Security Architecture
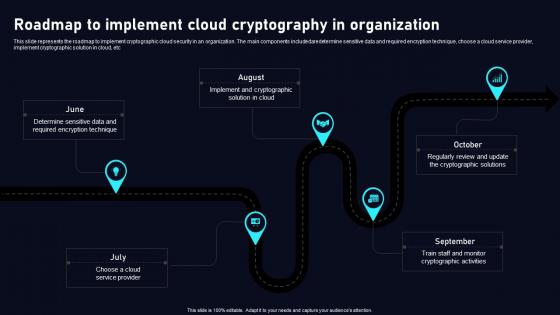
Roadmap To Implement Cloud Data Security Using Cryptography Information Pdf
This slide represents the roadmap to implement cryptographic cloud security in an organization. The main components includedaredetermine sensitive data and required encryption technique, choose a cloud service provider, implement cryptographic solution in cloud, etc Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Roadmap To Implement Cloud Data Security Using Cryptography Information Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Roadmap To Implement Cloud Data Security Using Cryptography Information Pdf today and make your presentation stand out from the rest This slide represents the roadmap to implement cryptographic cloud security in an organization. The main components includedaredetermine sensitive data and required encryption technique, choose a cloud service provider, implement cryptographic solution in cloud, etc
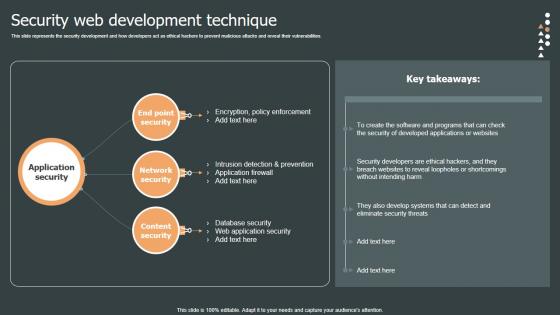
Security Web Development Role Web Designing User Engagement Topics PDF
This slide represents the security development and how developers act as ethical hackers to prevent malicious attacks and reveal their vulnerabilities. Are you searching for a Security Web Development Role Web Designing User Engagement Topics PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Security Web Development Role Web Designing User Engagement Topics PDF from Slidegeeks today. This slide represents the security development and how developers act as ethical hackers to prevent malicious attacks and reveal their vulnerabilities.
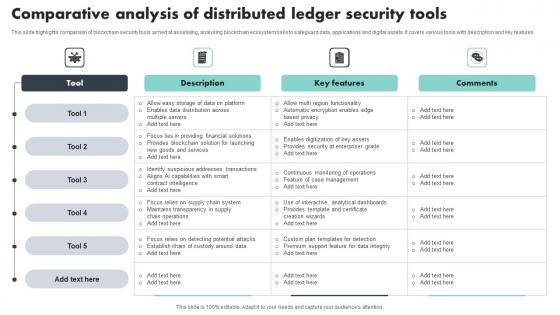
Comparative Analysis Of Distributed Ledger Security Tools Sample Pdf
This slide highlights comparison of blockchain security tools aimed at assessing, analysing blockchain ecosystem risks to safeguard data, applications and digital assets. It covers various tools with description and key features Showcasing this set of slides titled Comparative Analysis Of Distributed Ledger Security Tools Sample Pdf The topics addressed in these templates are Key Features, Comparative Analysis, Security Tools All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide highlights comparison of blockchain security tools aimed at assessing, analysing blockchain ecosystem risks to safeguard data, applications and digital assets. It covers various tools with description and key features

Global 5G Network Security Market Dynamics Designs Pdf
This slide shows 5g security market dynamics globally to understand market scenario . It further includes dynamics such as increasing cyber attacks , Emergence of IoT, AI, Machine Learning, and Blockchain Technologies etc. Showcasing this set of slides titled Global 5G Network Security Market Dynamics Designs Pdf. The topics addressed in these templates are Market Dynamics, Description. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide shows 5g security market dynamics globally to understand market scenario . It further includes dynamics such as increasing cyber attacks , Emergence of IoT, AI, Machine Learning, and Blockchain Technologies etc.
