Security Icon
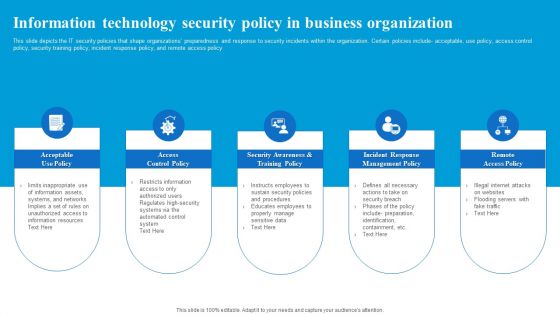
Information Technology Security Policy In Business Organization Download PDF
This slide depicts the IT security policies that shape organizations preparedness and response to security incidents within the organization. Certain policies include acceptable, use policy, access control policy, security training policy, incident response policy, and remote access policy. Presenting Information Technology Security Policy In Business Organization Download PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Access Control Policy, Acceptable Use Policy, Remote Access Policy. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Security Operations Team Roles And Responsibilities Infographics PDF
This slide exhibits key roles on the SecOps team with their roles and responsibilities that manage cybersecurity threats and attacks. It includes a security investigator, advanced security analyst, SOC manager, and security manager. Presenting Security Operations Team Roles And Responsibilities Infographics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Skills Required, Determine, Develop Mitigation. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Smart Phone Security Tools For Preventing Threats Topics PDF
This slide shows latest security tools for managing phone security model. The purpose of this slide is to highlight various tools names with description for selecting most suitable tool. It include tools such as data loss prevention, identify and access management, etc. Presenting Smart Phone Security Tools For Preventing Threats Topics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Data Loss Prevention, Identity Access Management, Security Event Management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
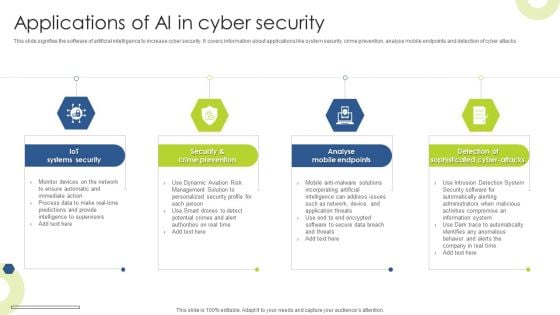
Applications Of AI In Cyber Security Infographics PDF
This slide signifies the software of artificial intelligence to increase cyber security. It covers information about applications like system security, crime prevention, analyse mobile endpoints and detection of cyber attacks Presenting Applications Of AI In Cyber Security Infographics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Iot Systems Security, Crime Prevention, Analyse Mobile Endpoints. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
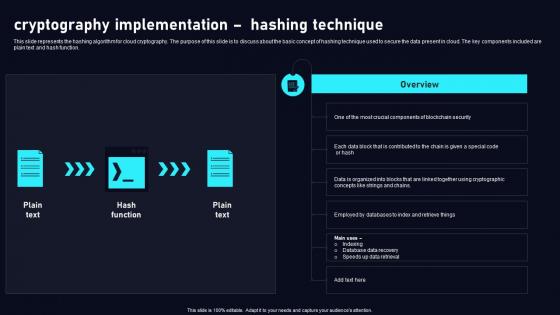
Cryptography Implementation Hashing Cloud Data Security Using Cryptography Pictures Pdf
This slide represents the hashing algorithm for cloud cryptography. The purpose of this slide is to discuss about the basic concept of hashing technique used to secure the data present in cloud. The key components included are plain text and hash function. Are you searching for a Cryptography Implementation Hashing Cloud Data Security Using Cryptography Pictures Pdf that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Cryptography Implementation Hashing Cloud Data Security Using Cryptography Pictures Pdf from Slidegeeks today. This slide represents the hashing algorithm for cloud cryptography. The purpose of this slide is to discuss about the basic concept of hashing technique used to secure the data present in cloud. The key components included are plain text and hash function.
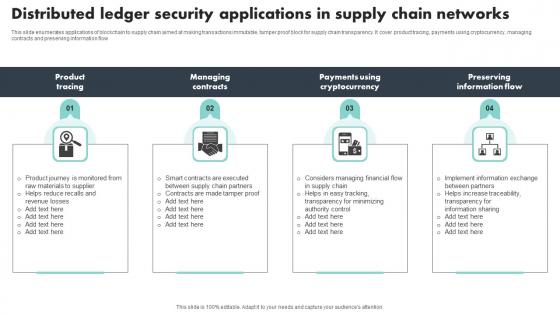
Distributed Ledger Security Applications In Supply Chain Networks Themes Pdf
This slide enumerates applications of blockchain to supply chain aimed at making transactions immutable, tamper proof block for supply chain transparency. It cover product tracing, payments using cryptocurrency, managing contracts and preserving information flow Pitch your topic with ease and precision using this Distributed Ledger Security Applications In Supply Chain Networks Themes Pdf This layout presents information on Product Tracing, Managing Contracts, Preserving Information Flow It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide enumerates applications of blockchain to supply chain aimed at making transactions immutable, tamper proof block for supply chain transparency. It cover product tracing, payments using cryptocurrency, managing contracts and preserving information flow

Overview Flow Chart Of Cyber Security Breach Summary Pdf
This templates shows the schematic illustration of a malware attack. The purpose of this slide to elaborate through various phases attack get implemented by attacker . The process starts withs cyber attackers send spam emails and various commands which ends with stealing data with devices Pitch your topic with ease and precision using this Overview Flow Chart Of Cyber Security Breach Summary Pdf This layout presents information on Email Delivered, Sending Commands, Injected Into It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This templates shows the schematic illustration of a malware attack. The purpose of this slide to elaborate through various phases attack get implemented by attacker . The process starts withs cyber attackers send spam emails and various commands which ends with stealing data with devices

Chain And Person Security PowerPoint Templates And PowerPoint Themes 0612
Chain And Person Security PowerPoint Templates And PowerPoint Themes 0612-Microsoft Powerpoint Templates and Background with human character person and a chain Our Chain And Person Security PowerPoint Templates And PowerPoint Themes 0612 have a fetish for excellence. They just can't settle for anything less.

