Security Gap Assessment
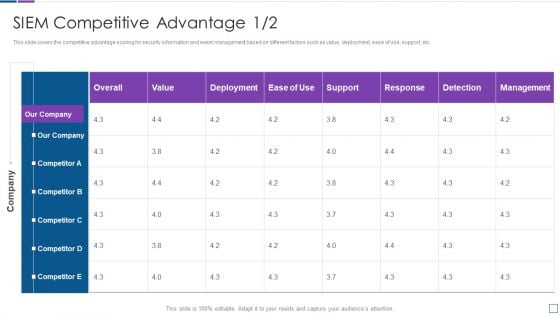
Competitive Advantage Real Time Assessment Of Security Threats SIEM Pictures PDF
This slide covers the competitive advantage scoring for security information and event management based on different factors such as value, deployment, ease of use, support, etc. Deliver an awe inspiring pitch with this creative competitive advantage real time assessment of security threats siem pictures pdf bundle. Topics like siem competitive advantage can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
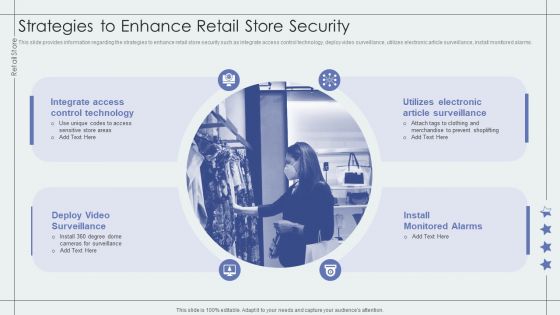
Strategies To Enhance Retail Store Security Retail Outlet Performance Assessment Professional PDF
This slide provides information regarding the strategies to enhance retail store security such as integrate access control technology, deploy video surveillance, utilizes electronic article surveillance, install monitored alarms.Deliver an awe inspiring pitch with this creative Strategies To Enhance Retail Store Security Retail Outlet Performance Assessment Professional PDF bundle. Topics like Integrate Access, Control Technology, Prevent Shoplifting can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Identifying Employees For Information Security Training Programme Cybersecurity Risk Assessment Pictures PDF
This slide showcases plan that can help organization to conduct training for employees for information security risk management. It will enable employees to monitor risks and resolve them in timely manner. There are so many reasons you need a Identifying Employees For Information Security Training Programme Cybersecurity Risk Assessment Pictures PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Security Management Plan Steps In Detail Risk Assessment And Analysis Template PDF
This is a security management plan steps in detail risk assessment and analysis template pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like potential consequence, security risks or liabilities, management to educate You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
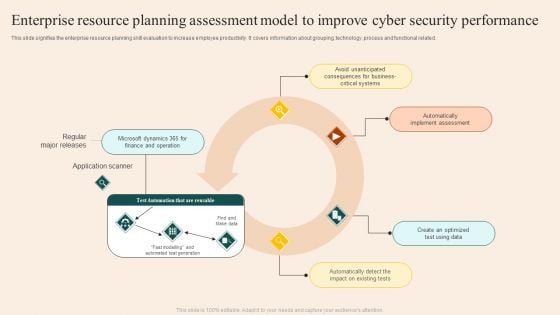
Enterprise Resource Planning Assessment Model To Improve Cyber Security Performance Guidelines PDF
This slide signifies the enterprise resource planning skill evaluation to increase employee productivity. It covers information about grouping, technology ,process and functional related. Showcasing this set of slides titled Enterprise Resource Planning Assessment Model To Improve Cyber Security Performance Guidelines PDF. The topics addressed in these templates are Regular Major Releases, Application Scanner, Implement Assessment. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
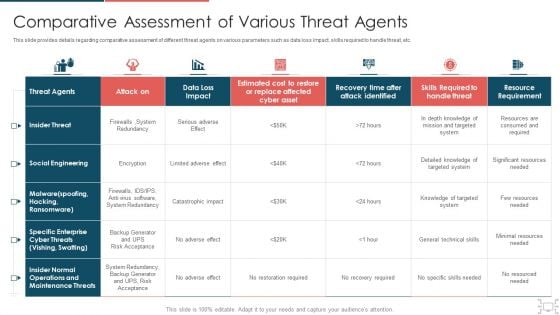
Cyber Security Administration In Organization Comparative Assessment Of Various Threat Agents Infographics PDF
This slide provides details regarding comparative assessment of different threat agents on various parameters such as data loss impact, skills required to handle threat, etc. Deliver and pitch your topic in the best possible manner with this cyber security administration in organization comparative assessment of various threat agents infographics pdf. Use them to share invaluable insights on social engineering, operations, maintenance, redundancy and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
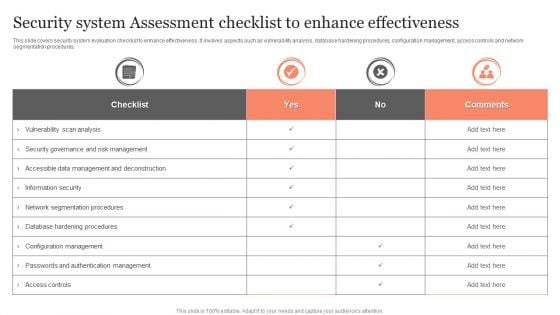
Security System Assessment Checklist To Enhance Effectiveness Ppt Visual Aids PDF
This slide covers security system evaluation checklist to enhance effectiveness. It involves aspects such as vulnerability analysis, database hardening procedures, configuration management, access controls and network segmentation procedures. Showcasing this set of slides titled Security System Assessment Checklist To Enhance Effectiveness Ppt Visual Aids PDF. The topics addressed in these templates are Checklist, Vulnerability Scan Analysis, Information Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
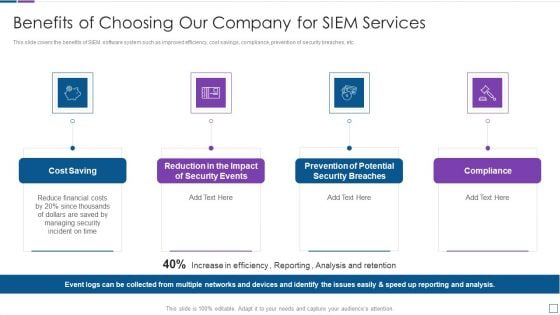
