Safety
Iot Device Authentication Methods To Ensure Data Iot Device Management Download Pdf
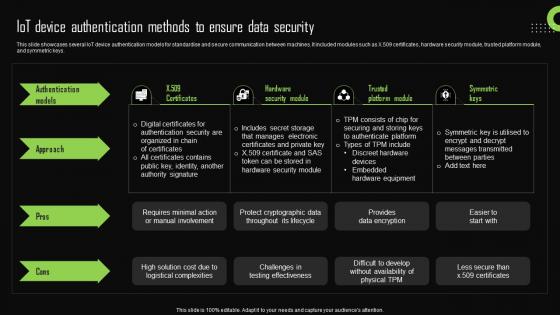
This slide showcases several IoT device authentication models for standardise and secure communication between machines. It included modules such as X.509 certificates, hardware security module, trusted platform module, and symmetric keys. Slidegeeks has constructed after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide showcases several IoT device authentication models for standardise and secure communication between machines. It included modules such as X.509 certificates, hardware security module, trusted platform module, and symmetric keys.
Allocation Of STO Project Budget For Exploring Investment Opportunities Demonstration Pdf
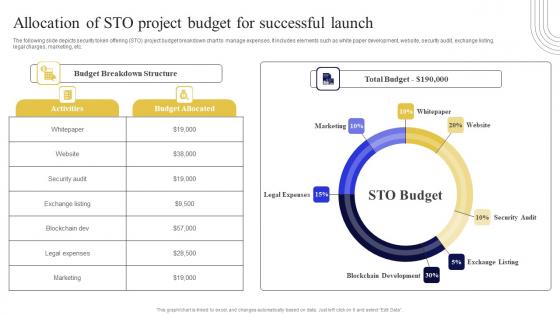
The following slide depicts security token offering STO project budget breakdown chart to manage expenses. It includes elements such as white paper development, website, security audit, exchange listing, legal charges, marketing, etc. Create an editable Allocation Of STO Project Budget For Exploring Investment Opportunities Demonstration Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Allocation Of STO Project Budget For Exploring Investment Opportunities Demonstration Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. The following slide depicts security token offering STO project budget breakdown chart to manage expenses. It includes elements such as white paper development, website, security audit, exchange listing, legal charges, marketing, etc.
Comparative Workflows Of Stos And Icos Exploring Investment Opportunities Professional Pdf
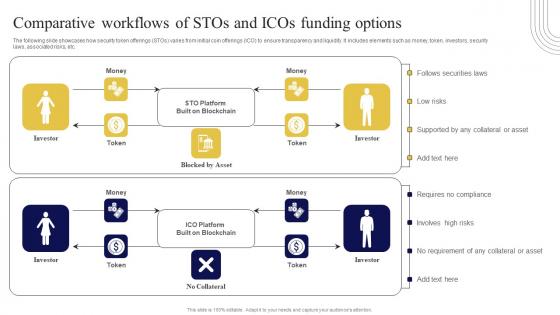
The following slide showcases how security token offerings STOs varies from initial coin offerings ICO to ensure transparency and liquidity. It includes elements such as money, token, investors, security laws, associated risks, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Comparative Workflows Of Stos And Icos Exploring Investment Opportunities Professional Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Comparative Workflows Of Stos And Icos Exploring Investment Opportunities Professional Pdf today and make your presentation stand out from the rest The following slide showcases how security token offerings STOs varies from initial coin offerings ICO to ensure transparency and liquidity. It includes elements such as money, token, investors, security laws, associated risks, etc.
Advanced Measures For Data Breach Prevention Data Breach Prevention Inspiration Pdf
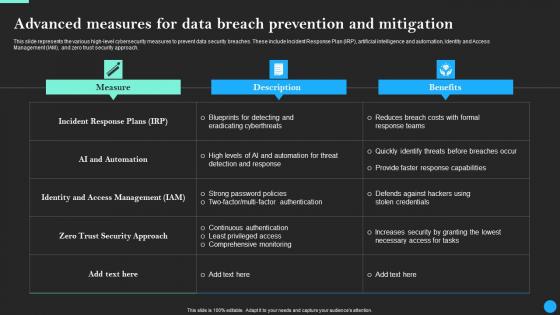
This slide represents the various high-level cybersecurity measures to prevent data security breaches. These include Incident Response Plan IRP, artificial intelligence and automation, Identity and Access Management IAM, and zero trust security approach. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Advanced Measures For Data Breach Prevention Data Breach Prevention Inspiration Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide represents the various high-level cybersecurity measures to prevent data security breaches. These include Incident Response Plan IRP, artificial intelligence and automation, Identity and Access Management IAM, and zero trust security approach.