Bank Security Through Internet PowerPoint Templates And PowerPoint Themes 0812
Bank Security Through Internet PowerPoint Templates And PowerPoint Themes 0812-Microsoft Powerpoint Templates and Background with bank with computer mouse Evoke surprise in your audience with our Bank Security Through Internet PowerPoint Templates And PowerPoint Themes 0812. See them realise how clever your plan is.
Security Breach Events Tracking Dashboard Data Breach Prevention Themes Pdf
Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Security Breach Events Tracking Dashboard Data Breach Prevention Themes Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide represents the dashboard to track data breach attacks. The purpose of this slide is to provide a graphical representation of cyber attacks that occurred in a specific period. It also depicts the overview of different types of attacks.
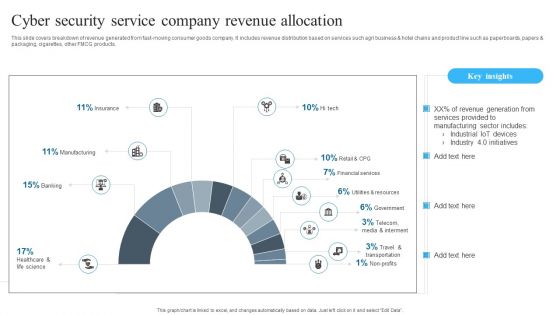
Cyber Security Service Company Revenue Allocation Background PDF
Showcasing this set of slides titled Cyber Security Service Company Revenue Allocation Background PDF. The topics addressed in these templates are Cyber Security, Service Company, Revenue Allocation. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
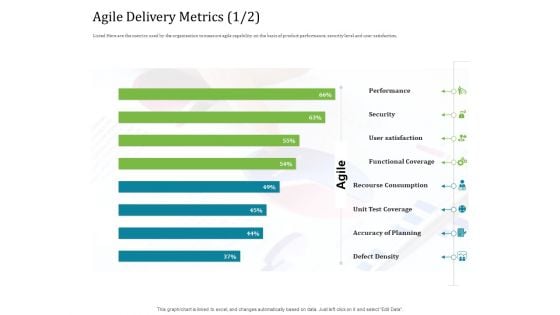
Agile Service Delivery Model Agile Delivery Metrics Security Professional PDF
Deliver an awe inspiring pitch with this creative agile service delivery model agile delivery metrics security professional pdf bundle. Topics like performance, security, user satisfaction, functional coverage, recourse consumption can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Evaluation Of HR Security Policy And Procedure Diagrams PDF
Persuade your audience using this Evaluation Of HR Security Policy And Procedure Diagrams PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Evaluation HR Security, Policy Procedure. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Differentiating 2 Items Graphic For Free Internet Security Guidelines PDF
Deliver an awe inspiring pitch with this creative differentiating 2 items graphic for free internet security guidelines pdf bundle. Topics like differentiating 2 items graphic for free internet security reviews can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
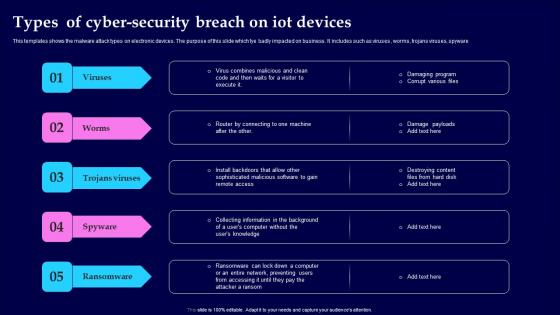
Types Of Cyber Security Breach On IOT Devices Themes Pdf
This templates shows the malware attack types on electronic devices. The purpose of this slide which tye badly impacted on business. It includes such as viruses, worms, trojans viruses, spyware Pitch your topic with ease and precision using this Types Of Cyber Security Breach On IOT Devices Themes Pdf This layout presents information on Viruses, Trojans Viruses, Spyware, Ransomware It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This templates shows the malware attack types on electronic devices. The purpose of this slide which tye badly impacted on business. It includes such as viruses, worms, trojans viruses, spyware
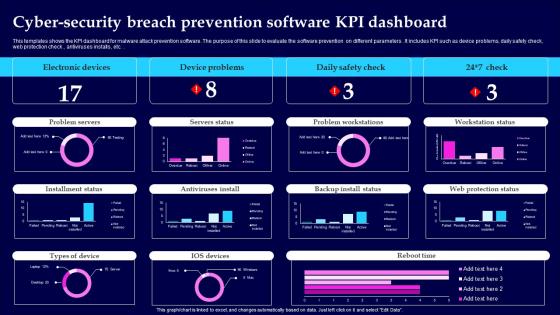
Cyber Security Breach Prevention Software KPI Dashboard Information Pdf
This templates shows the KPI dashboard for malware attack prevention software. The purpose of this slide to evaluate the software prevention on different parameters. It includes KPI such as device problems, daily safety check, web protection check, antiviruses installs , etc. Showcasing this set of slides titled Cyber Security Breach Prevention Software KPI Dashboard Information Pdf The topics addressed in these templates are Electronic Devices, Device Problems, Daily Safety Check All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This templates shows the KPI dashboard for malware attack prevention software. The purpose of this slide to evaluate the software prevention on different parameters. It includes KPI such as device problems, daily safety check, web protection check, antiviruses installs , etc.
