Security Icon

Global Data Security Industry Report Geographical Analysis For Cybersecurity Industry IR SS V
The slide highlights the geographical summary of current state of cybersecurity industry. The purpose of the slide is to provide insights on cybersecurity landscape, trends, development at regional levels. It helps stakeholders in understanding the market dynamics, regulatory environments and potential growth opportunities. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Global Data Security Industry Report Geographical Analysis For Cybersecurity Industry IR SS V and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates The slide highlights the geographical summary of current state of cybersecurity industry. The purpose of the slide is to provide insights on cybersecurity landscape, trends, development at regional levels. It helps stakeholders in understanding the market dynamics, regulatory environments and potential growth opportunities.
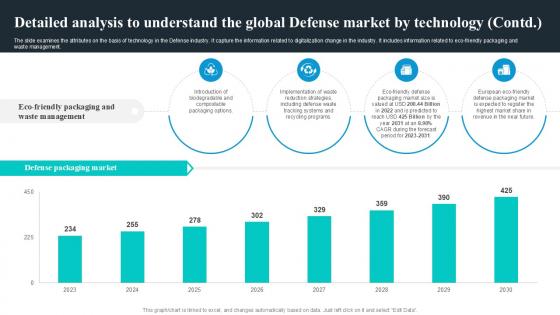
Detailed Analysis To Understand Global Security Industry PPT PowerPoint IR SS V
The slide examines the attributes on the basis of technology in the Defense industry. It capture the information related to digitalization change in the industry. It includes information related to eco-friendly packaging and waste management. Present like a pro with Detailed Analysis To Understand Global Security Industry PPT PowerPoint IR SS V. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. The slide examines the attributes on the basis of technology in the Defense industry. It capture the information related to digitalization change in the industry. It includes information related to eco-friendly packaging and waste management.
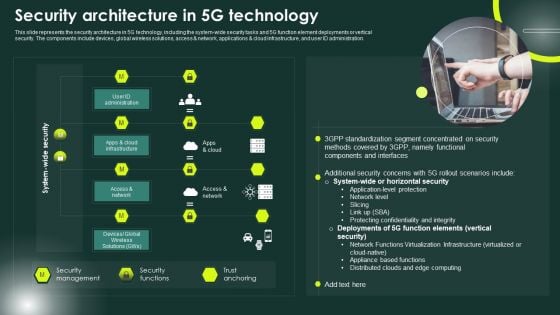
5G Network Applications And Features Security Architecture In 5G Technology Elements PDF
This slide represents the security architecture in 5G technology, including the system-wide security tasks and 5G function element deployments or vertical security. The components include devices, global wireless solutions, access and network, applications and cloud infrastructure, and user ID administration. Whether you have daily or monthly meetings, a brilliant presentation is necessary. 5G Network Applications And Features Security Architecture In 5G Technology Elements PDF can be your best option for delivering a presentation. Represent everything in detail using 5G Network Applications And Features Security Architecture In 5G Technology Elements PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Guidelines To Create An Advanced Security Management Plan Ppt PowerPoint Presentation Complete Deck With Slides
This complete deck acts as a great communication tool. It helps you in conveying your business message with personalized sets of graphics, icons etc. Comprising a set of fortytwo slides, this complete deck can help you persuade your audience. It also induces strategic thinking as it has been thoroughly researched and put together by our experts. Not only is it easily downloadable but also editable. The color, graphics, theme any component can be altered to fit your individual needs. So grab it now.

Products And Services Offered Voice Assistance Security Platform Investor Funding Rules Pdf
This slide represents product and solution categories offered by business which are session replays, heatmaps, team dashboards, user journeys, user segmentation, funnel analytics, events analytics, issue analytics, 3rd party integrations, understand UX, increase conversions, drive engagement and resolve issues. Do you know about Slidesgeeks Products And Services Offered Voice Assistance Security Platform Investor Funding Rules Pdf These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide represents product and solution categories offered by business which are session replays, heatmaps, team dashboards, user journeys, user segmentation, funnel analytics, events analytics, issue analytics, 3rd party integrations, understand UX, increase conversions, drive engagement and resolve issues.
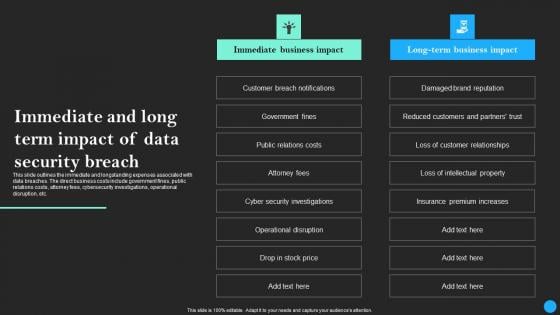
Immediate And Long Term Impact Of Data Security Breach Data Breach Prevention Topics Pdf
This slide outlines the immediate and longstanding expenses associated with data breaches. The direct business costs include government fines, public relations costs, attorney fees, cybersecurity investigations, operational disruption, etc. Retrieve professionally designed Immediate And Long Term Impact Of Data Security Breach Data Breach Prevention Topics Pdf to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide outlines the immediate and longstanding expenses associated with data breaches. The direct business costs include government fines, public relations costs, attorney fees, cybersecurity investigations, operational disruption, etc.

Next Step For Safety And Security System Services Proposal One Pager Sample Example Document
The following slide displays the next step that the organization has to take once the security proposal has been signed, these steps can be team meeting ,on-site visit etc. Presenting you an exemplary Next Step For Safety And Security System Services Proposal One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Next Step For Safety And Security System Services Proposal One Pager Sample Example Document brilliant piece now.
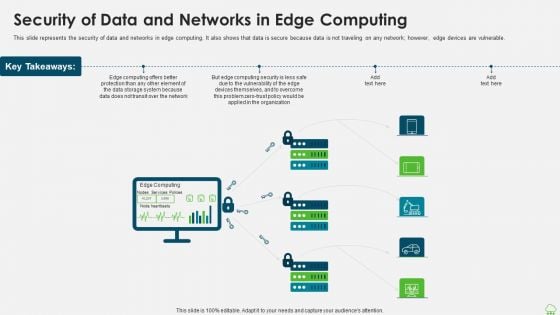
Distributed Computing IT Security Of Data And Networks In Edge Computing Themes PDF
This slide represents the security of data and networks in edge computing. It also shows that data is secure because data is not traveling on any network however, edge devices are vulnerable. Presenting distributed computing it security of data and networks in edge computing themes pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like organization, data storage, computing security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
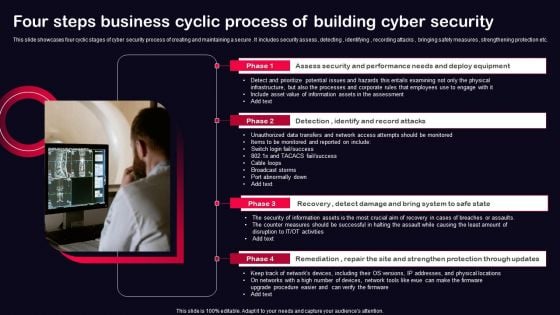
Four Steps Business Cyclic Process Of Building Cyber Security Ppt PowerPoint Presentation File Model PDF
This slide showcases four cyclic stages of cyber security process of creating and maintaining a secure . It includes security assess , detecting , identifying , recording attacks , bringing safety measures , strengthening protection etc. Presenting Four Steps Business Cyclic Process Of Building Cyber Security Ppt PowerPoint Presentation File Model PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Recovery, Remediation, Repair, Site And Strengthen, Protection Through Updates. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
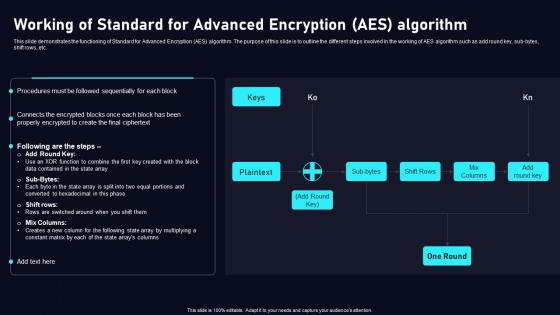
Working Of Standard For Advanced Cloud Data Security Using Cryptography Diagrams Pdf
This slide demonstrates the functioning of Standard for Advanced Encryption AES algorithm. The purpose of this slide is to outline the different steps involved in the working of AES algorithm such as add round key, sub bytes, shift rows, etc. Create an editableWorking Of Standard For Advanced Cloud Data Security Using Cryptography Diagrams Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save timeWorking Of Standard For Advanced Cloud Data Security Using Cryptography Diagrams Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide demonstrates the functioning of Standard for Advanced Encryption AES algorithm. The purpose of this slide is to outline the different steps involved in the working of AES algorithm such as add round key, sub bytes, shift rows, etc.
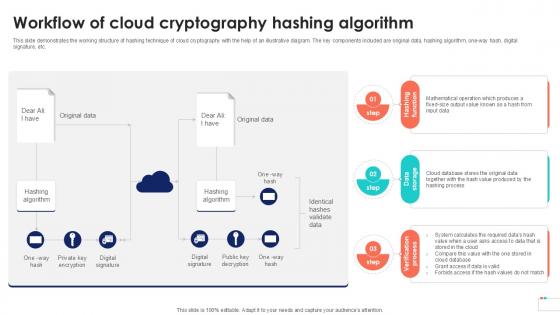
Workflow Of Cloud Cryptography Data Security In Cloud Computing Ppt Example
This slide demonstrates the working structure of hashing technique of cloud cryptography with the help of an illustrative diagram. The key components included are original data, hashing algorithm, one-way hash, digital signature, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Workflow Of Cloud Cryptography Data Security In Cloud Computing Ppt Example is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Workflow Of Cloud Cryptography Data Security In Cloud Computing Ppt Example and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide demonstrates the working structure of hashing technique of cloud cryptography with the help of an illustrative diagram. The key components included are original data, hashing algorithm, one-way hash, digital signature, etc.
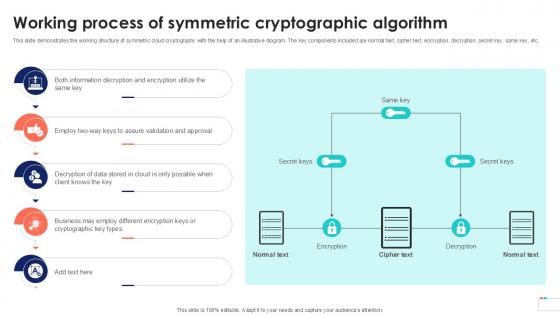
Working Process Of Symmetric Data Security In Cloud Computing Ppt Template
This slide demonstrates the working structure of symmetric cloud cryptography with the help of an illustrative diagram. The key components included are normal text, cipher text, encryption, decryption, secret key, same key, etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Working Process Of Symmetric Data Security In Cloud Computing Ppt Template was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Working Process Of Symmetric Data Security In Cloud Computing Ppt Template This slide demonstrates the working structure of symmetric cloud cryptography with the help of an illustrative diagram. The key components included are normal text, cipher text, encryption, decryption, secret key, same key, etc.

Global Data Security Industry Report Global Cybersecurity Industry A Quick Snapshot IR SS V
This slide provides a glimpse of key highlights of the cybersecurity industry, enabling executives to grasp the main findings quickly. It serves as a snapshot highlighting revenue, CAGR, fastest growing region, segments, regional breakdown, and key market players. If you are looking for a format to display your unique thoughts, then the professionally designed Global Data Security Industry Report Global Cybersecurity Industry A Quick Snapshot IR SS V is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Global Data Security Industry Report Global Cybersecurity Industry A Quick Snapshot IR SS V and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide provides a glimpse of key highlights of the cybersecurity industry, enabling executives to grasp the main findings quickly. It serves as a snapshot highlighting revenue, CAGR, fastest growing region, segments, regional breakdown, and key market players.
