Safety

Eye With Code Technology PowerPoint Templates And PowerPoint Backgrounds 0311
Microsoft PowerPoint Template and Background with eye viewing digital information represented by ones and zeros Double your growth with our Eye With Code Technology PowerPoint Templates And PowerPoint Backgrounds 0311. Download without worries with our money back guaranteee.

Data Fraud Business PowerPoint Templates And PowerPoint Backgrounds 0511
Microsoft PowerPoint Template and Background with a magnifying glass over computer data background Launch your campaign with our Data Fraud Business PowerPoint Templates And PowerPoint Backgrounds 0511. Make sure your presentation gets the attention it deserves.

Data Fraud Business PowerPoint Themes And PowerPoint Slides 0511
Microsoft PowerPoint Theme and Slide with a magnifying glass over computer data Slide Exhort your team with our Data Fraud Business PowerPoint Themes And PowerPoint Slides 0511. Urge them on to go one better.

Eye With Code Technology PowerPoint Themes And PowerPoint Slides 0311
Microsoft PowerPoint Theme and Slide with eye viewing digital information represented by ones and zeros Evoke dormant ambitions with our Eye With Code Technology PowerPoint Themes And PowerPoint Slides 0311. Encourage desires to develop anew.
Financing Catalogue For Security Underwriting Agreement IPO And Manda Deals Split By Sectors Icons PDF
The slide provides the graph of current deals bifurcation by sectors-automobile, construction, financials services etc. under different services merger and acquisition, underwriting, asset management, sales and trading, advisory etc. Deliver and pitch your topic in the best possible manner with this financing catalogue for security underwriting agreement ipo and manda deals split by sectors icons pdf. Use them to share invaluable insights on automobile, construction, financials services and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
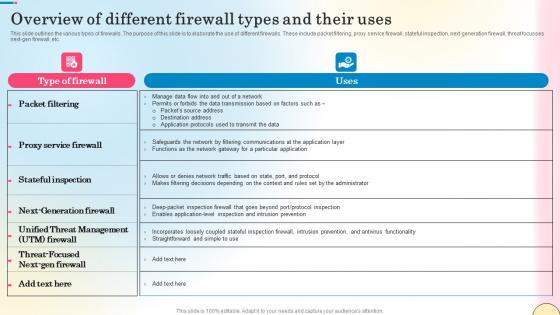
Overview Of Different Firewall Types And Their Uses Network Security Infographics Pdf
This slide talks about the role of Firewall-as-a-Service inside a secure access service edge framework. The purpose of this slide is to explain how FWaaS and SASE work together to provide network security. The components include SASE, Cloudflare Magic Firewall, etc. Find a pre-designed and impeccable Overview Of Different Firewall Types And Their Uses Network Security Infographics Pdf. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide talks about the role of Firewall-as-a-Service inside a secure access service edge framework. The purpose of this slide is to explain how FWaaS and SASE work together to provide network security. The components include SASE, Cloudflare Magic Firewall, etc.
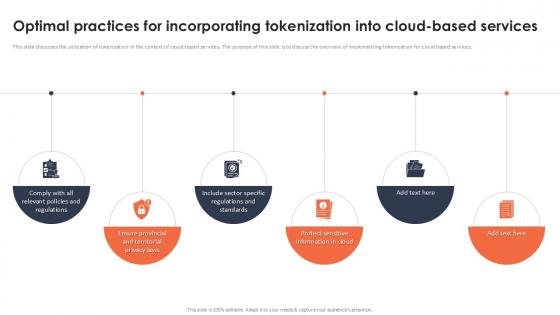
Optimal Practices For Incorporating Tokenization Into Cloud Securing Your Data Ppt Sample
This slide discusses the utilization of tokenization in the context of cloud-based services. The purpose of this slide is to discuss the overview of implementing tokenization for cloud based services. Are you searching for a Optimal Practices For Incorporating Tokenization Into Cloud Securing Your Data Ppt Sample that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Optimal Practices For Incorporating Tokenization Into Cloud Securing Your Data Ppt Sample from Slidegeeks today. This slide discusses the utilization of tokenization in the context of cloud-based services. The purpose of this slide is to discuss the overview of implementing tokenization for cloud based services.

Organize Cyber Security Training For Employees Regularly Ppt PowerPoint Presentation File Diagrams PDF
The following slide depicts the staff cyber security training plan to educate them regarding technology threats and practices. It mainly includes elements such as topics to be covered, target audience, trainer name, mode, proposed date, timings etc. Create an editable Organize Cyber Security Training For Employees Regularly Ppt PowerPoint Presentation File Diagrams PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre designed presentation templates help save time. Organize Cyber Security Training For Employees Regularly Ppt PowerPoint Presentation File Diagrams PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Secure Files Security PowerPoint Presentation Slides C
Microsoft PowerPoint Slides and Backgrounds with illustration of a lock place dinfront of and open file folder Do not leave it all up to fate. Fashion your destiny with our Secure Files Security PowerPoint Presentation Slides C.
Secure Files Security PowerPoint Presentation Slides Cc
Microsoft PowerPoint Slides and Backgrounds with illustration of a lock place dinfront of and open file folder Achieve strong & sustainable quality gains with our Secure Files Security PowerPoint Presentation Slides Cc. They will make you look good.

Secure Files Security PowerPoint Presentation Slides F
Microsoft PowerPoint Slides and Backgrounds with illustration of a lock place dinfront of and open file folder Give your thoughts an exclusive feel. Our Secure Files Security PowerPoint Presentation Slides F will give them a distinctive touch.