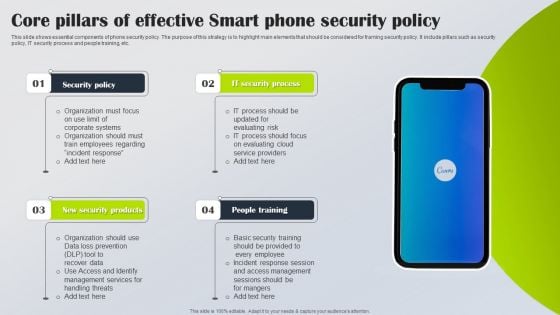
Core Pillars Of Effective Smart Phone Security Policy Slides PDF
This slide shows essential components of phone security policy. The purpose of this strategy is to highlight main elements that should be considered for framing security policy. It include pillars such as security policy, IT security process and people training, etc. Persuade your audience using this Core Pillars Of Effective Smart Phone Security Policy Slides PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Security Policy, IT Security Process, New Security Products. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Icons Slide For Zero Trust Security Template Pdf
Introducing our well designed Icons Slide For Zero Trust Security Template Pdf set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience. Our Icons Slide For Zero Trust Security Template Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Icons Slide For Cloud Data Security Using Cryptography Diagrams Pdf
Introducing our well designed Icons Slide For Cloud Data Security Using Cryptography Diagrams Pdf set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience. Our Icons Slide For Cloud Data Security Using Cryptography Diagrams Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Icons Slide For Tokenization Strategies For Data Security PPT Presentation
Introducing our well designed Icons Slide For Tokenization Strategies For Data Security PPT Presentation set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience. Our Icons Slide For Tokenization Strategies For Data Security PPT Presentation are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
5G Network Security Icon For Device Safety Sample Pdf
Pitch your topic with ease and precision using this 5G Network Security Icon For Device Safety Sample Pdf. This layout presents information on 5G Network Security, Device Safety. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Our 5G Network Security Icon For Device Safety Sample Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Employee Incentives Icon For Healthcare And Financial Security Designs Pdf
Showcasing this set of slides titled Employee Incentives Icon For Healthcare And Financial Security Designs Pdf The topics addressed in these templates are Employee Incentives, Icon For Healthcare, Financial Security All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Our Employee Incentives Icon For Healthcare And Financial Security Designs Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
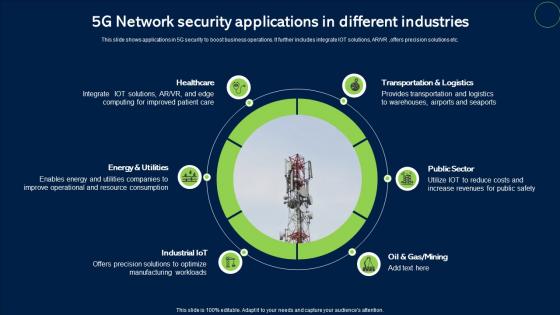
5G Network Security Applications In Different Industries Infographics Pdf
This slide shows applications in 5G security to boost business operations. It further includes integrate IOT solutions, ARVR ,offers precision solutions etc. Showcasing this set of slides titled 5G Network Security Applications In Different Industries Infographics Pdf. The topics addressed in these templates are Healthcare, Public Sector, Transportation And Logistics. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide shows applications in 5G security to boost business operations. It further includes integrate IOT solutions, ARVR ,offers precision solutions etc.

Internet Security Challenges And Solutions In Banking Industry Download Pdf
This slide showcase cyber security challenges in digital banking and tactics to mitigate data risk. It include challenges like malware, spoofing, phishing, third part service.Showcasing this set of slides titled Internet Security Challenges And Solutions In Banking Industry Download Pdf The topics addressed in these templates are Installing Intergraded, Introducing Firewall, Learning Algorisms All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcase cyber security challenges in digital banking and tactics to mitigate data risk. It include challenges like malware, spoofing, phishing, third part service.
