Security Architecture
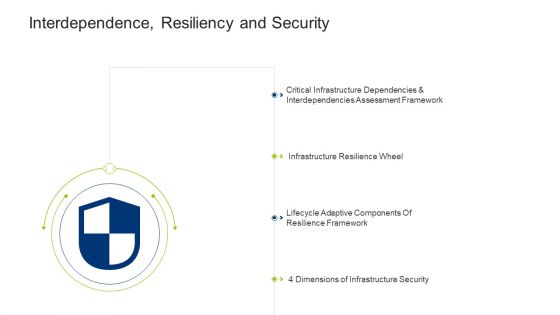
Infrastructure Building Administration Interdependence Resiliency And Security Microsoft PDF
This is a infrastructure building administration interdependence resiliency and security microsoft pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like infrastructure resilience wheel, lifecycle adaptive components of resilience framework, 4 dimensions of infrastructure security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
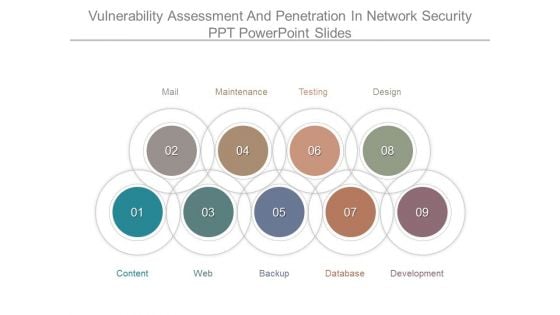
Vulnerability Assessment And Penetration In Network Security Ppt Powerpoint Slides
This is a vulnerability assessment and penetration in network security ppt powerpoint slides. This is a nine stage process. The stages in this process are mail, maintenance, testing, design, development, database, backup, web, content.
IT Security Program Icon For Protecting Client Data Ideas PDF
Persuade your audience using this IT Security Program Icon For Protecting Client Data Ideas PDF This PPT design covers one stage, thus making it a great tool to use. It also caters to a variety of topics including It Security, Program Icon, Protecting Client Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
IT Security Plan Icon Depicting Computer Protection Icons PDF
Persuade your audience using this IT Security Plan Icon Depicting Computer Protection Icons PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including IT Security Plan Icon, Depicting Computer Protection. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Protecting Against Phishing Cyber Security Attack Ppt Model Maker PDF
Persuade Your Audience Using This Protecting Against Phishing Cyber Security Attack Ppt Model Maker PDF. This PPT Design Covers Five Stages, Thus Making It A Great Tool To Use. It Also Caters To A Variety Of Topics Including Updating Security Software, Backing Up Data, Block Unreliable Websites. Download This PPT Design Now To Present A Convincing Pitch That Not Only Emphasizes The Topic But Also Showcases Your Presentation Skills.

Cyber Exploitation IT Use Of Security Programs Mockup PDF
This slide represents the usage of security programs such as secure socket layer, web application firewall, website, and software scanners that will secure and help detect malicious attacks. Presenting cyber exploitation it use of security programs mockup pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like secure sockets layer, web application firewall, website and software scanners. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Service Assessment Icon To Track Network Security Information PDF
Persuade your audience using this Service Assessment Icon To Track Network Security Information PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Service Assessment Icon To Track Network Security. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
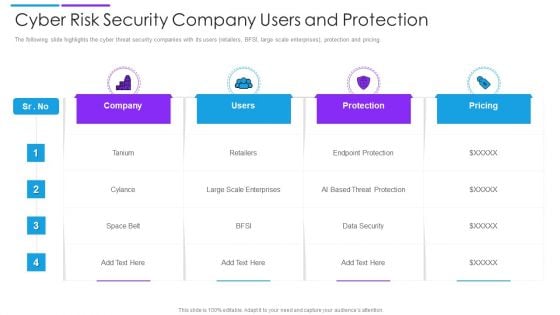
Cyber Risk Security Company Users And Protection Introduction PDF
The following slide highlights the cyber threat security companies with its users retailers, BFSI, large scale enterprises, protection and pricing. Showcasing this set of slides titled cyber risk security company users and protection introduction pdf. The topics addressed in these templates are company, users, protection. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Computer Folder Security PowerPoint Templates And PowerPoint Backgrounds 0211
Microsoft PowerPoint Template and Background with yellow computer folder with shield Our Computer Folder Security PowerPoint Templates And PowerPoint Backgrounds 0211 are designed for authenticity. They do not encourage any farce.
