Security Icon

Cloud Based Email Security Market Report Industry Trends Ppt Styles Diagrams PDF
Major trends of the E mail security industry are shown in this slide. This is a cloud based email security market report industry trends ppt styles diagrams pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security system, artificial intelligence, supply chain security, security adaptive approach. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
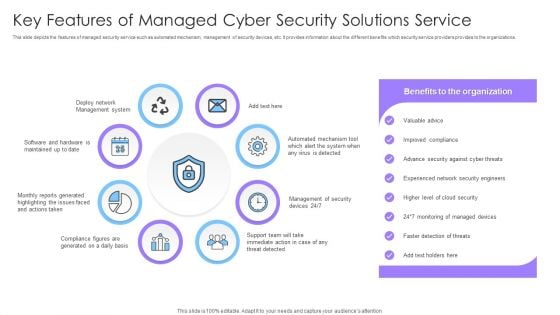
Key Features Of Managed Cyber Security Solutions Service Ppt Pictures Layouts PDF
This slide depicts the features of managed security service such as automated mechanism, management of security devices, etc. It provides information about the different benefits which security service providers provides to the organizations. Presenting Key Features Of Managed Cyber Security Solutions Service Ppt Pictures Layouts PDF to dispense important information. This template comprises eight stages. It also presents valuable insights into the topics including Deploy Network, Management System, Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Building Trust With IoT Security Deploy Tools For Continuous Device Monitoring And Diagnostics IoT SS V
This slide exhibits key activities and tools for monitoring and diagnostics of IoT device security. It includes activities such as continuous monitoring, anomaly detection, vulnerability scanning, auditing and reporting, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Building Trust With IoT Security Deploy Tools For Continuous Device Monitoring And Diagnostics IoT SS V is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Building Trust With IoT Security Deploy Tools For Continuous Device Monitoring And Diagnostics IoT SS V and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide exhibits key activities and tools for monitoring and diagnostics of IoT device security. It includes activities such as continuous monitoring, anomaly detection, vulnerability scanning, auditing and reporting, etc.

Saas Cloud Security Implementation Checklist For Managers Ppt PowerPoint Presentation File Professional PDF
The following slide represents checklist for SaaS security implementation and assessment. It includes activities such as run security test, training staff, planning backup, installing automated security alert along with their status. Presenting Saas Cloud Security Implementation Checklist For Managers Ppt PowerPoint Presentation File Professional PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Run Security Test, Planned Backup, New Threats. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
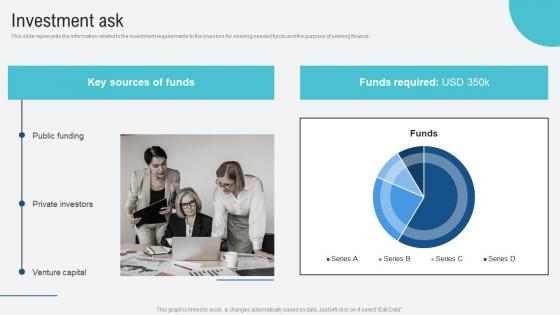
Investment Ask Voice Assistance Security Platform Investor Funding Presentation Elements Pdf
This slide represents the information related to the investment requirements to the investors for seeking needed funds and the purpose of seeking finance. Are you searching for a Investment Ask Voice Assistance Security Platform Investor Funding Presentation Elements Pdf that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Investment Ask Voice Assistance Security Platform Investor Funding Presentation Elements Pdf from Slidegeeks today. This slide represents the information related to the investment requirements to the investors for seeking needed funds and the purpose of seeking finance.
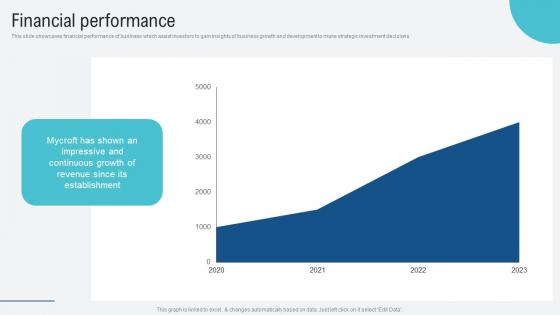
Financial Performance Voice Assistance Security Platform Investor Funding Presentation Portrait Pdf
This slide showcases financial performance of business which assist investors to gain insights of business growth and development to make strategic investment decisions. Explore a selection of the finest Financial Performance Voice Assistance Security Platform Investor Funding Presentation Portrait Pdf here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Financial Performance Voice Assistance Security Platform Investor Funding Presentation Portrait Pdf to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide showcases financial performance of business which assist investors to gain insights of business growth and development to make strategic investment decisions.
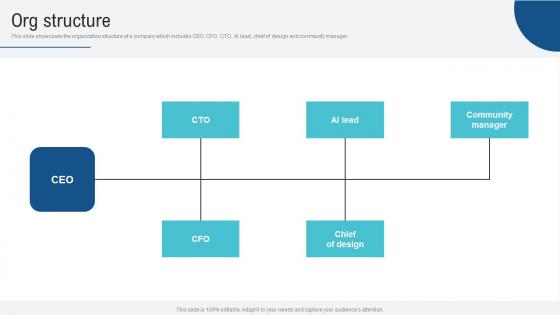
Org Structure Voice Assistance Security Platform Investor Funding Presentation Pictures Pdf
This slide showcases the organization structure of a company which includes CEO, CFO, CTO, AI lead, chief of design and community manager. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download Org Structure Voice Assistance Security Platform Investor Funding Presentation Pictures Pdf to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the Org Structure Voice Assistance Security Platform Investor Funding Presentation Pictures Pdf. This slide showcases the organization structure of a company which includes CEO, CFO, CTO, AI lead, chief of design and community manager.