Agile Threat Modeling Overview About Duration Process Crafting A Sustainable Company Designs Pdf
This slide provides information regarding agile threat modeling as a risk-based approach that helps develop secure systems. The approach is suitable for business analysts, product managers, security teams, technical and non-technical professionals, etc. Create an editable Agile Threat Modeling Overview About Duration Process Crafting A Sustainable Company Designs Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Agile Threat Modeling Overview About Duration Process Crafting A Sustainable Company Designs Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide provides information regarding agile threat modeling as a risk-based approach that helps develop secure systems. The approach is suitable for business analysts, product managers, security teams, technical and non-technical professionals, etc.
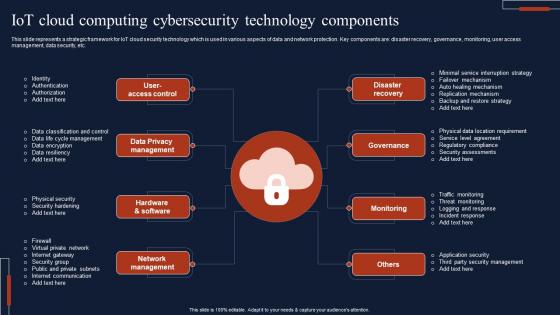
IOT Cloud Computing Cybersecurity Technology Components Template Pdf
This slide represents a strategic framework for IoT cloud security technology which is used in various aspects of data and network protection. Key components are disaster recovery, governance, monitoring, user access management, data security, etc. Pitch your topic with ease and precision using this IOT Cloud Computing Cybersecurity Technology Components Template Pdf This layout presents information on Privacy Management, Hardware And Software, Network Management It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide represents a strategic framework for IoT cloud security technology which is used in various aspects of data and network protection. Key components are disaster recovery, governance, monitoring, user access management, data security, etc.
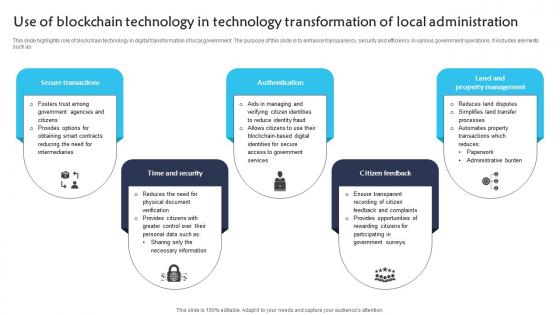
Use Of Blockchain Technology In Technology Transformation Of Local Administration Infographics pdf
This slide highlights role of blockchain technology in digital transformation of local government. The purpose of this slide is to enhance transparency, security and efficiency in various government operations. It includes elements such as. Showcasing this set of slides titled Use Of Blockchain Technology In Technology Transformation Of Local Administration Infographics pdf. The topics addressed in these templates are Secure Transactions, Authentication, Citizen Feedback, Time And Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide highlights role of blockchain technology in digital transformation of local government. The purpose of this slide is to enhance transparency, security and efficiency in various government operations. It includes elements such as.
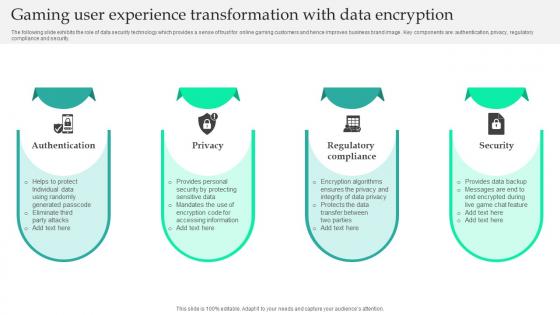
Gaming User Experience Transformation With Data Encryption Portrait Pdf
The following slide exhibits the role of data security technology which provides a sense of trust for online gaming customers and hence improves business brand image . Key components are authentication, privacy, regulatory compliance and security. Pitch your topic with ease and precision using this Gaming User Experience Transformation With Data Encryption Portrait Pdf. This layout presents information on Authentication, Privacy, Regulatory Compliance. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. The following slide exhibits the role of data security technology which provides a sense of trust for online gaming customers and hence improves business brand image . Key components are authentication, privacy, regulatory compliance and security.
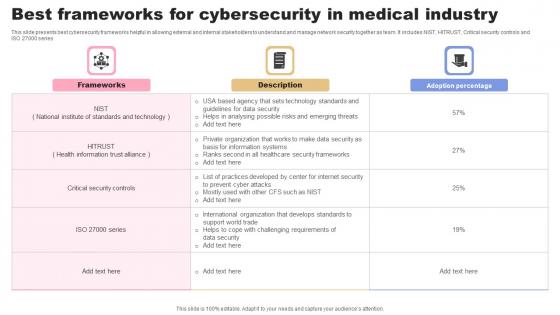
Best Frameworks For Cybersecurity In Medical Industry Guidelines Pdf
This slide presents best cybersecurity frameworks helpful in allowing external and internal stakeholders to understand and manage network security together as team. It includes NIST, HITRUST, Critical security controls and ISO 27000 series Showcasing this set of slides titled Best Frameworks For Cybersecurity In Medical Industry Guidelines Pdf. The topics addressed in these templates are Frameworks, Description, Adoption Percentage. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide presents best cybersecurity frameworks helpful in allowing external and internal stakeholders to understand and manage network security together as team. It includes NIST, HITRUST, Critical security controls and ISO 27000 series
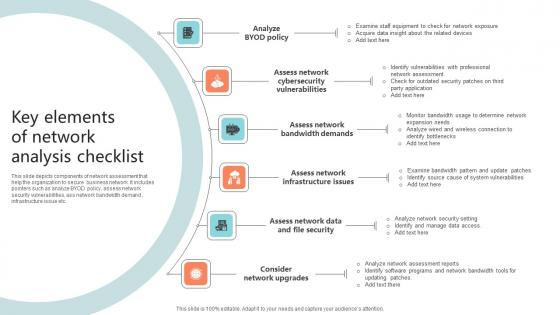
Key Elements Of Network Analysis Checklist Microsoft Pdf
This slide depicts components of network assessment that help the organization to secure business network. It includes pointers such as analyze BYOD policy, assess network security vulnerabilities, ass network bandwidth demand , infrastructure issue etc.Pitch your topic with ease and precision using this Key Elements Of Network Analysis Checklist Microsoft Pdf This layout presents information on Cybersecurity Vulnerabilities, Bandwidth Demands, Assess Network It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide depicts components of network assessment that help the organization to secure business network. It includes pointers such as analyze BYOD policy, assess network security vulnerabilities, ass network bandwidth demand , infrastructure issue etc.

Web Consulting Business Cybersecurity Issues Overview And Key Statistics
Mentioned slide provides introduction about cyber security issues. It includes key elements such as description, types of security issue, key facts, and negative impact on business. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Web Consulting Business Cybersecurity Issues Overview And Key Statistics to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. Mentioned slide provides introduction about cyber security issues. It includes key elements such as description, types of security issue, key facts, and negative impact on business.
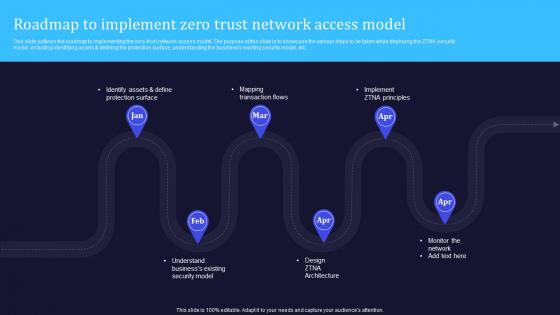
A20 Zero Trust Model Roadmap To Implement Zero Trust Network Access
This slide outlines the roadmap to implementing the zero-trust network access model. The purpose of this slide is to showcase the various steps to be taken while deploying the ZTNA security model, including identifying assets and defining the protection surface, understanding the businesss existing security model, etc. Find a pre-designed and impeccable A20 Zero Trust Model Roadmap To Implement Zero Trust Network Access. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide outlines the roadmap to implementing the zero-trust network access model. The purpose of this slide is to showcase the various steps to be taken while deploying the ZTNA security model, including identifying assets and defining the protection surface, understanding the businesss existing security model, etc.

