Security Architecture

Medical Care Benefits Of Using Healthcare Data Management Mobile App Diagrams PDF
This slide shows the benefits of using healthcare data management mobile app. This includes various benefits of the application to the providers and the customers such as easily availability of health related information, secure connection, customization, etc. Presenting medical care benefits of using healthcare data management mobile app diagrams pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like security, patient, information, benefits. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
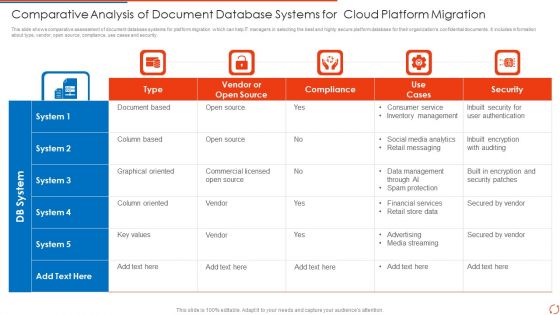
Comparative Analysis Of Document Database Systems For Cloud Platform Migration Portrait PDF
This slide shows comparative assessment of document database systems for platform migration which can help IT managers in selecting the best and highly secure platform database for their organizations confidential documents. It includes information about type, vendor, open source, compliance, use cases and security.Showcasing this set of slides titled Comparative Analysis Of Document Database Systems For Cloud Platform Migration Portrait PDF. The topics addressed in these templates are Compliance, Consumer, Data Management. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
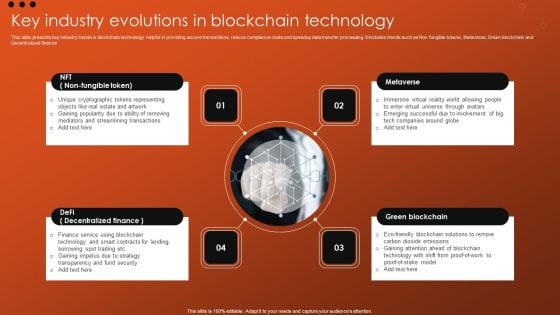
Key Industry Evolutions In Blockchain Technology Infographics PDF
This slide presents key industry trends in blockchain technology helpful in providing secure transactions, reduce compliance costs and speedup data transfer processing. It includes trends such as Non fungible tokens, Metaverse, Green blockchain and Decentralized finance. Pitch your topic with ease and precision using this Key Industry Evolutions In Blockchain Technology Infographics PDF. This layout presents information on Involvement, Security, Strategy. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
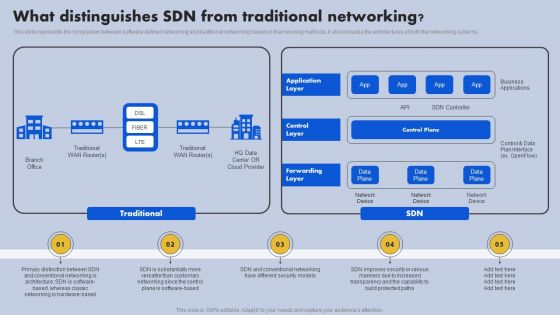
What Distinguishes SDN From Traditional Networking Ppt File Portfolio PDF
This slide represents the comparison between software-defined networking and traditional networking based on their working methods. It also includes the architectures of both the networking systems. Take your projects to the next level with our ultimate collection of What Distinguishes SDN From Traditional Networking Ppt File Portfolio PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest.
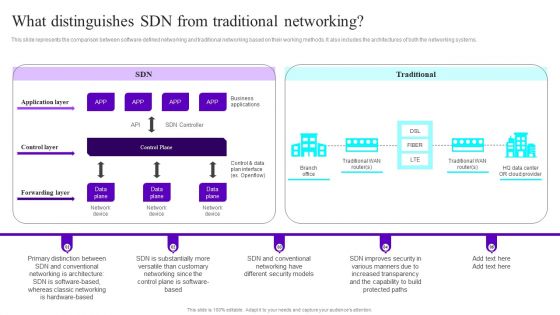
What Distinguishes SDN From Traditional Networking Ppt Layouts Designs Download PDF
This slide represents the comparison between software-defined networking and traditional networking based on their working methods. It also includes the architectures of both the networking systems. Take your projects to the next level with our ultimate collection of What Distinguishes SDN From Traditional Networking Ppt Layouts Designs Download PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest.
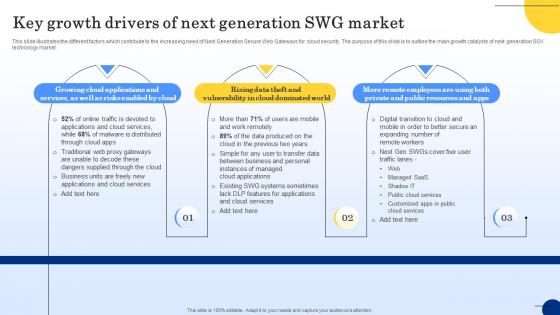
Key Growth Drivers Of Next Generation SWG Market Web Threat Protection System
This slide illustrates the different factors which contribute to the increasing need of Next Generation Secure Web Gateways for cloud security. The purpose of this slide is to outline the main growth catalysts of next generation SGV technology market. Explore a selection of the finest Key Growth Drivers Of Next Generation SWG Market Web Threat Protection System here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Key Growth Drivers Of Next Generation SWG Market Web Threat Protection System to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide illustrates the different factors which contribute to the increasing need of Next Generation Secure Web Gateways for cloud security. The purpose of this slide is to outline the main growth catalysts of next generation SGV technology market.
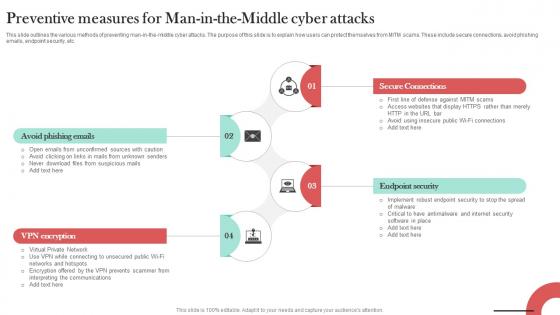
Preventive Measures For Man In The Middle Man In The Middle Phishing IT
This slide outlines the various methods of preventing man-in-the-middle cyber attacks. The purpose of this slide is to explain how users can protect themselves from MITM scams. These include secure connections, avoid phishing emails, endpoint security, etc. Get a simple yet stunning designed Preventive Measures For Man In The Middle Man In The Middle Phishing IT. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Preventive Measures For Man In The Middle Man In The Middle Phishing IT can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide outlines the various methods of preventing man-in-the-middle cyber attacks. The purpose of this slide is to explain how users can protect themselves from MITM scams. These include secure connections, avoid phishing emails, endpoint security, etc.
