Security Icon
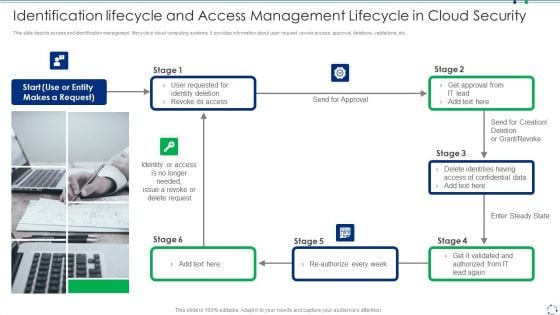
Identification Lifecycle And Access Management Lifecycle In Cloud Security Guidelines PDF
This slide depicts access and identification management lifecycle in cloud computing systems. It provides information about user request, revoke access, approval, deletions, validations, etc.Presenting identification lifecycle and access management lifecycle in cloud security guidelines pdf to dispense important information. This template comprises one stage. It also presents valuable insights into the topics including identity deletion, revoke its access, identity or access This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
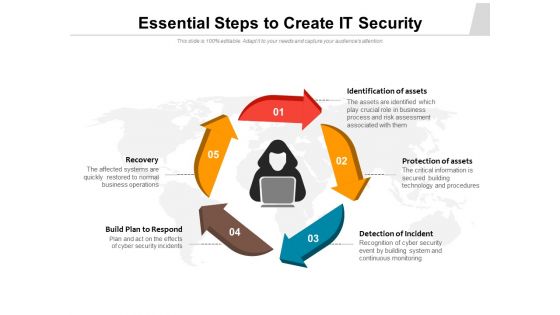
Essential Steps To Create IT Security Ppt PowerPoint Presentation Design Templates PDF
Presenting essential steps to create it security ppt powerpoint presentation design templates pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including identification of assets, protection of assets, detection of incident, recovery, build plan to respond. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
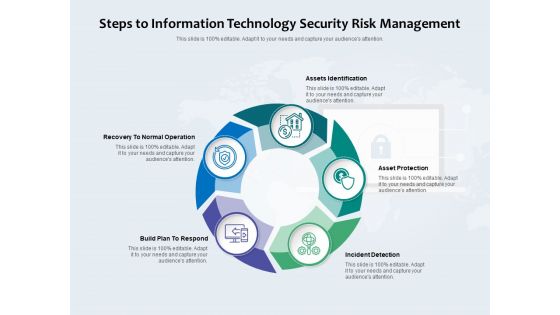
Steps To Information Technology Security Risk Management Ppt PowerPoint Presentation Gallery Example File PDF
Presenting steps to information technology security risk management ppt powerpoint presentation gallery example file pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including assets identification, asset protection, incident detection, build plan to respond, recovery to normal operation. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Structured Networking Process Diagram 7 Stages Ppt Security Business Plan PowerPoint Slides
We present our structured networking process diagram 7 stages ppt security business plan PowerPoint Slides.Download our Business PowerPoint Templates because It will get your audience in sync. Use our Network Diagrams PowerPoint Templates because Our PowerPoint Templates and Slides will let you meet your Deadlines. Present our Shapes PowerPoint Templates because You can Hit a home run with our PowerPoint Templates and Slides. See your ideas sail into the minds of your audience. Download and present our Circle Charts PowerPoint Templates because Your ideas provide food for thought. Our PowerPoint Templates and Slides will help you create a dish to tickle the most discerning palate. Download our Curves and Lines PowerPoint Templates because Our PowerPoint Templates and Slides are topically designed to provide an attractive backdrop to any subject.Use these PowerPoint slides for presentations relating to art, business, button, chart, clip, communication, design, diagram, element, graph, graphic, green, icon, illustration, isolated, network, process, round, set, shape, shiny, symbol, teamwork, vector, web. The prominent colors used in the PowerPoint template are Gray, White, Black. Aim for the skies with our Structured Networking Process Diagram 7 Stages Ppt Security Business Plan PowerPoint Slides. You will come out on top.

