Safety
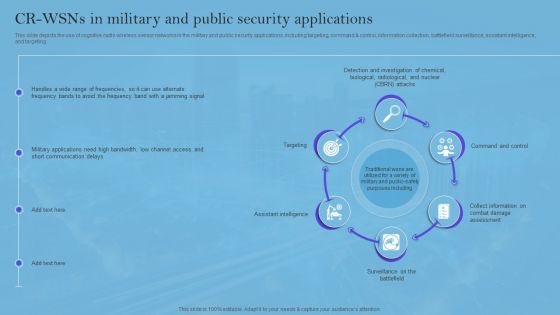
Smart Wireless Sensor Networks CR Wsns In Military And Public Security Applications Elements PDF
This slide depicts the use of cognitive radio wireless sensor networks in the military and public security applications, including targeting, command and control, information collection, battlefield surveillance, assistant intelligence, and targeting. Want to ace your presentation in front of a live audience Our Smart Wireless Sensor Networks CR Wsns In Military And Public Security Applications Elements PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.
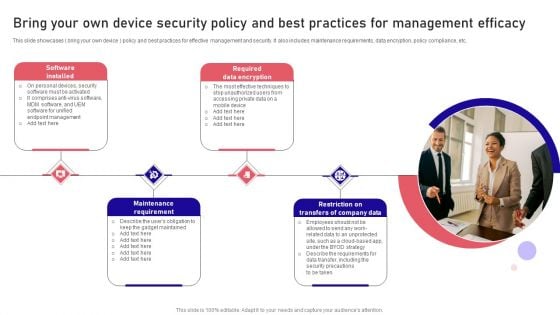
Bring Your Own Device Security Policy And Best Practices For Management Efficacy Summary PDF
This slide showcases bring your own device policy and best practices for effective management and security. It also includes maintenance requirements, data encryption, policy compliance, etc. Persuade your audience using this Bring Your Own Device Security Policy And Best Practices For Management Efficacy Summary PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Software Installed, Maintenance Requirement, Encryption . Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
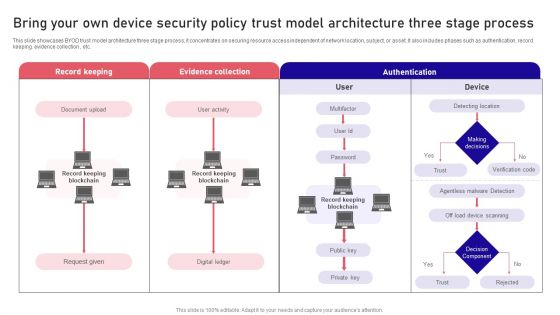
Bring Your Own Device Security Policy Trust Model Architecture Three Stage Process Rules PDF
This slide showcases BYOD trust model architecture three stage process, it concentrates on securing resource access independent of network location, subject, or asset. It also includes phases such as authentication, record keeping. evidence collection , etc. Persuade your audience using this Bring Your Own Device Security Policy Trust Model Architecture Three Stage Process Rules PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Record Keeping, Evidence Collection, Authentication . Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Steps To Enhance Bring Your Own Device Security Policy In Devices Icons PDF
This slide showcases steps to enhance bring your own device security to protect devices. It also includes steps such as cloud networks, password protection, routine back ups, data access, etc. Persuade your audience using this Steps To Enhance Bring Your Own Device Security Policy In Devices Icons PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Password Protection, Data Access, Antivirus Software. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Iot Integration In Manufacturing Managing Cyber Security In Manufacturing 30 Days Plan Template PDF
This slide describes the first 30 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. There are so many reasons you need a Iot Integration In Manufacturing Managing Cyber Security In Manufacturing 30 Days Plan Template PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
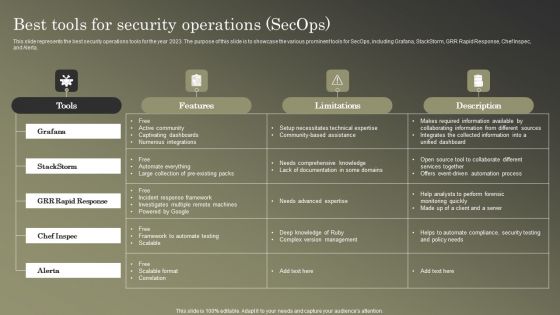
Cybersecurity Operations Cybersecops Best Tools For Security Operations Secops Graphics PDF
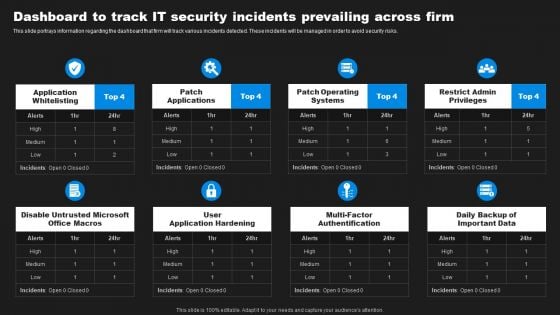
