Security Assessment
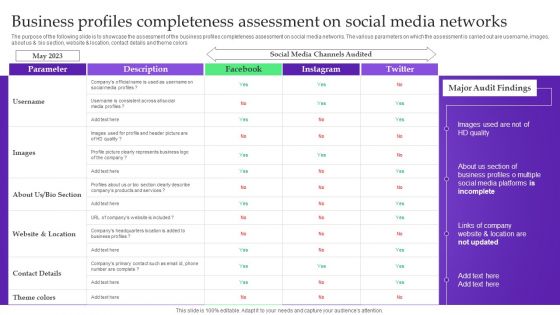
Analysis Plan For E Commerce Promotion Tactics Business Profiles Completeness Assessment On Social Media Networks Ideas PDF
The purpose of the following slide is to showcase the assessment of the business profiles completeness assessment on social media networks. The various parameters on which the assessment is carried out are username, images, about us and bio section, website and location, contact details and theme colors Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Analysis Plan For E Commerce Promotion Tactics Business Profiles Completeness Assessment On Social Media Networks Ideas PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

COVID 19 Risk Analysis Mitigation Policies Ocean Liner Sector Readiness Assessment Checklist For The Cruise Company Structure PDF
This slide provides assessment checklist for the cruise industry. It includes the key questions related to risk mitigation and safety measures in the ship. Deliver an awe inspiring pitch with this creative covid 19 risk analysis mitigation policies ocean liner sector readiness assessment checklist for the cruise company structure pdf bundle. Topics like business, planned, risks can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
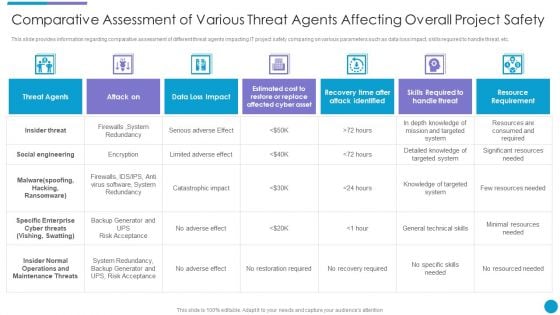
Major Techniques For Project Safety IT Comparative Assessment Of Various Threat Agents Affecting Overall Project Safety Portrait PDF
This slide provides information regarding comparative assessment of different threat agents impacting IT project safety comparing on various parameters such as data loss impact, skills required to handle threat, etc. Deliver an awe inspiring pitch with this creative major techniques for project safety it comparative assessment of various threat agents affecting overall project safety portrait pdf bundle. Topics like threat agents, attack on, data loss impact, resource requirement can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Apples Strategy To Achieve Top Brand Value Position Assessment Of Core Values Associated With Apple Download PDF

Data Center Migration For Information Technology Systems Assessment And To Create Resilient Network Ppt PowerPoint Presentation Complete Deck
Executing a project plan for a business need Here is a top-notch solution for you to carry out the required tasks with complete precision and consistency. Deploy this easy-to-use Data Center Migration For Information Technology Systems Assessment And To Create Resilient Network Ppt PowerPoint Presentation Complete Deck to list the number of activities to be executed, key deliverables, and project phases to bring clarity for your team members. Grab this well-crafted fourty four slide complete deck to deliver a quality project within your deadline. The presentation template is also equipped to do this with its 100 precent editable and customizable capability. Download now.

Strategic Fund Acquisition Plan For Business Opertions Expansion Comparative Assessment Of Banks For Availing Loan Professional PDF
This slide showcases comparison table that can help organization to evaluate the different banks available in market to obtain loans. Its key components are bank, amount, interest rate, EMI per month, time period and collateral needed. Take your projects to the next level with our ultimate collection of Strategic Fund Acquisition Plan For Business Opertions Expansion Comparative Assessment Of Banks For Availing Loan Professional PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest.
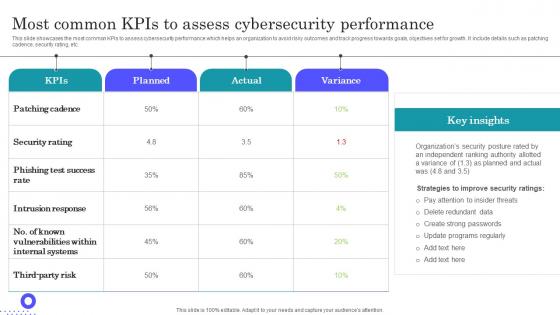
Most Common KPIs To Assess Cybersecurity Performance Slides Pdf
Showcasing this set of slides titled Most Common KPIs To Assess Cybersecurity Performance Slides Pdf The topics addressed in these templates are Intrusion Response, Phishing Test Success, Security Rating All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcases the most common KPIs to assess cybersecurity performance which helps an organization to avoid risky outcomes and track progress towards goals, objectives set for growth. It include details such as patching cadence, security rating, etc.

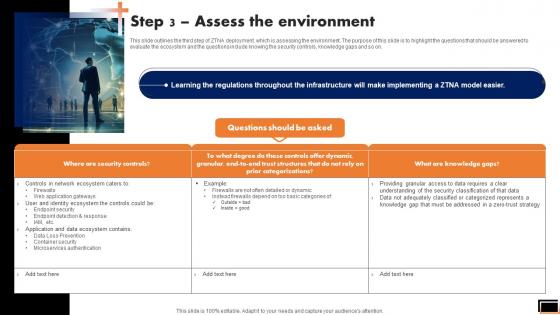
Zero Trust Network Access Step 3 Assess The Environment
This slide outlines the third step of ZTNA deployment, which is assessing the environment. The purpose of this slide is to highlight the questions that should be answered to evaluate the ecosystem and the questions include knowing the security controls, knowledge gaps and so on. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Zero Trust Network Access Step 3 Assess The Environment and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide outlines the third step of ZTNA deployment, which is assessing the environment. The purpose of this slide is to highlight the questions that should be answered to evaluate the ecosystem and the questions include knowing the security controls, knowledge gaps and so on.
Step 3 Assess The Environment Software Defined Perimeter SDP
This slide outlines the third step of ZTNA deployment, which is assessing the environment. The purpose of this slide is to highlight the questions that should be answered to evaluate the ecosystem and the questions include knowing the security controls, knowledge gaps and so on. There are so many reasons you need a Step 3 Assess The Environment Software Defined Perimeter SDP. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide outlines the third step of ZTNA deployment, which is assessing the environment. The purpose of this slide is to highlight the questions that should be answered to evaluate the ecosystem and the questions include knowing the security controls, knowledge gaps and so on.

