Safety Pyramid
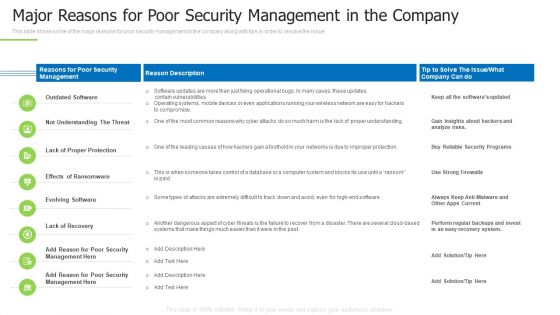
Techniques And Strategies To Reduce Security Management Risks Major Reasons For Poor Security Guidelines PDF
This slide shows some of the major reasons for poor security management in the company along with tips in order to resolve the issue.Deliver an awe inspiring pitch with this creative techniques and strategies to reduce security management risks major reasons for poor security guidelines pdf bundle. Topics like outdated software, lack of proper protection, another dangerous aspect can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
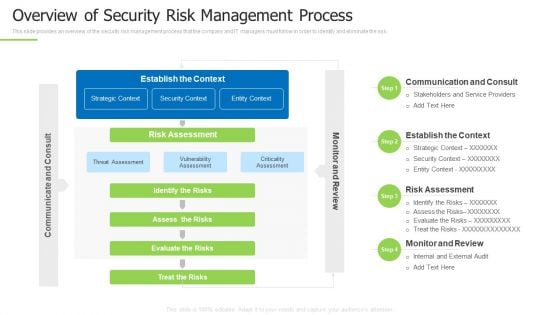
Techniques And Strategies To Reduce Security Management Risks Overview Of Security Risk Background PDF
This slide provides an overview of the security risk management process that the company and IT managers must follow in order to identify and eliminate the risk. Deliver an awe inspiring pitch with this creative techniques and strategies to reduce security management risks overview of security risk background pdf bundle. Topics like identify the risks, strategic context, vulnerability assessment can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
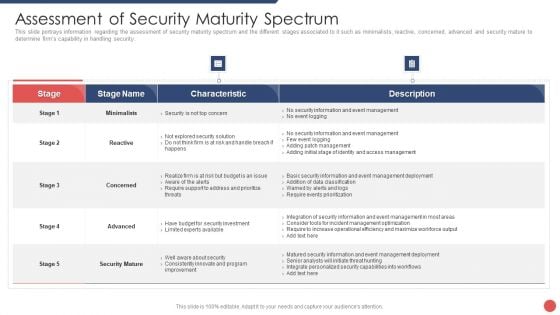
Security Functioning Centre Assessment Of Security Maturity Spectrum Slides PDF
This slide portrays information regarding the assessment of security maturity spectrum and the different stages associated to it such as minimalists, reactive, concerned, advanced and security mature to determine firms capability in handling security. Deliver an awe inspiring pitch with this creative security functioning centre assessment of security maturity spectrum slides pdf bundle. Topics like security mature, operational efficiency, security capabilities can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
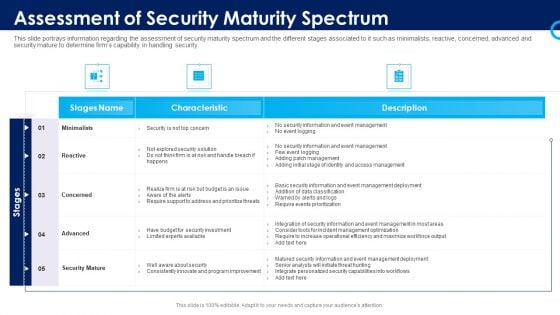
Organizational Security Solutions Assessment Of Security Maturity Spectrum Rules PDF
This slide portrays information regarding the assessment of security maturity spectrum and the different stages associated to it such as minimalists, reactive, concerned, advanced and security mature to determine firms capability in handling security. Deliver an awe inspiring pitch with this creative organizational security solutions assessment of security maturity spectrum rules pdf bundle. Topics like minimalists, reactive, concerned, advanced, security mature can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
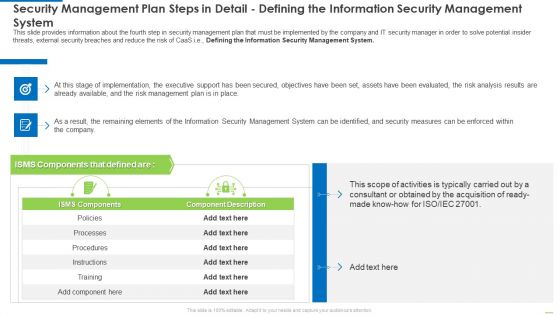
Security Management Plan Steps In Detail Defining The Information Security Management System Diagrams PDF
This slide provides information about the fourth step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Defining the Information Security Management System. Deliver an awe inspiring pitch with this creative security management plan steps in detail defining the information security management system diagrams pdf bundle. Topics like security management plan steps in detail - defining the information security management system can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Management Plan Steps In Detail Defining The Information Security Management System Sample PDF
This slide provides information about the fourth step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. Defining the Information Security Management System. Deliver an awe inspiring pitch with this creative security management plan steps in detail defining the information security management system sample pdf bundle. Topics like security management plan steps in detail defining the information security management system can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