Evolving BI Infrastructure Timeframe For Incident Management In Security Centre Pictures PDF
This slide provides information regarding entire duration of incident handling process which occur in various phases. Deliver an awe inspiring pitch with this creative evolving bi infrastructure timeframe for incident management in security centre pictures pdf bundle. Topics like incident logging, ticket creation, incident categorization, incident prioritization, incident resolution, incident closure can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
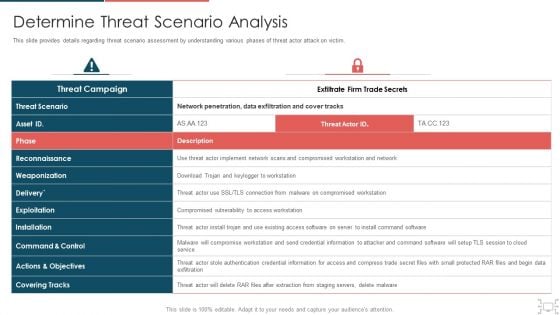
Cyber Security Administration In Organization Determine Threat Scenario Analysis Introduction PDF
This slide provides details regarding threat scenario assessment by understanding various phases of threat actor attack on victim. Deliver an awe inspiring pitch with this creative cyber security administration in organization determine threat scenario analysis introduction pdf bundle. Topics like determine threat scenario analysis can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
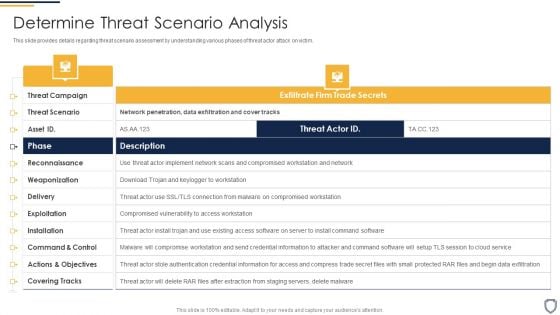
Corporate Security And Risk Management Determine Threat Scenario Analysis Formats PDF
This slide provides details regarding threat scenario assessment by understanding various phases of threat actor attack on victim. Deliver an awe inspiring pitch with this creative corporate security and risk management determine threat scenario analysis formats pdf bundle. Topics like determine threat scenario analysis can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Intelligent Infrastructure Timeframe For Incident Management In Security Centre Microsoft PDF
This slide provides information regarding entire duration of incident handling process which occur in various phases. Deliver an awe inspiring pitch with this creative Intelligent Infrastructure Timeframe For Incident Management In Security Centre Microsoft PDF bundle. Topics like Incident Logging, Ticket Creation, Incident Categorization, Incident Prioritization can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Developing Business Analytics Framework Timeframe For Incident Management In Security Centre Demonstration PDF
This slide provides information regarding entire duration of incident handling process which occur in various phases.Deliver and pitch your topic in the best possible manner with this Developing Business Analytics Framework Timeframe For Incident Management In Security Centre Demonstration PDF Use them to share invaluable insights on Incident Categorization, Incident Prioritization, Incident Resolution and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
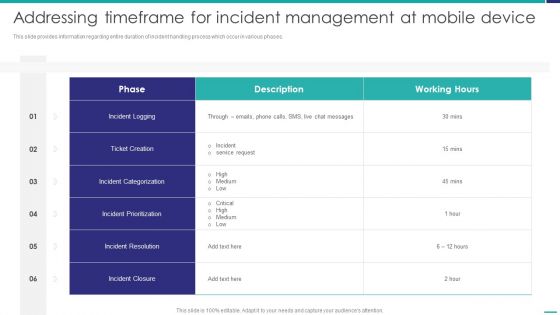
Addressing Timeframe For Incident Management At Mobile Device Mobile Device Security Management Microsoft PDF
This slide provides information regarding entire duration of incident handling process which occur in various phases.Deliver and pitch your topic in the best possible manner with this Addressing Timeframe For Incident Management At Mobile Device Mobile Device Security Management Microsoft PDF. Use them to share invaluable insights on Incident Categorization, Incident Prioritization, Incident Resolution and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
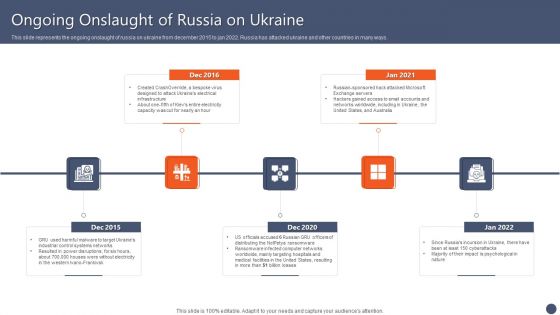
Series Of Cyber Security Attacks Against Ukraine 2022 Ongoing Onslaught Of Russia On Ukraine Introduction PDF
This slide represents the ongoing onslaught of russia on ukraine from december 2015 to jan 2022. Russia has attacked ukraine and other countries in many ways. If you are looking for a format to display your unique thoughts, then the professionally designed Series Of Cyber Security Attacks Against Ukraine 2022 Ongoing Onslaught Of Russia On Ukraine Introduction PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Series Of Cyber Security Attacks Against Ukraine 2022 Ongoing Onslaught Of Russia On Ukraine Introduction PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Table Of Contents For Business Mobile Device Security Management And Mitigation Sample PDF
If you are looking for a format to display your unique thoughts, then the professionally designed Table Of Contents For Business Mobile Device Security Management And Mitigation Sample PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Table Of Contents For Business Mobile Device Security Management And Mitigation Sample PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Table Of Contents Developing Information Technology Security Awareness Training Program For Employees Graphics PDF
