Safety Summary
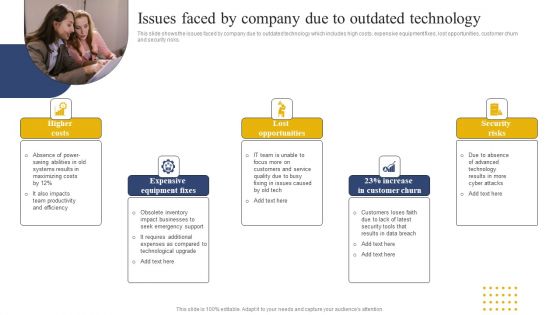
Transition Plan For Business Management Issues Faced By Company Due To Outdated Technology Introduction PDF
This slide shows the issues faced by company due to outdated technology which includes high costs, expensive equipment fixes, lost opportunities, customer churn and security risks. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Transition Plan For Business Management Issues Faced By Company Due To Outdated Technology Introduction PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Transition Plan For Business Management Issues Faced By Company Due To Outdated Technology Introduction PDF

Critical Measures For Ensuring How Firm Handle Various Insider Threats At Workplace Graphics PDF
This slide provides information regarding how firm will handle insider threats through employee training, IT security and HR coordination, etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Critical Measures For Ensuring How Firm Handle Various Insider Threats At Workplace Graphics PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Critical Measures For Ensuring How Firm Handle Various Insider Threats At Workplace Graphics PDF.
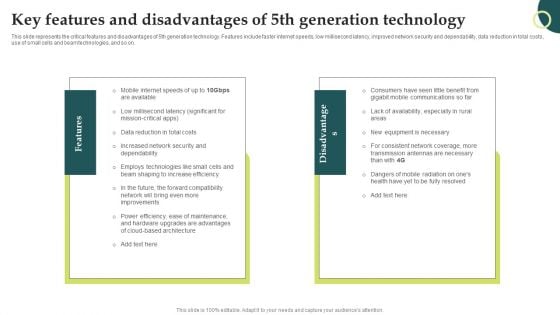
Evolution Of Wireless Technologies Key Features And Disadvantages Of 5Th Generation Structure PDF
This slide represents the critical features and disadvantages of 5th generation technology. Features include faster internet speeds, low millisecond latency, improved network security and dependability, data reduction in total costs, use of small cells and beam technologies, and so on. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Evolution Of Wireless Technologies Key Features And Disadvantages Of 5Th Generation Structure PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Cybersecurity Guidelines IT Email And Chat Policy Objective And Guidelines Introduction PDF
This slide represents the email and chat policy, including its objective and general guidelines. It also includes the ways to ensure email security which covers the installation of antivirus and spam filters. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Cybersecurity Guidelines IT Email And Chat Policy Objective And Guidelines Introduction PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
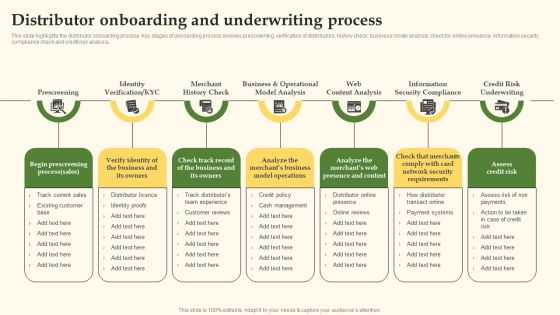
Distributor Onboarding And Underwriting Process Slides PDF
This slide highlights the distributor onboarding process. Key stages of onboarding process involves prescreening, verification of distributors, history check, business model analysis, check for online presence, information security compliance check and credit risk analysis. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Distributor Onboarding And Underwriting Process Slides PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Distributor Onboarding And Underwriting Process Slides PDF.
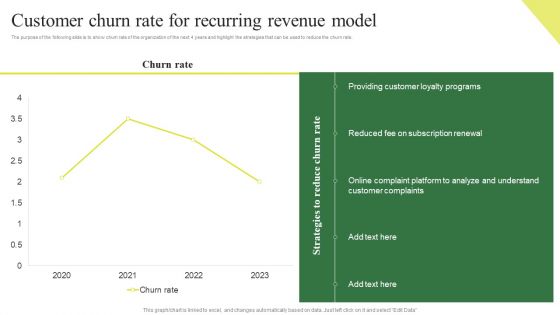
Consumption Based Pricing Model Customer Churn Rate For Recurring Revenue Model Information PDF
The purpose of the following slide is to show multiple challenges that the company can face while implementing a recurring revenue model , these challenges can be customer management, payment security and invoicing. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Consumption Based Pricing Model Customer Churn Rate For Recurring Revenue Model Information PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Consumption Based Pricing Model Customer Churn Rate For Recurring Revenue Model Information PDF
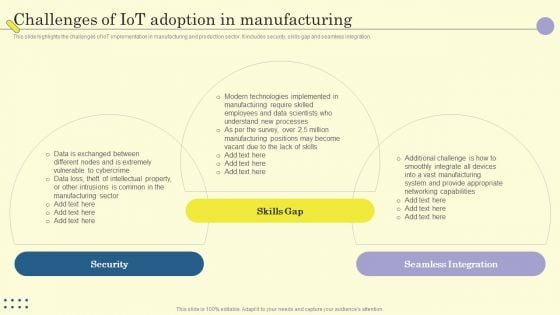
Internet Of Things In Manufacturing Sector Challenges Of Iot Adoption In Manufacturing Clipart PDF
This slide highlights the challenges of IoT implementation in manufacturing and production sector. It includes security, skills gap and seamless integration. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Internet Of Things In Manufacturing Sector Challenges Of Iot Adoption In Manufacturing Clipart PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
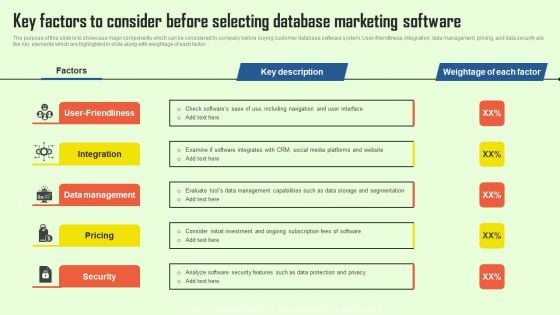
Increasing Consumer Engagement With Database Key Factors To Consider Before Selecting Microsoft PDF
The purpose of this slide is to showcase major components which can be considered by company before buying customer database software system. User-friendliness, integration, data management, pricing, and data security are the key elements which are highlighted in slide along with weightage of each factor. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Increasing Consumer Engagement With Database Key Factors To Consider Before Selecting Microsoft PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
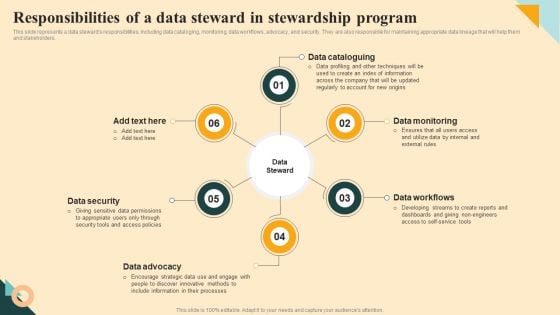
Responsibilities Of A Data Steward In Stewardship Program Diagrams PDF
This slide represents a data stewards responsibilities, including data cataloging, monitoring, data workflows, advocacy, and security. They are also responsible for maintaining appropriate data lineage that will help them and stakeholders. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Responsibilities Of A Data Steward In Stewardship Program Diagrams PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
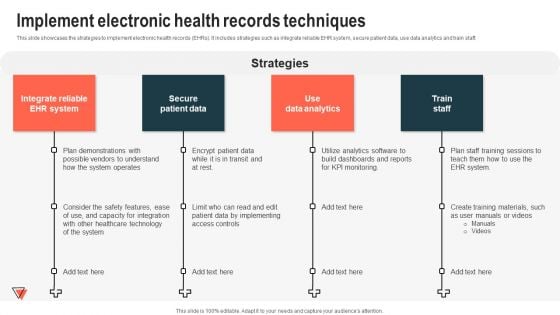
Implement Electronic Health Records Techniques Brochure PDF
This slide showcases the strategies to implement electronic health records EHRs. It includes strategies such as integrate reliable EHR system, secure patient data, use data analytics and train staff. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Implement Electronic Health Records Techniques Brochure PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Implement Electronic Health Records Techniques Brochure PDF
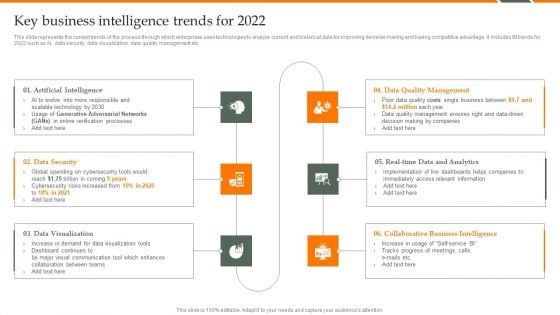
Human Resource Analytics Key Business Intelligence Trends For 2022 Elements PDF
This slide represents the current trends of the process through which enterprises uses technologies to analyze current and historical data for improving decision making and having competitive advantage. It includes BI trends for 2022 such as AI, data security, data visualization, data quality management etc. Welcome to our selection of the Human Resource Analytics Key Business Intelligence Trends For 2022 Elements PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.