Zero Trust Model Step 3 Assess The Environment
This slide outlines the third step of ZTNA deployment, which is assessing the environment. The purpose of this slide is to highlight the questions that should be answered to evaluate the ecosystem and the questions include knowing the security controls, knowledge gaps and so on. Get a simple yet stunning designed Zero Trust Model Step 3 Assess The Environment. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Zero Trust Model Step 3 Assess The Environment can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide outlines the third step of ZTNA deployment, which is assessing the environment. The purpose of this slide is to highlight the questions that should be answered to evaluate the ecosystem and the questions include knowing the security controls, knowledge gaps and so on.

Application Protection Ppt Layout Presentation Design
This is a application protection ppt layout presentation design. This is a seven stage process. The stages in this process are content security, risk mitigation, risk assessment, application security, evaluation and assessment, endpoint security, network security.

Monitor And Assess Vendor Risk Management Ppt PowerPoint Presentation File Infographics PDF
The following slide showcases vendor risk analysis checklist to ensure customer data safety. It includes key elements such as information security and privacy, physical assets, web application, infrastructure security etc. The following slide showcases vendor risk analysis checklist to ensure customer data safety. It includes key elements such as information security and privacy, physical assets, web application, infrastructure security etc. Boost your pitch with our creative Monitor And Assess Vendor Risk Management Ppt PowerPoint Presentation File Infographics PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
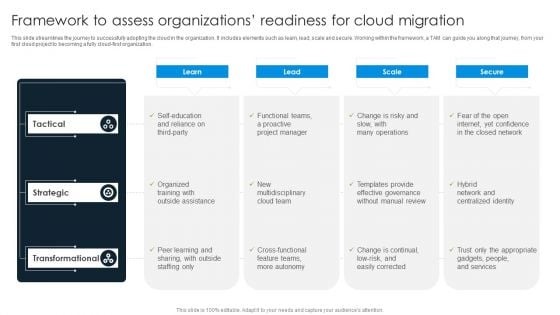
Framework To Assess Organizations Readiness For Cloud Migration Information PDF
This slide streamlines the journey to successfully adopting the cloud in the organization. It includes elements such as learn, lead, scale and secure. Working within the framework, a TAM can guide you along that journey, from your first cloud project to becoming a fully cloud-first organization. Pitch your topic with ease and precision using this Framework To Assess Organizations Readiness For Cloud Migration Information PDF. This layout presents information on Tactical, Strategic, Transformational. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
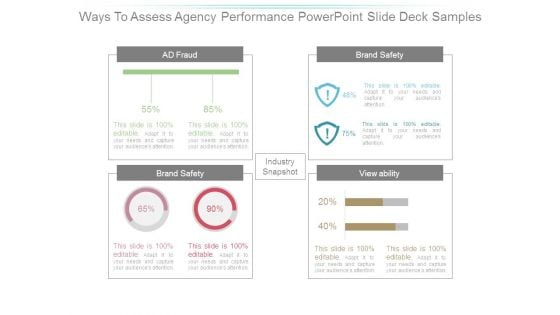
Ways To Assess Agency Performance Powerpoint Slide Deck Samples
This is a ways to assess agency performance powerpoint slide deck samples. This is a four stage process. The stages in this process are industry snapshot, brand safety, ad fraud, viewability, tra score.
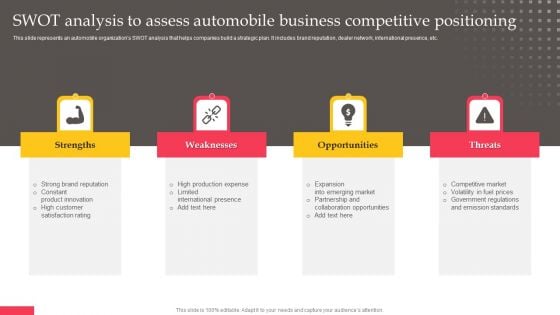
SWOT Analysis To Assess Automobile Business Competitive Positioning Clipart PDF
This slide represents an automobile organizations SWOT analysis that helps companies build a strategic plan. It includes brand reputation, dealer network, international presence, etc. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit SWOT Analysis To Assess Automobile Business Competitive Positioning Clipart PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.
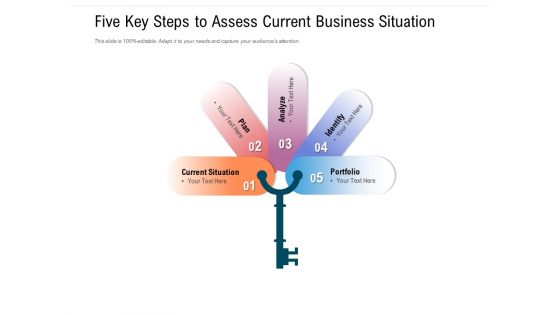
Five Key Steps To Assess Current Business Situation Ppt PowerPoint Presentation Visual Aids Styles PDF
Persuade your audience using this five key steps to assess current business situation ppt powerpoint presentation visual aids styles pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including current situation, plan, analyze, identify, portfolio. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