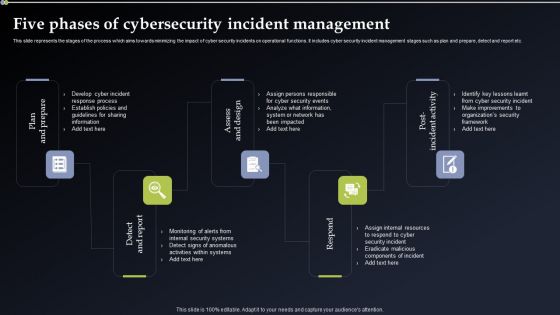
Deploying Cyber Security Incident Response Administration Five Phases Of Cybersecurity Incident Management Diagrams PDF
This slide represents the stages of the process which aims towards minimizing the impact of cyber security incidents on operational functions. It includes cyber security incident management stages such as plan and prepare, detect and report etc. There are so many reasons you need a Deploying Cyber Security Incident Response Administration Five Phases Of Cybersecurity Incident Management Diagrams PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
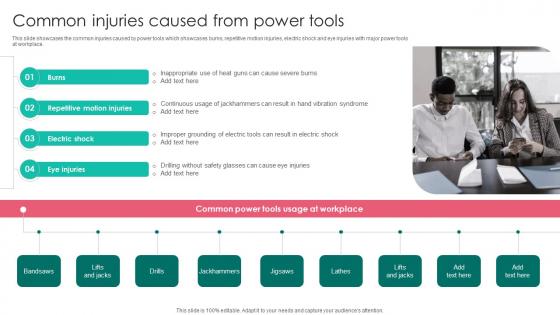
Common Injuries Caused Power Workplace Safety Protocol And Security Practices Portrait Pdf
This slide showcases the common injuries caused by power tools which showcases burns, repetitive motion injuries, electric shock and eye injuries with major power tools at workplace. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Common Injuries Caused Power Workplace Safety Protocol And Security Practices Portrait Pdf can be your best option for delivering a presentation. Represent everything in detail using Common Injuries Caused Power Workplace Safety Protocol And Security Practices Portrait Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide showcases the common injuries caused by power tools which showcases burns, repetitive motion injuries, electric shock and eye injuries with major power tools at workplace.

How To Configure Firewall As A Service Fwaas Network Security Diagrams Pdf
This slide talks about the steps of configuring Firewall-as-a-Service. The purpose of this slide is to illustrate how FWaaS packages can be installed and configured. The key steps explained in this slide are enable FWaaS and configure FWaaS. Welcome to our selection of the How To Configure Firewall As A Service Fwaas Network Security Diagrams Pdf. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today This slide talks about the steps of configuring Firewall-as-a-Service. The purpose of this slide is to illustrate how FWaaS packages can be installed and configured. The key steps explained in this slide are enable FWaaS and configure FWaaS.

Highest Number Of Malware Attacks On Departments Hacking Prevention Awareness Training For IT Security Themes PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. Deliver and pitch your topic in the best possible manner with this highest number of malware attacks on departments hacking prevention awareness training for it security themes pdf. Use them to share invaluable insights on r and d department, it department, accounts department, sales department and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Companys Data Safety Recognition Impact Of Security Awareness Training Demonstration PDF
This slide covers the good impact of security awareness program such as declining in the number of security threats which are phishing, network intrusion, inadvertent disclosure, stolen or lost devices or records and system misconfiguration. Deliver an awe-inspiring pitch with this creative companys data safety recognition impact of security awareness training demonstration pdf bundle. Topics like system misconfiguration, inadvertent disclosure, network intrusion can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
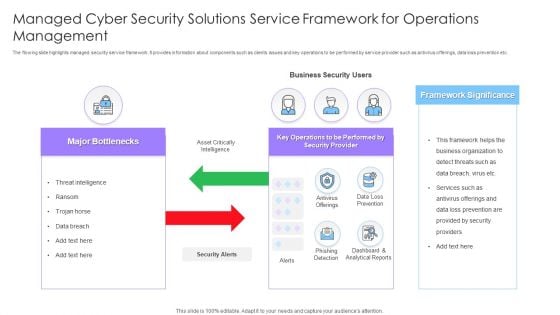
Managed Cyber Security Solutions Service Framework For Operations Management Ppt Styles Themes PDF
The flowing slide highlights managed security service framework. It provides information about components such as clients issues and key operations to be performed by service provider such as antivirus offerings, data loss prevention etc. Presenting Managed Cyber Security Solutions Service Framework For Operations Management Ppt Styles Themes PDF to dispense important information. This template comprises two stages. It also presents valuable insights into the topics including Framework Significance, Business Security Users, Major Bottlenecks. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
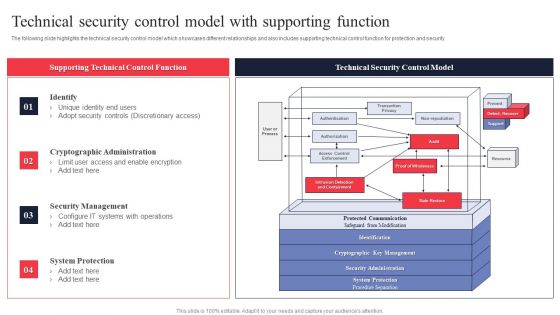
IT System Risk Management Guide Technical Security Control Model With Supporting Function Themes PDF
The following slide highlights the technical security control model which showcases different relationships and also includes supporting technical control function for protection and security. Slidegeeks has constructed IT System Risk Management Guide Technical Security Control Model With Supporting Function Themes PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.

Challenge And Solutions 2 Cloud Threats And Security Ppt Outline Design Inspiration PDF
This slide shows the problem that the company is facing related to cloud threats and security issues due to improper encryption and password protection. Additionally, the slide covers the key majors solutions which the company needs to follow. Deliver an awe inspiring pitch with this creative challenge and solutions 2 cloud threats and security ppt outline design inspiration pdf bundle. Topics like implement data encryption techniques to eliminate risk of infiltration, security and compliance risks are major considerations for the company, professional business can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
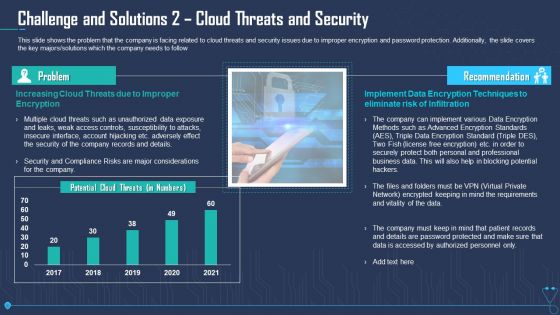
Challenge And Solutions 2 Cloud Threats And Security Ppt Gallery Images PDF
This slide shows the problem that the company is facing related to cloud threats and security issues due to improper encryption and password protection. Additionally, the slide covers the key majors or solutions which the company needs to follow. Deliver an awe inspiring pitch with this creative challenge and solutions 2 cloud threats and security ppt gallery images pdf bundle. Topics like challenge and solutions 2 cloud threats and security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Challenge And Solutions 2 Cloud Threats And Security Ppt Inspiration Slideshow PDF
This slide shows the problem that the company is facing related to cloud threats and security issues due to improper encryption and password protection. Additionally, the slide covers the key majors or solutions which the company needs to follow. Deliver and pitch your topic in the best possible manner with this challenge and solutions 2 cloud threats and security ppt inspiration slideshow pdf. Use them to share invaluable insights on security, risks, encryption methods, echniques and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
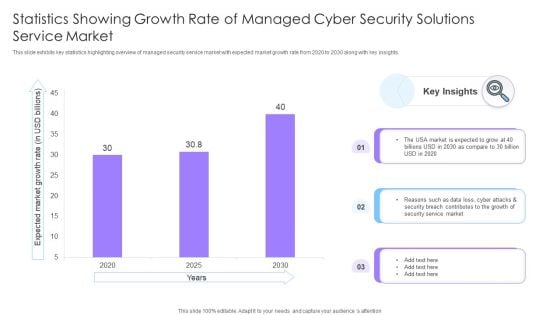
Statistics Showing Growth Rate Of Managed Cyber Security Solutions Service Market Ppt Show Inspiration PDF
This slide exhibits key statistics highlighting overview of managed security service market with expected market growth rate from 2020 to 2030 along with key insights. Pitch your topic with ease and precision using this Statistics Showing Growth Rate Of Managed Cyber Security Solutions Service Market Ppt Show Inspiration PDF. This layout presents information on Statistics Showing Growth, Cyber Security, Solutions Service Market. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
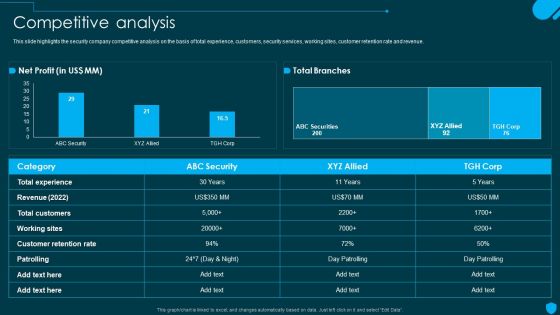
Security And Human Resource Services Business Profile Competitive Analysis Elements PDF
This slide highlights the security company competitive analysis on the basis of total experience, customers, security services, working sites, customer retention rate and revenue. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Security And Human Resource Services Business Profile Competitive Analysis Elements PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
Dashboard For Threat Tracking In Information Technology Security Ppt Portfolio Shapes PDF
This slide depicts the dashboard for threat tracking in network security by covering monthly threat status, current risk status, threat-based on the role, threats by owners, risk by threats, and threat report. Deliver and pitch your topic in the best possible manner with this dashboard for threat tracking in information technology security ppt portfolio shapes pdf. Use them to share invaluable insights on dashboard for threat tracking in information technology security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
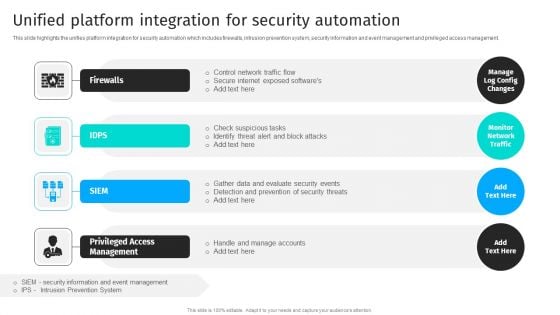
Security Automation To Analyze And Mitigate Cyberthreats Unified Platform Integration Themes PDF
This slide highlights the unifies platform integration for security automation which includes firewalls, intrusion prevention system, security information and event management and privileged access management.The Security Automation To Analyze And Mitigate Cyberthreats Unified Platform Integration Themes PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
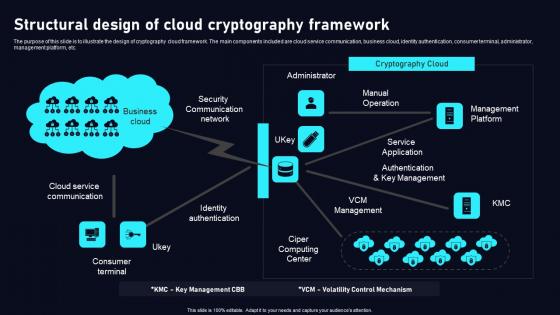
Structural Design Of Cloud Cryptography Cloud Data Security Using Cryptography Themes Pdf
The purpose of this slide is to illustrate the design of cryptography cloud framework. The main components included are cloud service communication, business cloud, identity authentication, consumer terminal, administrator, management platform, etc. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Structural Design Of Cloud Cryptography Cloud Data Security Using Cryptography Themes Pdf and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates The purpose of this slide is to illustrate the design of cryptography cloud framework. The main components included are cloud service communication, business cloud, identity authentication, consumer terminal, administrator, management platform, etc.

