Safety Plan

Phase 3 Respond To Cloud Protection Issues Cloud Computing Security IT Ppt Gallery Rules PDF
This slide represents phase 3 of cloud security, such as respond to cloud protection issues. It includes an advanced authentication process, manages cloud access standards when new services come up, and eliminates malware from cloud services. Deliver and pitch your topic in the best possible manner with this phase 3 respond to cloud protection issues cloud computing security it ppt gallery rules pdf. Use them to share invaluable insights on authentication process, service, web policies and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
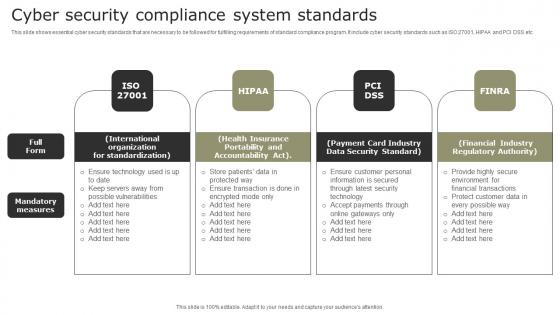
Cyber Security Compliance System Standards Demonstration Pdf
This slide shows essential cyber security standards that are necessary to be followed for fulfilling requirements of standard compliance program. It include cyber security standards such as ISO 27001, HIPAA and PCI DSS etc. Showcasing this set of slides titled Cyber Security Compliance System Standards Demonstration Pdf. The topics addressed in these templates are International Organization, Health Insurance, Payment Card Industry. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide shows essential cyber security standards that are necessary to be followed for fulfilling requirements of standard compliance program. It include cyber security standards such as ISO 27001, HIPAA and PCI DSS etc.
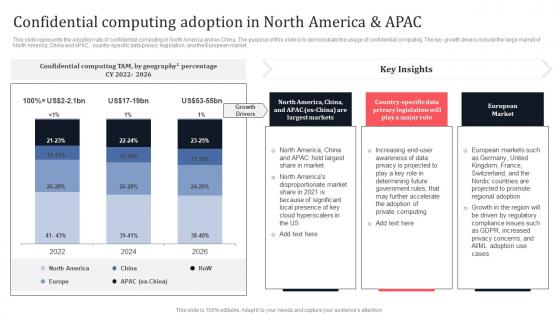
Confidential Computing Adoption In North America And APAC Secure Multi Party Brochure Pdf
This slide represents the adoption rate of confidential computing in North America and ex-China. The purpose of this slide is to demonstrate the usage of confidential computing. The key growth drivers include the large market of North America, China and APAC, country-specific data privacy legislation, and the European market. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Confidential Computing Adoption In North America And APAC Secure Multi Party Brochure Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide represents the adoption rate of confidential computing in North America and ex-China. The purpose of this slide is to demonstrate the usage of confidential computing. The key growth drivers include the large market of North America, China and APAC, country-specific data privacy legislation, and the European market.
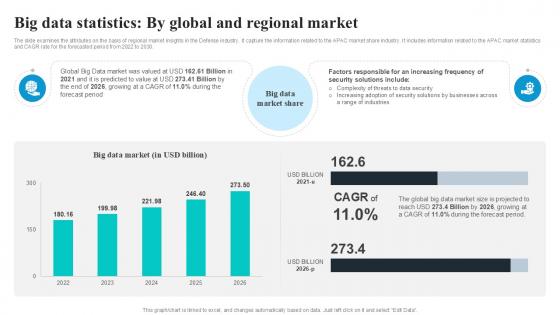
Big Data Statistics By Global Security Industry PPT Sample IR SS V
The slide examines the attributes on the basis of regional market insights in the Defense industry. It capture the information related to the APAC market share industry. It includes information related to the APAC market statistics and CAGR rate for the forecasted period from 2022 to 2030. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Big Data Statistics By Global Security Industry PPT Sample IR SS V for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. The slide examines the attributes on the basis of regional market insights in the Defense industry. It capture the information related to the APAC market share industry. It includes information related to the APAC market statistics and CAGR rate for the forecasted period from 2022 to 2030.
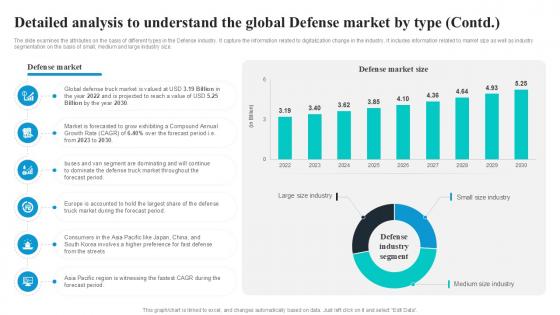
Detailed Analysis To Understand The Global Global Security Industry PPT PowerPoint IR SS V
The slide examines the attributes on the basis of different types in the Defense industry. It capture the information related to digitalization change in the industry. It includes information related to market size as well as industry segmentation on the basis of small, medium and large industry size. Slidegeeks is here to make your presentations a breeze with Detailed Analysis To Understand The Global Global Security Industry PPT PowerPoint IR SS V With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first The slide examines the attributes on the basis of different types in the Defense industry. It capture the information related to digitalization change in the industry. It includes information related to market size as well as industry segmentation on the basis of small, medium and large industry size.

Comparative Analysis Of Top Content Management Developing And Creating Digital Content Strategy SS V
The following slide highlights comparison of multiple content management software to select the best alternative. It includes elements such as automatic notification, easy navigations, ensuring privacy, security, offering customization etc. There are so many reasons you need a Comparative Analysis Of Top Content Management Developing And Creating Digital Content Strategy SS V. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. The following slide highlights comparison of multiple content management software to select the best alternative. It includes elements such as automatic notification, easy navigations, ensuring privacy, security, offering customization etc.
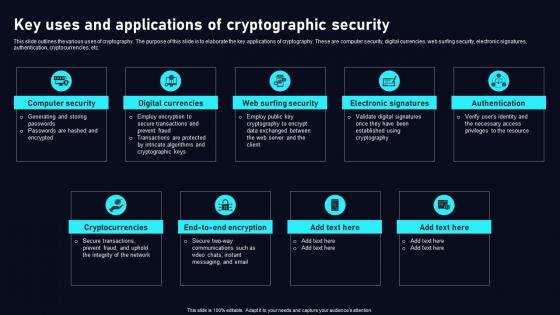
Key Uses And Applications Cryptographic Cloud Data Security Using Cryptography Sample Pdf
This slide outlines the various uses of cryptography. The purpose of this slide is to elaborate the key applications of cryptography. These are computer security, digital currencies, web surfing security, electronic signatures, authentication, cryptocurrencies, etc. Want to ace your presentation in front of a live audience Our Key Uses And Applications Cryptographic Cloud Data Security Using Cryptography Sample Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use. This slide outlines the various uses of cryptography. The purpose of this slide is to elaborate the key applications of cryptography. These are computer security, digital currencies, web surfing security, electronic signatures, authentication, cryptocurrencies, etc.