Real Time Assessment Of Security Threats Benefits Of Choosing Our Company For SIEM Services Introduction PDF
This slide covers the benefits of SIEM software system such as improved efficiency, cost savings, compliance, prevention of security breaches, etc. This is a real time assessment of security threats benefits of choosing our company for siem services introduction pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cost saving, security events, compliance. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
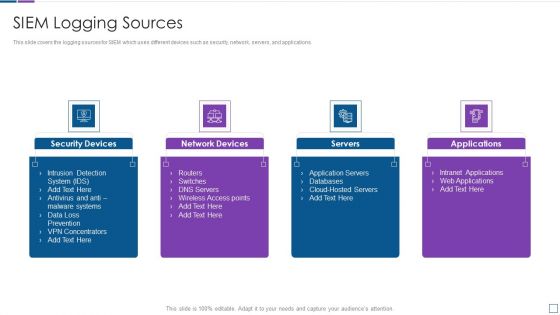
Real Time Assessment Of Security Threats SIEM Logging Sources Infographics PDF
This slide covers the logging sources for SIEM which uses different devices such as security, network, servers, and applications. This is a real time assessment of security threats siem logging sources infographics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security devices, network devices, servers, applications. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
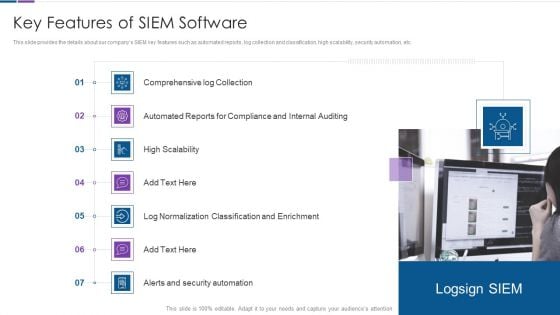
Real Time Assessment Of Security Threats Key Features Of SIEM Software Inspiration PDF
This slide provides the details about our companys SIEM key features such as automated reports, log collection and classification, high scalability, security automation, etc. Presenting real time assessment of security threats key features of siem software inspiration pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like compliance and internal auditing, high scalability, classification and enrichment, security automation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
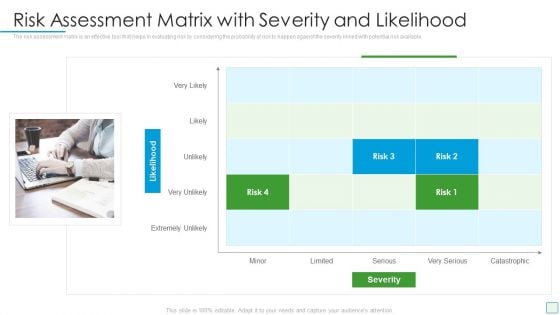
Developing Firm Security Strategy Plan Risk Assessment Matrix With Severity And Likelihood Portrait PDF
The risk assessment matrix is an effective tool that helps in evaluating risk by considering the probability of risk to happen against the severity linked with potential risk available. This is a developing firm security strategy plan risk assessment matrix with severity and likelihood portrait pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like risk assessment matrix with severity and likelihood. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
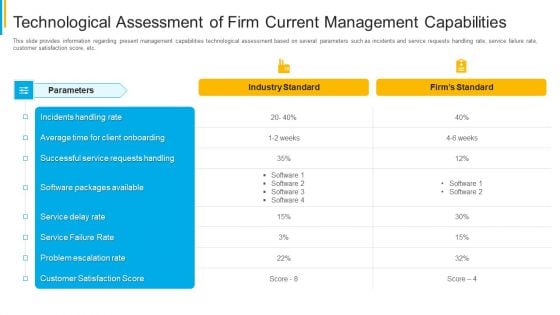
Project Security Administration IT Technological Assessment Of Firm Current Management Capabilities Professional PDF
This slide provides information regarding present management capabilities technological assessment based on several parameters such as incidents and service requests handling rate, service failure rate, customer satisfaction score, etc. Deliver and pitch your topic in the best possible manner with this project security administration it technological assessment of firm current management capabilities professional pdf. Use them to share invaluable insights on technological assessment of firm current management capabilities and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
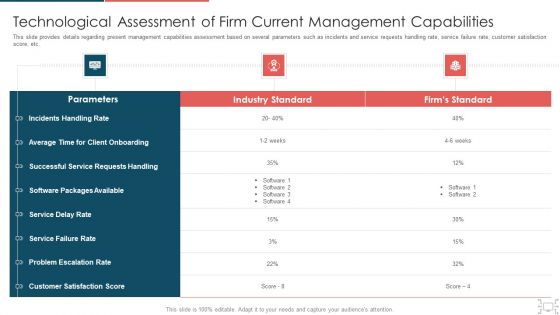
Cyber Security Administration In Organization Technological Assessment Of Firm Current Management Elements PDF
This slide provides details regarding present management capabilities assessment based on several parameters such as incidents and service requests handling rate, service failure rate, customer satisfaction score, etc. Deliver and pitch your topic in the best possible manner with this cyber security administration in organization technological assessment of firm current management elements pdf. Use them to share invaluable insights on technological assessment of firm current management capabilities and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
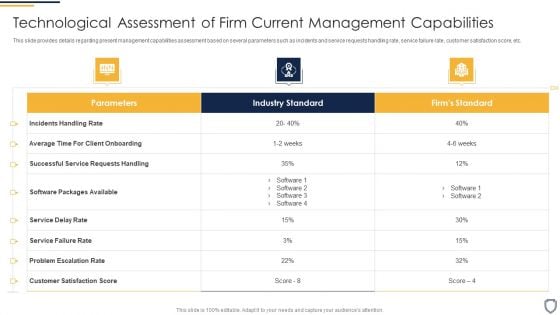
Corporate Security And Risk Management Technological Assessment Of Firm Current Designs PDF
This slide provides details regarding present management capabilities assessment based on several parameters such as incidents and service requests handling rate, service failure rate, customer satisfaction score, etc. Deliver and pitch your topic in the best possible manner with this corporate security and risk management technological assessment of firm current designs pdf. Use them to share invaluable insights on technological assessment of firm current management capabilities and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