Zero Trust Model Case Study Intellectual Property Protection
This slide represents the case study for implementing the ZTNA security model into a food and beverage organization to secure intellectual property, supply chain and manufacturing. The purpose of this slide is to highlight the key requirements, solutions and impact of ZTNA implementation on the business. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Zero Trust Model Case Study Intellectual Property Protection will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide represents the case study for implementing the ZTNA security model into a food and beverage organization to secure intellectual property, supply chain and manufacturing. The purpose of this slide is to highlight the key requirements, solutions and impact of ZTNA implementation on the business.
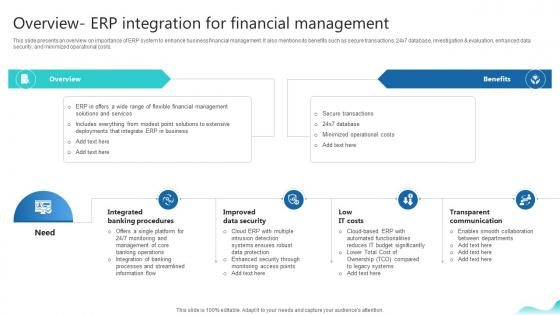
Overview Erp Integration For Financial Management Erp And Digital Transformation For Maximizing DT SS V
This slide presents an overview on importance of ERP system to enhance business financial management. It also mentions its benefits such as secure transactions, 24x7 database, investigation and evaluation, enhanced data security, and minimized operational costs.The Overview Erp Integration For Financial Management Erp And Digital Transformation For Maximizing DT SS V is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide presents an overview on importance of ERP system to enhance business financial management. It also mentions its benefits such as secure transactions, 24x7 database, investigation and evaluation, enhanced data security, and minimized operational costs.
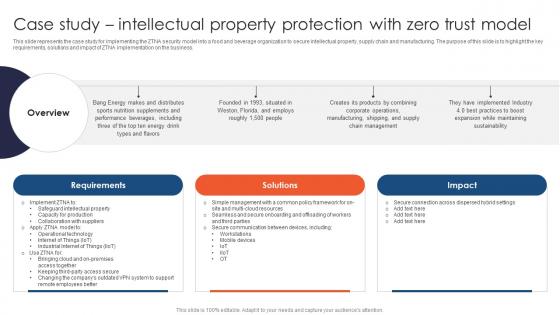
Zero Trust Network Access Case Study Intellectual Property Protection With Zero Trust Model
This slide represents the case study for implementing the ZTNA security model into a food and beverage organization to secure intellectual property, supply chain and manufacturing. The purpose of this slide is to highlight the key requirements, solutions and impact of ZTNA implementation on the business. Make sure to capture your audiences attention in your business displays with our gratis customizable Zero Trust Network Access Case Study Intellectual Property Protection With Zero Trust Model. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide represents the case study for implementing the ZTNA security model into a food and beverage organization to secure intellectual property, supply chain and manufacturing. The purpose of this slide is to highlight the key requirements, solutions and impact of ZTNA implementation on the business.
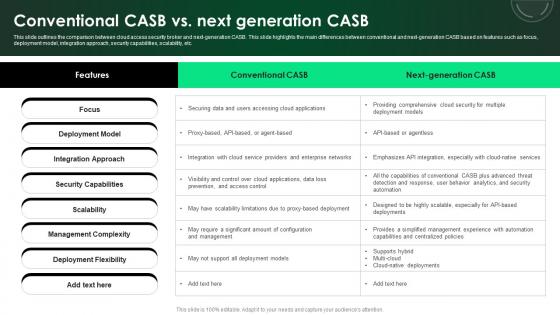
CASB 2 0 IT Conventional CASB Vs Next Generation CASB
This slide outlines the comparison between cloud access security broker and next-generation CASB. This slide highlights the main differences between conventional and next-generation CASB based on features such as focus, deployment model, integration approach, security capabilities, scalability, etc. Find a pre-designed and impeccable CASB 2 0 IT Conventional CASB Vs Next Generation CASB. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide outlines the comparison between cloud access security broker and next-generation CASB. This slide highlights the main differences between conventional and next-generation CASB based on features such as focus, deployment model, integration approach, security capabilities, scalability, etc.

Managing Technical And Non Cybersecurity Issues Overview And Key Statistics
Mentioned slide provides introduction about cyber security issues. It includes key elements such as description, types of security issue, key facts, and negative impact on business. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Managing Technical And Non Cybersecurity Issues Overview And Key Statistics was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Managing Technical And Non Cybersecurity Issues Overview And Key Statistics. Mentioned slide provides introduction about cyber security issues. It includes key elements such as description, types of security issue, key facts, and negative impact on business.

Benefits Of Technological Advancement For E Wallets In Depth Guide To Digital Wallets Fin SS V
This slide exhibits the multiple advantages of technological advancement for digital wallets that lead to secure and seamless processing of operations. The major factors are user convenience, improved security, etc. Want to ace your presentation in front of a live audience Our Benefits Of Technological Advancement For E Wallets In Depth Guide To Digital Wallets Fin SS V can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide exhibits the multiple advantages of technological advancement for digital wallets that lead to secure and seamless processing of operations. The major factors are user convenience, improved security, etc.