Strategic Tips To Improve Physical Data Center Management Security Download PDF
This slide highlights tips to improve security of physical datacentre by having a thorough understanding of security measures and service level agreements. It covers secure location, physical access controls with building management security. Presenting Strategic Tips To Improve Physical Data Center Management Security Download PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Secure Location, Physical Access Controls, Secure Building Management Systems. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Table Of Contents For Global Data Security Industry Report IR SS V
Retrieve professionally designed Table Of Contents For Global Data Security Industry Report IR SS V to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. Our Table Of Contents For Global Data Security Industry Report IR SS V are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

SWOT Analysis To Understand The Global Security Industry PPT Slide IR SS V
Retrieve professionally designed SWOT Analysis To Understand The Global Security Industry PPT Slide IR SS V to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. Our SWOT Analysis To Understand The Global Security Industry PPT Slide IR SS V are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
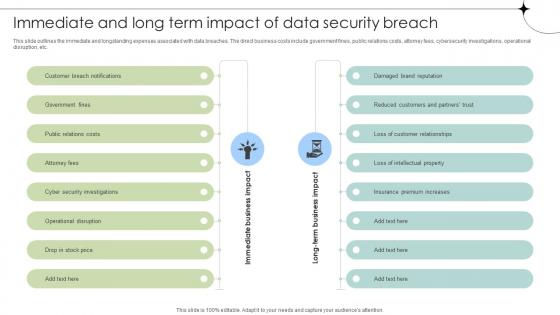
Immediate And Long Term Impact Of Data Security Breach Data Fortification Strengthening Defenses
This slide outlines the immediate and longstanding expenses associated with data breaches. The direct business costs include government fines, public relations costs, attorney fees, cybersecurity investigations, operational disruption, etc. Are you searching for a Immediate And Long Term Impact Of Data Security Breach Data Fortification Strengthening Defenses that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Immediate And Long Term Impact Of Data Security Breach Data Fortification Strengthening Defenses from Slidegeeks today. This slide outlines the immediate and longstanding expenses associated with data breaches. The direct business costs include government fines, public relations costs, attorney fees, cybersecurity investigations, operational disruption, etc.
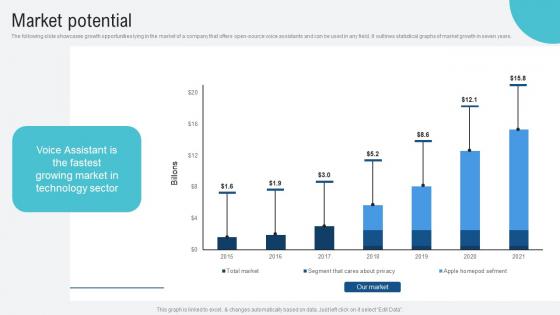
Market Potential Voice Assistance Security Platform Investor Funding Presentation Download Pdf
The following slide showcases growth opportunities lying in the market of a company that offers open source voice assistants and can be used in any field. It outlines statistical graphs of market growth in seven years. Presenting this PowerPoint presentation, titled Market Potential Voice Assistance Security Platform Investor Funding Presentation Download Pdf, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Market Potential Voice Assistance Security Platform Investor Funding Presentation Download Pdf. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Market Potential Voice Assistance Security Platform Investor Funding Presentation Download Pdf that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. The following slide showcases growth opportunities lying in the market of a company that offers open source voice assistants and can be used in any field. It outlines statistical graphs of market growth in seven years.

Global Data Security Industry Report Overview Of Cybersecurity Market Landscape IR SS V
The slide highlights a comprehensive overview of the cyber security industry. The purpose of the slide is to provide insights to stakeholders enabling them to make strategic decisions. The slide covers market sizing, and statistics related to cybersecurity spending, cybercrimes, and venture funding. This modern and well-arranged Global Data Security Industry Report Overview Of Cybersecurity Market Landscape IR SS V provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. The slide highlights a comprehensive overview of the cyber security industry. The purpose of the slide is to provide insights to stakeholders enabling them to make strategic decisions. The slide covers market sizing, and statistics related to cybersecurity spending, cybercrimes, and venture funding.
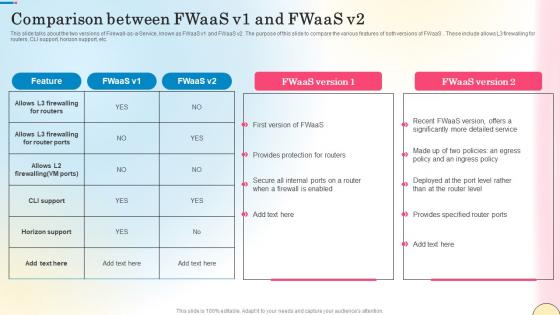
Comparison Between Fwaas V1 And Fwaas V2 Network Security Brochure Pdf
This slide talks about the two versions of Firewall-as-a-Service, known as FWaaS v1 and FWaaS v2. The purpose of this slide to compare the various features of both versions of FWaaS . These include allows L3 firewalling for routers, CLI support, horizon support, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Comparison Between Fwaas V1 And Fwaas V2 Network Security Brochure Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Comparison Between Fwaas V1 And Fwaas V2 Network Security Brochure Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide talks about the two versions of Firewall-as-a-Service, known as FWaaS v1 and FWaaS v2. The purpose of this slide to compare the various features of both versions of FWaaS . These include allows L3 firewalling for routers, CLI support, horizon support, etc.
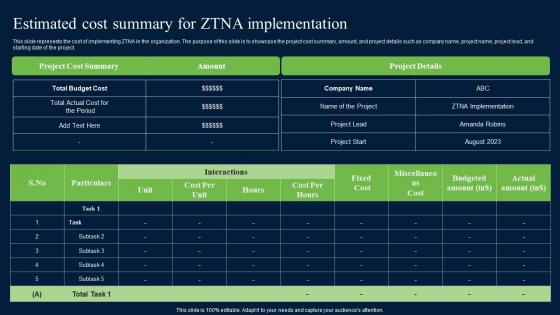
Estimated Cost Summary For ZTNA Zero Trust Network Security Elements Pdf
This slide represents the cost of implementing ZTNA in the organization. The purpose of this slide is to showcase the project cost summary, amount, and project details such as company name, project name, project lead, and starting date of the project. If you are looking for a format to display your unique thoughts, then the professionally designed Estimated Cost Summary For ZTNA Zero Trust Network Security Elements Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Estimated Cost Summary For ZTNA Zero Trust Network Security Elements Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide represents the cost of implementing ZTNA in the organization. The purpose of this slide is to showcase the project cost summary, amount, and project details such as company name, project name, project lead, and starting date of the project.