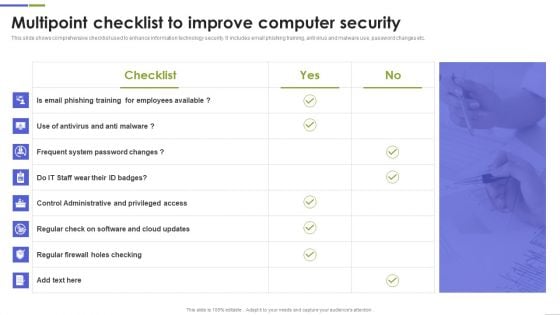
Multipoint Checklist To Improve Computer Security Guidelines PDF
This slide shows comprehensive checklist used to enhance information technology security. It includes email phishing training, anti virus and malware use, password changes etc. Showcasing this set of slides titled Multipoint Checklist To Improve Computer Security Guidelines PDF The topics addressed in these templates are Frequent System, Control Administrative, System Password All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Wireless Network Security System Icon Depicting Router Connectivity Background PDF
Persuade your audience using this wireless network security system icon depicting router connectivity background pdf. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including wireless network security system icon depicting router connectivity. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Wireless Remote Control For Network Security System Themes PDF
Persuade your audience using this wireless remote control for network security system themes pdf. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including wireless remote control for network security system. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
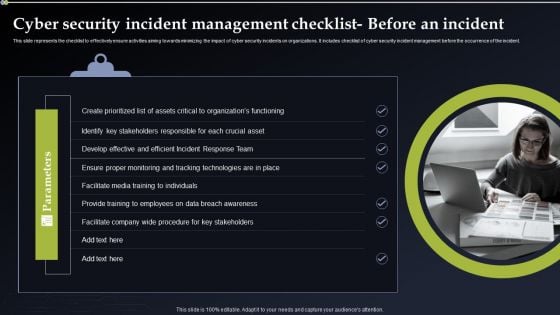
Cyber Security Incident Management Checklist Before An Incident Themes PDF
This slide represents the checklist to effectively ensure activities aiming towards minimizing the impact of cyber security incidents on organizations. It includes checklist of cyber security incident management before the occurrence of the incident. Create an editable Cyber Security Incident Management Checklist Before An Incident Themes PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Cyber Security Incident Management Checklist Before An Incident Themes PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
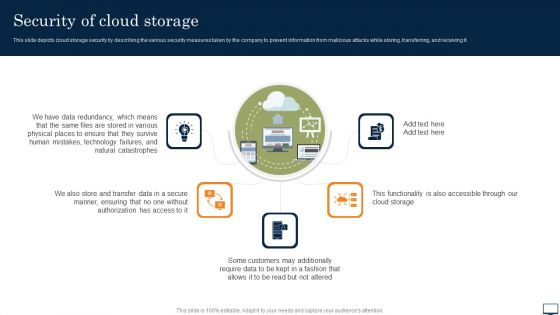
Security Of Cloud Storage Ppt PowerPoint Presentation File Styles PDF
This slide depicts cloud storage security by describing the various security measures taken by the company to prevent information from malicious attacks while storing, transferring, and receiving it. Get a simple yet stunning designed Security Of Cloud Storage Ppt PowerPoint Presentation File Styles PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Security Of Cloud Storage Ppt PowerPoint Presentation File Styles PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
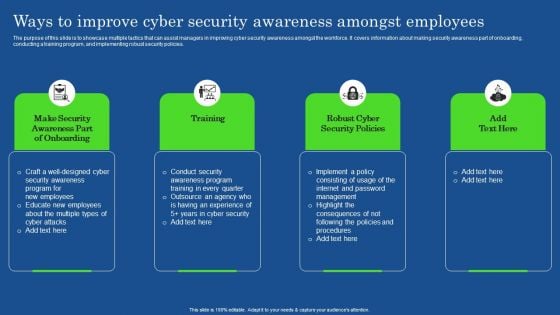
Ways To Improve Cyber Security Awareness Amongst Employees Elements PDF
The purpose of this slide is to showcase multiple tactics that can assist managers in improving cyber security awareness amongst the workforce. It covers information about making security awareness part of onboarding, conducting a training program, and implementing robust security policies. The Ways To Improve Cyber Security Awareness Amongst Employees Elements PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Cyber Security Incident Handler Contact Information Information PDF
This slide represents the contact information of the members responsible for handling and managing the cyber security incidents. It includes details related to name, organization, role and contact details of cyber security incident handler. This Cyber Security Incident Handler Contact Information Information PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Cyber Security Incident Handler Contact Information Information PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today