Security Training Program Frameworks Ppt Outline Layout Ideas PDF
This slide outlines the criteria, describes possible positions that could be subject to instruction, instruction information sources, and metrics to assess training success in those control areas. Deliver and pitch your topic in the best possible manner with this security training program frameworks ppt outline layout ideas pdf. Use them to share invaluable insights on requirements, metrics, systems security, materials and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Best Practices For Cloud Data Security Using Cryptography Diagrams Pdf
This slide talks about the steps to be taken for successful cloud cryptography management. The best practices involved are analyse security needs for cloud implementation, take regular backup of cloud data, main transparency and control, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Best Practices For Cloud Data Security Using Cryptography Diagrams Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Best Practices For Cloud Data Security Using Cryptography Diagrams Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide talks about the steps to be taken for successful cloud cryptography management. The best practices involved are analyse security needs for cloud implementation, take regular backup of cloud data, main transparency and control, etc.
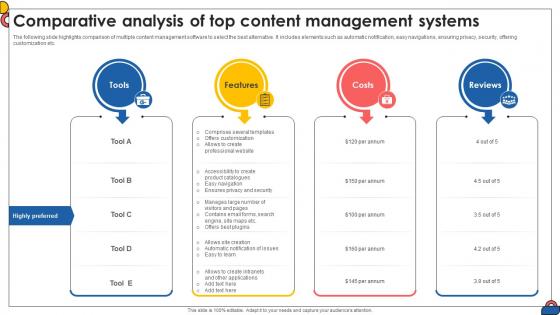
Comparative Analysis Of Top Content Management Comprehensive Guide To Implement Strategy SS V
The following slide highlights comparison of multiple content management software to select the best alternative. It includes elements such as automatic notification, easy navigations, ensuring privacy, security, offering customization etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Comparative Analysis Of Top Content Management Comprehensive Guide To Implement Strategy SS V a try. Our experts have put a lot of knowledge and effort into creating this impeccable Comparative Analysis Of Top Content Management Comprehensive Guide To Implement Strategy SS V. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today The following slide highlights comparison of multiple content management software to select the best alternative. It includes elements such as automatic notification, easy navigations, ensuring privacy, security, offering customization etc.
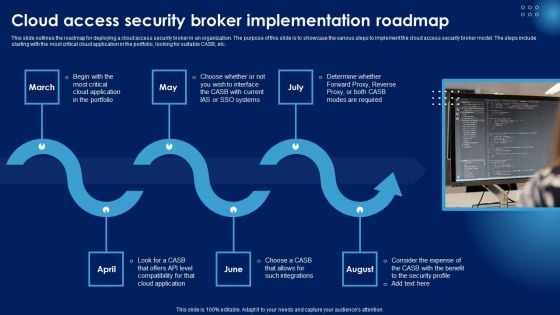
Cloud Access Security Broker Implementation Roadmap Ppt PowerPoint Presentation Diagram Lists PDF
This slide outlines the roadmap for deploying a cloud access security broker in an organization. The purpose of this slide is to showcase the various steps to implement the cloud access security broker model. The steps include starting with the most critical cloud application in the portfolio, looking for suitable CASB, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Cloud Access Security Broker Implementation Roadmap Ppt PowerPoint Presentation Diagram Lists PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Secure Internet Browser Computer PowerPoint Templates And PowerPoint Backgrounds 0811
Microsoft PowerPoint Template and Background with transparent internet browser with a lock padlock intersecting it List your core competencies with our Secure Internet Browser Computer PowerPoint Templates And PowerPoint Backgrounds 0811. They will make you look good.

Staff Recruitment Strategy At Workplace Ppt PowerPoint Presentation Complete With Slides
Pitch yourself both in house and outside by utilizing this complete deck. This Staff Recruitment Strategy At Workplace Ppt PowerPoint Presentation Complete With Slides focuses on key fundamentals of the topic, displayed using different slides. With a total of sixty three slides, this template is the best tool you can use to persuade your audience. It will not only help you create great presentations but also induce strategic thinking because of its well researched content and graphics. You can easily personalize any of the elements to suit your unique business setting. Additionally, it can be saved in PNG, JPG, and PDF formats to save your time and resources.
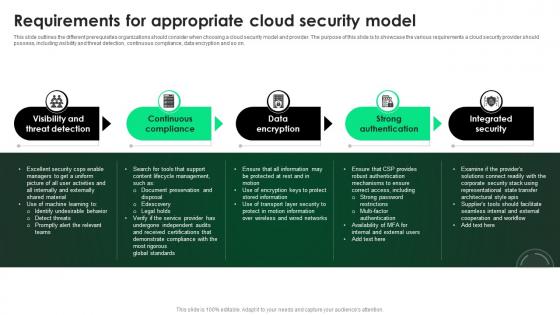
CASB 2 0 IT Requirements For Appropriate Cloud Security Model
This slide outlines the different prerequisites organizations should consider when choosing a cloud security model and provider. The purpose of this slide is to showcase the various requirements a cloud security provider should possess, including visibility and threat detection, continuous compliance, data encryption and so on. Find highly impressive CASB 2 0 IT Requirements For Appropriate Cloud Security Model on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download CASB 2 0 IT Requirements For Appropriate Cloud Security Model for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide outlines the different prerequisites organizations should consider when choosing a cloud security model and provider. The purpose of this slide is to showcase the various requirements a cloud security provider should possess, including visibility and threat detection, continuous compliance, data encryption and so on.
