Security Dashboard

Cyber Security Compliance Framework With Individual Rights Ppt PowerPoint Presentation Infographics Graphics Pictures
Presenting this set of slides with name cyber security compliance framework with individual rights ppt powerpoint presentation infographics graphics pictures. This is a twelve stage process. The stages in this process are raise awareness, information held, communicating privacy, individual rights, subject access requests, legalities of processing personal data, consent, protecting childrens data, data breaches, data protection by design, data protection officers, international work. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
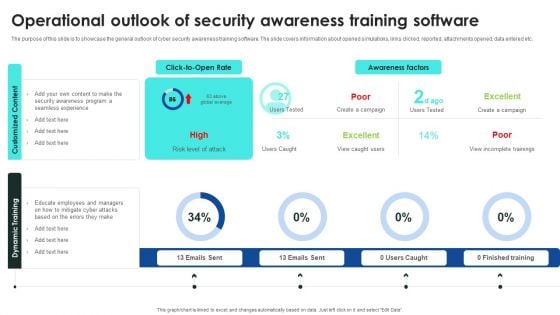
Implementing Cybersecurity Awareness Program To Prevent Attacks Operational Outlook Of Security Awareness Elements PDF
The purpose of this slide is to showcase the general outlook of cyber security awareness training software. The slide covers information about opened simulations, links clicked, reported, attachments opened, data entered etc. Slidegeeks has constructed Implementing Cybersecurity Awareness Program To Prevent Attacks Operational Outlook Of Security Awareness Elements PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.

Key Practices For Data Security Management Ppt PowerPoint Presentation File Background Designs PDF
Persuade your audience using this key practices for data security management ppt powerpoint presentation file background designs pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including management, deployment, implementation. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cyber Security Plan Implementation Timeline Ppt PowerPoint Presentation File Infographic Template PDF
The following slide presents the cyber security program execution timeline to organize tasks and ensure timely execution. It includes activities such as updating systems and passwords, performing penetration test, checking disaster recovery system, conducting training etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Cyber Security Plan Implementation Timeline Ppt PowerPoint Presentation File Infographic Template PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
Four Steps Of Cyber Security Data Breach Threats Process Ppt Icon Format Ideas PDF
This slide covers steps utilised to breach data. It includes stages such as probing, performing initial attack, expansion of attacks and data lifting. Presenting Four Steps Of Cyber Security Data Breach Threats Process Ppt Icon Format Ideas PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Probe, Initial Attack, Expanded Attack, Data Lift. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Prevention Of Information Cyber Security Awareness Trends In 2023 Infographics PDF
The purpose of this slide is to showcase security awareness trends which the organization has to look out for in 2023. increase in malware and ransomware attack, more employees will be targeted by mobile malware attack and advancement of phishing attack are some of the major trends mentioned in the slide. rom laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Prevention Of Information Cyber Security Awareness Trends In 2023 Infographics PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
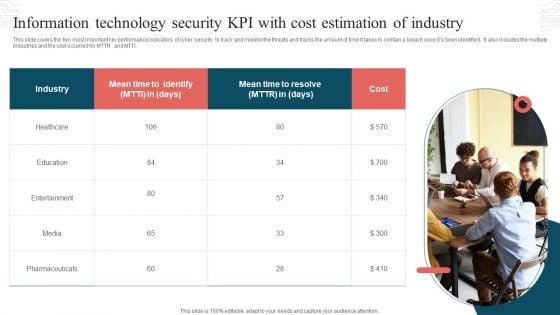
Information Technology Security KPI With Cost Estimation Of Industry Topics PDF
This slide covers the two most important key performance indicators of cyber security to track and monitor the threats and tracks the amount of time it takes to contain a breach once its been identified. It also includes the multiple industries and the cost occurred for MTTR and MTTI. Persuade your audience using this Information Technology Security KPI With Cost Estimation Of Industry Topics PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Industry, Mean Time, Cost. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Incident Response Techniques Deployement Cyber Security Systems Monitoring Report Microsoft PDF
This slide represents the report to effectively monitor the networks and systems of the organization. It includes kpis such as total intrusion attempts, mean detect team, mean resolve time etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Incident Response Techniques Deployement Cyber Security Systems Monitoring Report Microsoft PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Incident Response Techniques Deployement Cyber Security Systems Monitoring Report Microsoft PDF today and make your presentation stand out from the rest.