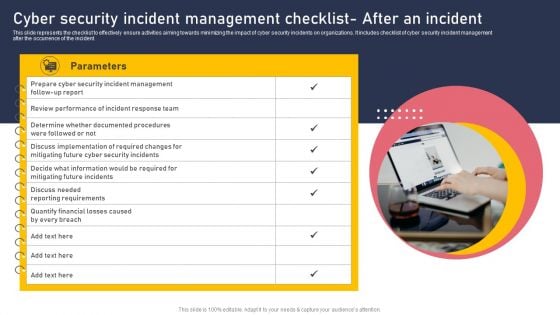
Cyber Security Incident Management Checklist After An Incident Elements PDF
This slide represents the checklist to effectively ensure activities aiming towards minimizing the impact of cyber security incidents on organizations. It includes checklist of cyber security incident management after the occurrence of the incident. Explore a selection of the finest Cyber Security Incident Management Checklist After An Incident Elements PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Cyber Security Incident Management Checklist After An Incident Elements PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
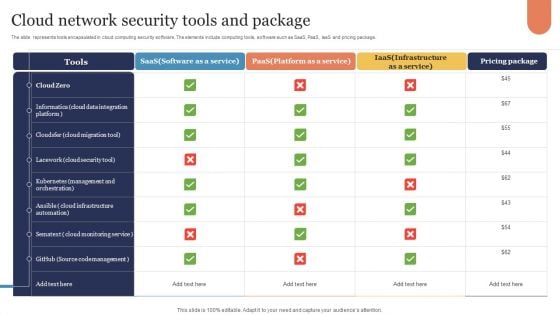
Cloud Network Security Tools And Package Graphics PDF
The slide represents tools encapsulated in cloud computing security software. The elements include computing tools, software such as SaaS, PaaS, IaaS and pricing package. Showcasing this set of slides titled Cloud Network Security Tools And Package Graphics PDF. The topics addressed in these templates are Saas, Paas, Iaas. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
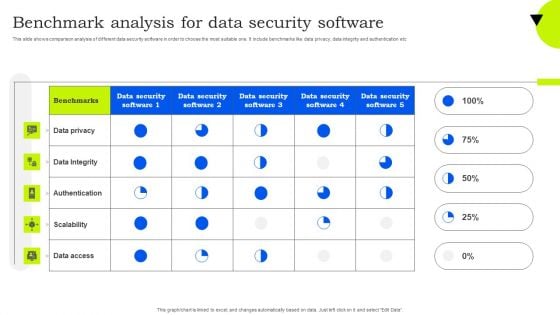
Benchmark Analysis For Data Security Software Mockup PDF
This slide shows comparison analysis of different data security software in order to choose the most suitable one. It include benchmarks like data privacy, data integrity and authentication etc. Showcasing this set of slides titled Benchmark Analysis For Data Security Software Mockup PDF. The topics addressed in these templates are Data Privacy, Data Integrity, Authentication. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
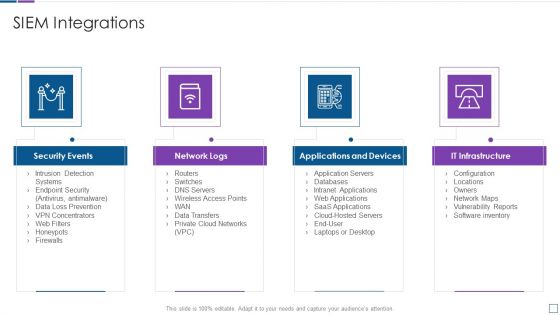
Real Time Assessment Of Security Threats SIEM Integrations Slides PDF
Presenting real time assessment of security threats siem integrations slides pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like security events, network logs, applications and devices, it infrastructure. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Safety And Security Icon For Hotel Industry Formats PDF
Persuade your audience using this Safety And Security Icon For Hotel Industry Formats PDF This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Safety And Security, Icon Hotel, Industry Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Icon For Digital Cyber Safety And Security Report Pictures PDF
Persuade your audience using this Icon For Digital Cyber Safety And Security Report Pictures PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Security Report, Icon For Digital, Cyber Safety. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
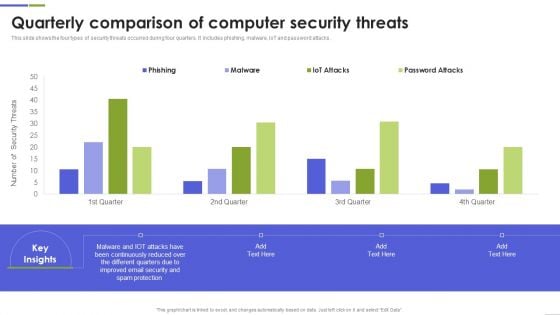
Quarterly Comparison Of Computer Security Threats Mockup PDF
This slide shows the four types of security threats occurred during four quarters. It includes phishing, malware, IoT and password attacks. Pitch your topic with ease and precision using this Quarterly Comparison Of Computer Security Threats Mockup PDF This layout presents information on Continuously Reduced, Different Quarters, Spam Protection It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Roadmap For Security Camera Services One Pager Sample Example Document
Presenting you an exemplary Roadmap For Security Camera Services One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Roadmap For Security Camera Services One Pager Sample Example Document brilliant piece now.