IT Risk Control Strategies Risk Management Framework Mockup PDF
This slide shows the framework for information technology risk management which includes cyber security governance, IT and security risk assessment, training and awareness, security operation centre, independent audit and gap analysis. Persuade your audience using this IT Risk Control Strategies Risk Management Framework Mockup PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Cyber Security Governance, IT Risk Assessment, Security Assessment. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
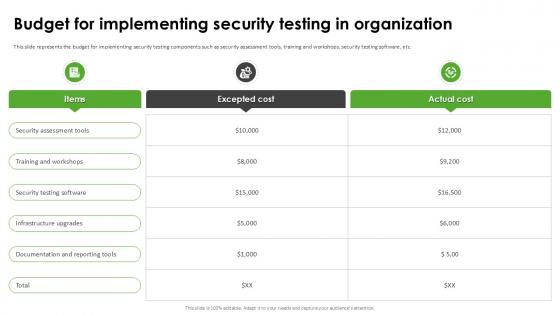
Budget For Implementing Harnessing The World Of Ethical Ppt Presentation
This slide represents the budget for implementing security testing components such as security assessment tools, training and workshops, security testing software, etc. Get a simple yet stunning designed Budget For Implementing Harnessing The World Of Ethical Ppt Presentation It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Budget For Implementing Harnessing The World Of Ethical Ppt Presentation can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide represents the budget for implementing security testing components such as security assessment tools, training and workshops, security testing software, etc.
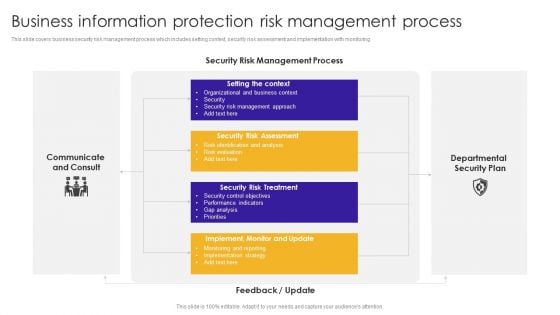
Business Information Protection Risk Management Process Structure PDF
This slide covers business security risk management process which includes setting context, security risk assessment and implementation with monitoring. Pitch your topic with ease and precision using this Business Information Protection Risk Management Process Structure PDF. This layout presents information on Organizational Business, Security Risk Assessment, Performance Indicators. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
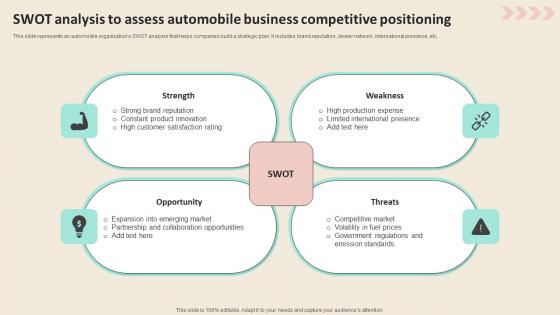
Swot Analysis To Assess Automobile Business Promotional Strategies To Increase Mockup PDF
This slide represents an automobile organizations SWOT analysis that helps companies build a strategic plan. It includes brand reputation, dealer network, international presence, etc. Do you know about Slidesgeeks Swot Analysis To Assess Automobile Business Promotional Strategies To Increase Mockup PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide represents an automobile organizations SWOT analysis that helps companies build a strategic plan. It includes brand reputation, dealer network, international presence, etc.
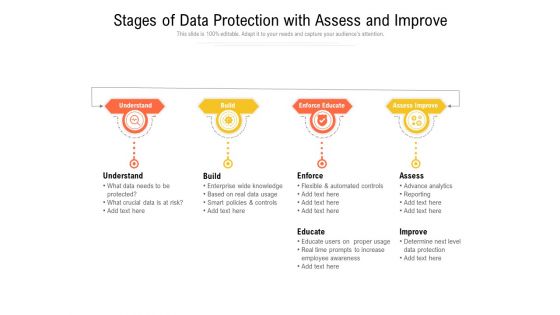
Stages Of Data Protection With Assess And Improve Ppt PowerPoint Presentation File Graphics Example PDF
Persuade your audience using this stages of data protection with assess and improve ppt powerpoint presentation file graphics example pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including educate, assess, build. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
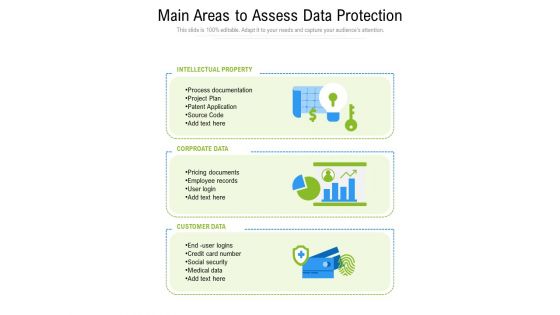
Main Areas To Assess Data Protection Ppt PowerPoint Presentation Gallery Example PDF
Presenting main areas to assess data protection ppt powerpoint presentation gallery example pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including intellectual property, corporate data, customer data. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
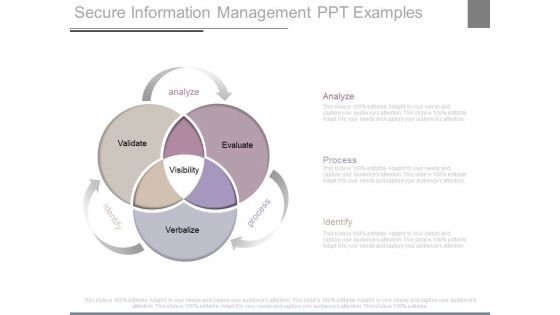
Secure Information Management Ppt Examples
This is a secure information management ppt examples. This is a three stage process. The stages in this process are analyze, process, identify, evaluate, validate, visibility, verbalize.
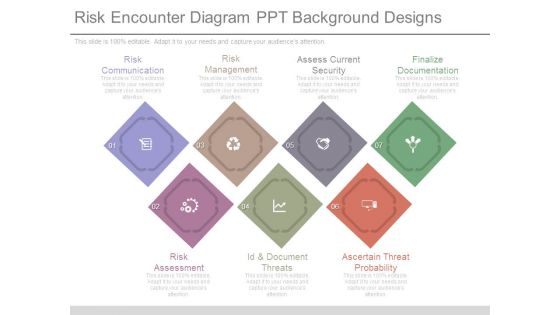
Risk Encounter Diagram Ppt Background Designs
This is a risk encounter diagram ppt background designs. This is a seven stage process. The stages in this process are risk communication, risk management, assess current security, finalize documentation, risk assessment, id and document threats, ascertain threat probability.
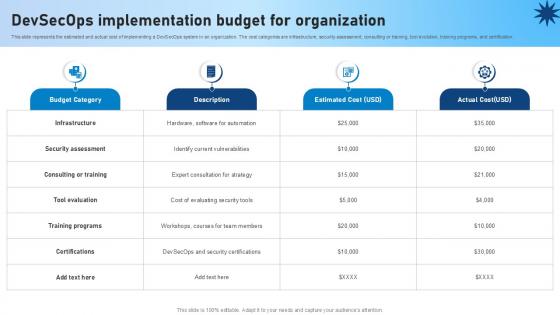
Devsecops Implementation Budget For Organization Role Of Devsecops Ppt Powerpoint
This slide represents the estimated and actual cost of implementing a DevSecOps system in an organization. The cost categories are infrastructure, security assessment, consulting or training, tool evolution, training programs, and certification. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Devsecops Implementation Budget For Organization Role Of Devsecops Ppt Powerpoint and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide represents the estimated and actual cost of implementing a DevSecOps system in an organization. The cost categories are infrastructure, security assessment, consulting or training, tool evolution, training programs, and certification.

