for a key, installing the environment, developing, computing and building, and executing.
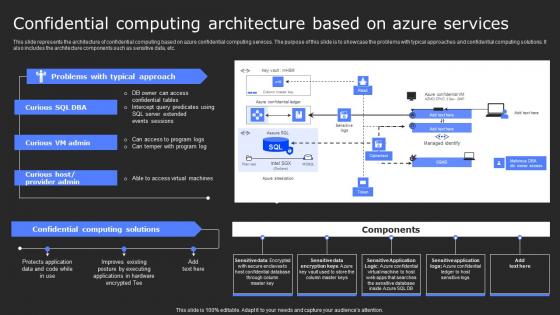
Confidential Computing Architecture Based On Secure Computing Framework Elements Pdf
This slide represents the architecture of confidential computing based on azure confidential computing services. The purpose of this slide is to showcase the problems with typical approaches and confidential computing solutions. It also includes the architecture components such as sensitive data, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Confidential Computing Architecture Based On Secure Computing Framework Elements Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Confidential Computing Architecture Based On Secure Computing Framework Elements Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide represents the architecture of confidential computing based on azure confidential computing services. The purpose of this slide is to showcase the problems with typical approaches and confidential computing solutions. It also includes the architecture components such as sensitive data, etc.
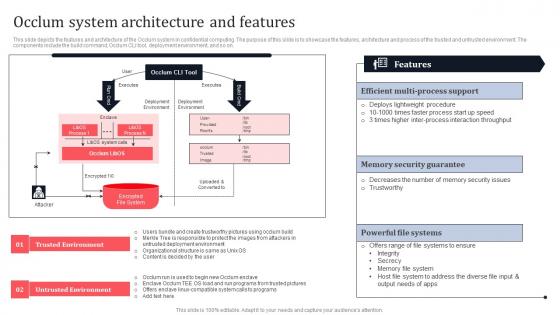
Occlum System Architecture And Features Secure Multi Party Slides Pdf
This slide depicts the features and architecture of the Occlum system in confidential computing. The purpose of this slide is to showcase the features, architecture and process of the trusted and untrusted environment. The components include the build command, Occlum CLI tool, deployment environment, and so on. Want to ace your presentation in front of a live audience Our Occlum System Architecture And Features Secure Multi Party Slides Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide depicts the features and architecture of the Occlum system in confidential computing. The purpose of this slide is to showcase the features, architecture and process of the trusted and untrusted environment. The components include the build command, Occlum CLI tool, deployment environment, and so on.
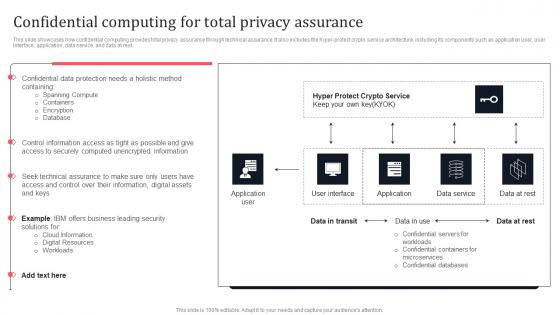
Confidential Computing For Total Privacy Assurance Secure Multi Party Brochure Pdf
This slide showcases how confidential computing provides total privacy assurance through technical assurance. It also includes the hyper-protect crypto service architecture, including its components such as application user, user interface, application, data service, and data at rest. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Confidential Computing For Total Privacy Assurance Secure Multi Party Brochure Pdf template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Confidential Computing For Total Privacy Assurance Secure Multi Party Brochure Pdf that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers. This slide showcases how confidential computing provides total privacy assurance through technical assurance. It also includes the hyper-protect crypto service architecture, including its components such as application user, user interface, application, data service, and data at rest.
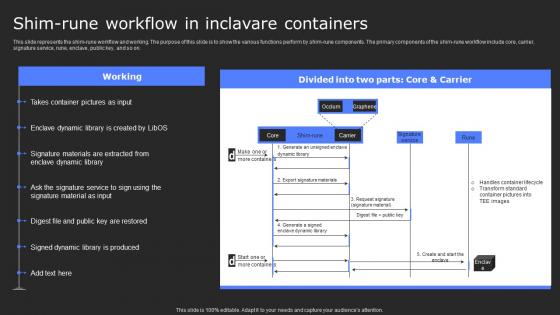
Shim Rune Workflow In Inclavare Containers Secure Computing Framework Infographics Pdf
This slide represents the shim-rune workflow and working. The purpose of this slide is to show the various functions perform by shim-rune components. The primary components of the shim-rune workflow include core, carrier, signature service, rune, enclave, public key, and so on. Create an editable Shim Rune Workflow In Inclavare Containers Secure Computing Framework Infographics Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Shim Rune Workflow In Inclavare Containers Secure Computing Framework Infographics Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide represents the shim-rune workflow and working. The purpose of this slide is to show the various functions perform by shim-rune components. The primary components of the shim-rune workflow include core, carrier, signature service, rune, enclave, public key, and so on.