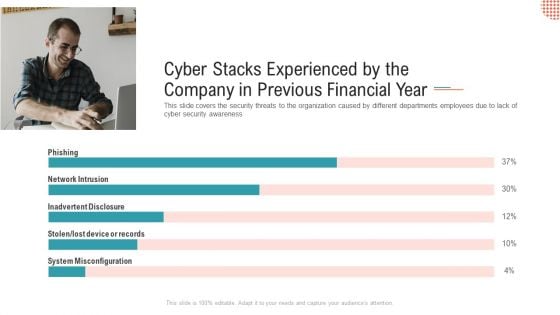
Cyber Stacks Experienced By The Company In Previous Financial Year Ppt Show Themes PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness Deliver and pitch your topic in the best possible manner with this cyber stacks experienced by the company in previous financial year ppt show themes pdf. Use them to share invaluable insights on network intrusion, inadvertent disclosure, system misconfiguration and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
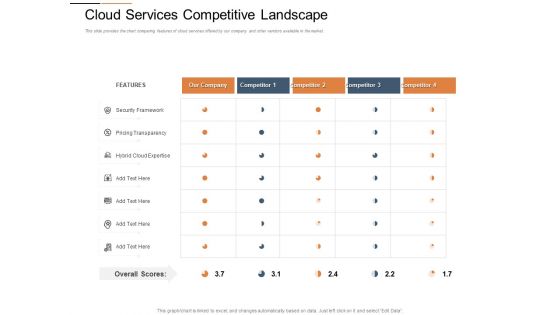
Cloud Services Best Practices Marketing Plan Agenda Cloud Services Competitive Landscape Guidelines PDF
Deliver an awe inspiring pitch with this creative cloud services best practices marketing plan agenda cloud services competitive landscape guidelines pdf bundle. Topics like security framework, pricing transparency, hybrid cloud expertise can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
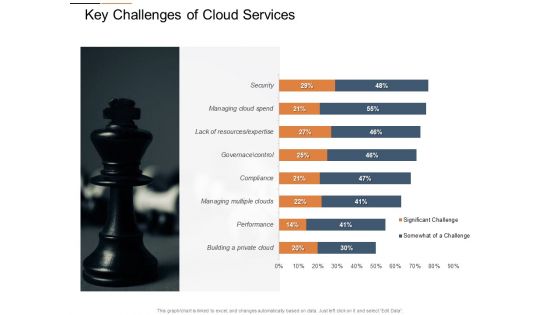
Cloud Services Best Practices Marketing Plan Agenda Key Challenges Of Cloud Services Background PDF
Deliver an awe inspiring pitch with this creative cloud services best practices marketing plan agenda key challenges of cloud services background pdf bundle. Topics like performance, security, governance, resource, clouds can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Help On Web Internet PowerPoint Templates And PowerPoint Themes 1112
We present our Help On Web Internet PowerPoint Templates And PowerPoint Themes 1112.Use our Security PowerPoint Templates because, Bullet-point your thoughts and ideas to profitably accomplish every step of every stage along the way. Use our Computer PowerPoint Templates because, Trigger their minds with your interesting ideas. Use our Internet PowerPoint Templates because, Listen to ideas and thoughts. Use our Business PowerPoint Templates because, The alphabetical order is a time honoured concept. Use our Success PowerPoint Templates because, Your foot is on the pedal and your company is purring along smoothly.Use these PowerPoint slides for presentations relating to Help on web internet, security, computer, internet, business, success. The prominent colors used in the PowerPoint template are Red, Orange, White Cover the gaps with our Help On Web Internet PowerPoint Templates And PowerPoint Themes 1112. They provide an ideal filling.

Golden Key Chain With Earth Globe PowerPoint Templates And PowerPoint Themes 1112
We present our Golden Key Chain With Earth Globe PowerPoint Templates And PowerPoint Themes 1112.Use our Security PowerPoint Templates because, The alphabetical order is a time honoured concept. Use our Success PowerPoint Templates because, Individual components well researched and understood in their place. Use our Globe PowerPoint Templates because, Decorate it with your well wrapped ideas and colourful thoughts. Use our Spheres PowerPoint Templates because, Creating a winner is your passion and dream. Use our Business PowerPoint Templates because, Employ the right colours for your brilliant ideas.Use these PowerPoint slides for presentations relating to Key from the world, security, success, spheres, business, globe. The prominent colors used in the PowerPoint template are Yellow, Blue light, White Face the audience with complete assurance. Acquire faith and confidence with our Golden Key Chain With Earth Globe PowerPoint Templates And PowerPoint Themes 1112.