Security Gate Icon In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Security Gate Icon In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Security Gate Icon that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Security Gate Icon In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Security System In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Security System In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Security System that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well-structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Security System In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Security Wireless In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Security Wireless In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Security Wireless that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Security Wireless In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Application Security Program In Powerpoint And Google Slides Cpb
Presenting our innovatively-designed set of slides titled Application Security Program In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Application Security Program that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well-structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Application Security Program In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Wifi Systems Security In Powerpoint And Google Slides Cpb
Presenting our innovatively-designed set of slides titled Wifi Systems Security In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Wifi Systems Security that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well-structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Wifi Systems Security In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Computer Personal Security In Powerpoint And Google Slides Cpb
Presenting our innovatively-designed set of slides titled Computer Personal Security In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Computer Personal Security that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well-structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Computer Personal Security In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
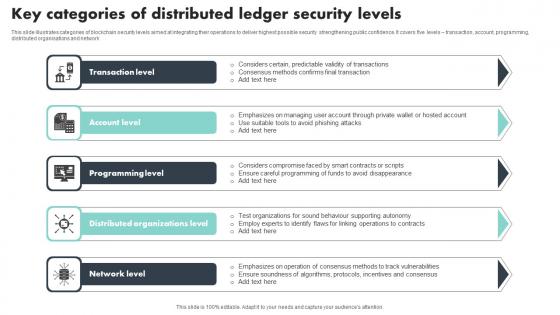
Key Categories Of Distributed Ledger Security Levels Portrait Pdf
This slide illustrates categories of blockchain security levels aimed at integrating their operations to deliver highest possible security strengthening public confidence. It covers five levels transaction, account, programming, distributed organisations and network Pitch your topic with ease and precision using this Key Categories Of Distributed Ledger Security Levels Portrait Pdf This layout presents information on Transaction Level, Account Level, Programming Level It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide illustrates categories of blockchain security levels aimed at integrating their operations to deliver highest possible security strengthening public confidence. It covers five levels transaction, account, programming, distributed organisations and network
Internet Of Things Security Icon For Software Management Template Pdf
Showcasing this set of slides titled Internet Of Things Security Icon For Software Management Template Pdf The topics addressed in these templates are Internet Of Things Security, Icon For Software, Management All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Our Internet Of Things Security Icon For Software Management Template Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Data Transfer Security Using Distributed Ledger Technology Icon Topics Pdf
Pitch your topic with ease and precision using this Data Transfer Security Using Distributed Ledger Technology Icon Topics Pdf This layout presents information on Data Transfer Security, Distributed Ledger, Technology Icon It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Our Data Transfer Security Using Distributed Ledger Technology Icon Topics Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Distributed Ledger Security Protocol List Icon Structure Pdf
Pitch your topic with ease and precision using this Distributed Ledger Security Protocol List Icon Structure Pdf This layout presents information on Data Transfer Security, Distributed Ledger, Technology Icon It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Our Distributed Ledger Security Protocol List Icon Structure Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Ecommerce Payment Security Using Distributed Ledger Technology Icon Portrait Pdf
Showcasing this set of slides titled Ecommerce Payment Security Using Distributed Ledger Technology Icon Portrait Pdf The topics addressed in these templates are Ecommerce Payment Security, Distributed Ledger, Technology Icon All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Our Ecommerce Payment Security Using Distributed Ledger Technology Icon Portrait Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Cyber Security Breach Icon Corrupting Devices Files Pictures Pdf
Pitch your topic with ease and precision using this Cyber Security Breach Icon Corrupting Devices Files Pictures Pdf This layout presents information on Cyber Security Breach, Icon Corrupting Devices Files It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Our Cyber Security Breach Icon Corrupting Devices Files Pictures Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Cyber Security Breach Icon Sending Malicious Emails Guidelines Pdf
Showcasing this set of slides titled Cyber Security Breach Icon Sending Malicious Emails Guidelines Pdf The topics addressed in these templates are Cyber Security Breach, Icon Sending Malicious Emails All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Our Cyber Security Breach Icon Sending Malicious Emails Guidelines Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
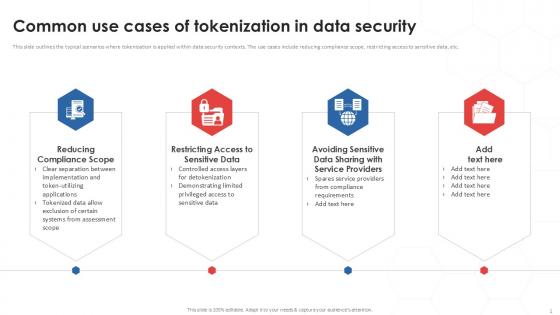
Common Use Cases Of Tokenization In Data Security PPT Template
This slide outlines the typical scenarios where tokenization is applied within data security contexts. The use cases include reducing compliance scope, restricting access to sensitive data, etc. Find a pre-designed and impeccable Common Use Cases Of Tokenization In Data Security PPT Template. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide outlines the typical scenarios where tokenization is applied within data security contexts. The use cases include reducing compliance scope, restricting access to sensitive data, etc.

Managing Technical And Non Website Security Management Action Plan
Mentioned slide provides insights into site security management tips which can be implemented by businesses to prevent hacking. It includes key components such as select secure domain registrar, use safe plugins, anti malware programs, regular backup, etc. Welcome to our selection of the Managing Technical And Non Website Security Management Action Plan. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. Mentioned slide provides insights into site security management tips which can be implemented by businesses to prevent hacking. It includes key components such as select secure domain registrar, use safe plugins, anti malware programs, regular backup, etc.