Enhancing Information Technology With Strategic Dashboard To Track IT Security Summary PDF
This slide portrays information regarding the dashboard that firm will track various incidents detected. These incidents will be managed in order to avoid security risks. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Enhancing Information Technology With Strategic Dashboard To Track IT Security Summary PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
Enhancing Information Technology With Strategic Information Security And Governance Icons PDF
This slide provides information regarding information security and governance management framework. The key elements include compliance, audit, response and recovery, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Enhancing Information Technology With Strategic Information Security And Governance Icons PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Comprehensive Guide For Ensuring IT Infrastructure Security Table Of Contents Summary PDF
Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Comprehensive Guide For Ensuring IT Infrastructure Security Table Of Contents Summary PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Comprehensive Guide For Ensuring IT Infrastructure Security Table Of Contents Summary PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today
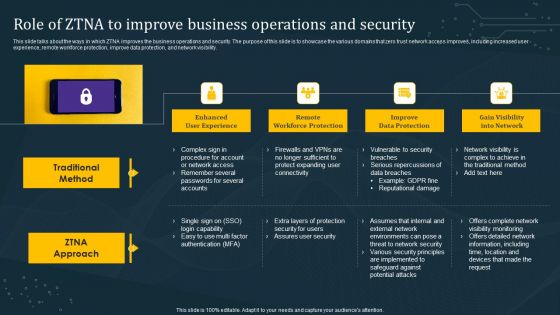
Role Of ZTNA To Improve Business Operations And Security Slides PDF
This slide talks about the ways in which ZTNA improves the business operations and security. The purpose of this slide is to showcase the various domains that zero trust network access improves, including increased user experience, remote workforce protection, improve data protection, and network visibility. There are so many reasons you need a Role Of ZTNA To Improve Business Operations And Security Slides PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
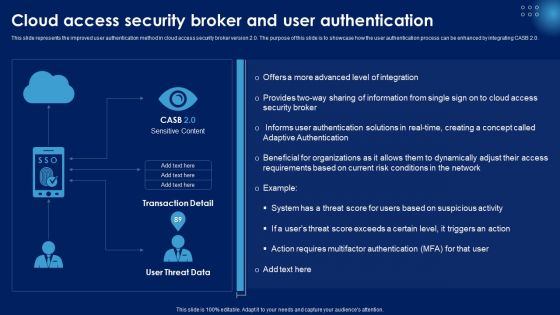
Cloud Access Security Broker And User Authentication Ppt PowerPoint Presentation File Deck PDF
This slide represents the improved user authentication method in cloud access security broker version 2.0. The purpose of this slide is to showcase how the user authentication process can be enhanced by integrating CASB 2.0. Make sure to capture your audiences attention in your business displays with our gratis customizable Cloud Access Security Broker And User Authentication Ppt PowerPoint Presentation File Deck PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
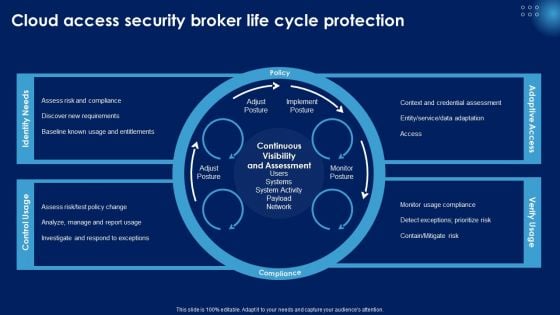
Cloud Access Security Broker Life Cycle Protection Ppt PowerPoint Presentation File Diagrams PDF
Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Cloud Access Security Broker Life Cycle Protection Ppt PowerPoint Presentation File Diagrams PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Cloud Access Security Broker Life Cycle Protection Ppt PowerPoint Presentation File Diagrams PDF.