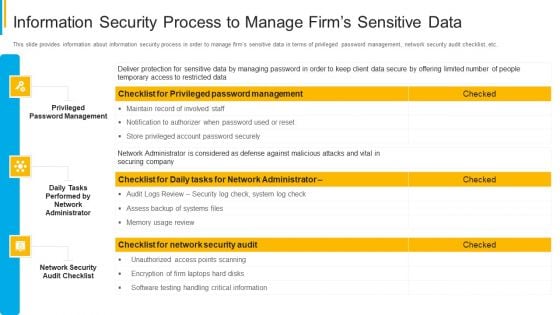
Project Security Administration IT Information Security Process To Manage Firms Sensitive Data Summary PDF
This slide provides information about information security process in order to manage firms sensitive data in terms of privileged password management, network security audit checklist, etc. Deliver an awe inspiring pitch with this creative project security administration it information security process to manage firms sensitive data summary pdf bundle. Topics like privileged password management, daily tasks performed by network administrator, network security audit checklist can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
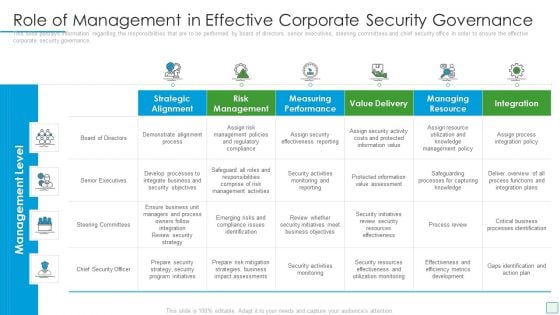
Developing Firm Security Strategy Plan Role Of Management In Effective Corporate Security Governance Slides PDF
This slide portrays information regarding the responsibilities that are to be performed by board of directors, senior executives, steering committees and chief security office in order to ensure the effective corporate security governance. Deliver an awe inspiring pitch with this creative developing firm security strategy plan role of management in effective corporate security governance slides pdf bundle. Topics like strategic alignment, risk management, measuring performance, value delivery, managing resource can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
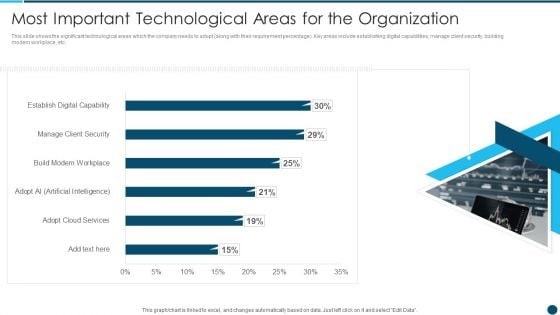
Digital Technology Adoption In Banking Industry Case Competition Most Important Portrait PDF
This slide shows the significant technological areas which the company needs to adopt along with their requirement percentage. Key areas include establishing digital capabilities, manage client security, building modern workplace, etc. Deliver an awe inspiring pitch with this creative Digital Technology Adoption In Banking Industry Case Competition Most Important Portrait PDF bundle. Topics like Adopt Cloud Services, Build Modern Workplace, Manage Client Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
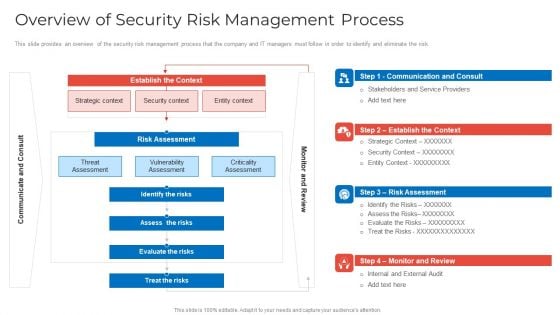
Implementing Security Management Strategy To Mitigate Risk Overview Of Security Risk Management Process Pictures PDF
This slide provides an overview of the security risk management process that the company and IT managers must follow in order to identify and eliminate the risk. Deliver an awe inspiring pitch with this creative implementing security management strategy to mitigate risk overview of security risk management process pictures pdf bundle. Topics like identify the risks, assess the risks, evaluate the risks can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Mesh Computing Technology Hybrid Private Public Iaas Paas Saas Workplan Characteristics Of Software As A Service Saas Pictures PDF
Deliver an awe inspiring pitch with this creative mesh computing technology hybrid private public iaas paas saas workplan characteristics of software as a service saas pictures pdf bundle. Topics like high availability, elastic infrastructure, data security, application security, automated provisioning can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

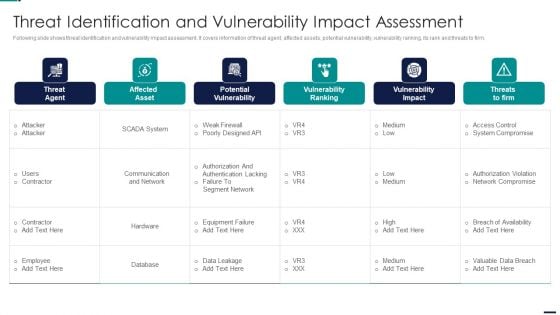
Cyber Security Risk Management Plan Threat Identification And Vulnerability Impact Assessment Brochure PDF
Following slide shows threat identification and vulnerability impact assessment. It covers information of threat agent, affected assets, potential vulnerability, vulnerability ranking, its rank and threats to firm. Deliver and pitch your topic in the best possible manner with this cyber security risk management plan threat identification and vulnerability impact assessment brochure pdf. Use them to share invaluable insights on threat agent, affected assets, potential vulnerability, vulnerability ranking, threats to firm and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Risk Management Model For Data Security Threat Identification And Vulnerability Impact Slides PDF
Following slide shows threat identification and vulnerability impact assessment. It covers information of threat agent, affected assets, potential vulnerability, vulnerability ranking, its rank and threats to firm. Deliver and pitch your topic in the best possible manner with this Risk Management Model For Data Security Threat Identification And Vulnerability Impact Slides PDF. Use them to share invaluable insights on Threat Agent, Affected Asset, Potential Vulnerability, Vulnerability Ranking and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Housing Mortgage Additional Benefits For Home Loan Proposal Ppt Slides Background PDF
Deliver an awe inspiring pitch with this creative housing mortgage additional benefits for home loan proposal ppt slides background pdf bundle. Topics like credit cards, easy security investment can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
IT Security Risk Management Approach Introduction Threat Vulnerability Asset Matrix Icons PDF