Secure Files Security PowerPoint Presentation Slides R
Microsoft PowerPoint Slides and Backgrounds with illustration of a lock place dinfront of and open file folder Your ideas will raise the stocks. Gain equity with our Secure Files Security PowerPoint Presentation Slides R.

Secure Files Security PowerPoint Presentation Slides S
Microsoft PowerPoint Slides and Backgrounds with illustration of a lock place dinfront of and open file folder Give a fillip to your campaign. Give it a fitting finale with our Secure Files Security PowerPoint Presentation Slides S.
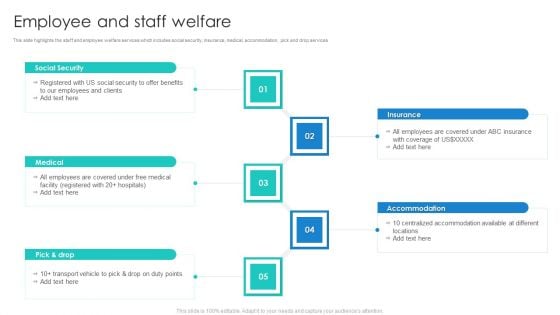
Manpower Corporate Security Business Profile Employee And Staff Welfare Designs PDF
This slide highlights the staff and employee welfare services which includes social security, insurance, medical, accommodation, pick and drop services. This is a Manpower Corporate Security Business Profile Employee And Staff Welfare Designs PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Medical, Social Security, Insurance, Accommodation. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
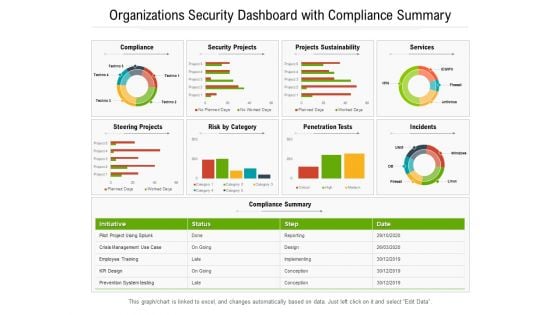
Organizations Security Dashboard With Compliance Summary Ppt PowerPoint Presentation Gallery Layouts PDF
Presenting this set of slides with name organizations security dashboard with compliance summary ppt powerpoint presentation gallery layouts pdf. The topics discussed in these slides are sustainability, security, services. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
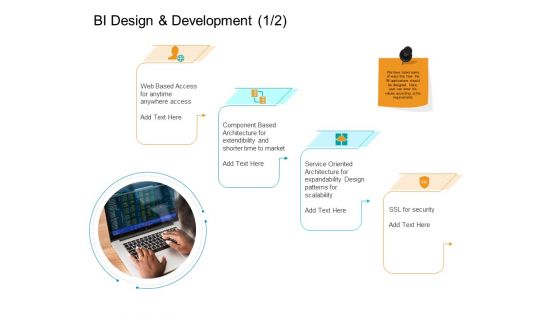
Facts Assessment BI Design And Development Security Ppt PowerPoint Presentation Slides Master Slide PDF
Presenting this set of slides with name facts assessment bi design and development security ppt powerpoint presentation slides master slide pdf. This is a four stage process. The stages in this process are web based access, component based architecture, service oriented architecture, ssl security. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
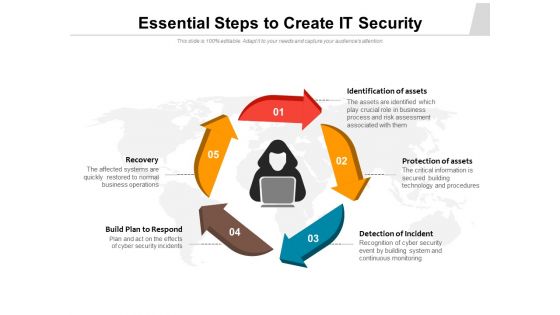
Essential Steps To Create IT Security Ppt PowerPoint Presentation Design Templates PDF
Presenting essential steps to create it security ppt powerpoint presentation design templates pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including identification of assets, protection of assets, detection of incident, recovery, build plan to respond. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
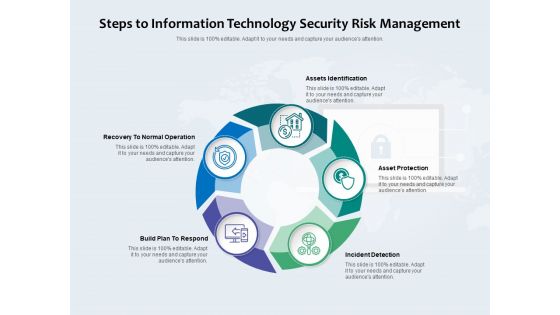
Steps To Information Technology Security Risk Management Ppt PowerPoint Presentation Gallery Example File PDF
Presenting steps to information technology security risk management ppt powerpoint presentation gallery example file pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including assets identification, asset protection, incident detection, build plan to respond, recovery to normal operation. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
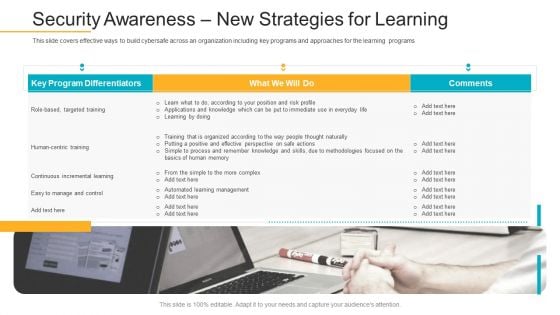
Data Breach Prevention Recognition Security Awareness New Strategies For Learning Download PDF
This slide covers effective ways to build cybersafe across an organization including key programs and approaches for the learning programs. Deliver an awe-inspiring pitch with this creative data breach prevention recognition security awareness new strategies for learning download pdf bundle. Topics like cybersafe across, organization, key programs, approaches, learning programs can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
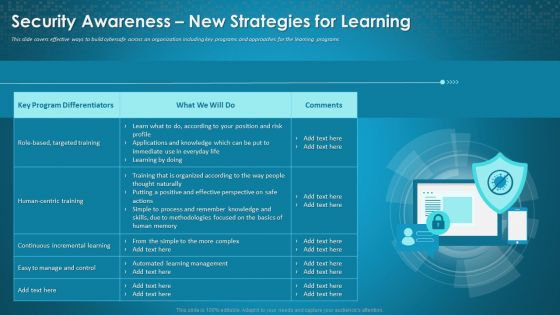
Organizational Network Staff Learning Security Awareness New Strategies For Learning Rules PDF
This slide cover effective way to build cybersafe across on organization including key programs and approaches for the learning programs. Deliver an awe-inspiring pitch with this creative organizational network staff learning security awareness new strategies for learning rules pdf bundle. Topics like human centric training, manage and control, targeted training can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Awareness New Strategies For Learning Ppt Infographic Template Graphic Images PDF