If you are looking for a format to display your unique thoughts, then the professionally designed Table Of Contents Developing Information Technology Security Awareness Training Program For Employees Graphics PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Table Of Contents Developing Information Technology Security Awareness Training Program For Employees Graphics PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
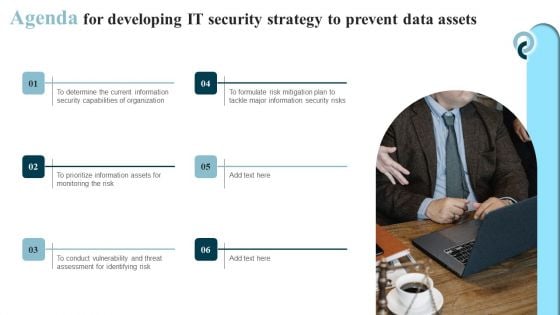
Agenda For Developing IT Security Strategy To Prevent Data Assets Portrait PDF
If you are looking for a format to display your unique thoughts, then the professionally designed Agenda For Developing IT Security Strategy To Prevent Data Assets Portrait PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Agenda For Developing IT Security Strategy To Prevent Data Assets Portrait PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Table Of Contents Increasing Information Security Awareness In Company Using Various Techniques Clipart PDF
If you are looking for a format to display your unique thoughts, then the professionally designed Table Of Contents Increasing Information Security Awareness In Company Using Various Techniques Clipart PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Table Of Contents Increasing Information Security Awareness In Company Using Various Techniques Clipart PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Table Of Contents For Comprehensive Guide For Ensuring IT Infrastructure Security Slides PDF
If you are looking for a format to display your unique thoughts, then the professionally designed Table Of Contents For Comprehensive Guide For Ensuring IT Infrastructure Security Slides PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Table Of Contents For Comprehensive Guide For Ensuring IT Infrastructure Security Slides PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
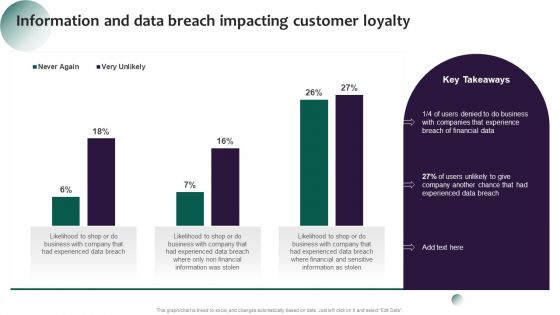
Information Systems Security And Risk Management Plan Information And Data Breach Impacting Customer Loyalty Brochure PDF
Make sure to capture your audiences attention in your business displays with our gratis customizable Information Systems Security And Risk Management Plan Information And Data Breach Impacting Customer Loyalty Brochure PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
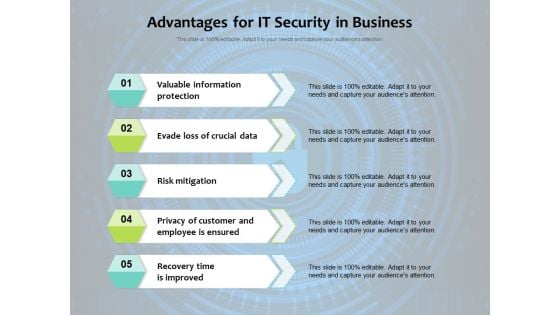
Advantages For IT Security In Business Ppt PowerPoint Presentation Infographic Template Microsoft PDF
Presenting advantages for it security in business ppt powerpoint presentation infographic template microsoft pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including valuable information protection, evade loss of crucial data, risk mitigation, privacy of customer and employee is ensured, recovery time is improved. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
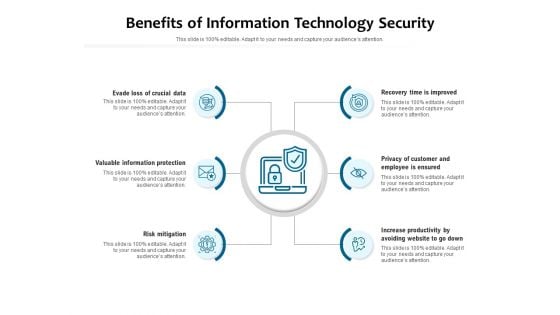
Benefits Of Information Technology Security Ppt PowerPoint Presentation Layouts Layouts PDF
Presenting benefits of information technology security ppt powerpoint presentation layouts layouts pdf to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including evade loss of crucial data, valuable information protection, risk mitigation, recovery time is improved, privacy of customer and employee is ensured, increase productivity by avoiding website to go down. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
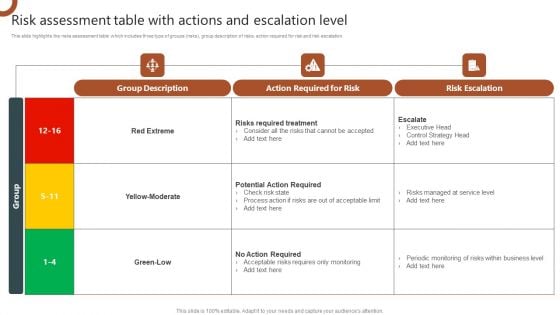
Organizations Risk Management And IT Security Risk Assessment Table With Actions And Escalation Level Background PDF
This slide highlights the risks assessment table which includes three type of groups risks, group description of risks, action required for risk and risk escalation. Retrieve professionally designed Organizations Risk Management And IT Security Technical Security Control Model With Supporting Function Structure PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Techniques To Monitor Transactions Major Roles And Responsibilities Of Financial Security Team Pictures PDF
The following slide Major roles and responsibilities of financial security department . It includes information about risk level determination, laws and regulations, team training, operational compliance, automatic workflows, red flags, etc. Retrieve professionally designed Techniques To Monitor Transactions Major Roles And Responsibilities Of Financial Security Team Pictures PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You dont have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