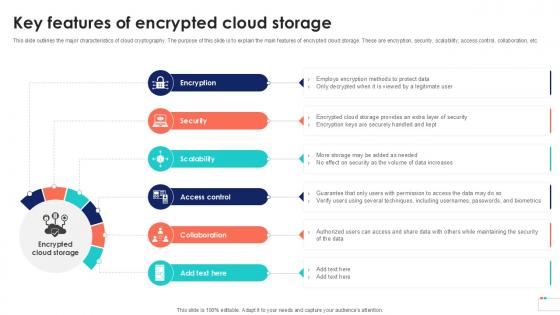
Key Features Of Encrypted Cloud Data Security In Cloud Computing Ppt Example
This slide outlines the major characteristics of cloud cryptography. The purpose of this slide is to explain the main features of encrypted cloud storage. These are encryption, security, scalability, access control, collaboration, etc. This Key Features Of Encrypted Cloud Data Security In Cloud Computing Ppt Example from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide outlines the major characteristics of cloud cryptography. The purpose of this slide is to explain the main features of encrypted cloud storage. These are encryption, security, scalability, access control, collaboration, etc.
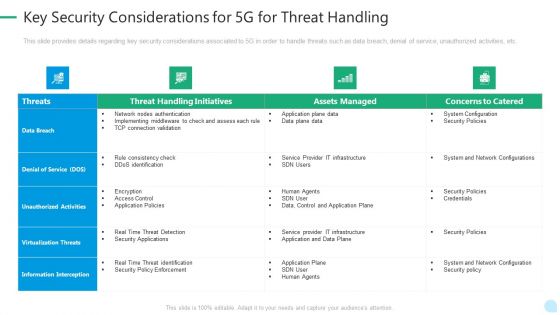
5G Network Technology Key Security Considerations For 5G For Threat Handling Ppt Gallery Gridlines PDF
This slide provides details regarding key security considerations associated to 5G in order to handle threats such as data breach, denial of service, unauthorized activities, etc. Deliver an awe inspiring pitch with this creative 5g network technology key security considerations for 5g for threat handling ppt gallery gridlines pdf bundle. Topics like virtualization threats, information interception, security policies, infrastructure can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
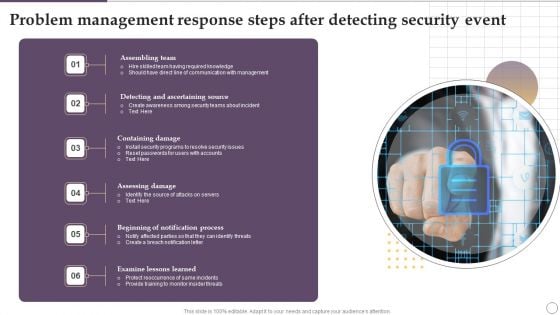
Problem Management Response Steps After Detecting Security Event Ppt Outline Brochure PDF
Presenting Problem Management Response Steps After Detecting Security Event Ppt Outline Brochure PDF to dispense important information. This template comprises seven stages. It also presents valuable insights into the topics including Assembling Team, Containing Damage, Assessing Damage, Examine Lessons Learned. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
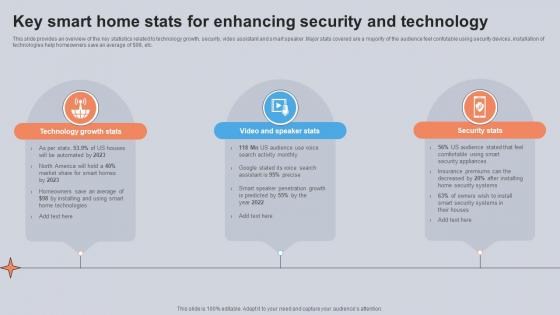
Key Smart Home Stats For Enhancing Security And Technology Utilizing Smart Appliances IoT SS V
This slide provides an overview of the key statistics related to technology growth, security, video assistant and smart speaker. Major stats covered are a majority of the audience feel confutable using security devices, installation of technologies help homeowners save an average of dollar 98, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Key Smart Home Stats For Enhancing Security And Technology Utilizing Smart Appliances IoT SS V. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide provides an overview of the key statistics related to technology growth, security, video assistant and smart speaker. Major stats covered are a majority of the audience feel confutable using security devices, installation of technologies help homeowners save an average of dollar 98, etc.

Prominent Users Of Secure Web Gateway Web Threat Protection System
This slide outlines the various Secure Web Gateway clients. The purpose of this slide is to explain how different users are utilizing SWG in their organizations. These are IT security experts, network administrators, compliance officers, HR managers, etc. Retrieve professionally designed Prominent Users Of Secure Web Gateway Web Threat Protection System to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide outlines the various Secure Web Gateway clients. The purpose of this slide is to explain how different users are utilizing SWG in their organizations. These are IT security experts, network administrators, compliance officers, HR managers, etc.
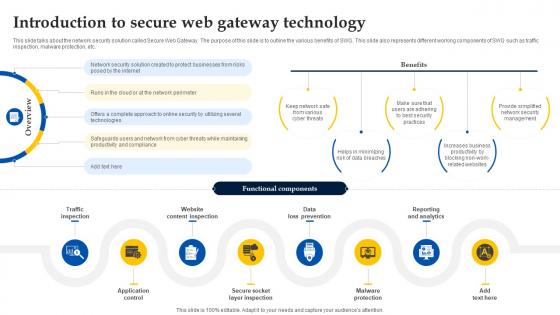
Web Access Control Solution Introduction To Secure Web Gateway Technology
This slide talks about the network security solution called Secure Web Gateway. The purpose of this slide is to outline the various benefits of SWG. This slide also represents different working components of SWG such as traffic inspection, malware protection, etc. Retrieve professionally designed Web Access Control Solution Introduction To Secure Web Gateway Technology to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide talks about the network security solution called Secure Web Gateway. The purpose of this slide is to outline the various benefits of SWG. This slide also represents different working components of SWG such as traffic inspection, malware protection, etc.

Training Program For Insider Threat In Cyber Security Awareness Guidelines PDF
This slide shows program for insider threat awareness training. It provides information such as program, details, system requirements, duration, fee or charge, etc. Showcasing this set of slides titled Training Program For Insider Threat In Cyber Security Awareness Guidelines PDF. The topics addressed in these templates are Indicators Insider Threat, Protection Confidential Data, Insider Threat. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Icons Slide For Developing Cyber Security Threat Awareness Staff Training Program Information PDF
Introducing our well designed Icons Slide For Developing Cyber Security Threat Awareness Staff Training Program Information PDF set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.
Icons Slide For Developing Information Technology Security Awareness Training Program For Employees Rules PDF
Introducing our well designed Icons Slide For Developing Information Technology Security Awareness Training Program For Employees Rules PDF set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.