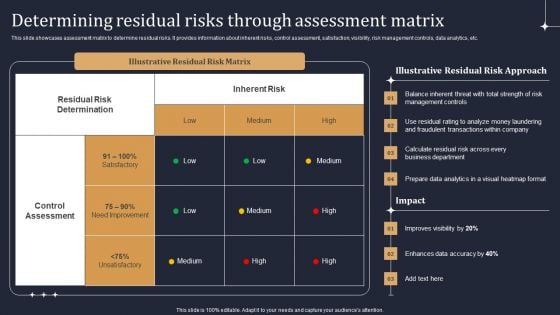
KYC Transaction Monitoring System Business Security Determining Residual Risks Topics PDF
This slide showcases assessment matrix to determine residual risks. It provides information about inherent risks, control assessment, satisfaction, visibility, risk management controls, data analytics, etc. Explore a selection of the finest KYC Transaction Monitoring System Business Security Determining Residual Risks Topics PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our KYC Transaction Monitoring System Business Security Determining Residual Risks Topics PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
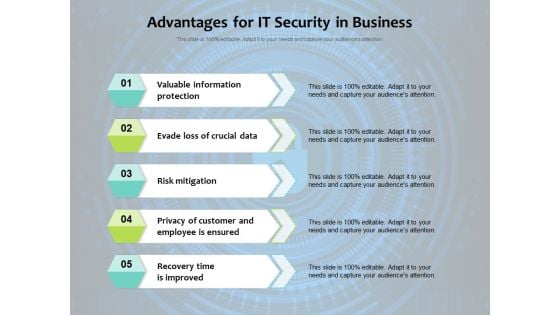
Advantages For IT Security In Business Ppt PowerPoint Presentation Infographic Template Microsoft PDF
Presenting advantages for it security in business ppt powerpoint presentation infographic template microsoft pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including valuable information protection, evade loss of crucial data, risk mitigation, privacy of customer and employee is ensured, recovery time is improved. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
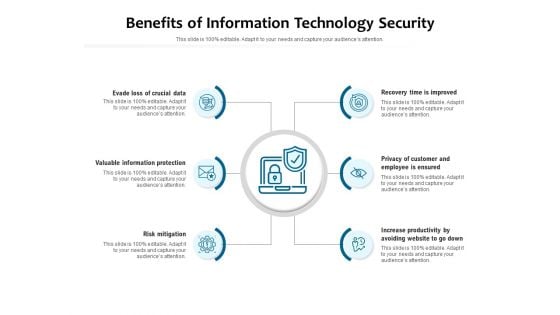
Benefits Of Information Technology Security Ppt PowerPoint Presentation Layouts Layouts PDF
Presenting benefits of information technology security ppt powerpoint presentation layouts layouts pdf to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including evade loss of crucial data, valuable information protection, risk mitigation, recovery time is improved, privacy of customer and employee is ensured, increase productivity by avoiding website to go down. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

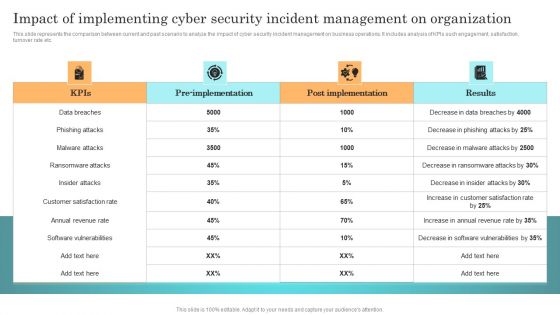
Impact Of Implementing Cyber Security Incident Management On Organization Microsoft PDF
This slide represents the comparison between current and past scenario to analyze the impact of cyber security incident management on business operations. It includes analysis of KPIs such engagement, satisfaction, turnover rate etc. Slidegeeks has constructed Impact Of Implementing Cyber Security Incident Management On Organization Microsoft PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.
Incident Response Techniques Deployement Impact Of Implementing Cyber Security Incident Management Formats PDF
This slide represents the comparison between current and past scenario to analyze the impact of cyber security incident management on business operations. It includes analysis of KPIs such engagement, satisfaction, turnover rate etc. Retrieve professionally designed Incident Response Techniques Deployement Impact Of Implementing Cyber Security Incident Management Formats PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
Impact Of Implementing Cyber Security Incident Management On Organization Icons PDF
This slide represents the comparison between current and past scenario to analyze the impact of cyber security incident management on business operations. It includes analysis of KPIs such engagement, satisfaction, turnover rate etc. Present like a pro with Impact Of Implementing Cyber Security Incident Management On Organization Icons PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Workplace Security Management Program Ppt PowerPoint Presentation Complete Deck With Slides
Using this ready-made PowerPoint slide, you can incorporate your own data to make an impact with your business innovation and clarity of goals. Use this brilliantly designed Workplace Security Management Program Ppt PowerPoint Presentation Complete Deck With Slides to showcase how ultimately all business concepts are related. This presentation template can also be used to record resource allocation in a visual form. The twenty one Slide Workplace Security Management Program Ppt PowerPoint Presentation Complete Deck With Slides is suitable for all your business needs, where you need to make sure that all bases are covered. Download this PPT template now to start a journey on your chosen business, with customer satisfaction the key aim.

Cloud Information Security Theft Or Loss Of Intellectual Property Ppt Show Guidelines PDF
Presenting Cloud Information Security Theft Or Loss Of Intellectual Property Ppt Show Guidelines PDF to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like Crucial Data, Businesses Experience, Cloud Storage. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Padlock On Keyboard Data Security PowerPoint Templates Ppt Backgrounds For Slides 0113
We present our Padlock On Keyboard Data Security PowerPoint Templates PPT Backgrounds For Slides 0113.Use our Computer PowerPoint Templates because Our PowerPoint Templates and Slides will let you Hit the right notes. Watch your audience start singing to your tune. Download our Technology PowerPoint Templates because Our PowerPoint Templates and Slides will help you be quick off the draw. Just enter your specific text and see your points hit home. Download our Marketing PowerPoint Templates because Our PowerPoint Templates and Slides will Embellish your thoughts. They will help you illustrate the brilliance of your ideas. Download our Business PowerPoint Templates because Our PowerPoint Templates and Slides will let you Clearly mark the path for others to follow. Present our Success PowerPoint Templates because Our PowerPoint Templates and Slides has conjured up a web of all you need with the help of our great team. Use them to string together your glistening ideas.Use these PowerPoint slides for presentations relating to A padlock on keyboard, computer, technology, marketing, business, success. The prominent colors used in the PowerPoint template are Yellow, Blue navy, White. Professionals tell us our Padlock On Keyboard Data Security And Protection PowerPoint Templates PPT Backgrounds For Slides 0113 will save the presenter time. PowerPoint presentation experts tell us our marketing PowerPoint templates and PPT Slides are readymade to fit into any presentation structure. You can be sure our Padlock On Keyboard Data Security And Protection PowerPoint Templates PPT Backgrounds For Slides 0113 will make the presenter look like a pro even if they are not computer savvy. PowerPoint presentation experts tell us our on PowerPoint templates and PPT Slides are readymade to fit into any presentation structure. We assure you our Padlock On Keyboard Data Security And Protection PowerPoint Templates PPT Backgrounds For Slides 0113 will save the presenter time. PowerPoint presentation experts tell us our technology PowerPoint templates and PPT Slides look good visually. With our Padlock On Keyboard Data Security PowerPoint Templates Ppt Backgrounds For Slides 0113 there is no need to exaggerate. They are always brief and accurate.