Your Requirement And Our Solution Proposal For Security Guard Services One Pager Sample Example Document
Purpose of the following slide is to show the project requirement and solution for security guard proposal, as it displays the key phases such as evaluating premise etc. Presenting you an exemplary Your Requirement And Our Solution Proposal For Security Guard Services One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Your Requirement And Our Solution Proposal For Security Guard Services One Pager Sample Example Document brilliant piece now.
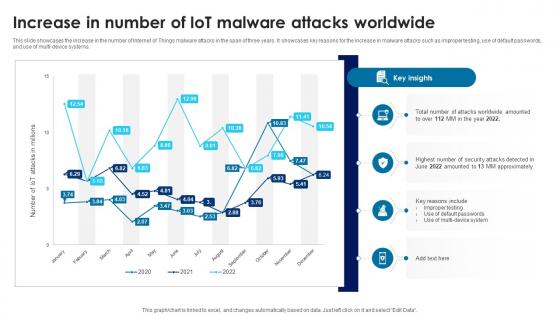
Building Trust With IoT Security Increase In Number Of IoT Malware Attacks Worldwide IoT SS V
This slide showcases the increase in the number of Internet of Things malware attacks in the span of three years. It showcases key reasons for the increase in malware attacks such as improper testing, use of default passwords, and use of multi-device systems. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Building Trust With IoT Security Increase In Number Of IoT Malware Attacks Worldwide IoT SS V to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide showcases the increase in the number of Internet of Things malware attacks in the span of three years. It showcases key reasons for the increase in malware attacks such as improper testing, use of default passwords, and use of multi-device systems.
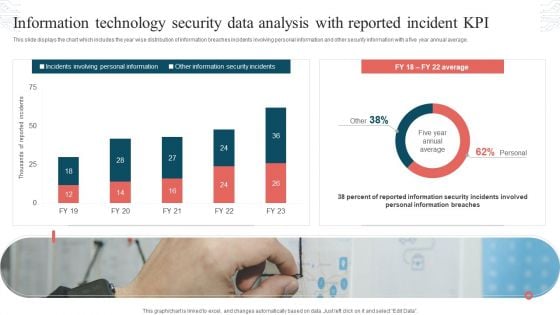
Information Technology Security Data Analysis With Reported Incident KPI Download PDF
This slide displays the chart which includes the year wise distribution of information breaches incidents involving personal information and other security information with a five year annual average. Showcasing this set of slides titled Information Technology Security Data Analysis With Reported Incident KPI Download PDF. The topics addressed in these templates are Incidents Involving, Personal Information, Other Information, Security Incidents. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Comparative Analysis Of Cloud And Traditional Computing It Security Diagrams PDF
This slide provide the difference between the cloud computer security and standard computer security that enable manager to choose the best strategy. It shows the variation of data centers, initial cost investment, price, time to market etc.Persuade your audience using this Comparative Analysis Of Cloud And Traditional Computing It Security Diagrams PDF. This PPT design covers one stage, thus making it a great tool to use. It also caters to a variety of topics including Provided Parties, Initial Cost Investment, Comparatively Longer. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Cybersecurity Dashboard For Threat Tracking In Electronic Information Security Ppt Ideas Graphics PDF
This slide depicts the dashboard for threat tracking in cyber security by covering monthly threat status, current risk status, threat based on the role, threats by owners, risk by threats, and threat report. Deliver an awe inspiring pitch with this creative cybersecurity dashboard for threat tracking in electronic information security ppt ideas graphics pdf bundle. Topics like dashboard for threat tracking in electronic information security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
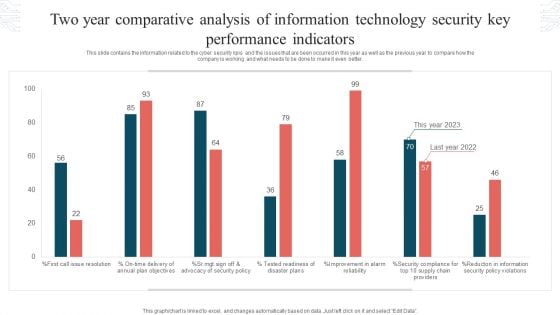
Two Year Comparative Analysis Of Information Technology Security Key Performance Indicators Graphics PDF
This slide contains the information related to the cyber security kpis and the issues that are been occurred in this year as well as the previous year to compare how the company is working and what needs to be done to make it even better. Showcasing this set of slides titled Two Year Comparative Analysis Of Information Technology Security Key Performance Indicators Graphics PDF. The topics addressed in these templates are Tested Readiness, Disaster Plans, Security Policy Violations. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
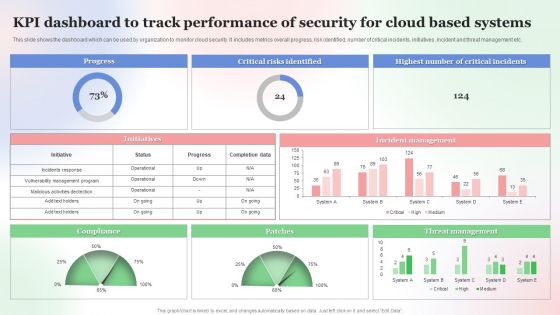
KPI Dashboard To Track Performance Of Security For Cloud Based Systems Clipart PDF
This slide shows the dashboard which can be used by organization to monitor cloud security. It includes metrics overall progress, risk identified, number of critical incidents, initiatives, incident and threat management etc. Showcasing this set of slides titled KPI Dashboard To Track Performance Of Security For Cloud Based Systems Clipart PDF. The topics addressed in these templates are Kpi Dashboard To Track, Performance Of Security, Cloud Based Systems . All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
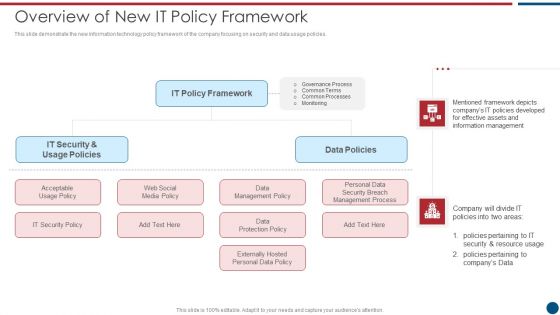
Risk Based Procedures To IT Security Overview Of New IT Policy Framework Guidelines PDF
This slide demonstrate the new information technology policy framework of the company focusing on security and data usage policies. Presenting Risk Based Procedures To IT Security Overview Of New IT Policy Framework Guidelines PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like IT Policy, Data Policies, IT Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
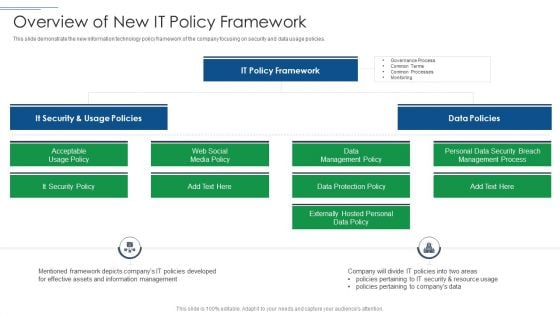
IT Security Risk Management Approach Introduction Overview Of New It Policy Framework Ideas PDF
This slide demonstrate the new information technology policy framework of the company focusing on security and data usage policies. Presenting IT Security Risk Management Approach Introduction Overview Of New It Policy Framework Ideas PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like It Security, It Policy Framework, Data Policies. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
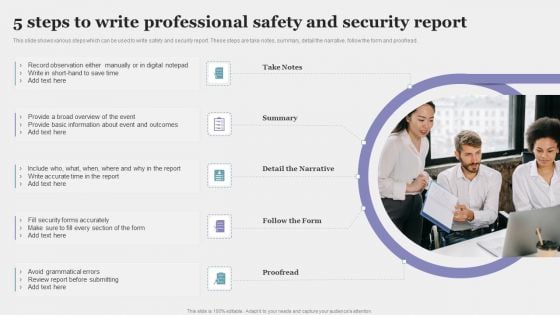
5 Steps To Write Professional Safety And Security Report Formats PDF
This slide shows various steps which can be used to write safety and security report. These steps are take notes, summary, detail the narrative, follow the form and proofread. Presenting 5 Steps To Write Professional Safety And Security Report Formats PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Security Forms Accurately, Basic Information. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
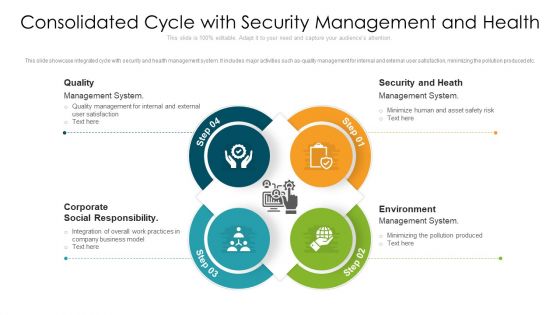
Consolidated Cycle With Security Management And Health Ppt PowerPoint Presentation File Show PDF
This slide showcase integrated cycle with security and health management system. It includes major activities such as-quality management for internal and external user satisfaction, minimizing the pollution produced etc. Presenting consolidated cycle with security management and health ppt powerpoint presentation file show pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including security and heath, corporate social responsibility, environment. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
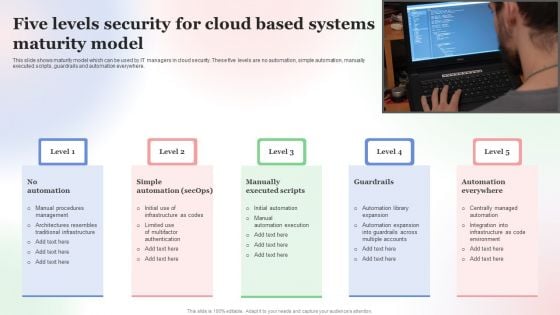
Five Levels Security For Cloud Based Systems Maturity Model Microsoft PDF
This slide shows maturity model which can be used by IT managers in cloud security. These five levels are no automation, simple automation, manually executed scripts, guardrails and automation everywhere. Presenting Five Levels Security For Cloud Based Systems Maturity Model Microsoft PDF to dispense important information. This template comprises Five stages. It also presents valuable insights into the topics including Five Levels Security, Cloud Based Systems, Maturity Model. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
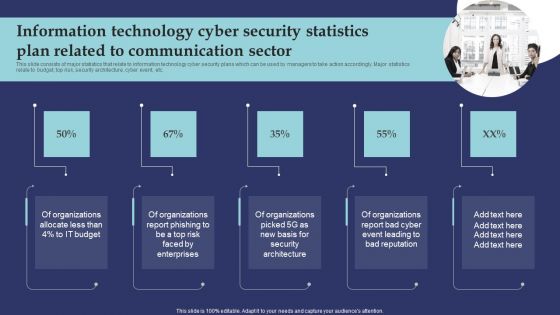
Information Technology Cyber Security Statistics Plan Related To Communication Sector Microsoft PDF
This slide consists of major statistics that relate to information technology cyber security plans which can be used by managers to take action accordingly. Major statistics relate to budget, top risk, security architecture, cyber event, etc. Presenting Information Technology Cyber Security Statistics Plan Related To Communication Sector Microsoft PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Organizations Allocate, Organizations Report Phishing, Organizations Report Bad Cyber. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
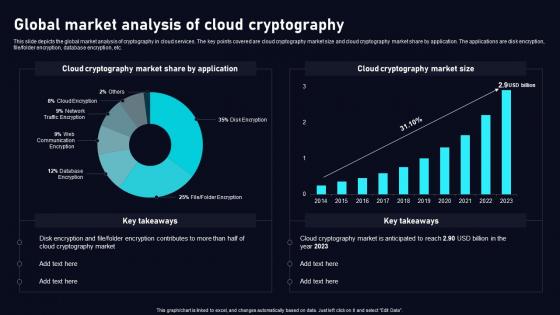
Global Market Analysis Of Cloud Data Security Using Cryptography Portrait Pdf
This slide depicts the global market analysis of cryptography in cloud services. The key points covered are cloud cryptography market size and cloud cryptography market share by application. The applications are disk encryption, file folder encryption, database encryption, etc. Do you know about Slidesgeeks Global Market Analysis Of Cloud Data Security Using Cryptography Portrait Pdf These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide depicts the global market analysis of cryptography in cloud services. The key points covered are cloud cryptography market size and cloud cryptography market share by application. The applications are disk encryption, file folder encryption, database encryption, etc.