Key Objectives Of People Centric Work Culture Security System Infographics PDF
The following slide highlights the main reasons to develop human centric security system for better security features. It mainly includes activities such as establishing secure perimeter, comprehending cause behind user actions, optimizing remote security operations etc. Presenting Key Objectives Of People Centric Work Culture Security System Infographics PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Establish Secure Perimeter, Acknowledges Potential Threats, Employee Roles. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
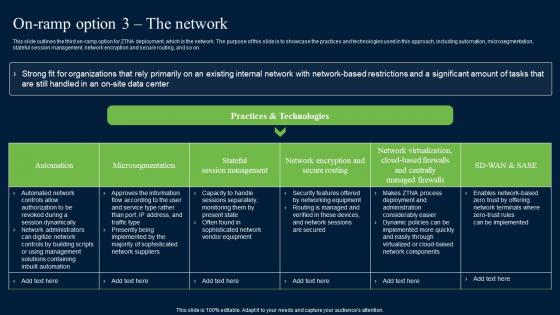
On Ramp Option 3 The Network Zero Trust Network Security Information Pdf
This slide outlines the third on-ramp option for ZTNA deployment, which is the network. The purpose of this slide is to showcase the practices and technologies used in this approach, including automation, microsegmentation, stateful session management, network encryption and secure routing, and so on. Are you searching for a On Ramp Option 3 The Network Zero Trust Network Security Information Pdf that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download On Ramp Option 3 The Network Zero Trust Network Security Information Pdf from Slidegeeks today. This slide outlines the third on-ramp option for ZTNA deployment, which is the network. The purpose of this slide is to showcase the practices and technologies used in this approach, including automation, microsegmentation, stateful session management, network encryption and secure routing, and so on.
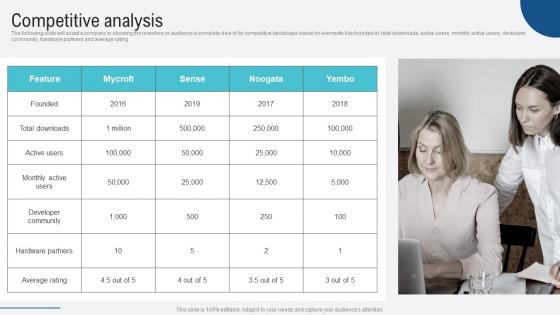
Competitive Analysis Voice Assistance Security Platform Investor Funding Presentation Themes Pdf
The following slide will assist a company in showing the investors or audience a complete view of its competitive landscape based on elements like founded in, total downloads, active users, monthly active users, developer community, hardware partners and average rating. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Competitive Analysis Voice Assistance Security Platform Investor Funding Presentation Themes Pdf was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Competitive Analysis Voice Assistance Security Platform Investor Funding Presentation Themes Pdf The following slide will assist a company in showing the investors or audience a complete view of its competitive landscape based on elements like founded in, total downloads, active users, monthly active users, developer community, hardware partners and average rating.
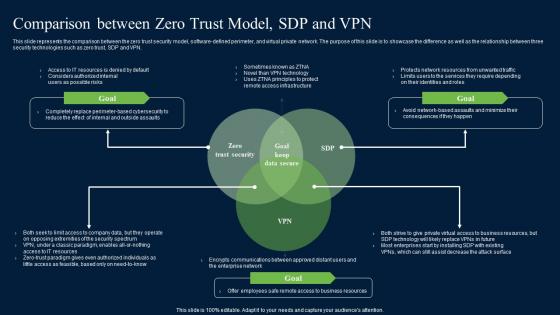
Comparison Between Zero Trust Model SDP Zero Trust Network Security Guidelines Pdf
This slide represents the comparison between the zero trust security model, software-defined perimeter, and virtual private network. The purpose of this slide is to showcase the difference as well as the relationship between three security technologies such as zero trust, SDP and VPN. Present like a pro with Comparison Between Zero Trust Model SDP Zero Trust Network Security Guidelines Pdf Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide represents the comparison between the zero trust security model, software-defined perimeter, and virtual private network. The purpose of this slide is to showcase the difference as well as the relationship between three security technologies such as zero trust, SDP and VPN.
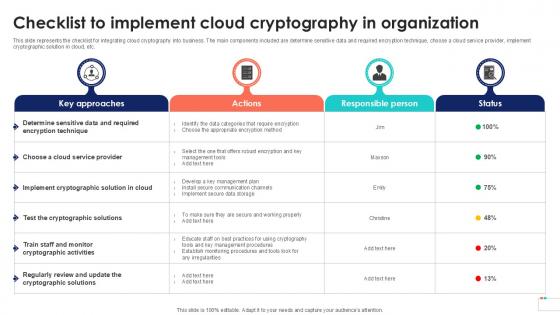
Checklist To Implement Cloud Data Security In Cloud Computing Ppt Powerpoint
This slide represents the checklist for integrating cloud cryptography into business. The main components included are determine sensitive data and required encryption technique, choose a cloud service provider, implement cryptographic solution in cloud, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Checklist To Implement Cloud Data Security In Cloud Computing Ppt Powerpoint can be your best option for delivering a presentation. Represent everything in detail using Checklist To Implement Cloud Data Security In Cloud Computing Ppt Powerpoint and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide represents the checklist for integrating cloud cryptography into business. The main components included are determine sensitive data and required encryption technique, choose a cloud service provider, implement cryptographic solution in cloud, etc.

Internet Of Things Security Ppt Powerpoint Presentation Complete Deck With Slides
If designing a presentation takes a lot of your time and resources and you are looking for a better alternative, then this Internet Of Things Security Ppt Powerpoint Presentation Complete Deck With Slides is the right fit for you. This is a prefabricated set that can help you deliver a great presentation on the topic. All the twenty eight slides included in this sample template can be used to present a birds-eye view of the topic. These slides are also fully editable, giving you enough freedom to add specific details to make this layout more suited to your business setting. Apart from the content, all other elements like color, design, theme are also replaceable and editable. This helps in designing a variety of presentations with a single layout. Not only this, you can use this PPT design in formats like PDF, PNG, and JPG once downloaded. Therefore, without any further ado, download and utilize this sample presentation as per your liking. Our Internet Of Things Security Ppt Powerpoint Presentation Complete Deck With Slides are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
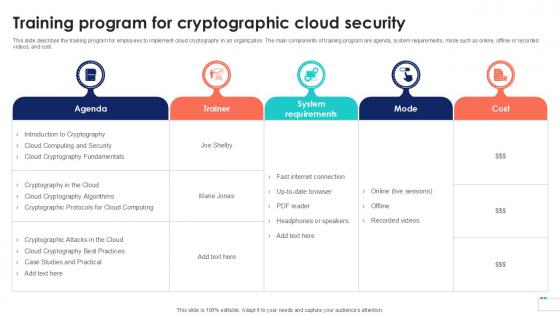
Training Program For Cryptographic Data Security In Cloud Computing Ppt Powerpoint
This slide describes the training program for employees to implement cloud cryptography in an organization. The main components of training program are agenda, system requirements, mode such as online, offline or recorded videos, and cost. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Training Program For Cryptographic Data Security In Cloud Computing Ppt Powerpoint can be your best option for delivering a presentation. Represent everything in detail using Training Program For Cryptographic Data Security In Cloud Computing Ppt Powerpoint and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide describes the training program for employees to implement cloud cryptography in an organization. The main components of training program are agenda, system requirements, mode such as online, offline or recorded videos, and cost.