Mentioned slide displays the threat vulnerability asset matrix covering sections namely ranked threat agent and details about critical resources ranked from most critical to least. Deliver and pitch your topic in the best possible manner with this IT Security Risk Management Approach Introduction Threat Vulnerability Asset Matrix Icons PDF. Use them to share invaluable insights on Social Engineering, Server Systems, Internet and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
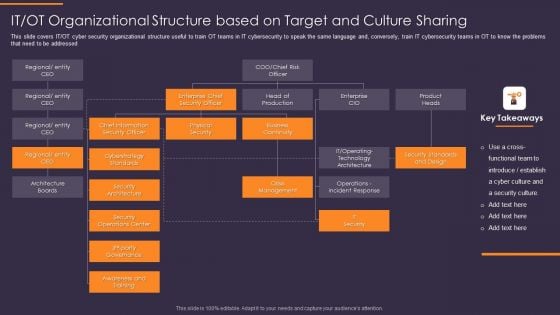
IT OT Organizational Structure Based On Target And Culture Convergence Strategy Mockup PDF
This slide covers IT or OT cyber security organizational structure useful to train OT teams in IT cybersecurity to speak the same language and, conversely, train IT cybersecurity teams in OT to know the problems that need to be addressed. Presenting IT OT Organizational Structure Based On Target And Culture Convergence Strategy Mockup PDF to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like Architecture Boards, Security Architecture, Awareness and Training. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
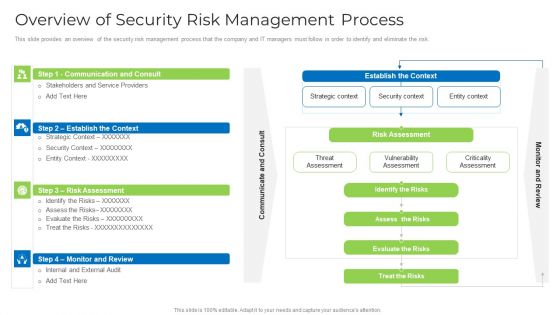
Overview Of Security Risk Management Process Formats PDF
This slide provides an overview of the security risk management process that the company and IT managers must follow in order to identify and eliminate the risk. Deliver an awe inspiring pitch with this creative overview of security risk management process formats pdf bundle. Topics like strategic context, vulnerability assessment, security context, risks can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Civil Infrastructure Designing Services Management It Infrastructure Optimization Pictures PDF
Deliver an awe inspiring pitch with this creative civil infrastructure designing services management it infrastructure optimization pictures pdf bundle. Topics like management, security, process, service, customer can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
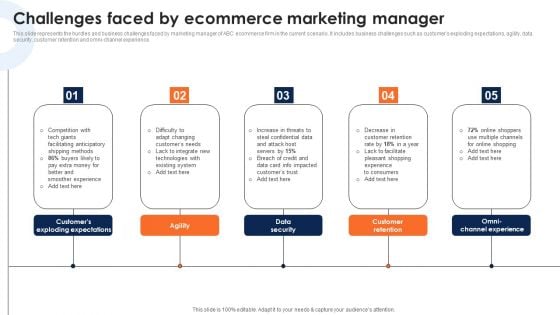
Challenges Faced By Ecommerce Marketing Manager Deploying Ecommerce Order Management Introduction PDF
This slide represents the hurdles and business challenges faced by marketing manager of ABC ecommerce firm in the current scenario. It includes business challenges such as customers exploding expectations, agility, data security, customer retention and omni-channel experience.Want to ace your presentation in front of a live audience Our Challenges Faced By Ecommerce Marketing Manager Deploying Ecommerce Order Management Introduction PDF can help you do that by engaging all the users towards you.. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.

Support Services Management IT Infrastructure Optimization Ppt Pictures Brochure PDF
Deliver an awe inspiring pitch with this creative support services management it infrastructure optimization ppt pictures brochure pdf bundle. Topics like identity and access management, data protection and recovery, security process, management process and governance can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
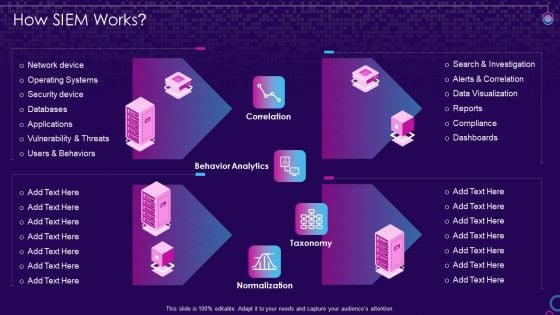
SIEM Services How SIEM Works Ppt Microsoft PDF
Deliver an awe inspiring pitch with this creative siem services how siem works ppt microsoft pdf bundle. Topics like network device, operating systems, security device, vulnerability and threats can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
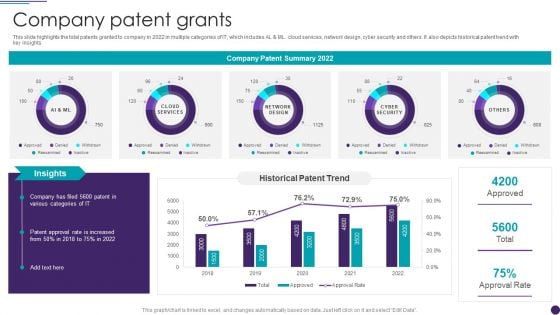
IT Services Business Profile Company Patent Grants Infographics PDF
This slide highlights the total patents granted to company in 2022 in multiple categories of IT, which includes AL and ML. cloud services, network design, cyber security and others. It also depicts historical patent trend with key insights. Deliver an awe inspiring pitch with this creative IT Services Business Profile Company Patent Grants Infographics PDF bundle. Topics like Network Design, Cyber Security, Cloud Services can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
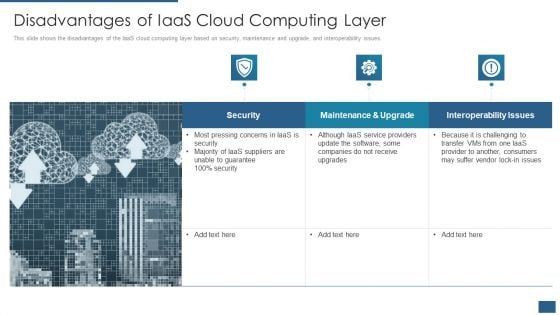
Cloud Computing Service Models IT Disadvantages Of Iaas Cloud Computing Layer Rules PDF
This slide shows the disadvantages of the IaaS cloud computing layer based on security, maintenance and upgrade, and interoperability issues. Deliver an awe inspiring pitch with this creative cloud computing service models it disadvantages of iaas cloud computing layer rules pdf bundle. Topics like security, maintenance and upgrade, interoperability issues can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
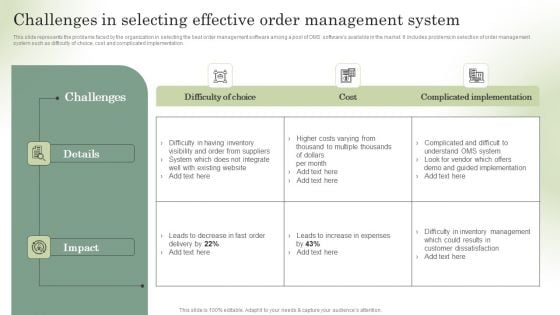
Optimizing Online Stores Challenges In Selecting Effective Order Management Graphics PDF
This slide represents the hurdles and business challenges faced by marketing manager of abc ecommerce firm in the current scenario. it includes business challenges such as customers exploding expectations, agility, data security, customer retention and omni-channel experience. there are so many reasons you need a optimizing online stores challenges faced by ecommerce marketing manager demonstration pdf. the first reason is you cant spend time making everything from scratch, thus, slidegeeks has made presentation templates for you too. you can easily download these templates from our website easily.