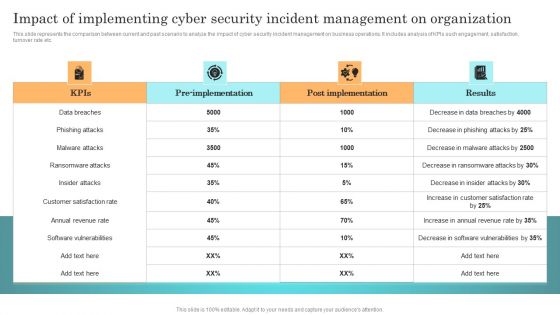
Incident Response Techniques Deployement Impact Of Implementing Cyber Security Incident Management Formats PDF
This slide represents the comparison between current and past scenario to analyze the impact of cyber security incident management on business operations. It includes analysis of KPIs such engagement, satisfaction, turnover rate etc. Retrieve professionally designed Incident Response Techniques Deployement Impact Of Implementing Cyber Security Incident Management Formats PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
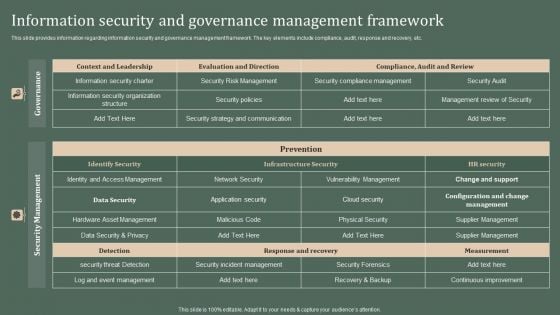
Deploying Corporate Aligned IT Strategy Information Security And Governance Management Framework Download PDF
This slide provides information regarding information security and governance management framework. The key elements include compliance, audit, response and recovery, etc. Retrieve professionally designed Deploying Corporate Aligned IT Strategy Information Security And Governance Management Framework Download PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
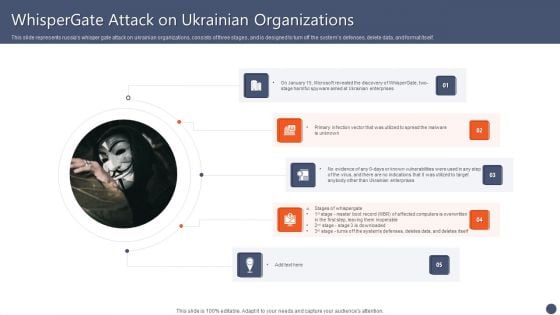
Series Of Cyber Security Attacks Against Ukraine 2022 Whispergate Attack On Ukrainian Organizations Information PDF
This slide represents russias whisper gate attack on ukrainian organizations, consists of three stages, and is designed to turn off the systems defenses, delete data, and format itself. Are you searching for a Series Of Cyber Security Attacks Against Ukraine 2022 Whispergate Attack On Ukrainian Organizations Information PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Series Of Cyber Security Attacks Against Ukraine 2022 Whispergate Attack On Ukrainian Organizations Information PDF from Slidegeeks today.

Analyzing The Impact On Assets Due To Information Breach Information Security Risk Administration Introduction PDF
This slide showcases impact of information breach on different assets which can help organization in formulating risk monitoring policy. Its key components are criterion, criterion weight and information assets.Are you searching for a Analyzing The Impact On Assets Due To Information Breach Information Security Risk Administration Introduction PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you ve put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Analyzing The Impact On Assets Due To Information Breach Information Security Risk Administration Introduction PDF from Slidegeeks today.
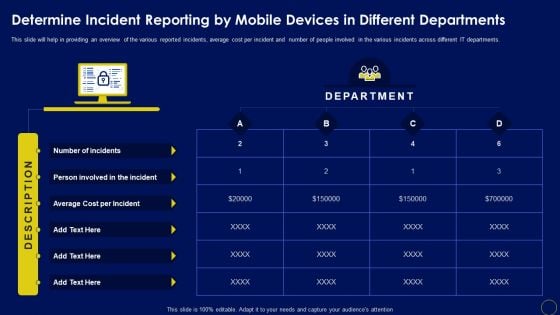
Determine Incident Reporting By Mobile Devices In Business Mobile Device Security Management Designs PDF
This slide will help in providing an overview of the various reported incidents, average cost per incident and number of people involved in the various incidents across different IT departments. Are you searching for a Determine Incident Reporting By Mobile Devices In Business Mobile Device Security Management Designs PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you ve put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Determine Incident Reporting By Mobile Devices In Business Mobile Device Security Management Designs PDF from Slidegeeks today.
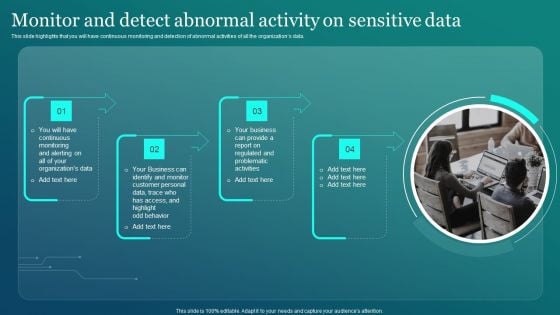
Information Security Monitor And Detect Abnormal Activity On Sensitive Data Elements PDF
This slide highlights that you will have continuous monitoring and detection of abnormal activities of all the organizations data. Are you searching for a Information Security Monitor And Detect Abnormal Activity On Sensitive Data Elements PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Information Security Monitor And Detect Abnormal Activity On Sensitive Data Elements PDF from Slidegeeks today.
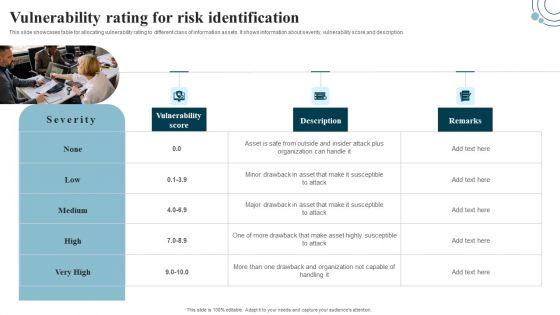
Developing IT Security Strategy Vulnerability Rating For Risk Identification Topics PDF
This slide showcases table for allocating vulnerability rating to different class of information assets. It shows information about severity, vulnerability score and description. Are you searching for a Developing IT Security Strategy Vulnerability Rating For Risk Identification Topics PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Developing IT Security Strategy Vulnerability Rating For Risk Identification Topics PDF from Slidegeeks today.