Empowering The Future Challenges And Solutions In Advanced Metering Infrastructure IoT SS V
This slide exhibits AMI system challenges and appropriate solutions to enhance grid reliability. It includes challenges such as communication network challenges, network-based security threats, security standards, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Empowering The Future Challenges And Solutions In Advanced Metering Infrastructure IoT SS V. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Empowering The Future Challenges And Solutions In Advanced Metering Infrastructure IoT SS V today and make your presentation stand out from the rest This slide exhibits AMI system challenges and appropriate solutions to enhance grid reliability. It includes challenges such as communication network challenges, network-based security threats, security standards, etc.
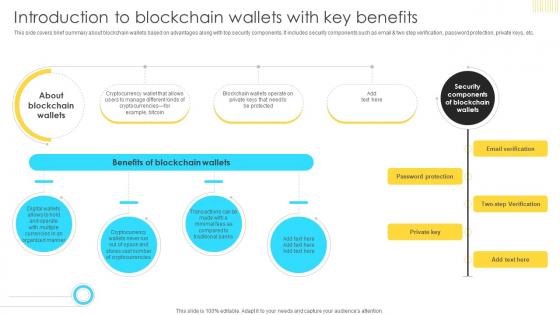
Mastering Blockchain Wallets Introduction To Blockchain Wallets With Key BCT SS V
This side covers brief summary about blockchain wallets based on advantages along with top security components. It includes security components such as email and two step verification, password protection, private keys, etc Do you know about Slidesgeeks Mastering Blockchain Wallets Introduction To Blockchain Wallets With Key BCT SS V These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This side covers brief summary about blockchain wallets based on advantages along with top security components. It includes security components such as email and two step verification, password protection, private keys, etc

Content Protection Mechanisms In Mobile Application Areas Of Mobile Cloud Computing
The purpose of the mentioned slide is to showcase the content protection techniques to secure mobile cloud media streaming. It includes encryption, secure authentication and authorization, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Content Protection Mechanisms In Mobile Application Areas Of Mobile Cloud Computing will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. The purpose of the mentioned slide is to showcase the content protection techniques to secure mobile cloud media streaming. It includes encryption, secure authentication and authorization, etc.

Beginners Guide To Commercial Addressing Cybersecurity Challenges In Commercial Fin SS V
This slide shows extensive details regarding various solutions which can be used against cyberthreats by banks. These solutions are network security, multifactor authentication, data encryption and secure communications, etc. Want to ace your presentation in front of a live audience Our Beginners Guide To Commercial Addressing Cybersecurity Challenges In Commercial Fin SS V can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide shows extensive details regarding various solutions which can be used against cyberthreats by banks. These solutions are network security, multifactor authentication, data encryption and secure communications, etc.

Comprehensive Guide For Website Cybersecurity Issues Overview And Key Statistics
Mentioned slide provides introduction about cyber security issues. It includes key elements such as description, types of security issue, key facts, and negative impact on business. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Comprehensive Guide For Website Cybersecurity Issues Overview And Key Statistics to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. Mentioned slide provides introduction about cyber security issues. It includes key elements such as description, types of security issue, key facts, and negative impact on business.

Addressing Cybersecurity Challenges In Complete Guide On Managing Banking Fin SS V
This slide shows extensive details regarding various solutions which can be used against cyberthreats by banks. These solutions are network security, multifactor authentication, data encryption and secure communications, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Addressing Cybersecurity Challenges In Complete Guide On Managing Banking Fin SS V for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide shows extensive details regarding various solutions which can be used against cyberthreats by banks. These solutions are network security, multifactor authentication, data encryption and secure communications, etc.
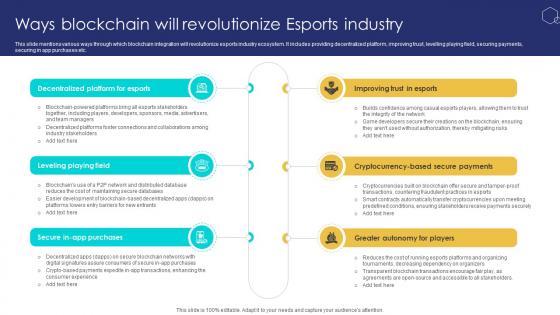
Unlocking The Potential Of Ways Blockchain Will Revolutionize Esports Industry BCT SS V
This slide mentions various ways through which blockchain integration will revolutionize esports industry ecosystem. It includes providing decentralized platform, improving trust, levelling playing field, securing payments, securing in app purchases etc. Do you know about Slidesgeeks Unlocking The Potential Of Ways Blockchain Will Revolutionize Esports Industry BCT SS V These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide mentions various ways through which blockchain integration will revolutionize esports industry ecosystem. It includes providing decentralized platform, improving trust, levelling playing field, securing payments, securing in app purchases etc.
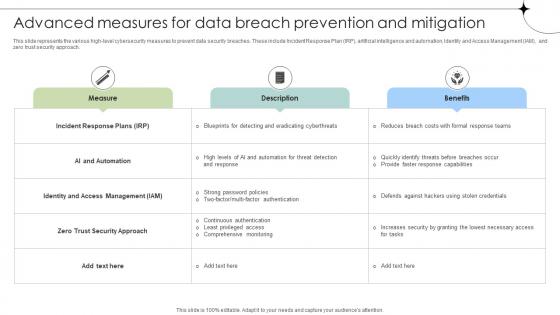
Advanced Measures For Data Breach Prevention And Mitigation Data Fortification Strengthening Defenses
This slide represents the various high-level cybersecurity measures to prevent data security breaches. These include Incident Response Plan IRP, artificial intelligence and automation, Identity and Access Management IAM, and zero trust security approach.Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Advanced Measures For Data Breach Prevention And Mitigation Data Fortification Strengthening Defenses for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide represents the various high-level cybersecurity measures to prevent data security breaches. These include Incident Response Plan IRP, artificial intelligence and automation, Identity and Access Management IAM, and zero trust security approach.