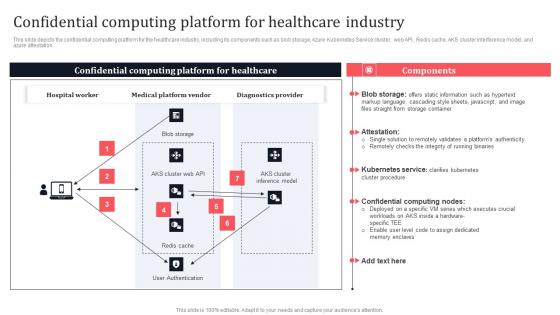
Confidential Computing Platform For Healthcare Industry Secure Multi Party Information Pdf
This slide depicts the confidential computing platform for the healthcare industry, including its components such as blob storage, Azure Kubernetes Service cluster, web API, Redis cache, AKS cluster interference model, and azure attestation. This modern and well-arranged Confidential Computing Platform For Healthcare Industry Secure Multi Party Information Pdf provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide depicts the confidential computing platform for the healthcare industry, including its components such as blob storage, Azure Kubernetes Service cluster, web API, Redis cache, AKS cluster interference model, and azure attestation.
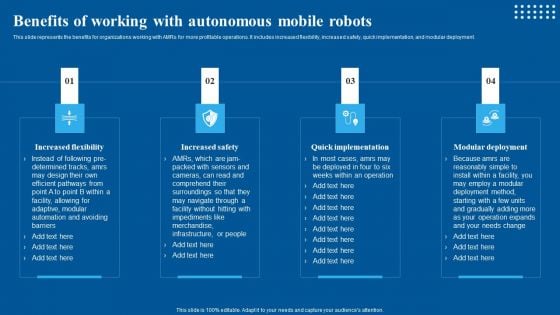
Benefits Of Working With Autonomous Mobile Robots Designs PDF
This slide represents the benefits for organizations working with AMRs for more profitable operations. It includes increased flexibility, increased safety, quick implementation, and modular deployment. This Benefits Of Working With Autonomous Mobile Robots Designs PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

Comparison Between Fwaas And Cloud Firewalls Network Security Portrait Pdf
This slide illustrates the concept of cloud firewalls and Firewall-as-a-Service. The purpose of this slide is to explain if cloud firewalls, and Firewall-as-Service are same or not. This slide also talks about the correlation of both the terms with each other. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Comparison Between Fwaas And Cloud Firewalls Network Security Portrait Pdf and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide illustrates the concept of cloud firewalls and Firewall-as-a-Service. The purpose of this slide is to explain if cloud firewalls, and Firewall-as-Service are same or not. This slide also talks about the correlation of both the terms with each other.
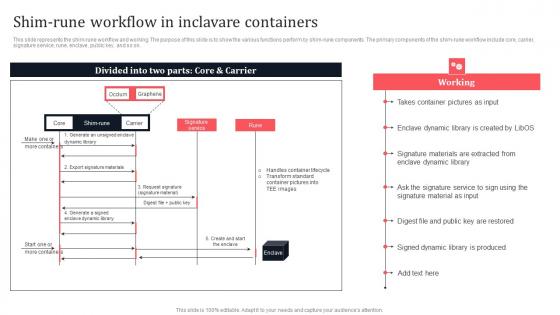
Shim Rune Workflow In Inclavare Containers Secure Multi Party Ideas Pdf
This slide represents the shim-rune workflow and working. The purpose of this slide is to show the various functions perform by shim-rune components. The primary components of the shim-rune workflow include core, carrier, signature service, rune, enclave, public key, and so on. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Shim Rune Workflow In Inclavare Containers Secure Multi Party Ideas Pdf can be your best option for delivering a presentation. Represent everything in detail using Shim Rune Workflow In Inclavare Containers Secure Multi Party Ideas Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide represents the shim-rune workflow and working. The purpose of this slide is to show the various functions perform by shim-rune components. The primary components of the shim-rune workflow include core, carrier, signature service, rune, enclave, public key, and so on.
Ack Tee 2 0 Architecture And Workflow Secure Multi Party Mockup Pdf
This slide outlines the architecture of Container Service for Kubernetes trusted execution environment version 2. The purpose of this slide is to demonstrate the features, date of launch and target users. It also covers the architecture and working of ACK TEE 2.0. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Ack Tee 2 0 Architecture And Workflow Secure Multi Party Mockup Pdf to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Ack Tee 2 0 Architecture And Workflow Secure Multi Party Mockup Pdf This slide outlines the architecture of Container Service for Kubernetes trusted execution environment version 2. The purpose of this slide is to demonstrate the features, date of launch and target users. It also covers the architecture and working of ACK TEE 2.0.