This slide covers effective ways to build cybersafe across an organization including key programs and approaches for the learning programs. Deliver and pitch your topic in the best possible manner with this Security Awareness New Strategies For Learning Ppt Infographic Template Graphic Images Pdf. Use them to share invaluable insights on key program, targeted training, management, methodologies, process and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
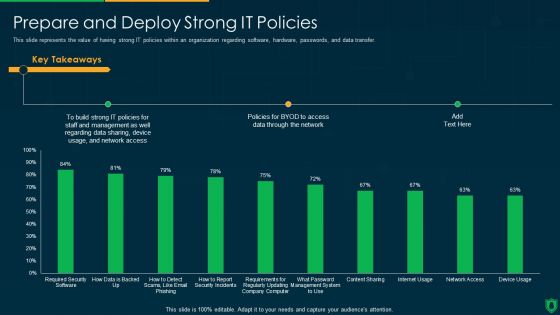
Info Security Prepare And Deploy Strong IT Policies Ppt PowerPoint Presentation File Model PDF
This slide represents the value of having strong IT policies within an organization regarding software, hardware, passwords, and data transfer. Deliver an awe inspiring pitch with this creative info security prepare and deploy strong it policies ppt powerpoint presentation file model pdf bundle. Topics like build strong, it policies, data sharing, access data can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Security And Performance Digital Marketing Google Analytics For All Web Tracking Mockup PDF
This template covers tools to measure marketing analytics such as google analytics for all web tracking, google data studio to build real-time reporting dashboards and google data studio reports.Deliver and pitch your topic in the best possible manner with this Security And Performance Digital Marketing Google Analytics For All Web Tracking Mockup PDF. Use them to share invaluable insights on Demographics, Social Networks, Sessions and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
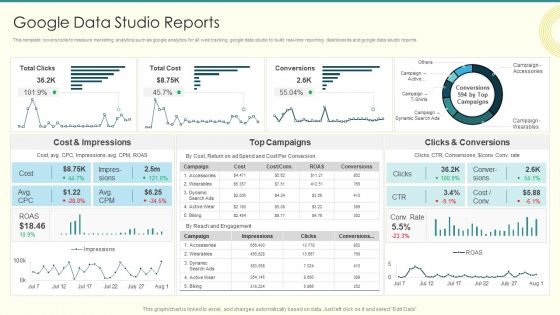
Security And Performance Digital Marketing Google Data Studio Reports Brochure PDF
This template covers tools to measure marketing analytics such as google analytics for all web tracking, google data studio to build real-time reporting dashboards and google data studio reports.Deliver an awe inspiring pitch with this creative Security And Performance Digital Marketing Google Data Studio Reports Brochure PDF bundle. Topics like Impressions, Clicks Conversions, Cost Impressions can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
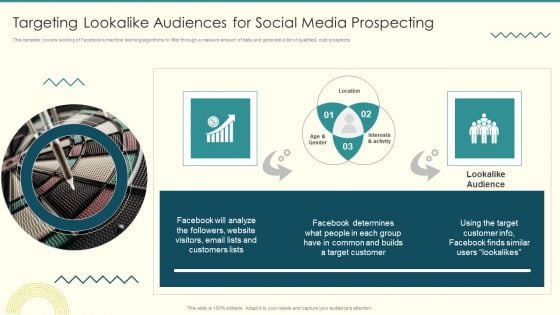
Security And Performance Digital Marketing Targeting Lookalike Audiences For Social Media Prospecting Themes PDF
This template covers working of Facebooks machine learning or algorithms to filter through a massive amount of data and generate a list of qualified, cold prospects.Deliver an awe inspiring pitch with this creative Security And Performance Digital Marketing Targeting Lookalike Audiences For Social Media Prospecting Themes PDF bundle. Topics like Interests Activity, Common Builds, Target Customer can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Table Of Contents For Security And Performance Digital Marketing Playbook Slide Inspiration PDF
This is a Table Of Contents For Security And Performance Digital Marketing Playbook Slide Inspiration PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Target Strategic, Build Personas, Create Content. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Infrastructure IT Security IT Budget For Fy2020 Ppt Ideas Elements PDF
This slide represents the budget for IT infrastructure after implementing cyber security, and it also shows the amount each task will cost the company. Deliver an awe inspiring pitch with this creative it infrastructure it security it budget for fy2020 ppt ideas elements pdf bundle. Topics like cloud security, costs, software application, security services can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
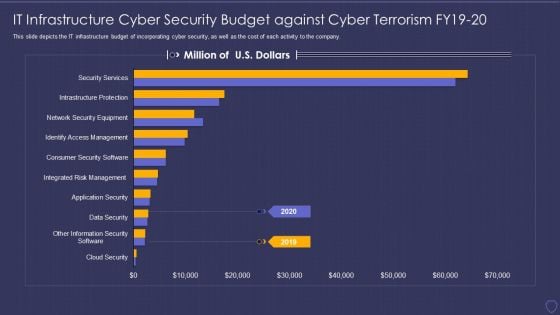
Global Cyber Terrorism Incidents On The Rise IT IT Infrastructure Cyber Security Budget Pictures PDF