Performing Cyber Training Exercises For Improving Cybersecurity With Incident Introduction PDF
Purpose of this slide is to address and perform various cyber training exercises in order to secure companys assets. Exercises covered are defense in depth, capture the flag etc.Welcome to our selection of the Performing Cyber Training Exercises For Improving Cybersecurity With Incident Introduction PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100precent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.
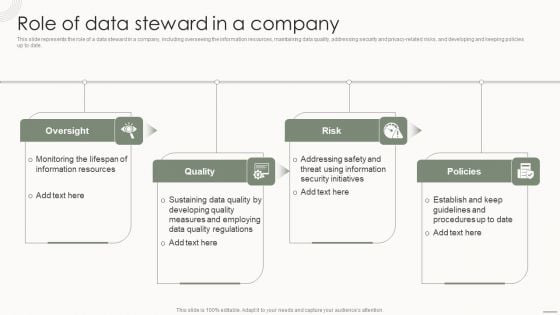
Data Governance IT Role Of Data Steward In A Company Demonstration PDF
This slide represents the role of a data steward in a company, including overseeing the information resources, maintaining data quality, addressing security and privacy related risks, and developing and keeping policies up to date. Welcome to our selection of the Data Governance IT Role Of Data Steward In A Company Demonstration PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.
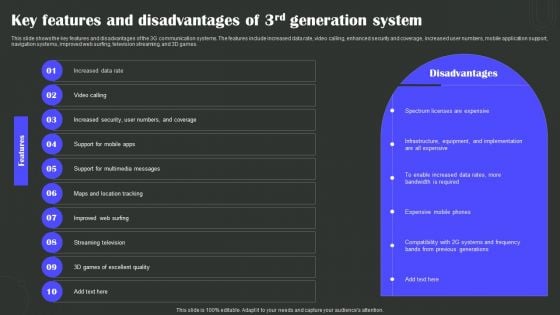
Key Features And Disadvantages Of 3Rd Generation System Wireless Technology Transformation Introduction PDF
This slide shows the key features and disadvantages of the 3G communication systems. The features include increased data rate, video calling, enhanced security and coverage, increased user numbers, mobile application support, navigation systems, improved web surfing, television streaming, and 3D games. Welcome to our selection of the Key Features And Disadvantages Of 3Rd Generation System Wireless Technology Transformation Introduction PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.

Implementing Smart Manufacturing Technology To Increase Productivity Major Impact Of Smart Factory On Enterprises Elements PDF
This slide represents major impacts of smart factory. It includes production process monitoring, asset visibility, data analysis and employee and asset security. Welcome to our selection of the Implementing Smart Manufacturing Technology To Increase Productivity Major Impact Of Smart Factory On Enterprises Elements PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.

Formulating Money Laundering Major Roles And Responsibilities Of Financial Themes PDF
The following slide Major roles and responsibilities of financial security department . It includes information about risk level determination, laws and regulations, team training, operational compliance, automatic workflows, red flags, etc. Welcome to our selection of the Formulating Money Laundering Major Roles And Responsibilities Of Financial Themes PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.
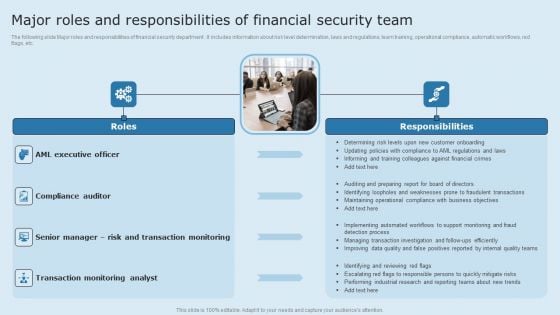
Actual Time Transaction Monitoring Software And Strategies Major Roles And Responsibilities Of Financial Slides PDF
The following slide Major roles and responsibilities of financial security department . It includes information about risk level determination, laws and regulations, team training, operational compliance, automatic workflows, red flags, etc. Welcome to our selection of the Actual Time Transaction Monitoring Software And Strategies Major Roles And Responsibilities Of Financial Slides PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.
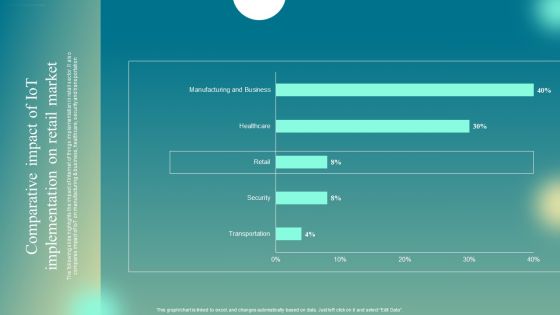
Comparative Impact Of Iot Implementation On Retail Market Clipart PDF
The following slide highlights the impact of Internet of things implementation in retail sector. It also compares impact of IoT on manufacturing and business, healthcare, security and transportation. Welcome to our selection of the Comparative Impact Of Iot Implementation On Retail Market Clipart PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today