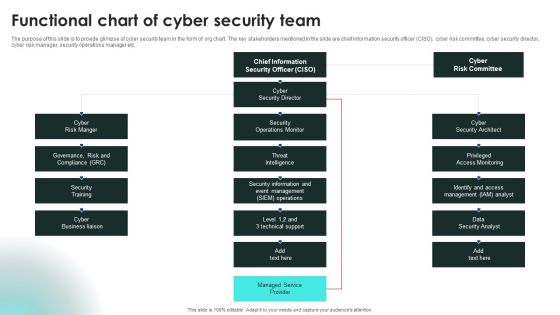
Prevention Of Information Functional Chart Of Cyber Security Team Themes PDF
The purpose of this slide is to provide glimpse of cyber security team in the form of org chart. The key stakeholders mentioned in the slide are chief information security officer CISO, cyber risk committee, cyber security director, cyber risk manager, security operations manager etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Prevention Of Information Functional Chart Of Cyber Security Team Themes PDF can be your best option for delivering a presentation. Represent everything in detail using Prevention Of Information Functional Chart Of Cyber Security Team Themes PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
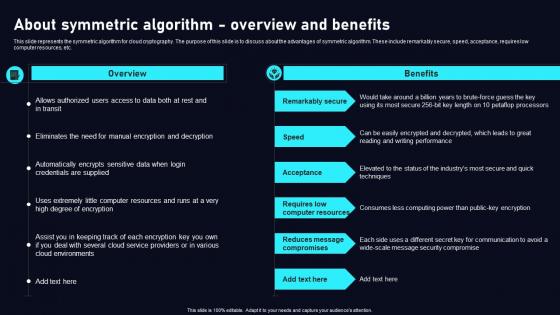
About Symmetric Algorithm Overview Cloud Data Security Using Cryptography Microsoft Pdf
This slide represents the symmetric algorithm for cloud cryptography. The purpose of this slide is to discuss about the advantages of symmetric algorithm. These include remarkably secure, speed, acceptance, requires low computer resources, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. About Symmetric Algorithm Overview Cloud Data Security Using Cryptography Microsoft Pdf can be your best option for delivering a presentation. Represent everything in detail using About Symmetric Algorithm Overview Cloud Data Security Using Cryptography Microsoft Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide represents the symmetric algorithm for cloud cryptography. The purpose of this slide is to discuss about the advantages of symmetric algorithm. These include remarkably secure, speed, acceptance, requires low computer resources, etc.
Implementing Cybersecurity Awareness Program To Prevent Attacks Functional Chart Of Cyber Security Team Inspiration PDF
The purpose of this slide is to provide glimpse of cyber security team in the form of org chart. The key stakeholders mentioned in the slide are chief information security officer CISO, cyber risk committee, cyber security director, cyber risk manager, security operations manager etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Implementing Cybersecurity Awareness Program To Prevent Attacks Functional Chart Of Cyber Security Team Inspiration PDF can be your best option for delivering a presentation. Represent everything in detail using Implementing Cybersecurity Awareness Program To Prevent Attacks Functional Chart Of Cyber Security Team Inspiration PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Functional Chart Of Cyber Security Team Ppt Layouts Graphics Example PDF
The purpose of this slide is to provide glimpse of cyber security team in the form of org chart. The key stakeholders mentioned in the slide are chief information security officer CISO, cyber risk committee, cyber security director, cyber risk manager, security operations manager etc. Get a simple yet stunning designed Functional Chart Of Cyber Security Team Ppt Layouts Graphics Example PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Functional Chart Of Cyber Security Team Ppt Layouts Graphics Example PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Cyber Terrorism Assault IT Infrastructure Cyber Security Budget Against Cyber Terrorism FY19 20 Themes PDF
This slide depicts the IT infrastructure budget of incorporating cyber security, as well as the cost of each activity to the company.Deliver and pitch your topic in the best possible manner with this cyber terrorism assault it infrastructure cyber security budget against cyber terrorism fy19 20 themes pdf Use them to share invaluable insights on cloud security, integrated risk management, identify access management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Chart Showing Technology Threats Methods And Technology For Cyber Security Ppt PowerPoint Presentation Ideas Slideshow PDF
Presenting chart showing technology threats methods and technology for cyber security ppt powerpoint presentation ideas slideshow pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including computer security attributes, attack methods, technology for internet security, confidentiality, integrity, privacy, availability. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Data Safety Initiatives Checklist For Effectively Managing Asset Security Themes PDF
Following slide displays system management checklist that company will use for effectively managing asset security. It also includes system management activities and frequency of performing them. Deliver and pitch your topic in the best possible manner with this data safety initiatives checklist for effectively managing asset security themes pdf. Use them to share invaluable insights on system monitoring, data backup, security patches and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
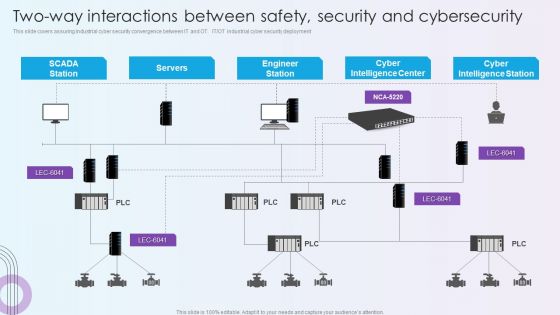
Digitalization Of Operative Enterprises Two Way Interactions Between Safety Security And Cybersecurity Themes PDF
This slide covers assuring industrial cyber security convergence between IT and OT. IT or OT industrial cyber security deployment. Deliver and pitch your topic in the best possible manner with this Digitalization Of Operative Enterprises Two Way Interactions Between Safety Security And Cybersecurity Themes PDF. Use them to share invaluable insights on Cyber Intelligence Center, Cyber Intelligence Station, Engineer Station and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
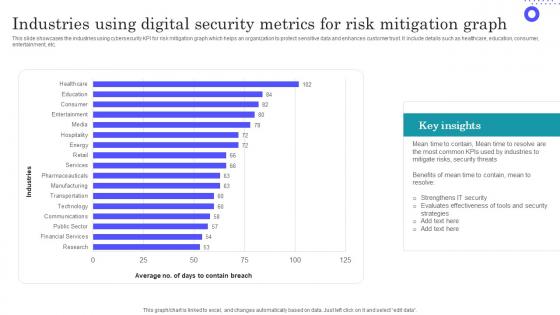
Industries Using Digital Security Metrics For Risk Mitigation Graph Inspiration Pdf
Showcasing this set of slides titled Industries Using Digital Security Metrics For Risk Mitigation Graph Inspiration Pdf The topics addressed in these templates are Evaluates Effectiveness, Most Common, Key Insights All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcases the industries using cybersecurity KPI for risk mitigation graph which helps an organization to protect sensitive data and enhances customer trust. It include details such as healthcare, education, consumer, entertainment, etc.