Security Camera Services About Us One Pager Sample Example Document
Presenting you an exemplary Security Camera Services About Us One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Security Camera Services About Us One Pager Sample Example Document brilliant piece now.
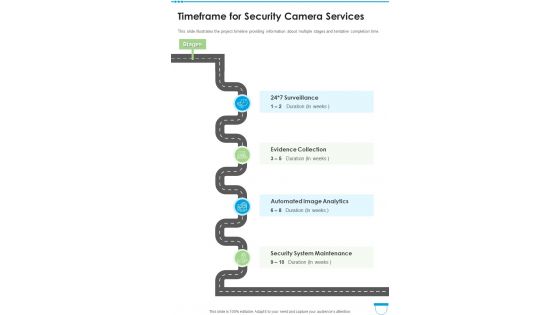
Timeframe For Security Camera Services One Pager Sample Example Document
This slide illustrates the project timeline providing information about multiple stages and tentative completion time. Presenting you an exemplary Timeframe For Security Camera Services One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Timeframe For Security Camera Services One Pager Sample Example Document brilliant piece now.
Timeline For Security Camera Services One Pager Sample Example Document
Presenting you an exemplary Timeline For Security Camera Services One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Timeline For Security Camera Services One Pager Sample Example Document brilliant piece now.
Roadmap For Security Services Proposal One Pager Sample Example Document
Presenting you an exemplary Roadmap For Security Services Proposal One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Roadmap For Security Services Proposal One Pager Sample Example Document brilliant piece now.
Timeline For Security Services Proposal One Pager Sample Example Document
Presenting you an exemplary Timeline For Security Services Proposal One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Timeline For Security Services Proposal One Pager Sample Example Document brilliant piece now.
Safety And Security App Mapping Icon Slides PDF
This slide showcases comparative analysis various tools used for application mapping to help organization identify best available option. It further includes details about price, free trail and characteristics. Showcasing this set of slides titled Safety And Security App Mapping Icon Slides PDF. The topics addressed in these templates are Safety And Security, App Mapping Icon. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
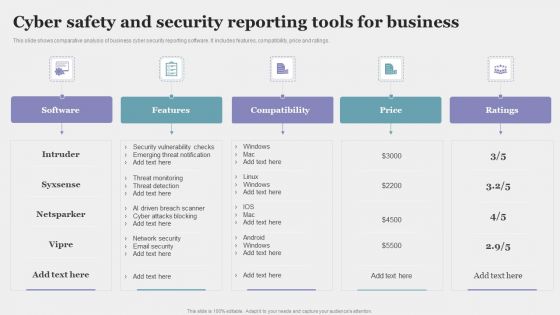
Cyber Safety And Security Reporting Tools For Business Rules PDF
This slide shows comparative analysis of business cyber security reporting software. It includes features, compatibility, price and ratings. Pitch your topic with ease and precision using this Cyber Safety And Security Reporting Tools For Business Rules PDF. This layout presents information on Compatibility, Price, Ratings. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
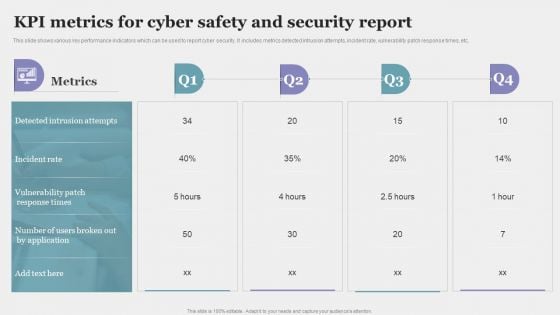
KPI Metrics For Cyber Safety And Security Report Elements PDF
This slide shows various key performance indicators which can be used to report cyber security. It includes metrics detected intrusion attempts, incident rate, vulnerability patch response times, etc. Showcasing this set of slides titled KPI Metrics For Cyber Safety And Security Report Elements PDF. The topics addressed in these templates are Incident Rate, Application, Metrics. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
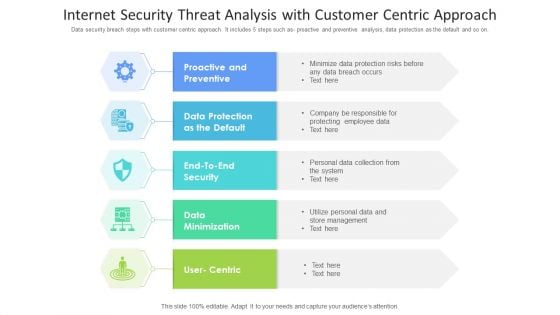
Internet Security Threat Analysis With Customer Centric Approach Mockup PDF
Data security breach steps with customer centric approach. It includes 5 steps such as- proactive and preventive analysis, data protection as the default and so on. Showcasing this set of slides titled internet security threat analysis with customer centric approach mockup pdf. The topics addressed in these templates are data minimization, data protection, proactive and preventive. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Certified Information Systems Security Professional Cissp Examination Details Topics PDF