Aiops Use Cases Related To Cloudops Devops And Secops Information PDF
This slide describes the AIOps use cases to automate cloudops, devops, and secops operations. This slide aims to showcase how aiops can be applied to multi-cloud operations, development environments, and secure applications in real-time. Welcome to our selection of the Aiops Use Cases Related To Cloudops Devops And Secops Information PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today
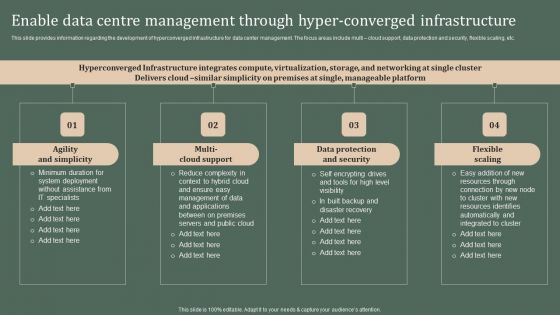
Deploying Corporate Aligned IT Strategy Enable Data Centre Management Through Hyper Converged Infrastructure Information PDF
This slide provides information regarding the development of hyperconverged infrastructure for data center management. The focus areas include multi cloud support, data protection and security, flexible scaling, etc. Welcome to our selection of the Deploying Corporate Aligned IT Strategy Enable Data Centre Management Through Hyper Converged Infrastructure Information PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.

E Commerce Operations In B2b Major Factors Affecting Selection For Ecommerce Designs PDF
This slide represents key factors that effect the selection for platform by b2b ecommerce business. It includes types of b2b business, sales team buy in, customer onboarding plan, platform integration and security. Welcome to our selection of the E Commerce Operations In B2b Major Factors Affecting Selection For Ecommerce Designs PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.
Heroku Cloud Application Impact On Customer Icons PDF
This slide highlights overall impact of Heroku cloud application on customers of industries using this platform. It further includes various impacts such as customer experience, accessibility, privacy and security, and future readiness. Welcome to our selection of the Heroku Cloud Application Impact On Customer Icons PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today

Outliers Model For Predictive Analytics Predictive Analytics For Improved Professional Pdf
This slide talks about the outliers model used for predictive analytics, including its use cases, impact and algorithm used in it, such as the generalized linear model for two values. This model helps banking, finance, and cyber security organizations to detect fraud and cyber crimes. Find highly impressive Outliers Model For Predictive Analytics Predictive Analytics For Improved Professional Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Outliers Model For Predictive Analytics Predictive Analytics For Improved Professional Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now. This slide talks about the outliers model used for predictive analytics, including its use cases, impact and algorithm used in it, such as the generalized linear model for two values. This model helps banking, finance, and cyber security organizations to detect fraud and cyber crimes.
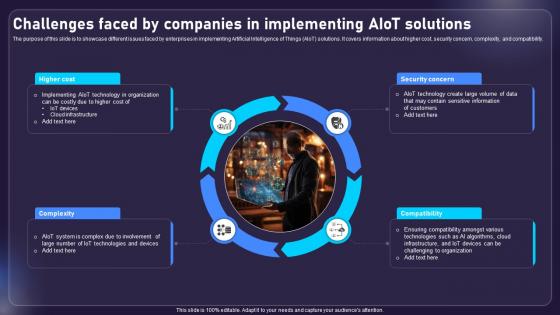
Challenges Faced By Companies In Implementing AIOT Applications For Various Industries IoT SS V
The purpose of this slide is to showcase different issues faced by enterprises in implementing Artificial Intelligence of Things AIoT solutions. It covers information about higher cost, security concern, complexity, and compatibility. Find highly impressive Challenges Faced By Companies In Implementing AIOT Applications For Various Industries IoT SS V on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Challenges Faced By Companies In Implementing AIOT Applications For Various Industries IoT SS V for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now The purpose of this slide is to showcase different issues faced by enterprises in implementing Artificial Intelligence of Things AIoT solutions. It covers information about higher cost, security concern, complexity, and compatibility.
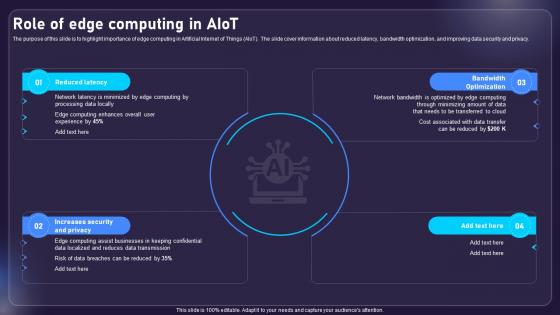
Role Of Edge Computing In AIOT Applications For Various Industries IoT SS V
The purpose of this slide is to highlight importance of edge computing in Artificial Internet of Things AIoT. The slide cover information about reduced latency, bandwidth optimization, and improving data security and privacy. Find highly impressive Role Of Edge Computing In AIOT Applications For Various Industries IoT SS V on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Role Of Edge Computing In AIOT Applications For Various Industries IoT SS V for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now The purpose of this slide is to highlight importance of edge computing in Artificial Internet of Things AIoT. The slide cover information about reduced latency, bandwidth optimization, and improving data security and privacy.

Comparing Decentralized And Centralized Complete Roadmap To Blockchain BCT SS V
This slide covers comparison between two cryptocurrencies based on different factors. It includes factors such as range of crypto offerings, supporting fiat currencies, user friendliness and funds custodian, privacy, security, liquidity and adoption rates for centralized and decentralized crypto exchanges. Find highly impressive Comparing Decentralized And Centralized Complete Roadmap To Blockchain BCT SS V on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Comparing Decentralized And Centralized Complete Roadmap To Blockchain BCT SS V for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide covers comparison between two cryptocurrencies based on different factors. It includes factors such as range of crypto offerings, supporting fiat currencies, user friendliness and funds custodian, privacy, security, liquidity and adoption rates for centralized and decentralized crypto exchanges.