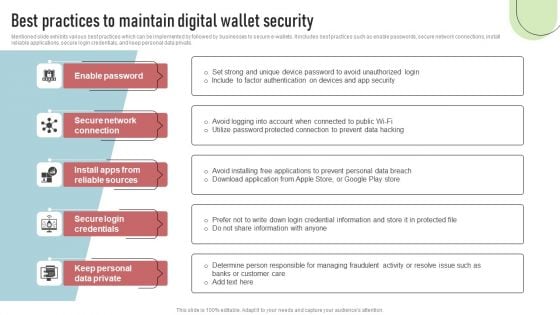
Cashless Payment Strategies To Enhance Business Performance Best Practices To Maintain Digital Wallet Security Brochure PDF
Mentioned slide exhibits various best practices which can be implemented by followed by businesses to secure e-wallets. It includes best practices such as enable passwords, secure network connections, install reliable applications, secure login credentials, and keep personal data private. Retrieve professionally designed Cashless Payment Strategies To Enhance Business Performance Best Practices To Maintain Digital Wallet Security Brochure PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Security Software Company Investor Funding Pitch Deck Core Team Guidelines PDF
The following slide showcases key personnel of executive team of IT company which are CEO, chief architect, VP marketing, sales, product, engineering, chief data scientist, chief scientist, etc. Get a simple yet stunning designed Security Software Company Investor Funding Pitch Deck Core Team Guidelines PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Security Software Company Investor Funding Pitch Deck Core Team Guidelines PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
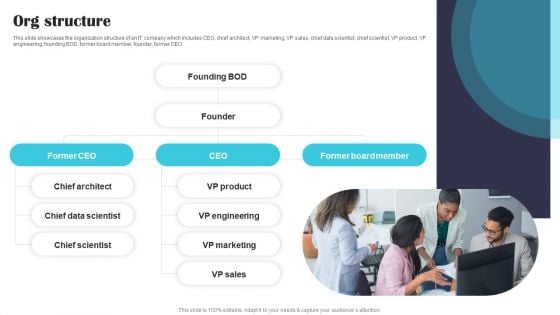
Security Software Company Investor Funding Pitch Deck Org Structure Guidelines PDF
This slide showcases the organization structure of an IT company which includes CEO, chief architect, VP marketing, VP sales, chief data scientist, chief scientist, VP product, VP engineering, founding BOD, former board member, founder, former CEO. Find highly impressive Security Software Company Investor Funding Pitch Deck Org Structure Guidelines PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Security Software Company Investor Funding Pitch Deck Org Structure Guidelines PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.
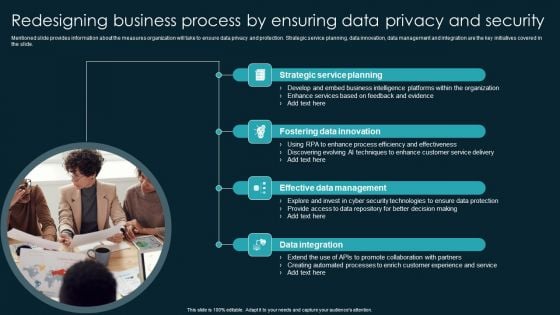
Redesigning Business Process By Ensuring Data Privacy And Security Infographics PDF
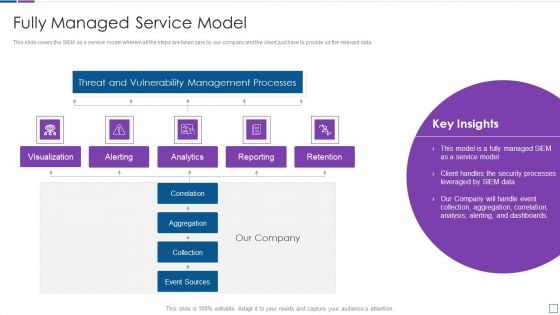
Real Time Assessment Of Security Threats Fully Managed Service Model Demonstration PDF
This slide covers the SIEM as a service model wherein all the steps are taken care by our company and the client just have to provide us the relevant data. Deliver an awe inspiring pitch with this creative real time assessment of security threats fully managed service model demonstration pdf bundle. Topics like threat and vulnerability management processes, reporting, retention, correlation, collection can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
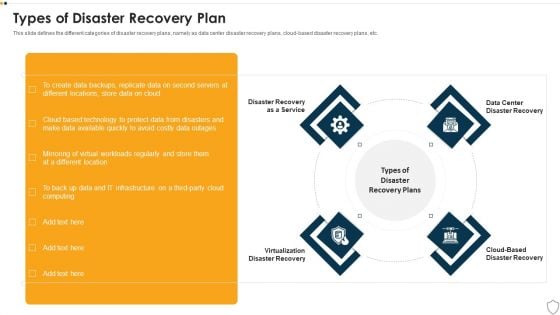
IT Security Types Of Disaster Recovery Plan Ppt Outline Show PDF
This slide defines the different categories of disaster recovery plans, namely as data center disaster recovery plans, cloud-based disaster recovery plans, etc. This is a it security types of disaster recovery plan ppt outline show pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like disaster recovery as a service, virtualization disaster recovery, cloud based disaster recovery, data center disaster recovery. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
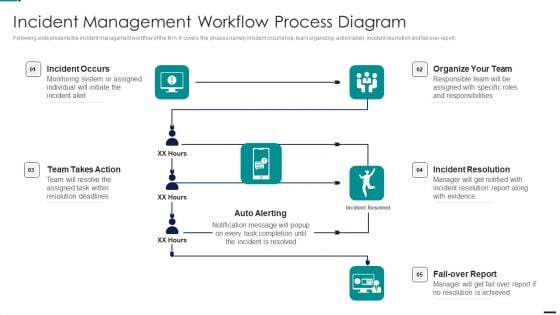
Risk Management Model For Data Security Incident Management Workflow Process Diagram Topics PDF
Following slide presents the incident management workflow of the firm. It covers five phases namely incident occurrence, team organizing, action taken, incident resolution and fail over report. Presenting Risk Management Model For Data Security Incident Management Workflow Process Diagram Topics PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Incident Occurs, Organize Team, Incident Resolution, Fail Over Report, Auto Alerting, Team Takes Action. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
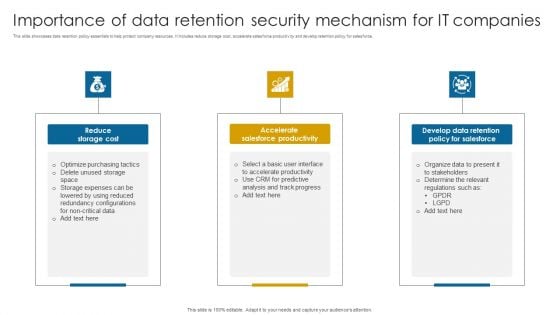
Importance Of Data Retention Security Mechanism For It Companies Professional PDF
This slide showcases data retention policy essentials to help protect company resources. It includes reduce storage cost, accelerate salesforce productivity and develop retention policy for salesforce.Presenting Importance Of Data Retention Security Mechanism For It Companies Professional PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Salesforce Productivity, Develop Data Retention, Determine Relevant. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Dispose Data And Equipment Properly IT Security IT Ppt Icon Clipart Images PDF