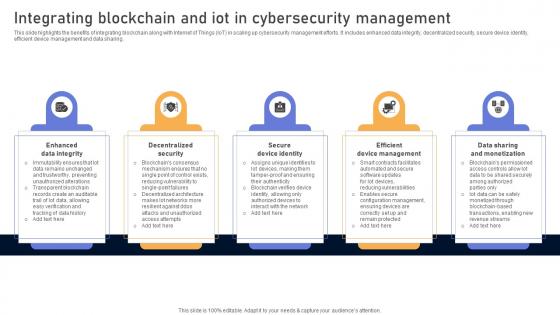
Comprehensive Look At Blockchain Technologys Integrating Blockchain And IoT BCT SS V
This slide highlights the benefits of integrating blockchain along with Internet of Things IoT in scaling up cybersecurity management efforts. It includes enhanced data integrity, decentralized security, secure device identity, efficient device management and data sharing. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Comprehensive Look At Blockchain Technologys Integrating Blockchain And IoT BCT SS V. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Comprehensive Look At Blockchain Technologys Integrating Blockchain And IoT BCT SS V today and make your presentation stand out from the rest This slide highlights the benefits of integrating blockchain along with Internet of Things IoT in scaling up cybersecurity management efforts. It includes enhanced data integrity, decentralized security, secure device identity, efficient device management and data sharing.
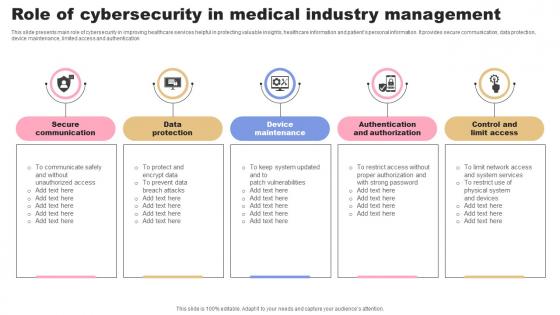
Role Of Cybersecurity In Medical Industry Management Rules Pdf
This slide presents main role of cybersecurity in improving healthcare services helpful in protecting valuable insights, healthcare information and patients personal information. It provides secure communication, data protection, device maintenance, limited access and authentication Pitch your topic with ease and precision using this Role Of Cybersecurity In Medical Industry Management Rules Pdf. This layout presents information on Secure Communication, Data Protection, Maintenance. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide presents main role of cybersecurity in improving healthcare services helpful in protecting valuable insights, healthcare information and patients personal information. It provides secure communication, data protection, device maintenance, limited access and authentication
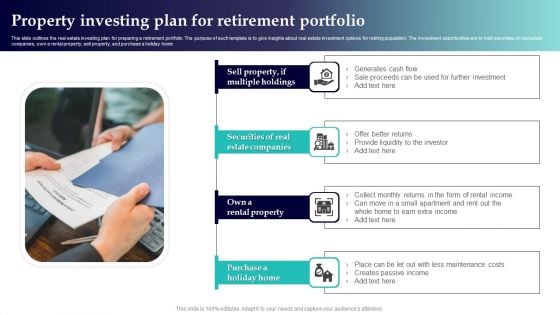
Property Investing Plan For Retirement Portfolio Themes PDF
This slide outlines the real estate investing plan for preparing a retirement portfolio. The purpose of such template is to give insights about real estate investment options for retiring population. The investment opportunities are to hold securities of real estate companies, own a rental property, sell property, and purchase a holiday home. Presenting Property Investing Plan For Retirement Portfolio Themes PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Securities Real Estate Companies, Own Rental Property, Purchase Holiday Home. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
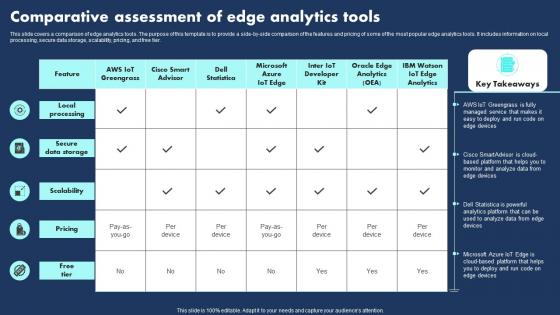
Comparative Assessment Of Edge Analytics Tools Graphics Pdf
This slide covers a comparison of edge analytics tools. The purpose of this template is to provide a side by side comparison of the features and pricing of some of the most popular edge analytics tools. It includes information on local processing, secure data storage, scalability, pricing, and free tier.Showcasing this set of slides titled Comparative Assessment Of Edge Analytics Tools Graphics Pdf The topics addressed in these templates are Local Processing, Secure Data Storage, Scalability All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide covers a comparison of edge analytics tools. The purpose of this template is to provide a side by side comparison of the features and pricing of some of the most popular edge analytics tools. It includes information on local processing, secure data storage, scalability, pricing, and free tier.