Comprehensive Guide For Website Website Security Management Action Plan
Mentioned slide provides insights into site security management tips which can be implemented by businesses to prevent hacking. It includes key components such as select secure domain registrar, use safe plugins, anti malware programs, regular backup, etc. Welcome to our selection of the Comprehensive Guide For Website Website Security Management Action Plan. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. Mentioned slide provides insights into site security management tips which can be implemented by businesses to prevent hacking. It includes key components such as select secure domain registrar, use safe plugins, anti malware programs, regular backup, etc.
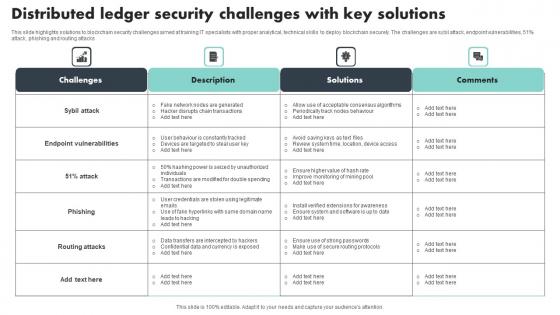
Distributed Ledger Security Challenges With Key Solutions Introduction Pdf
This slide highlights solutions to blockchain security challenges aimed at training IT specialists with proper analytical, technical skills to deploy blockchain securely. The challenges are sybil attack, endpoint vulnerabilities, 51percent attack, phishing and routing attacks Showcasing this set of slides titled Distributed Ledger Security Challenges With Key Solutions Introduction Pdf The topics addressed in these templates are Endpoint Vulnerabilities, Routing Attacks, Phishing All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide highlights solutions to blockchain security challenges aimed at training IT specialists with proper analytical, technical skills to deploy blockchain securely. The challenges are sybil attack, endpoint vulnerabilities, 51 percent attack, phishing and routing attacks

Web Consulting Business Website Security Management Action Plan
Mentioned slide provides insights into site security management tips which can be implemented by businesses to prevent hacking. It includes key components such as select secure domain registrar, use safe plugins, anti malware programs, regular backup, etc. The Web Consulting Business Website Security Management Action Plan is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. Mentioned slide provides insights into site security management tips which can be implemented by businesses to prevent hacking. It includes key components such as select secure domain registrar, use safe plugins, anti malware programs, regular backup, etc.

Compound Annual Growth Rate CAGR Of Application Security Testing
This slide depicts the market growth of application security by software tools such as white-box testing, black-box testing, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Compound Annual Growth Rate CAGR Of Application Security Testing template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Compound Annual Growth Rate CAGR Of Application Security Testing that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide depicts the market growth of application security by software tools such as white-box testing, black-box testing, etc.
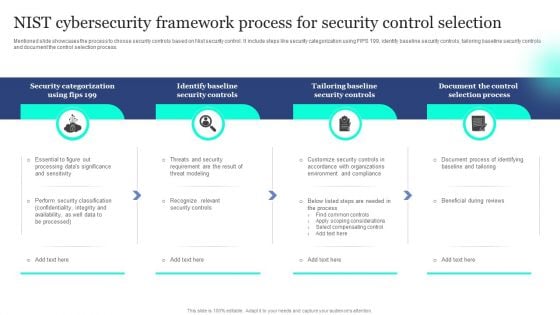
NIST Cybersecurity Framework Process For Security Control Selection Introduction PDF
Mentioned slide showcases the process to choose security controls based on Nist security control. It include steps like security categorization using FIPS 199, identify baseline security controls, tailoring baseline security controls and document the control selection process. Presenting NIST Cybersecurity Framework Process For Security Control Selection Introduction PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Security Controls, Tailoring Baseline, Selection Process. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
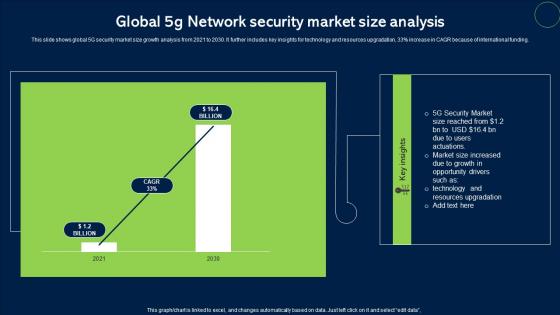
Global 5G Network Security Market Size Analysis Topics Pdf
This slide shows global 5G security market size growth analysis from 2021 to 2030. It further includes key insights for technology and resources upgradation, 33percent increase in CAGR because of international funding. Pitch your topic with ease and precision using this Global 5G Network Security Market Size Analysis Topics Pdf. This layout presents information on Network Security, Market Size. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide shows global 5G security market size growth analysis from 2021 to 2030. It further includes key insights for technology and resources upgradation, 33percent increase in CAGR because of international funding.