This slide depicts the importance of disposal of the data and equipment that is not in use anymore and restricts the employees who already left the organization. Presenting dispose data and equipment properly it security it ppt icon clipart images pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like dispose data and equipment properly. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
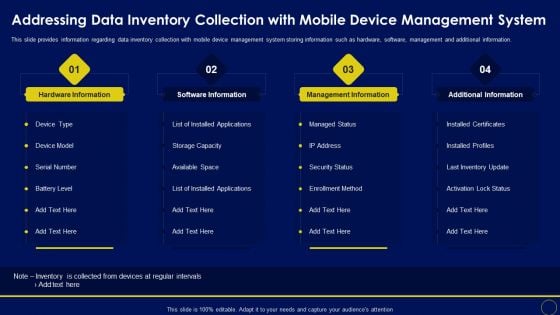
Addressing Data Inventory Collection With Mobile Business Mobile Device Security Management Structure PDF
This slide provides information regarding data inventory collection with mobile device management system storing information such as hardware, software, management and additional information. Make sure to capture your audiences attention in your business displays with our gratis customizable Addressing Data Inventory Collection With Mobile Business Mobile Device Security Management Structure PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
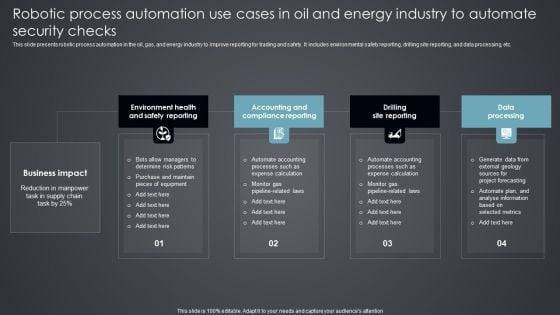
Robotic Process Automation Use Cases In Oil And Energy Industry To Automate Security Checks Introduction PDF
This slide presents robotic process automation in the oil, gas, and energy industry to improve reporting for trading and safety. It includes environmental safety reporting, drilling site reporting, and data processing, etc. Presenting Robotic Process Automation Use Cases In Oil And Energy Industry To Automate Security Checks Introduction PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Environment Health, Accounting Compliance Reporting, Drilling Site Reporting. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
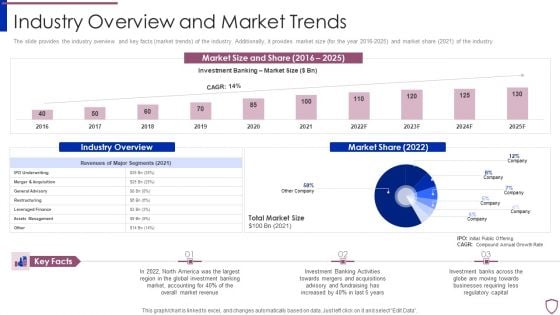
Financing Catalogue For Security Underwriting Agreement Industry Overview And Market Trends Introduction PDF
The slide provides the industry overview and key facts market trends of the industry. Additionally, it provides market size for the year 2016-2025 and market share 2021 of the industry. Deliver an awe inspiring pitch with this creative financing catalogue for security underwriting agreement industry overview and market trends introduction pdf bundle. Topics like assets management, leveraged finance, restructuring, general advisory, merger and acquisition can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
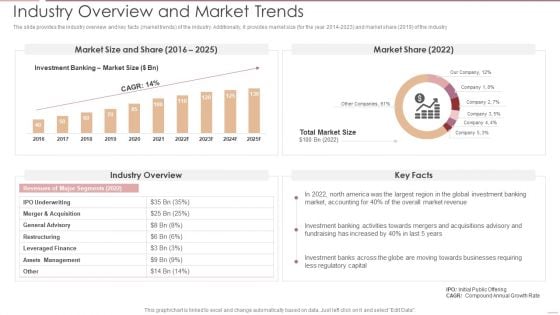
Investment Banking Security Underwriting Pitchbook Industry Overview And Market Trends Ideas PDF
The slide provides the industry overview and key facts market trends of the industry. Additionally, it provides market size for the year 2014 to 202 and market share 2019 of the industry.Deliver and pitch your topic in the best possible manner with this Investment Banking Security Underwriting Pitchbook Industry Overview And Market Trends Ideas PDF Use them to share invaluable insights on Assets Management, Leveraged Finance, Restructuring and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Online Settlement Revolution Payment Security And Fraud Management Solutions Analysis Ppt Slides File Formats PDF
From prevention to detection and resolution, Data Fraud Management solutions allow you to leverage proven technologies to create customized strategies that help limit losses while maintaining a high level of customer satisfaction. Presenting online settlement revolution payment security and fraud management solutions analysis ppt slides file formats pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like before the payment, on the payment page, after the payment. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Security Control Techniques For Real Estate Project Hazard Impact Analysis For Construction Site Icons PDF
The Security Control Techniques For Real Estate Project Hazard Impact Analysis For Construction Site Icons PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Kpis To Measure Information Security Risk Management Cybersecurity Risk Assessment Infographics PDF