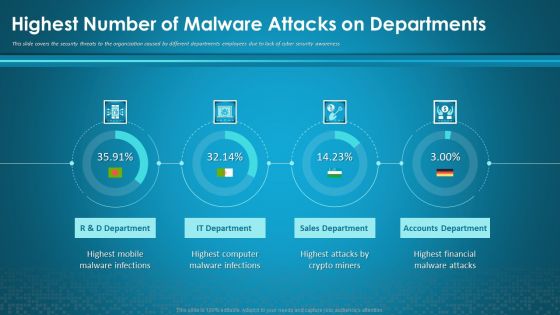
Organizational Network Security Awareness Staff Learning Highest Number Of Malware Attacks On Departments Information PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. Deliver and pitch your topic in the best possible manner with this organizational network security awareness staff learning highest number of malware attacks on departments information pdf. Use them to share invaluable insights on sales department, accounts department, financial, computer, mobile and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
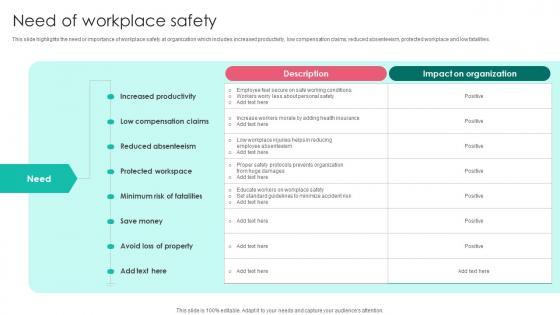
Need Of Workplace Safety Workplace Safety Protocol And Security Practices Template Pdf
This slide highlights the need or importance of workplace safety at organization which includes increased productivity, low compensation claims, reduced absenteeism, protected workplace and low fatalities. Retrieve professionally designed Need Of Workplace Safety Workplace Safety Protocol And Security Practices Template Pdf to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide highlights the need or importance of workplace safety at organization which includes increased productivity, low compensation claims, reduced absenteeism, protected workplace and low fatalities.
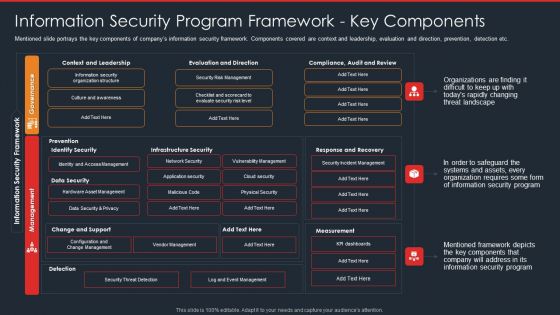
Data Safety Initiatives Information Security Program Framework Key Components Diagrams PDF
Mentioned slide portrays the key components of companys information security framework. Components covered are context and leadership, evaluation and direction, prevention, detection etc. Deliver and pitch your topic in the best possible manner with this data safety initiatives information security program framework key components diagrams pdf. Use them to share invaluable insights on governance, management, context and leadership, evaluation and direction, infrastructure security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cybersecurity Risk Administration Plan Current Security Infrastructure Performance Analysis Clipart PDF
Mentioned slide displays performance analysis of current security infrastructure based on NIST core functions. Core functions included are identify, protect, detect, respond, recover. Deliver an awe inspiring pitch with this creative Cybersecurity Risk Administration Plan Current Security Infrastructure Performance Analysis Clipart PDF bundle. Topics like Asset Management, Protect Data Security, Incident Mitigation Plan can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
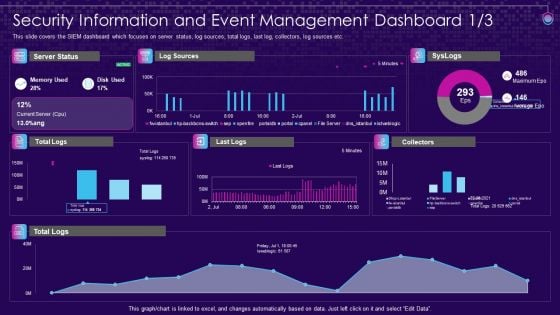
SIEM Services Security Information And Event Management Ppt File Objects PDF
This slide covers the SIEM dashboard which focuses on security events, event categories, data sources, logger event, multiple events, etc. Deliver an awe inspiring pitch with this creative siem services security information and event management ppt file objects pdf bundle. Topics like security information and event management dashboard can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
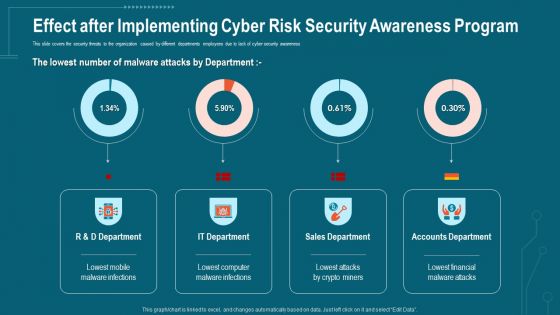
Companys Data Safety Recognition Effect After Implementing Cyber Risk Security Awareness Program Formats PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. Deliver an awe-inspiring pitch with this creative companys data safety recognition effect after implementing cyber risk security awareness program formats pdf bundle. Topics like sales department, accounts department, it department can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
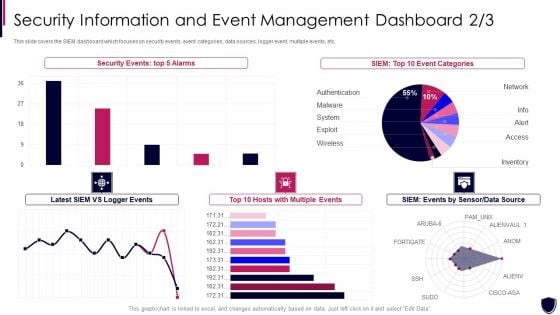
Enhancing Cyber Safety With Vulnerability Administration Security Information And Event Formats PDF
This slide covers the SIEM dashboard which focuses on security events, event categories, data sources, logger event, multiple events, etc. Deliver an awe inspiring pitch with this creative enhancing cyber safety with vulnerability administration security information and event formats pdf bundle. Topics like security events, event categories, data source, multiple events can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