Resources And Training That Companies Man In The Middle Phishing IT
This slide demonstrates the resources and training that can be provided by companies to their staff. These include employee training, check to see if youve already been breached, be aware of the various phishing attacks, invest in security education, etc. Find highly impressive Resources And Training That Companies Man In The Middle Phishing IT on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Resources And Training That Companies Man In The Middle Phishing IT for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide demonstrates the resources and training that can be provided by companies to their staff. These include employee training, check to see if youve already been breached, be aware of the various phishing attacks, invest in security education, etc.

IoT Device Management Fundamentals IoT Device Update Management Process IoT Ss V
This slide exhibits IoT device management and maintenance process in order to avoid security threats. It includes steps such as analyse IoT fleet, Create backup, Test updates, schedule plan, divide fleet into groups, execute updates, and collect feedback. Find highly impressive IoT Device Management Fundamentals IoT Device Update Management Process IoT SS V on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download IoT Device Management Fundamentals IoT Device Update Management Process IoT SS V for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide exhibits IoT device management and maintenance process in order to avoid security threats. It includes steps such as analyse IoT fleet, Create backup, Test updates, schedule plan, divide fleet into groups, execute updates, and collect feedback.
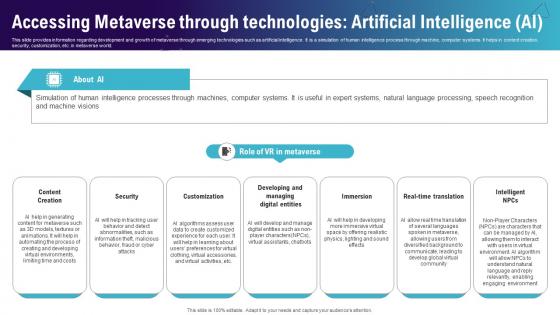
Accessing Metaverse Through Technologies Artificial Continuum Of Technology Revamping Business AI SS V
This slide provides information regarding development and growth of metaverse through emerging technologies such as artificial intelligence. It is a simulation of human intelligence process through machine, computer systems. It helps in content creation, security, customization, etc. in metaverse world. Create an editable Accessing Metaverse Through Technologies Artificial Continuum Of Technology Revamping Business AI SS V that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Accessing Metaverse Through Technologies Artificial Continuum Of Technology Revamping Business AI SS V is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide provides information regarding development and growth of metaverse through emerging technologies such as artificial intelligence. It is a simulation of human intelligence process through machine, computer systems. It helps in content creation, security, customization, etc. in metaverse world.

Technologies Used To Protect Data In Confidential Computing Technologies Guidelines Pdf
This slide depicts the related technologies used to protect the information in processing. The purpose of this slide is to showcase the technologies and comparison between these technologies based on security and scalability. The technologies include homomorphic encryption, multi-party computation, and so on. Present like a pro with Technologies Used To Protect Data In Confidential Computing Technologies Guidelines Pdf Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide depicts the related technologies used to protect the information in processing. The purpose of this slide is to showcase the technologies and comparison between these technologies based on security and scalability. The technologies include homomorphic encryption, multi-party computation, and so on.

Mastering Blockchain Wallets Nice To Have Features For Blockchain Wallet BCT SS V
This slide covers top attributes of blockchain wallet applications allowing users to perform various functions. It includes features related to user authorization, QR code scanner, importing paper wallets, using multiple currencies, enabling push notification, creating secure payment gateways, 24 or 7 customer support, etc. Present like a pro with Mastering Blockchain Wallets Nice To Have Features For Blockchain Wallet BCT SS V. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide covers top attributes of blockchain wallet applications allowing users to perform various functions. It includes features related to user authorization, QR code scanner, importing paper wallets, using multiple currencies, enabling push notification, creating secure payment gateways, 24 or 7 customer support, etc.

Design Software Playbook Engineers Software Testing Methodologies- Acceptance Testing Mockup PDF
This template covers software testing methodologies such as functional testing and non functional testing. It also includes types of functional and non functional testing such as unit, integration, system, acceptance testing, performance, security, usability and compatibility testing. Slidegeeks has constructed Design Software Playbook Engineers Software Testing Methodologies- Acceptance Testing Mockup PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