This slide showcases KPIs that can help organization to measure the impact of cybersecurity risk management programme. It showcases estimated figures before and after implementation of plan. Slidegeeks has constructed Kpis To Measure Information Security Risk Management Cybersecurity Risk Assessment Infographics PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.
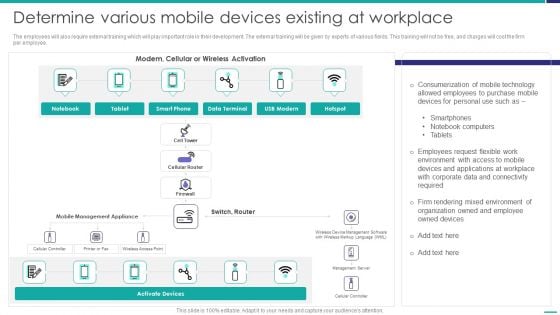
Determine Various Mobile Devices Existing At Workplace Mobile Device Security Management Guidelines PDF
The employees will also require external training which will play important role in their development. The external training will be given by experts of various fields. This training will not be free, and charges will cost the firm per employee. Deliver an awe inspiring pitch with this creative Determine Various Mobile Devices Existing At Workplace Mobile Device Security Management Guidelines PDF bundle. Topics like Corporate Data, Allowed Employees, Consumerization Technology can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Control Techniques For Real Estate Project Ppt PowerPoint Presentation Complete Deck With Slides
This Security Control Techniques For Real Estate Project Ppt PowerPoint Presentation Complete Deck With Slides is designed to help you retain your audiences attention. This content-ready PowerPoint Template enables you to take your audience on a journey and share information in a way that is easier to recall. It helps you highlight the crucial parts of your work so that the audience does not get saddled with information download. This Fifty one slide PPT Deck comes prepared with the graphs and charts you could need to showcase your information through visuals. You only need to enter your own data in them. Download this editable PowerPoint Theme and walk into that meeting with confidence.
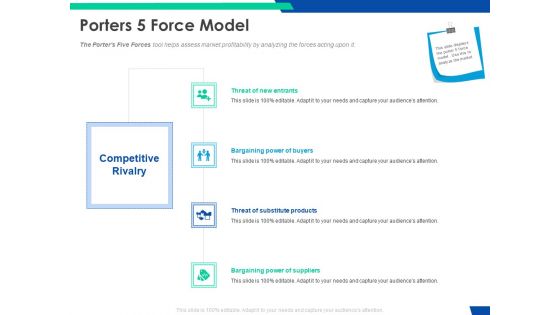
Cloud Based Email Security Market Report Porters 5 Force Model Ppt Inspiration Sample PDF
The Porters Five Forces tool helps assess market profitability by analyzing the forces acting upon it. This is a cloud based email security market report porters 5 force model ppt inspiration sample pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like threat of new entrants, bargaining power of buyers, threat of substitute products, bargaining power of suppliers. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

SDN Security Architecture Comparison Between Software Defined Networking And SD WAN Structure PDF
This slide depicts the comparison between software defined networking and an SD WAN, which is an internet traffic distribution system that uses SDN ideas to dynamically find the most efficient path for traffic to and from branch locations and data center sites across WANs. Make sure to capture your audiences attention in your business displays with our gratis customizable SDN Security Architecture Comparison Between Software Defined Networking And SD WAN Structure PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Security And Performance Digital Marketing Optimize Onpage SEO Include ALT Tags For Images Infographics PDF
This template covers search engine optimization guidelines for images. It also depicts that Alt Attributes must be added at backend of the images to assists search engine crawlers in indexing. This is a Security And Performance Digital Marketing Optimize Onpage SEO Include ALT Tags For Images Infographics PDF template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Context Descriptions, Search Engine, Assisting Indexing. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Online Payment Service Payment Security And Fraud Management Solutions End Structure PDF
From prevention to detection and resolution, Data Fraud Management solutions allow you to leverage proven technologies to create customized strategies that help limit losses while maintaining a high level of customer satisfaction. This is a online payment service payment security and fraud management solutions end structure pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like market basket analysis, optimization, geolocation analysis, customer velocity. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Data Safety Initiatives Information Security Program Values To Business Background PDF