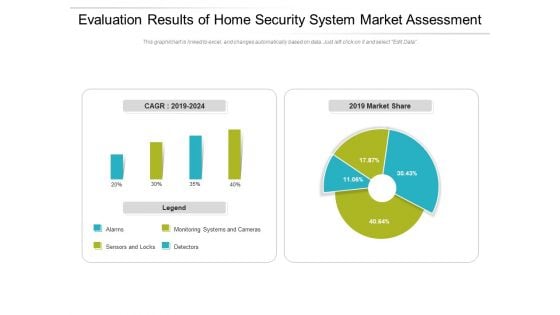
Evaluation Results Of Home Security System Market Assessment Ppt PowerPoint Presentation Gallery Deck PDF
Pitch your topic with ease and precision using this evaluation results of home security system market assessment ppt powerpoint presentation gallery deck pdf. This layout presents information on monitoring, market, detectors. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Comparative Assessment Of Security Problem Management Tools Ppt Model Influencers PDF
Pitch your topic with ease and precision using this Comparative Assessment Of Security Problem Management Tools Ppt Model Influencers PDF. This layout presents information on Customized Workflows, Threat Intelligence Integration, Real Time Alerts. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Computer Security Incident Handling Business Impact Assessment Ppt Infographics Rules PDF
Presenting this set of slides with name computer security incident handling business impact assessment ppt infographics rules pdf. The topics discussed in these slides are strengths, weaknesses, loss impact. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security Implementation Framework Business Impact Assessment Ppt PowerPoint Presentation Layouts Visuals PDF
Presenting this set of slides with name cyber security implementation framework business impact assessment ppt powerpoint presentation layouts visuals pdf. This is a three stage process. The stages in this process are department or function, executive, employees, business, strengths, weaknesses, loss impact. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Internet Security Risk Assessment Report For Business Ppt PowerPoint Presentation Gallery Graphics Example PDF
Pitch your topic with ease and precision using this internet security risk assessment report for business ppt powerpoint presentation gallery graphics example pdf. This layout presents information on process, unit, risk level. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
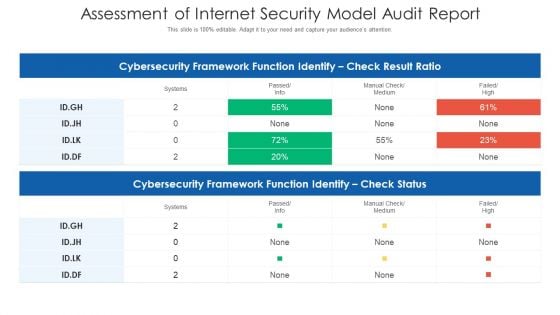
Assessment Of Internet Security Model Audit Report Ppt PowerPoint Presentation Portfolio Information PDF
Showcasing this set of slides titled assessment of internet security model audit report ppt powerpoint presentation portfolio information pdf. The topics addressed in these templates are cybersecurity framework function identify, manual check or medium, failed or high. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
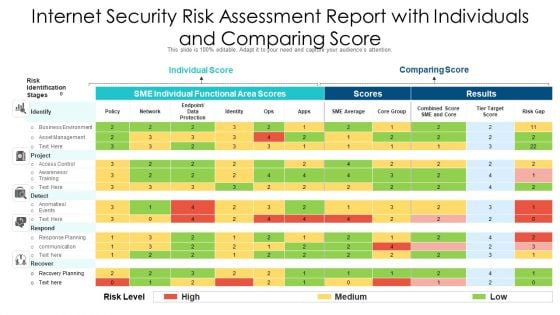
Internet Security Risk Assessment Report With Individuals And Comparing Score Ppt PowerPoint Presentation File Good PDF
Showcasing this set of slides titled internet security risk assessment report with individuals and comparing score ppt powerpoint presentation file good pdf. The topics addressed in these templates are individual score, comparing score, identify. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
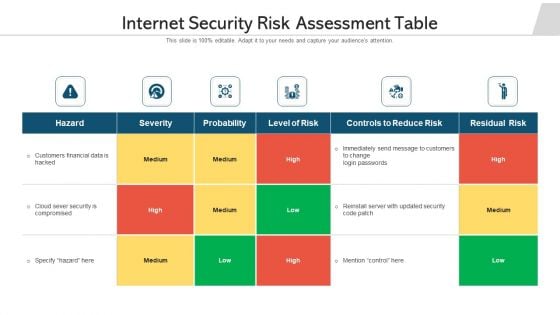
Internet Security Risk Assessment Table Ppt PowerPoint Presentation Gallery Design Inspiration PDF
Showcasing this set of slides titled internet security risk assessment table ppt powerpoint presentation gallery design inspiration pdf. The topics addressed in these templates are probability, level of risk, residual risk. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Internet Security Risk Assessment Report With Vulnerability And Impact Ppt PowerPoint Presentation Icon Backgrounds PDF
Pitch your topic with ease and precision using this internet security risk assessment report with vulnerability and impact ppt powerpoint presentation icon backgrounds pdf. This layout presents information on vulnerability, asset, impact. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
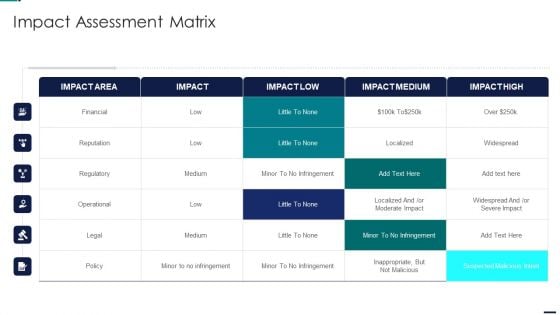