Endpoint Security Protection Services Ppt PowerPoint Presentation Professional Backgrounds Cpb Pdf
Presenting this set of slides with name endpoint security protection services ppt powerpoint presentation professional backgrounds cpb pdf. This is an editable Powerpoint six stages graphic that deals with topics like endpoint security protection services to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Implementing Cyber Security Incident Five Phases Of Cybersecurity Incident Clipart PDF
This slide represents the stages of the process which aims towards minimizing the impact of cyber security incidents on operational functions. It includes cyber security incident management stages such as plan and prepare, detect and report etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Implementing Cyber Security Incident Five Phases Of Cybersecurity Incident Clipart PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Implementing Cyber Security Incident Five Phases Of Cybersecurity Incident Clipart PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Impact Of Cyber Security Policies And Practices Ppt PowerPoint Presentation Diagram Graph Charts PDF
The following slide focuses on drafting cyber security policies to manage data control and breach. It mainly includes elements such as impact of existing cyber safety policies, mitigation actions, Presenting this PowerPoint presentation, titled Impact Of Cyber Security Policies And Practices Ppt PowerPoint Presentation Diagram Graph Charts PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Impact Of Cyber Security Policies And Practices Ppt PowerPoint Presentation Diagram Graph Charts PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Impact Of Cyber Security Policies And Practices Ppt PowerPoint Presentation Diagram Graph Charts PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.
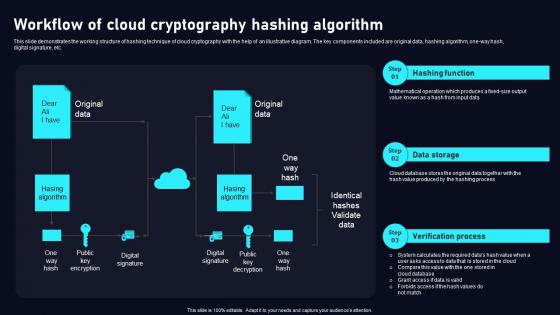
Workflow Of Cloud Cryptography Cloud Data Security Using Cryptography Clipart Pdf
This slide demonstrates the working structure of hashing technique of cloud cryptography with the help of an illustrative diagram. The key components included are original data, hashing algorithm, one way hash, digital signature, etc. Find a pre designed and impeccableWorkflow Of Cloud Cryptography Cloud Data Security Using Cryptography Clipart Pdf. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide demonstrates the working structure of hashing technique of cloud cryptography with the help of an illustrative diagram. The key components included are original data, hashing algorithm, one way hash, digital signature, etc.
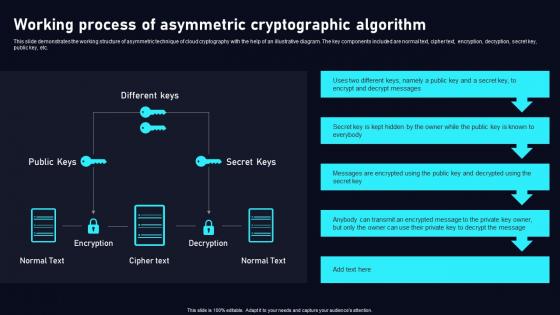
Working Process Of Asymmetric Cloud Data Security Using Cryptography Demonstration Pdf
This slide demonstrates the working structure of asymmetric technique of cloud cryptography with the help of an illustrative diagram. The key components included are normal text, cipher text, encryption, decryption, secret key, public key, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulateWorking Process Of Asymmetric Cloud Data Security Using Cryptography Demonstration Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide demonstrates the working structure of asymmetric technique of cloud cryptography with the help of an illustrative diagram. The key components included are normal text, cipher text, encryption, decryption, secret key, public key, etc.
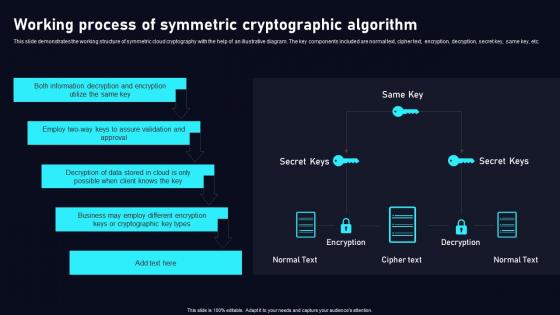
Working Process Of Symmetric Cloud Data Security Using Cryptography Download Pdf
This slide demonstrates the working structure of symmetric cloud cryptography with the help of an illustrative diagram. The key components included are normal text, cipher text, encryption, decryption, secret key, same key, etc. Want to ace your presentation in front of a live audience OurWorking Process Of Symmetric Cloud Data Security Using Cryptography Download Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use. This slide demonstrates the working structure of symmetric cloud cryptography with the help of an illustrative diagram. The key components included are normal text, cipher text, encryption, decryption, secret key, same key, etc.
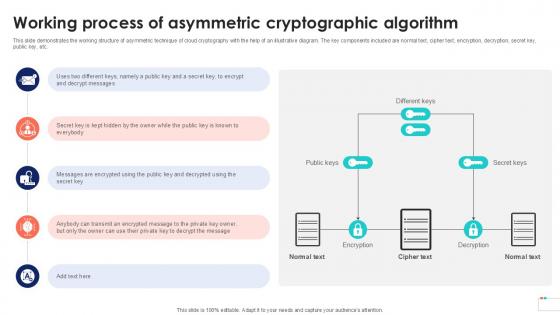
Working Process Of Asymmetric Data Security In Cloud Computing Ppt Powerpoint
This slide demonstrates the working structure of asymmetric technique of cloud cryptography with the help of an illustrative diagram. The key components included are normal text, cipher text, encryption, decryption, secret key, public key, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Working Process Of Asymmetric Data Security In Cloud Computing Ppt Powerpoint. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide demonstrates the working structure of asymmetric technique of cloud cryptography with the help of an illustrative diagram. The key components included are normal text, cipher text, encryption, decryption, secret key, public key, etc.
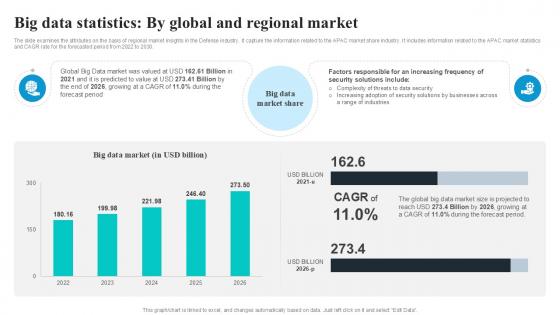
Big Data Statistics By Global Security Industry PPT Sample IR SS V
The slide examines the attributes on the basis of regional market insights in the Defense industry. It capture the information related to the APAC market share industry. It includes information related to the APAC market statistics and CAGR rate for the forecasted period from 2022 to 2030. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Big Data Statistics By Global Security Industry PPT Sample IR SS V for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. The slide examines the attributes on the basis of regional market insights in the Defense industry. It capture the information related to the APAC market share industry. It includes information related to the APAC market statistics and CAGR rate for the forecasted period from 2022 to 2030.
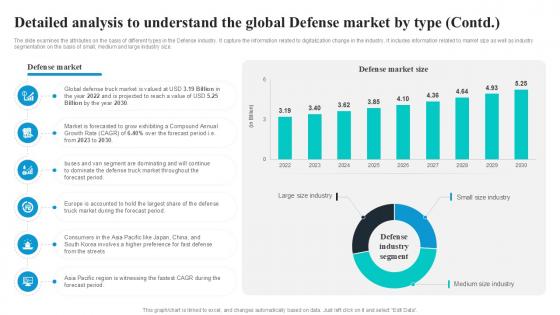
Detailed Analysis To Understand The Global Global Security Industry PPT PowerPoint IR SS V
The slide examines the attributes on the basis of different types in the Defense industry. It capture the information related to digitalization change in the industry. It includes information related to market size as well as industry segmentation on the basis of small, medium and large industry size. Slidegeeks is here to make your presentations a breeze with Detailed Analysis To Understand The Global Global Security Industry PPT PowerPoint IR SS V With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first The slide examines the attributes on the basis of different types in the Defense industry. It capture the information related to digitalization change in the industry. It includes information related to market size as well as industry segmentation on the basis of small, medium and large industry size.
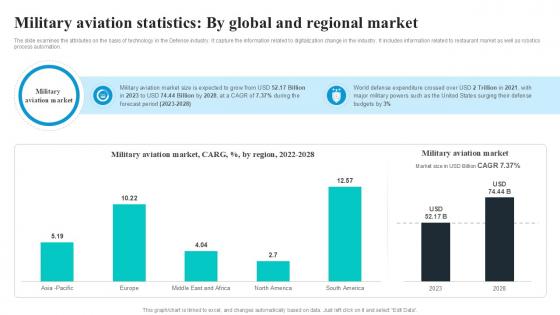
Military Aviation Statistics By Global Security Industry PPT PowerPoint IR SS V
The slide examines the attributes on the basis of technology in the Defense industry. It capture the information related to digitalization change in the industry. It includes information related to restaurant market as well as robotics process automation. Welcome to our selection of the Military Aviation Statistics By Global Security Industry PPT PowerPoint IR SS V. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. The slide examines the attributes on the basis of technology in the Defense industry. It capture the information related to digitalization change in the industry. It includes information related to restaurant market as well as robotics process automation.

Cloud Information Security Phase 1 Understand Cloud Utilization And Risk Ppt Infographics Topics PDF
This slide shows how an understanding of cloud utilization and risk is mandatory in cloud security and what factors it includes to take care of. Deliver and pitch your topic in the best possible manner with this Cloud Information Security Phase 1 Understand Cloud Utilization And Risk Ppt Infographics Topics PDF. Use them to share invaluable insights on Recognize Critical, Discover Malicious, Risk Assessment and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
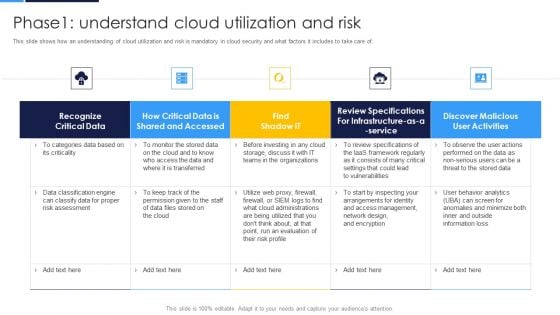
Cloud Security Assessment Phase1 Understand Cloud Utilization And Risk Professional PDF
This slide shows how an understanding of cloud utilization and risk is mandatory in cloud security and what factors it includes to take care of.Deliver an awe inspiring pitch with this creative Cloud Security Assessment Phase1 Understand Cloud Utilization And Risk Professional PDF bundle. Topics like Shared And Accessed, Risk Assessment, Review Specifications can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Laptop And Help Button Security PowerPoint Themes And PowerPoint Slides 0711
Microsoft PowerPoint Theme and Slide with laptop and help button to resolve the customer problem Our Laptop And Help Button Security PowerPoint Themes And PowerPoint Slides 0711 are the epitome of craftsmanship. They are created by exquisite artists.