Following slide displays the major program values to companys business. Values here are divided in two areas namely detection and response and attack surface management. This is a data safety initiatives information security program values to business background pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like detection and response, attack surface management, current network. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
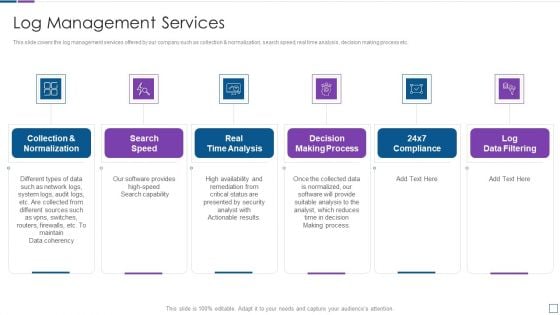
Real Time Assessment Of Security Threats Log Management Services Information PDF
This slide covers the log management services offered by our company such as collection and normalization, search speed, real time analysis, decision making process etc. Presenting real time assessment of security threats log management services information pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like collection and normalization, real time analysis, decision making process, log data filtering. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
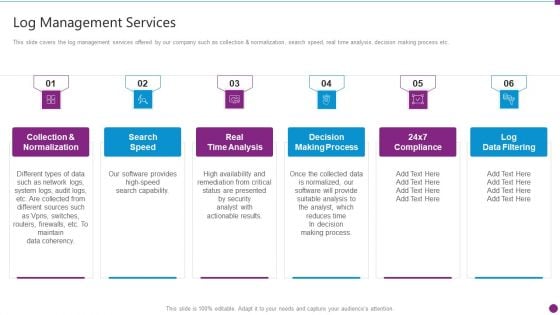
Security Information And Event Management Strategies For Financial Audit And Compliance Log Management Services Microsoft PDF
This slide covers the log management services offered by our company such as collection and normalization, search speed, real time analysis, decision making process etc. This is a security information and event management strategies for financial audit and compliance log management services microsoft pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like collection and normalization, search speed, real time analysis, decision making process, log data filtering. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
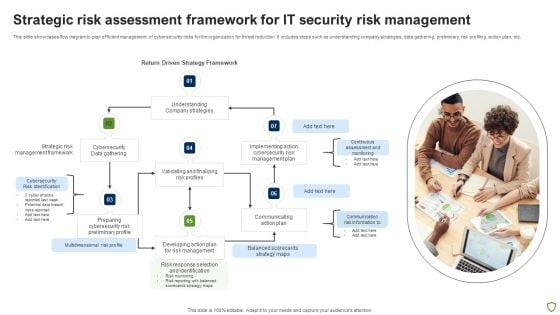
Strategic Risk Assessment Framework For IT Security Risk Management Ideas PDF
This slide showcases flow diagram to plan efficient management of cybersecurity risks for the organization for threat reduction. It includes steps such as understanding company strategies, data gathering, preliminary risk profiling, action plan, etc. Presenting Strategic Risk Assessment Framework For IT Security Risk Management Ideas PDF to dispense important information. This template comprises seven stages. It also presents valuable insights into the topics including Strategic Risk, Cybersecurity, Management Framework, Data Gathering. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Hurdles In Business Data Security In Trade Secret Ppt PowerPoint Presentation Pictures Master Slide PDF
Showcasing this set of slides titled hurdles in business data security in trade secret ppt powerpoint presentation pictures master slide pdf. The topics addressed in these templates are once trade secret is made public, it can be accessed by anyone, difficult to enforce than patent, level of protection granted to trade is generally considered weak and is different from country country. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Biometric Technology For Enhancing Mobile Banking Security Ppt Model Graphics PDF
This slide shows information which can be used by organizations to get insights about biometric technology growth in mobile banking. It includes details about process and types of biometric data. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Biometric Technology For Enhancing Mobile Banking Security Ppt Model Graphics PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Info Security Prepare Data Backup For Sensitive Information Ppt PowerPoint Presentation File Rules PDF
This slide represents the preparation of data backup for sensitive information and how data backup should be created and stored within an organization. This is a info security prepare data backup for sensitive information ppt powerpoint presentation file rules pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like data backup, provide cloud, prevent data, natural disasters. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
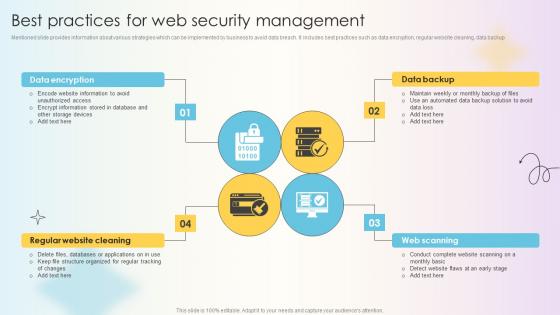
Managing Technical And Non Technical Best Practices For Web Security Management