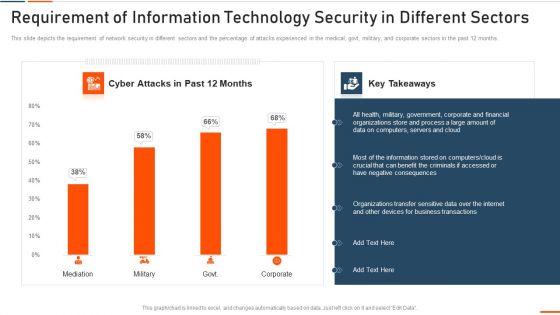
Requirement Of Information Technology Security In Different Sectors Ppt Ideas Shapes PDF
This slide depicts the requirement of network security in different sectors and the percentage of attacks experienced in the medical, govt, military, and corporate sectors in the past 12 months. Deliver an awe inspiring pitch with requirement of information technology security in different sectors ppt ideas shapes pdf bundle. Topics like requirement of information technology security in different sectors can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Quarterly Comparison Of Security For Cloud Based Systems Threats Infographics PDF
This slide shows the various types of cloud security threats occurred during four quarters. It includes phishing, malware, IoT and password attacks. Pitch your topic with ease and precision using this Quarterly Comparison Of Security For Cloud Based Systems Threats Infographics PDF. This layout presents information on Quarterly Comparison Of Security, Cloud Based Systems Threats. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
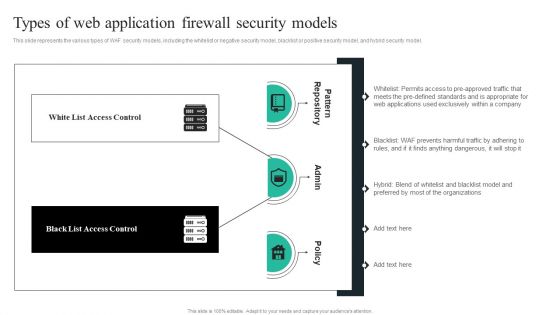
WAF Introduction Types Of Web Application Firewall Security Models Information PDF
This slide represents the various types of WAF security models, including the whitelist or negative security model, blacklist or positive security model, and hybrid security model. Are you searching for a WAF Introduction Types Of Web Application Firewall Security Models Information PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal. With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download WAF Introduction Types Of Web Application Firewall Security Models Information PDF from Slidegeeks today.
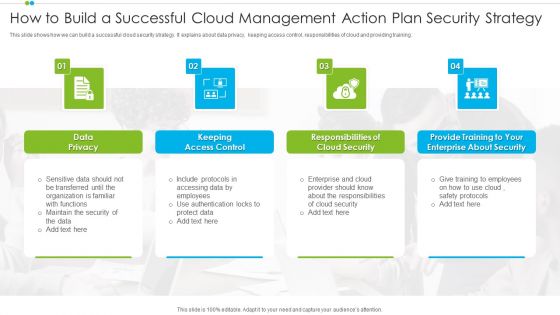
How To Build A Successful Cloud Management Action Plan Security Strategy Sample PDF
This slide shows how we can build a successful cloud security strategy. It explains about data privacy, keeping access control, responsibilities of cloud and providing training.Presenting How To Build A Successful Cloud Management Action Plan Security Strategy Sample PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Security, Enterprise, Data Privacy. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Website Designing And Development Service Security Web Development Technique Themes PDF
This slide represents the security development and how developers act as ethical hackers to prevent malicious attacks and reveal their vulnerabilities.This is a Website Designing And Development Service Security Web Development Technique Themes PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Network Security, Content Security, Loopholes Or Shortcomings You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
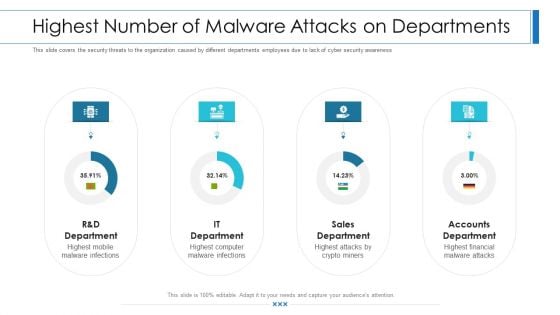
Workforce Security Realization Coaching Plan Highest Number Of Malware Attacks On Departments Professional PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. Deliver an awe-inspiring pitch with this creative workforce security realization coaching plan highest number of malware attacks on departments professional pdf bundle. Topics like sales department, accounts department, it department can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
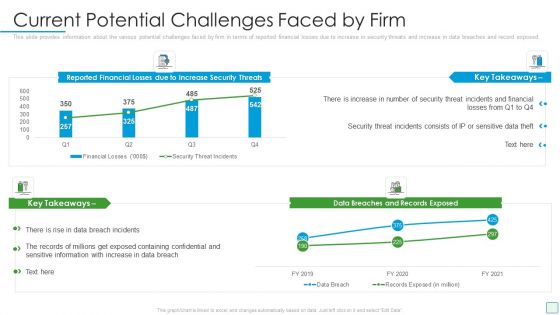
Developing Firm Security Strategy Plan Current Potential Challenges Faced By Firm Designs PDF
This slide provides information about the various potential challenges faced by firm in terms of reported financial losses due to increase in security threats and increase in data breaches and record exposed. Deliver an awe inspiring pitch with this creative developing firm security strategy plan current potential challenges faced by firm designs pdf bundle. Topics like security, financial can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