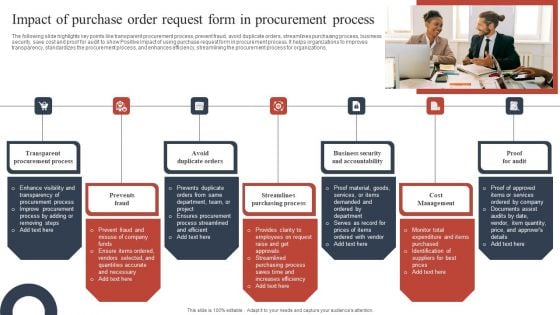
Impact Of Purchase Order Request Form In Procurement Process Inspiration PDF
The following slide highlights key points like transparent procurement process, prevent fraud, avoid duplicate orders, streamlines purchasing process, business security, save cost and proof for audit to show Positive impact of using purchase request form in procurement process. It helps organizations to improves transparency, standardizes the procurement process, and enhances efficiency, streamlining the procurement process for organizations. Presenting Impact Of Purchase Order Request Form In Procurement Process Inspiration PDF to dispense important information. This template comprises seven stages. It also presents valuable insights into the topics including Transparent Procurement Process, Prevents Fraud, Avoid Duplicate Orders. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Ecommerce Payment Gateway System Architecture Deploying Ecommerce Order Management Software Icons PDF
This slide represents the architecture showing the ways in which payment gateway validates consumers card details securely and ensures availability of funds and eventually enables merchants to get paid.Find highly impressive Ecommerce Payment Gateway System Architecture Deploying Ecommerce Order Management Software Icons PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Ecommerce Payment Gateway System Architecture Deploying Ecommerce Order Management Software Icons PDF for your upcoming presentation. All the presentation templates are 100precent editable and you can change the color and personalize the content accordingly. Download now.
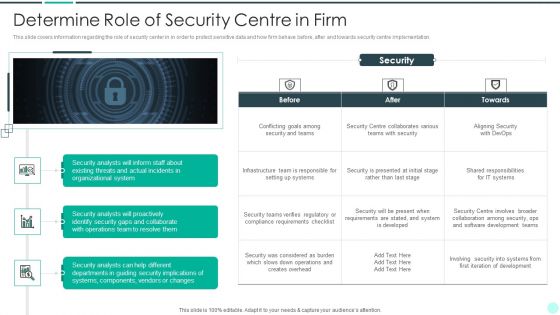
Executing Advance Data Analytics At Workspace Determine Role Of Security Centre In Firm Sample PDF
This slide covers information regarding the role of security center in in order to protect sensitive data and how firm behave before, after and towards security centre implementation. This is a executing advance data analytics at workspace determine role of security centre in firm sample pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like determine role of security centre in firm. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Developing Firm Security Strategy Plan Security Incidents Tracking Dashboard Growth Guidelines PDF
This slide portrays information regarding the dashboard that firm will track various security incidents detected. These incidents will be managed in order to avoid security risks. Deliver and pitch your topic in the best possible manner with this developing firm security strategy plan security incidents tracking dashboard growth guidelines pdf. Use them to share invaluable insights on number of open security incidents, open security incidents by age, average age of open security incidents, security incident backlog growth and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Security Management Plan Steps In Detail Defining The Information Security Management System Mockup PDF
This slide provides information about the fourth step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. Defining the Information Security Management System. Deliver and pitch your topic in the best possible manner with this security management plan steps in detail defining the information security management system mockup pdf. Use them to share invaluable insights on implementation, management plan, security management, security measures and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Techniques And Strategies To Reduce Security Management Risks Security Management Plan Steps In Detail Remote Summary PDF
This slide provides information about the sixth step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Remote Access Control. Deliver an awe inspiring pitch with this creative techniques and strategies to reduce security management risks security management plan steps in detail remote summary pdf bundle. Topics like requirement for additional, remote access control, control security status can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
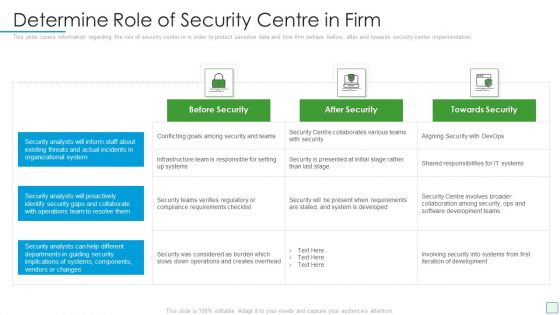
Developing Firm Security Strategy Plan Determine Role Of Security Centre In Firm Graphics PDF