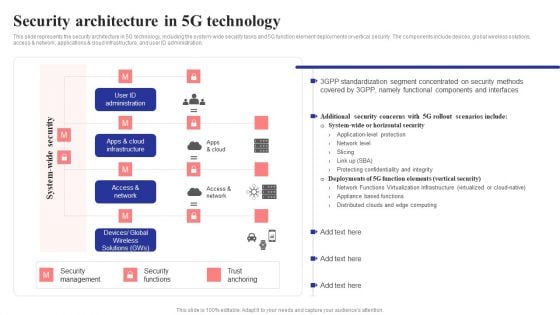
Security Architecture In 5G Technology 5G Network Structure Background PDF
This slide represents the security architecture in 5G technology, including the system-wide security tasks and 5G function element deployments or vertical security. The components include devices, global wireless solutions, access network, applications cloud infrastructure, and user ID administration.Are you searching for a Security Architecture In 5G Technology 5G Network Structure Background PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Security Architecture In 5G Technology 5G Network Structure Background PDF from Slidegeeks today.
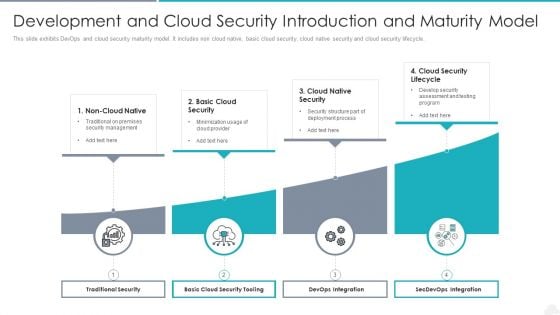
Development And Cloud Security Introduction And Maturity Model Graphics PDF
Presenting development and cloud security introduction and maturity model graphics pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including traditional security, devops integration, secdevops integration. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
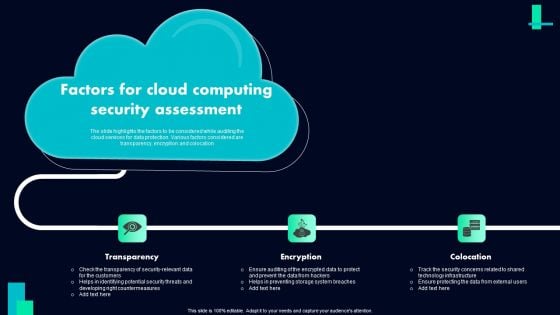
Factors For Cloud Computing Security Assessment Ppt Gallery Deck PDF
Presenting Factors For Cloud Computing Security Assessment Ppt Gallery Deck PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Factors For, Cloud Computing, Security Assessment. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
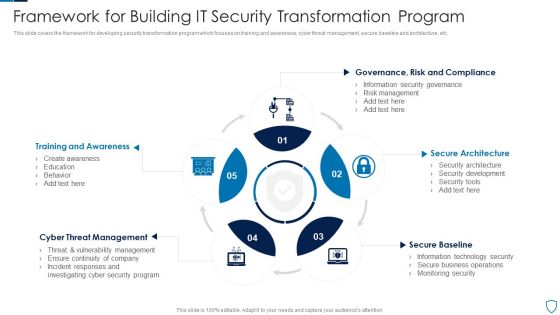
Framework For Building IT Security Transformation Program Pictures PDF
This slide covers the framework for developing security transformation program which focuses on training and awareness, cyber threat management, secure baseline and architecture, etc.Presenting Framework For Building IT Security Transformation Program Pictures PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Training Awareness, Threat Management, Secure Architecture This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
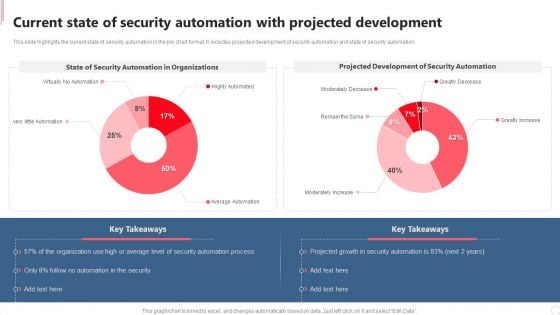
Current State Of Security Automation With Projected Development Rules PDF
This slide highlights the current state of security automation in the pie chart format. It includes projected development of security automation and state of security automation. If you are looking for a format to display your unique thoughts, then the professionally designed Current State Of Security Automation With Projected Development Rules PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Current State Of Security Automation With Projected Development Rules PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
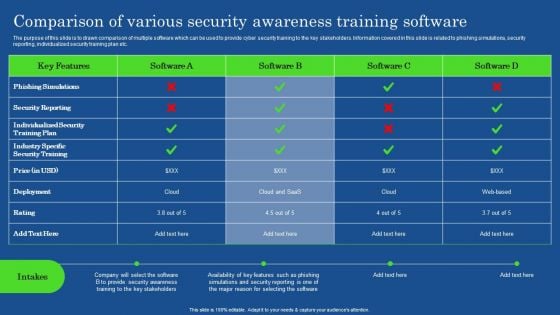
Comparison Of Various Security Awareness Training Software Demonstration PDF
The purpose of this slide is to drawn comparison of multiple software which can be used to provide cyber security training to the key stakeholders. Information covered in this slide is related to phishing simulations, security reporting, individualized security training plan etc. If you are looking for a format to display your unique thoughts, then the professionally designed Comparison Of Various Security Awareness Training Software Demonstration PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Comparison Of Various Security Awareness Training Software Demonstration PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
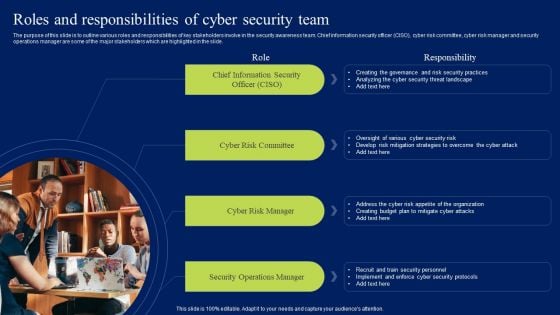
Roles And Responsibilities Of Cyber Security Team Ppt Portfolio
The purpose of this slide is to outline various roles and responsibilities of key stakeholders involve in the security awareness team. Chief information security officer CISO, cyber risk committee, cyber risk manager and security operations manager are some of the major stakeholders which are highlighted in the slide. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Roles And Responsibilities Of Cyber Security Team Ppt Portfolio can be your best option for delivering a presentation. Represent everything in detail using Roles And Responsibilities Of Cyber Security Team Ppt Portfolio and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Internet Security Threat Analysis Report Chart Introduction PDF