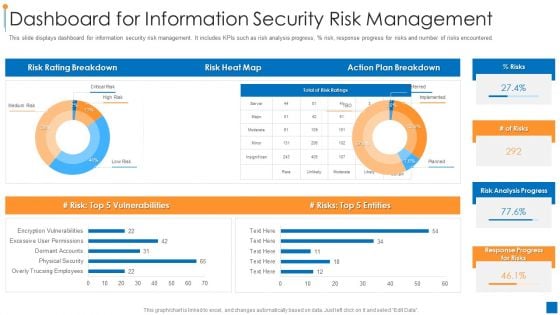
International Organization Standardization 270001 Dashboard For Information Security Risk Management Pictures PDF
This slide displays dashboard for information security risk management. It includes KPIs such as risk analysis progress, parcent risk, response progress for risks and number of risks encountered. Deliver an awe inspiring pitch with this creative international organization standardization 270001 dashboard for information security risk management pictures pdf bundle. Topics like dashboard for information security risk management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
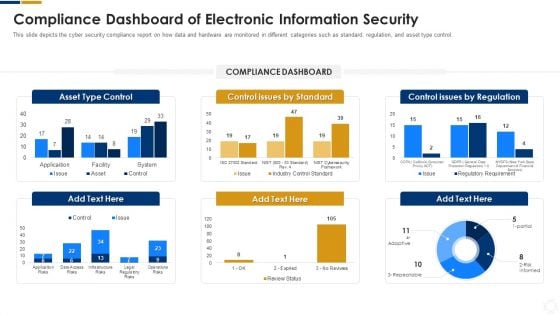
Cybersecurity Compliance Dashboard Of Electronic Information Security Ppt Outline Graphic Tips PDF
This slide depicts the cyber security compliance report on how data and hardware are monitored in different categories such as standard, regulation, and asset type control. Deliver an awe inspiring pitch with this creative cybersecurity compliance dashboard of electronic information security ppt outline graphic tips pdf bundle. Topics like compliance dashboard of electronic information security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
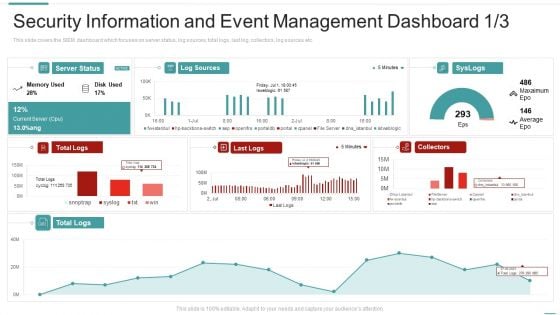
Risk Recognition Automation Security Information And Event Management Dashboard Ppt Model Elements PDF
This slide covers the SIEM dashboard which focuses on security events, event categories, data sources, logger event, multiple events, etc. Deliver an awe inspiring pitch with this creative risk recognition automation security information and event management dashboard ppt model elements pdf bundle. Topics like security information and event management dashboard can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
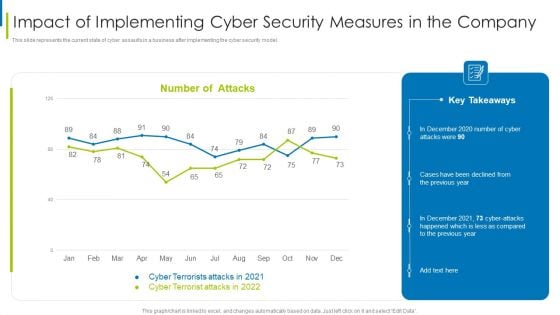
Cyber Terrorism Assault Impact Of Implementing Cyber Security Measures In The Company Professional PDF
This slide represents the current state of cyber assaults in a business after implementing the cyber security model.Deliver an awe inspiring pitch with this creative cyber terrorism assault impact of implementing cyber security measures in the company professional pdf bundle. Topics like impact of implementing cyber security measures in the company can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
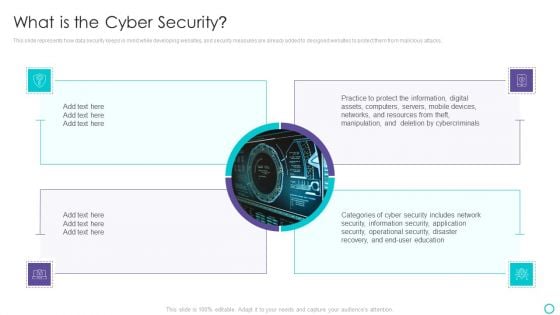
Website Designing And Development Service What Is The Cyber Security Diagrams PDF
This slide represents how data security keeps in mind while developing websites, and security measures are already added to designed websites to protect them from malicious attacks.Presenting Website Designing And Development Service What Is The Cyber Security Diagrams PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Practice To Protect, Information Digital, Operational Security In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
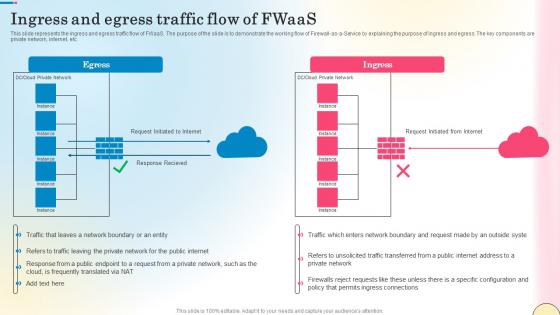
Ingress And Egress Traffic Flow Of Fwaas Network Security Elements Pdf
This slide represents the ingress and egress traffic flow of FWaaS. The purpose of the slide is to demonstrate the working flow of Firewall-as-a-Service by explaining the purpose of ingress and egress. The key components are private network, internet, etc. Are you searching for a Ingress And Egress Traffic Flow Of Fwaas Network Security Elements Pdf that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Ingress And Egress Traffic Flow Of Fwaas Network Security Elements Pdf from Slidegeeks today. This slide represents the ingress and egress traffic flow of FWaaS. The purpose of the slide is to demonstrate the working flow of Firewall-as-a-Service by explaining the purpose of ingress and egress. The key components are private network, internet, etc.