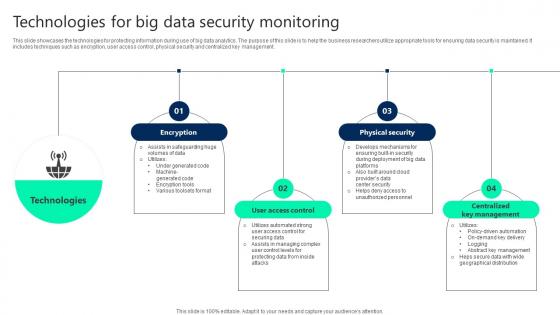
Technologies For Big Data Security Monitoring Summary pdf
This slide showcases the technologies for protecting information during use of big data analytics. The purpose of this slide is to help the business researchers utilize appropriate tools for ensuring data security is maintained. It includes techniques such as encryption, user access control, physical security and centralized key management. Showcasing this set of slides titled Technologies For Big Data Security Monitoring Summary pdf. The topics addressed in these templates are User Access Control, Physical Security, Centralized Key Management. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcases the technologies for protecting information during use of big data analytics. The purpose of this slide is to help the business researchers utilize appropriate tools for ensuring data security is maintained. It includes techniques such as encryption, user access control, physical security and centralized key management.
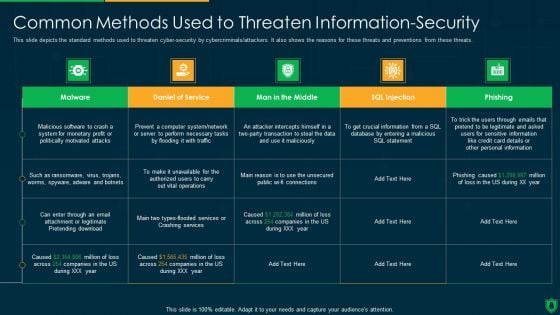
Info Security Common Methods Used To Threaten Information Security Ppt PowerPoint Presentation Gallery Clipart Images PDF
This slide depicts the standard methods used to threaten cyber-security by cybercriminals or attackers. It also shows the reasons for these threats and preventions from these threats. Deliver an awe inspiring pitch with this creative info security common methods used to threaten information security ppt powerpoint presentation gallery clipart images pdf bundle. Topics like personal information, phishing caused, sql statement can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Global Data Security Industry Report Challenges Impeding Cybersecurity Industry Growth IR SS V
The purpose of the slide is to analyze challenges facing cybersecurity industry. It will assist stakeholders to devise effective strategies and solutions to overcome the repercussions. It covers restraints like shortage skills, rapidly evolving threat landscape, budget constraints, cloud security concerns, IoT and connected devices. Want to ace your presentation in front of a live audience Our Global Data Security Industry Report Challenges Impeding Cybersecurity Industry Growth IR SS V can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. The purpose of the slide is to analyze challenges facing cybersecurity industry. It will assist stakeholders to devise effective strategies and solutions to overcome the repercussions. It covers restraints like shortage skills, rapidly evolving threat landscape, budget constraints, cloud security concerns, IoT and connected devices.
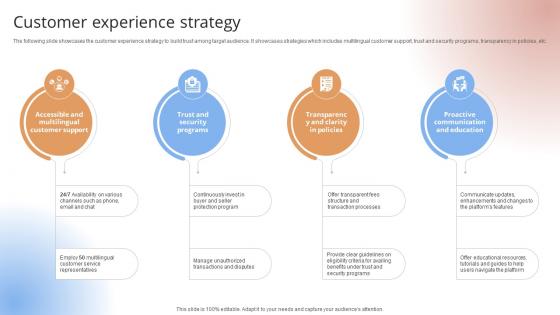
Customer Experience Strategy Payment Gateway Provider Startup GTM Strategy GTM SS V
The following slide showcases the customer experience strategy to build trust among target audience. It showcases strategies which includes multilingual customer support, trust and security programs, transparency in policies, etc.The following slide showcases the customer experience strategy to build trust among target audience. It showcases strategies which includes multilingual customer support, trust and security programs, transparency in policies, etc.Get a simple yet stunning designed Customer Experience Strategy Payment Gateway Provider Startup GTM Strategy GTM SS V. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Customer Experience Strategy Payment Gateway Provider Startup GTM Strategy GTM SS V can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. The following slide showcases the customer experience strategy to build trust among target audience. It showcases strategies which includes multilingual customer support, trust and security programs, transparency in policies, etc.
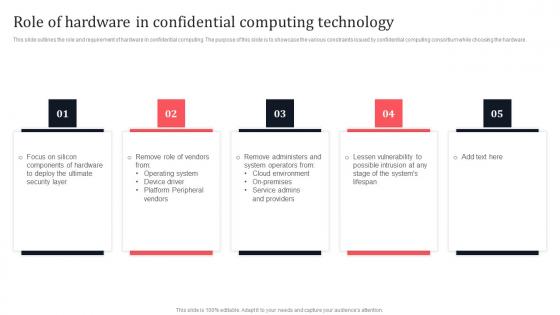
Role Of Hardware In Confidential Computing Technology Secure Multi Party Download Pdf
This slide outlines the role and requirement of hardware in confidential computing. The purpose of this slide is to showcase the various constraints issued by confidential computing consortium while choosing the hardware. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Role Of Hardware In Confidential Computing Technology Secure Multi Party Download Pdf With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Role Of Hardware In Confidential Computing Technology Secure Multi Party Download Pdf today and make your presentation stand out from the rest. This slide outlines the role and requirement of hardware in confidential computing. The purpose of this slide is to showcase the various constraints issued by confidential computing consortium while choosing the hardware.

Steps To Implement Cryptographic Data Security In Cloud Computing Ppt Sample
The purpose of this slide is to outline the various steps to be followed while implementing cloud cryptography. These include identify and classify sensitive data, choose the appropriate cryptographic algorithm, use strong encryption keys, manage keys effectively, etc. Get a simple yet stunning designed Steps To Implement Cryptographic Data Security In Cloud Computing Ppt Sample. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Steps To Implement Cryptographic Data Security In Cloud Computing Ppt Sample can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. The purpose of this slide is to outline the various steps to be followed while implementing cloud cryptography. These include identify and classify sensitive data, choose the appropriate cryptographic algorithm, use strong encryption keys, manage keys effectively, etc.