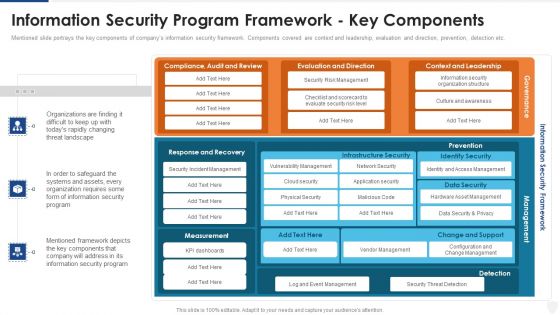
Information Security Program Framework Key Components Ppt Inspiration Ideas PDF
Mentioned slide portrays the key components of companys information security framework. Components covered are context and leadership, evaluation and direction, prevention, detection etc. Deliver and pitch your topic in the best possible manner with this information security program framework key components ppt inspiration ideas pdf. Use them to share invaluable insights on network security, application security, vendor management, data security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Framework Of Information IT Security Action Program Slides PDF
This slide focuses on information security action program framework which covers governance plan, security standards, stakeholder engagement and operational management to manage risks, handling threat, data security management, etc.Showcasing this set of slides titled Framework Of Information IT Security Action Program Slides PDF The topics addressed in these templates are Security Standards, Data Protection, Response Structure All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
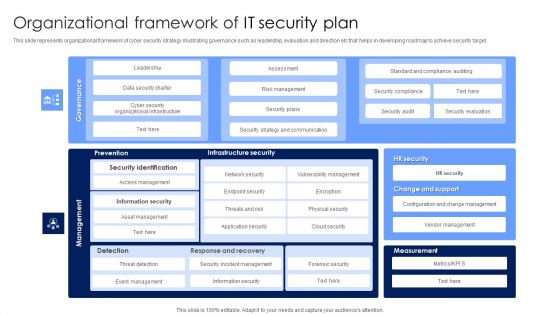
Organizational Framework Of IT Security Plan Microsoft PDF
This slide represents organizational framework of cyber security strategy illustrating governance such as leadership, evaluation and direction etc that helps in developing roadmap to achieve security target. Showcasing this set of slides titled Organizational Framework Of IT Security Plan Microsoft PDF. The topics addressed in these templates are Infrastructure Security, Management, Information Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Protection Cyber Security In Powerpoint And Google Slides Cpb
Introducing our well designed Protection Cyber Security In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Protection Cyber Security. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Protection Cyber Security In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
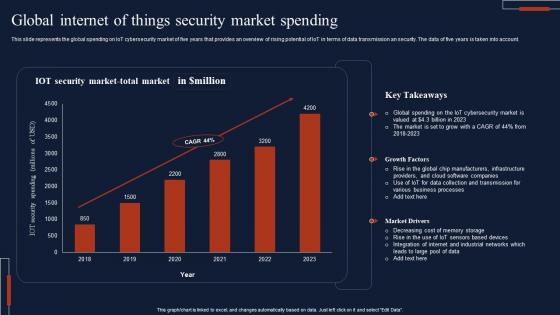
Global Internet Of Things Security Market Spending Download Pdf
This slide represents the global spending on IoT cybersecurity market of five years that provides an overview of rising potential of IoT in terms of data transmission an security. The data of five years is taken into account. Pitch your topic with ease and precision using this Global Internet Of Things Security Market Spending Download Pdf This layout presents information on IOT Security, Market Total, Key Takeaways It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide represents the global spending on IoT cybersecurity market of five years that provides an overview of rising potential of IoT in terms of data transmission an security. The data of five years is taken into account.