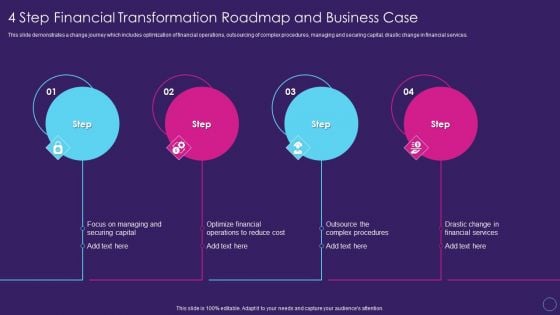
Digital Transformation Toolkit Accounting Finance 4 Step Financial Transformation Roadmap Mockup PDF
This slide demonstrates a change journey which includes optimization of financial operations, outsourcing of complex procedures, managing and securing capital, drastic change in financial services. This is a digital transformation toolkit accounting finance 4 step financial transformation roadmap mockup pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like managing, securing, operations, financial, procedures. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
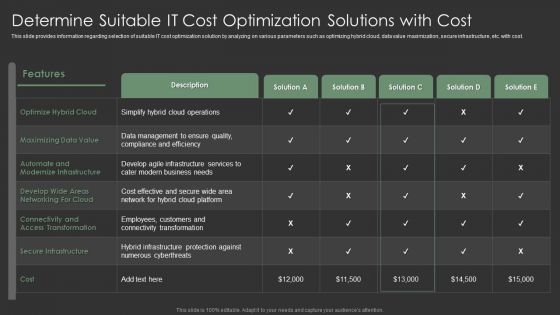
IT Spend Management Priorities By Cios Determine Suitable IT Cost Optimization Solutions With Cost Designs PDF
This slide provides information regarding selection of suitable IT cost optimization solution by analyzing on various parameters such as optimizing hybrid cloud, data value maximization, secure infrastructure, etc. with cost. Deliver an awe inspiring pitch with this creative IT Spend Management Priorities By Cios Determine Suitable IT Cost Optimization Solutions With Cost Designs PDF bundle. Topics like Secure Infrastructure, Maximizing Data Value, Data Management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
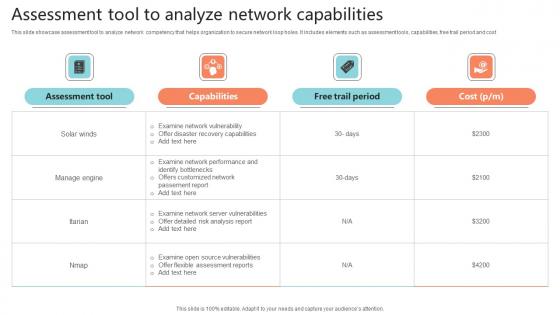
Assessment Tool To Analyze Network Capabilities Pictures Pdf
This slide showcase assessment tool to analyze network competency that helps organization to secure network loop holes. It includes elements such as assessment tools, capabilities, free trail period and cost.Showcasing this set of slides titled Assessment Tool To Analyze Network Capabilities Pictures Pdf The topics addressed in these templates are Examine Network, Flexible Assessment, Recovery Capabilities All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcase assessment tool to analyze network competency that helps organization to secure network loop holes. It includes elements such as assessment tools, capabilities, free trail period and cost.
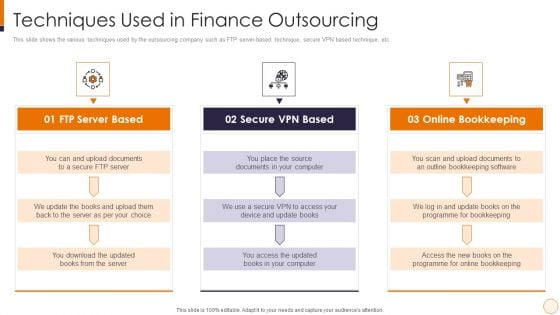
SME And Startups Financing Services Techniques Used In Finance Outsourcing Microsoft PDF
This slide shows the various techniques used by the outsourcing company such as FTP server-based technique, secure VPN based technique, etc. Presenting sme and startups financing services techniques used in finance outsourcing microsoft pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like ftp server based, secure vpn based, online bookkeeping. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Fund Outsourcing Upgrade Efficiency Efficacy Fund Function Techniques Used In Finance Outsourcing Ppt Professional Deck
This slide shows the various techniques used by the outsourcing company such as FTP server-based technique, secure VPN based technique, etc. Presenting fund outsourcing upgrade efficiency efficacy fund function techniques used in finance outsourcing ppt professional deck to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like ftp serve based, secure vpn based, online bookkeeping. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Finance And Accountancy BPO Techniques Used In Finance Outsourcing Brochure PDF
This slide shows the various techniques used by the outsourcing company such as FTP server-based technique, secure VPN based technique, etc. Presenting finance and accountancy bpo techniques used in finance outsourcing brochure pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like ftp serve based, secure vpn based, online bookkeeping. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
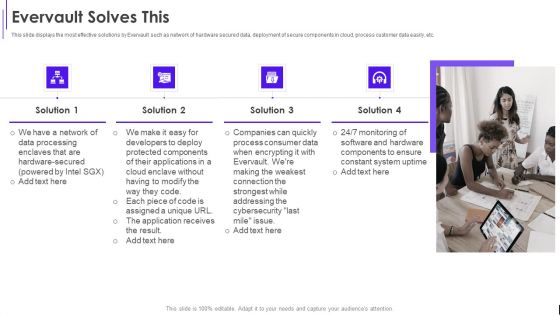
Fundraising Pitch Deck For Evervault Evervault Solves This Ppt Gallery Grid PDF
This slide displays the most effective solutions by Evervault such as network of hardware secured data, deployment of secure components in cloud, process customer data easily, etc. Presenting Fundraising Pitch Deck For Evervault Evervault Solves This Ppt Gallery Grid PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Data Processing, Protected Components, Monitoring Software. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Open Source Corporate Vulnerability Analysis Software Tools Demonstration PDF
This slide showcases open source enterprise vulnerability management software tools that aids companies in securing their networks by locating and repairing flaws. It also includes descriptions regarding tools such as triviy, metasploit, openscap, etc. Persuade your audience using this Open Source Corporate Vulnerability Analysis Software Tools Demonstration PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Environment, Secure Web Applications, Industrial. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

IT System Risk Management Guide Preventive IT Technical Control Measures Graphics PDF
The following slide highlights the preventive information technical controls which includes authentication, authorization, enable control enforcement, nonrepudiation, secured communications and secured transactions. This IT System Risk Management Guide Preventive IT Technical Control Measures Graphics PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The product features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, don not wait, grab the presentation templates today.