Mentioned slide provides information about various strategies which can be implemented by business to avoid data breach. It includes best practices such as data encryption, regular website cleaning, data backup Present like a pro with Managing Technical And Non Technical Best Practices For Web Security Management. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. Mentioned slide provides information about various strategies which can be implemented by business to avoid data breach. It includes best practices such as data encryption, regular website cleaning, data backup
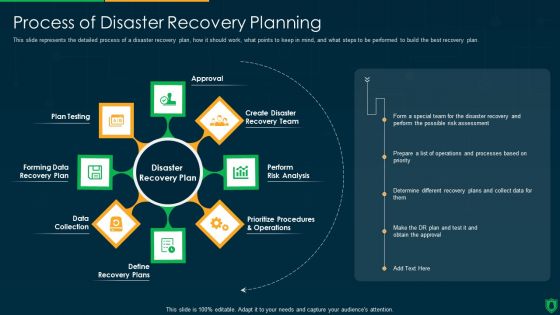
Info Security Process Of Disaster Recovery Planning Ppt PowerPoint Presentation File Summary PDF
This slide represents the detailed process of a disaster recovery plan, how it should work, what points to keep in mind, and what steps to be performed to build the best recovery plan. This is a info security process of disaster recovery planning ppt powerpoint presentation file summary pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like approval, perform risk analysis, define recovery plans, data collection, forming data recovery plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
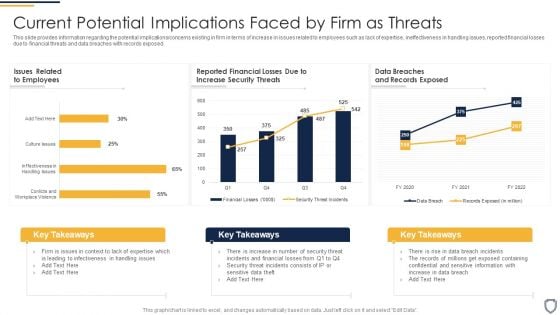
Corporate Security And Risk Management Current Potential Implications Faced By Firm As Threats Inspiration PDF
This slide provides information regarding the potential implications or concerns existing in firm in terms of increase in issues related to employees such as lack of expertise, ineffectiveness in handling issues, reported financial losses due to financial threats and data breaches with records exposed. Deliver an awe inspiring pitch with this creative corporate security and risk management current potential implications faced by firm as threats inspiration pdf bundle. Topics like current potential implications faced by firm as threats can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Process Of Disaster Recovery Planning IT Security IT Ppt Outline Example Introduction PDF
This slide represents the detailed process of a disaster recovery plan, how it should work, what points to keep in mind, and what steps to be performed to build the best recovery plan. This is a process of disaster recovery planning it security it ppt outline example introduction pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like data collection, plan testing, approval, perform risk analysis, prioritize procedures and operations. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
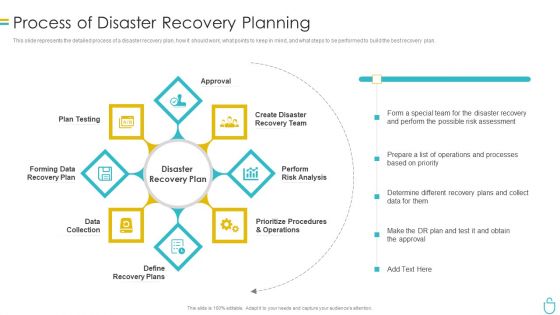
Information Security Process Of Disaster Recovery Planning Ppt Portfolio Backgrounds PDF
This slide represents the detailed process of a disaster recovery plan, how it should work, what points to keep in mind, and what steps to be performed to build the best recovery plan. Presenting information security process of disaster recovery planning ppt portfolio backgrounds pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like recovery team, risk analysis, prioritize procedures, recovery plan, data collection. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
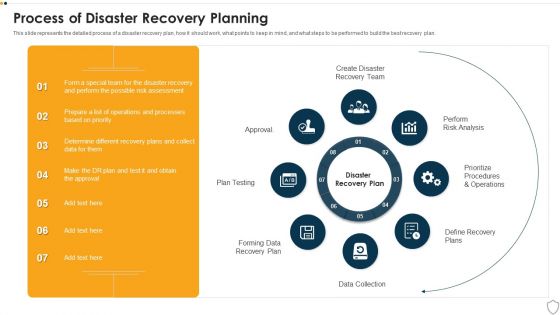
IT Security Process Of Disaster Recovery Planning Ppt Portfolio Microsoft PDF
This slide represents the detailed process of a disaster recovery plan, how it should work, what points to keep in mind, and what steps to be performed to build the best recovery plan. Presenting it security process of disaster recovery planning ppt portfolio microsoft pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like plan testing, perform risk analysis, data collection, prioritize procedures and operations. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
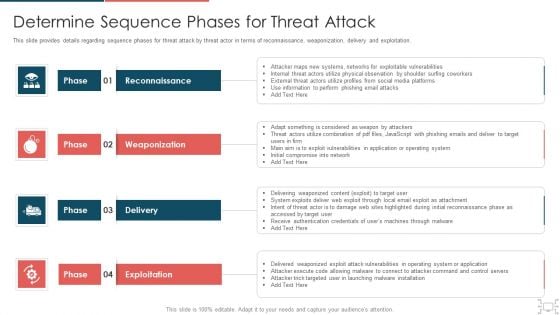
cyber security administration in organization determine sequence phases for threat attack infographics pdf
This slide provides details regarding sequence phases for threat attack by threat actor in terms of reconnaissance, weaponization, delivery and exploitation. This is a cyber security administration in organization determine sequence phases for threat attack infographics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like internal, threat, perform, phishing, combination . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security And Performance Digital Marketing Use Top Of Funnel Content In Cold Calling Campaigns Template PDF