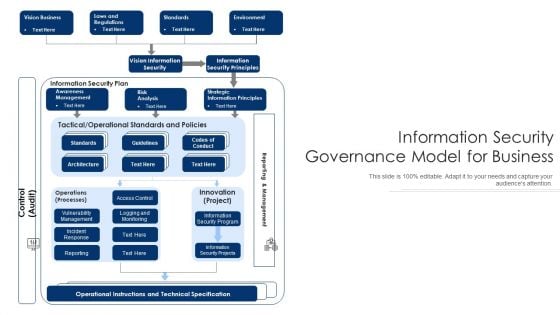
Information Security Governance Model For Business Ppt PowerPoint Presentation Show Graphics PDF
Persuade your audience using this information security governance model for business ppt powerpoint presentation show graphics pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including vision information security, information security principles, operational instructions and technical specification. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Smart Home Security Solutions Company Profile Executive Leadership And Management Team Themes PDF
This slide highlights the security company leadership and management team which includes president and CEO, executive vice president of finance, EVP home security, chief administration officer. This is a Smart Home Security Solutions Company Profile Executive Leadership And Management Team Themes PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Executive Leadership Management, Team Business Security, Financial Management Services. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
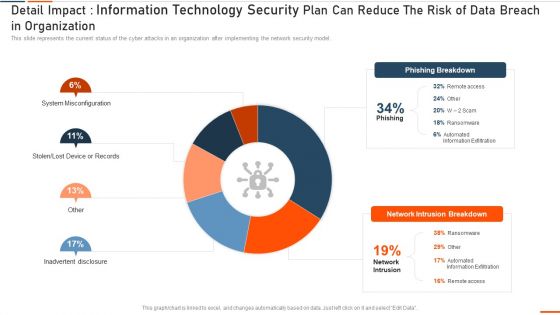
Detail Impact Information Technology Security Plan Can Reduce Ppt Show Slide Download PDF
This slide represents the current status of the cyber attacks in an organization after implementing the network security model. Deliver an awe inspiring pitch with this creative it security detail impact detail impact information technology security plan can reduce ppt show slide download pdf bundle. Topics like detail impact information technology security plan can reduce the risk of data breach in organization can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cloud Technology Risks With Security Incident Management Ppt PowerPoint Presentation Gallery Graphics Template PDF
Presenting cloud technology risks with security incident management ppt powerpoint presentation gallery graphics template pdf. to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including identification and allowance, management interface vulnerability, security incident management, application security management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
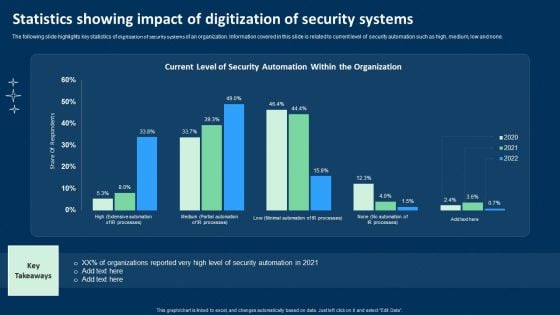
Statistics Showing Impact Of Digitization Of Security Systems Ppt Show Ideas PDF
The following slide highlights key statistics of digitization of security systems of an organization. Information covered in this slide is related to current level of security automation such as high, medium, low and none. Showcasing this set of slides titled Statistics Showing Impact Of Digitization Of Security Systems Ppt Show Ideas PDF. The topics addressed in these templates are Current Level, Security Automation, Organization. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Measures To Maintain Data Security In Datafication Ethical Dimensions Of Datafication Infographics Pdf
This slide talks about the measures to keep data secure in datafication, including legal requirements, technical measures and business practices, containing marketing campaigns, sales operations and customer service. The technical measures include encryption, firewalls, and access controls. Do you know about Slidesgeeks Measures To Maintain Data Security In Datafication Ethical Dimensions Of Datafication Infographics Pdf These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide talks about the measures to keep data secure in datafication, including legal requirements, technical measures and business practices, containing marketing campaigns, sales operations and customer service. The technical measures include encryption, firewalls, and access controls.
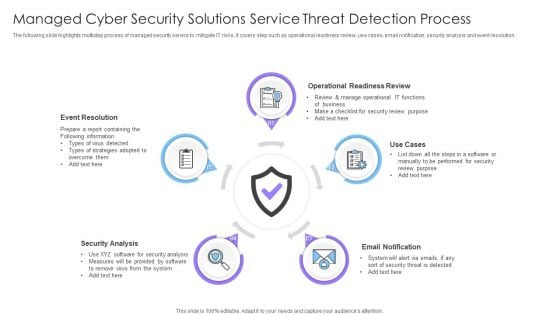
Managed Cyber Security Solutions Service Threat Detection Process Ppt Portfolio Pictures PDF
The following slide highlights multistep process of managed security service to mitigate IT risks. It covers step such as operational readiness review, use cases, email notification, security analysis and event resolution. Presenting Managed Cyber Security Solutions Service Threat Detection Process Ppt Portfolio Pictures PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Event Resolution, Security Analysis, Use Cases, Operational Readiness Review. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
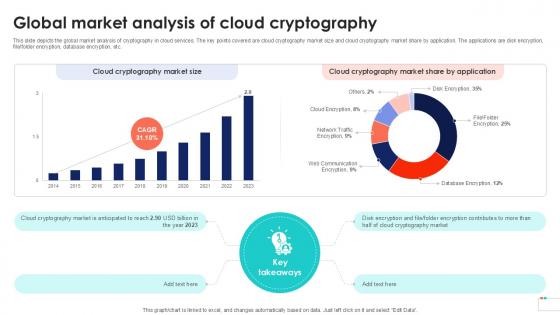
Global Market Analysis Of Cloud Data Security In Cloud Computing Ppt Powerpoint
This slide depicts the global market analysis of cryptography in cloud services. The key points covered are cloud cryptography market size and cloud cryptography market share by application. The applications are disk encryption, file, folder encryption, database encryption, etc. Are you searching for a Global Market Analysis Of Cloud Data Security In Cloud Computing Ppt Powerpoint that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Global Market Analysis Of Cloud Data Security In Cloud Computing Ppt Powerpoint from Slidegeeks today. This slide depicts the global market analysis of cryptography in cloud services. The key points covered are cloud cryptography market size and cloud cryptography market share by application. The applications are disk encryption, file, folder encryption, database encryption, etc.

Key Facts Voice Assistance Security Platform Investor Funding Presentation Demonstration Pdf
The following slide showcases various factors that presents how company is becoming a leading in market. It highlights growth rate, current ratio, quick ratio, gross profit, net profit and EPS. Retrieve professionally designed Key Facts Voice Assistance Security Platform Investor Funding Presentation Demonstration Pdf to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. The following slide showcases various factors that presents how company is becoming a leading in market. It highlights growth rate, current ratio, quick ratio, gross profit, net profit and EPS.


 Continue with Email
Continue with Email

 Home
Home


