Importance Of Software Defined Networking SDN Evolution Of SDN Controllers Demonstration Pdf
This slide depicts the importance of software-defined networking that allows network administrators to design, create, and run their networks innovatively. It includes high security, programmable network infrastructure, and incredible speed and flexibility with increased control. Explore a selection of the finest Importance Of Software Defined Networking SDN Evolution Of SDN Controllers Demonstration Pdf here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Importance Of Software Defined Networking SDN Evolution Of SDN Controllers Demonstration Pdf to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide depicts the importance of software-defined networking that allows network administrators to design, create, and run their networks innovatively. It includes high security, programmable network infrastructure, and incredible speed and flexibility with increased control.
Data Stewardship In Business Processes Uses Of Data Stewardship Program Icons Pdf
This slide represents the uses of a data stewardship program that includes resolving any data or data related challenges, decreasing risks by security measures, improving data documentation, developing and using quality measures, and so on. Explore a selection of the finest Data Stewardship In Business Processes Uses Of Data Stewardship Program Icons Pdf here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Data Stewardship In Business Processes Uses Of Data Stewardship Program Icons Pdf to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide represents the uses of a data stewardship program that includes resolving any data or data related challenges, decreasing risks by security measures, improving data documentation, developing and using quality measures, and so on.
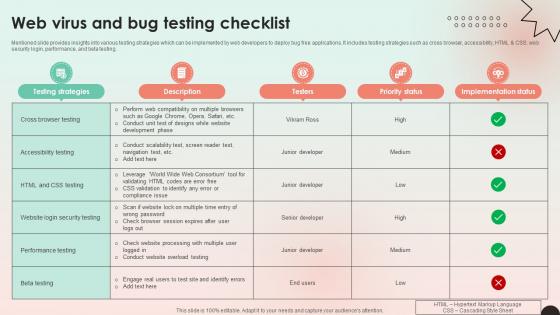
Web Consulting Business Web Virus And Bug Testing Checklist
Mentioned slide provides insights into various testing strategies which can be implemented by web developers to deploy bug free applications. It includes testing strategies such as cross browser, accessibility, HTML and CSS, web security login, performance, and beta testing. Explore a selection of the finest Web Consulting Business Web Virus And Bug Testing Checklist here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Web Consulting Business Web Virus And Bug Testing Checklist to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. Mentioned slide provides insights into various testing strategies which can be implemented by web developers to deploy bug free applications. It includes testing strategies such as cross browser, accessibility, HTML and CSS, web security login, performance, and beta testing.
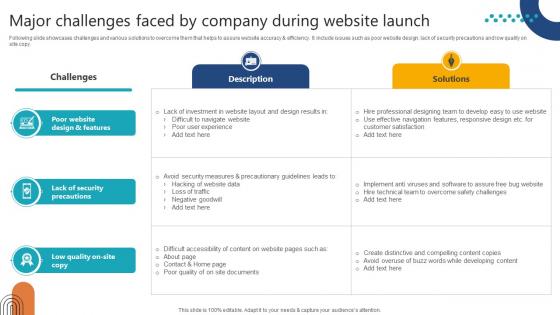
Complete Guide To Launch Major Challenges Faced By Company During Website
Following slide showcases challenges and various solutions to overcome them that helps to assure website accuracy and efficiency. It include issues such as poor website design, lack of security precautions and low quality on site copy. Explore a selection of the finest Complete Guide To Launch Major Challenges Faced By Company During Website here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Complete Guide To Launch Major Challenges Faced By Company During Website to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. Following slide showcases challenges and various solutions to overcome them that helps to assure website accuracy and efficiency. It include issues such as poor website design, lack of security precautions and low quality on site copy.
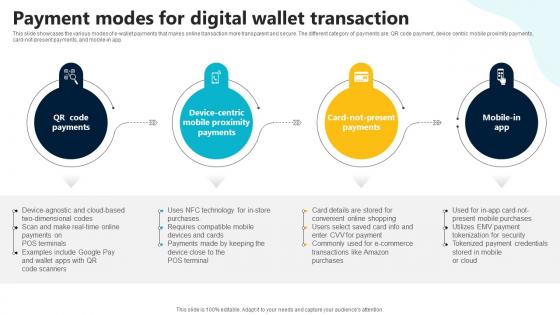
Payment Modes For Digital Wallet Transaction In Depth Guide To Digital Wallets Fin SS V
This slide showcases the various modes of e-wallet payments that makes online transaction more transparent and secure. The different category of payments are QR code payment, device centric mobile proximity payments, card-not-present payments, and mobile-in app. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Payment Modes For Digital Wallet Transaction In Depth Guide To Digital Wallets Fin SS V can be your best option for delivering a presentation. Represent everything in detail using Payment Modes For Digital Wallet Transaction In Depth Guide To Digital Wallets Fin SS V and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide showcases the various modes of e-wallet payments that makes online transaction more transparent and secure. The different category of payments are QR code payment, device centric mobile proximity payments, card-not-present payments, and mobile-in app.
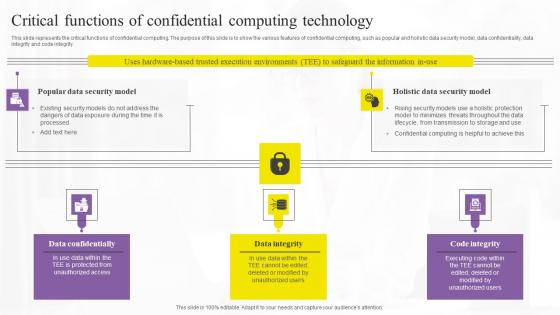
Critical Functions Of Confidential Computing Technology Demonstration Pdf
This slide represents the critical functions of confidential computing. The purpose of this slide is to show the various features of confidential computing, such as popular and holistic data security model, data confidentiality, data integrity and code integrity. Presenting this PowerPoint presentation, titled Critical Functions Of Confidential Computing Technology Demonstration Pdf, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Critical Functions Of Confidential Computing Technology Demonstration Pdf. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Critical Functions Of Confidential Computing Technology Demonstration Pdf that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide represents the critical functions of confidential computing. The purpose of this slide is to show the various features of confidential computing, such as popular and holistic data security model, data confidentiality, data integrity and code integrity.
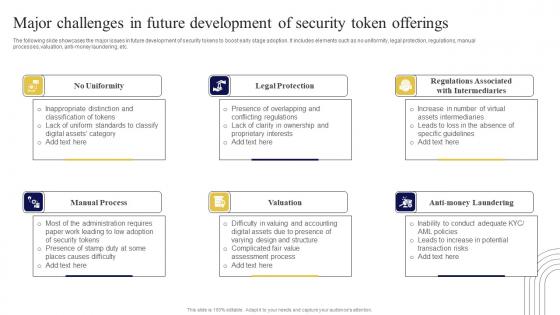
Major Challenges In Future Development Exploring Investment Opportunities Portrait Pdf
The following slide showcases the major issues in future development of security tokens to boost early stage adoption. It includes elements such as no uniformity, legal protection, regulations, manual processes, valuation, anti-money laundering, etc. Presenting this PowerPoint presentation, titled Major Challenges In Future Development Exploring Investment Opportunities Portrait Pdf, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Major Challenges In Future Development Exploring Investment Opportunities Portrait Pdf. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Major Challenges In Future Development Exploring Investment Opportunities Portrait Pdf that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. The following slide showcases the major issues in future development of security tokens to boost early stage adoption. It includes elements such as no uniformity, legal protection, regulations, manual processes, valuation, anti-money laundering, etc.