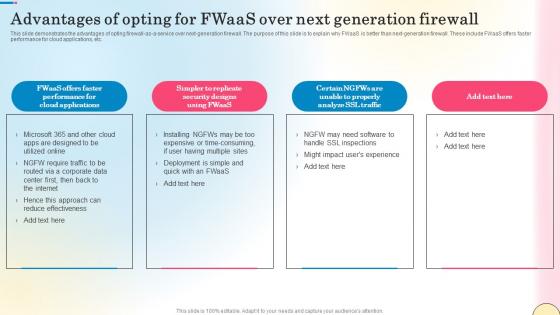
Advantages Of Opting For Fwaas Over Next Network Security Diagrams Pdf
This slide demonstrates the advantages of opting firewall-as-a-service over next-generation firewall. The purpose of this slide is to explain why FWaaS is better than next-generation firewall. These include FWaaS offers faster performance for cloud applications, etc. Create an editable Advantages Of Opting For Fwaas Over Next Network Security Diagrams Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Advantages Of Opting For Fwaas Over Next Network Security Diagrams Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide demonstrates the advantages of opting firewall-as-a-service over next-generation firewall. The purpose of this slide is to explain why FWaaS is better than next-generation firewall. These include FWaaS offers faster performance for cloud applications, etc.
Ack Tee Introduction And Version 1 0 Secure Multi Party Slides Pdf
This slide talks about the introduction of Container Service for Kubernetes trusted execution environment and its version 1.0. The purpose of this slide is to showcase its features, data of launch, objective and target users. It also includes the architecture and workflow of ACK TEE and its working. This Ack Tee Introduction And Version 1 0 Secure Multi Party Slides Pdf from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide talks about the introduction of Container Service for Kubernetes trusted execution environment and its version 1.0. The purpose of this slide is to showcase its features, data of launch, objective and target users. It also includes the architecture and workflow of ACK TEE and its working.
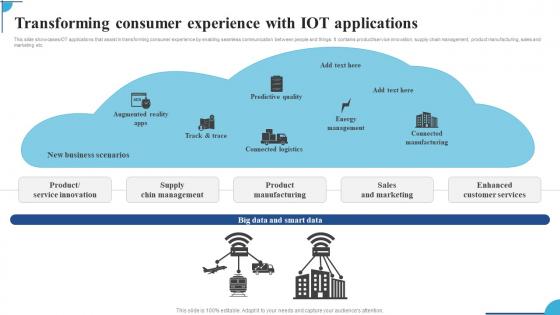
Transforming Consumer Experience With IOT Applications Ppt Slides Pictures Pdf
This slide showcases IOT applications that assist in transforming consumer experience by enabling seamless communication between people and things. It contains product service innovation,supply chain management,product manufacturing,sales and marketing etc. Showcasing this set of slides titled Transforming Consumer Experience With IOT Applications Ppt Slides Pictures Pdf. The topics addressed in these templates are Supply Chin Management,Product Manufacturing,Sales And Marketing. All the content presented in this PPT design is completely editable. Download it and make adjustments in color,background,font etc. as per your unique business setting. This slide showcases IOT applications that assist in transforming consumer experience by enabling seamless communication between people and things. It contains product service innovation,supply chain management,product manufacturing,sales and marketing etc.
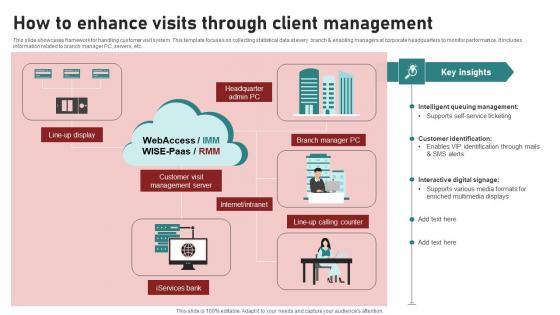
How To Enhance Visits Through Client Management Ppt Sample pdf
This slide showcases framework for handling customer visit system. This template focuses on collecting statistical data at every branch and enabling managers at corporate headquarters to monitor performance. It includes information related to branch manager PC, servers, etc. Showcasing this set of slides titled How To Enhance Visits Through Client Management Ppt Sample pdf. The topics addressed in these templates are Branch Manager PC, Services Bank, Customer Visit Management. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcases framework for handling customer visit system. This template focuses on collecting statistical data at every branch and enabling managers at corporate headquarters to monitor performance. It includes information related to branch manager PC, servers, etc.

Cyber Security Strategic Agenda Checklist Mockup Pdf
This slide represents action plan of checklist of cyber security. It further includes tasks such as determine potential areas like challenges regarding cyber security and security loopholes, etc and their status. Showcasing this set of slides titled Cyber Security Strategic Agenda Checklist Mockup Pdf. The topics addressed in these templates are Cyber Security, Strategic Agenda Checklist. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide represents action plan of checklist of cyber security. It further includes tasks such as determine potential areas like challenges regarding cyber security and security loopholes, etc and their status.