Following slide exhibits security and data breach report chart it includes major statistics such as- loss or theft of data, failure to redirect data and data posting to incorrect recipient. Pitch your topic with ease and precision using this internet security threat analysis report chart introduction pdf. This layout presents information on internet security threat analysis report chart. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
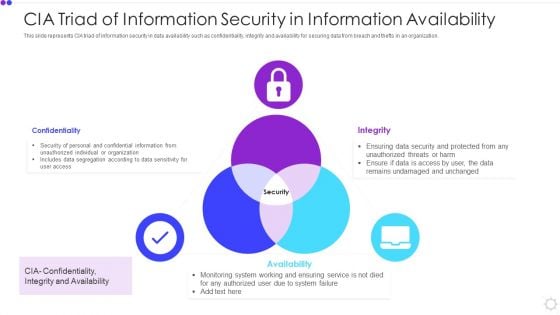
Cia Triad Of Information Security In Information Availability Microsoft PDF
This slide represents CIA triad of information security in data availability such as confidentiality, integrity and availability for securing data from breach and thefts in an organization. Presenting cia triad of information security in information availability microsoft pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including confidentiality, integrity, availability. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
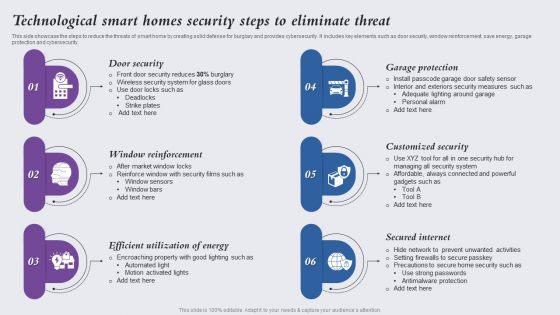
Technological Smart Homes Security Steps To Eliminate Threat Themes PDF
This side showcase the steps to reduce the threats of smart home by creating solid defense for burglary and provides cybersecurity. It includes key elements such as door security, window reinforcement, save energy, garage protection and cybersecurity. Presenting Technological Smart Homes Security Steps To Eliminate Threat Themes PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Door Security, Window Reinforcement, Efficient Utilization Energy. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
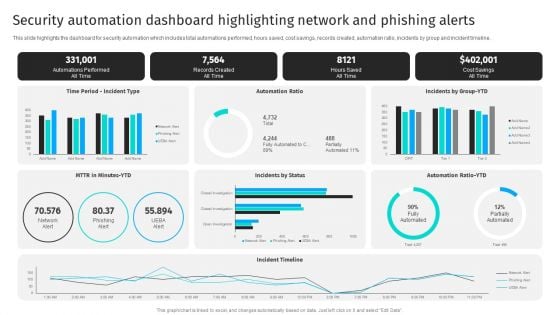
Security Automation Dashboard Highlighting Network And Phishing Alerts Professional PDF
This slide highlights the dashboard for security automation which includes total automations performed, hours saved, cost savings, records created, automation ratio, incidents by group and incident timeline.Get a simple yet stunning designed Security Automation Dashboard Highlighting Network And Phishing Alerts Professional PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Security Automation Dashboard Highlighting Network And Phishing Alerts Professional PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Five Key Consideration For Hotel Protection And Security Infographics PDF
This slide highlights five strategies to ensure safety and security in hotels. It involves strategies such as installation of proper lighting, CCTV security cameras, fire alarms, emergency power and manual.Presenting Five Key Consideration For Hotel Protection And Security Infographics PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Emergency Power, Emergency Manual, Proper Lighting This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
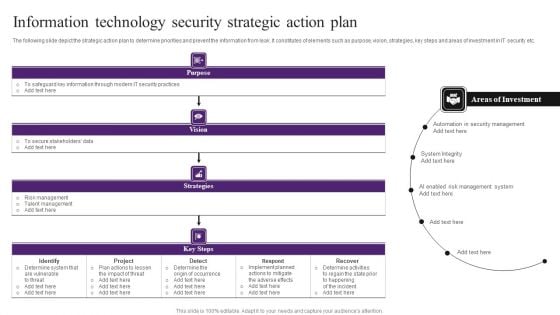
Information Technology Security Strategic Action Plan Themes PDF
The following slide depict the strategic action plan to determine priorities and prevent the information from leak. It constitutes of elements such as purpose, vision, strategies, key steps and areas of investment in IT security etc. Showcasing this set of slides titled Information Technology Security Strategic Action Plan Themes PDF. The topics addressed in these templates are Determine System, Implement, Security Management. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
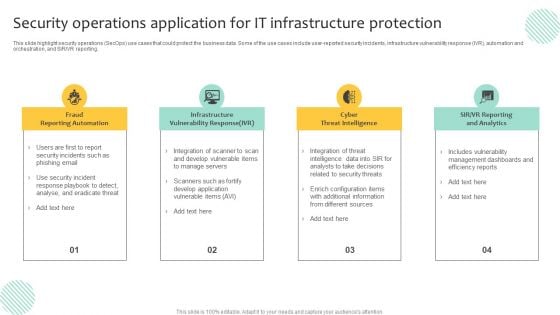
Security Operations Application For IT Infrastructure Protection Template PDF