This slide covers information regarding the role of security center in in order to protect sensitive data and how firm behave before, after and towards security center implementation. Deliver and pitch your topic in the best possible manner with this developing firm security strategy plan determine role of security centre in firm graphics pdf. Use them to share invaluable insights on before security, after security, towards security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Essential Elements Of Security Monitoring Plan Sample PDF
This slide provides information about some of the essential elements that must be a part of security monitoring plan in order to protect sensitive information. Deliver an awe inspiring pitch with this creative modern security observation plan to eradicate cybersecurity risk and data breach essential elements of security monitoring plan sample pdf bundle. Topics like critical infrastructure, cloud security, application security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
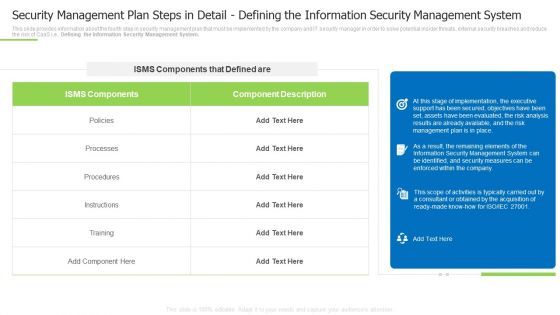
Security Management Plan Steps In Detail Defining The Information Security Management System Summary PDF
This slide provides information about the fourth step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Defining the Information Security Management System. Deliver and pitch your topic in the best possible manner with this security management plan steps in detail defining the information security management system summary pdf Use them to share invaluable insights on instructions, processes, implementation, the executive and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Techniques And Strategies To Reduce Security Management Risks Security Detail Risk Assessment And Analysis Template PDF
This slide provides information about the third step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Risk Assessment and Analysis. Deliver and pitch your topic in the best possible manner with this techniques and strategies to reduce security management risks security detail risk assessment and analysis template pdf Use them to share invaluable insights on security breach, perform a threat, several measures and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Organizational Security Solutions Quotes Ppt Model PDF
Deliver an awe inspiring pitch with this creative organizational security solutions quotes ppt model pdf bundle. Topics like quotes can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
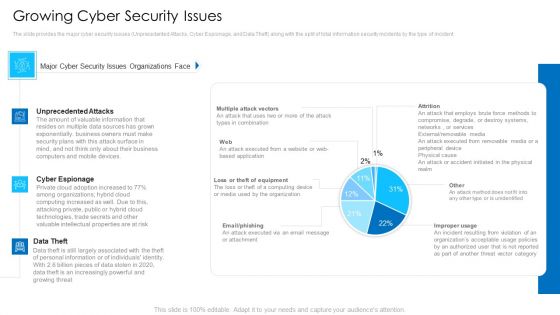
Growing Cyber Security Issues Mockup PDF
Deliver an awe inspiring pitch with this creative growing cyber security issues mockup pdf bundle. Topics like unprecedented attacks, cyber espionage, data theft can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Risk Management Assessment Checklist Mockup PDF
This slide shows a security risk management assessment checklist with multiple categories. Deliver an awe inspiring pitch with this creative security risk management assessment checklist mockup pdf bundle. Topics like information security policy document, identification of risks from third party, reporting security threat incidents can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
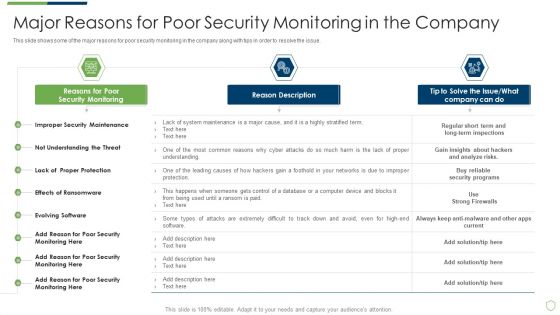
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Major Reasons For Poor Security Elements PDF
This slide shows some of the major reasons for poor security monitoring in the company along with tips in order to resolve the issue. Deliver an awe inspiring pitch with this creative modern security observation plan to eradicate cybersecurity risk and data breach major reasons for poor security elements pdf bundle. Topics like major reasons for poor security monitoring in the company can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
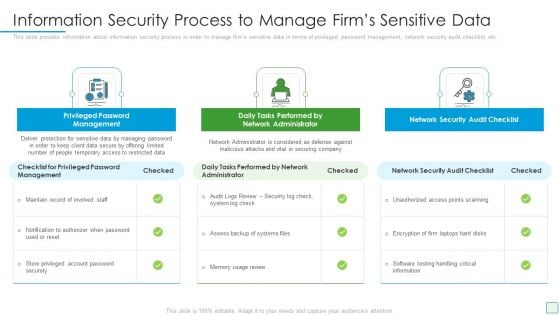
Developing Firm Security Strategy Plan Information Security Process To Manage Firms Sensitive Data Introduction PDF
This slide provides information about information security process in order to manage firms sensitive data in terms of privileged password management, network security audit checklist, etc. This is a developing firm security strategy plan information security process to manage firms sensitive data introduction pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like privileged password management, daily tasks performed by network administrator, network security audit checklist. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
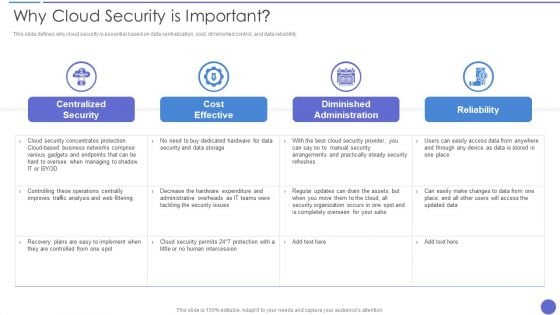
Why Cloud Security Is Important Demonstration PDF