Measurable Benefits Of 5S Lean Production Strategies Manufacturing Methodology Template PDF
This slide defines the advantages of 5s lean in manufacturing methodology that can be measured. It includes information related to increased productivity, improved safety, reduce wastage and workers commitment. Presenting Measurable Benefits Of 5S Lean Production Strategies Manufacturing Methodology Template PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Increased Productivity, Improved Safety, Reduction Waste. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
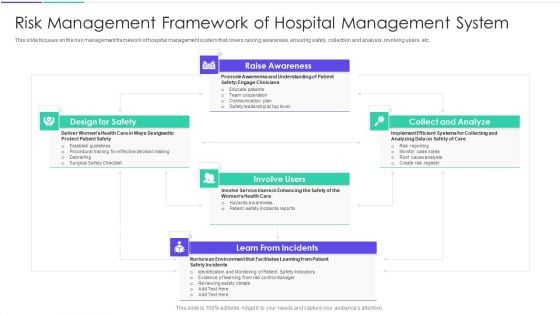
Medical Inventory Management System Risk Management Framework Of Hospital Management System Portrait PDF
This slide focuses on the risk management framework of hospital management system that covers raising awareness, ensuring safety, collection and analysis, involving users, etc.Presenting medical inventory management system risk management framework of hospital management system portrait pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like design for safety, raise awareness, learn from incidents In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
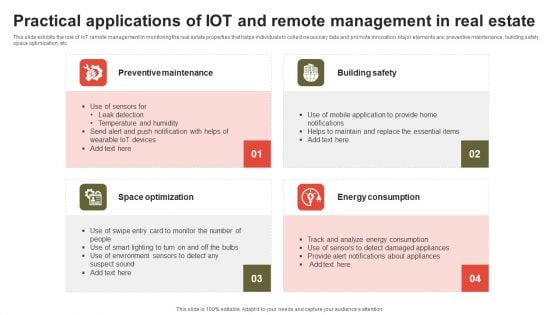
Practical Applications Of IOT And Remote Management In Real Estate Rules PDF
This slide exhibits the role of IoT remote management in monitoring the real estate properties that helps individuals to collect necessary data and promote innovation. Major elements are preventive maintenance, building safety, space optimization, etc. Presenting Practical Applications Of IOT And Remote Management In Real Estate Rules PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Preventive Maintenance, Building Safety, Space Optimization . This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
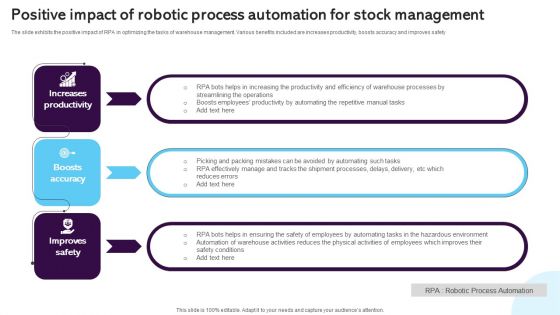
Positive Impact Of Robotic Process Automation For Stock Management Diagrams PDF
The slide exhibits the positive impact of RPA in optimizing the tasks of warehouse management. Various benefits included are increases productivity, boosts accuracy and improves safety. Presenting Positive Impact Of Robotic Process Automation For Stock Management Diagrams PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Increases Productivity, Boosts Accuracy, Improves Safety. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
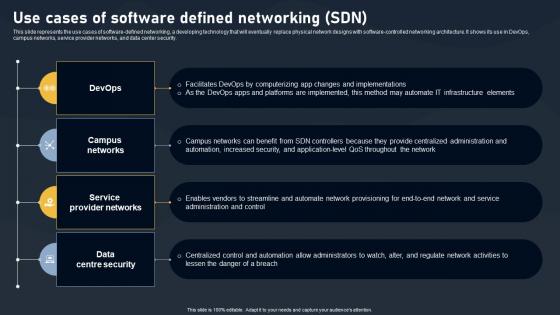
Use Cases Of Software Defined Networking SDN Building Blocks Summary Pdf
This slide represents the use cases of software-defined networking, a developing technology that will eventually replace physical network designs with software-controlled networking architecture. It shows its use in DevOps, campus networks, service provider networks, and data center security.Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Use Cases Of Software Defined Networking SDN Building Blocks Summary Pdf was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Use Cases Of Software Defined Networking SDN Building Blocks Summary Pdf. This slide represents the use cases of software defined networking, a developing technology that will eventually replace physical network designs with software controlled networking architecture. It shows its use in DevOps, campus networks, service provider networks, and data center security.