Unlocking The Potential Of Traditional Vs Blockchain Gaming Comparative BCT SS V
This slide showcases a comparative analysis between traditional gaming and blockchain enabled gaming. Basis of differentiation include ownership of assets, decentralization, security, gameplay and monetization. Presenting this PowerPoint presentation, titled Unlocking The Potential Of Traditional Vs Blockchain Gaming Comparative BCT SS V, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Unlocking The Potential Of Traditional Vs Blockchain Gaming Comparative BCT SS V. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Unlocking The Potential Of Traditional Vs Blockchain Gaming Comparative BCT SS V that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide showcases a comparative analysis between traditional gaming and blockchain enabled gaming. Basis of differentiation include ownership of assets, decentralization, security, gameplay and monetization.
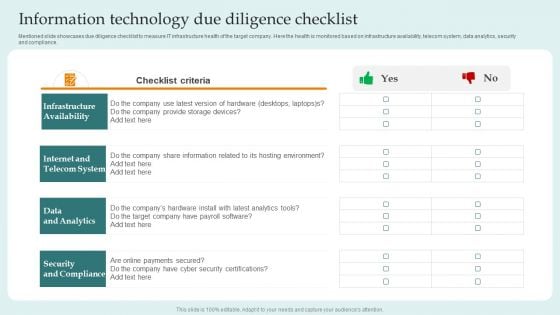
Information Technology Due Diligence Checklist Guide For Successful Merger And Acquisition Pictures PDF
Mentioned slide showcases due diligence checklist to measure IT infrastructure health of the target company. Here the health is monitored based on infrastructure availability, telecom system, data analytics, security and compliance.Slidegeeks has constructed Information Technology Due Diligence Checklist Guide For Successful Merger And Acquisition Pictures PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.
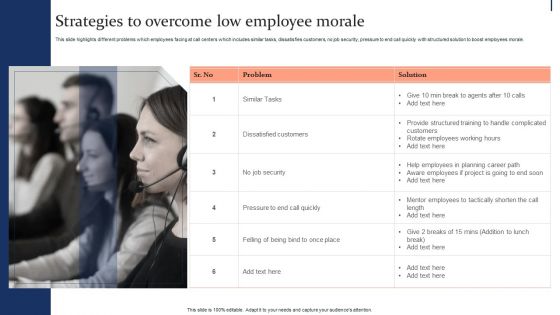
Quality Enhancement Strategic Strategies To Overcome Low Employee Morale Infographics PDF
This slide highlights different problems which employees facing at call centers which includes similar tasks, dissatisfies customers, no job security, pressure to end call quickly with structured solution to boost employees morale. Slidegeeks has constructed Quality Enhancement Strategic Strategies To Overcome Low Employee Morale Infographics PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.
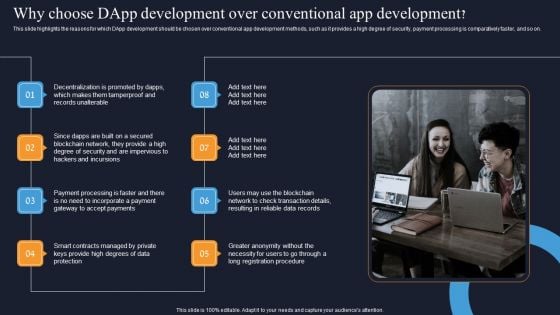
Why Choose Dapp Development Over Conventional App Development Elements PDF
This slide highlights the reasons for which DApp development should be chosen over conventional app development methods, such as it provides a high degree of security, payment processing is comparatively faster, and so on. Slidegeeks has constructed Why Choose Dapp Development Over Conventional App Development Elements PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.

Nike Emotional Branding Strategy Key Strategies For Brands To Empower Customers Structure PDF
This slide showcases major branding techniques to empower customers which can assist managers in retaining them for long run. It provides details such as technology, support desk, security, feedback, compliance, etc. Slidegeeks has constructed Nike Emotional Branding Strategy Key Strategies For Brands To Empower Customers Structure PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.
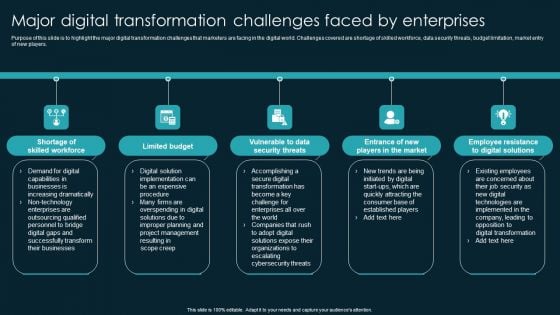
Major Digital Transformation Challenges Faced By Enterprises Diagrams PDF
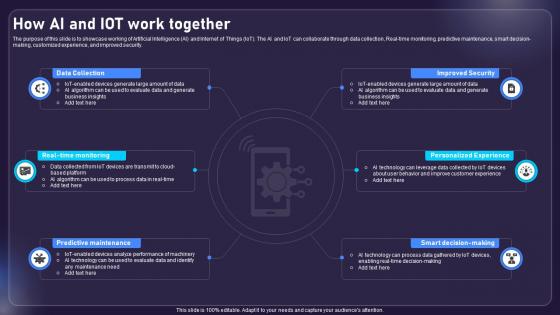
How Ai And Iot Work Together AIOT Applications For Various Industries IoT SS V
The purpose of this slide is to showcase working of Artificial Intelligence AI and Internet of Things IoT. The AI and IoT can collaborate through data collection, Real-time monitoring, predictive maintenance, smart decision-making, customized experience, and improved security. This How Ai And Iot Work Together AIOT Applications For Various Industries IoT SS V is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The How Ai And Iot Work Together AIOT Applications For Various Industries IoT SS V features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today The purpose of this slide is to showcase working of Artificial Intelligence AI and Internet of Things IoT. The AI and IoT can collaborate through data collection, Real-time monitoring, predictive maintenance, smart decision-making, customized experience, and improved security.
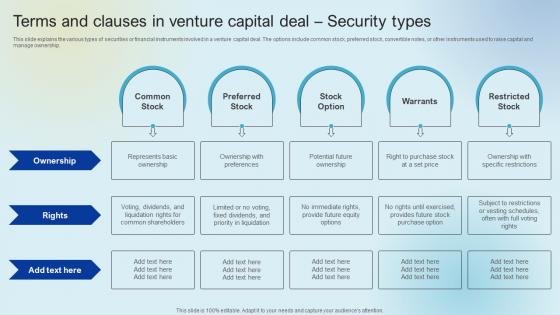
Terms And Clauses In Venture Raising Venture Capital A Holistic Approach Fin SS V
This slide explains the various types of securities or financial instruments involved in a venture capital deal. The options include common stock, preferred stock, convertible notes, or other instruments used to raise capital and manage ownership. This Terms And Clauses In Venture Raising Venture Capital A Holistic Approach Fin SS V is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Terms And Clauses In Venture Raising Venture Capital A Holistic Approach Fin SS V features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide explains the various types of securities or financial instruments involved in a venture capital deal. The options include common stock, preferred stock, convertible notes, or other instruments used to raise capital and manage ownership.

Zero Trust Model Zero Trust Network Access Architectural Models
This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption. This Zero Trust Model Zero Trust Network Access Architectural Models is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Zero Trust Model Zero Trust Network Access Architectural Models features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption.