Presenting Certified Information Systems Security Professional Cissp Examination Details Topics PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Software Development, Security Assessment, Communications And Network. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Stages For Minimizing Internet Security Threats Ideas PDF
Following slide exhibits steps for minimizing security and data breach. It includes major steps such as- malware protection and monitoring, source code assessment etc. Pitch your topic with ease and precision using this stages for minimizing internet security threats ideas pdf. This layout presents information on infrastructure management, cyber analysis, vulnerability management. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
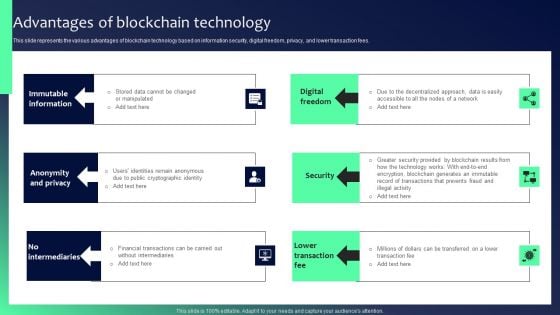
Blockchain Security Solutions Deployment Advantages Of Blockchain Technology Brochure PDF
This slide represents the various advantages of blockchain technology based on information security, digital freedom, privacy, and lower transaction fees. Find a pre-designed and impeccable Blockchain Security Solutions Deployment Advantages Of Blockchain Technology Brochure PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Table Of Contents For Project Security Administration IT Pictures PDF
Presenting table of contents for project security administration it pictures pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like project safety management, security centre implementation, budget assessment, dashboard analysis, project management team. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Building Data Analytics And Cyber Security Strategy Framework Icons PDF
This slide covers various practices to be employed to expand healthcare business. It includes data culture, internal integration, predictive analytics, shareholders involvement and data security. Persuade your audience using this Building Data Analytics And Cyber Security Strategy Framework Icons PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Data Collection, Expansion, Standardize And Automate. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Security Of Business Database Vector Icon Ppt PowerPoint Presentation Portfolio
Persuade your audience using this security of business database vector icon ppt powerpoint presentation portfolio. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including security business database vector icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Information Security Operations Training Department Program Icon Introduction PDF
Persuade your audience using this Information Security Operations Training Department Program Icon Introduction PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Information Security, Operations Training, Department Program, Icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Electronic Banking Security Icon With Dollar Sign Information PDF
Persuade your audience using this Electronic Banking Security Icon With Dollar Sign Information PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Electronic Banking Security Icon, Dollar Sign. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Standard Computing Vs Modern Information Security Icon Microsoft PDF
Persuade your audience using this Standard Computing Vs Modern Information Security Icon Microsoft PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Standard Computing, Modern Information Security Icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