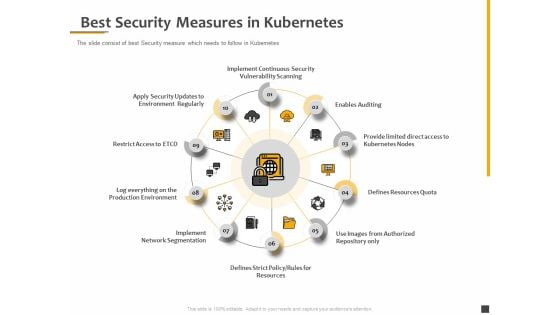
Understanding The Kubernetes Components Through Diagram Best Security Measures In Kubernetes Themes PDF
Presenting this set of slides with name understanding the kubernetes components through diagram best security measures in kubernetes themes pdf. This is a ten stage process. The stages in this process are implement continuous security vulnerability scanning, enables auditing, provide limited direct access to kubernetes nodes, defines resources quota, use images from authorized repository only, defines strict policy, rules for resources, implement network segmentation. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
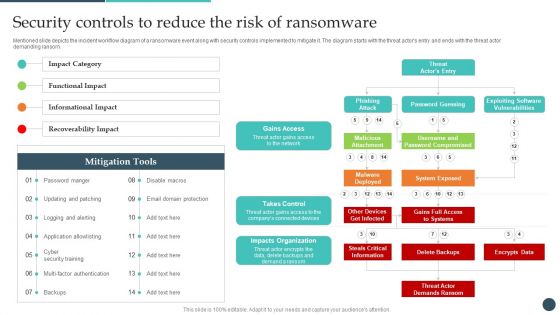
Safety Breach Response Playbook Security Controls To Reduce The Risk Topics PDF
Mentioned slide depicts the incident workflow diagram of a ransomware event along with security controls implemented to mitigate it. The diagram starts with the threat actors entry and ends with the threat actor demanding ransom. Presenting this PowerPoint presentation, titled Safety Breach Response Playbook Security Controls To Reduce The Risk Topics PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Safety Breach Response Playbook Security Controls To Reduce The Risk Topics PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Safety Breach Response Playbook Security Controls To Reduce The Risk Topics PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.
Gantt Chart For Safety And Security System Services Proposal One Pager Sample Example Document
Presenting you an exemplary Gantt Chart For Safety And Security System Services Proposal One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Gantt Chart For Safety And Security System Services Proposal One Pager Sample Example Document brilliant piece now.
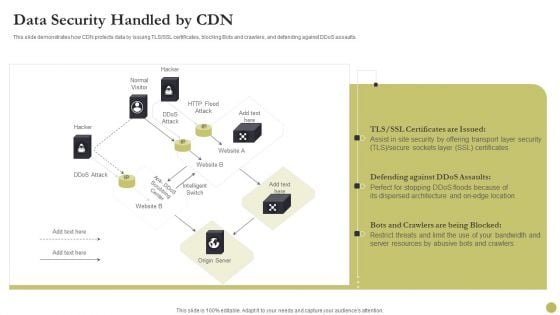
Content Delivery Network Edge Server Data Security Handled By CDN Diagrams PDF
This slide demonstrates how CDN protects data by issuing TLS or SSL certificates, blocking Bots and crawlers, and defending against DDoS assaults. Deliver and pitch your topic in the best possible manner with this Content Delivery Network Edge Server Data Security Handled By CDN Diagrams PDF. Use them to share invaluable insights on Security, Location, Server Resources and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
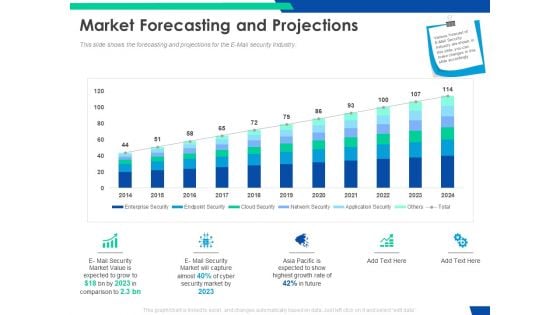
Cloud Based Email Security Market Report Market Forecasting And Projections Ppt Infographics Themes PDF
This slide shows the forecasting and projections for the E Mail security Industry. Deliver and pitch your topic in the best possible manner with this cloud based email security market report market forecasting and projections ppt infographics themes pdf. Use them to share invaluable insights on market forecasting and projections and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Small Business Cyber Security Ppt PowerPoint Presentation Outline Design Templates Cpb
Presenting this set of slides with name small business cyber security ppt powerpoint presentation outline design templates cpb. This is an editable Powerpoint five stages graphic that deals with topics like small business cyber security to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Benefits Application Security Testing Ppt PowerPoint Presentation Layouts File Formats Cpb
Presenting this set of slides with name benefits application security testing ppt powerpoint presentation layouts file formats cpb. This is an editable Powerpoint four stages graphic that deals with topics like benefits application security testing to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Sensitive Data Security Ppt PowerPoint Presentation Professional Design Templates Cpb Pdf
Presenting this set of slides with name sensitive data security ppt powerpoint presentation professional design templates cpb pdf. This is an editable Powerpoint four stages graphic that deals with topics like sensitive data security to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
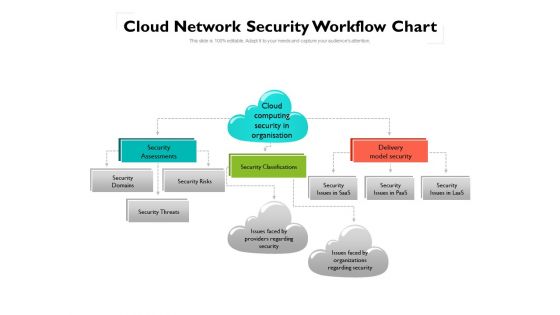
Cloud Network Security Workflow Chart Ppt PowerPoint Presentation Gallery Ideas PDF
This is a cloud network security workflow chart ppt powerpoint presentation gallery ideas pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security, organizations, domains. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Golden Key With Men Security PowerPoint Themes And PowerPoint Slides 0511
Microsoft PowerPoint Theme and Slide with a man standing in a circle around a golden key Bite the bullet with our Golden Key With Men Security PowerPoint Themes And PowerPoint Slides 0511. Face the issues head-on.
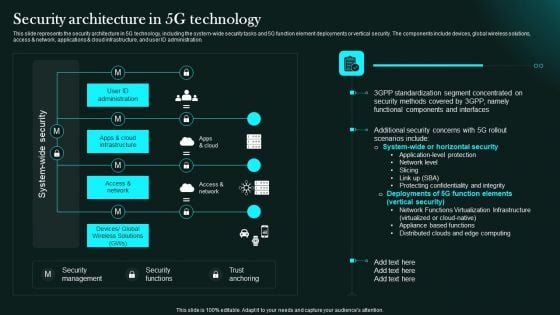
Security Architecture In 5G Technology 5G Network Functional Architecture Clipart PDF
This slide represents the security architecture in 5G technology, including the system-wide security tasks and 5G function element deployments or vertical security. The components include devices, global wireless solutions, access network, applications cloud infrastructure, and user ID administration.Retrieve professionally designed Security Architecture In 5G Technology 5G Network Functional Architecture Clipart PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You Do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Implementing Cybersecurity Awareness Program To Prevent Attacks Running Cyber Security Awareness Campaign Themes PDF
The purpose of this slide is to provide an overview of cyber security awareness campaign which can be used to educate staff members. The campaign covers information about the objectives, security awareness topics to cover and various activities which will be covered. Create an editable Implementing Cybersecurity Awareness Program To Prevent Attacks Running Cyber Security Awareness Campaign Themes PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre designed presentation templates help save time. Implementing Cybersecurity Awareness Program To Prevent Attacks Running Cyber Security Awareness Campaign Themes PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
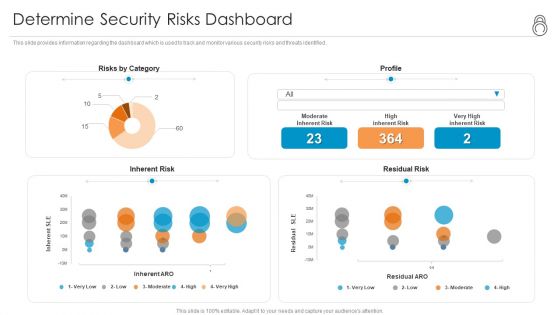
Enhanced Protection Corporate Event Administration Determine Security Risks Dashboard Summary PDF
This slide provides information regarding the dashboard which is used to track and monitor various security risks and threats identified. Deliver and pitch your topic in the best possible manner with this enhanced protection corporate event administration determine security risks dashboard summary pdf. Use them to share invaluable insights on moderate inherent risk, high inherent risk, very high inherent risk and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Safety And Security Objectives In Cyber Physical Systems Ppt Slides Themes PDF
This slide represents cyber physical systems safety and security objectives, including confidentiality, integrity, availability, authenticity, and robustness. Presenting Safety And Security Objectives In Cyber Physical Systems Ppt Slides Themes PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Availability, Authenticity, Confidentiality. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
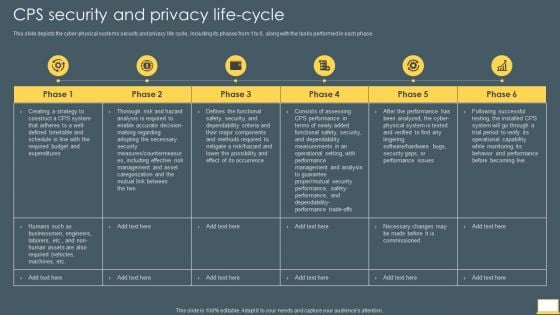
Cyber Intelligent Computing System CPS Security And Privacy Life Cycle Slides PDF
This slide depicts the cyber physical systems security and privacy life cycle, including its phases from 1 to 6, along with the tasks performed in each phase. Deliver an awe inspiring pitch with this creative Cyber Intelligent Computing System CPS Security And Privacy Life Cycle Slides PDF bundle. Topics like Management, Analysis, Required can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
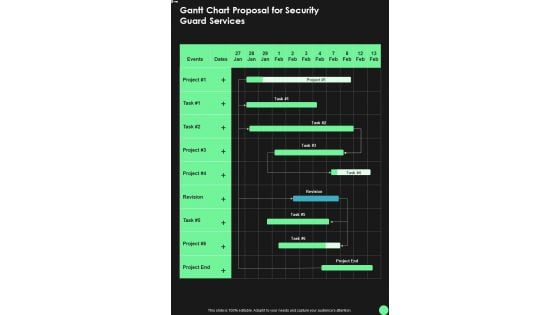
Gantt Chart Proposal For Security Guard Services One Pager Sample Example Document
Presenting you an exemplary Gantt Chart Proposal For Security Guard Services One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Gantt Chart Proposal For Security Guard Services One Pager Sample Example Document brilliant piece now.
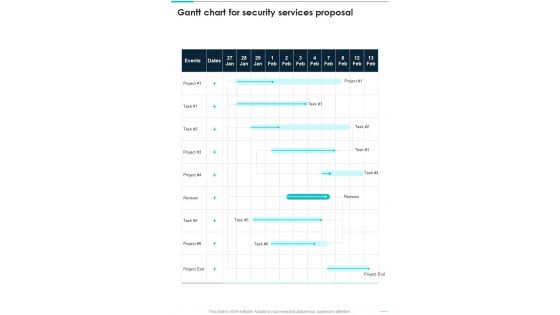
Gantt Chart For Security Services Proposal One Pager Sample Example Document
Presenting you an exemplary Gantt Chart For Security Services Proposal One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Gantt Chart For Security Services Proposal One Pager Sample Example Document brilliant piece now.