This slide highlight security operations SecOps use cases that could protect the business data. Some of the use cases include user-reported security incidents, infrastructure vulnerability response IVR, automation and orchestration, and SIR or VR reporting. Presenting Security Operations Application For IT Infrastructure Protection Template PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Infrastructure Vulnerability Response, Cyber Threat Intelligence, Fraud Reporting Automation. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
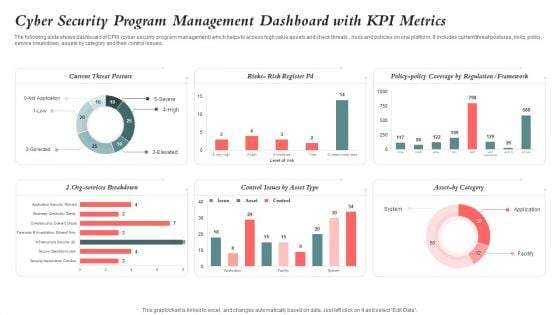
Cyber Security Program Management Dashboard With KPI Metrics Ideas PDF
The following slide shows dashboard of CPM cyber security program management which helps to access high value assets and check threats , risks and policies on one platform. It includes current threat postures, risks, policy, service breakdown, assets by category and their control issues. Pitch your topic with ease and precision using this Cyber Security Program Management Dashboard With KPI Metrics Ideas PDF. This layout presents information on Cyber Security, Program Management Dashboard, Kpi Metrics. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
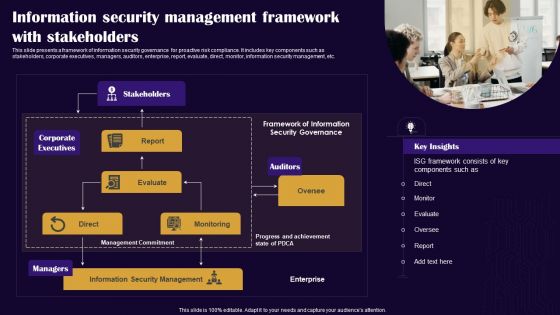
Information Security Management Framework With Stakeholders Diagrams PDF
This slide presents a framework of information security governance for proactive risk compliance. It includes key components such as stakeholders, corporate executives, managers, auditors, enterprise, report, evaluate, direct, monitor, information security management, etc. Persuade your audience using this Information Security Management Framework With Stakeholders Diagrams PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Stakeholders, Auditors, Corporate Executives. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cybersecurity Operations Cybersecops Security Operations Model And Incidents Diagrams PDF
This slide represents the security operations model, covering the incidents managed by the security operations center. The model includes three teams such as hunters, investigators, and triage. The incidents include multi-stage incidents, known campaign tracking, and high-volume incidents. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Cybersecurity Operations Cybersecops Security Operations Model And Incidents Diagrams PDF from Slidegeeks and deliver a wonderful presentation.

Insurance Agent Protection Security PowerPoint Presentation Slides C
Microsoft PowerPoint Slides and Backgrounds with in the field giving you the best protection everywhere Deliver a dose of enlightenment with our Insurance Agent Protection Security PowerPoint Presentation Slides C. Light up the bulbs in the minds of your audience.

Insurance Agent Protection Security PowerPoint Presentation Slides Cc
Microsoft PowerPoint Slides and Backgrounds with in the field giving you the best protection everywhere Our Insurance Agent Protection Security PowerPoint Presentation Slides Cc can be very enticing. Their blend of colors will captivate anyone.

Insurance Agent Protection Security PowerPoint Presentation Slides F
Microsoft PowerPoint Slides and Backgrounds with in the field giving you the best protection everywhere Exert influence with your thoughts. Let our Insurance Agent Protection Security PowerPoint Presentation Slides F be the conduit.

Insurance Agent Protection Security PowerPoint Presentation Slides R
Microsoft PowerPoint Slides and Backgrounds with in the field giving you the best protection everywhere Attain victory with our Insurance Agent Protection Security PowerPoint Presentation Slides R. You will come out on top.

Insurance Agent Protection Security PowerPoint Presentation Slides S
Microsoft PowerPoint Slides and Backgrounds with in the field giving you the best protection everywhere Stimulate peoples brain with our Insurance Agent Protection Security PowerPoint Presentation Slides S. Just download, type and present.