IT Security Awareness Training Program Icons Ppt Layouts Structure PDF
Persuade your audience using this IT Security Awareness Training Program Icons Ppt Layouts Structure PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including IT Security Awareness, Training Program, Icons. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
IT Security Awareness Training Program For Employees Icon Mockup PDF
Persuade your audience using this IT Security Awareness Training Program For Employees Icon Mockup PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including IT Security Awareness, Training Program, Employees Icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Information Technology Security KPI Icon With Monitor Pictures PDF
Persuade your audience using this Information Technology Security KPI Icon With Monitor Pictures PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Information Technology, Security KPI, Icon With Monitor. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Blockchain Business Methodology For Business Security Icon Clipart PDF
Persuade your audience using this Blockchain Business Methodology For Business Security Icon Clipart PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Blockchain Business Methodology, Business Security Icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Security Software Deployment Implementation Project Planning Icon Ideas PDF
Persuade your audience using this Security Software Deployment Implementation Project Planning Icon Ideas PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Security Software, Deployment Implementation, Project Planning. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Face Scanning Smart Phone Security Technique Icon Brochure PDF
Persuade your audience using this Face Scanning Smart Phone Security Technique Icon Brochure PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Face Scanning, Smart Phone, Security Technique Icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Smart Phone Device Web Cam Security Icon Download PDF
Persuade your audience using this Smart Phone Device Web Cam Security Icon Download PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Smart Phone, Device Web, Cam Security Icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Cyber Security Risk Analysis Shield Software Icon Themes PDF
Persuade your audience using this Cyber Security Risk Analysis Shield Software Icon Themes PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Cyber Security Risk Analysis, Shield Software Icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Case Study 2 Banks Cyber Security Infrastructure Mockup PDF
Presenting case study 2 banks cyber security infrastructure mockup pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like case study 2 banks cyber security infrastructure. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
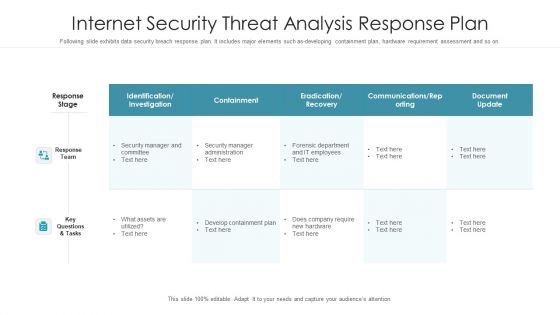
Internet Security Threat Analysis Response Plan Graphics PDF
Following slide exhibits data security breach response plan. It includes major elements such as-developing containment plan, hardware requirement assessment and so on. Pitch your topic with ease and precision using this internet security threat analysis response plan graphics pdf. This layout presents information on response team, response stage, key questions and tasks. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Current Security Management Challenges The Company Is Facing Download PDF