Open Source WAF Features Ppt Portfolio Influencers PDF
This slide represents the characteristics of an open-source Web Application Firewall. The purpose of this slide is to give an overview of the primary features of open-source WAF, including continuous passive security assessment, real-time application security monitoring, full HTTP traffic logging, and web application hardening. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Open Source WAF Features Ppt Portfolio Influencers PDF from Slidegeeks and deliver a wonderful presentation.
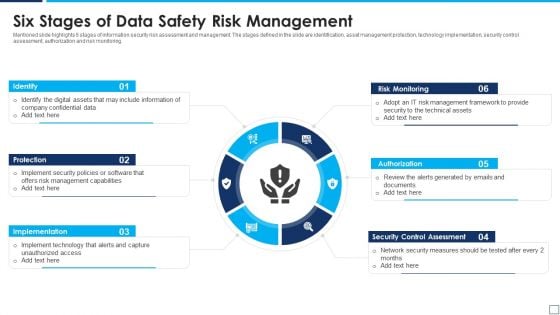
Six Stages Of Data Safety Risk Management Summary PDF
Mentioned slide highlights 6 stages of information security risk assessment and management. The stages defined in the slide are identification, asset management protection, technology implementation, security control assessment, authorization and risk monitoring. Presenting six stages of data safety risk management summary pdf to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including identify, protection, implementation. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Implementing Cybersecurity Awareness Program To Prevent Attacks How Much Employees Are Aware Elements PDF
The purpose of this slide is to showcase the cyber security assessment test result. It covers information about the pass fail rate of employees who received the security awareness training and fail rate by age. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Implementing Cybersecurity Awareness Program To Prevent Attacks How Much Employees Are Aware Elements PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates
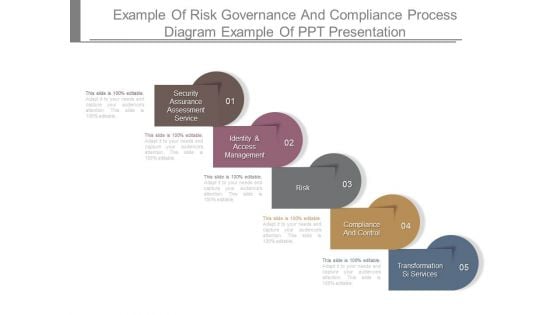
Example Of Risk Governance And Compliance Process Diagram Example Of Ppt Presentation
This is a example of risk governance and compliance process diagram example of ppt presentation. This is a five stage process. The stages in this process are security assurance assessment service, identity and access management, risk, compliance and control, transformation si services.