This slide depicts the IT infrastructure budget of incorporating cyber security, as well as the cost of each activity to the company. Deliver an awe inspiring pitch with this creative global cyber terrorism incidents on the rise it it infrastructure cyber security budget pictures pdf bundle. Topics like data security, infrastructure protections, access management, security service can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
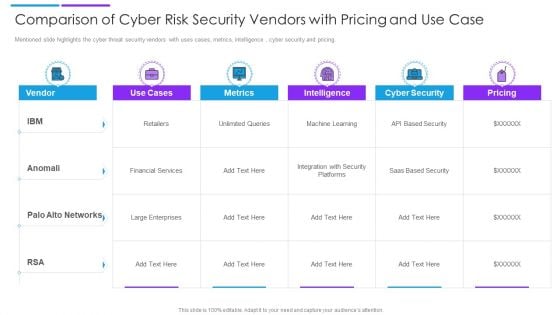
Comparison Of Cyber Risk Security Vendors With Pricing And Use Case Formats PDF
Mentioned slide highlights the cyber threat security vendors with uses cases, metrics, intelligence , cyber security and pricing. Pitch your topic with ease and precision using this comparison of cyber risk security vendors with pricing and use case formats pdf. This layout presents information on financial services, cyber security, intelligence. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
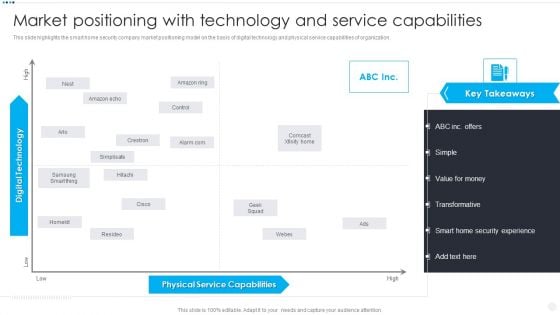
Smart Home Security Solutions Company Profile Market Positioning With Technology Information PDF
This slide highlights the smart home security company market positioning model on the basis of digital technology and physical service capabilities of organization. This is a Smart Home Security Solutions Company Profile Market Positioning With Technology Information PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Physical Service Capabilities, Digital Technology High. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Information Security Phase 3 Respond To Cloud Protection Issues Ppt Layouts Influencers PDF
This slide represents phase 3 of cloud security, such as respond to cloud protection issues. It includes an advanced authentication process, manages cloud access standards when new services come up, and eliminates malware from cloud services. Deliver and pitch your topic in the best possible manner with this Cloud Information Security Phase 3 Respond To Cloud Protection Issues Ppt Layouts Influencers PDF. Use them to share invaluable insights on Advanced Authentication, Cloud Access, Eliminate Malware and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cloud Security Assessment Phase 3 Respond To Cloud Protection Issues Topics PDF
This slide represents phase 3 of cloud security, such as respond to cloud protection issues. It includes an advanced authentication process, manages cloud access standards when new services come up, and eliminates malware from cloud services.Deliver and pitch your topic in the best possible manner with this Cloud Security Assessment Phase 3 Respond To Cloud Protection Issues Topics PDF Use them to share invaluable insights on Authentication Process, Access Standards, Eliminate Malware and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
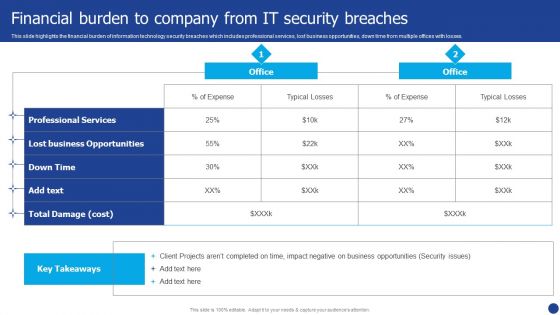
Information Technology Threat Mitigation Methods Financial Burden To Company From IT Security Breaches Formats PDF
This slide highlights the financial burden of information technology security breaches which includes professional services, lost business opportunities, down time from multiple offices with losses. Deliver and pitch your topic in the best possible manner with this Information Technology Threat Mitigation Methods Financial Burden To Company From IT Security Breaches Formats PDF. Use them to share invaluable insights on Professional Services, Lost Business Opportunities, Expense and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Website Audit To Increase Conversion Rate Website Security Auditing And Testing Background PDF
This slide highlights the website security audit which includes host discovery, services inspection, services fingerprinting, site structure, web application analysis, and code assessment. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Website Audit To Increase Conversion Rate Website Security Auditing And Testing Background PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.