Risk Management Model For Data Security Impact Assessment Matrix Formats PDF
Deliver an awe inspiring pitch with this creative Risk Management Model For Data Security Impact Assessment Matrix Formats PDF bundle. Topics like Financial, Reputation, Regulatory, Operational can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Security For Your Organization Risk Assessment Matrix Ppt Ideas PDF
Presenting this set of slides with name cyber security for your organization risk assessment matrix ppt ideas pdf. This is a one stage process. The stages in this process are insignificant, minor, severity, risk, catastrophic. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Computer Security Incident Handling Risk Assessment Matrix Ppt Show Design Ideas PDF
Presenting this set of slides with name computer security incident handling risk assessment matrix ppt show design ideas pdf. This is a four stage process. The stages in this process are minor, significant, serious, catastrophic, insignificant. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Strategies To Mitigate Cyber Security Risks Risk Assessment Matrix Ppt Visuals PDF
Presenting this set of slides with name strategies to mitigate cyber security risks risk assessment matrix ppt visuals pdf. This is a four stage process. The stages in this process are insignificant, minor significant, serious, catastrophic. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
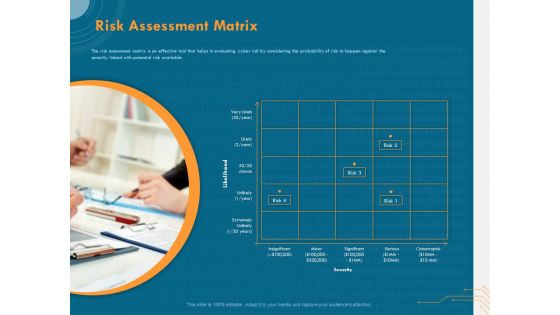
Cyber Security Implementation Framework Risk Assessment Matrix Ppt PowerPoint Presentation Visual Aids Backgrounds PDF
Presenting this set of slides with name cyber security implementation framework risk assessment matrix ppt powerpoint presentation visual aids backgrounds pdf. This is a one stage process. The stages in this process are insignificant, minor, catastrophic, serious. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
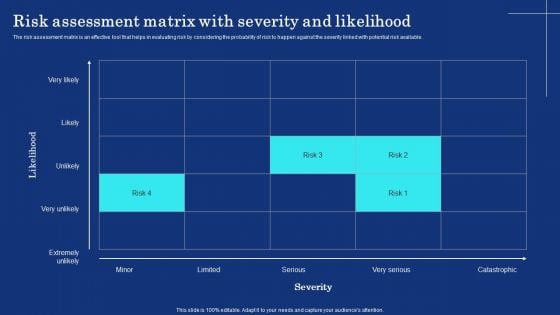
Organizational Assets Security Management Strategy Risk Assessment Matrix With Severity And Likelihood Brochure PDF
The risk assessment matrix is an effective tool that helps in evaluating risk by considering the probability of risk to happen against the severity linked with potential risk available. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download Organizational Assets Security Management Strategy Risk Assessment Matrix With Severity And Likelihood Brochure PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the Organizational Assets Security Management Strategy Risk Assessment Matrix With Severity And Likelihood Brochure PDF.
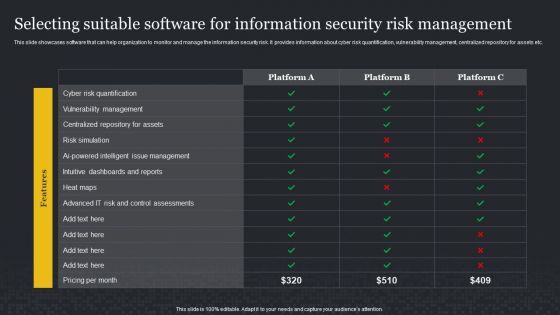
Selecting Suitable Software For Information Security Risk Management Cybersecurity Risk Assessment Infographics PDF
This slide showcases software that can help organization to monitor and manage the information security risk. It provides information about cyber risk quantification, vulnerability management, centralized repository for assets etc. If you are looking for a format to display your unique thoughts, then the professionally designed Selecting Suitable Software For Information Security Risk Management Cybersecurity Risk Assessment Infographics PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Selecting Suitable Software For Information Security Risk Management Cybersecurity Risk Assessment Infographics PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Timeline For Information Security Risk Management Training Cybersecurity Risk Assessment Pictures PDF
This slide showcases timeline that can help organization to conduct training for information security risk management programme. It also showcases weekly and step progress. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Timeline For Information Security Risk Management Training Cybersecurity Risk Assessment Pictures PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Timeline For Information Security Risk Management Training Cybersecurity Risk Assessment Pictures PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.