Global Cyber Terrorism Incidents On The Rise IT Checklist To Deal With Cyber Terrorism Threats Key Template PDF
This slide represents the checklist to deal with cyber-terrorism threats which involve 24 7 monitoring, employee training, keeping software updated. Presenting global cyber terrorism incidents on the rise it checklist to deal with cyber terrorism threats key template pdf to provide visual cues and insights. Share and navigate important information on nine stages that need your due attention. This template can be used to pitch topics like employee training, monitoring, cyber security assessment, incident response plan, limited access privileges. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Global Cyber Terrorism Incidents On The Rise IT Checklist To Deal With Cyber Terrorism Threats Infographics PDF
This slide represents the checklist to deal with cyber-terrorism threats which involve 24 7 monitoring, employee training, keeping software updated. This is a global cyber terrorism incidents on the rise it checklist to deal with cyber terrorism threats infographics pdf template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like employee training, monitoring, cyber security assessment, incident response plan, limited access privileges. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
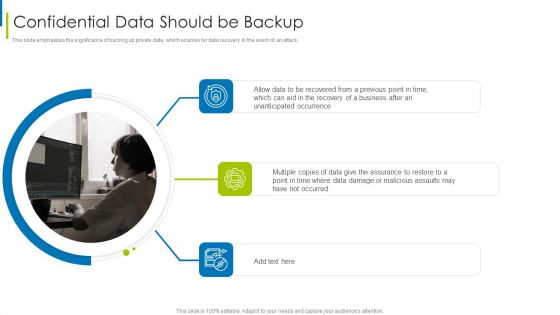
Cyber Terrorism Assault Confidential Data Should Be Backup Brochure PDF
This slide emphasizes the significance of backing up private data, which enables for data recovery in the event of an attack.Presenting cyber terrorism assault confidential data should be backup brochure pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Cyber Security Assessment, Limited Access Privileges, Employee Training In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Benefits Of Using Cybersecurity Key Performance Indicators Slides Pdf
Showcasing this set of slides titled Benefits Of Using Cybersecurity Key Performance Indicators Slides Pdf The topics addressed in these templates are Organizations Network, Security Assessments, Provides Privileged All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcases the benefits of using cybersecurity key performance indicators which help an organization to provide a snapshot to its relevant stakeholders, managers. It include details such as removes unknown devices on an organizations network, etc.
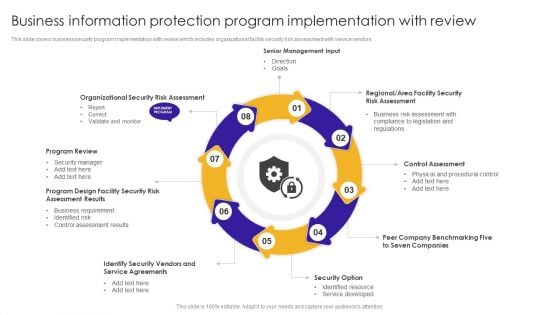
Business Information Protection Program Implementation With Review Information PDF
This slide covers business security program implementation with review which includes organizational facility security risk assessment with service vendors.Persuade your audience using this Business Information Protection Program Implementation With Review Information PDF. This PPT design covers eight stages, thus making it a great tool to use. It also caters to a variety of topics including Program Review, Assessment Results, Business Requirement. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
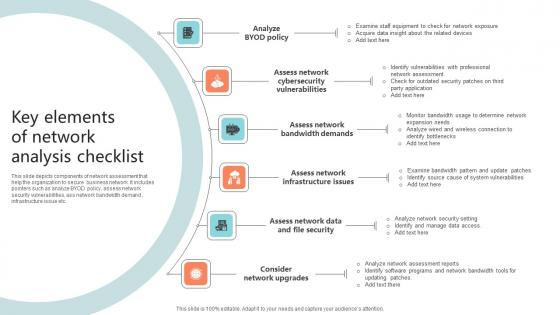
Key Elements Of Network Analysis Checklist Microsoft Pdf
This slide depicts components of network assessment that help the organization to secure business network. It includes pointers such as analyze BYOD policy, assess network security vulnerabilities, ass network bandwidth demand , infrastructure issue etc.Pitch your topic with ease and precision using this Key Elements Of Network Analysis Checklist Microsoft Pdf This layout presents information on Cybersecurity Vulnerabilities, Bandwidth Demands, Assess Network It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide depicts components of network assessment that help the organization to secure business network. It includes pointers such as analyze BYOD policy, assess network security vulnerabilities, ass network bandwidth demand , infrastructure issue etc.
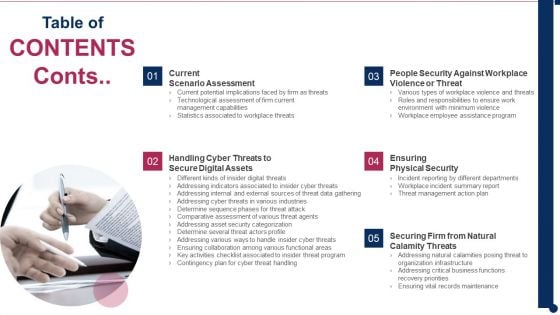
Threat Management At Workplace Contents Conts Diagrams Pdf
This is a threat management at workplace contents conts diagrams pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like ensuring physical security, current scenario assessment, people security against workplace violence or threat. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
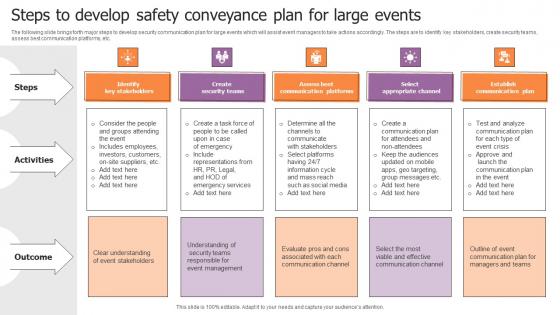
Steps To Develop Safety Conveyance Plan For Large Events Designs Pdf
The following slide brings forth major steps to develop security communication plan for large events which will assist event managers to take actions accordingly. The steps are to identify key stakeholders, create security teams, assess best communication platforms, etc. Showcasing this set of slides titled Steps To Develop Safety Conveyance Plan For Large Events Designs Pdf. The topics addressed in these templates are Identify Key Stakeholders, Create Security Teams, Select Appropriate Channel. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. The following slide brings forth major steps to develop security communication plan for large events which will assist event managers to take actions accordingly. The steps are to identify key stakeholders, create security teams, assess best communication platforms, etc.
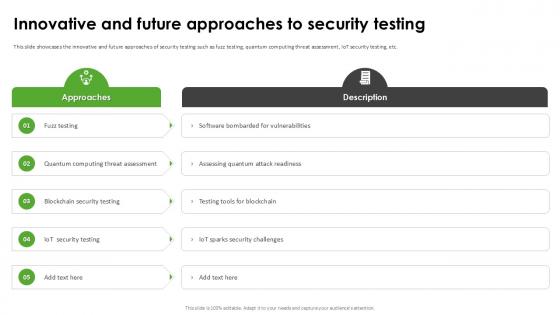
Innovative And Future Approaches Harnessing The World Of Ethical Ppt Slide
This slide showcases the innovative and future approaches of security testing such as fuzz testing, quantum computing threat assessment, IoT security testing, etc. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Innovative And Future Approaches Harnessing The World Of Ethical Ppt Slide and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide showcases the innovative and future approaches of security testing such as fuzz testing, quantum computing threat assessment, IoT security testing, etc.

Table Of Contents Mitigating Cybersecurity Threats And Vulnerabilities Portrait PDF
Presenting table of contents mitigating cybersecurity threats and vulnerabilities portrait pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like current scenario assessment, secure digital assets, physical security, natural calamity threats. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Secure Internet Access Computer PowerPoint Themes And PowerPoint Slides 0811
Microsoft PowerPoint Theme and Slide with transparent internet browser with a large chrome key protruding out from the window Fight off critics with our Secure Internet Access Computer PowerPoint Themes And PowerPoint Slides 0811. Be confident and convinced of your assessment.