This slide defines why cloud security is essential based on data centralization, cost, diminished control, and data reliability. Deliver an awe inspiring pitch with this creative Why Cloud Security Is Important Demonstration PDF bundle. Topics like Cost Effective, Centralized Security, Diminished Administration can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
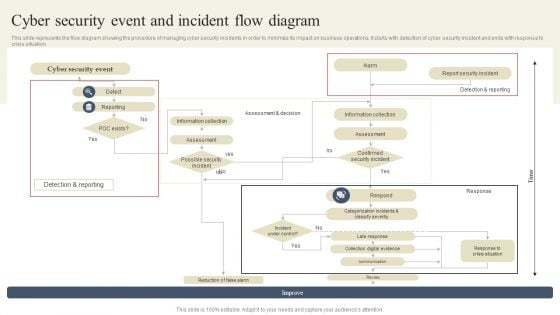
CYBER Security Breache Response Strategy Cyber Security Event And Incident Flow Diagram Sample PDF
This slide represents the flow diagram showing the procedure of managing cyber security incidents in order to minimize its impact on business operations. It starts with detection of cyber security incident and ends with response to crisis situation. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. CYBER Security Breache Response Strategy Cyber Security Event And Incident Flow Diagram Sample PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
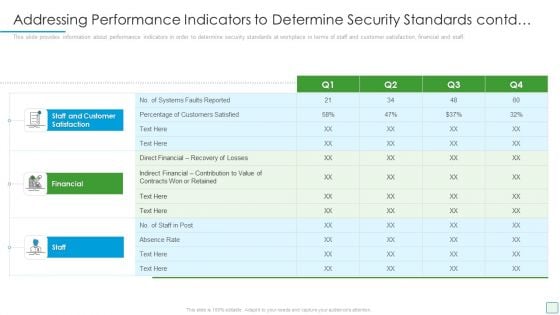
Developing Firm Security Strategy Plan Addressing Performance Indicators To Determine Security Standards Contd Themes PDF
This slide provides information about performance indicators in order to determine security standards at workplace in terms of staff and customer satisfaction, financial and staff. Deliver and pitch your topic in the best possible manner with this developing firm security strategy plan addressing performance indicators to determine security standards contd themes pdf. Use them to share invaluable insights on staff and customer satisfaction, financial, staff and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Developing Firm Security Strategy Plan Information Security Process To Manage Firms Sensitive Data Contd Brochure PDF
This slide provides information about information security process in order to manage firms sensitive data in terms of firewall audit checklist, VPN configuration, penetrating testing. Presenting developing firm security strategy plan information security process to manage firms sensitive data contd brochure pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like firewall audit checklist, vpn configuration, penetrating testing. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Developing Firm Security Strategy Plan Security Incidents Tracking Dashboard Alerts Graphics PDF
This slide portrays information regarding the dashboard that firm will track various incidents detected. These incidents will be managed in order to avoid security risks. Presenting developing firm security strategy plan security incidents tracking dashboard alerts graphics pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like application whitelisting, patch applications, patch operating systems, restrict admin privileges. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Project Security Administration IT Information Security Process To Manage Firms Sensitive Data Contd Graphics PDF
This slide provides information about information security process in order to manage firms sensitive data in terms of firewall audit checklist, VPN configuration, penetrating testing. Deliver and pitch your topic in the best possible manner with this project security administration it information security process to manage firms sensitive data contd graphics pdf. Use them to share invaluable insights on firewall audit checklist, vpn configuration, penetrating testing and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
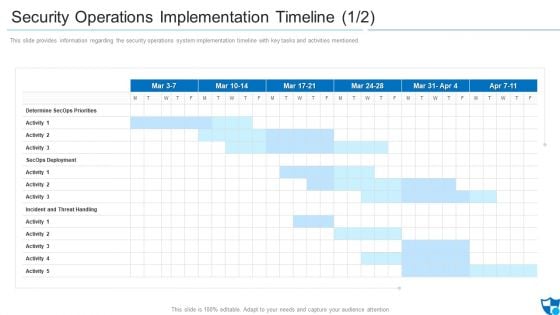
Security Operations Implementation Timeline Priorities Introduction PDF
This slide provides information regarding the security operations system implementation timeline with key tasks and activities mentioned.Deliver an awe inspiring pitch with this creative security operations implementation timeline priorities introduction pdf bundle. Topics like determine secops priorities, secops deployment, incident and threat handling can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
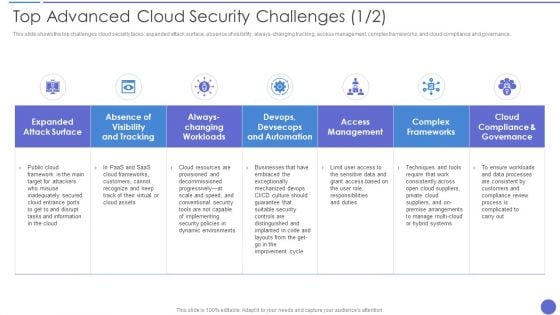
Top Advanced Cloud Security Challenges Brochure PDF
This slide shows the top challenges cloud security faces expanded attack surface, absence of visibility, always changing tracking, access management, complex frameworks, and cloud compliance and governance. Deliver an awe inspiring pitch with this creative Top Advanced Cloud Security Challenges Brochure PDF bundle. Topics like Complex Frameworks, Access Management, Dynamic Environments can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