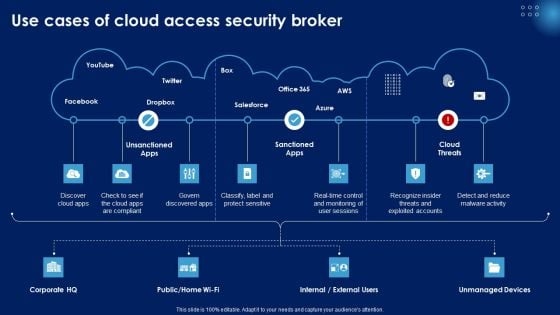
Use Cases Of Cloud Access Security Broker Ppt PowerPoint Presentation Diagram Graph Charts PDF
Find highly impressive Use Cases Of Cloud Access Security Broker Ppt PowerPoint Presentation Diagram Graph Charts PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Use Cases Of Cloud Access Security Broker Ppt PowerPoint Presentation Diagram Graph Charts PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.
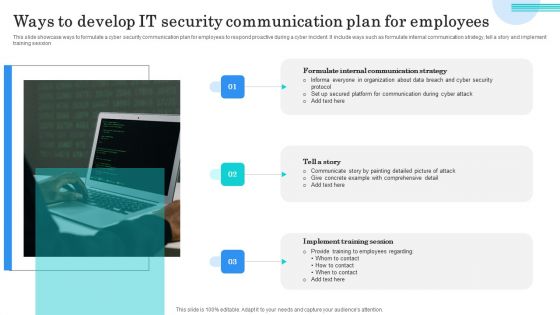
Ways To Develop IT Security Communication Plan For Employees Elements PDF
This slide showcase ways to formulate a cyber security communication plan for employees to respond proactive during a cyber incident. It include ways such as formulate internal communication strategy, tell a story and implement training session. Presenting Ways To Develop IT Security Communication Plan For Employees Elements PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Formulate Internal Communication, Tell Story, Implement Training Session. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Communication Plan For Information Technology Security Based On Audience Type Demonstration PDF
This slide consists of a communication plan information technology security to be deployed by managers based on the type of audience. Key elements include communication, frequency, communication goal, owner, etc. Presenting Communication Plan For Information Technology Security Based On Audience Type Demonstration PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Project Status Report, Team Standup, Task Progress Updates. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
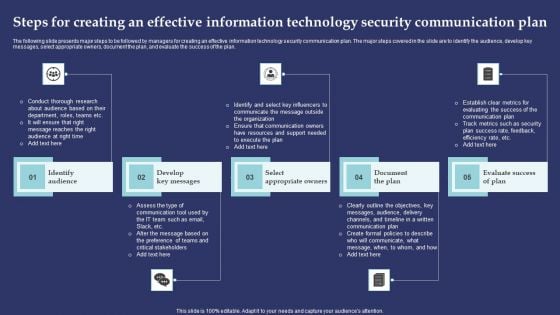
Steps For Creating An Effective Information Technology Security Communication Plan Introduction PDF
The following slide presents major steps to be followed by managers for creating an effective information technology security communication plan. The major steps covered in the slide are to identify the audience, develop key messages, select appropriate owners, document the plan, and evaluate the success of the plan. Presenting Steps For Creating An Effective Information Technology Security Communication Plan Introduction PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Identify Audience, Develop Key Messages, Select Appropriate Owners. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.m
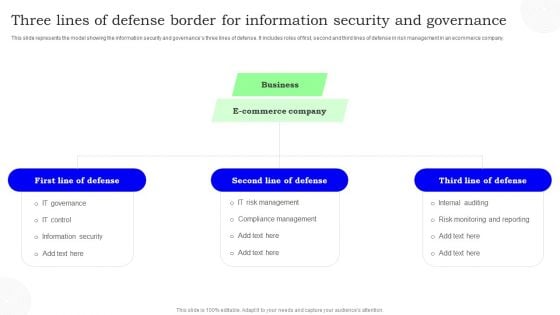
Three Lines Of Defense Border For Information Security And Governance Information PDF
This slide represents the model showing the information security and governances three lines of defense. It includes roles of first, second and third lines of defense in risk management in an ecommerce company. Persuade your audience using this Three Lines Of Defense Border For Information Security And Governance Information PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Defense, Commerce Company, Business. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Strategic Plan Roadmap To Develop Effective Cyber Security Strategy Icons PDF