Estimated Impact Of Information Security Risk Management Plan Cybersecurity Risk Assessment Rules PDF
This slide showcases capabilities of organization regarding information and data security after risk management plan. Its key component are risk management functions, required standard rating and actual standard rating. Explore a selection of the finest Estimated Impact Of Information Security Risk Management Plan Cybersecurity Risk Assessment Rules PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Estimated Impact Of Information Security Risk Management Plan Cybersecurity Risk Assessment Rules PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
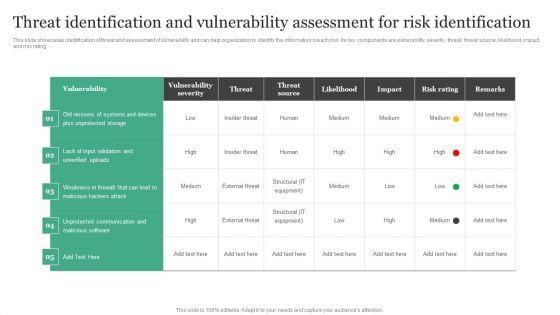
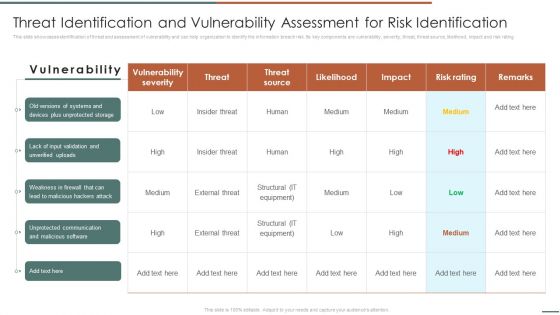
Threat Identification And Vulnerability Assessment For Risk Identification Information Security Risk Administration Slides PDF
This slide showcases identification of threat and assessment of vulnerability and can help organization to identify the information breach risk. Its key components are vulnerability, severity, threat, threat source, likelihood, impact and risk rating.Get a simple yet stunning designed Threat Identification And Vulnerability Assessment For Risk Identification Information Security Risk Administration Slides PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Threat Identification And Vulnerability Assessment For Risk Identification Information Security Risk Administration Slides PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
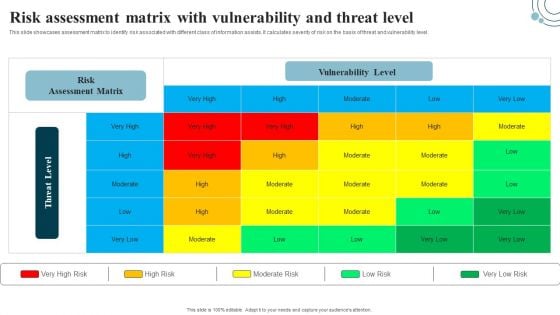
Developing IT Security Strategy Risk Assessment Matrix With Vulnerability And Threat Level Download PDF
This slide showcases assessment matrix to identify risk associated with different class of information assists. It calculates severity of risk on the basis of threat and vulnerability level. This Developing IT Security Strategy Risk Assessment Matrix With Vulnerability And Threat Level Download PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Developing IT Security Strategy Risk Assessment Matrix With Vulnerability And Threat Level Download PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today.
Key Benefits Of Cloud Security Assessment Ppt PowerPoint Presentation Icon Infographics PDF
The slide exhibits various advantages of the cloud audit in assessing and improvising the overall security controls. Various benefits included are ensure compliance, understand the system, evaluate the effectiveness and overall improvement. Presenting Key Benefits Of Cloud Security Assessment Ppt PowerPoint Presentation Icon Infographics PDF to dispense important information. This template comprises FOUR stages. It also presents valuable insights into the topics including Ensure Compliance, Evaluate The Effectiveness, Understand The System, Overall Improvement. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
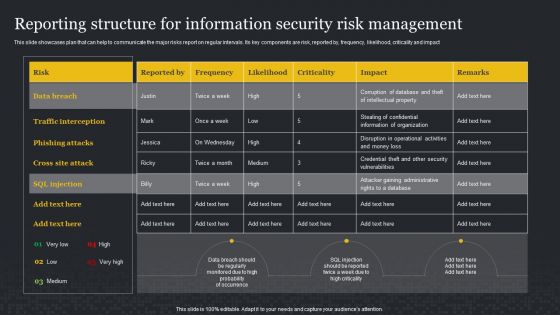
Reporting Structure For Information Security Risk Management Cybersecurity Risk Assessment Formats PDF
This slide showcases plan that can help to communicate the major risks report on regular intervals. Its key components are risk, reported by, frequency, likelihood, criticality and impact. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Reporting Structure For Information Security Risk Management Cybersecurity Risk Assessment Formats PDF can be your best option for delivering a presentation. Represent everything in detail using Reporting Structure For Information Security Risk Management Cybersecurity Risk Assessment Formats PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
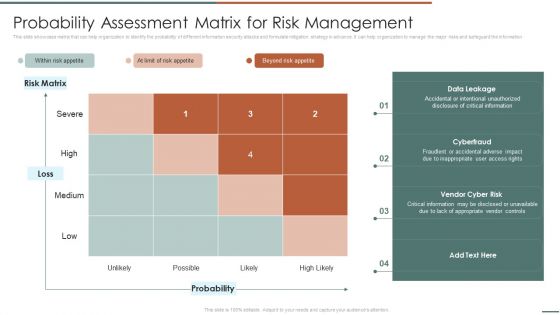
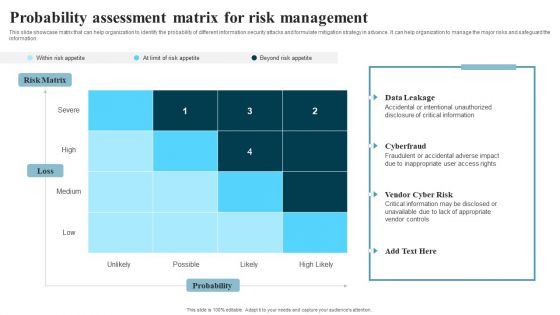
Information Security Risk Evaluation Probability Assessment Matrix For Risk Management Demonstration PDF
This slide showcase matrix that can help organization to identify the probability of different information security attacks and formulate mitigation strategy in advance. It can help organization to manage the major risks and safeguard the information.Deliver and pitch your topic in the best possible manner with this Information Security Risk Evaluation Probability Assessment Matrix For Risk Management Demonstration PDF. Use them to share invaluable insights on Accidental Intentional, Unauthorized, Critical Information and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cloud Security Assessment Phase 3 Respond To Cloud Protection Issues Topics PDF