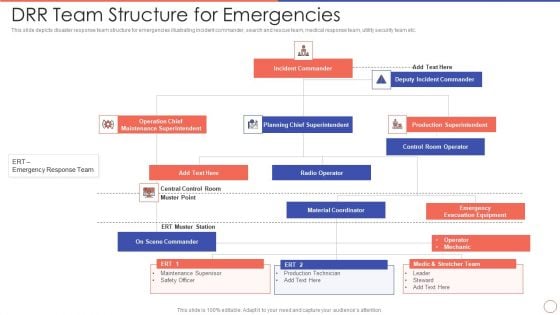
DRR Team Structure For Emergencies Ppt Layouts Outfit PDF
This slide depicts disaster response team structure for emergencies illustrating incident commander, search and rescue team, medical response team, utility security team etc. Presenting drr team structure for emergencies ppt layouts outfit pdf to dispense important information. This template comprises two stages. It also presents valuable insights into the topics including incident commander, production superintendent, radio operator, material coordinator, operation chief, maintenance superintendent. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
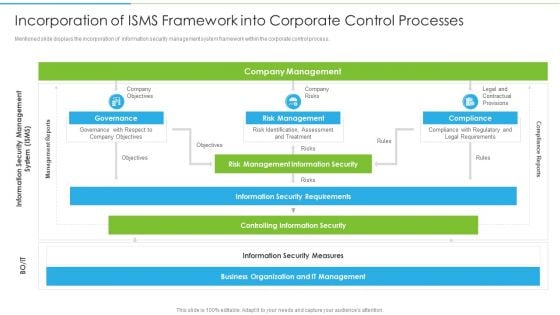
Ways To Accomplish ISO 27001 Accreditation Incorporation Of ISMS Framework Into Corporate Microsoft PDF
Mentioned slide displays the incorporation of information security management system framework within the corporate control process. This is a Ways To Accomplish ISO 27001 Accreditation Incorporation Of ISMS Framework Into Corporate Microsoft PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Company Objectives, Company Management, Company Risks. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Planning And Budgeting Sample Of Ppt Presentation
This is a planning and budgeting sample of ppt presentation. This is a eight stage process. The stages in this process are planning and budgeting, promoting stability and order, motivating and inspiring, aligning people, establishing direction, promoting change, controlling and problem solving, organizing and staffing.
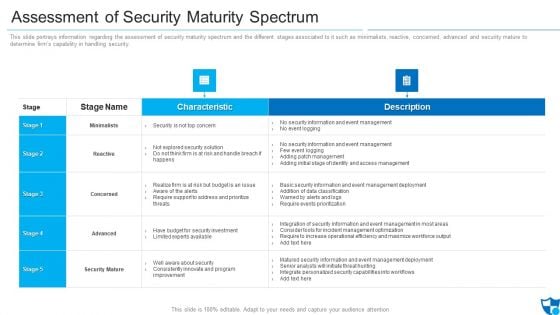
Assessment Of Security Maturity Spectrum Clipart PDF
This slide portrays information regarding the assessment of security maturity spectrum and the different stages associated to it such as minimalists, reactive, concerned, advanced and security mature to determine firms capability in handling security. Deliver an awe inspiring pitch with this creative assessment of security maturity spectrum clipart pdf bundle. Topics like security is not top concern, require support to address, improvement can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Web Application Development Best Practices Ppt Inspiration Tips Pdf
This slide represents best practices of web application development for users. It includes various practices such as take right tech stack, build attractive design, use robust CMS and ensure security. Showcasing this set of slides titled Web Application Development Best Practices Ppt Inspiration Tips Pdf. The topics addressed in these templates are Right Tech Stack, Build Attractive Design, Use Robust CMS. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide represents best practices of web application development for users. It includes various practices such as take right tech stack, build attractive design, use robust CMS and ensure security.

Stock Photo Unlocked Money With Key For Security Concept PowerPoint Slide
This image slide displays unlocked money security concept with key. This image slide has been designed with dollar bundle locked with padlock and key. This image slide may be used in your presentations to express views on finance, savings, protection and accounting business finance. Create professional presentations using this image slide.

Automated Government Procedures Government To Consumer Services Demonstration PDF
Our IT Solutions enable seamless and secure interactions between governments and citizens. We support these interactions through powerful government IT applications and a robust infrastructure. Deliver an awe-inspiring pitch with this creative automated government procedures government to consumer services demonstration pdf bundle. Topics like government to consumer services can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
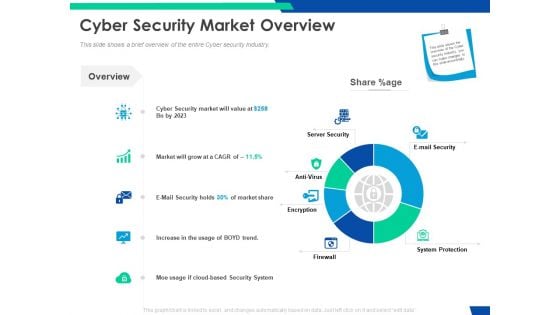
Cloud Based Email Security Market Report Cyber Security Market Overview Ppt Infographics Format PDF
This slide shows a brief overview of the entire Cyber security Industry. Deliver an awe inspiring pitch with this creative cloud based email security market report cyber security market overview ppt infographics format pdf bundle. Topics like cyber security market overview can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.


 Continue with Email
Continue with Email

 Home
Home


