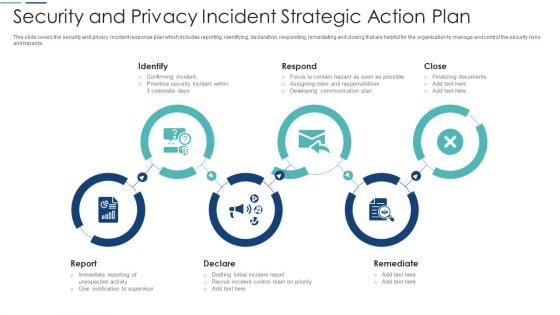
Security And Privacy Incident Strategic Action Plan Download PDF
This slide covers the security and privacy incident response plan which includes reporting, identifying, declaration, responding, remediating and closing that are helpful for the organization to manage and control the security risks and hazards. Presenting security and privacy incident strategic action plan download pdf to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including confirming incident, assigning responsibilities, communication plan, supervisor. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Business Data Encryption Security Management Technology Ideas PDF
This slide highlights the role of encryption technology which is used by business and organisation to protect the confidentiality of digital data storage and transmission. Key components are authentication, privacy, regulatory compliance and security. Presenting Business Data Encryption Security Management Technology Ideas PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Authentication, Privacy, Regulatory Compliance, Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

How Security Concerns Affect Firm In Present Times Pictures PDF
This slide portrays information regarding the concerns that are currently existing in the organizations. It is essential for top level management to keep check on existing concerns as they have severe impact on firms growth in terms of huge financial losses and bad public image. Deliver an awe inspiring pitch with this creative how security concerns affect firm in present times pictures pdf bundle. Topics like reported financial losses due to increase security threats, data breaches and records exposed, security threat incidents can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
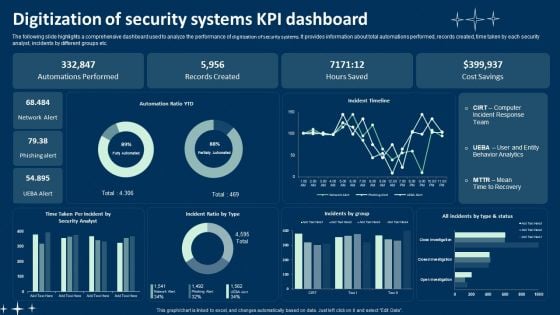
Digitization Of Security Systems KPI Dashboard Ppt Summary Portfolio PDF
The following slide highlights a comprehensive dashboard used to analyze the performance of digitization of security systems. It provides information about total automations performed, records created, time taken by each security analyst, incidents by different groups etc. Showcasing this set of slides titled Digitization Of Security Systems KPI Dashboard Ppt Summary Portfolio PDF. The topics addressed in these templates are Automations Performed, Records Created, Hours Saved. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
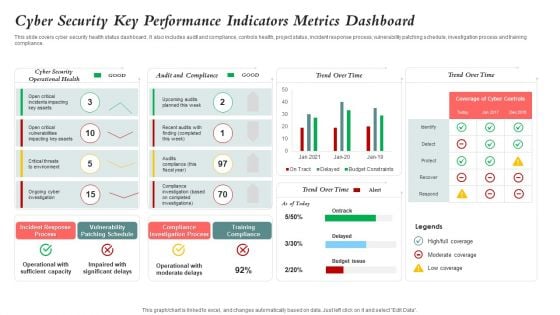
Cyber Security Key Performance Indicators Metrics Dashboard Mockup PDF
This slide covers cyber security health status dashboard . It also includes audit and compliance, controls health, project status, incident response process, vulnerability patching schedule, investigation process and training compliance. Pitch your topic with ease and precision using this Cyber Security Key Performance Indicators Metrics Dashboard Mockup PDF. This layout presents information on Cyber Security, Vulnerability Patching Schedule, Compliance Investigation Process. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
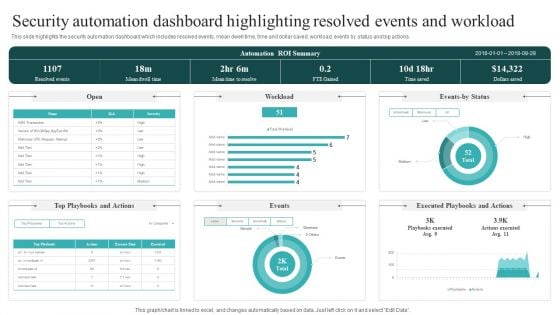
Security Automation Dashboard Highlighting Resolved Events And Workload Guidelines PDF
This slide highlights the security automation dashboard which includes resolved events, mean dwell time, time and dollar saved, workload, events by status and top actions. This Security Automation Dashboard Highlighting Resolved Events And Workload Guidelines PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Security Automation Dashboard Highlighting Resolved Events And Workload Guidelines PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, don not wait, grab the presentation templates today.
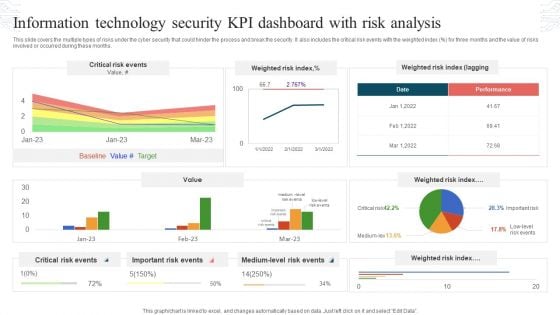
Information Technology Security KPI Dashboard With Risk Analysis Topics PDF
This slide covers the multiple types of risks under the cyber security that could hinder the process and break the security. It also includes the critical risk events with the weighted index percent for three months and the value of risks involved or occurred during these months. Showcasing this set of slides titled Information Technology Security KPI Dashboard With Risk Analysis Topics PDF. The topics addressed in these templates are Critical Risk Events, Weighted Risk Index, Important Risk Events. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