This slide signifies the strategic plan timeline to create effective cyber security project. It covers information about steps like identify, analyse, evaluate, prioritise, treat and monitor Persuade your audience using this Strategic Plan Roadmap To Develop Effective Cyber Security Strategy Icons PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Evaluate, Identify, Analyse. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Icons Slide For Comprehensive Guide To Blockchain Digital Security Risk Management Professional Pdf
Introducing our well designed Icons Slide For Comprehensive Guide To Blockchain Digital Security Risk Management Professional Pdf set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience. Our Icons Slide For Comprehensive Guide To Blockchain Digital Security Risk Management Professional Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Female Holding Pair Of Key Security PowerPoint Templates And PowerPoint Backgrounds 0311
Microsoft PowerPoint Template and Background with female holding out pair of keys over dramatic clouds and Sky with sun rays Assist yourself with our Female Holding Pair Of Key Security PowerPoint Templates And PowerPoint Backgrounds 0311. Download without worries with our money back guaranteee.

Female Holding Pair Of Key Security PowerPoint Themes And PowerPoint Slides 0311
Microsoft PowerPoint Theme and Slide with female holding out pair of keys over dramatic clouds and Sky with sun rays Compile targets with our Female Holding Pair Of Key Security PowerPoint Themes And PowerPoint Slides 0311. Download without worries with our money back guaranteee.

American Intelligence And Security PowerPoint Templates Ppt Backgrounds For Slides 0813
Put yourself in a dominant position. Our American Intelligence And Security PowerPoint Templates PPT Backgrounds For Slides will confirm your superiority. Dominate proceedings with your ideas. Our Americana PowerPoint Templates will empower your thoughts. Our Medical PowerPoint Templates have a domino effect. Your ideas will generate one after another.

Data Security Is Must PowerPoint Templates Ppt Backgrounds For Slides 0913
Your ideas will do the trick. Wave the wand with our Data Security Is Must PowerPoint Templates PPT Backgrounds For Slides. Our Holidays PowerPoint Templates team are a dogged lot. They keep at it till they get it right. Dole it out with our AmericanaPowerPoint Templates. Your thoughts will get the right proportions.
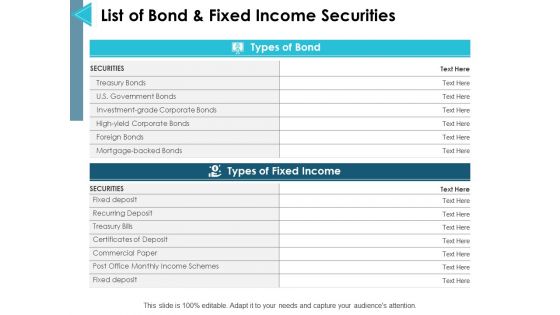
List Of Bond And Fixed Income Securities Ppt PowerPoint Presentation Layouts Graphics Design
This is a list of bond and fixed income securities ppt powerpoint presentation layouts graphics design. The topics discussed in this diagram are management, marketing, business, strategy, planning. This is a completely editable PowerPoint presentation, and is available for immediate download.