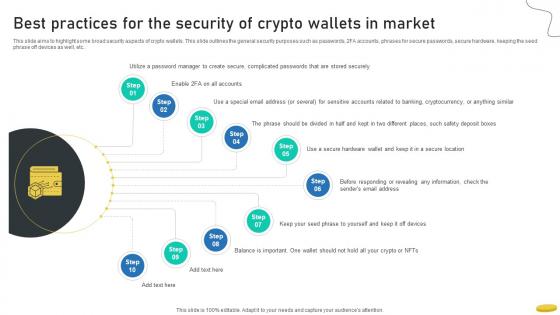
Best Practices For The Security Of Crypto Wallets In Market Cryptocurrency Management With Blockchain
This slide aims to highlight some broad security aspects of crypto wallets. This slide outlines the general security purposes such as passwords, 2FA accounts, phrases for secure passwords, secure hardware, keeping the seed phrase off devices as well, etc.Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Best Practices For The Security Of Crypto Wallets In Market Cryptocurrency Management With Blockchain. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Best Practices For The Security Of Crypto Wallets In Market Cryptocurrency Management With Blockchain today and make your presentation stand out from the rest This slide aims to highlight some broad security aspects of crypto wallets. This slide outlines the general security purposes such as passwords, 2FA accounts, phrases for secure passwords, secure hardware, keeping the seed phrase off devices as well, etc.
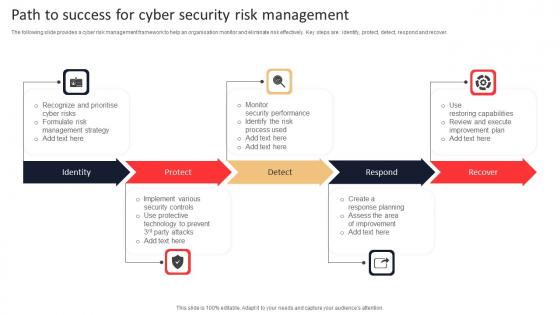
Path To Success For Cyber Security Risk Management Rules Pdf
The following slide provides a cyber risk management framework to help an organisation monitor and eliminate risk effectively. Key steps are identify, protect, detect, respond and recover. Pitch your topic with ease and precision using this Path To Success For Cyber Security Risk Management Rules Pdf. This layout presents information on Identity, Protect, Respond, Recover. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. The following slide provides a cyber risk management framework to help an organisation monitor and eliminate risk effectively. Key steps are identify, protect, detect, respond and recover.

Smart Home Security Solutions Company Profile Executive Leadership And Management Team Themes PDF
This slide highlights the security company leadership and management team which includes president and CEO, executive vice president of finance, EVP home security, chief administration officer. This is a Smart Home Security Solutions Company Profile Executive Leadership And Management Team Themes PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Executive Leadership Management, Team Business Security, Financial Management Services. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Digital Wallet Management System For Secure In Depth Guide To Digital Wallets Fin SS V
This slide provides a financial management strategy for businesses with the help of digital wallet integration. The process involves contactless payments with QR codes, collaboration with digital wallet apps, choosing the right payment processing, customer rewards, etc. Find highly impressive Digital Wallet Management System For Secure In Depth Guide To Digital Wallets Fin SS V on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Digital Wallet Management System For Secure In Depth Guide To Digital Wallets Fin SS V for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide provides a financial management strategy for businesses with the help of digital wallet integration. The process involves contactless payments with QR codes, collaboration with digital wallet apps, choosing the right payment processing, customer rewards, etc.
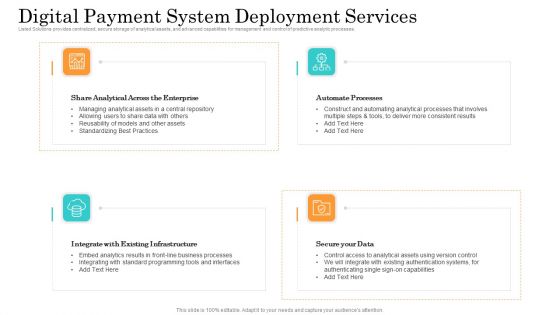
Online Payment Service Digital Payment System Deployment Services Ppt Slides Brochure PDF
Listed Solutions provides centralized, secure storage of analytical assets, and advanced capabilities for management and control of predictive analytic processes. This is a online payment service digital payment system deployment services ppt slides brochure pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like automate processes, share analytical across, infrastructure, secure your data. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
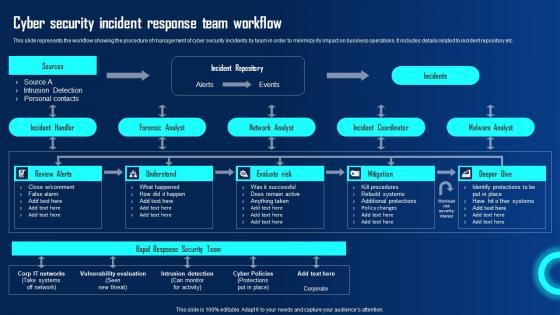
Cyber Security Incident Response Team Workflow Ppt Powerpoint Presentation File Deck Pdf
This slide represents the workflow showing the procedure of management of cyber security incidents by team in order to minimize its impact on business operations. It includes details related to incident repository etc. This modern and well arranged Cyber Security Incident Response Team Workflow Ppt Powerpoint Presentation File Deck Pdf provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide represents the workflow showing the procedure of management of cyber security incidents by team in order to minimize its impact on business operations. It includes details related to incident repository etc.

Security Camera System Company Profile Executive Leadership And Management Team Designs PDF
This slide highlights the security company leadership and management team which includes president CEO, executive vice president of finance, EVP home security, chief administration officer. This is a Security Camera System Company Profile Executive Leadership And Management Team Designs PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Business Security, Southern University, Management Services. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
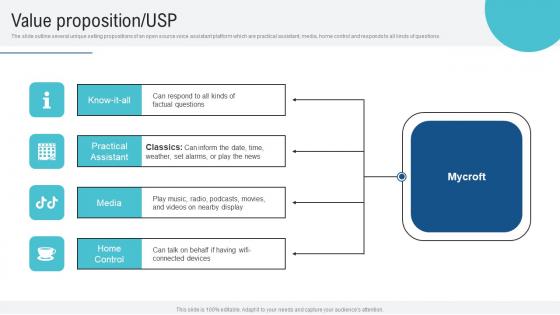
Value Proposition USP Voice Assistance Security Platform Investor Funding Presentation Demonstration Pdf
The slide outline several unique selling propositions of an open source voice assistant platform which are practical assistant, media, home control and responds to all kinds of questions. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Value Proposition USP Voice Assistance Security Platform Investor Funding Presentation Demonstration Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. The slide outline several unique selling propositions of an open source voice assistant platform which are practical assistant, media, home control and responds to all kinds of questions.