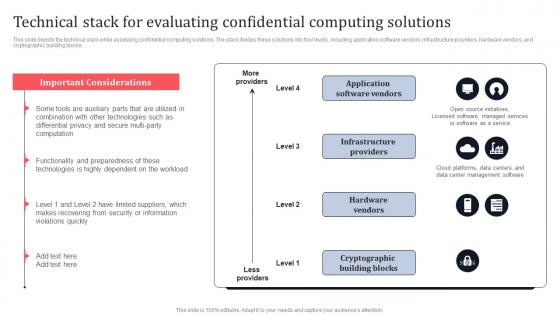
Technical Stack For Evaluating Confidential Computing Solutions Secure Multi Party Topics Pdf
This slide depicts the technical stack while assessing confidential computing solutions. The stack divides these solutions into four levels, including application software vendors, infrastructure providers, hardware vendors, and cryptographic building blocks. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Technical Stack For Evaluating Confidential Computing Solutions Secure Multi Party Topics Pdf and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide depicts the technical stack while assessing confidential computing solutions. The stack divides these solutions into four levels, including application software vendors, infrastructure providers, hardware vendors, and cryptographic building blocks.
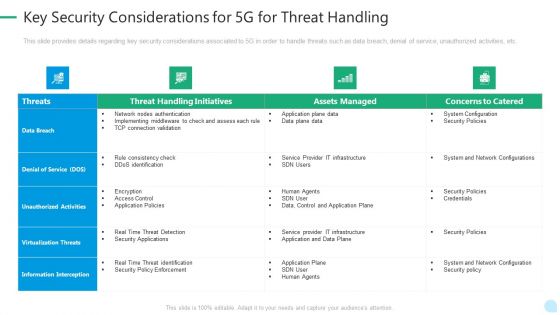
5G Network Technology Key Security Considerations For 5G For Threat Handling Ppt Gallery Gridlines PDF
This slide provides details regarding key security considerations associated to 5G in order to handle threats such as data breach, denial of service, unauthorized activities, etc. Deliver an awe inspiring pitch with this creative 5g network technology key security considerations for 5g for threat handling ppt gallery gridlines pdf bundle. Topics like virtualization threats, information interception, security policies, infrastructure can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
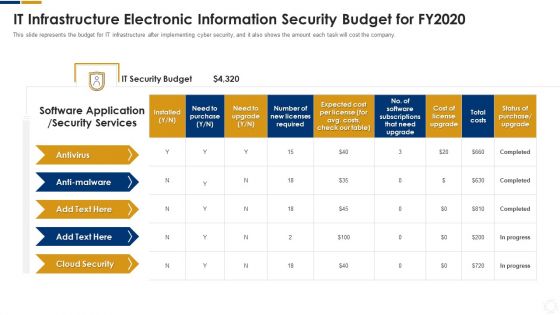
Cybersecurity IT Infrastructure Electronic Information Security Budget For FY2020 Ppt Infographics Graphics Download PDF
This slide represents the budget for IT infrastructure after implementing cyber security, and it also shows the amount each task will cost the company. Deliver an awe inspiring pitch with this creative cybersecurity it infrastructure electronic information security budget for fy2020 ppt infographics graphics download pdf bundle. Topics like required, application, security services, costs can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
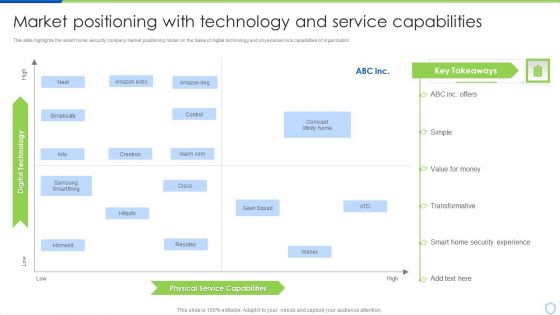
Security And Surveillance Company Profile Market Positioning With Technology Mockup PDF
This slide highlights the smart home security company market positioning model on the basis of digital technology and physical service capabilities of organization. Deliver an awe inspiring pitch with this creative Security And Surveillance Company Profile Market Positioning With Technology Mockup PDF bundle. Topics like Monitoring, Bluestone Security, Launched Integrated can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Computer Security Web Internet Icons PowerPoint Slides And Ppt Diagram Templates
Computer Security Web Internet Icons PowerPoint Slides And PPT Diagram Templates-These high quality powerpoint pre-designed slides and powerpoint templates have been carefully created by our professional team to help you impress your audience. All slides have been created and are 100% editable in powerpoint. Each and every property of any graphic - color, size, orientation, shading, outline etc. can be modified to help you build an effective powerpoint presentation. Any text can be entered at any point in the powerpoint template or slide. Simply DOWNLOAD, TYPE and PRESENT! Compose your song with our Computer Security Web Internet Icons PowerPoint Slides And Ppt Diagram Templates. You will come out on top.