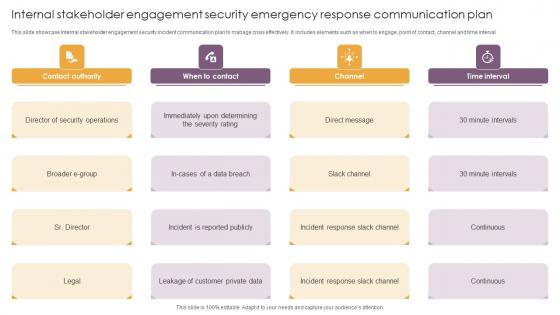
Internal Stakeholder Engagement Security Emergency Response Communication Plan Introduction Pdf
This slide showcase Internal stakeholder engagement security incident communication plan to manage crisis effectively. It includes elements such as when to engage, point of contact, channel and time interval Showcasing this set of slides titled Internal Stakeholder Engagement Security Emergency Response Communication Plan Introduction Pdf The topics addressed in these templates are Contact Authority, Time Interval, Director Of Security Operations All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcase Internal stakeholder engagement security incident communication plan to manage crisis effectively. It includes elements such as when to engage, point of contact, channel and time interval
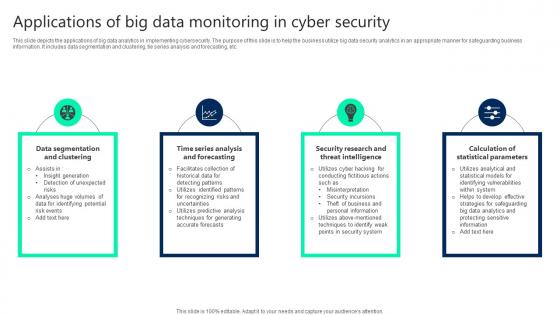
Applications Of Big Data Monitoring In Cyber Security Themes pdf
This slide depicts the applications of big data analytics in implementing cybersecurity. The purpose of this slide is to help the business utilize big data security analytics in an appropriate manner for safeguarding business information. It includes data segmentation and clustering, tie series analysis and forecasting, etc. Pitch your topic with ease and precision using this Applications Of Big Data Monitoring In Cyber Security Themes pdf. This layout presents information on Data Segmentation, Security Research, Threat Intelligence. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide depicts the applications of big data analytics in implementing cybersecurity. The purpose of this slide is to help the business utilize big data security analytics in an appropriate manner for safeguarding business information. It includes data segmentation and clustering, tie series analysis and forecasting, etc.
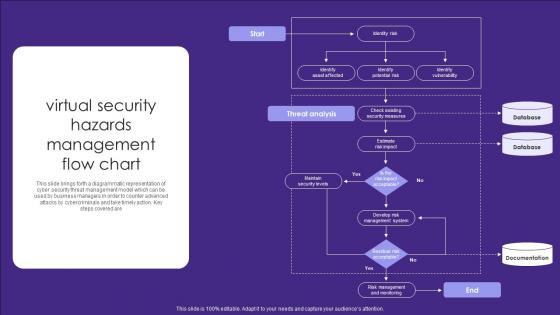
Virtual Security Hazards Management Flow Chart Infographics Pdf
This slide brings forth a diagrammatic representation of cyber security threat management model which can be used by business managers in order to counter advanced attacks by cybercriminals and take timely action. Key steps covered are Showcasing this set of slides titled Virtual Security Hazards Management Flow Chart Infographics Pdf. The topics addressed in these templates are Security Measures, Database, Documentation. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide brings forth a diagrammatic representation of cyber security threat management model which can be used by business managers in order to counter advanced attacks by cybercriminals and take timely action. Key steps covered are

Security Knowledge Framework In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Security Knowledge Framework In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Security Knowledge Framework that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Security Knowledge Framework In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

RPA Security Framework In Powerpoint And Google Slides Cpb
Introducing our well designed RPA Security Framework In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like RPA Security Framework. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our RPA Security Framework In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
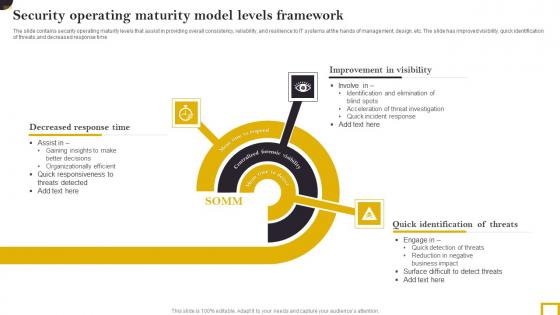
Security Operating Maturity Model Levels Framework Elements Pdf
The slide contains security operating maturity levels that assist in providing overall consistency, reliability, and resilience to IT systems at the hands of management, design, etc. The slide has improved visibility, quick identification of threats,and decreased response time. Pitch your topic with ease and precision using this Security Operating Maturity Model Levels Framework Elements Pdf. This layout presents information on Decreased Response Time,Improvement Visibility, Quick Identification Threats. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. The slide contains security operating maturity levels that assist in providing overall consistency, reliability, and resilience to IT systems at the hands of management, design, etc. The slide has improved visibility, quick identification of threats,and decreased response time.