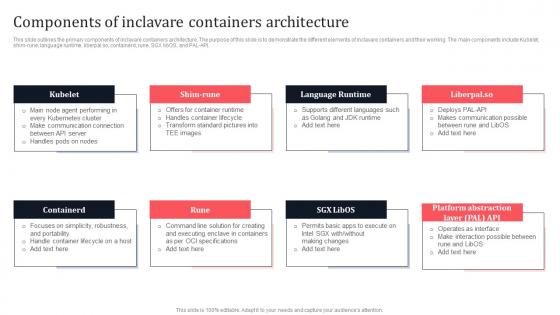
Components Of Inclavare Containers Architecture Secure Multi Party Information Pdf
This slide outlines the primary components of inclavare containers architecture. The purpose of this slide is to demonstrate the different elements of inclavare containers and their working. The main components include Kubelet, shim-rune, language runtime, liberpal.so, containerd, rune, SGX libOS, and PAL-API. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Components Of Inclavare Containers Architecture Secure Multi Party Information Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Components Of Inclavare Containers Architecture Secure Multi Party Information Pdf You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today. This slide outlines the primary components of inclavare containers architecture. The purpose of this slide is to demonstrate the different elements of inclavare containers and their working. The main components include Kubelet, shim-rune, language runtime, liberpal.so, containerd, rune, SGX libOS, and PAL-API.
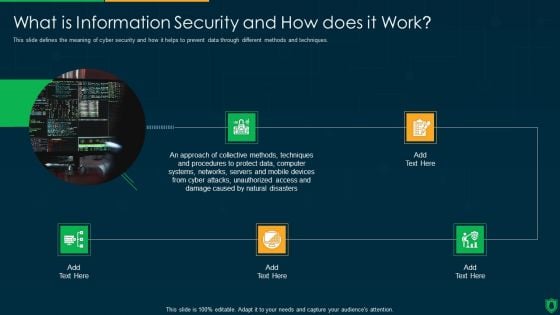
Info Security What Is Information Security And How Does It Work Ppt PowerPoint Presentation File Clipart PDF
This slide defines the meaning of cyber security and how it helps to prevent data through different methods and techniques. This is a info security what is information security and how does it work ppt powerpoint presentation file clipart pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like collective methods, techniques and procedures, protect data, computer systems, networks. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
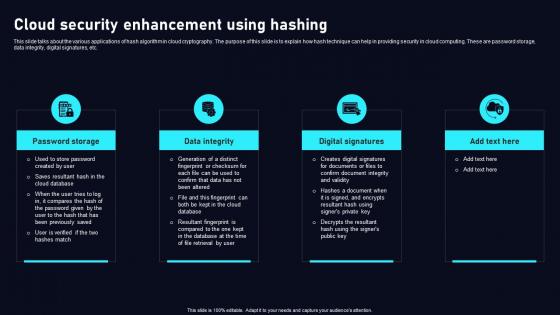
Cloud Security Enhancement Using Cloud Data Security Using Cryptography Elements Pdf
This slide talks about the various applications of hash algorithm in cloud cryptography. The purpose of this slide is to explain how hash technique can help in providing security in cloud computing. These are password storage, data integrity, digital signatures, etc. This Cloud Security Enhancement Using Cloud Data Security Using Cryptography Elements Pdf is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Cloud Security Enhancement Using Cloud Data Security Using Cryptography Elements Pdf features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide talks about the various applications of hash algorithm in cloud cryptography. The purpose of this slide is to explain how hash technique can help in providing security in cloud computing. These are password storage, data integrity, digital signatures, etc.
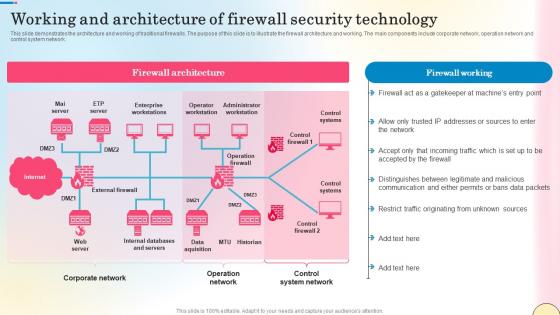
Working And Architecture Of Firewall Security Technology Network Security Summary Pdf
This slide demonstrates the architecture and working of traditional firewalls. The purpose of this slide is to illustrate the firewall architecture and working. The main components include corporate network, operation network and control system network. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Working And Architecture Of Firewall Security Technology Network Security Summary Pdf can be your best option for delivering a presentation. Represent everything in detail using Working And Architecture Of Firewall Security Technology Network Security Summary Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide demonstrates the architecture and working of traditional firewalls. The purpose of this slide is to illustrate the firewall architecture and working. The main components include corporate network, operation network and control system network.

Agenda Of Security Risk Management Graphics PDF
This is a agenda of security risk management graphics pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like vulnerabilities, organizational, security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Police Line Security PowerPoint Themes And PowerPoint Slides 0811
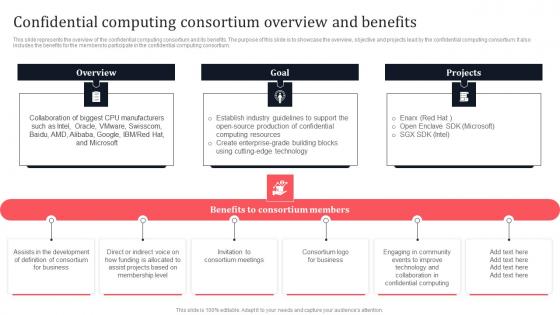
Confidential Computing Consortium Overview And Benefits Secure Multi Party Demonstration Pdf
This slide represents the overview of the confidential computing consortium and its benefits. The purpose of this slide is to showcase the overview, objective and projects lead by the confidential computing consortium. It also includes the benefits for the members to participate in the confidential computing consortium. If you are looking for a format to display your unique thoughts, then the professionally designed Confidential Computing Consortium Overview And Benefits Secure Multi Party Demonstration Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Confidential Computing Consortium Overview And Benefits Secure Multi Party Demonstration Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide represents the overview of the confidential computing consortium and its benefits. The purpose of this slide is to showcase the overview, objective and projects lead by the confidential computing consortium. It also includes the benefits for the members to participate in the confidential computing consortium.