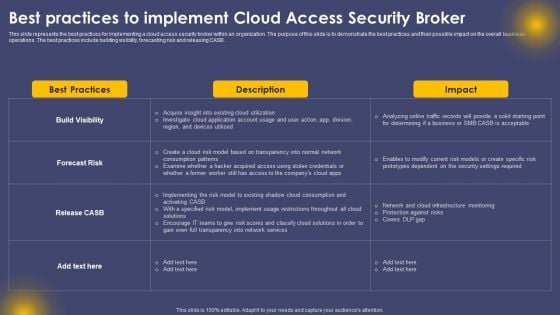
Best Practices To Implement Cloud Access Security Broker Ppt Portfolio Influencers PDF
This slide represents the best practices for implementing a cloud access security broker within an organization. The purpose of this slide is to demonstrate the best practices and their possible impact on the overall business operations. The best practices include building visibility, forecasting risk and releasing CASB. There are so many reasons you need a Best Practices To Implement Cloud Access Security Broker Ppt Portfolio Influencers PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Mastering Blockchain Wallets Best Practices To Optimize Web Wallet Security BCT SS V
This slide covers tips to enhance web wallet security for users. The purpose of this template is to provide recommendations to build strong security with practices such as regularly updating devices operating system, verifying the authenticity of websites, exercising caution when using public WIFI networks, using dedicated devices, etc. Get a simple yet stunning designed Mastering Blockchain Wallets Best Practices To Optimize Web Wallet Security BCT SS V. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Mastering Blockchain Wallets Best Practices To Optimize Web Wallet Security BCT SS V can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide covers tips to enhance web wallet security for users. The purpose of this template is to provide recommendations to build strong security with practices such as regularly updating devices operating system, verifying the authenticity of websites, exercising caution when using public WIFI networks, using dedicated devices, etc.
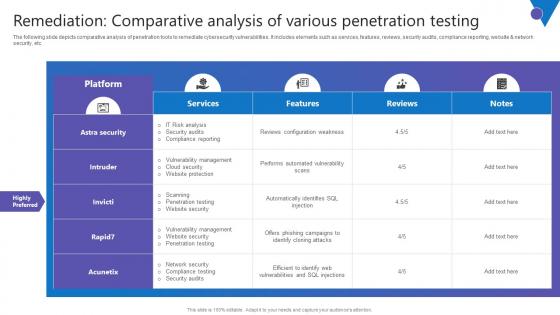
Remediation Comparative Analysis Comprehensive Guide To Blockchain Digital Security Portrait Pdf
The following slide depicts comparative analysis of penetration tools to remediate cybersecurity vulnerabilities. It includes elements such as services, features, reviews, security audits, compliance reporting, website and network security, etc. Take your projects to the next level with our ultimate collection of Remediation Comparative Analysis Comprehensive Guide To Blockchain Digital Security Portrait Pdf. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest The following slide depicts comparative analysis of penetration tools to remediate cybersecurity vulnerabilities. It includes elements such as services, features, reviews, security audits, compliance reporting, website and network security, etc.
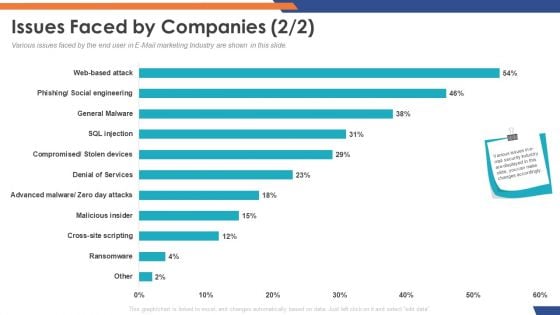
Email Security Market Research Report Issues Faced By Companies Cross Site Download PDF
Presenting this set of slides with name email security market research report issues faced by companies cross site download pdf. The topics discussed in these slides are general malware, social engineering, cross site scripting, denial of service, web based attack. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
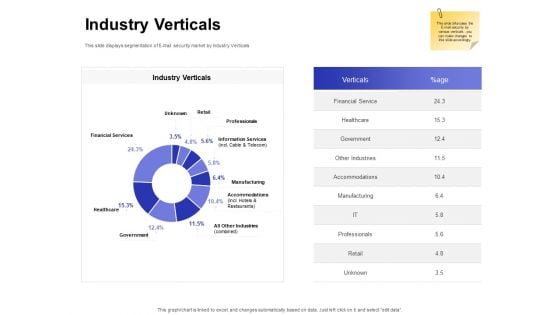
Global Cloud Based Email Security Market Industry Verticals Retail Demonstration PDF
Presenting this set of slides with name global cloud based email security market industry verticals retail demonstration pdf. The topics discussed in these slides are financial service, healthcare, government, accommodations, professionals, manufacturing, retail. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Global Cloud Based Email Security Market Issues Faced By Companies Download PDF
Presenting this set of slides with name global cloud based email security market issues faced by companies download pdf. The topics discussed in these slides are general malware, social engineering, cross site scripting, denial of service, web based attack. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Global Cloud Based Email Security Market About Us Ppt Layouts Infographics PDF
Presenting this set of slides with name global cloud based email security market about us ppt layouts infographics pdf. This is a three stage process. The stages in this process are target audiences, premium services, value clients. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