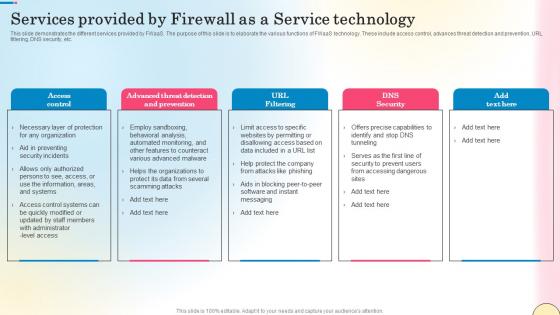
Services Provided By Firewall As A Service Technology Network Security Infographics Pdf
This slide demonstrates the different services provided by FWaaS. The purpose of this slide is to elaborate the various functions of FWaaS technology. These include access control, advances threat detection and prevention, URL filtering, DNS security, etc. There are so many reasons you need a Services Provided By Firewall As A Service Technology Network Security Infographics Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide demonstrates the different services provided by FWaaS. The purpose of this slide is to elaborate the various functions of FWaaS technology. These include access control, advances threat detection and prevention, URL filtering, DNS security, etc.
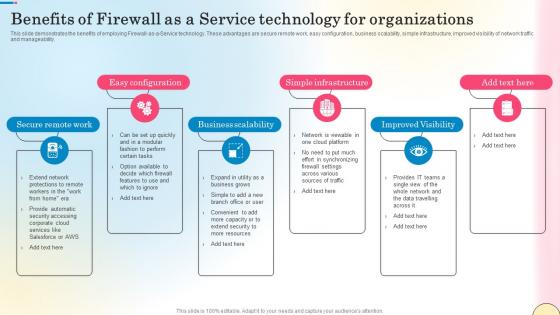
Benefits Of Firewall As A Service Technology For Network Security Inspiration Pdf
This slide demonstrates the benefits of employing Firewall-as-a-Service technology. These advantages are secure remote work, easy configuration, business scalability, simple infrastructure, improved visibility of network traffic and manageability. There are so many reasons you need a Benefits Of Firewall As A Service Technology For Network Security Inspiration Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide demonstrates the benefits of employing Firewall-as-a-Service technology. These advantages are secure remote work, easy configuration, business scalability, simple infrastructure, improved visibility of network traffic and manageability.
Confidential Computing Architecture Based On Azure Services Secure Multi Party Icons Pdf
This slide represents the architecture of confidential computing based on Azure confidential computing services. The purpose of this slide is to showcase the problems with typical approaches and confidential computing solutions. It also includes the architecture components such as sensitive data, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Confidential Computing Architecture Based On Azure Services Secure Multi Party Icons Pdf With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Confidential Computing Architecture Based On Azure Services Secure Multi Party Icons Pdf today and make your presentation stand out from the rest. This slide represents the architecture of confidential computing based on Azure confidential computing services. The purpose of this slide is to showcase the problems with typical approaches and confidential computing solutions. It also includes the architecture components such as sensitive data, etc.
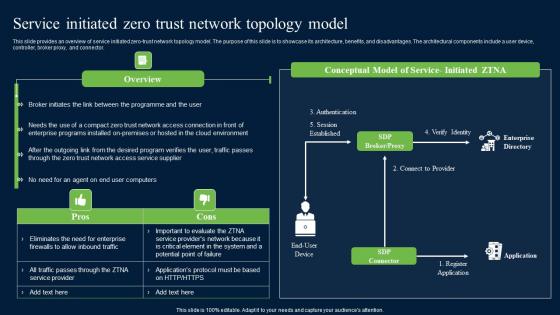
Service Initiated Zero Trust Network Topology Model Zero Trust Network Security Guidelines Pdf
This slide provides an overview of service initiated zero-trust network topology model. The purpose of this slide is to showcase its architecture, benefits, and disadvantages. The architectural components include a user device, controller, broker proxy, and connector. Find a pre-designed and impeccable Service Initiated Zero Trust Network Topology Model Zero Trust Network Security Guidelines Pdf. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide provides an overview of service initiated zero-trust network topology model. The purpose of this slide is to showcase its architecture, benefits, and disadvantages. The architectural components include a user device, controller, broker proxy, and connector.
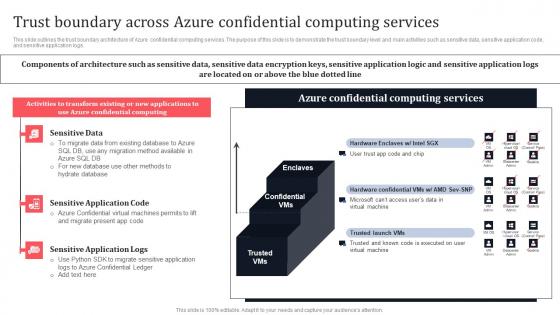
Trust Boundary Across Azure Confidential Computing Services Secure Multi Party Ideas Pdf
This slide outlines the trust boundary architecture of Azure confidential computing services. The purpose of this slide is to demonstrate the trust boundary level and main activities such as sensitive data, sensitive application code, and sensitive application logs. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Trust Boundary Across Azure Confidential Computing Services Secure Multi Party Ideas Pdf and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide outlines the trust boundary architecture of Azure confidential computing services. The purpose of this slide is to demonstrate the trust boundary level and main activities such as sensitive data, sensitive application code, and sensitive application logs.