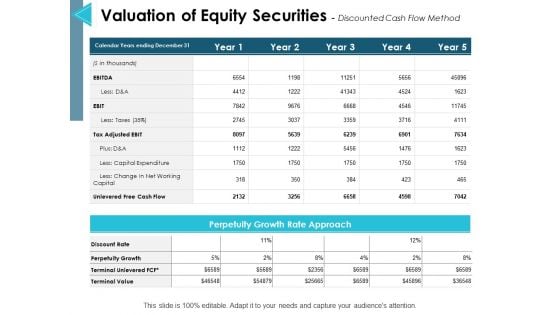
Valuation Of Equity Securities Discounted Cash Flow Method Ppt PowerPoint Presentation Infographic Template Introduction
This is a valuation of equity securities discounted cash flow method ppt powerpoint presentation infographic template introduction. The topics discussed in this diagram are management, marketing, business, strategy, planning. This is a completely editable PowerPoint presentation, and is available for immediate download.

Employee Benefits Template Social Securities Ppt PowerPoint Presentation Layouts Background Image
Presenting this set of slides with name employee benefits template social securities ppt powerpoint presentation layouts background image. This is a five stage process. The stages in this process are finance, marketing, management, investment, analysis. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
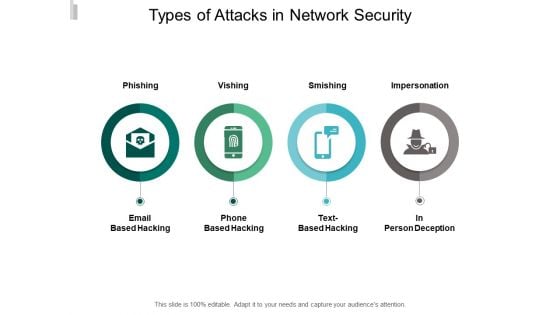
Types Of Attacks In Network Security Ppt PowerPoint Presentation Portfolio Layouts
Presenting this set of slides with name types of attacks in network security ppt powerpoint presentation portfolio layouts. This is a four stage process. The stages in this process are technology, social network, social engineering. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
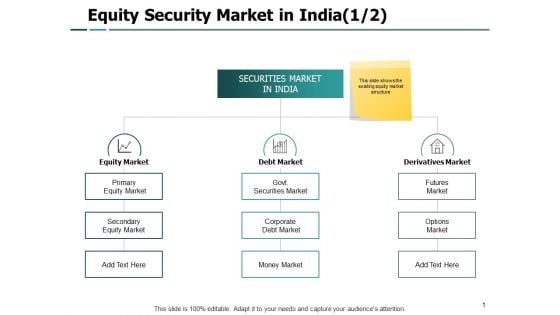
Equity Security Market In India Business Ppt PowerPoint Presentation Summary Layout
Presenting this set of slides with name equity security market in india business ppt powerpoint presentation summary layout. This is a three stage process. The stages in this process are marketing, business, management, planning, strategy. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Financial Instruments Bonds And Fixed Income Securities Ppt PowerPoint Presentation Show Graphics Pictures
Presenting this set of slides with name financial instruments bonds and fixed income securities ppt powerpoint presentation show graphics pictures. The topics discussed in these slides are marketing, business, management, planning, strategy. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
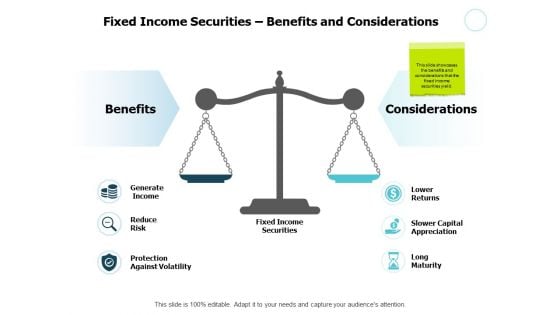
Fixed Income Securities Benefits And Considerations Ppt PowerPoint Presentation File Good
Presenting this set of slides with name fixed income securities benefits and considerations ppt powerpoint presentation file good. This is a two stage process. The stages in this process are compare, marketing, business, management, planning. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Fixed Income Securities Icons Slide Gears Dollar Ppt PowerPoint Presentation Ideas Guidelines
Presenting this set of slides with name fixed income securities icons slide gears dollar ppt powerpoint presentation ideas guidelines. The topics discussed in these slides are marketing, process, management, planning, strategy. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
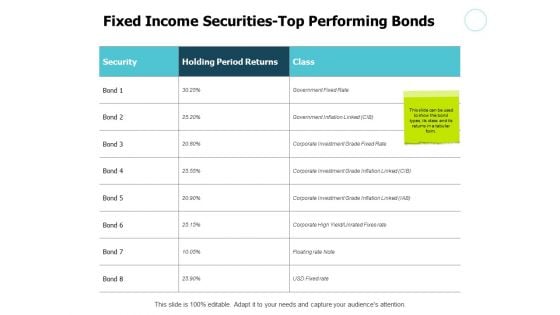
Fixed Income Securities Top Performing Bonds Ppt PowerPoint Presentation Layouts Portrait
Presenting this set of slides with name fixed income securities top performing bonds ppt powerpoint presentation layouts portrait. The topics discussed in these slides are marketing, process, management, planning, strategy. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Security Documents For Banks Loan Ppt PowerPoint Presentation Visual Aids Outline
Presenting this set of slides with name security documents for banks loan ppt powerpoint presentation visual aids outline. This is a three stage process. The stages in this process are collateral, documents granting, documents required. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Five Stages Circular Process Business Cyber Security Ppt PowerPoint Presentation Icon Tips