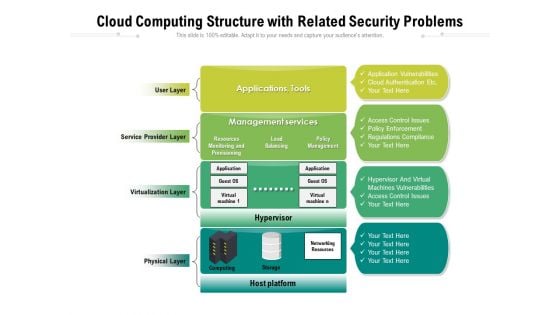
Cloud Computing Structure With Related Security Problems Ppt PowerPoint Presentation Gallery Infographics PDF
Presenting this set of slides with name cloud computing structure with related security problems ppt powerpoint presentation gallery infographics pdf. This is a four stage process. The stages in this process are management, services, virtualization. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Internet Security Kpis And Metrics Ppt PowerPoint Presentation Gallery Outline PDF
Showcasing this set of slides titled internet security kpis and metrics ppt powerpoint presentation gallery outline pdf. The topics addressed in these templates are threat detection, risk and compliance, services compliance. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
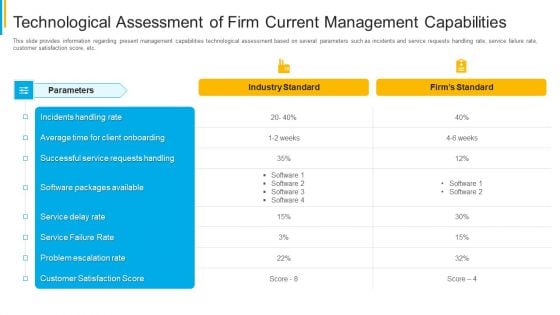
Project Security Administration IT Technological Assessment Of Firm Current Management Capabilities Professional PDF
This slide provides information regarding present management capabilities technological assessment based on several parameters such as incidents and service requests handling rate, service failure rate, customer satisfaction score, etc. Deliver and pitch your topic in the best possible manner with this project security administration it technological assessment of firm current management capabilities professional pdf. Use them to share invaluable insights on technological assessment of firm current management capabilities and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
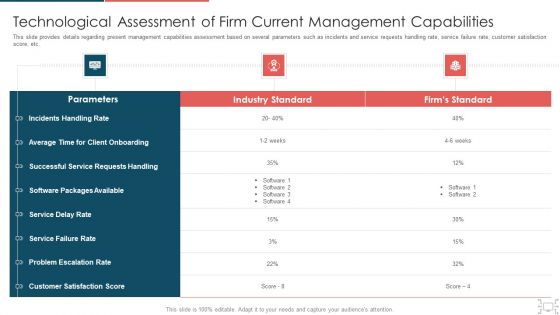
Cyber Security Administration In Organization Technological Assessment Of Firm Current Management Elements PDF
This slide provides details regarding present management capabilities assessment based on several parameters such as incidents and service requests handling rate, service failure rate, customer satisfaction score, etc. Deliver and pitch your topic in the best possible manner with this cyber security administration in organization technological assessment of firm current management elements pdf. Use them to share invaluable insights on technological assessment of firm current management capabilities and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
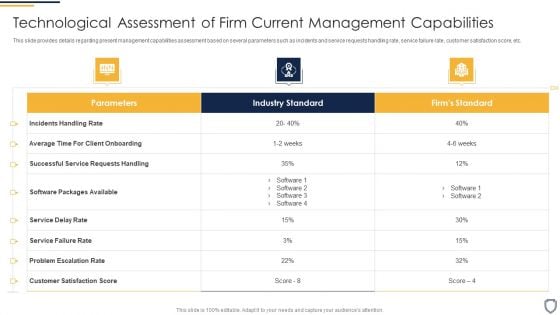
Corporate Security And Risk Management Technological Assessment Of Firm Current Designs PDF
This slide provides details regarding present management capabilities assessment based on several parameters such as incidents and service requests handling rate, service failure rate, customer satisfaction score, etc. Deliver and pitch your topic in the best possible manner with this corporate security and risk management technological assessment of firm current designs pdf. Use them to share invaluable insights on technological assessment of firm current management capabilities and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
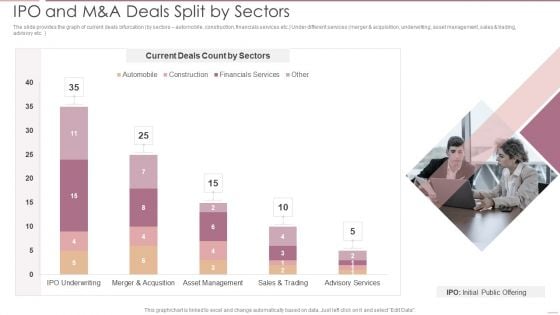
Investment Banking Security Underwriting Pitchbook IPO And M And A Deals Split By Sectors Brochure PDF
The slide provides the graph of current deals bifurcation by sectors automobile, construction, financials services etc.Under different services merger and acquisition, underwriting, asset management, sales trading, advisory etc.Deliver and pitch your topic in the best possible manner with this Investment Banking Security Underwriting Pitchbook IPO And M And A Deals Split By Sectors Brochure PDF Use them to share invaluable insights on Current Deals, Merger And Acquisition, Asset Management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
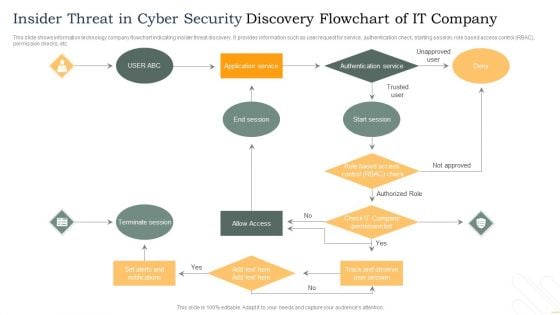
Insider Threat In Cyber Security Discovery Flowchart Of IT Company Template PDF
This slide shows information technology company flowchart indicating insider threat discovery. It provides information such as user request for service, authentication check, starting session, role based access control RBAC, permission checks, etc. Persuade your audience using this Insider Threat In Cyber Security Discovery Flowchart Of IT Company Template PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Terminate Session, Allow Access, Authentication Service. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