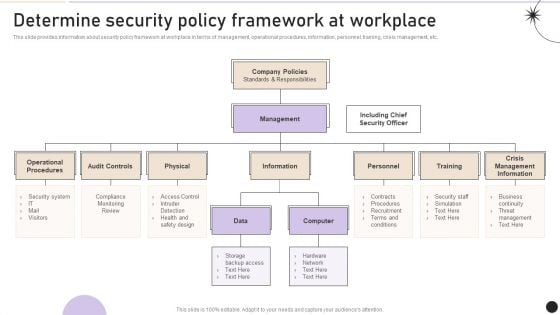
Determine Security Policy Framework At Workplace Pictures PDF
This slide provides information about security policy framework at workplace in terms of management, operational procedures, information, personnel, training, crisis management, etc. Get a simple yet stunning designed Determine Security Policy Framework At Workplace Pictures PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Determine Security Policy Framework At Workplace Pictures PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
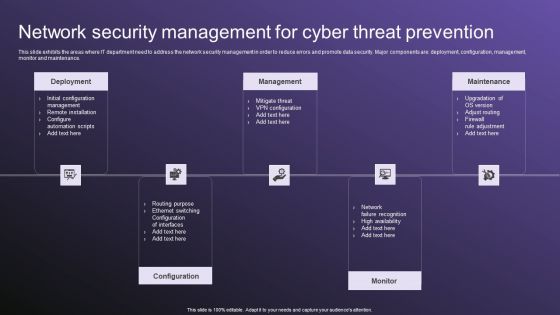
Network Security Management For Cyber Threat Prevention Demonstration PDF
This slide exhibits the areas where IT department need to address the network security management in order to reduce errors and promote data security. Major components are deployment, configuration, management, monitor and maintenance. Presenting Network Security Management For Cyber Threat Prevention Demonstration PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Deployment, Management, Configuration. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
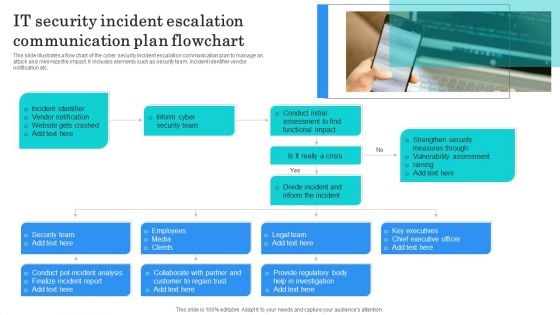
IT Security Incident Escalation Communication Plan Flowchart Structure PDF
This slide illustrates a flow chart of the cyber security incident escalation communication plan to manage an attack and minimize the impact. It includes elements such as security team, incident identifier vendor notification etc. Presenting IT Security Incident Escalation Communication Plan Flowchart Structure PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Incident Identifier, Vendor Notification, Website Gets Crashed. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
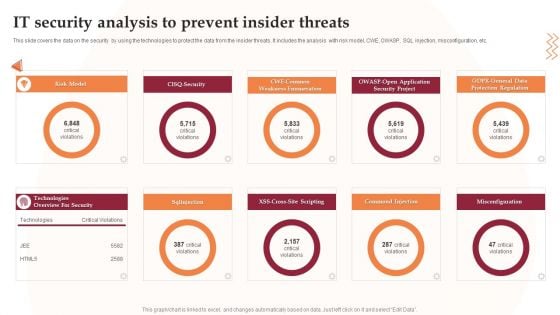
IT Security Analysis To Prevent Insider Threats Infographics PDF
This slide covers the data on the security by using the technologies to protect the data from the insider threats. It includes the analysis with risk model, CWE, OWASP, SQL injection, misconfiguration, etc. Presenting IT Security Analysis To Prevent Insider Threats Infographics PDF to dispense important information. This template comprises nine stages. It also presents valuable insights into the topics including Security Project, Application, Risk Model. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
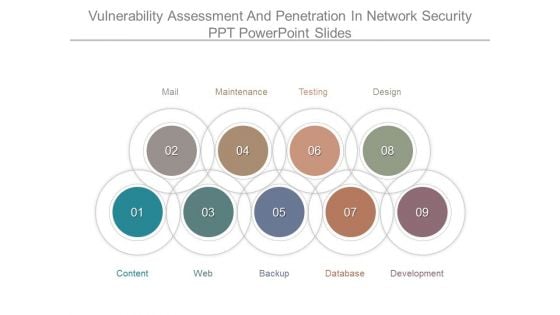
Vulnerability Assessment And Penetration In Network Security Ppt Powerpoint Slides
This is a vulnerability assessment and penetration in network security ppt powerpoint slides. This is a nine stage process. The stages in this process are mail, maintenance, testing, design, development, database, backup, web, content.
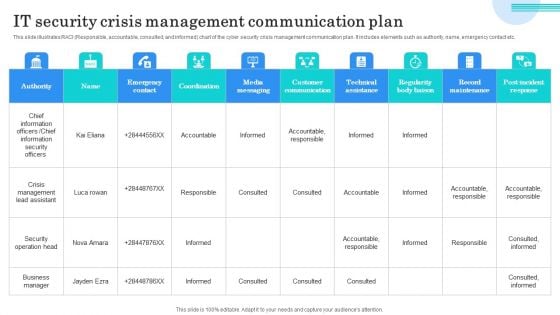
IT Security Crisis Management Communication Plan Microsoft PDF
This slide illustrates RACI Responsible, accountable, consulted, and informed chart of the cyber security crisis management communication plan. It includes elements such as authority, name, emergency contact etc. Showcasing this set of slides titled IT Security Crisis Management Communication Plan Microsoft PDF. The topics addressed in these templates are Chief Information Officers, Chief Information Security Officers, Crisis Management Lead Assistant. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
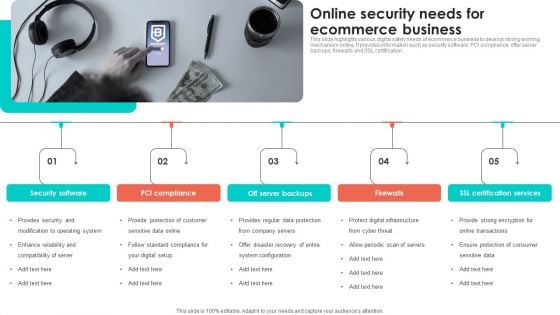
Online Security Needs For Ecommerce Business Professional PDF
This slide highlights various digital safety needs of ecommerce business to develop strong working mechanism online. It provides information such as security software, PCI compliance, offer server backups, firewalls and SSL certification. Presenting Online Security Needs For Ecommerce Business Professional PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including PCI Compliance, Off Server Backups, Security Software. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
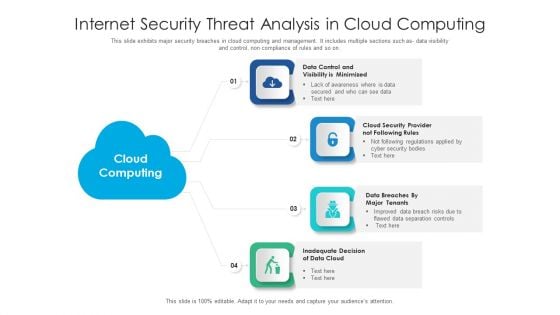
Internet Security Threat Analysis In Cloud Computing Information PDF
This slide exhibits major security breaches in cloud computing and management. It includes multiple sections such as- data visibility and control, non compliance of rules and so on. Presenting internet security threat analysis in cloud computing information pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including data cloud, cloud security, data control. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