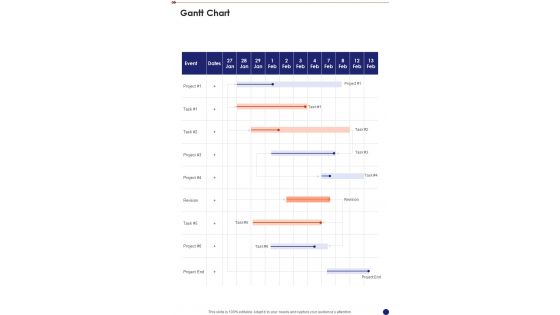
Gantt Chart Security And Safety System Proposal One Pager Sample Example Document
Presenting you an exemplary Gantt Chart Security And Safety System Proposal One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Gantt Chart Security And Safety System Proposal One Pager Sample Example Document brilliant piece now.
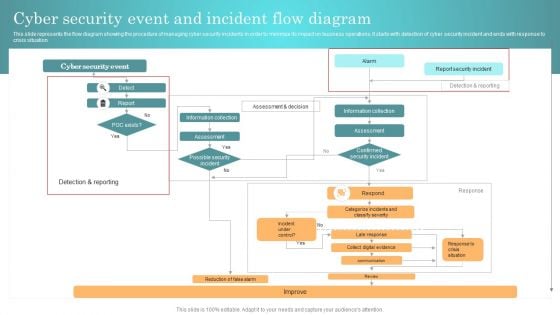
Incident Response Techniques Deployement Cyber Security Event And Incident Flow Diagram Structure PDF
This slide represents the flow diagram showing the procedure of managing cyber security incidents in order to minimize its impact on business operations. It starts with detection of cyber security incident and ends with response to crisis situation. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Incident Response Techniques Deployement Cyber Security Event And Incident Flow Diagram Structure PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Incident Response Techniques Deployement Cyber Security Event And Incident Flow Diagram Structure PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.
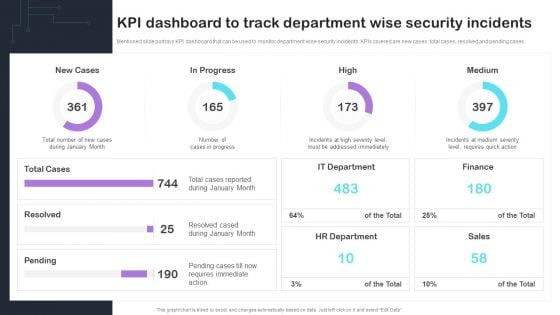
Cyber Risks And Incident Response Playbook KPI Dashboard To Track Department Wise Security Incidents Mockup PDF
Mentioned slide portrays KPI dashboard that can be used to monitor department wise security incidents. KPIs covered are new cases, total cases, resolved and pending cases. Presenting this PowerPoint presentation, titled Cyber Risks And Incident Response Playbook KPI Dashboard To Track Department Wise Security Incidents Mockup PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Cyber Risks And Incident Response Playbook KPI Dashboard To Track Department Wise Security Incidents Mockup PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Cyber Risks And Incident Response Playbook KPI Dashboard To Track Department Wise Security Incidents Mockup PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.
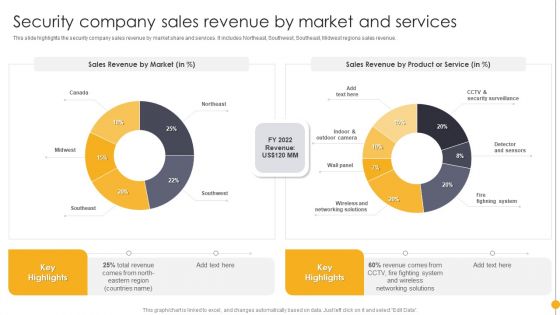
Portable Home Safety Systems Company Profile Security Company Sales Revenue By Market Rules PDF
This slide highlights the security company sales revenue by market share and services. It includes Northeast, Southwest, Southeast, Midwest regions sales revenue. Deliver an awe inspiring pitch with this creative Portable Home Safety Systems Company Profile Security Company Sales Revenue By Market Rules PDF bundle. Topics like Sales Revenue Market, Sales Revenue, Product, Service can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Data Safety Initiatives For Effective IT Security Threats Administration Table Of Contents Themes PDF
Presenting data safety initiatives for effective it security threats administration table of contents themes pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like global market insights, gap identification, defining business priorities, about security program, companies digitization levels. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Growth Charts And Put Them In Security PowerPoint Templates Ppt Backgrounds For Slides 0713
Be your own editor with our Growth Charts And Put Them In Security PowerPoint Templates PPT Backgrounds For Slides. Align your thoughts as per your wishes. Land the idea with our Pie Charts PowerPoint Templates. Help it grow with your thoughts. Cover the compass with our Arrows PowerPoint Templates. Your ideas will be acceptable to all. Our Growth Charts And Put Them In Security PowerPoint Templates Ppt Backgrounds For Slides 0713 don't fib about. They display factual conditions.
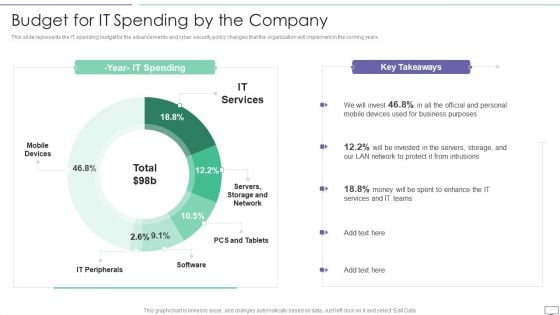
IT Security Hacker Budget For IT Spending By The Company Download PDF
This slide represents the IT spending budget for the advancements and cyber security policy changes that the organization will implement in the coming years.Deliver an awe inspiring pitch with this creative IT Security Hacker Budget For IT Spending By The Company Download PDF bundle. Topics like Business Purposes, Protect Intrusions, Services Teams can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Information Security Organization Chart Ppt PowerPoint Presentation Layouts Design Templates Cpb Pdf
Presenting this set of slides with name information security organization chart ppt powerpoint presentation layouts design templates cpb pdf. This is an editable Powerpoint four stages graphic that deals with topics like information security organization chart to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Security KPI Dashboard With Various Charts And Graphs Ppt Summary Background Image PDF
Persuade your audience using this Security KPI Dashboard With Various Charts And Graphs Ppt Summary Background Image PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Various Charts, Security KPI Dashboard, Graphs. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Proposal For Enterprise Security System Gantt Chart One Pager Sample Example Document
Presenting you an exemplary Proposal For Enterprise Security System Gantt Chart One Pager Sample Example Document. Our one pager comprises all the must have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Proposal For Enterprise Security System Gantt Chart One Pager Sample Example Document brilliant piece now.
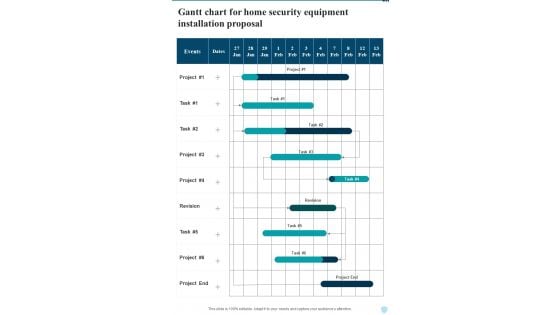
Gantt Chart For Home Security Equipment Installation Proposal One Pager Sample Example Document
Presenting you an exemplary Gantt Chart For Home Security Equipment Installation Proposal One Pager Sample Example Document. Our one pager comprises all the must have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Gantt Chart For Home Security Equipment Installation Proposal One Pager Sample Example Document brilliant piece now.
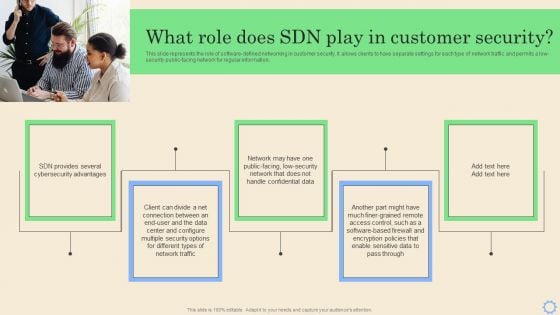
Software Defined Networking Development Strategies What Role Does SDN Play In Customer Security Brochure PDF
This slide represents the role of software-defined networking in customer security. It allows clients to have separate settings for each type of network traffic and permits a low-security public-facing network for regular information. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Software Defined Networking Development Strategies What Role Does SDN Play In Customer Security Brochure PDF can be your best option for delivering a presentation. Represent everything in detail using Software Defined Networking Development Strategies What Role Does SDN Play In Customer Security Brochure PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
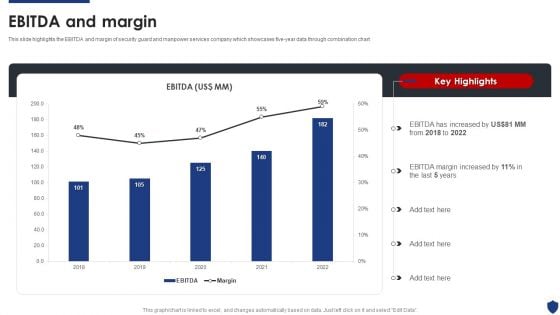
Security Officer Service Company Profile Ebitda And Margin Ppt PowerPoint Presentation File Deck PDF
This slide highlights the EBITDA and margin of security guard and manpower services company which showcases five-year data through combination chart. Deliver and pitch your topic in the best possible manner with this Security Officer Service Company Profile Ebitda And Margin Ppt PowerPoint Presentation File Deck PDF. Use them to share invaluable insights on EBITDA Increased, 2018 To 2022, EBITDA Margin Increased and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Cyber Infra Security Services Ppt PowerPoint Presentation Show Diagrams Cpb Pdf
Presenting this set of slides with name cyber infra security services ppt powerpoint presentation show diagrams cpb pdf. This is an editable Powerpoint four stages graphic that deals with topics like cyber infra security services to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