Data Breach Prevention Strategies For Enterprises Data Fortification Strengthening Defenses
The purpose of this slide is to outline the data breach mitigation strategies for businesses. These include access control, encryption, web security solutions, network security, up-to-date software and hardware, preparation, training employees and users, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Data Breach Prevention Strategies For Enterprises Data Fortification Strengthening Defenses. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. The purpose of this slide is to outline the data breach mitigation strategies for businesses. These include access control, encryption, web security solutions, network security, up-to-date software and hardware, preparation, training employees and users, etc.
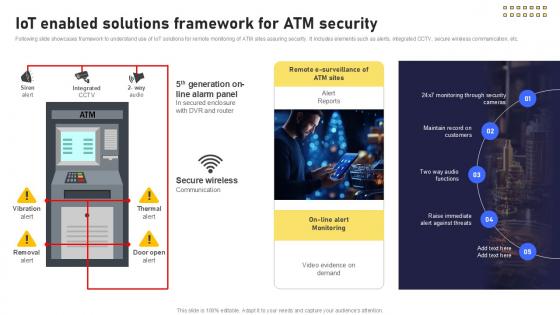
IoT Enabled Solutions Framework Banking Future With IoT Ppt Sample IoT SS V
Following slide showcases framework to understand use of IoT solutions for remote monitoring of ATM sites assuring security. It includes elements such as alerts, integrated CCTV, secure wireless communication, etc. Find highly impressive IoT Enabled Solutions Framework Banking Future With IoT Ppt Sample IoT SS V on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download IoT Enabled Solutions Framework Banking Future With IoT Ppt Sample IoT SS V for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now Following slide showcases framework to understand use of IoT solutions for remote monitoring of ATM sites assuring security. It includes elements such as alerts, integrated CCTV, secure wireless communication, etc.

Overview Of Recruitment Blockchain Cloud Recruiting Technologies PPT Slide
This slide showcases introduction to blockchain technology that possesses qualities in making recruitment process faster and secure. It provides details about legitimacy, secure access, quick verification, applicant profiles, fraud elimination, etc. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Overview Of Recruitment Blockchain Cloud Recruiting Technologies PPT Slide from Slidegeeks and deliver a wonderful presentation. This slide showcases introduction to blockchain technology that possesses qualities in making recruitment process faster and secure. It provides details about legitimacy, secure access, quick verification, applicant profiles, fraud elimination, etc.

Challenges With Devsecops Implementation And Solutions Role Of Devsecops Ppt Powerpoint
This slide explain the various limitations with DevSecOps and its solution. The purpose of this slide is to discuss the solutions provided to different challenges associated with DevSecOps. These include late sage security integration, tool integration and complexity, security awareness and training, etc. There are so many reasons you need a Challenges With Devsecops Implementation And Solutions Role Of Devsecops Ppt Powerpoint The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide explain the various limitations with DevSecOps and its solution. The purpose of this slide is to discuss the solutions provided to different challenges associated with DevSecOps. These include late sage security integration, tool integration and complexity, security awareness and training, etc.

Client Testimonials Email And Data Protection Platform Capital Funding Pitch Deck PPT Slide
This slide covers customer reviews about the email security company. It includes positive feedback related to user-friendly secure email software, helpful and professional team, seamless integration with Gmail. Create an editable Client Testimonials Email And Data Protection Platform Capital Funding Pitch Deck PPT Slide that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Client Testimonials Email And Data Protection Platform Capital Funding Pitch Deck PPT Slide is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide covers customer reviews about the email security company. It includes positive feedback related to user-friendly secure email software, helpful and professional team, seamless integration with Gmail.

Problem Statement Email And Data Protection Platform Capital Funding Pitch Deck PPT Slide
This slide covers major email security issues faced by customers. It includes issues such as inadequate secure file-sharing options and spam and viruses overwhelming email systems. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Problem Statement Email And Data Protection Platform Capital Funding Pitch Deck PPT Slide was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Problem Statement Email And Data Protection Platform Capital Funding Pitch Deck PPT Slide This slide covers major email security issues faced by customers. It includes issues such as inadequate secure file-sharing options and spam and viruses overwhelming email systems.

Overview Of Recruitment Blockchain Technology PPT Presentation
This slide showcases introduction to blockchain technology that possesses qualities in making recruitment process faster and secure. It provides details about legitimacy, secure access, quick verification, applicant profiles, fraud elimination, etc. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Overview Of Recruitment Blockchain Technology PPT Presentation from Slidegeeks and deliver a wonderful presentation. This slide showcases introduction to blockchain technology that possesses qualities in making recruitment process faster and secure. It provides details about legitimacy, secure access, quick verification, applicant profiles, fraud elimination, etc.
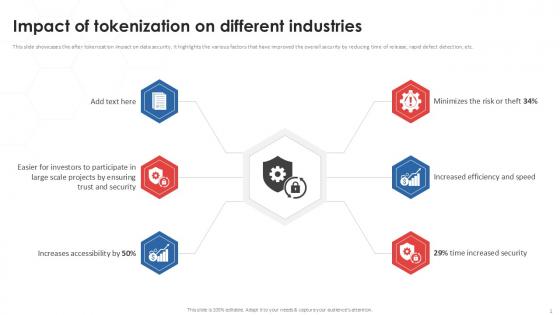
Impact Of Tokenization On Different Industries PPT Template
This slide showcases the after tokenization impact on data security. It highlights the various factors that have improved the overall security by reducing time of release, rapid defect detection, etc. Find a pre-designed and impeccable Impact Of Tokenization On Different Industries PPT Template. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide showcases the after tokenization impact on data security. It highlights the various factors that have improved the overall security by reducing time of release, rapid defect detection, etc.
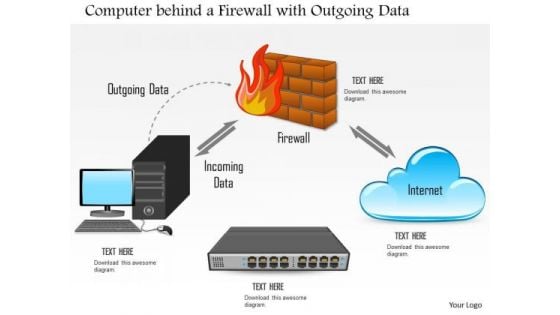
1 Computer Behind A Firewall With Outgoing Data And Network Switch Ppt Slides
This image slide displays computer behind a firewall with outgoing data and network switch. This image slide has been crafted with graphic of computer, cloud, server and firewall icon. This image slide depicts cloud computing security. You may change size, color and orientation of any icon to your liking. Use this PowerPoint template, in your presentations to explain concepts like cloud computing, technology, networking and security. This image slide will enhance the quality of your presentations.