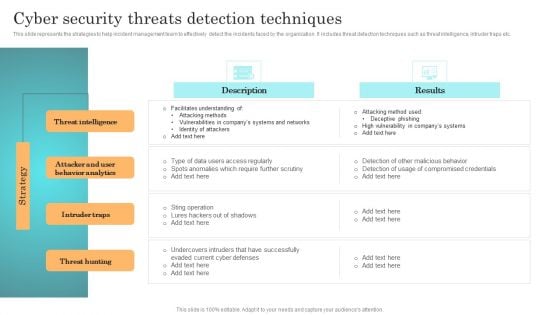
Incident Response Techniques Deployement Cyber Security Threats Detection Techniques Portrait PDF
This slide represents the strategies to help incident management team to effectively detect the incidents faced by the organization. It includes threat detection techniques such as threat intelligence, intruder traps etc. Are you searching for a Incident Response Techniques Deployement Cyber Security Threats Detection Techniques Portrait PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal. With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Incident Response Techniques Deployement Cyber Security Threats Detection Techniques Portrait PDF from Slidegeeks today.

Certified Information Systems Security Professional CISSP Details IT Certifications To Enhance Rules PDF
This slide covers CISSP certification details such as what is the CISSP, how to become certified, how to prepare for CISSP and why to get CISSP certifications. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Certified Information Systems Security Professional CISSP Details IT Certifications To Enhance Rules PDF can be your best option for delivering a presentation. Represent everything in detail using Certified Information Systems Security Professional CISSP Details IT Certifications To Enhance Rules PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
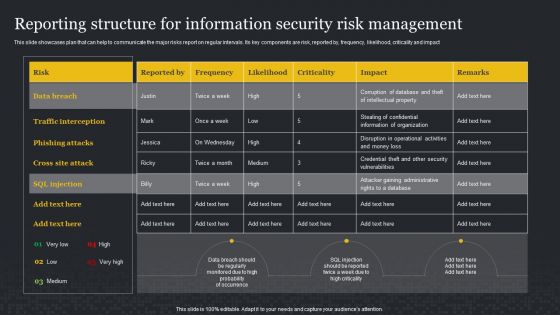
Reporting Structure For Information Security Risk Management Cybersecurity Risk Assessment Formats PDF
This slide showcases plan that can help to communicate the major risks report on regular intervals. Its key components are risk, reported by, frequency, likelihood, criticality and impact. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Reporting Structure For Information Security Risk Management Cybersecurity Risk Assessment Formats PDF can be your best option for delivering a presentation. Represent everything in detail using Reporting Structure For Information Security Risk Management Cybersecurity Risk Assessment Formats PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Checklist For Information Security Risk Management Cybersecurity Risk Assessment Summary PDF
This slide showcases checklist that can help to ensure formulate and implementing data security risk management program in organization. Its key components are activity, assigned to and status. Do you know about Slidesgeeks Checklist For Information Security Risk Management Cybersecurity Risk Assessment Summary PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
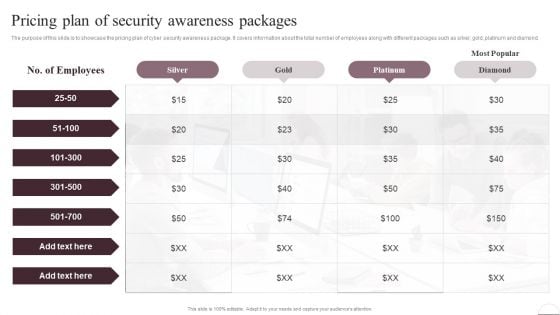
Prevention Of Information Pricing Plan Of Security Awareness Packages Elements PDF
The purpose of this slide is to showcase the pricing plan of cyber security awareness package. It covers information about the total number of employees along with different packages such as silver, gold, platinum and diamond. Do you know about Slidesgeeks Prevention Of Information Pricing Plan Of Security Awareness Packages Elements PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.

Information Security Seven Principles Of GDPR Law Ppt PowerPoint Presentation File Inspiration PDF
This slide represents the seven principles of GDPR law, including lawfulness and transparency, purpose limitation, data minimization, accuracy, storage limitation, integrity and confidentiality, accountability. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Information Security Seven Principles Of GDPR Law Ppt PowerPoint Presentation File Inspiration PDF can be your best option for delivering a presentation. Represent everything in detail using Information Security Seven Principles Of GDPR Law Ppt PowerPoint Presentation File Inspiration PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
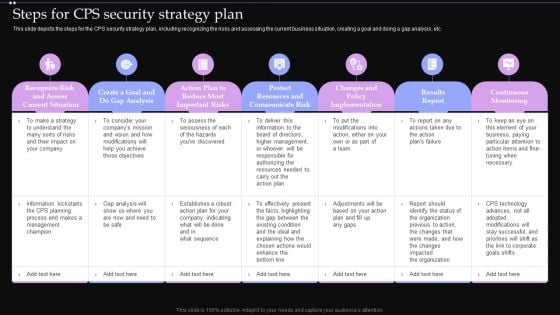
Steps For CPS Security Strategy Plan Ppt PowerPoint Presentation File Portfolio PDF
This slide depicts the steps for the CPS security strategy plan, including recognizing the risks and assessing the current business situation, creating a goal and doing a gap analysis, etc. Do you know about Slidesgeeks Steps For CPS Security Strategy Plan Ppt PowerPoint Presentation File Portfolio PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.