Technical Stack For Evaluating Confidential Secure Computing Framework Information Pdf
This slide depicts the technical stack while assessing confidential computing solutions. The stack divides these solutions into four levels, including application software vendors, infrastructure providers, hardware vendors, and cryptographic building blocks. Want to ace your presentation in front of a live audience Our Technical Stack For Evaluating Confidential Secure Computing Framework Information Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide depicts the technical stack while assessing confidential computing solutions. The stack divides these solutions into four levels, including application software vendors, infrastructure providers, hardware vendors, and cryptographic building blocks.
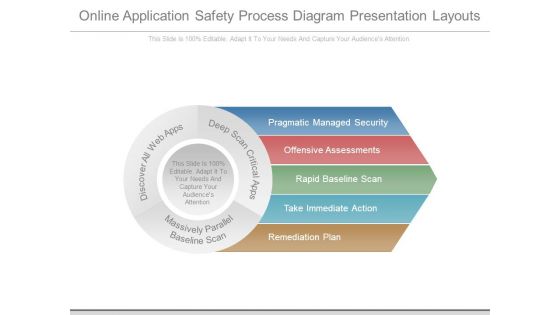
Online Application Safety Process Diagram Presentation Layouts
This is a online application safety process diagram presentation layouts. This is a five stage process. The stages in this process are pragmatic managed security, offensive assessments, rapid baseline scan, take immediate action, remediation plan, discover all web apps, deep scan critical apps, massively parallel, baseline scan.
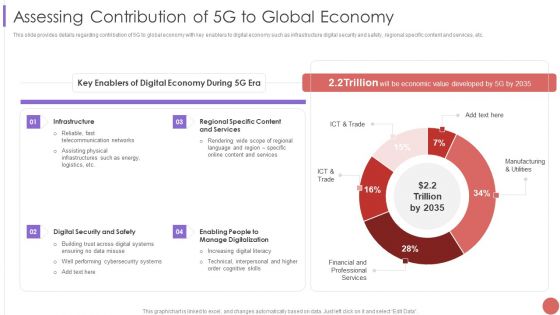
Assessing Contribution Of 5G To Global Economy Pictures PDF
This slide provides details regarding contribution of 5G to global economy with key enablers to digital economy such as infrastructure digital security and safety, regional specific content and services, etc.Deliver an awe inspiring pitch with this creative Assessing Contribution Of 5G To Global Economy Pictures PDF bundle. Topics like Telecommunication Networks, Across Digital Systems, Manage Digitalization can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Assessing Contribution Of 5G To Global Economy Icons PDF
This slide provides details regarding contribution of 5G to global economy with key enablers to digital economy such as infrastructure digital security and safety, regional specific content and services, etc. Deliver and pitch your topic in the best possible manner with this Assessing Contribution Of 5G To Global Economy Icons PDF. Use them to share invaluable insights on Financial, Economic Value Developed, Digital Systems and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
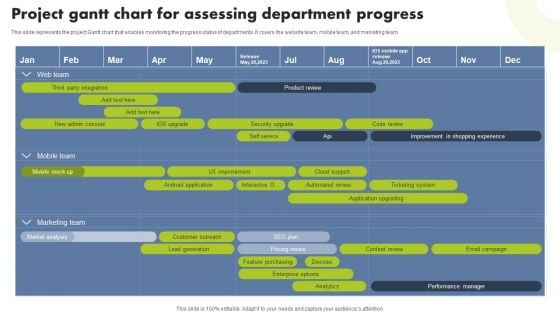
Project Gantt Chart For Assessing Department Progress Brochure PDF
This slide represents the project Gantt chart that enables monitoring the progress status of departments. It covers the website team, mobile team, and marketing team. Showcasing this set of slides titled Project Gantt Chart For Assessing Department Progress Brochure PDF. The topics addressed in these templates are Third Party Integration, New Admin Console, Security Upgrade. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
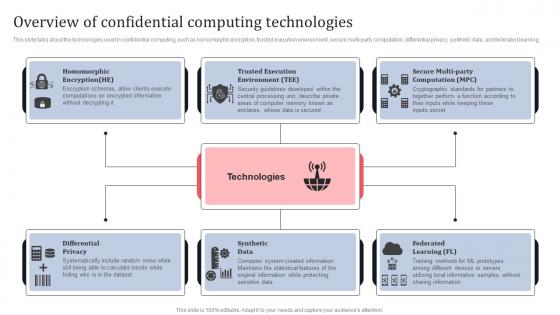
Overview Of Confidential Computing Technologies Secure Multi Party Designs Pdf
This slide talks about the technologies used in confidential computing, such as homomorphic encryption, trusted execution environment, secure multi-party computation, differential privacy, synthetic data, and federated learning. Get a simple yet stunning designed Overview Of Confidential Computing Technologies Secure Multi Party Designs Pdf It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Overview Of Confidential Computing Technologies Secure Multi Party Designs Pdf can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide talks about the technologies used in confidential computing, such as homomorphic encryption, trusted execution environment, secure multi-party computation, differential privacy, synthetic data, and federated learning.
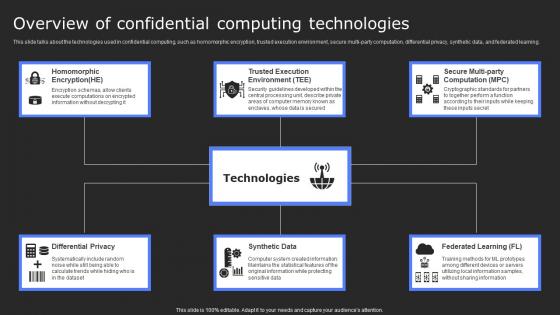
Overview Of Confidential Computing Technologies Secure Computing Framework Slides Pdf
This slide talks about the technologies used in confidential computing, such as homomorphic encryption, trusted execution environment, secure multi-party computation, differential privacy, synthetic data, and federated learning. Present like a pro with Overview Of Confidential Computing Technologies Secure Computing Framework Slides Pdf Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide talks about the technologies used in confidential computing, such as homomorphic encryption, trusted execution environment, secure multi-party computation, differential privacy, synthetic data, and federated learning.
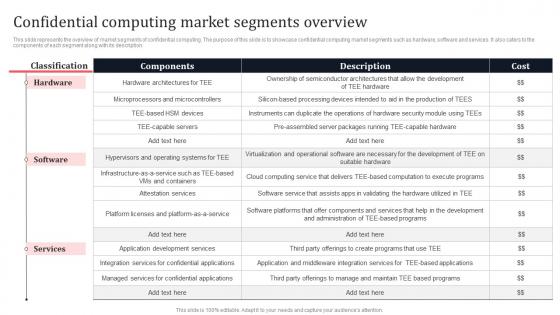
Confidential Computing Market Segments Overview Secure Multi Party Background Pdf
This slide represents the overview of market segments of confidential computing. The purpose of this slide is to showcase confidential computing market segments such as hardware, software and services. It also caters to the components of each segment along with its description. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Confidential Computing Market Segments Overview Secure Multi Party Background Pdf was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Confidential Computing Market Segments Overview Secure Multi Party Background Pdf This slide represents the overview of market segments of confidential computing. The purpose of this slide is to showcase confidential computing market segments such as hardware, software and services. It also caters to the components of each segment along with its description.