Presenting this set of slides with name five stages circular process business cyber security ppt powerpoint presentation icon tips. This is a five stage process. The stages in this process are technology, strategy, steps approach. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Security Compliance Set Of Icons Ppt PowerPoint Presentation Infographics Graphics Tutorials
Presenting this set of slides with name security compliance set of icons ppt powerpoint presentation infographics graphics tutorials. This is a six stage process. The stages in this process are hazard symbol, risk icon, risk management icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

CVV On Debit Card For Security Ppt PowerPoint Presentation Pictures Background Images
Presenting this set of slides with name cvv on debit card for security ppt powerpoint presentation pictures background images. This is a one stage process. The stages in this process are credit card, atm card, online purchase. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Barriers And Solutions Icons Slide Security Technology Ppt PowerPoint Presentation Model Information
Presenting this set of slides with name barriers and solutions icons slide security technology ppt powerpoint presentation model information. The topics discussed in these slides are technology, communication, planning, strategy, marketing. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Tqm Model Security Process Ppt PowerPoint Presentation Infographic Template File Formats
Presenting this set of slides with name tqm model security process ppt powerpoint presentation infographic template file formats. This is a five stage process. The stages in this process are marketing, business, management, planning, strategy. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Risks Types Of Outsourcing Fraud Financial And Data Security Ppt PowerPoint Presentation File Example
Presenting this set of slides with name risks types of outsourcing fraud financial and data security ppt powerpoint presentation file example. This is a four stage process. The stages in this process are business process outsourcing, circular infographics, threats. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Cyber Security Testing Process With Icons Ppt PowerPoint Presentation Infographic Template Demonstration
Presenting this set of slides with name cyber security testing process with icons ppt powerpoint presentation infographic template demonstration. This is a five stage process. The stages in this process are Penetration Testing, Internal Testing, Gaining access. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Five Steps Circular Process For Application Security Testing Ppt PowerPoint Presentation Styles Icon
Presenting this set of slides with name five steps circular process for application security testing ppt powerpoint presentation styles icon. This is a five stage process. The stages in this process are Penetration Testing, Internal Testing, Gaining access. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Five Steps Vulnerability Security Testing With Icon Ppt PowerPoint Presentation Inspiration Topics
Presenting this set of slides with name five steps vulnerability security testing with icon ppt powerpoint presentation inspiration topics. This is a five stage process. The stages in this process are Penetration Testing, Internal Testing, Gaining access. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
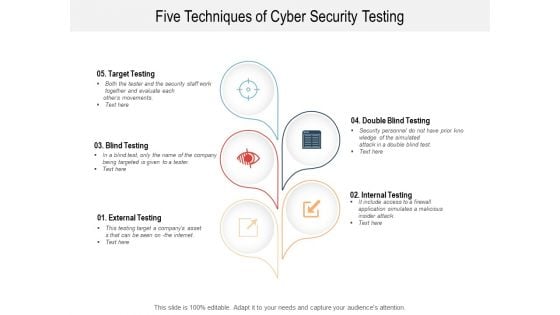