Implementing Cybersecurity Awareness Program To Prevent Attacks Pricing Plan Of Security Awareness Packages Template PDF
The purpose of this slide is to showcase the pricing plan of cyber security awareness package. It covers information about the total number of employees along with different packages such as silver, gold, platinum and diamond. Do you know about Slidesgeeks Implementing Cybersecurity Awareness Program To Prevent Attacks Pricing Plan Of Security Awareness Packages Template PDF. These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
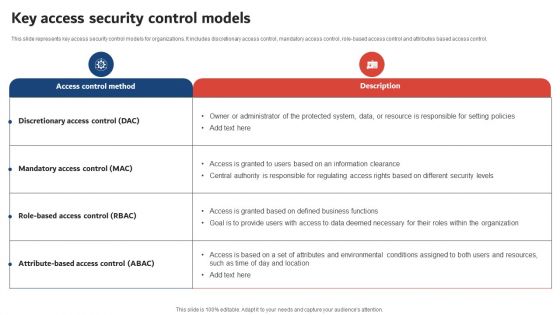
Execution Of ICT Strategic Plan Key Access Security Control Models Topics PDF
This slide represents key access security control models for organizations. It includes discretionary access control, mandatory access control, role-based access control and attributes based access control, Do you know about Slidesgeeks Execution Of ICT Strategic Plan Key Access Security Control Models Topics PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
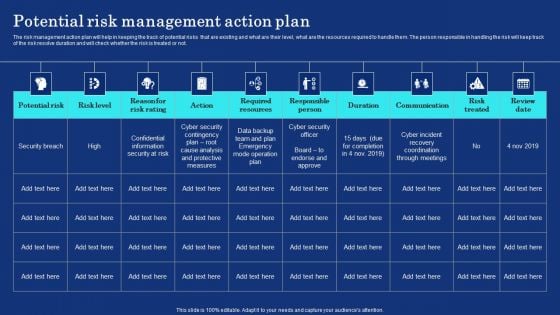
Organizational Assets Security Management Strategy Potential Risk Management Action Plan Information PDF
The risk management action plan will help in keeping the track of potential risks that are existing and what are their level, what are the resources required to handle them. The person responsible in handling the risk will keep track of the risk resolve duration and will check whether the risk is treated or not. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Organizational Assets Security Management Strategy Potential Risk Management Action Plan Information PDF can be your best option for delivering a presentation. Represent everything in detail using Organizational Assets Security Management Strategy Potential Risk Management Action Plan Information PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Table Of Contents Exploring Investment Opportunities With Security Token Offerings Graphics Pdf
Do you know about Slidesgeeks Table Of Contents Exploring Investment Opportunities With Security Token Offerings Graphics Pdf These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. Our Table Of Contents Exploring Investment Opportunities With Security Token Offerings Graphics Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
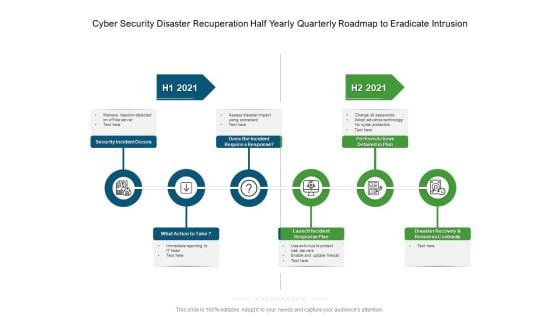
Cyber Security Disaster Recuperation Half Yearly Quarterly Roadmap To Eradicate Intrusion Graphics
Presenting our innovatively-structured cyber security disaster recuperation half yearly quarterly roadmap to eradicate intrusion graphics Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.
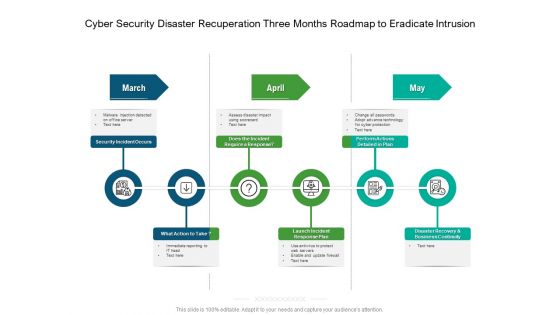
Cyber Security Disaster Recuperation Three Months Roadmap To Eradicate Intrusion Topics
Presenting our jaw-dropping cyber security disaster recuperation three months roadmap to eradicate intrusion topics. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well-researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually-appealing design by clicking the download button given below.
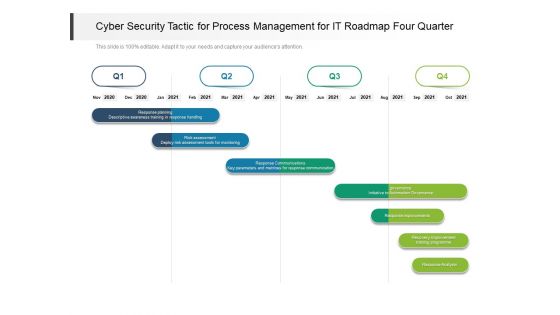
Cyber Security Tactic For Process Management For IT Roadmap Four Quarter Pictures
Presenting our innovatively structured cyber security tactic for process management for it roadmap four quarter pictures Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.