1 Computer Network Mesh With Devices Behind Firewall Connected To The Internet Ppt Slides
This image slide displays computer network mesh with devices behind firewall connected to the internet. This image slide has been crafted with graphic of cloud, technology devices and firewall application icon. This image slide depicts cloud computing and security. You may change size, color and orientation of any icon to your liking. Use this PowerPoint template, in your presentations to explain concepts like cloud computing, technology, networking and security. This image slide will enhance the quality of your presentations.

1 Computers Behind A Firewall Connected To A Centralized Server Ppt Slides
This image slide displays computer behind a firewall connected to a centralized server. This image slide has been crafted with graphic of laptops, server and firewall icon connected. This image slide depicts security in networking. You may change size, color and orientation of any icon to your liking. Use this PowerPoint template, in your presentations to explain concepts technology, networking and security. This image slide will enhance the quality of your presentations.
1 Icon Of A Firewall To Separate The Internal Network From The External World Ppt Slides
This image slide displays icon of firewall. This image slide has been crafted with graphic of firewall icon to separate internal network from the external world. This image slide depicts security on network. You may change size, color and orientation of any icon to your liking. Use this PowerPoint template, in your presentations to explain concepts like networking and security. This image slide will enhance the quality of your presentations.
Risk And Return In Financial Management Ppt PowerPoint Presentation Icon Gallery PDF
Presenting this set of slides with name risk and return in financial management ppt powerpoint presentation icon gallery pdf. This is a four stage process. The stages in this process are shares also known as equity securities, property, fixed interest also known as debt securities cash, risk, return. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
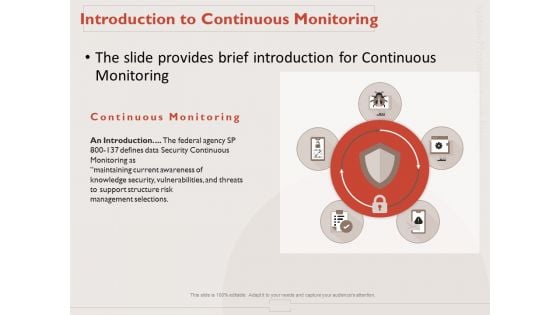
Monitoring Computer Software Application Introduction To Continuous Monitoring Ppt PowerPoint Presentation Model Files PDF
Presenting this set of slides with name monitoring computer software application introduction to continuous monitoring ppt powerpoint presentation model files pdf. This is a five stage process. The stages in this process are introduction, data security continuous monitoring, maintaining current awareness, knowledge security, vulnerabilities, and threats, support structure, risk management selections. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

All About Nagios Core Introduction To Continuous Monitoring Ppt PowerPoint Presentation Styles Infographics PDF
Presenting this set of slides with name all about nagios core introduction to continuous monitoring ppt powerpoint presentation styles infographics pdf. This is a five stage process. The stages in this process are introduction, data security continuous monitoring, maintaining current awareness, knowledge security, vulnerabilities, and threats, support structure, risk management selections. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
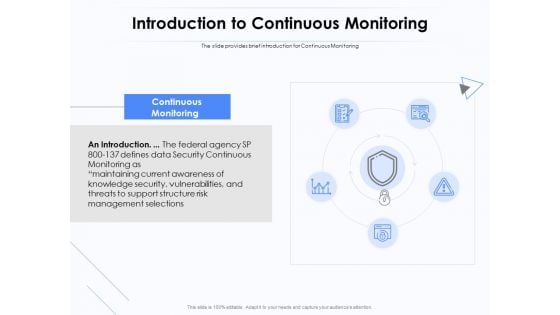
Network Monitoring Tool Overview Introduction To Continuous Monitoring Ppt PowerPoint Presentation Model Slide Download PDF
Presenting this set of slides with name network monitoring tool overview introduction to continuous monitoring ppt powerpoint presentation model slide download pdf. This is a five stage process. The stages in this process are continuous monitoring, introduction, data security, support structure, risk management selections, knowledge security. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
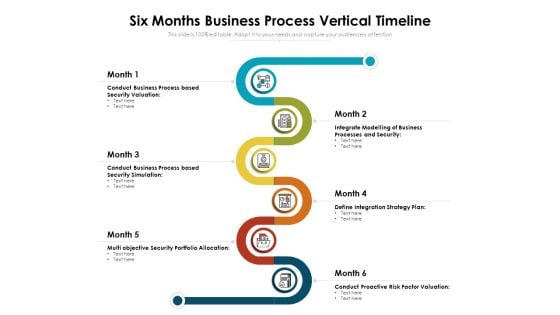
Six Months Business Process Vertical Timeline Ppt Model Design Inspiration PDF
Presenting six months business process vertical timeline ppt model design inspiration pdf to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including conduct business process based security valuation, integrate modelling of business processes and security, define integration strategy plan. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
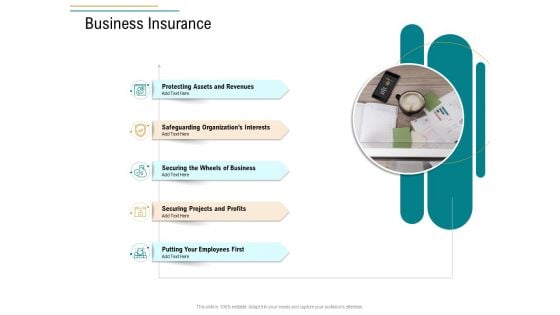
Business Operations Assessment Business Insurance Ppt Portfolio Graphics Design PDF
This is a business operations assessment business insurance ppt portfolio graphics design pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like protecting assets and revenues, safeguarding organizations interests, securing wheels business, securing projects and profits, putting employees first. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