Icons Slide For Data Security In Cloud Computing Ppt Presentation
Download our innovative and attention grabbing Icons Slide For Data Security In Cloud Computing Ppt Presentation template. The set of slides exhibit completely customizable icons. These icons can be incorporated into any business presentation. So download it immediately to clearly communicate with your clientele. Our Icons Slide For Data Security In Cloud Computing Ppt Presentation are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Digital Security Metrics Icon Showcasing Threat Protection Topics Pdf
Pitch your topic with ease and precision using this Digital Security Metrics Icon Showcasing Threat Protection Topics Pdf This layout presents information on Digital Security, Metrics Icon, Showcasing Threat Protection It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Our Digital Security Metrics Icon Showcasing Threat Protection Topics Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Cyber Security Strategic Agenda For Data Protection Icon Template Pdf
Pitch your topic with ease and precision using this Cyber Security Strategic Agenda For Data Protection Icon Template Pdf. This layout presents information on Cyber Security Strategic, Agenda For Data Protection. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Our Cyber Security Strategic Agenda For Data Protection Icon Template Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Complete Guide To Launch Website Security Management Strategic Plan
Following slide outlines website security action plan to assure safety from external threats and cyber crimes. It include steps such as strong passwords, new configurations, mitigate DDOS, safety from SQL, hide website version etc. Slidegeeks has constructed Complete Guide To Launch Website Security Management Strategic Plan after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. Following slide outlines website security action plan to assure safety from external threats and cyber crimes. It include steps such as strong passwords, new configurations, mitigate DDOS, safety from SQL, hide website version etc.
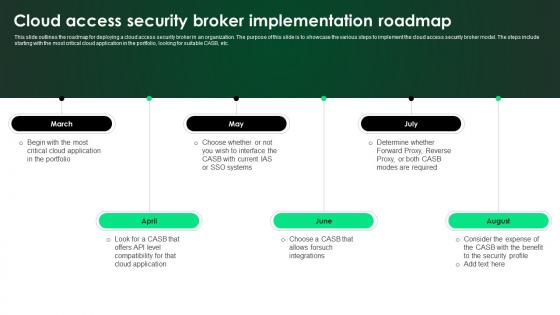
CASB 2 0 IT Cloud Access Security Broker Implementation Roadmap
This slide outlines the roadmap for deploying a cloud access security broker in an organization. The purpose of this slide is to showcase the various steps to implement the cloud access security broker model. The steps include starting with the most critical cloud application in the portfolio, looking for suitable CASB, etc. Welcome to our selection of the CASB 2 0 IT Cloud Access Security Broker Implementation Roadmap. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. This slide outlines the roadmap for deploying a cloud access security broker in an organization. The purpose of this slide is to showcase the various steps to implement the cloud access security broker model. The steps include starting with the most critical cloud application in the portfolio, looking for suitable CASB, etc.

Default Network Security In Powerpoint And Google Slides Cpb
Presenting our innovatively-designed set of slides titled Default Network Security In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Default Network Security that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well-structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Default Network Security In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
5G Wi Fi Signal Icon For Network Security Inspiration Pdf
Pitch your topic with ease and precision using this 5G Wi Fi Signal Icon For Network Security Inspiration Pdf. This layout presents information on 5G Wi Fi Signal, Network Security. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Our 5G Wi Fi Signal Icon For Network Security Inspiration Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
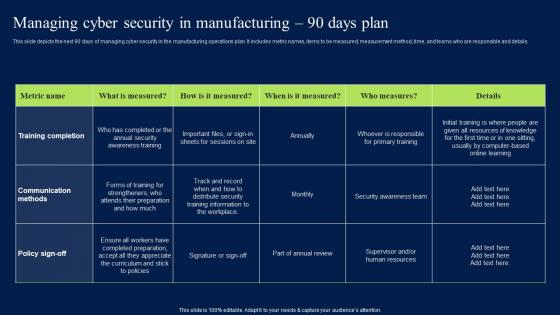
Managing Cyber Security In Manufacturing 90 Days Plan Professional PDF
This slide depicts the next 90 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, andteams who are responsible and details. Slidegeeks has constructed Managing Cyber Security In Manufacturing 90 Days Plan Professional PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide depicts the next 90 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details.