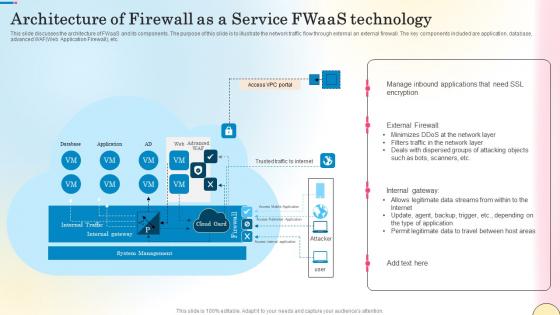
Architecture Of Firewall As A Service Fwaas Technology Network Security Themes Pdf
This slide discusses the architecture of FWaaS and its components. The purpose of this slide is to illustrate the network traffic flow through external an external firewall. The key components included are application, database, advanced WAFWeb Application Firewall, etc. Want to ace your presentation in front of a live audience Our Architecture Of Firewall As A Service Fwaas Technology Network Security Themes Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide discusses the architecture of FWaaS and its components. The purpose of this slide is to illustrate the network traffic flow through external an external firewall. The key components included are application, database, advanced WAFWeb Application Firewall, etc.

Pillars Of Cloud Security Identity Security Diagrams PDF
This slide depicts the identity security pillar of cloud security. It also shows how it could be beneficial to protect data from loss. Deliver an awe inspiring pitch with this creative Pillars Of Cloud Security Identity Security Diagrams PDF bundle. Topics like Service Permissions, Application, Required can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
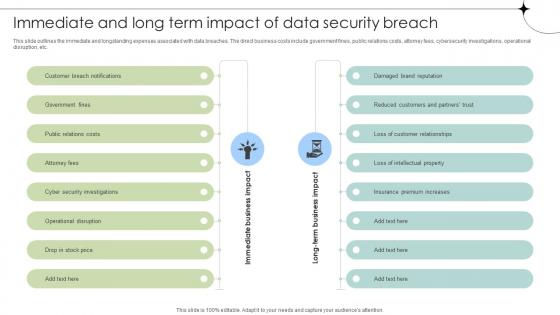
Immediate And Long Term Impact Of Data Security Breach Data Fortification Strengthening Defenses
This slide outlines the immediate and longstanding expenses associated with data breaches. The direct business costs include government fines, public relations costs, attorney fees, cybersecurity investigations, operational disruption, etc. Are you searching for a Immediate And Long Term Impact Of Data Security Breach Data Fortification Strengthening Defenses that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Immediate And Long Term Impact Of Data Security Breach Data Fortification Strengthening Defenses from Slidegeeks today. This slide outlines the immediate and longstanding expenses associated with data breaches. The direct business costs include government fines, public relations costs, attorney fees, cybersecurity investigations, operational disruption, etc.

Security Agency Business Profile Corporate And Industrial Security Services Information PDF
This slide highlights the industrial and corporate security services by manpower security company which includes administer electronic access control, respond to alarms, visitor pass management and patrol inside the factory. Deliver and pitch your topic in the best possible manner with this Security Agency Business Profile Corporate And Industrial Security Services Information PDF. Use them to share invaluable insights on Corporate Security, Industrial Security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
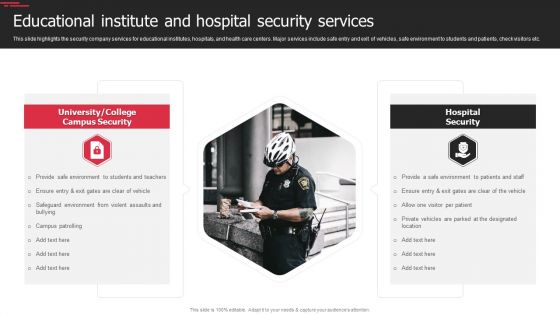
Security Agency Business Profile Educational Institute And Hospital Security Services Guidelines PDF
This slide highlights the security company services for educational institutes, hospitals, and health care centers. Major services include safe entry and exit of vehicles, safe environment to students and patients, check visitors etc. Deliver and pitch your topic in the best possible manner with this Security Agency Business Profile Educational Institute And Hospital Security Services Guidelines PDF. Use them to share invaluable insights on Campus Security, Hospital Security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
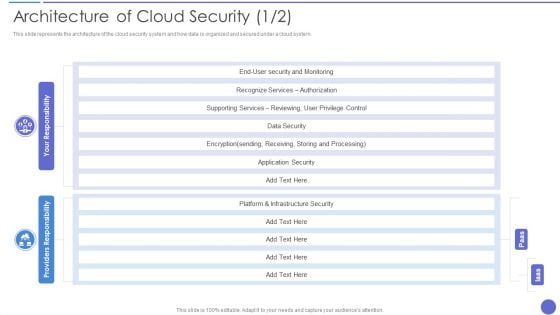
Architecture Of Cloud Security Ideas PDF
This slide represents the architecture of the cloud security system and how data is organized and secured under a cloud system. Deliver an awe inspiring pitch with this creative Architecture Of Cloud Security Ideas PDF bundle. Topics like Recognize Services, Supporting Services, Infrastructure Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Home Security Company Services And Contact Information Structure PDF
This slide showcases services provided to insured against losses from insurance company. The services provided are interior and exterior renovation and remodeling, general contracting and new home construction. Showcasing this set of slides titled Home Security Company Services And Contact Information Structure PDF. The topics addressed in these templates are Reimbursement, Contract For Protection, Representing Services Provided. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
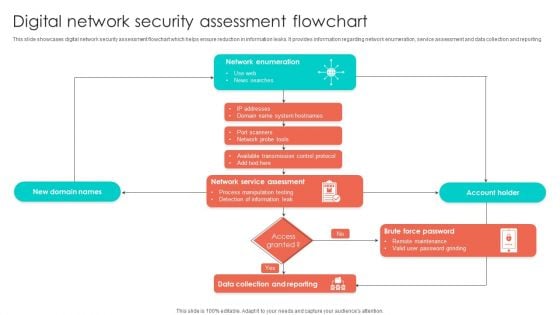
Digital Network Security Assessment Flowchart Structure PDF