In Depth Business Assessment Business Insurance Ppt PowerPoint Presentation Gallery Brochure PDF
This is a in depth business assessment business insurance ppt powerpoint presentation gallery brochure pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like protecting assets and revenues, safeguarding organizations interests, securing wheels business, securing projects and profits, putting employees first. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
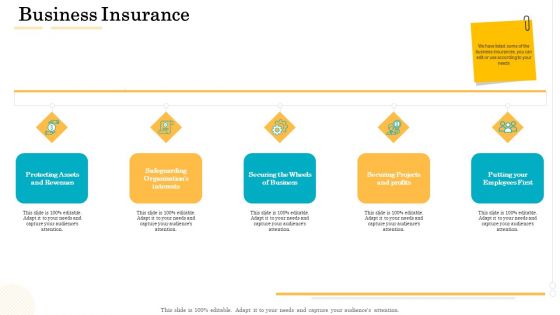
Administrative Regulation Business Insurance Ppt PowerPoint Presentation Templates PDF
This is a administrative regulation business insurance ppt powerpoint presentation templates pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like protecting assets and revenues, safeguarding organizations interests, securing wheels business, securing projects and profits, putting employees first. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Business Strategy Development Process Business Insurance Ideas PDF
Presenting business strategy development process business insurance ideas pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like protecting assets and revenues, safeguarding organizations interests, securing the wheels of business, securing projects and profits. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
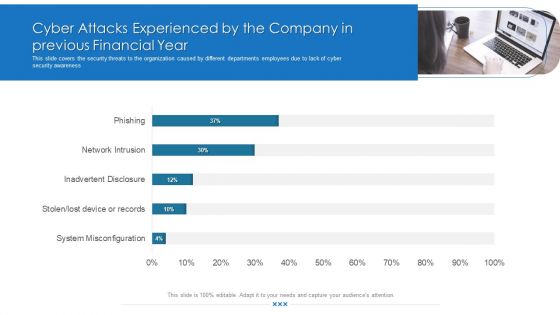
Cyber Attacks Experienced By The Company In Previous Financial Year Download PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. Deliver and pitch your topic in the best possible manner with this cyber attacks experienced by the company in previous financial year download pdf. Use them to share invaluable insights on cyber attacks experienced by the company in previous financial year and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
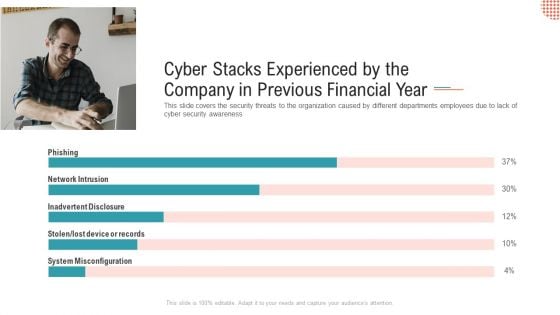
Cyber Stacks Experienced By The Company In Previous Financial Year Ppt Show Themes PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness Deliver and pitch your topic in the best possible manner with this cyber stacks experienced by the company in previous financial year ppt show themes pdf. Use them to share invaluable insights on network intrusion, inadvertent disclosure, system misconfiguration and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
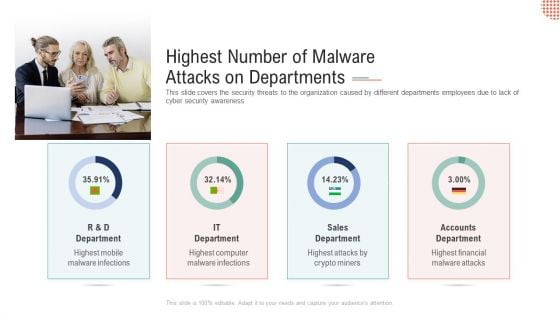
Highest Number Of Malware Attacks On Departments Ppt Inspiration Deck PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness Deliver an awe-inspiring pitch with this creative highest number of malware attacks on departments ppt inspiration deck pdf. bundle. Topics like r ans d department, sales department, accounts department can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Table Of Contents For Data Breach Prevention Recognition Ppt Model Skills PDF
Presenting table of contents for data breach prevention recognition ppt model skills pdf to provide visual cues and insights. Share and navigate important information on fourteen stages that need your due attention. This template can be used to pitch topics like budget, communication plan, security awareness, security programs, cost. In addition, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.
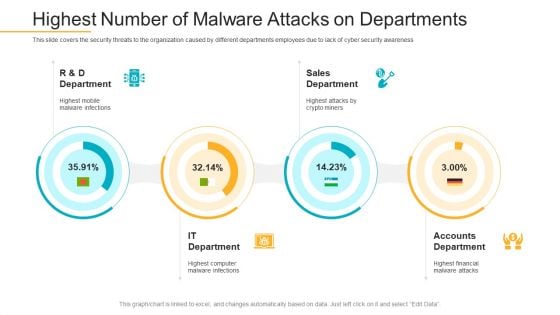
Data Breach Prevention Recognition Highest Number Of Malware Attacks On Departments Pictures PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. Deliver and pitch your topic in the best possible manner with this data breach prevention recognition highest number of malware attacks on departments pictures pdf. Use them to share invaluable insights on sales department, accounts department, it department and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
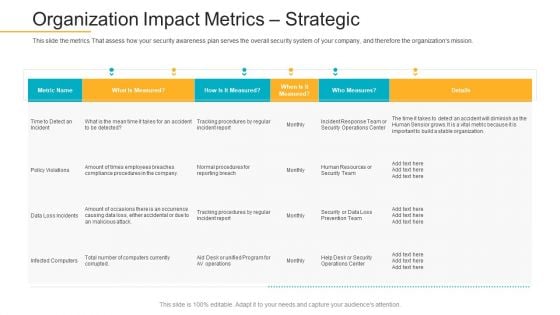
Data Breach Prevention Recognition Organization Impact Metrics Strategic Microsoft PDF