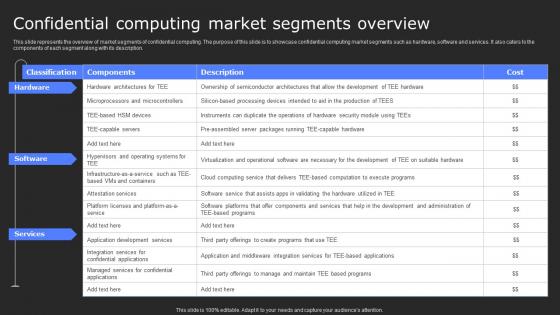
Confidential Computing Market Segments Overview Secure Computing Framework Structure Pdf
This slide represents the overview of market segments of confidential computing. The purpose of this slide is to showcase confidential computing market segments such as hardware, software and services. It also caters to the components of each segment along with its description. his modern and well-arranged Confidential Computing Market Segments Overview Secure Computing Framework Structure Pdf provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide represents the overview of market segments of confidential computing. The purpose of this slide is to showcase confidential computing market segments such as hardware, software and services. It also caters to the components of each segment along with its description.
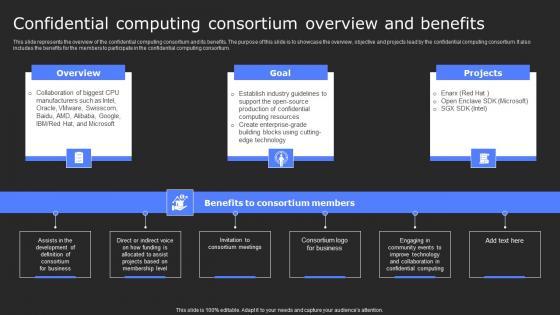
Confidential Computing Consortium Overview And Secure Computing Framework Inspiration Pdf
This slide represents the overview of the confidential computing consortium and its benefits. The purpose of this slide is to showcase the overview, objective and projects lead by the confidential computing consortium. It also includes the benefits for the members to participate in the confidential computing consortium. Make sure to capture your audiences attention in your business displays with our gratis customizable Confidential Computing Consortium Overview And Secure Computing Framework Inspiration Pdf. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide represents the overview of the confidential computing consortium and its benefits. The purpose of this slide is to showcase the overview, objective and projects lead by the confidential computing consortium. It also includes the benefits for the members to participate in the confidential computing consortium.
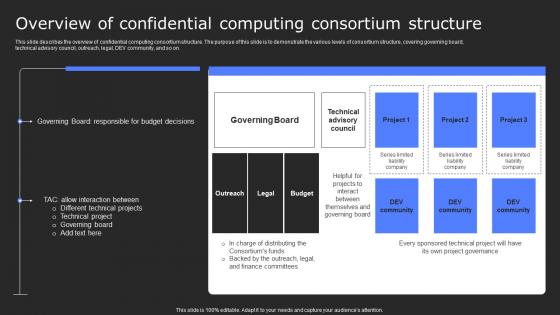
Overview Of Confidential Computing Consortium Secure Computing Framework Professional Pdf
This slide describes the overview of confidential computing consortium structure. The purpose of this slide is to demonstrate the various levels of consortium structure, covering governing board, technical advisory council, outreach, legal, DEV community, and so on. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Overview Of Confidential Computing Consortium Secure Computing Framework Professional Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide describes the overview of confidential computing consortium structure. The purpose of this slide is to demonstrate the various levels of consortium structure, covering governing board, technical advisory council, outreach, legal, DEV community, and so on.
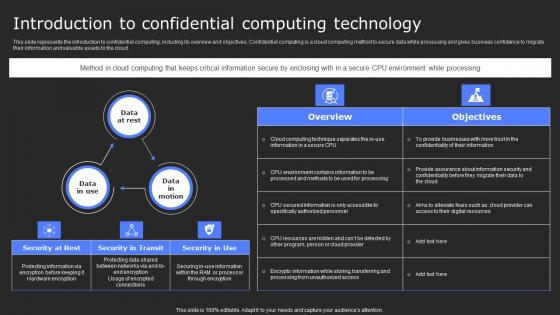
Introduction To Confidential Computing Technology Secure Computing Framework Elements Pdf
This slide represents the introduction to confidential computing, including its overview and objectives. Confidential computing is a cloud computing method to secure data while processing and gives business confidence to migrate their information and valuable assets to the cloud. Boost your pitch with our creative Introduction To Confidential Computing Technology Secure Computing Framework Elements Pdf. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide represents the introduction to confidential computing, including its overview and objectives. Confidential computing is a cloud computing method to secure data while processing and gives business confidence to migrate their information and valuable assets to the cloud.
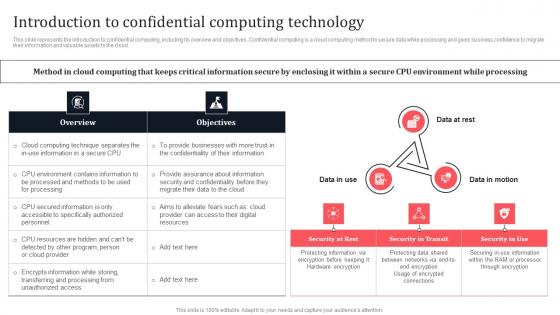
Introduction To Confidential Computing Technology Secure Multi Party Download Pdf
This slide represents the introduction to confidential computing, including its overview and objectives. Confidential computing is a cloud computing method to secure data while processing and gives business confidence to migrate their information and valuable assets to the cloud. Do you know about Slidesgeeks Introduction To Confidential Computing Technology Secure Multi Party Download Pdf These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide represents the introduction to confidential computing, including its overview and objectives. Confidential computing is a cloud computing method to secure data while processing and gives business confidence to migrate their information and valuable assets to the cloud.
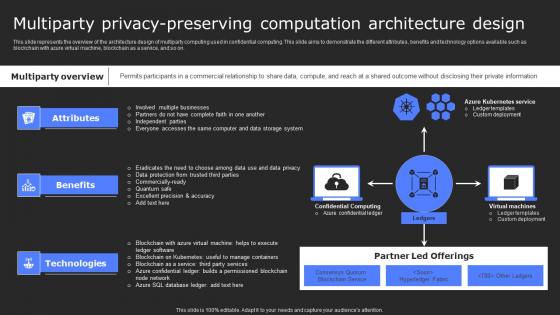
Multiparty Privacy Preserving Computation Secure Computing Framework Topics Pdf
This slide represents the overview of the architecture design of multiparty computing used in confidential computing. This slide aims to demonstrate the different attributes, benefits and technology options available such as blockchain with azure virtual machine, blockchain as a service, and so on. Want to ace your presentation in front of a live audience Our Multiparty Privacy Preserving Computation Secure Computing Framework Topics Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide represents the overview of the architecture design of multiparty computing used in confidential computing. This slide aims to demonstrate the different attributes, benefits and technology options available such as blockchain with azure virtual machine, blockchain as a service, and so on.