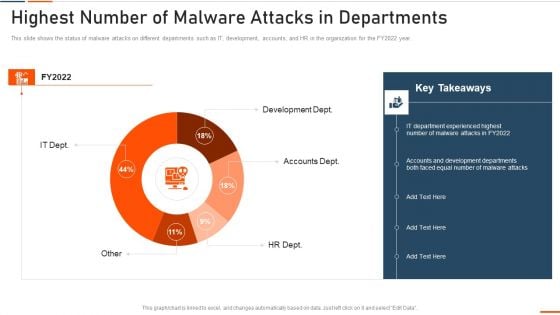
Information Technology Security Highest Number Of Malware Attacks In Departments Ppt Styles Slide Portrait PDF
This slide depicts the impact of network security training on an organization. It also shows how trained employees can reduce network attacks in the organization. Deliver and pitch your topic in the best possible manner with this information technology security highest number of malware attacks in departments ppt styles slide portrait pdf. Use them to share invaluable insights on phishing, network, intrusion, inadvertent disclosure and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
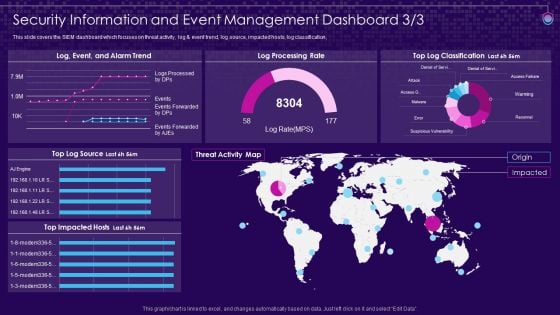
SIEM Services Security Information And Event Management Dashboard Source Ppt Outline Design Inspiration PDF
This slide covers the SIEM dashboard which focuses on threat activity, log and event trend, log source, impacted hosts, log classification, Deliver an awe inspiring pitch with this creative siem services security information and event management dashboard source ppt outline design inspiration pdf bundle. Topics like security information and event management dashboard can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
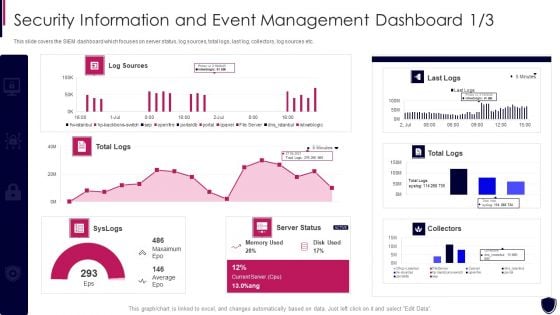
Security Information And Event Dashboard Enhancing Cyber Safety With Vulnerability Administration Formats PDF
This slide covers the SIEM dashboard which focuses on server status, log sources, total logs, last log, collectors, log sources etc. Deliver and pitch your topic in the best possible manner with this security information and event dashboard enhancing cyber safety with vulnerability administration formats pdf. Use them to share invaluable insights on security information and event management dashboard and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
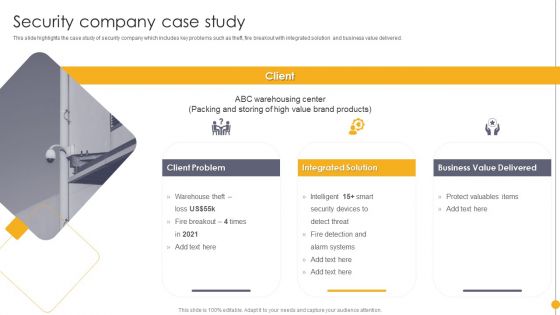
Portable Home Safety Systems Company Profile Security Company Case Study Background PDF
This slide highlights the case study of security company which includes key problems such as theft, fire breakout with integrated solution and business value delivered. Deliver and pitch your topic in the best possible manner with this Portable Home Safety Systems Company Profile Security Company Case Study Background PDF. Use them to share invaluable insights on Client Problem, Integrated Solution, Business Value Delivered and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
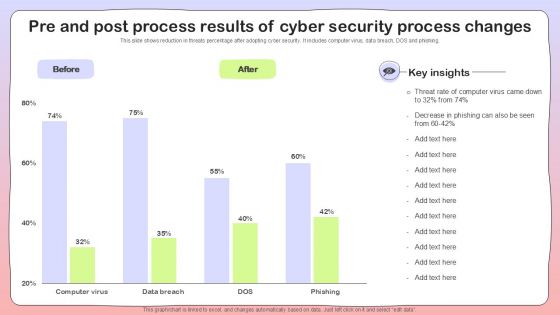
Pre And Post Process Results Of Cyber Security Process Changes Sample PDF
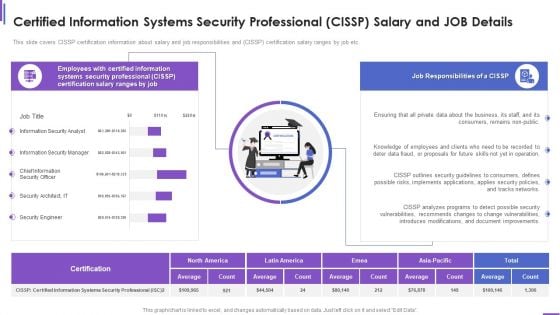
Certified Information Systems Security Professional Cissp Salary And Job Details Brochure PDF
This slide covers CISSP certification information about salary and job responsibilities and CISSP certification salary ranges by job etc. Deliver and pitch your topic in the best possible manner with this certified information systems security professional cissp salary and job details brochure pdf. Use them to share invaluable insights on consumers, security, document, networks, implements and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
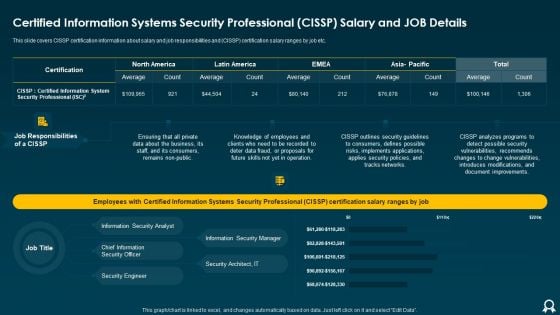
Certified Information Systems Security Professional CISSP Salary And Job Details Clipart PDF
This slide covers CISSP certification information about salary and job responsibilities and CISSP certification salary ranges by job etc. Deliver an awe inspiring pitch with this creative Certified Information Systems Security Professional CISSP Salary And Job Details Clipart PDF bundle. Topics like Average, Tracks Networks, Applies Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Agenda For Executing Security Management Plan To Minimize Threats Diagrams PDF
This is a agenda for executing security management plan to minimize threats diagrams pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like organizational, protect, risks, reduce, security management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
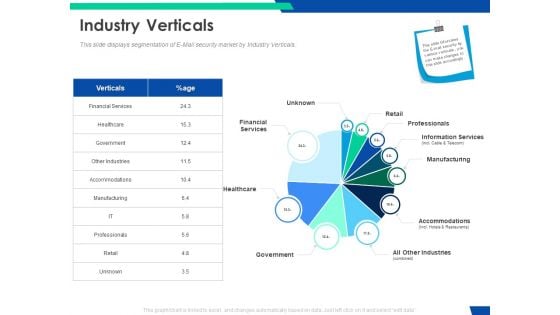
Cloud Based Email Security Market Report Industry Verticals Ppt Layouts Background Designs PDF
This slide displays segmentation of E Mail security market by Industry Verticals. Deliver and pitch your topic in the best possible manner with this cloud based email security market report industry verticals ppt layouts background designs pdf. Use them to share invaluable insights on financial services, retail, professionals, information services, manufacturing and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Security Operation Center Concepts Implementation Ppt PowerPoint Presentation Themes Cpb Pdf
Presenting this set of slides with name security operation center concepts implementation ppt powerpoint presentation themes cpb pdf. This is an editable Powerpoint three stages graphic that deals with topics like security operation center concepts implementation to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Utilizing Infrastructure Management Using Latest Methods Interdependence Resiliency And Security Themes PDF
This is a utilizing infrastructure management using latest methods interdependence resiliency and security themes pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like critical infrastructure dependencies and interdependencies assessment framework, infrastructure resilience wheel, lifecycle adaptive components resilience framework, dimensions infrastructure security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
8 Steps Circle Of Internal Audit And Cyber Security Ppt PowerPoint Presentation Gallery Themes PDF
Persuade your audience using this 8 steps circle of internal audit and cyber security ppt powerpoint presentation gallery themes pdf. This PPT design covers eight stages, thus making it a great tool to use. It also caters to a variety of topics including 8 steps circle of internal audit and cyber security. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
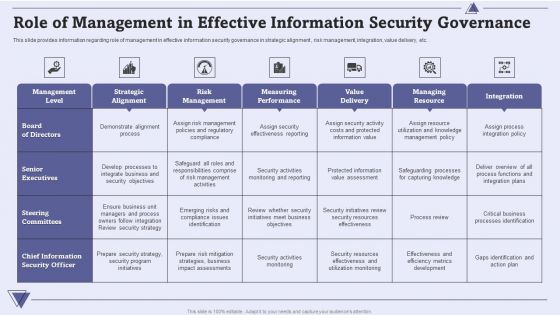
CIO For IT Cost Optimization Techniques Role Of Management In Effective Information Security Governance Themes PDF
This slide provides information regarding role of management in effective information security governance in strategic alignment , risk management, integration, value delivery, etc. Deliver and pitch your topic in the best possible manner with this CIO For IT Cost Optimization Techniques Role Of Management In Effective Information Security Governance Themes PDF. Use them to share invaluable insights on Management Level, Strategic Alignment, Risk Management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
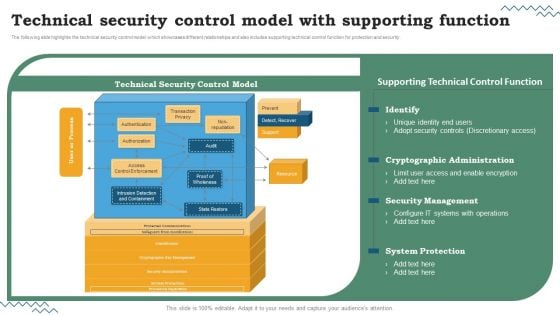
Software Development Life Cycle Planning Technical Security Control Model With Supporting Function Inspiration PDF
The following slide highlights the technical security control model which showcases different relationships and also includes supporting technical control function for protection and security. Are you searching for a Software Development Life Cycle Planning Technical Security Control Model With Supporting Function Inspiration PDF that is uncluttered, straightforward, and original. Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort youve put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Software Development Life Cycle Planning Technical Security Control Model With Supporting Function Inspiration PDF from Slidegeeks today.