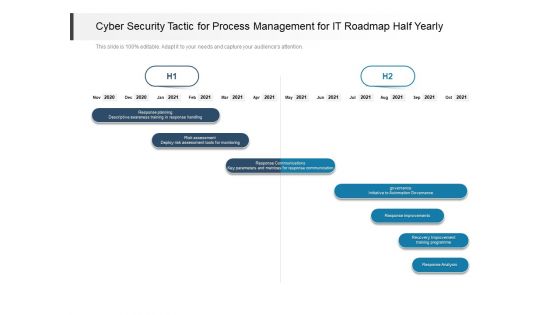
Cyber Security Tactic For Process Management For IT Roadmap Half Yearly Topics
Introducing our cyber security tactic for process management for it roadmap half yearly topics. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.

Framework Administration 4 Dimensions Of Infrastructure Security Ppt Infographic Template Slide Download PDF
This is a framework administration 4 dimensions of infrastructure security ppt infographic template slide download pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like people, data, applications, infrastructure. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
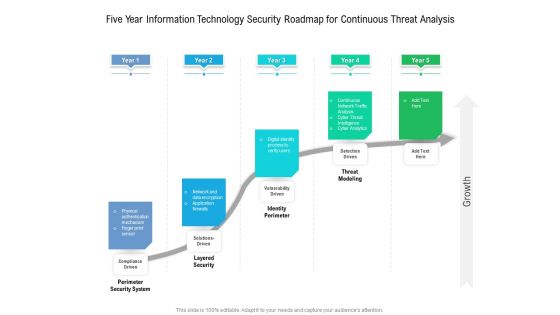
Five Year Information Technology Security Roadmap For Continuous Threat Analysis Summary
Presenting our innovatively structured five year information technology security roadmap for continuous threat analysis summary Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.
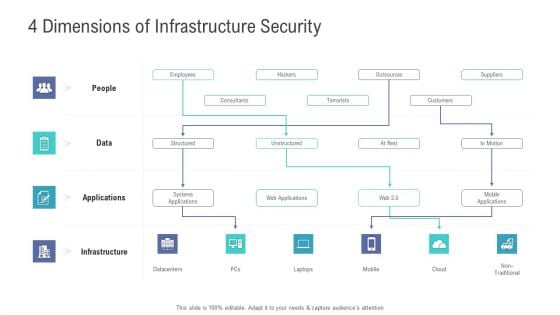
Financial Functional Assessment 4 Dimensions Of Infrastructure Security Ppt Professional Ideas PDF
This is a financial functional assessment 4 dimensions of infrastructure security ppt professional ideas pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like infrastructure, applications, data, people. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
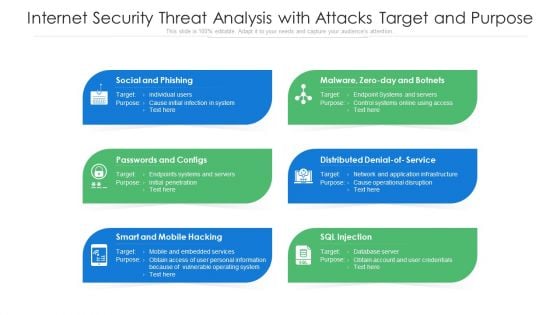
Internet Security Threat Analysis With Attacks Target And Purpose Ppt PowerPoint Presentation Pictures Structure PDF
Presenting internet security threat analysis with attacks target and purpose ppt powerpoint presentation pictures structure pdf to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including social and phishing, passwords and configs, smart and mobile hacking. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
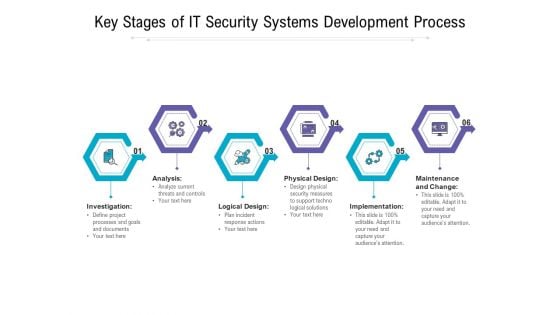
Key Stages Of IT Security Systems Development Process Ppt PowerPoint Presentation Slides Display PDF
Presenting key stages of it security systems development process ppt powerpoint presentation slides display pdf to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including investigation, analysis, logical design, physical design, implementation, maintenance and change. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
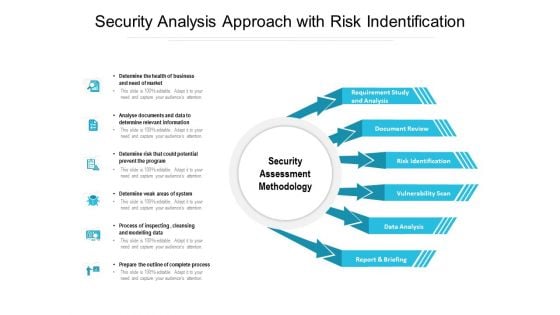
Security Analysis Approach With Risk Indentification Ppt PowerPoint Presentation Professional Gridlines PDF
Presenting security analysis approach with risk indentification ppt powerpoint presentation professional gridlines pdf. to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including analyse, of business, need of market, prevent the program, process of inspecting. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
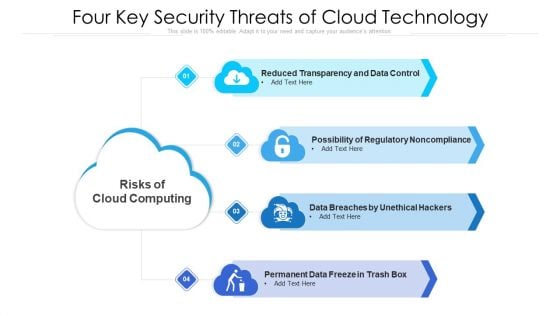
Four Key Security Threats Of Cloud Technology Ppt PowerPoint Presentation Gallery Introduction PDF
Presenting four key security threats of cloud technology ppt powerpoint presentation gallery introduction pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including data breaches by unethical hackers, permanent data freeze in trash box, possibility of regulatory noncompliance. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
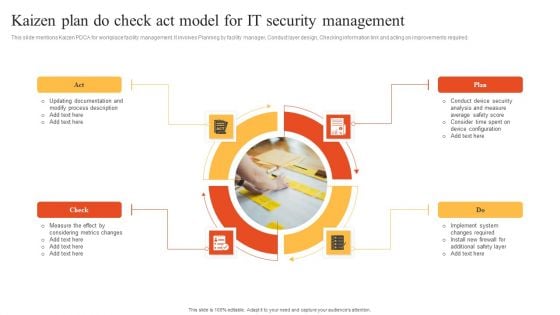
Kaizen Plan Do Check Act Model For IT Security Management Information PDF