Five Techniques Of Cyber Security Testing Ppt PowerPoint Presentation Layouts Model
Presenting this set of slides with name five techniques of cyber security testing ppt powerpoint presentation layouts model. This is a five stage process. The stages in this process are Penetration Testing, Internal Testing, Gaining access. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
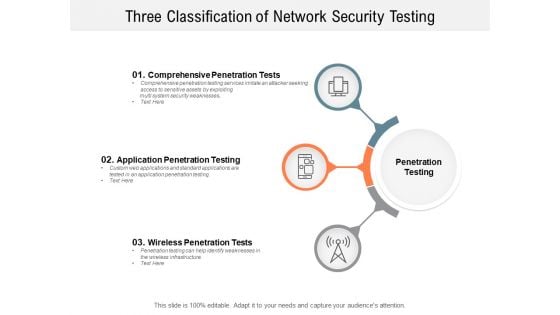
Three Classification Of Network Security Testing Ppt PowerPoint Presentation Slides Demonstration
Presenting this set of slides with name three classification of network security testing ppt powerpoint presentation slides demonstration. This is a three stage process. The stages in this process are Penetration Testing, Internal Testing, Gaining access. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Web Application Security Testing Vector Icon Ppt PowerPoint Presentation Pictures Clipart Images
Presenting this set of slides with name web application security testing vector icon ppt powerpoint presentation pictures clipart images. This is a one stage process. The stages in this process are Penetration Testing, Internal Testing, Gaining access. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Risk Contingency Plan Example With Security Controls Ppt PowerPoint Presentation File Outline
Presenting this set of slides with name risk contingency plan example with security controls ppt powerpoint presentation file outline. This is a six stage process. The stages in this process are risk framework, risk management, planning process. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
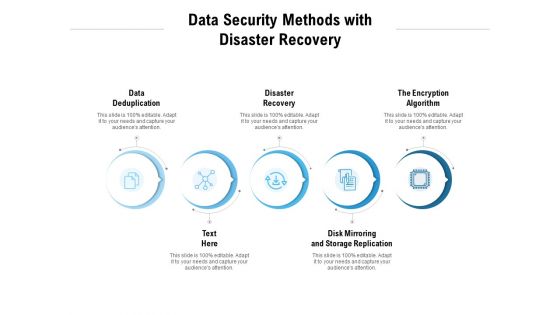
Data Security Methods With Disaster Recovery Ppt PowerPoint Presentation Pictures Vector
Presenting this set of slides with name data security methods with disaster recovery ppt powerpoint presentation pictures vector. This is a five stage process. The stages in this process are data deduplication, disaster recovery, the encryption algorithm, disk mirroring and storage replication. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security For Your Organization Ppt PowerPoint Presentation Complete Deck With Slides
Presenting this set of slides with name cyber security for your organization ppt powerpoint presentation complete deck with slides. The topics discussed in these slides are risk management, business, analysis, goal, marketing. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security For Your Organization Amount Spent On Cyber Fraud Settlements Ppt File Elements PDF
Presenting this set of slides with name cyber security for your organization amount spent on cyber fraud settlements ppt file elements pdf. This is a ONE stage process. The stages in this process are settlements, amount, average per settlement. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security For Your Organization Backup Maintenance Recovery Budget Planning Ppt Inspiration Slide Portrait PDF
Presenting this set of slides with name cyber security for your organization backup maintenance recovery budget planning ppt inspiration slide portrait pdf. The topics discussed in these slides are vendor costs, hardware costs, software costs, travel shipping costs, labor contractor costs, testing costs, supply costs. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security For Your Organization Critical Business Functions Recovery Priorities Ppt Inspiration Slide PDF
Presenting this set of slides with name cyber security for your organization critical business functions recovery priorities ppt inspiration slide pdf. This is a one stage process. The stages in this process are priorities, maximum allowable downtime, department. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security For Your Organization Essential Contingency Plan Strategies Ppt Layouts Vector PDF