Zero Trust Network Access Architectural Models Software Defined Perimeter SDP
This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption. This Zero Trust Network Access Architectural Models Software Defined Perimeter SDP is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Zero Trust Network Access Architectural Models Software Defined Perimeter SDP features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption.
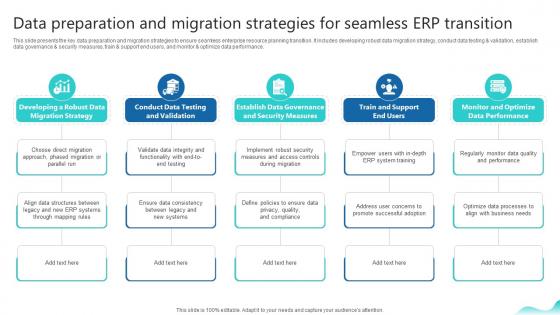
Data Preparation And Migration Strategies For Seamless Erp And Digital Transformation For Maximizing DT SS V
This slide presents the key data preparation and migration strategies to ensure seamless enterprise resource planning transition. It includes developing robust data migration strategy, conduct data testing and validation, establish data governance and security measures, train and support end users, and monitor and optimize data performance. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Data Preparation And Migration Strategies For Seamless Erp And Digital Transformation For Maximizing DT SS V template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Data Preparation And Migration Strategies For Seamless Erp And Digital Transformation For Maximizing DT SS V that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide presents the key data preparation and migration strategies to ensure seamless enterprise resource planning transition. It includes developing robust data migration strategy, conduct data testing and validation, establish data governance and security measures, train and support end users, and monitor and optimize data performance.
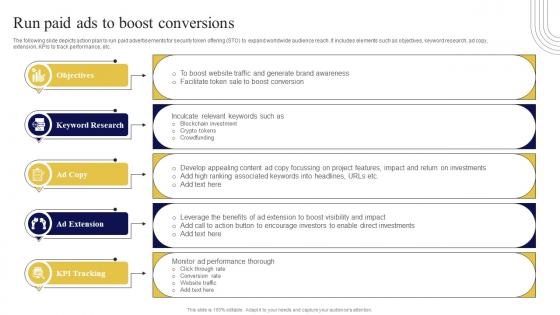
Run Paid Ads To Boost Conversions Exploring Investment Opportunities Diagrams Pdf
The following slide depicts action plan to run paid advertisements for security token offering STO to expand worldwide audience reach. It includes elements such as objectives, keyword research, ad copy, extension, KPIs to track performance, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Run Paid Ads To Boost Conversions Exploring Investment Opportunities Diagrams Pdf can be your best option for delivering a presentation. Represent everything in detail using Run Paid Ads To Boost Conversions Exploring Investment Opportunities Diagrams Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. The following slide depicts action plan to run paid advertisements for security token offering STO to expand worldwide audience reach. It includes elements such as objectives, keyword research, ad copy, extension, KPIs to track performance, etc.
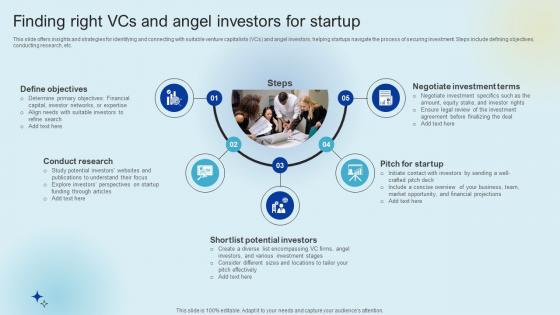
Finding Right VCS And Angel Investors For Startup Raising Venture Capital A Holistic Approach Fin SS V
This slide offers insights and strategies for identifying and connecting with suitable venture capitalists VCs and angel investors, helping startups navigate the process of securing investment. Steps include defining objectives, conducting research, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Finding Right VCS And Angel Investors For Startup Raising Venture Capital A Holistic Approach Fin SS V can be your best option for delivering a presentation. Represent everything in detail using Finding Right VCS And Angel Investors For Startup Raising Venture Capital A Holistic Approach Fin SS V and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide offers insights and strategies for identifying and connecting with suitable venture capitalists VCs and angel investors, helping startups navigate the process of securing investment. Steps include defining objectives, conducting research, etc.