This slide represents phase 3 of cloud security, such as respond to cloud protection issues. It includes an advanced authentication process, manages cloud access standards when new services come up, and eliminates malware from cloud services.Deliver and pitch your topic in the best possible manner with this Cloud Security Assessment Phase 3 Respond To Cloud Protection Issues Topics PDF Use them to share invaluable insights on Authentication Process, Access Standards, Eliminate Malware and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

E Commerce Business Cyber Security Assessment Threats And Solutions Guidelines PDF
This slide shows potential threats along with prevention for online business websites that could damage the business and also lose trust of online customers. the certain threats includes direct site attacks, password assault, social engineering and malwares. Showcasing this set of slides titled E Commerce Business Cyber Security Assessment Threats And Solutions Guidelines PDF. The topics addressed in these templates are Business Security Risks, Threat Type, Solutions. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
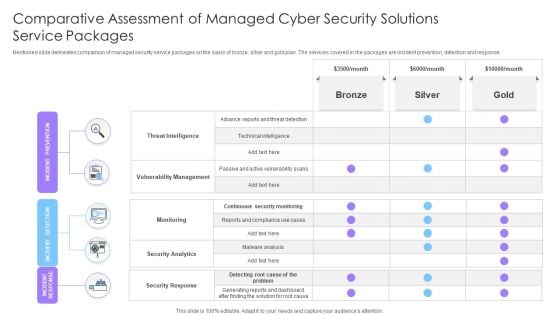
Comparative Assessment Of Managed Cyber Security Solutions Service Packages Ppt Gallery Inspiration PDF
Mentioned slide delineates comparison of managed security service packages on the basis of bronze, silver and gold plan. The services covered in the packages are incident prevention, detection and response. Showcasing this set of slides titled Comparative Assessment Of Managed Cyber Security Solutions Service Packages Ppt Gallery Inspiration PDF. The topics addressed in these templates are Threat Intelligence, Vulnerability Management, Monitoring. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Information Security Risk Evaluation Threat Identification And Vulnerability Assessment For Risk Identification Graphics PDF
This slide showcases identification of threat and assessment of vulnerability and can help organization to identify the information breach risk. Its key components are vulnerability, severity, threat, threat source, likelihood, impact and risk rating.Deliver and pitch your topic in the best possible manner with this Information Security Risk Evaluation Threat Identification And Vulnerability Assessment For Risk Identification Graphics PDF. Use them to share invaluable insights on Vulnerability Severity, Unprotected Storage, Unprotected Communication and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Real Time Assessment Of Security Threats Next Evolution Of SIEM Software Sample PDF
This slide focuses on the upcoming evolution of SIEM software which covers SIEM foundation, threat intelligence, user entity and behavior analytics, network traffic analysis, endpoint monitoring, and SOAR. This is a real time assessment of security threats next evolution of siem software sample pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like network traffic analysis, endpoint monitoring, threat intelligence, siem foundation, security orchestration. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
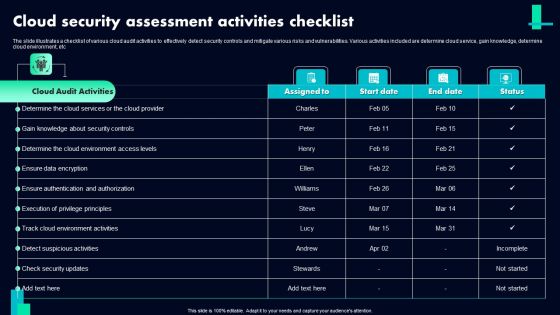
Cloud Security Assessment Activities Checklist Ppt PowerPoint Presentation Gallery Model PDF
The slide illustrates a checklist of various cloud audit activities to effectively detect security controls and mitigate various risks and vulnerabilities. Various activities included are determine cloud service, gain knowledge, determine cloud environment, etc. Showcasing this set of slides titled Cloud Security Assessment Activities Checklist Ppt PowerPoint Presentation Gallery Model PDF. The topics addressed in these templates are Cloud Audit Activities, Ensure Data Encryption, Detect Suspicious Activities. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Developing IT Security Strategy Probability Assessment Matrix For Risk Management Formats PDF
This slide showcase matrix that can help organization to identify the probability of different information security attacks and formulate mitigation strategy in advance. It can help organization to manage the major risks and safeguard the information. Make sure to capture your audiences attention in your business displays with our gratis customizable Developing IT Security Strategy Probability Assessment Matrix For Risk Management Formats PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Current Information And Data Security Capabilities Of Firm Cybersecurity Risk Assessment Infographics PDF
This slide showcases current capabilities of organization regarding information and data security. Its key component are risk management functions, required standard rating and actual standard rating. The Current Information And Data Security Capabilities Of Firm Cybersecurity Risk Assessment Infographics PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