This slide the metrics That assess how your security awareness plan serves the overall security system of your company, and therefore the organizations mission. Deliver and pitch your topic in the best possible manner with this data breach prevention recognition organization impact metrics strategic microsoft pdf. Use them to share invaluable insights on organization impact metrics strategic and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
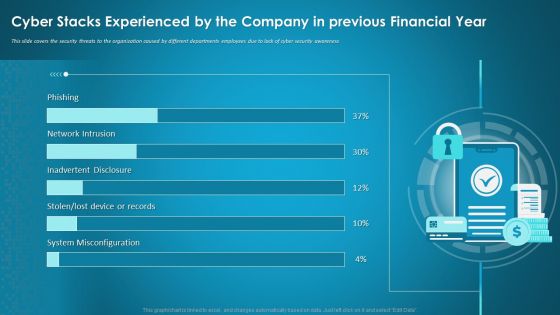
Cyber Stacks Experienced By The Company In Previous Financial Year Ppt Summary PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. Deliver an awe-inspiring pitch with this creative cyber stacks experienced by the company in previous financial year ppt summary pdf bundle. Topics like cyber stacks experienced by the company in previous financial year can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
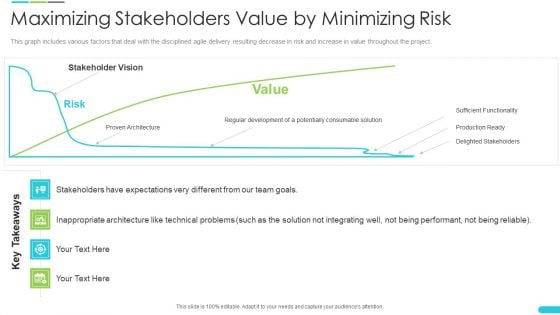
Discipline Agile Delivery Software Development Maximizing Stakeholders Value By Minimizing Risk Brochure PDF
Listed here are the metrics used by the organisation to measure agile capability on the basis of product performance, security level and user satisfaction. Deliver an awe-inspiring pitch with this creative discipline agile delivery software development maximizing stakeholders value by minimizing risk brochure pdf bundle. Topics like organisation, measure agile capability, product performance, security, planning can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
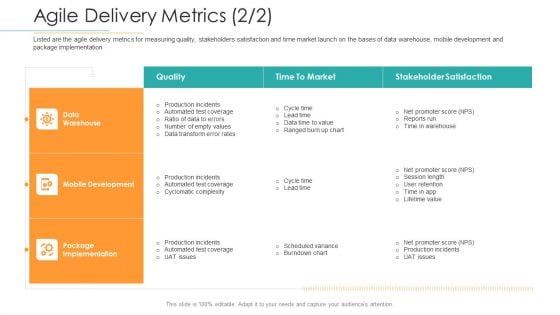
Disciplined Agile Distribution Responsibilities Agile Delivery Metrics Quality Formats PDF
Listed here are the metrics used by the organisation to measure agile capability on the basis of product performance, security level and user satisfaction. Deliver an awe-inspiring pitch with this creative disciplined agile distribution responsibilities agile delivery metrics quality formats pdf bundle. Topics like organisation, measure agile capability, product performance, security, planning can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Major Market Trends Of Intelligent Infrastructure Microsoft PDF
This is a major market trends of intelligent infrastructure microsoft pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security becomes central, infrastructure design security, backbone and access. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
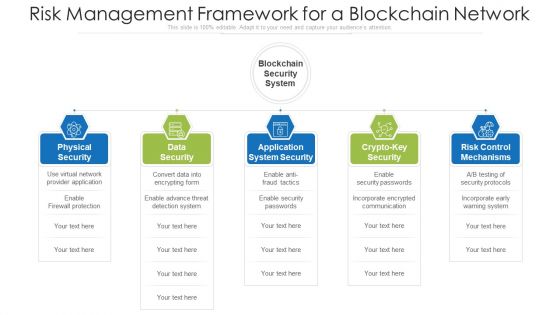
Risk Management Framework For A Blockchain Network Ppt PowerPoint Presentation Portfolio Format Ideas PDF
Persuade your audience using this risk management framework for a blockchain network ppt powerpoint presentation portfolio format ideas pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including application system security, risk control mechanisms, physical security. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
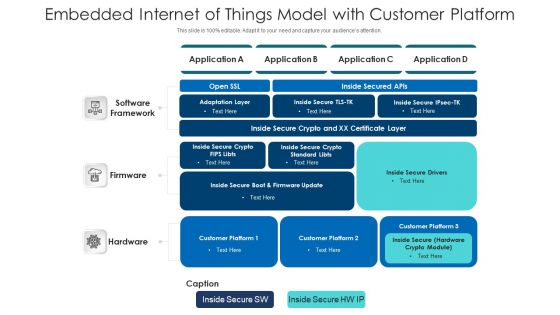
Embedded Internet Of Things Model With Customer Platform Ppt PowerPoint Presentation Infographics Pictures PDF
Presenting embedded internet of things model with customer platform ppt powerpoint presentation infographics pictures pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including inside secure crypto, inside secure boot and firmware update, software framework. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
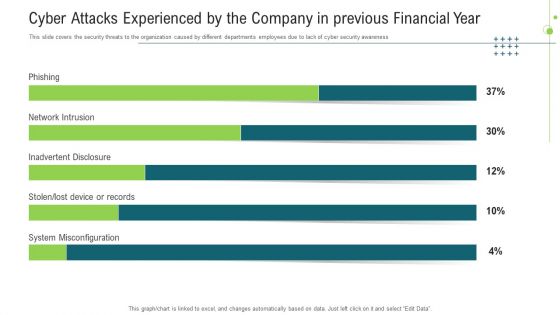
Cyber Attacks Experienced By The Company In Previous Financial Year Ppt Infographics PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. Deliver an awe inspiring pitch with this creative cyber attacks experienced by the company in previous financial year ppt infographics pdf bundle. Topics like cyber attacks experienced by the company in previous financial year can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.


 Continue with Email
Continue with Email

 Home
Home


