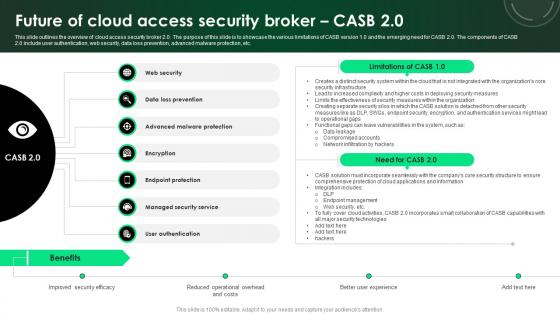
CASB 2 0 IT Future Of Cloud Access Security Broker CASB 2 0
This slide outlines the overview of cloud access security broker 2.0. The purpose of this slide is to showcase the various limitations of CASB version 1.0 and the emerging need for CASB 2.0. The components of CASB 2.0 include user authentication, web security, data loss prevention, advanced malware protection, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate CASB 2 0 IT Future Of Cloud Access Security Broker CASB 2 0 for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide outlines the overview of cloud access security broker 2.0. The purpose of this slide is to showcase the various limitations of CASB version 1.0 and the emerging need for CASB 2.0. The components of CASB 2.0 include user authentication, web security, data loss prevention, advanced malware protection, etc.

Cloud Security Enhancement Using Data Security In Cloud Computing Ppt Presentation
This slide talks about the various applications of hash algorithm in cloud cryptography. The purpose of this slide is to explain how hash technique can help in providing security in cloud computing. These are password storage, data integrity, digital signatures, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Cloud Security Enhancement Using Data Security In Cloud Computing Ppt Presentation and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide talks about the various applications of hash algorithm in cloud cryptography. The purpose of this slide is to explain how hash technique can help in providing security in cloud computing. These are password storage, data integrity, digital signatures, etc.
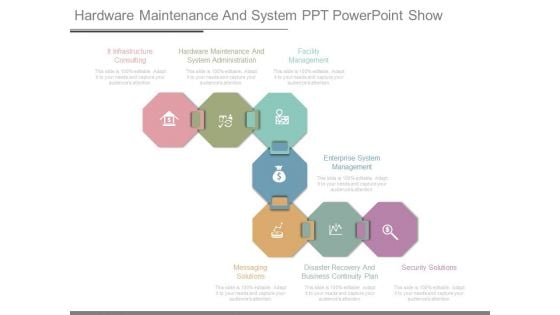
Hardware Maintenance And System Ppt Powerpoint Show
This is a hardware maintenance and system ppt powerpoint show. This is a seven stage process. The stages in this process are it infrastructure consulting, hardware maintenance and system administration, facility management, enterprise system management, messaging solutions, disaster recovery and business continuity plan, security solutions.
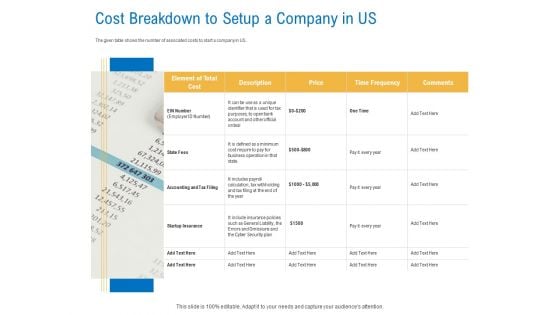
Digital Businesses Ecosystems Cost Breakdown To Setup A Company In Us Professional PDF
Deliver an awe inspiring pitch with this creative digital businesses ecosystems cost breakdown to setup a company in us professional pdf bundle. Topics like cyber security, plan, business, cost, price can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Cloud Management Tasks Ppt Icon Example Introduction PDF
This is a cloud management tasks ppt icon example introduction pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like awareness, system, planning, security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Security Implementation Framework Agenda For Cyber Security Management Ppt PowerPoint Presentation Gallery Ideas PDF
Presenting this set of slides with name cyber security implementation framework agenda for cyber security management ppt powerpoint presentation gallery ideas pdf. This is a one stage process. The stages in this process are determining roles and responsibilities, risk management, executives. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
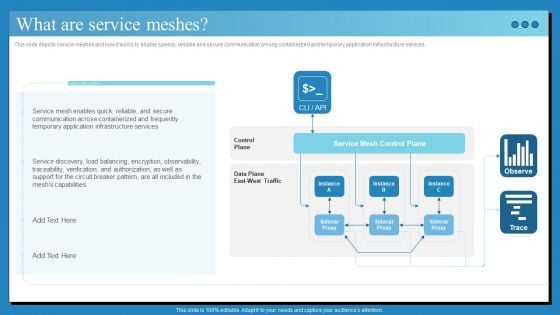
Data Center Infrastructure Technologies What Are Service Meshes Topics PDF
This slide depicts service meshes and how it works to enable speedy, reliable and secure communication among containerized and temporary application infrastructure services. Explore a selection of the finest Data Center Infrastructure Technologies What Are Service Meshes Topics PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Data Center Infrastructure Technologies What Are Service Meshes Topics PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
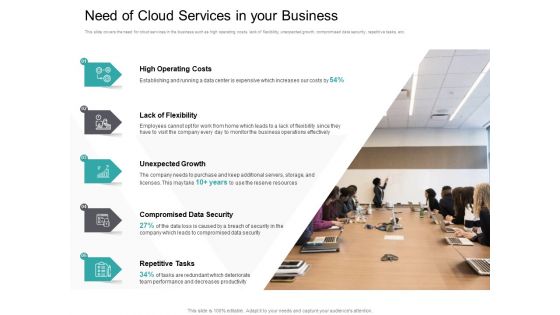
Cloud Based Marketing Need Of Cloud Services In Your Business Ppt PowerPoint Presentation Professional Show PDF
This slide covers the need for cloud services in the business such as high operating costs, lack of flexibility, unexpected growth, compromised data security, repetitive tasks, etc. Presenting cloud based marketing need of cloud services in your business ppt powerpoint presentation professional show pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like high operating costs, lack flexibility, unexpected growth, compromised data security, repetitive tasks. In addtion, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.