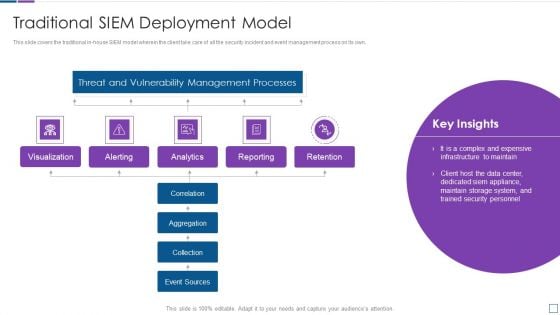
Real Time Assessment Of Security Threats Traditional SIEM Deployment Model Background PDF
This slide covers the traditional in house SIEM model wherein the client take care of all the security incident and event management process on its own. Deliver and pitch your topic in the best possible manner with this real time assessment of security threats traditional siem deployment model background pdf. Use them to share invaluable insights on threat and vulnerability management processes, visualization, retention, analytics and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Real Time Assessment Of Security Threats Cloud SIEM Model Icons PDF
This slide covers the cloud SIEM and self managed model wherein the client take care of mostly all the security incident and event management process on its own except aggregation and collection. Deliver and pitch your topic in the best possible manner with this real time assessment of security threats cloud siem model icons pdf. Use them to share invaluable insights on threat and vulnerability management processes, aggregation, collection, correlation and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
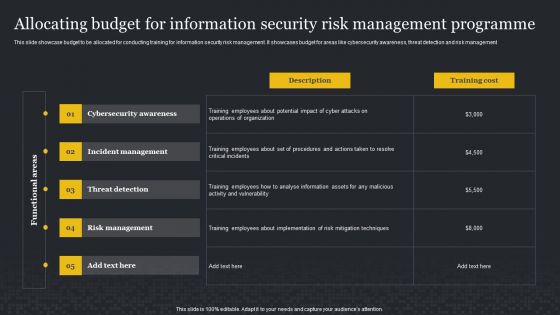
Allocating Budget For Information Security Risk Management Programme Cybersecurity Risk Assessment Brochure PDF
This slide showcase budget to be allocated for conducting training for information security risk management. It showcases budget for areas like cybersecurity awareness, threat detection and risk management. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Allocating Budget For Information Security Risk Management Programme Cybersecurity Risk Assessment Brochure PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Budget For Information Security Risk Management Cybersecurity Risk Assessment Demonstration PDF
This slide showcases budget that can should be allocated for different information security risk management activities. It provides information about employees training, software implementation, risk monitoring and data backup. Want to ace your presentation in front of a live audience Our Budget For Information Security Risk Management Cybersecurity Risk Assessment Demonstration PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.
Prevention Of Information Comparative Assessment Of Security Awareness Online Courses Icons PDF
The purpose of this slide is to showcase comparison of various advance cyber security training courses. The comparison is drawn on the basis of course description, level, duration, no. of companies enrolled for this course etc. Want to ace your presentation in front of a live audience Our Prevention Of Information Comparative Assessment Of Security Awareness Online Courses Icons PDF can help you do that by engaging all the users towards you.. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.

Implementing Cybersecurity Awareness Program To Prevent Attacks Comparative Assessment Of Security Graphics PDF
The purpose of this slide is to showcase comparison of various advance cyber security training courses. The comparison is drawn on the basis of course description, level, duration, no. of companies enrolled for this course etc. There are so many reasons you need a Implementing Cybersecurity Awareness Program To Prevent Attacks Comparative Assessment Of Security Graphics PDF. The first reason is you cannot spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
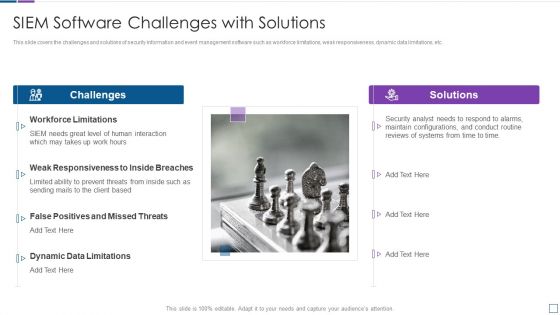
Real Time Assessment Of Security Threats SIEM Software Challenges With Solutions Inspiration PDF
This slide covers the challenges and solutions of security information and event management software such as workforce limitations, weak responsiveness, dynamic data limitations, etc. This is a real time assessment of security threats siem software challenges with solutions inspiration pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like challenges, solutions, workforce limitations, false positives and missed threats. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
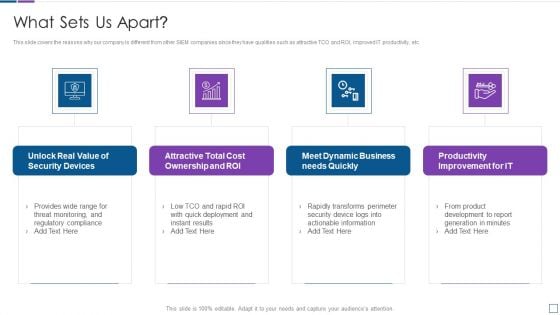
Real Time Assessment Of Security Threats What Sets Us Apart Microsoft PDF
This slide covers the reasons why our company is different from other SIEM companies since they have qualities such as attractive TCO and ROI, improved IT productivity, etc. Presenting real time assessment of security threats what sets us apart microsoft pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like security devices, cost ownership and roi, dynamic business, productivity improvement. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