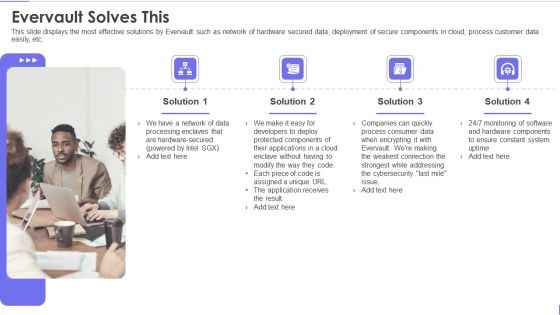
Evervault Capital Investment Elevator Pitch Deck Evervault Solves This Template PDF
This slide displays the most effective solutions by Evervault such as network of hardware secured data, deployment of secure components in cloud, process customer data easily, etc. Presenting evervault capital investment elevator pitch deck evervault solves this template pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like evervault solves this. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
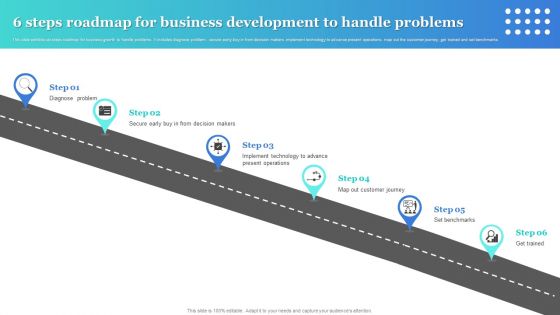
6 Steps Roadmap For Business Development To Handle Problems Guidelines PDF
This slide exhibits six steps roadmap for business growth to handle problems. It includes diagnose problem, secure early buy in from decision makers ,implement technology to advance present operations, map out the customer journey, get trained and set benchmarks. Persuade your audience using this 6 Steps Roadmap For Business Development To Handle Problems Guidelines PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Diagnose Problem, Secure Early Buy, Map Out Customer Journey. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

4 Best Practices Of Data Management Ethics In Organizations Ppt Infographics Grid PDF
This slide shows the various data practices that organizations can use in data collection. It includes having clear policies, get employees buy-in, secure IT systems and be transparent. Persuade your audience using this 4 Best Practices Of Data Management Ethics In Organizations Ppt Infographics Grid PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Clear Policies, Get Employees, Buy In, Secure IT Systems, Be Transparent. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
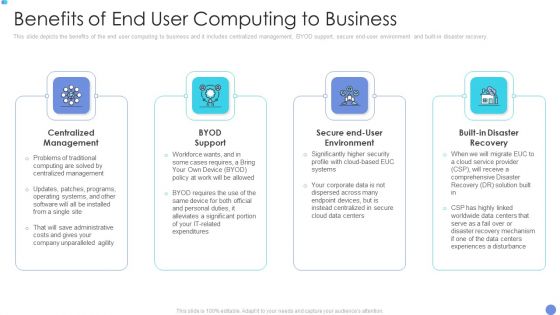
Customer Mesh Computing IT Benefits Of End User Computing To Business Download PDF
This slide depicts the benefits of the end user computing to business and it includes centralized management, BYOD support, secure end user environment and built in disaster recovery. Presenting to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like centralized management, byod support, secure end user environment. In addition, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

VID Benefits Of End User Computing To Business Sample PDF
This slide depicts the benefits of the end user computing to business and it includes centralized management, BYOD support, secure end user environment and built in disaster recovery.Presenting VID Benefits Of End User Computing To Business Sample PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Significantly Higher, Centralized In Secure, Disaster Recovery. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
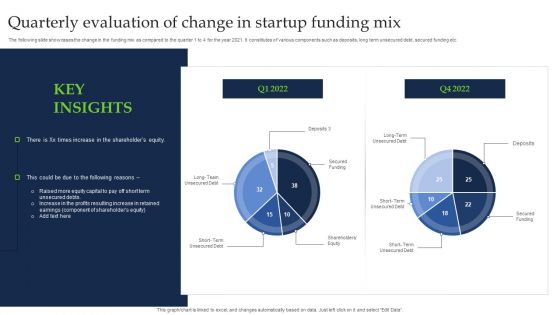
Quarterly Evaluation Of Change In Startup Funding Mix Diagrams PDF
The following slide showcases the change in the funding mix as compared to the quarter 1 to 4 for the year 2021. It constitutes of various components such as deposits, long term unsecured debt, secured funding etc. Showcasing this set of slides titled Quarterly Evaluation Of Change In Startup Funding Mix Diagrams PDF. The topics addressed in these templates are Secured Funding, Term Unsecured Debt, Shareholder Equity. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Supply Chain Management How Is Iot Significant In Overall Logistics Ideas PDF
The following slide illustrates role of internet of things IoT in logistics. It provides information about tracking products, securing operations, managing vehicles, unexpected failures, efficiency, costs, sensors, warehouse, supply, etc. Presenting Supply Chain Management How Is Iot Significant In Overall Logistics Ideas PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Tracking Products, Securing Operations, Managing Vehicles. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
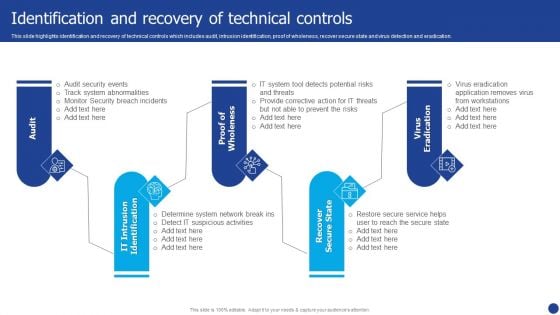
Information Technology Threat Mitigation Methods Identification And Recovery Of Technical Controls Demonstration PDF
This slide highlights identification and recovery of technical controls which includes audit, intrusion identification, proof of wholeness, recover secure state and virus detection and eradication. Presenting Information Technology Threat Mitigation Methods Identification And Recovery Of Technical Controls Demonstration PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Recover Secure State, Virus Eradication, Audit. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
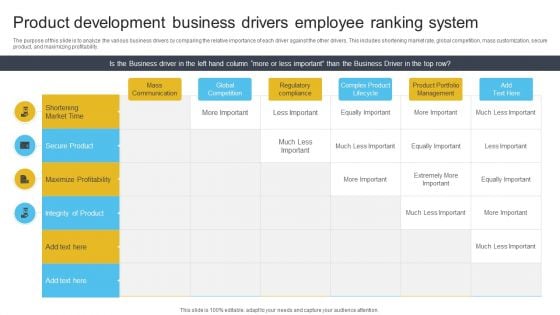
Product Development Business Drivers Employee Ranking System Themes PDF
The purpose of this slide is to analyze the various business drivers by comparing the relative importance of each driver against the other drivers. This includes shortening market rate, global competition, mass customization, secure product, and maximizing profitability. Pitch your topic with ease and precision using this Product Development Business Drivers Employee Ranking System Themes PDF. This layout presents information on Maximize Profitability, Secure Product, Global Competition. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