This slide showcases digital network security assessment flowchart which helps ensure reduction in information leaks. It provides information regarding network enumeration, service assessment and data collection and reporting. Showcasing this set of slides titled Digital Network Security Assessment Flowchart Structure PDF. The topics addressed in these templates are Account Holder, Information Leak, Network Service Assessment. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

What Is Cloud Security Guidelines PDF
This slide depicts the meaning of cloud security, and parties involve in a cloud security framework, such as customers and service providers. Deliver an awe inspiring pitch with this creative What Is Cloud Security Guidelines PDF bundle. Topics like Computing Systems, Protocols, Cloud Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Exit Strategy Voice Assistance Security Platform Investor Funding Presentation Structure Pdf
The slide provides most profitable feasible ways for investors to exit from their investment in the company. It consists of strategies like IPO Initial Public Offering and partnership exit. Welcome to our selection of the Exit Strategy Voice Assistance Security Platform Investor Funding Presentation Structure Pdf. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today The slide provides most profitable feasible ways for investors to exit from their investment in the company. It consists of strategies like IPO Initial Public Offering and partnership exit.

The Ultimate Guide To KPMG Business Canvas Model Value Proposition Strategy SS V
This slide covers techniques to secure customers confidential data through several cyber security strategies. The purpose for this template is to provide an overview on important elements This slide covers key elements of value proposition under KPMG canvas business model. The purpose of this template is to provide an overview on elements such as industry expertise, global reach, integrated services, technology enabled solutions, risk management expertise, etc. contributing towards executing KPMG operations effectively of top techniques deployed by the company . It includes strategies such as people, process, data and technology and regulatory. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. The Ultimate Guide To KPMG Business Canvas Model Value Proposition Strategy SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide covers techniques to secure customers confidential data through several cyber security strategies. The purpose for this template is to provide an overview on important elements This slide covers key elements of value proposition under KPMG canvas business model. The purpose of this template is to provide an overview on elements such as industry expertise, global reach, integrated services, technology enabled solutions, risk management expertise, etc. contributing towards executing KPMG operations effectively of top techniques deployed by the company . It includes strategies such as people, process, data and technology and regulatory.

Key Benefits Of Using Secure Web Gateway Web Threat Protection System
This slide outlines the advantages of implementing Secure Web Gateway into organizations. The purpose of this slide to explain various benefits of SWG such as improved security, increased productivity, reduced risk of data loss, compliance, etc. Welcome to our selection of the Key Benefits Of Using Secure Web Gateway Web Threat Protection System. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. This slide outlines the advantages of implementing Secure Web Gateway into organizations. The purpose of this slide to explain various benefits of SWG such as improved security, increased productivity, reduced risk of data loss, compliance, etc.
Icons Slide Building Security Awareness Among Workforce To Minimize Cybersecurity Threats Elements PDF
Introducing our well designed Icons Slide Building Security Awareness Among Workforce To Minimize Cybersecurity Threats Elements PDF set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.
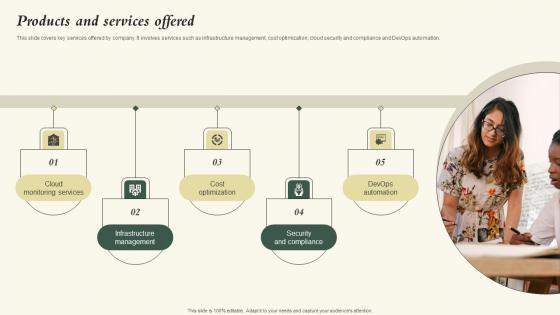
Products And Services Offered Nubity Capital Funding Pitch Deck Guidelines Pdf
This slide covers key services offered by company. It involves services such as infrastructure management, cost optimization, cloud security and compliance and DevOps automation. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Products And Services Offered Nubity Capital Funding Pitch Deck Guidelines Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide covers key services offered by company. It involves services such as infrastructure management, cost optimization, cloud security and compliance and DevOps automation.