Hardware Wallets For Secure Crypto Storage Cryptocurrency Management With Blockchain
This slide represents overview and hardware devices of hardware crypto wallet. The purpose of this slide is to highlight some device used such as ledger nano x, trezor model t, ledge nano s, etc.Presenting this PowerPoint presentation, titled Hardware Wallets For Secure Crypto Storage Cryptocurrency Management With Blockchain, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Hardware Wallets For Secure Crypto Storage Cryptocurrency Management With Blockchain. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Hardware Wallets For Secure Crypto Storage Cryptocurrency Management With Blockchain that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide represents overview and hardware devices of hardware crypto wallet. The purpose of this slide is to highlight some device used such as ledger nano x, trezor model t, ledge nano s, etc.
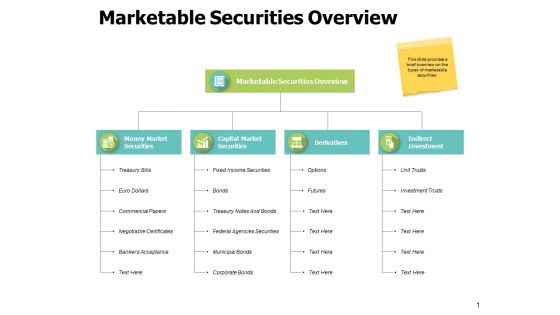
Marketable Securities Overview Ppt PowerPoint Presentation Gallery Demonstration
This is a marketable securities overview ppt powerpoint presentation gallery demonstration. This is a four stage process. The stages in this process are marketing, business, management, planning, strategy.
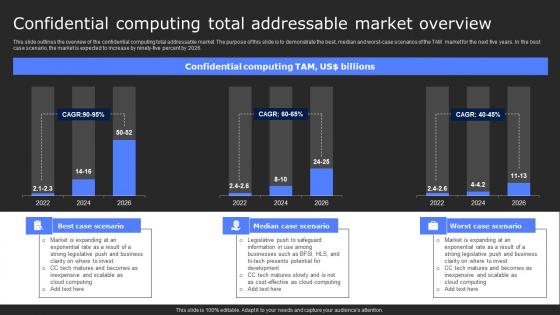
Confidential Computing Total Addressable Secure Computing Framework Themes Pdf
This slide outlines the overview of the confidential computing total addressable market. The purpose of this slide is to demonstrate the best, median and worst-case scenarios of the TAM market for the next five years. In the best case scenario, the market is expected to increase by ninety-five percent by 2026. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Confidential Computing Total Addressable Secure Computing Framework Themes Pdf from Slidegeeks and deliver a wonderful presentation. This slide outlines the overview of the confidential computing total addressable market. The purpose of this slide is to demonstrate the best, median and worst-case scenarios of the TAM market for the next five years. In the best case scenario, the market is expected to increase by ninety-five percent by 2026.
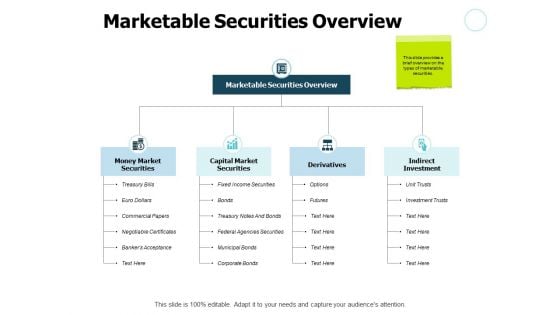
Marketable Securities Overview Investment Ppt PowerPoint Presentation Styles Graphic Images
Presenting this set of slides with name marketable securities overview investment ppt powerpoint presentation styles graphic images. This is a two stage process. The stages in this process are process, business, management, planning, strategy. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
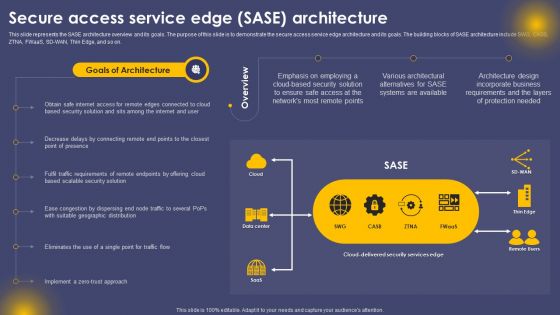
Secure Access Service Edge SASE Architecture Ppt Inspiration Grid PDF
This slide represents the SASE architecture overview and its goals. The purpose of this slide is to demonstrate the secure access service edge architecture and its goals. The building blocks of SASE architecture include SWG, CASB, ZTNA, FWaaS, SD-WAN, Thin Edge, and so on. This Secure Access Service Edge SASE Architecture Ppt Inspiration Grid PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The product features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today

Checklist Of Mandatory Documents Required For ISO 27001 Certification Structure PDF
Following slide displays checklist of mandatory documents required to get ISO 27001 certification along with the status. Deliver an awe inspiring pitch with this creative Checklist Of Mandatory Documents Required For ISO 27001 Certification Structure PDF bundle. Topics like Mandatory Documents, Information Security, Risk Assessment can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.


 Continue with Email
Continue with Email

 Home
Home


