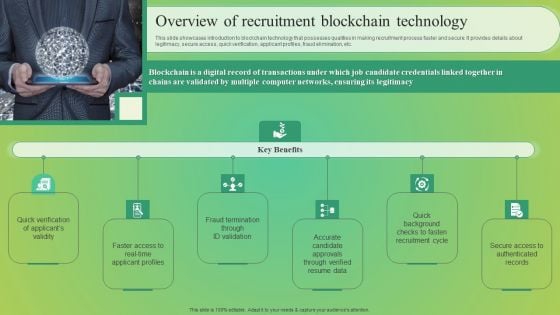
Overview Of Recruitment Blockchain Technology Pictures PDF
This slide showcases introduction to blockchain technology that possesses qualities in making recruitment process faster and secure. It provides details about legitimacy, secure access, quick verification, applicant profiles, fraud elimination, etc. Get a simple yet stunning designed Overview Of Recruitment Blockchain Technology Pictures PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Overview Of Recruitment Blockchain Technology Pictures PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
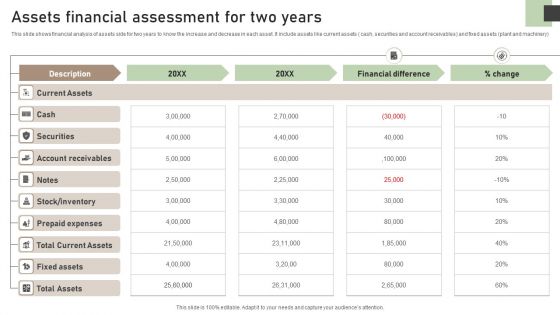
Assets Financial Assessment For Two Years Mockup PDF
This slide shows financial analysis of assets side for two years to know the increase and decrease in each asset. It include assets like current assets cash, securities and account receivables and fixed assets plant and machinery. Showcasing this set of slides titled Assets Financial Assessment For Two Years Mockup PDF. The topics addressed in these templates are Current Assets, Cash, Securities. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cybersecurity Awareness Areas For Effective Planning And Communication Demonstration Pdf
This slide showcases process of initiating cybersecurity communication plan. This template focuses on protecting information to ensure that it is not corrupted. It includes information related to network security,malware protection, etc.Showcasing this set of slides titled Cybersecurity Awareness Areas For Effective Planning And Communication Demonstration Pdf The topics addressed in these templates are Network Safety, Awareness Education, Secure Construction All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcases process of initiating cybersecurity communication plan. This template focuses on protecting information to ensure that it is not corrupted. It includes information related to network security,malware protection, etc.

Application Protection Ppt Layout Presentation Design
This is a application protection ppt layout presentation design. This is a seven stage process. The stages in this process are content security, risk mitigation, risk assessment, application security, evaluation and assessment, endpoint security, network security.
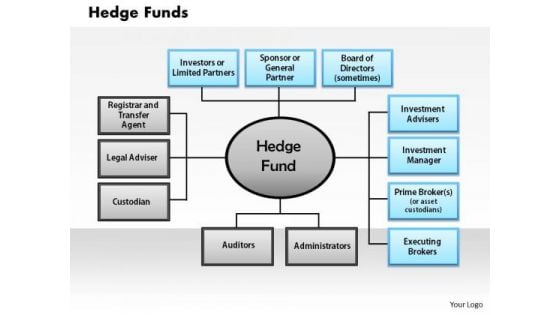
Business Framework Hedge Funds PowerPoint Presentation
This image slide displays hedge funds which is an investment vehicle that pools capital from a number of investors and invests in securities and other instruments. This image slide may be used to depict finance management in your presentations. This image slide will enhance the quality of your presentations.

Roles Of Channel Marketing Manager Ppt PowerPoint Presentation Pictures Designs Download
This is a roles of channel marketing manager ppt powerpoint presentation pictures designs download. This is a five stage process. The stages in this process are finding, securing and maintaining a relationship between a producer and a retailer, devise advertising strategies, negotiate contracts, establish standards for the retailer, address concerns.
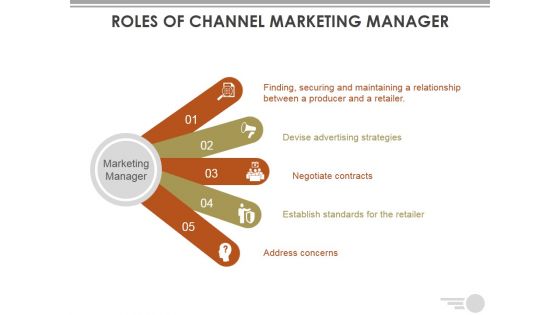
Roles Of Channel Marketing Manager Ppt PowerPoint Presentation Portfolio Graphics Design
This is a roles of channel marketing manager ppt powerpoint presentation portfolio graphics design. This is a five stage process. The stages in this process are finding, securing and maintaining a relationship between a producer and a retailer, devise advertising strategies, negotiate contracts, establish standards for the retailer, address concerns.
Steps For Developing An Effective Employee Mentoring Program Ppt PowerPoint Presentation Gallery Icons
Presenting this set of slides with name steps for developing an effective employee mentoring program ppt powerpoint presentation gallery icons. The topics discussed in these slides are Set framework, Secure participation, departments, interest and direction, Provide feedback opportunities. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Mastering Blockchain Wallets Steps To Set Up A Crypto Hardware Wallet BCT SS V
This slide covers process of setting up a hardware wallet for securely storing cryptocurrencies. The purpose of this template is to provide step-by-step overview of the setup process, allowing users to ensure proper configuration and usage of a hardware wallet. It includes steps from buying the hardware, installing the software, securing the seed phase, creating wallet, etc. This modern and well-arranged Mastering Blockchain Wallets Steps To Set Up A Crypto Hardware Wallet BCT SS V provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide covers process of setting up a hardware wallet for securely storing cryptocurrencies. The purpose of this template is to provide step-by-step overview of the setup process, allowing users to ensure proper configuration and usage of a hardware wallet. It includes steps from buying the hardware, installing the software, securing the seed phase, creating wallet, etc.