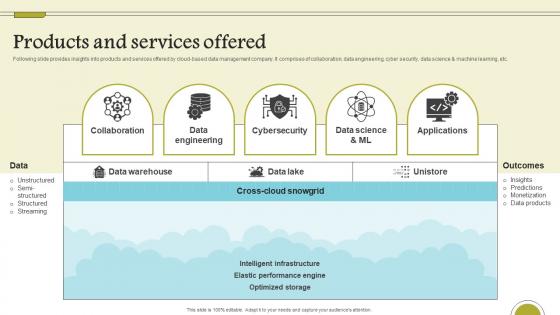
Products And Services Offered Cloud Data Computing Company Fund Raising Introduction Pdf
Following slide provides insights into products and services offered by cloud-based data management company. It comprises of collaboration, data engineering, cyber security, data science and machine learning, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Products And Services Offered Cloud Data Computing Company Fund Raising Introduction Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. Following slide provides insights into products and services offered by cloud-based data management company. It comprises of collaboration, data engineering, cyber security, data science and machine learning, etc.
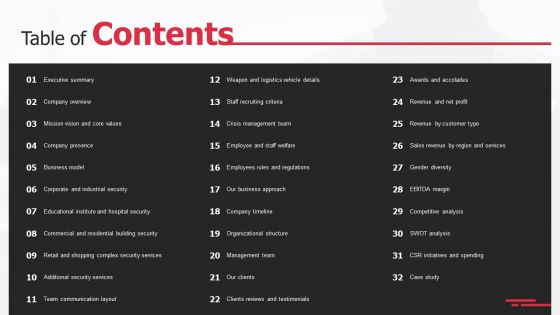
Security Agency Business Profile Table Of Contents Rules PDF
Deliver an awe inspiring pitch with this creative Security Agency Business Profile Table Of Contents Rules PDF bundle. Topics like Executive Summary, Business Model, Additional Security Services can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Methods To Overcome Cloud Data Security Using Cryptography Infographics Pdf
The purpose of this slide is to elaborate some ways that cloud cryptography can help overcome cloud data security challenges. The key points mentioned in this slide are confidentiality, integrity, access control and key management. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Methods To Overcome Cloud Data Security Using Cryptography Infographics Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Methods To Overcome Cloud Data Security Using Cryptography Infographics Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today The purpose of this slide is to elaborate some ways that cloud cryptography can help overcome cloud data security challenges. The key points mentioned in this slide are confidentiality, integrity, access control and key management.
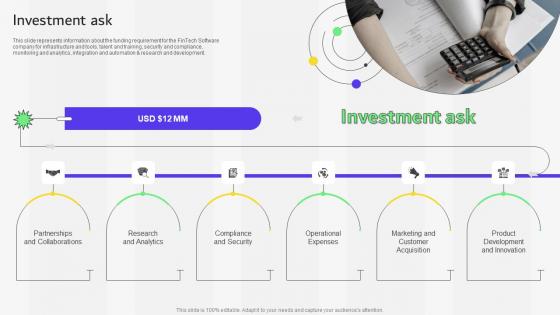
Investment Ask Financial Services Provider Investor Funding Elevator Pitch Deck
This slide represents information about the funding requirement for the FinTech Software company for infrastructure and tools, talent and training, security and compliance, monitoring and analytics, integration and automation and research and development. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Investment Ask Financial Services Provider Investor Funding Elevator Pitch Deck can be your best option for delivering a presentation. Represent everything in detail using Investment Ask Financial Services Provider Investor Funding Elevator Pitch Deck and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide represents information about the funding requirement for the FinTech Software company for infrastructure and tools, talent and training, security and compliance, monitoring and analytics, integration and automation and research and development.
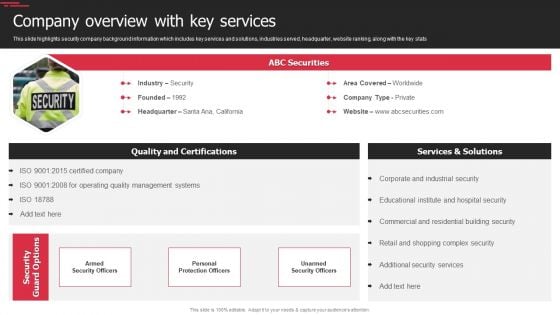
Security Agency Business Profile Company Overview With Key Services Inspiration PDF
This slide highlights security company background information which includes key services and solutions, industries served, headquarter, website ranking, along with the key stats. Deliver an awe inspiring pitch with this creative Security Agency Business Profile Company Overview With Key Services Inspiration PDF bundle. Topics like Quality Management Systems, Industrial Security, Security Services can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.


 Continue with Email
Continue with Email

 Home
Home


