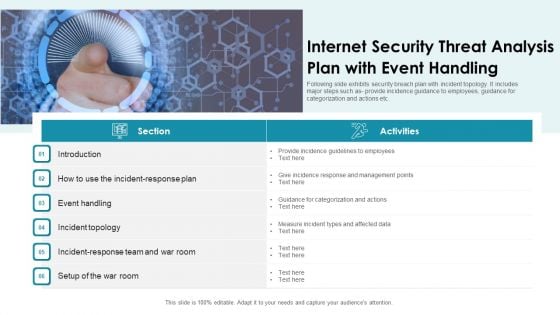
Internet Security Threat Analysis Plan With Event Handling Summary PDF
Following slide exhibits security breach plan with incident topology. It includes major steps such as- provide incidence guidance to employees, guidance for categorization and actions etc. Presenting internet security threat analysis plan with event handling summary pdf to dispense important information. This template comprises one stage. It also presents valuable insights into the topics including internet security threat analysis plan with event handling. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
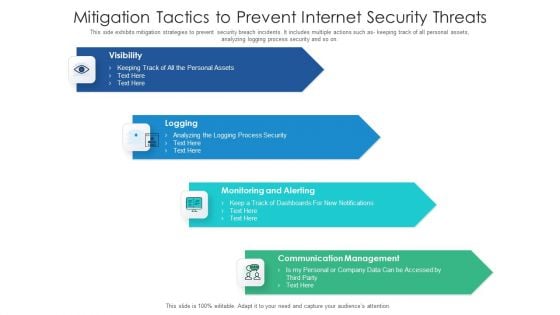
Mitigation Tactics To Prevent Internet Security Threats Formats PDF
This side exhibits mitigation strategies to prevent security breach incidents. It includes multiple actions such as keeping track of all personal assets, analyzing logging process security and so on. Presenting mitigation tactics to prevent internet security threats formats pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including communication management, monitoring and alerting, logging, visibility. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
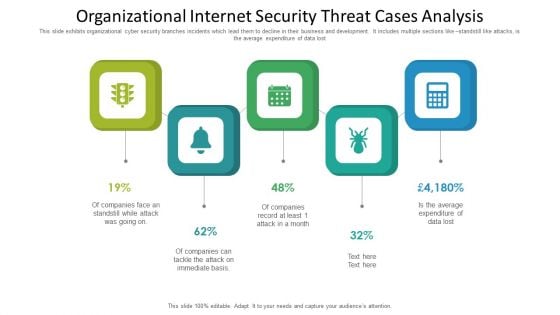
Organizational Internet Security Threat Cases Analysis Information PDF
This slide exhibits organizational cyber security branches incidents which lead them to decline in their business and development. It includes multiple sections like standstill like attacks, is the average expenditure of data lost. Presenting organizational internet security threat cases analysis information pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including organizational internet security threat cases analysis. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
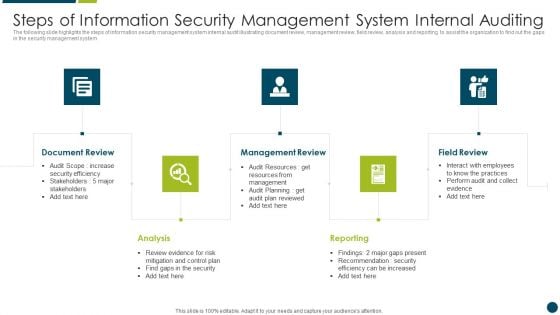
Steps Of Information Security Management System Internal Auditing Structure PDF
The following slide highlights the steps of information security management system internal audit illustrating document review, management review, field review, analysis and reporting to assist the organization to find out the gaps in the security management system Presenting Steps Of Information Security Management System Internal Auditing Structure PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Management Review, Reporting, Analysis. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully

Six Practices For IT Security Management Program Microsoft PDF
This slide shows the best practices for security management program which includes essential tasks such as risk analysis and identification, manage risk, threat and issues, security consolidation procedure, etc. With assigned owner and frequency.Presenting Six Practices For IT Security Management Program Microsoft PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Analysis Prioritization, Consolidation Procedure, Strategic Initiatives This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Information Technology Security Threats And Key Performance Indicators Formats PDF
This slide covers the information related to the various types of cyber threats and the key performance indicators used by the organization for dealing with these security breaches. Presenting Information Technology Security Threats And Key Performance Indicators Formats PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Threats Reported, Security Incidents, Intrusion Attempts. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
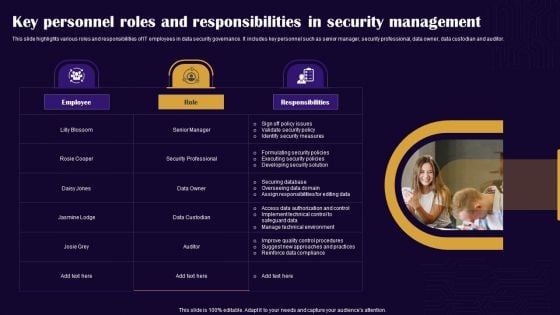
Key Personnel Roles And Responsibilities In Security Management Slides PDF
This slide highlights various roles and responsibilities of IT employees in data security governance. It includes key personnel such as senior manager, security professional, data owner, data custodian and auditor. Presenting Key Personnel Roles And Responsibilities In Security Management Slides PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Employee, Role, Responsibilities. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.


 Continue with Email
Continue with Email

 Home
Home


