Enterprise Tactical Planning Business Insurance Ppt Gallery Inspiration PDF
Presenting enterprise tactical planning business insurance ppt gallery inspiration pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like revenues, safeguarding organization, business, profits, securing projects. In addition, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.
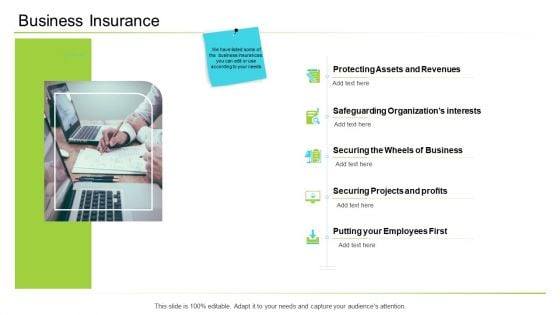
Business Insurance Ppt Infographic Template Good PDF
Presenting business insurance ppt infographic template good pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like revenues, business, profits, securing projects. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
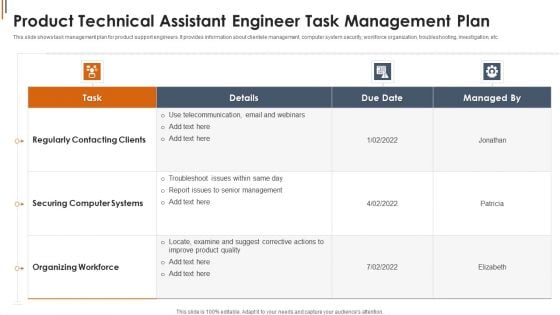
Product Technical Assistant Engineer Task Management Plan Background PDF
Showcasing this set of slides titled Product Technical Assistant Engineer Task Management Plan Background PDF. The topics addressed in these templates are Securing Computer Systems, Organizing Workforce, Telecommunication. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Reverse Proxy Web Server How Does A Reverse Proxy Web Server Application Icons PDF
This slide explains the working of a reverse proxy server in two ways proxying for load balancing and proxy as a stand-in for a server which is further divided into three parts such as secure client to proxy, secure proxy to content server and secure client to proxy and secure proxy to content server. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Reverse Proxy Web Server How Does A Reverse Proxy Web Server Application Icons PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Reverse Proxy Web Server How Does A Reverse Proxy Web Server Application Icons PDF.

Key Crowdfunding Regulatory Authorities In US Real Estate Crowdfunding To Unlock Fin SS V
This slide shows information about various agencies or authorities which are responsible for regulating crowdfunding in United States of America It includes Securities and Exchange Commission SEC, Financial Industry Regulatory Authority FINRA, etc. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Key Crowdfunding Regulatory Authorities In US Real Estate Crowdfunding To Unlock Fin SS V from Slidegeeks and deliver a wonderful presentation. This slide shows information about various agencies or authorities which are responsible for regulating crowdfunding in United States of America It includes Securities and Exchange Commission SEC, Financial Industry Regulatory Authority FINRA, etc.
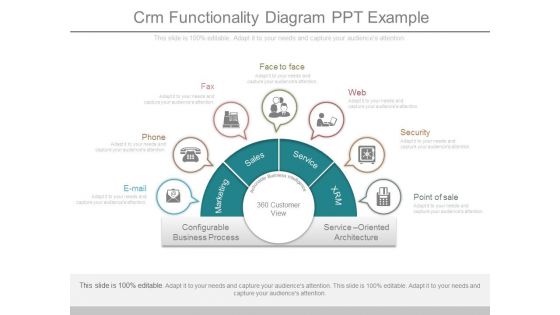
Crm Functionality Diagram Ppt Example
This is a crm functionality diagram ppt example. This is a seven stage process. The stages in this process are e mail, phone, fax, face to face, web, security, point of sale, marketing, sales, service, xrm, configurable business process, service oriented architecture, 360 customer view.
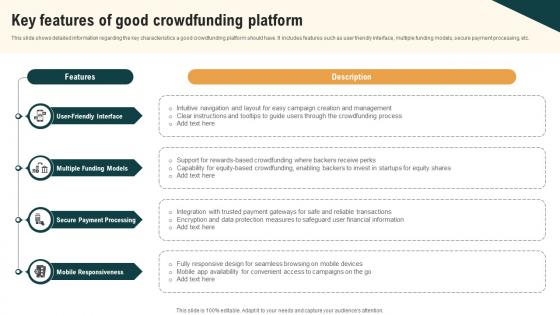
Key Features Of Good Crowdfunding Platform Real Estate Crowdfunding To Unlock Fin SS V
This slide shows detailed information regarding the key characteristics a good crowdfunding platform should have. It includes features such as user friendly interface, multiple funding models, secure payment processing, etc. Are you searching for a Key Features Of Good Crowdfunding Platform Real Estate Crowdfunding To Unlock Fin SS V that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Key Features Of Good Crowdfunding Platform Real Estate Crowdfunding To Unlock Fin SS V from Slidegeeks today. This slide shows detailed information regarding the key characteristics a good crowdfunding platform should have. It includes features such as user friendly interface, multiple funding models, secure payment processing, etc.
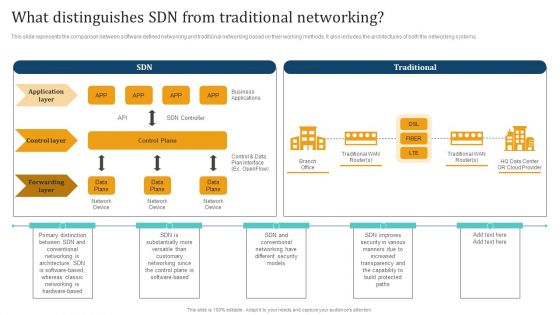
Empowering Network Agility Through SDN What Distinguishes SDN From Traditional Networking Introduction PDF
This slide represents the comparison between software defined networking and traditional networking based on their working methods. It also includes the architectures of both the networking systems. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download Empowering Network Agility Through SDN What Distinguishes SDN From Traditional Networking Introduction PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the Empowering Network Agility Through SDN What Distinguishes SDN From Traditional Networking Introduction PDF.