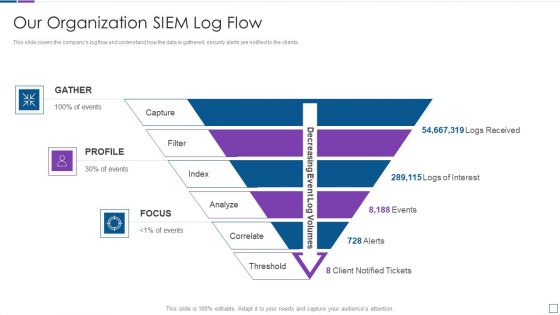
Real Time Assessment Of Security Threats Our Organization SIEM Log Flow Topics PDF
This slide covers the companys log flow and understand how the data is gathered, security alerts are notified to the clients. This is a real time assessment of security threats our organization siem log flow topics pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like our organization siem log flow. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
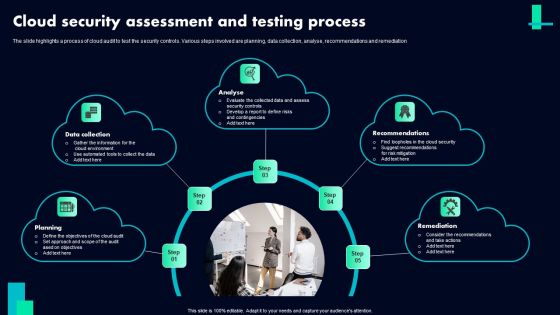
Cloud Security Assessment And Testing Process Ppt PowerPoint Presentation File Outline PDF
The slide highlights a process of cloud audit to test the security controls. Various steps involved are planning, data collection, analyse, recommendations and remediation Persuade your audience using this Cloud Security Assessment And Testing Process Ppt PowerPoint Presentation File Outline PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Data Collection, Analyse, Recommendations, Remediation. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
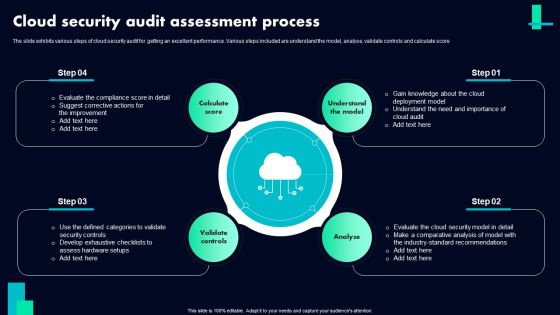
Cloud Security Audit Assessment Process Ppt PowerPoint Presentation Gallery Summary PDF
The slide exhibits various steps of cloud security audit for getting an excellent performance. Various steps included are understand the model, analyse, validate controls and calculate score. Persuade your audience using this Cloud Security Audit Assessment Process Ppt PowerPoint Presentation Gallery Summary PDF. This PPT design covers FOUR stages, thus making it a great tool to use. It also caters to a variety of topics including Calculate Score, Understand The Model, Analyse Validate Controls. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
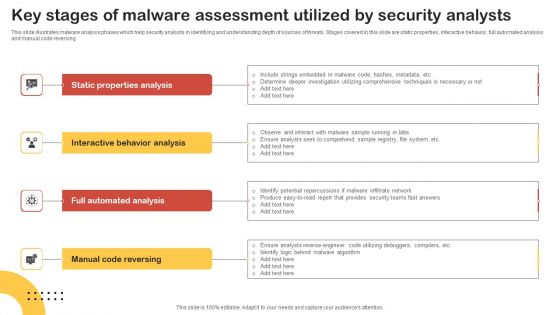
Key Stages Of Malware Assessment Utilized By Security Analysts Graphics PDF
This slide illustrates malware analysis phases which help security analysts in identifying and understanding depth of sources of threats. Stages covered in this slide are static properties, interactive behavior, full automated analysis and manual code reversing. Presenting Key Stages Of Malware Assessment Utilized By Security Analysts Graphics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Static Properties Analysis, Interactive Behavior Analysis, Full Automated Analysis. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
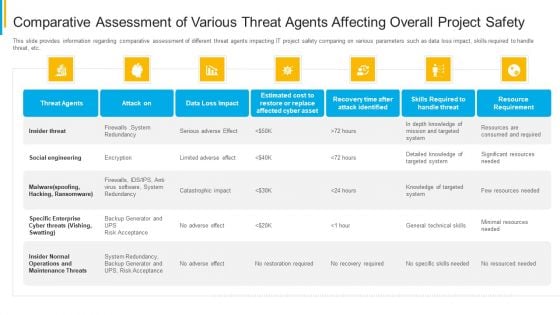
Project Security Administration IT Comparative Assessment Of Various Threat Agents Affecting Overall Project Safety Background PDF
This slide provides information regarding comparative assessment of different threat agents impacting IT project safety comparing on various parameters such as data loss impact, skills required to handle threat, etc. Deliver and pitch your topic in the best possible manner with this project security administration it comparative assessment of various threat agents affecting overall project safety background pdf. Use them to share invaluable insights on resource requirement, maintenance threats, cyber threats, social engineering and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Security Risk Management Plan Threat Identification And Vulnerability Impact Assessment Brochure PDF
Following slide shows threat identification and vulnerability impact assessment. It covers information of threat agent, affected assets, potential vulnerability, vulnerability ranking, its rank and threats to firm. Deliver and pitch your topic in the best possible manner with this cyber security risk management plan threat identification and vulnerability impact assessment brochure pdf. Use them to share invaluable insights on threat agent, affected assets, potential vulnerability, vulnerability ranking, threats to firm and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
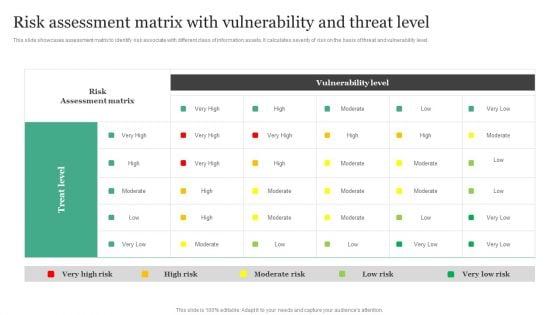
Risk Assessment Matrix With Vulnerability And Threat Level Information Security Risk Administration Rules PDF
This slide showcases assessment matrix to identify risk associate with different class of information assets. It calculates severity of risk on the basis of threat and vulnerability level.Boost your pitch with our creative Risk Assessment Matrix With Vulnerability And Threat Level Information Security Risk Administration Rules PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.


 Continue with Email
Continue with Email

 Home
Home


