Presenting this set of slides with name cyber security for your organization essential contingency plan strategies ppt layouts vector pdf. This is a one stage process. The stages in this process are contingency considerations, contingency solutions, server, vendor information, critical components, technologies integration. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security For Your Organization Incident Reporting By Different Cyber Departments Ppt Professional Topics PDF
Presenting this set of slides with name cyber security for your organization incident reporting by different cyber departments ppt professional topics pdf. This is a one stage process. The stages in this process are number incidents, person involved incident, average cost per incident, department. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security For Your Organization Our Mission Ppt Infographics Model PDF
Presenting this set of slides with name cyber security for your organization our mission ppt infographics model pdf. This is a one stage process. The stages in this process are vision, mission, goal. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security For Your Organization Our Team Ppt Ideas Infographic Template PDF
Presenting this set of slides with name cyber security for your organization our team ppt ideas infographic template pdf. This is a four stage process. The stages in this process are our team. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
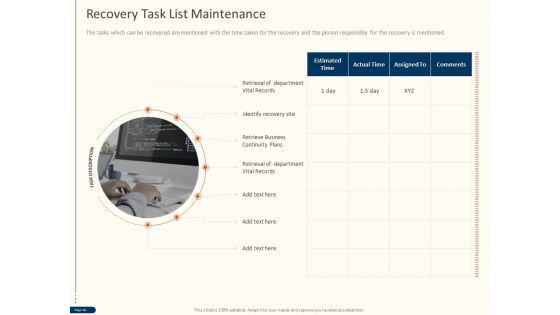
Cyber Security For Your Organization Recovery Task List Maintenance Ppt Layouts Designs Download PDF
Presenting this set of slides with name cyber security for your organization recovery task list maintenance ppt layouts designs download pdf. This is a one stage process. The stages in this process are estimated time, actual time, assigned, comments. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security For Your Organization Risk Assessment Matrix Ppt Ideas PDF
Presenting this set of slides with name cyber security for your organization risk assessment matrix ppt ideas pdf. This is a one stage process. The stages in this process are insignificant, minor, severity, risk, catastrophic. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security For Your Organization Staff Training Schedule With Cost Ppt Visual Aids Slides PDF
Presenting this set of slides with name cyber security for your organization staff training schedule with cost ppt visual aids slides pdf. This is a one stage process. The stages in this process are advanced software training, advanced skills train, training module. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security For Your Organization Thank You Ppt Portfolio Clipart PDF
Presenting this set of slides with name cyber security for your organization thank you ppt portfolio clipart pdf. The topics discussed in these slide is thank you. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Cyber Security For Your Organization Timeframe For Incident Management Ppt Icon Graphics Design PDF
Presenting this set of slides with name cyber security for your organization timeframe for incident management ppt icon graphics design pdf. This is a one stage process. The stages in this process are incident logging, ticket creation, incident categorization, incident prioritization, incident resolution, incident closure. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.


 Continue with Email
Continue with Email

 Home
Home


