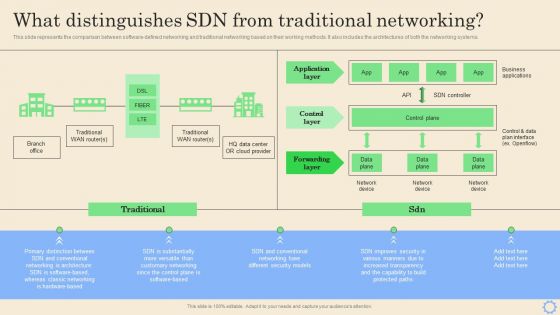
Software Defined Networking Development Strategies What Distinguishes Sdn From Traditional Background PDF
This slide represents the comparison between software-defined networking and traditional networking based on their working methods. It also includes the architectures of both the networking systems. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Software Defined Networking Development Strategies What Distinguishes Sdn From Traditional Background PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Software Defined Networking Development Strategies What Distinguishes Sdn From Traditional Background PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Construction Project Playbook Hybrid Or Semi Volumetric Construction Method Ppt Infographic Template File Formats PDF
This slide provides information regarding hybrid or semi volumetric construction method as modern method of construction along with benefits associated to it. Deliver an awe inspiring pitch with this creative construction project playbook hybrid or semi volumetric construction method ppt infographic template file formats pdf bundle. Topics like faster construction, benefits, improved site utilization, secured working environment can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Zero Trust Model Working Of Zero Trust Network Access Model
This slide outlines the working of zero trust network access. The purpose of this slide is to demonstrate the workflow of ZTNA, including the principles shared by all ZTNA architectures. The principles include no use of MPLS, hiding the IP addresses, securing devices, IDP and SSO platform, and so on. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Zero Trust Model Working Of Zero Trust Network Access Model to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide outlines the working of zero trust network access. The purpose of this slide is to demonstrate the workflow of ZTNA, including the principles shared by all ZTNA architectures. The principles include no use of MPLS, hiding the IP addresses, securing devices, IDP and SSO platform, and so on.
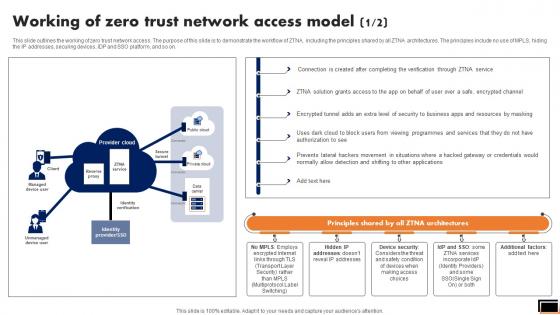
Working Of Zero Trust Network Access Model Software Defined Perimeter SDP
This slide outlines the working of zero trust network access. The purpose of this slide is to demonstrate the workflow of ZTNA, including the principles shared by all ZTNA architectures. The principles include no use of MPLS, hiding the IP addresses, securing devices, IDP and SSO platform, and so on. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Working Of Zero Trust Network Access Model Software Defined Perimeter SDP to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide outlines the working of zero trust network access. The purpose of this slide is to demonstrate the workflow of ZTNA, including the principles shared by all ZTNA architectures. The principles include no use of MPLS, hiding the IP addresses, securing devices, IDP and SSO platform, and so on.

Zero Trust Network Access Working Of Zero Trust Network Access Model
This slide outlines the working of zero trust network access. The purpose of this slide is to demonstrate the workflow of ZTNA, including the principles shared by all ZTNA architectures. The principles include no use of MPLS, hiding the IP addresses, securing devices, IDP and SSO platform, and so on. Presenting this PowerPoint presentation, titled Zero Trust Network Access Working Of Zero Trust Network Access Model, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Zero Trust Network Access Working Of Zero Trust Network Access Model. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Zero Trust Network Access Working Of Zero Trust Network Access Model that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide outlines the working of zero trust network access. The purpose of this slide is to demonstrate the workflow of ZTNA, including the principles shared by all ZTNA architectures. The principles include no use of MPLS, hiding the IP addresses, securing devices, IDP and SSO platform, and so on.

Key With Puzzle Piece Finance PowerPoint Templates And PowerPoint Themes 1012
Key With Puzzle Piece Finance PowerPoint Templates And PowerPoint Themes 1012-Aesthetically designed to make a great first impression this template highlights the concept of key and lock. It consists of golden keys tied with the puzzle. It indicates fasten, bar, bolt, lock up, padlock, secure, fix in place, lodge, wedge, confine, secure brace, clench, stiffen, tighten, link, clasp, intertwine, join, unite, interlink, clinch and interlock. Explain the process by which you intend to right it. Show them how you can save the day.-Key With Puzzle Piece Finance PowerPoint Templates And PowerPoint Themes 1012-This PowerPoint template can be used for presentations relating to-Golden Key With Puzzle Piece On Chain, Business, Symbol, Puzzles Or Jigsaws, Success, Design Experience a defining event with our Key With Puzzle Piece Finance PowerPoint Templates And PowerPoint Themes 1012. Change direction for the better.