This template covers the cold calling email campaign strategy. It also depicts that TOFU should include introductory content focusing on brand, MOFU should include useful information about brand and, BOFU should include social proofs.Presenting Security And Performance Digital Marketing Use Top Of Funnel Content In Cold Calling Campaigns Template PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Sample Reports, Testimonials, Landing Pages. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Risk Based Procedures To IT Security Communication Plan For Cyber Breaches Structure PDF
Mentioned slide portrays communication plan that company will use for effectively managing cyber breaches. Sections covered here are what to communicate, description, delivery method, frequency and responsible. Presenting Risk Based Procedures To IT Security Communication Plan For Cyber Breaches Structure PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Sprint Report, Delivery Method, Frequency Responsible. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
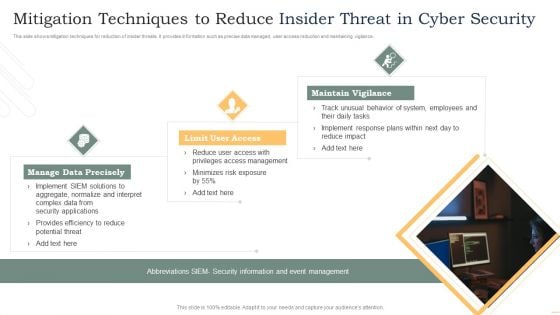
Mitigation Techniques To Reduce Insider Threat In Cyber Security Rules PDF
This slide shows mitigation techniques for reduction of insider threats. It provides information such as precise data managed, user access reduction and maintaining vigilance. Presenting Mitigation Techniques To Reduce Insider Threat In Cyber Security Rules PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Manage Data Precisely, Limit User Access, Maintain Vigilance. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
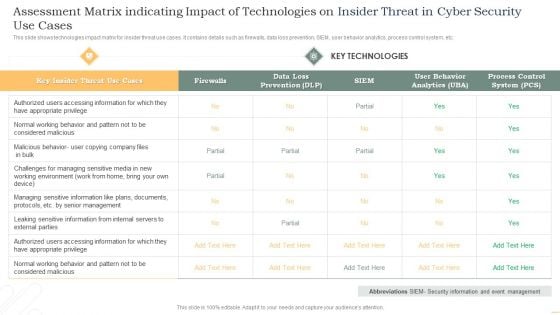
Assessment Matrix Indicating Impact Of Technologies On Insider Threat In Cyber Security Use Cases Themes PDF
This slide shows technologies impact matrix for insider threat use cases. It contains details such as firewalls, data loss prevention, SIEM, user behavior analytics, process control system, etc. Showcasing this set of slides titled Assessment Matrix Indicating Impact Of Technologies On Insider Threat In Cyber Security Use Cases Themes PDF. The topics addressed in these templates are Key Insider, Threat, Use Cases, Key Technologies. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
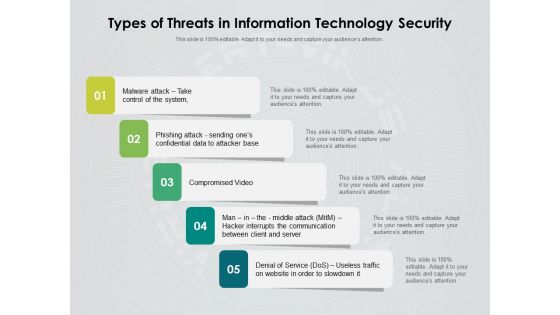
Types Of Threats In Information Technology Security Ppt PowerPoint Presentation Inspiration Rules PDF
Persuade your audience using this types of threats in information technology security ppt powerpoint presentation inspiration rules pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including malware attack take control of the system, phishing attack sending ones confidential data to attacker base, compromised video, man in the middle attack hacker interrupts the communication between client and server, denial of service dos, useless traffic on website in order to slowdown it. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
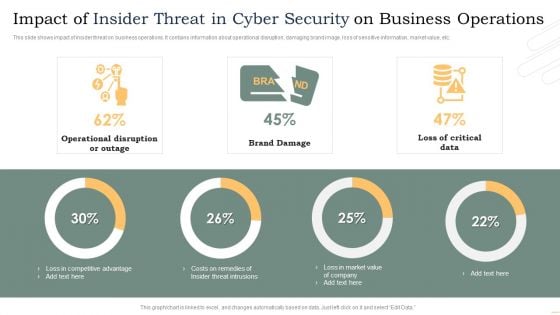
Impact Of Insider Threat In Cyber Security On Business Operations Microsoft PDF
This slide shows impact of insider threat on business operations. It contains information about operational disruption, damaging brand image, loss of sensitive information, market value, etc. Pitch your topic with ease and precision using this Impact Of Insider Threat In Cyber Security On Business Operations Microsoft PDF. This layout presents information on Operational Disruption Or Outage, Brand Damage, Loss Critical Data. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
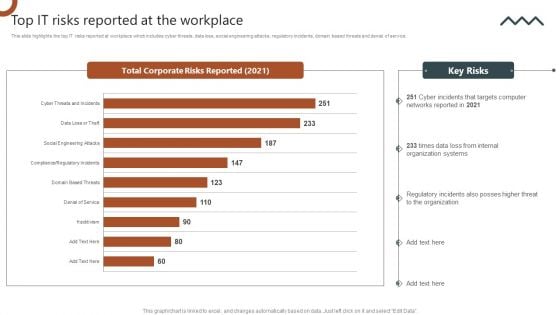
Organizations Risk Management And IT Security Top IT Risks Reported At The Workplace Brochure PDF
This slide highlights the top IT risks reported at workplace which includes cyber threats, data loss, social engineering attacks, regulatory incidents, domain based threats and denial of service. Slidegeeks has constructed Organizations Risk Management And IT Security Top IT Risks Reported At The Workplace Brochure PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.


 Continue with Email
Continue with Email

 Home
Home


