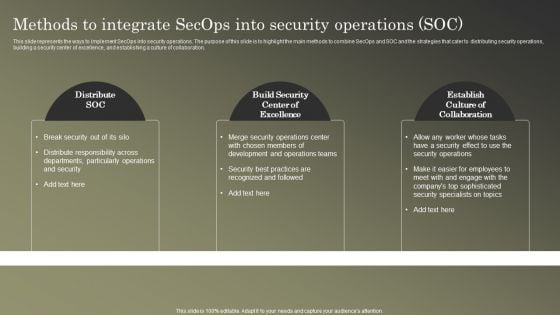
Cybersecurity Operations Cybersecops Methods To Integrate Secops Into Security Rules PDF
This slide represents the ways to implement SecOps into security operations. The purpose of this slide is to highlight the main methods to combine SecOps and SOC and the strategies that cater to distributing security operations, building a security center of excellence, and establishing a culture of collaboration. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Cybersecurity Operations Cybersecops Methods To Integrate Secops Into Security Rules PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Cybersecurity Operations Cybersecops Methods To Integrate Secops Into Security Rules PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
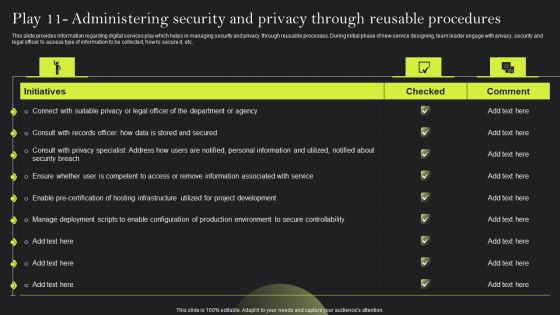
Playbook For Advancing Technology Play 11 Administering Security And Privacy Elements PDF
This slide provides information regarding digital services play which helps in managing security and privacy through reusable processes. During initial phase of new service designing, team leader engage with privacy, security and legal officer to assess type of information to be collected, how to secure it, etc. Retrieve professionally designed Playbook For Advancing Technology Play 11 Administering Security And Privacy Elements PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You dont have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
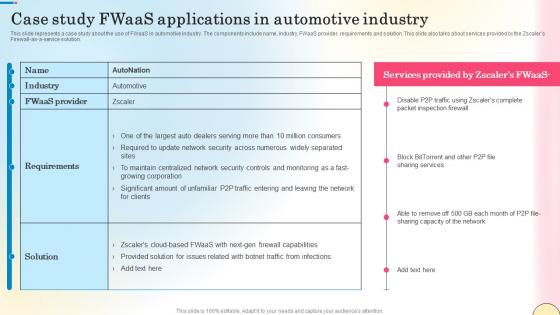
Case Study Fwaas Applications In Automotive Industry Network Security Clipart Pdf
This slide represents a case study about the use of FWaaS in automotive industry. The components include name, industry, FWaaS provider, requirements and solution. This slide also talks about services provided by the Zscalers Firewall-as-a-service solution. Present like a pro with Case Study Fwaas Applications In Automotive Industry Network Security Clipart Pdf Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide represents a case study about the use of FWaaS in automotive industry. The components include name, industry, FWaaS provider, requirements and solution. This slide also talks about services provided by the Zscalers Firewall-as-a-service solution.
Cloud Network Security Dimensions And Sections Ppt PowerPoint Presentation Icon Background Images PDF
Presenting cloud network security dimensions and sections ppt powerpoint presentation icon background images pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like security, service, threats. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
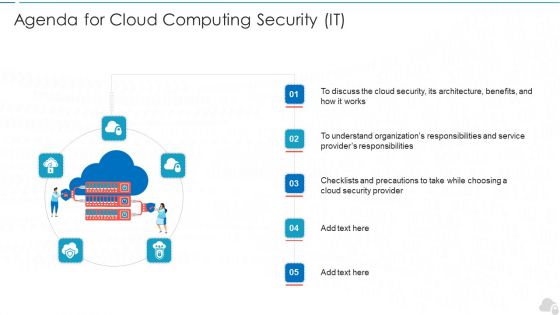
Agenda For Cloud Computing Security IT Ppt Infographic Template Inspiration PDF
Presenting agenda for cloud computing security it ppt infographic template inspiration pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like cloud security, service, architecture, organizations, responsibilities. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Prepare Data Backup For Sensitive Information IT Security IT Ppt Infographics Clipart PDF
This slide represents the preparation of data backup for sensitive information and how data backup should be created and stored within an organization. Deliver an awe inspiring pitch with this creative prepare data backup for sensitive information it security it ppt infographics clipart pdf bundle. Topics like manipulation, secure, disasters, cloud services can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Desktop Security Management Prepare Data Backup For Sensitive Information Download PDF
This slide represents the preparation of data backup for sensitive information and how data backup should be created and stored within an organization. Deliver an awe inspiring pitch with this creative desktop security management prepare data backup for sensitive information download pdf bundle. Topics like information, secure, service can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.


 Continue with Email
Continue with Email

 Home
Home


