Presenting current security management challenges the company is facing download pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like potential insider threats, external security breaches, rise of caas. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Differentiating 2 Items Illustration For Free Internet Security Clipart PDF
Presenting differentiating 2 items illustration for free internet security clipart pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like differentiating 2 items illustration for free internet security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
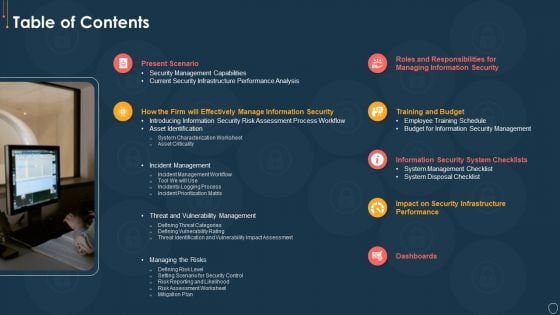
Cyber Security Risk Management Plan Table Of Contents Pictures PDF
Presenting cyber security risk management plan table of contents pictures pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like present scenario, roles and responsibilities, training and budget, dashboards, security infrastructure performance. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
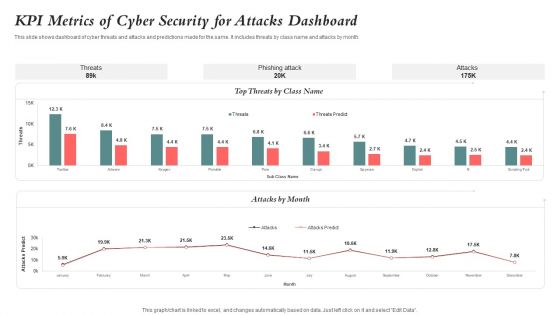
KPI Metrics Of Cyber Security For Attacks Dashboard Guidelines PDF
This slide shows dashboard of cyber threats and attacks and predictions made for the same. It includes threats by class name and attacks by month. Showcasing this set of slides titled KPI Metrics Of Cyber Security For Attacks Dashboard Guidelines PDF. The topics addressed in these templates are Kpi Metrics, Cyber Security, Attacks Dashboard. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
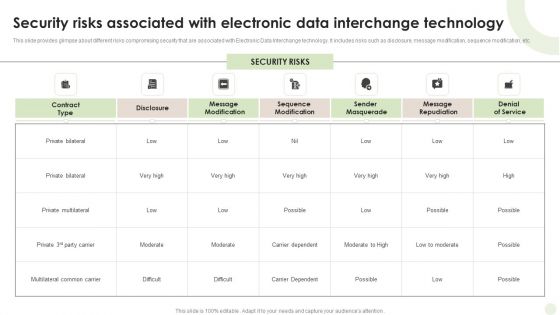
Security Risks Associated With Electronic Data Interchange Technology Guidelines PDF
This slide provides glimpse about different risks compromising security that are associated with Electronic Data Interchange technology. It includes risks such as disclosure, message modification, sequence modification, etc.Showcasing this set of slides titled Security Risks Associated With Electronic Data Interchange Technology Guidelines PDF. The topics addressed in these templates are Private Multilateral, Multilateral Common, Carrier Dependent. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
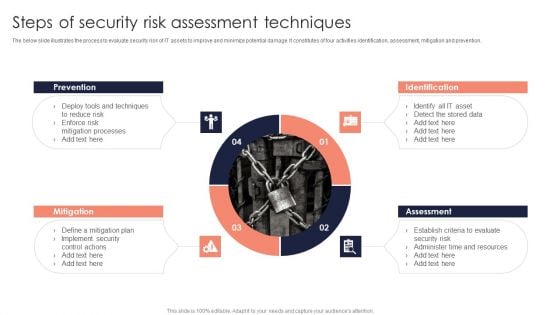
Steps Of Security Risk Assessment Techniques Introduction PDF
The below slide illustrates the process to evaluate security risk of IT assets to improve and minimize potential damage. It constitutes of four activities identification, assessment, mitigation and prevention. Showcasing this set of slides titled Steps Of Security Risk Assessment Techniques Introduction PDF. The topics addressed in these templates are Prevention, Identification, Assessment, Mitigation. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

One Page Internet Security Management Sheet PDF Document PPT Template
Presenting you an exemplary One Page Internet Security Management Sheet PDF Document PPT Template. Our one-pager template comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this One Page Internet Security Management Sheet PDF Document PPT Template Download now.
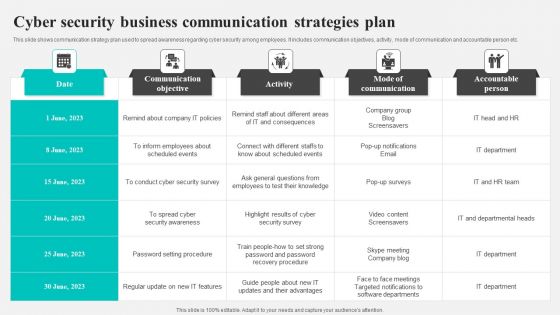
Cyber Security Business Communication Strategies Plan Background PDF
This slide shows communication strategy plan used to spread awareness regarding cyber security among employees. It includes communication objectives, activity, mode of communication and accountable person etc. Showcasing this set of slides titled Cyber Security Business Communication Strategies Plan Background PDF. The topics addressed in these templates are Communication Objective, Activity, Mode Communication. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.


 Continue with Email
Continue with Email

 Home
Home


