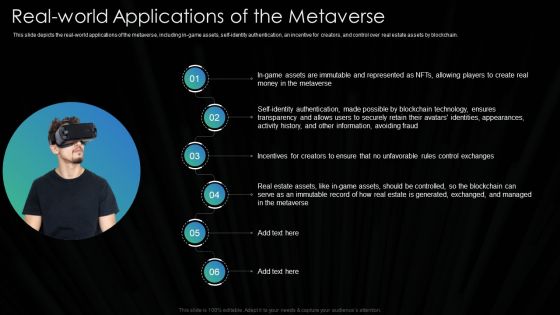
Metaverse Technology IT Real World Applications Of The Metaverse Ppt Show Layout Ideas PDF
This slide depicts the real-world applications of the metaverse, including in-game assets, self-identity authentication, an incentive for creators, and control over real estate assets by blockchain. Deliver an awe inspiring pitch with this creative Metaverse Technology IT Real World Applications Of The Metaverse Ppt Show Layout Ideas PDF bundle. Topics like Avoiding Fraud, Avatars Identities, Securely Retain can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Integrating Data Privacy System Why Choose Us For Data Privacy Icons PDF
This slide explains why you should choose us, including faster product delivery to market, decreased complexity, and secured integrations. This slide explains why you should choose us, including faster product delivery to market, decreased complexity, and secured integrations. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Integrating Data Privacy System Why Choose Us For Data Privacy Icons PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
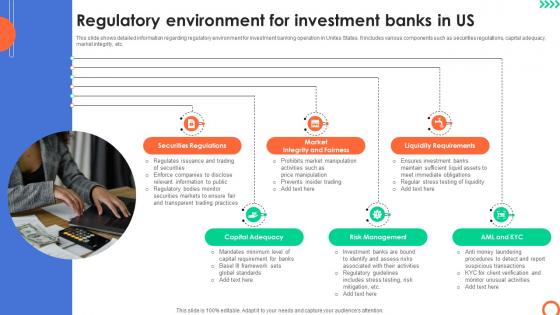
Regulatory Environment For Investment Banks Understanding Investment Banking Framework Fin SS V
This slide shows detailed information regarding regulatory environment for investment banking operation in Unites States. It includes various components such as securities regulations, capital adequacy, market integrity, etc. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Regulatory Environment For Investment Banks Understanding Investment Banking Framework Fin SS V from Slidegeeks and deliver a wonderful presentation. This slide shows detailed information regarding regulatory environment for investment banking operation in Unites States. It includes various components such as securities regulations, capital adequacy, market integrity, etc.
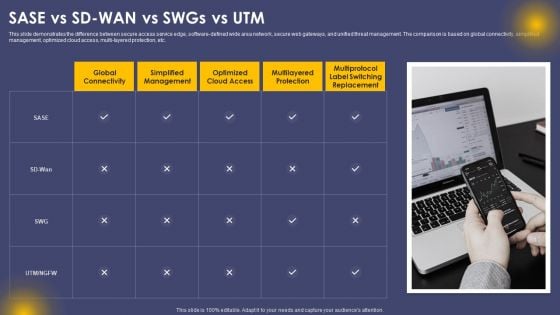
SASE Vs SD WAN Vs Swgs Vs UTM Ppt Layouts Design Inspiration PDF
This slide demonstrates the difference between secure access service edge, software-defined wide area network, secure web gateways, and unified threat management. The comparison is based on global connectivity, simplified management, optimized cloud access, multi-layered protection, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give SASE Vs SD WAN Vs Swgs Vs UTM Ppt Layouts Design Inspiration PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable SASE Vs SD WAN Vs Swgs Vs UTM Ppt Layouts Design Inspiration PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
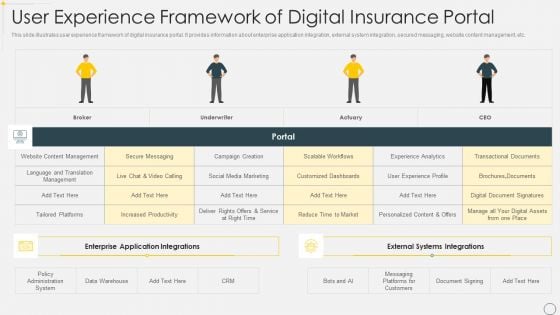
User Experience Framework Of Digital Insurance Portal Brochure PDF
This slide illustrates user experience framework of digital insurance portal. It provides information about enterprise application integration, external system integration, secured messaging, website content management, etc. Showcasing this set of slides titled User Experience Framework Of Digital Insurance Portal Brochure PDF. The topics addressed in these templates are Management, Customized Dashboards, Policy Administration System. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
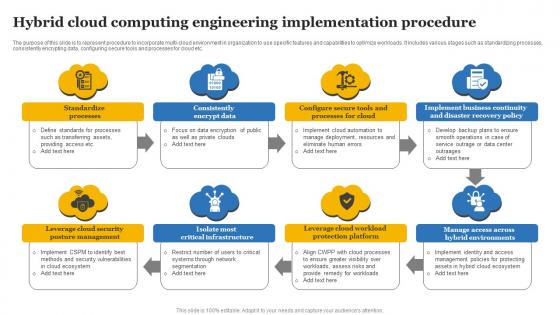
Hybrid Cloud Computing Engineering Implementation Procedure Designs Pdf
The purpose of this slide is to represent procedure to incorporate multi-cloud environment in organization to use specific features and capabilities to optimize workloads. It includes various stages such as standardizing processes, consistently encrypting data, configuring secure tools and processes for cloud etc. Showcasing this set of slides titled Hybrid Cloud Computing Engineering Implementation Procedure Designs Pdf The topics addressed in these templates are Standardize Processes, Consistently Encrypt Data, Business Continuity All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. The purpose of this slide is to represent procedure to incorporate multi-cloud environment in organization to use specific features and capabilities to optimize workloads. It includes various stages such as standardizing processes, consistently encrypting data, configuring secure tools and processes for cloud etc.

IOT Authorization And Authentication For Cybersecurity Management Sample Pdf
This slide provides multiple authorization protocols that helps businesses and organizations to ensure effective and secure management of operations and data transmission. The three protocols are one-way, two-way, and three-way authentication. Showcasing this set of slides titled IOT Authorization And Authentication For Cybersecurity Management Sample Pdf The topics addressed in these templates are One Way Authentication, Two Way Authentication All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide provides multiple authorization protocols that helps businesses and organizations to ensure effective and secure management of operations and data transmission. The three protocols are one-way, two-way, and three-way authentication.

Data Breach Prevention Strategies For Employees Data Fortification Strengthening Defenses
This slide highlights the data breach mitigation measures for workers. These strategies include maintain a record of banking receipts, dont believe everything, be mindful of sharing anything on social media, secure all devices, protect individual accounts, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Data Breach Prevention Strategies For Employees Data Fortification Strengthening Defenses template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Data Breach Prevention Strategies For Employees Data Fortification Strengthening Defenses that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide highlights the data breach mitigation measures for workers. These strategies include maintain a record of banking receipts, dont believe everything, be mindful of sharing anything on social media, secure all devices, protect individual accounts, etc.


 Continue with Email
Continue with Email

 Home
Home


