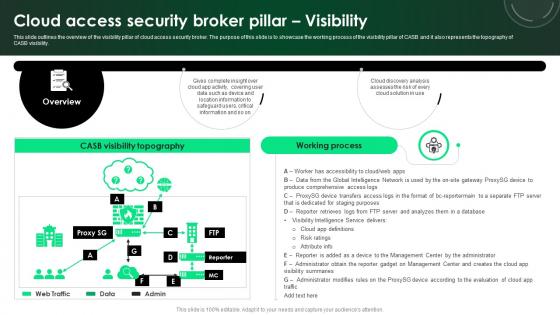
CASB 2 0 IT Cloud Access Security Broker Pillar Visibility
This slide outlines the overview of the visibility pillar of cloud access security broker. The purpose of this slide is to showcase the working process of the visibility pillar of CASB and it also represents the topography of CASB visibility. Slidegeeks has constructed CASB 2 0 IT Cloud Access Security Broker Pillar Visibility after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide outlines the overview of the visibility pillar of cloud access security broker. The purpose of this slide is to showcase the working process of the visibility pillar of CASB and it also represents the topography of CASB visibility.

Network Security Checklist Template In Powerpoint And Google Slides Cpb
Introducing our well designed Network Security Checklist Template In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Network Security Checklist Template. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Network Security Checklist Template In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
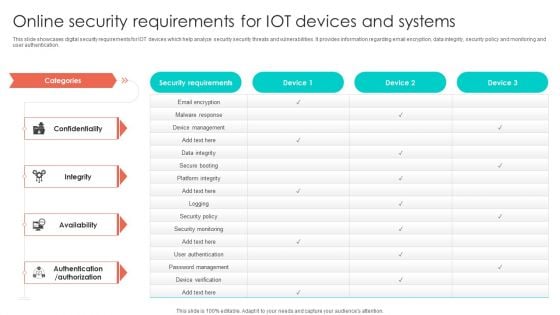
Online Security Requirements For Iot Devices And Systems Graphics PDF
This slide showcases digital security requirements for IOT devices which help analyze security security threats and vulnerabilities. It provides information regarding email encryption, data integrity, security policy and monitoring and user authentication. Pitch your topic with ease and precision using this Online Security Requirements For Iot Devices And Systems Graphics PDF. This layout presents information on Device Management, Security Policy, Security Monitoring. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Security Instalation Proposal In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Security Instalation Proposal In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Security Instalation Proposal that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Security Instalation Proposal In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Agenda For Zero Trust Network Security Pictures Pdf
Find a pre-designed and impeccable Agenda For Zero Trust Network Security Pictures Pdf. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. Our Agenda For Zero Trust Network Security Pictures Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Table Of Contents For Zero Trust Network Security Introduction Pdf
From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Table Of Contents For Zero Trust Network Security Introduction Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. Our Table Of Contents For Zero Trust Network Security Introduction Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Serverless Computing Security Role Serverless Computing Modern Technology Ideas Pdf
The purpose of this slide is to outline the security challenges and risks of serverless computing. These problems are vulnerable configuration, permissions for too powerful functions, infusion of event data, insufficient function recording and monitoring, etc. This modern and well arranged Serverless Computing Security Role Serverless Computing Modern Technology Ideas Pdf provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. The purpose of this slide is to outline the security challenges and risks of serverless computing. These problems are vulnerable configuration, permissions for too powerful functions, infusion of event data, insufficient function recording and monitoring, etc.
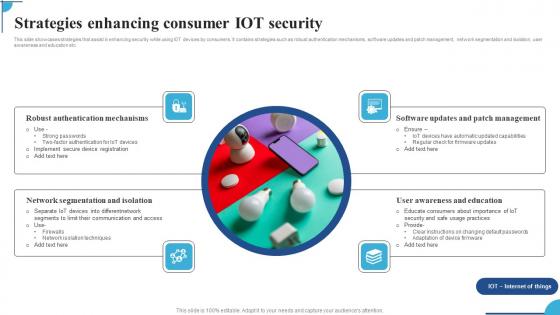
Strategies Enhancing Consumer IOT Security Ppt Pictures Graphic Images Pdf
This slide showcases strategies that assist in enhancing security while using IOT devices by consumers. It contains strategies such as robust authentication mechanisms,software updates and patch management,network segmentation and isolation,user awareness and education etc. Pitch your topic with ease and precision using this Strategies Enhancing Consumer IOT Security Ppt Pictures Graphic Images Pdf. This layout presents information on Robust Authentication Mechanisms,Network Segmentation Isolation,Software Updates. It is also available for immediate download and adjustment. So,changes can be made in the color,design,graphics or any other component to create a unique layout. This slide showcases strategies that assist in enhancing security while using IOT devices by consumers. It contains strategies such as robust authentication mechanisms,software updates and patch management,network segmentation and isolation,user awareness and education etc.


 Continue with Email
Continue with Email

 Home
Home


