Zero Trust Model Timeline To Implement Zero Trust Network Access
This slide showcases the timeline for implementing the ZTNA security model. This slide highlights the various steps organizations will take while deploying the ZTNA system, forming a dedicated team, choosing zero-trust implementation on-ramp, assessing the environment and so on. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Zero Trust Model Timeline To Implement Zero Trust Network Access can be your best option for delivering a presentation. Represent everything in detail using Zero Trust Model Timeline To Implement Zero Trust Network Access and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide showcases the timeline for implementing the ZTNA security model. This slide highlights the various steps organizations will take while deploying the ZTNA system, forming a dedicated team, choosing zero-trust implementation on-ramp, assessing the environment and so on.
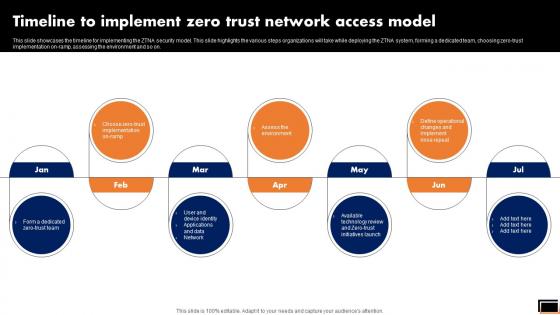
Timeline To Implement Zero Trust Network Access Model Software Defined Perimeter SDP
This slide showcases the timeline for implementing the ZTNA security model. This slide highlights the various steps organizations will take while deploying the ZTNA system, forming a dedicated team, choosing zero-trust implementation on-ramp, assessing the environment and so on. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Timeline To Implement Zero Trust Network Access Model Software Defined Perimeter SDP can be your best option for delivering a presentation. Represent everything in detail using Timeline To Implement Zero Trust Network Access Model Software Defined Perimeter SDP and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide showcases the timeline for implementing the ZTNA security model. This slide highlights the various steps organizations will take while deploying the ZTNA system, forming a dedicated team, choosing zero-trust implementation on-ramp, assessing the environment and so on.
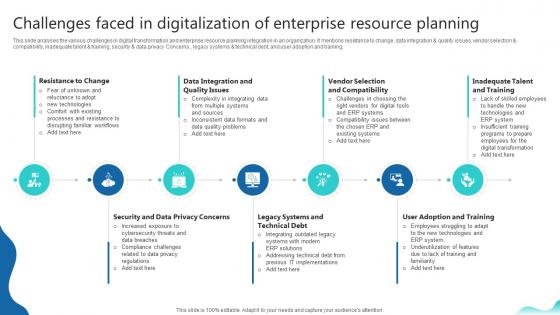
Challenges Faced In Digitalization Of Enterprise Erp And Digital Transformation For Maximizing DT SS V
This slide analyses the various challenges in digital transformation and enterprise resource planning integration in an organization. It mentions resistance to change, data integration and quality issues, vendor selection and compatibility, inadequate talent and training, security and data privacy Concerns , legacy systems and technical debt, and user adoption and training.Whether you have daily or monthly meetings, a brilliant presentation is necessary. Challenges Faced In Digitalization Of Enterprise Erp And Digital Transformation For Maximizing DT SS V can be your best option for delivering a presentation. Represent everything in detail using Challenges Faced In Digitalization Of Enterprise Erp And Digital Transformation For Maximizing DT SS V and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide analyses the various challenges in digital transformation and enterprise resource planning integration in an organization. It mentions resistance to change, data integration and quality issues, vendor selection and compatibility, inadequate talent and training, security and data privacy Concerns , legacy systems and technical debt, and user adoption and training.
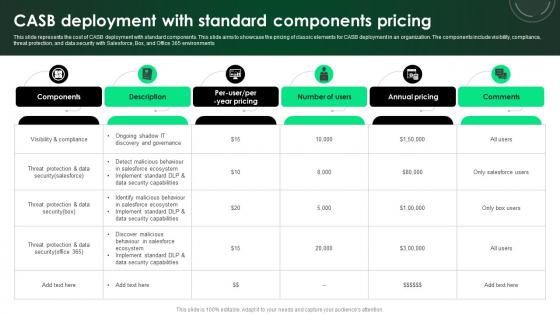
CASB 2 0 IT CASB Deployment With Standard Components Pricing
This slide represents the cost of CASB deployment with standard components. This slide aims to showcase the pricing of classic elements for CASB deployment in an organization. The components include visibility, compliance, threat protection, and data security with Salesforce, Box, and Office 365 environments. Whether you have daily or monthly meetings, a brilliant presentation is necessary. CASB 2 0 IT CASB Deployment With Standard Components Pricing can be your best option for delivering a presentation. Represent everything in detail using CASB 2 0 IT CASB Deployment With Standard Components Pricing and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide represents the cost of CASB deployment with standard components. This slide aims to showcase the pricing of classic elements for CASB deployment in an organization. The components include visibility, compliance, threat protection, and data security with Salesforce, Box, and Office 365 environments
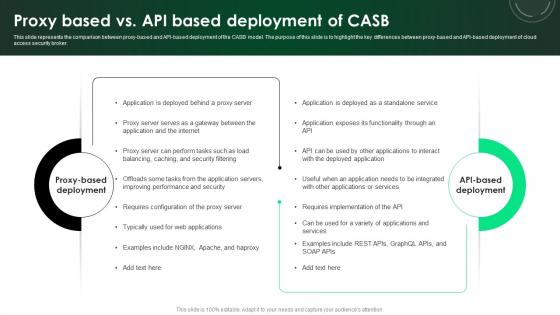
CASB 2 0 IT Proxy Based Vs API Based Deployment Of CASB
This slide represents the comparison between proxy-based and API-based deployment of the CASB model. The purpose of this slide is to highlight the key differences between proxy-based and API-based deployment of cloud access security broker. Whether you have daily or monthly meetings, a brilliant presentation is necessary. CASB 2 0 IT Proxy Based Vs API Based Deployment Of CASB can be your best option for delivering a presentation. Represent everything in detail using CASB 2 0 IT Proxy Based Vs API Based Deployment Of CASB and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide represents the comparison between proxy-based and API-based deployment of the CASB model. The purpose of this slide is to highlight the key differences between proxy-based and API-based deployment of cloud access security broker.

Digital Wallet Delivery Technology For Payment In Depth Guide To Digital Wallets Fin SS V
The following slide highlights the various technologies used in digital wallets for payment processing. The different technologies are near field communication. Magnetic secure transmission, and QR codes. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Digital Wallet Delivery Technology For Payment In Depth Guide To Digital Wallets Fin SS V can be your best option for delivering a presentation. Represent everything in detail using Digital Wallet Delivery Technology For Payment In Depth Guide To Digital Wallets Fin SS V and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. The following slide highlights the various technologies used in digital wallets for payment processing. The different technologies are near field communication. Magnetic secure transmission, and QR codes.
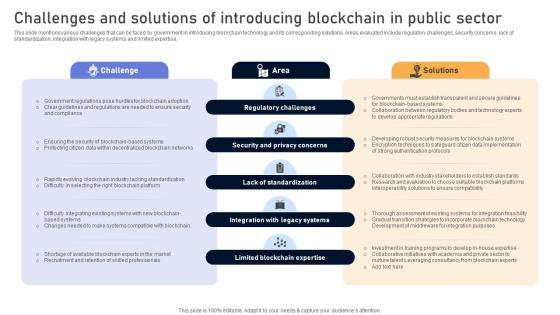
Comprehensive Look At Blockchain Challenges And Solutions Of Introducing BCT SS V
This slide mentions various challenges that can be faced by government in introducing blockchain technology and its corresponding solutions. Areas evaluated include regulatory challenges, security concerns, lack of standardization, integration with legacy systems and limited expertise. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Comprehensive Look At Blockchain Challenges And Solutions Of Introducing BCT SS V can be your best option for delivering a presentation. Represent everything in detail using Comprehensive Look At Blockchain Challenges And Solutions Of Introducing BCT SS V and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide mentions various challenges that can be faced by government in introducing blockchain technology and its corresponding solutions. Areas evaluated include regulatory challenges, security concerns, lack of standardization, integration with legacy systems and limited expertise.
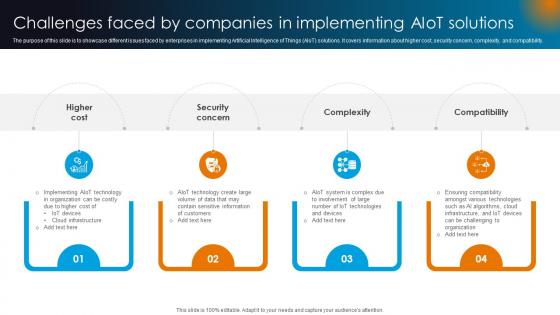
Integrating AI With IoT Challenges Faced By Companies In Implementing AIoT Solutions IoT SS V
The purpose of this slide is to showcase different issues faced by enterprises in implementing Artificial Intelligence of Things AIoT solutions. It covers information about higher cost, security concern, complexity, and compatibility. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Integrating AI With IoT Challenges Faced By Companies In Implementing AIoT Solutions IoT SS V can be your best option for delivering a presentation. Represent everything in detail using Integrating AI With IoT Challenges Faced By Companies In Implementing AIoT Solutions IoT SS V and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. The purpose of this slide is to showcase different issues faced by enterprises in implementing Artificial Intelligence of Things AIoT solutions. It covers information about higher cost, security concern, complexity, and compatibility.


 Continue with Email
Continue with Email

 Home
Home


