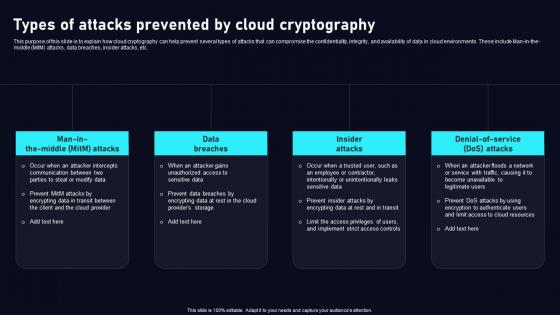
Types Of Attacks Prevented By Cloud Data Security Using Cryptography Guidelines Pdf
This purpose of this slide is to explain how cloud cryptography can help prevent several types of attacks that can compromise the confidentiality, integrity, and availability of data in cloud environments. These include Man in the middle MitM attacks, data breaches, insider attacks, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Types Of Attacks Prevented By Cloud Data Security Using Cryptography Guidelines Pdf. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This purpose of this slide is to explain how cloud cryptography can help prevent several types of attacks that can compromise the confidentiality, integrity, and availability of data in cloud environments. These include Man in the middle MitM attacks, data breaches, insider attacks, etc.
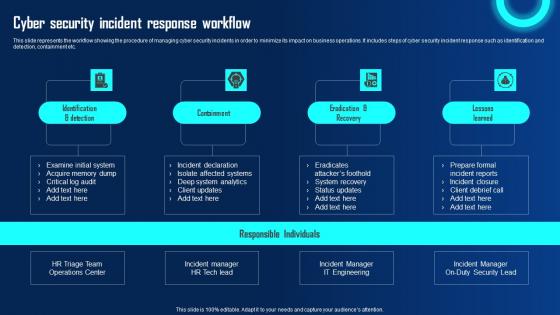
Cyber Security Incident Response Workflow Ppt Powerpoint Presentation File Diagrams Pdf
This slide represents the workflow showing the procedure of managing cyber security incidents in order to minimize its impact on business operations. It includes steps of cyber security incident response such as identification and detection, containment etc. This Cyber Security Incident Response Workflow Ppt Powerpoint Presentation File Diagrams Pdf is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Cyber Security Incident Response Workflow Ppt Powerpoint Presentation File Diagrams Pdf features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide represents the workflow showing the procedure of managing cyber security incidents in order to minimize its impact on business operations. It includes steps of cyber security incident response such as identification and detection, containment etc.
Company Security Policies Ppt PowerPoint Presentation Summary Portrait Cpb Pdf
Presenting this set of slides with name company security policies ppt powerpoint presentation summary portrait cpb pdf. This is an editable Powerpoint six stages graphic that deals with topics like company security policies to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Current Security Management Challenges The Company Is Facing Demonstration PDF
This slide shows some of the current Security Management challenges and issues that are faced by the company and IT security managers. Deliver an awe inspiring pitch with this creative current security management challenges the company is facing demonstration pdf bundle. Topics like potential insider threats, external security breaches, employee management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Measures And Ways To Mitigate Security Management Challenges Background PDF
This slide provides information about the ways and measures through which the company and IT security managers can overcome the problems and issues related to Security Management. Deliver an awe inspiring pitch with this creative measures and ways to mitigate security management challenges background pdf bundle. Topics like potential insider threats, external security breaches, weak links in the supply chain can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
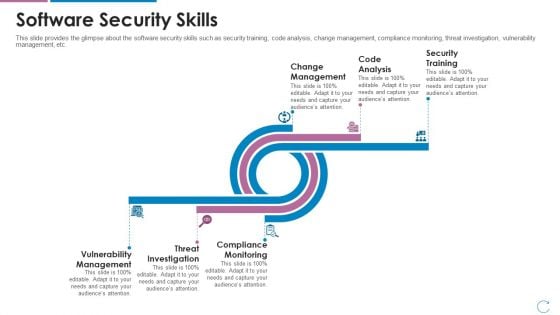
Devops Team Capabilities IT Software Security Skills Ppt Deck PDF
This slide provides the glimpse about the software security skills such as security training, code analysis, change management, compliance monitoring, threat investigation, vulnerability management, etc. Deliver an awe inspiring pitch with this creative devops team capabilities it software security skills ppt deck pdf bundle. Topics like change management, code analysis, security training, vulnerability management, threat investigation, compliance monitoring can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
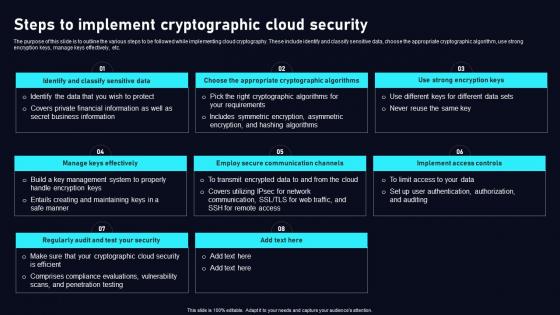
Steps To Implement Cryptographic Cloud Data Security Using Cryptography Brochure Pdf
The purpose of this slide is to outline the various steps to be followed while implementing cloud cryptography. These include identify and classify sensitive data, choose the appropriate cryptographic algorithm, use strong encryption keys, manage keys effectively, etc. Find highly impressive Steps To Implement Cryptographic Cloud Data Security Using Cryptography Brochure Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Steps To Implement Cryptographic Cloud Data Security Using Cryptography Brochure Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now The purpose of this slide is to outline the various steps to be followed while implementing cloud cryptography. These include identify and classify sensitive data, choose the appropriate cryptographic algorithm, use strong encryption keys, manage keys effectively, etc.
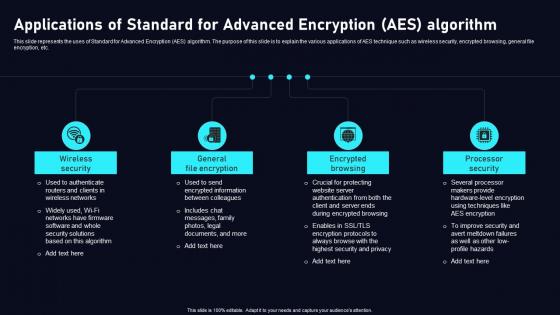
Applications Of Standard Advanced Cloud Data Security Using Cryptography Topics Pdf
This slide represents the uses of Standard for Advanced Encryption AES algorithm. The purpose of this slide is to explain the various applications of AES technique such as wireless security, encrypted browsing, general file encryption, etc. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Applications Of Standard Advanced Cloud Data Security Using Cryptography Topics Pdf and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide represents the uses of Standard for Advanced Encryption AES algorithm. The purpose of this slide is to explain the various applications of AES technique such as wireless security, encrypted browsing, general file encryption, etc.


 Continue with Email
Continue with Email

 Home
Home


