Security Automation To Analyze And Mitigate Cyberthreats Impacts Of Ineffective Information Designs PDF
This slide highlights the impacts of ineffective information technology security at organization level which includes average cost of security, average time to identify data breach and total legitimate risks.If you are looking for a format to display your unique thoughts, then the professionally designed Security Automation To Analyze And Mitigate Cyberthreats Impacts Of Ineffective Information Designs PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Security Automation To Analyze And Mitigate Cyberthreats Impacts Of Ineffective Information Designs PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
Comparing Two Choices Diagram For Security Policy Orchestration Ppt PowerPoint Presentation Gallery Design Templates PDF
Persuade your audience using this comparing two choices diagram for security policy orchestration ppt powerpoint presentation gallery design templates pdf. This PPT design covers two stages, thus making it a great tool to use. It also caters to a variety of topics including comparing two choices diagram for security policy orchestration. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Threat Intelligence Cyber Security Ppt PowerPoint Presentation Infographic Template Diagrams Cpb Pdf
Presenting this set of slides with name threat intelligence cyber security ppt powerpoint presentation infographic template diagrams cpb pdf. This is an editable Powerpoint five stages graphic that deals with topics like threat intelligence cyber security to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
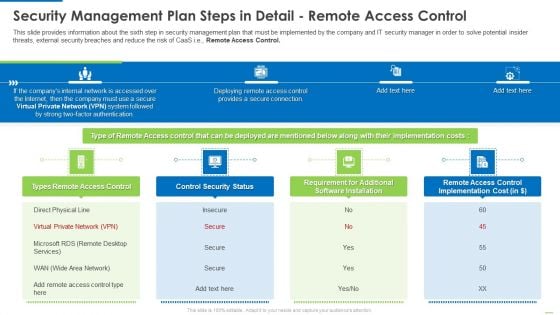
Security Management Plan Steps In Detail Remote Access Control Diagrams PDF
This is a security management plan steps in detail remote access control diagrams pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like control security status, requirement for additional software installation, remote access control. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

ISO 27001 Certification Procedure Current Security Management Capabilities Overview Diagrams PDF
Following slide illustrates present information security management capabilities overview of the company. Sections covered in the slide are core functions, description, key enablers, required and actual standard rating.Deliver and pitch your topic in the best possible manner with this ISO 27001 Certification Procedure Current Security Management Capabilities Overview Diagrams PDF. Use them to share invaluable insights on Assessing Information, Occurrence Identification, Communication and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
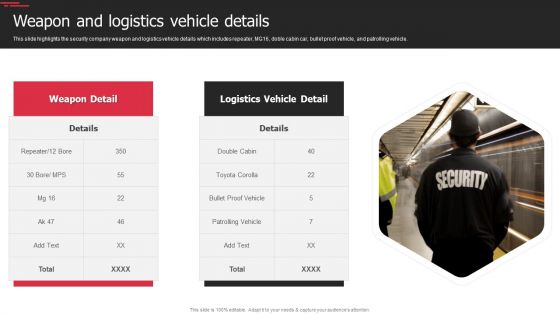
Security Agency Business Profile Weapon And Logistics Vehicle Details Diagrams PDF
This slide highlights the security company weapon and logistics vehicle details which includes repeater, MG16, doble cabin car, bullet proof vehicle, and patrolling vehicle. Deliver an awe inspiring pitch with this creative Security Agency Business Profile Weapon And Logistics Vehicle Details Diagrams PDF bundle. Topics like Weapon, Logistics Vehicle Details can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Business Intelligence With Data Governance And Security Ppt PowerPoint Presentation Infographics Example PDF
Pitch your topic with ease and precision using this business intelligence with data governance and security ppt powerpoint presentation infographics example pdf. This layout presents information on data governance, data discovery, data quality management, connected clouds, security. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
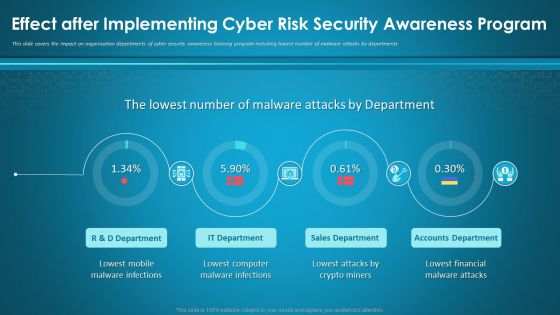
Effect After Implementing Cyber Risk Security Awareness Program Ppt Layouts Visuals PDF
This slide covers the impact on organization departments of cyber security awareness training program including lowest number of malware attacks by departments. Deliver an awe-inspiring pitch with this creative effect after implementing cyber risk security awareness program ppt layouts visuals pdf bundle. Topics like mobile, sales department, accounts department, financial, computer can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
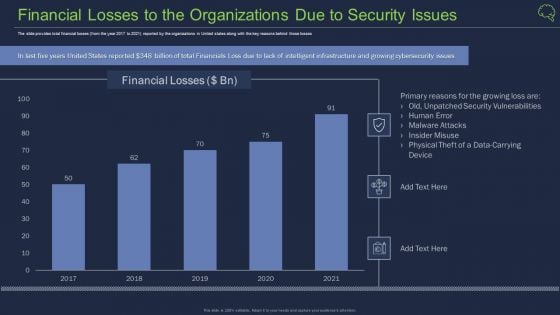
Financial Losses To The Organizations Due To Security Issues Ppt Background PDF
The slide provides total financial losses from the year 2017 to 2021 reported by the organizations in United states along with the key reasons behind those losses Deliver an awe inspiring pitch with this creative financial losses to the organizations due to security issues ppt background pdf bundle. Topics like financial losses to the organizations due to security issues can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
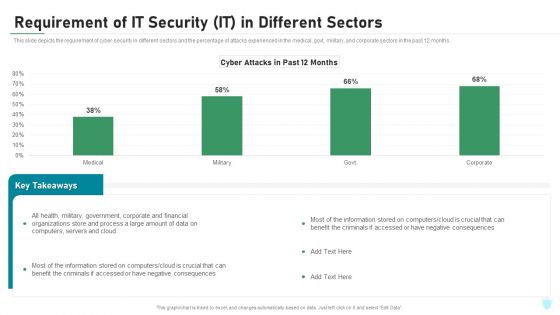
Requirement Of IT Security IT In Different Sectors Ppt Inspiration Deck PDF
This slide depicts the requirement of cyber security in different sectors and the percentage of attacks experienced in the medical, govt, military, and corporate sectors in the past 12 months. Deliver an awe inspiring pitch with this creative requirement of it security it in different sectors ppt inspiration deck pdf bundle. Topics like corporate, financial, organizations, process, computers, servers can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
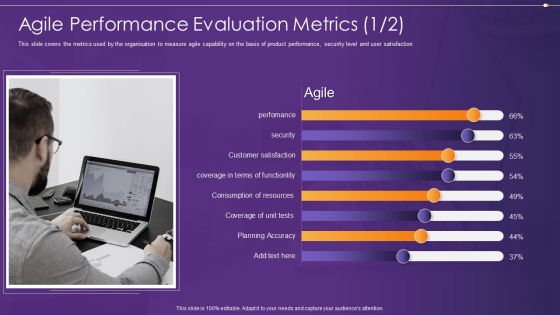
Agile Information Technology Project Administration Agile Performance Evaluation Metrics Security Ideas PDF
This slide covers the metrics used by the organisation to measure agile capability on the basis of product performance, security level and user satisfaction Deliver and pitch your topic in the best possible manner with this agile information technology project administration agile performance evaluation metrics security ideas pdf. Use them to share invaluable insights on agile performance evaluation metrics and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Effective IT Risk Management Process Impact On Security Infrastructure Structure PDF
Mentioned slide shows performance impact on security infrastructure after introducing risk assessment process. Deliver and pitch your topic in the best possible manner with this effective it risk management process impact on security infrastructure structure pdf. Use them to share invaluable insights on target, risk, performance and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
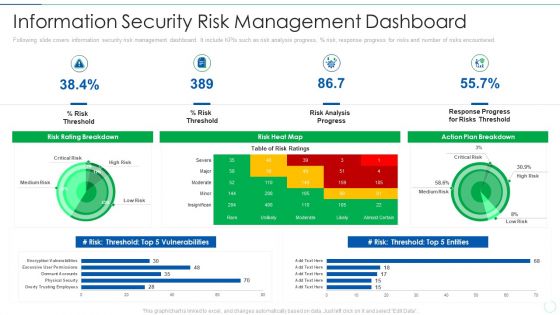
Effective IT Risk Management Process Information Security Risk Management Brochure PDF
Following slide covers information security risk management dashboard. It include KPIs such as risk analysis progress, percentage risk, response progress for risks and number of risks encountered. Deliver an awe inspiring pitch with this creative effective it risk management process information security risk management brochure pdf bundle. Topics like analysis, plan, risk, progress can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
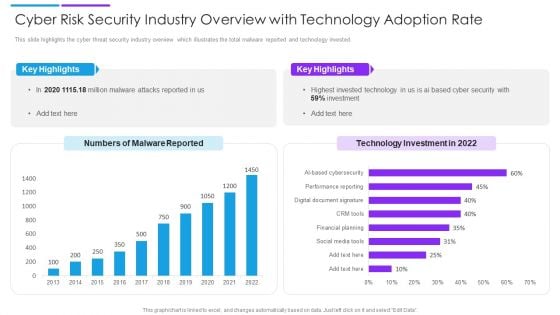
Cyber Risk Security Industry Overview With Technology Adoption Rate Slides PDF
This slide highlights the cyber threat security industry overview which illustrates the total malware reported and technology invested. Pitch your topic with ease and precision using this cyber risk security industry overview with technology adoption rate slides pdf. This layout presents information on key highlights, technology investment, malware reported. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
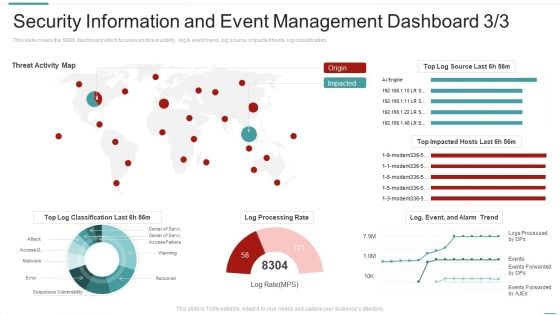
Risk Recognition Automation Security Information And Event Management Dashboard Activity Ppt Styles Influencers PDF
This slide covers the SIEM dashboard which focuses on threat activity, log and event trend, log source, impacted hosts, log classification, Deliver an awe inspiring pitch with this creative risk recognition automation security information and event management dashboard activity ppt styles influencers pdf bundle. Topics like security information and event management dashboard can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
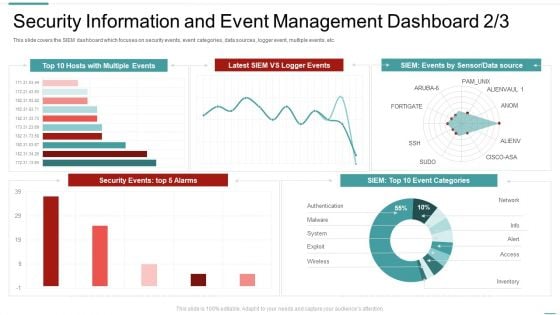
Risk Recognition Automation Security Information And Event Management Dashboard Source Ppt Professional Display PDF
This slide covers the SIEM dashboard which focuses on server status, log sources, total logs, last log, collectors, log sources etc. Deliver and pitch your topic in the best possible manner with this risk recognition automation security information and event management dashboard source ppt professional display pdf. Use them to share invaluable insights on security information and event management dashboard and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cybersecurity Risk Administration Plan Impact On Security Infrastructure Performance Background PDF
Mentioned slide shows performance impact on security infrastructure after introducing risk assessment process. Deliver and pitch your topic in the best possible manner with this Cybersecurity Risk Administration Plan Impact On Security Infrastructure Performance Background PDF Use them to share invaluable insights on Assessment Process, Target Met After Introducing, Standard And Technology and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
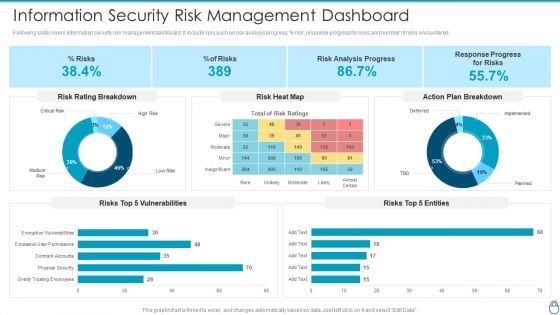
Cybersecurity Risk Administration Plan Information Security Risk Management Dashboard Summary PDF
Following slide covers information security risk management dashboard. It include kpis such as risk analysis progress, percent risk, response progress for risks and number of risks encountered.Deliver an awe inspiring pitch with this creative Cybersecurity Risk Administration Plan Information Security Risk Management Dashboard Summary PDF bundle. Topics like Risk Rating Breakdown, Action Plan Breakdown, Risk Analysis Progress can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
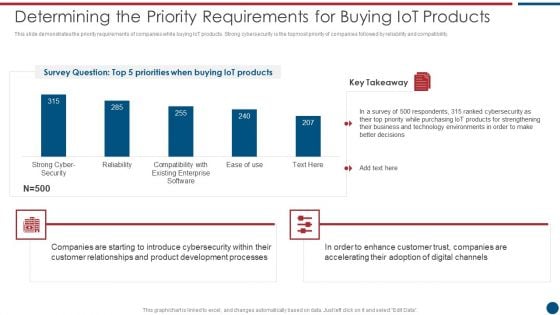
Risk Based Procedures To IT Security Determining The Priority Requirements For Buying Iot Products Rules PDF
This slide demonstrates the priority requirements of companies while buying IoT products. Strong cybersecurity is the topmost priority of companies followed by reliability and compatibility. Deliver an awe inspiring pitch with this creative Risk Based Procedures To IT Security Determining The Priority Requirements For Buying Iot Products Rules PDF bundle. Topics like Cyber Security, Existing Enterprise, IoT products can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Ways To Accomplish ISO 27001 Accreditation Dashboard For Information Security Risk Management Clipart PDF
This slide displays dashboard for information security risk management. It includes KPIs such as risk analysis progress, percent risk, response progress for risks and number of risks encountered. Deliver an awe inspiring pitch with this creative Ways To Accomplish ISO 27001 Accreditation Dashboard For Information Security Risk Management Clipart PDF bundle. Topics like Risk Heat, Action Plan, Risk Rating Breakdown can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

 Home
Home