This slide mentions Kaizen PDCA for workplace facility management. It involves Planning by facility manager, Conduct layer design, Checking information link and acting on improvements required. Presenting Kaizen Plan Do Check Act Model For IT Security Management Information PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Check, Plan, Act. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
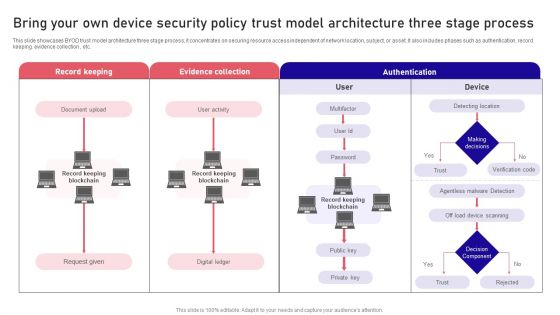
Bring Your Own Device Security Policy Trust Model Architecture Three Stage Process Rules PDF
This slide showcases BYOD trust model architecture three stage process, it concentrates on securing resource access independent of network location, subject, or asset. It also includes phases such as authentication, record keeping. evidence collection , etc. Persuade your audience using this Bring Your Own Device Security Policy Trust Model Architecture Three Stage Process Rules PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Record Keeping, Evidence Collection, Authentication . Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Optimization Of IoT Remote Monitoring Smart Doorbells Used For Maintaining Security IoT SS V
This slide provides an overview of the smart displays used in smart homes to monitor home activities. It further includes popular brands and factors to consider that are usage, size, resolution, cost, sound quality and energy use. Are you searching for a Optimization Of IoT Remote Monitoring Smart Doorbells Used For Maintaining Security IoT SS V that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Optimization Of IoT Remote Monitoring Smart Doorbells Used For Maintaining Security IoT SS V from Slidegeeks today. This slide provides an overview of the video doorbells used to enhance security. The slide includes features of smart doorbells that are motion detection, video storage, multi-user functionality, night vision camera, etc.
Collection Of Interrelated Tasks 6 Stages Security Business Plan PowerPoint Slides
We present our collection of interrelated tasks 6 stages security business plan PowerPoint Slides.Download and present our Arrows PowerPoint Templates because You will get more than you ever bargained for. Download our Circle Charts PowerPoint Templates because It can Bubble and burst with your ideas. Present our Shapes PowerPoint Templates because You have the co-ordinates for your destination of success. Let our PowerPoint Templates and Slides map out your journey. Download and present our Business PowerPoint Templates because you should Whip up a frenzy with our PowerPoint Templates and Slides. They will fuel the excitement of your team. Download and present our Process and Flows PowerPoint Templates because Our PowerPoint Templates and Slides will embellish your thoughts. See them provide the desired motivation to your team.Use these PowerPoint slides for presentations relating to arrow, circular, process, round, flow, business, vector, graphic, part, green, red, concept, yellow, presentation, symbol, circle, orange, repeat, cycle, illustration, icon, pink, six, purple, blue, repetitive. The prominent colors used in the PowerPoint template are Blue, Gray, Black. Rule the roost with our Collection Of Interrelated Tasks 6 Stages Security Business Plan PowerPoint Slides. They will enthrone your thoughts.
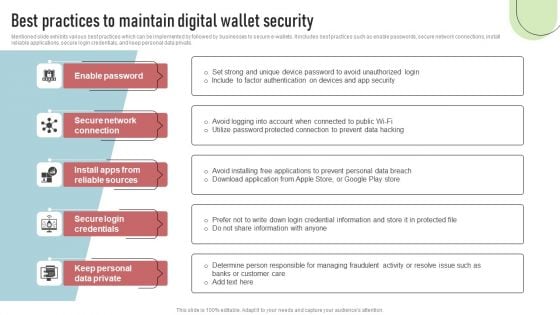
Cashless Payment Strategies To Enhance Business Performance Best Practices To Maintain Digital Wallet Security Brochure PDF
Mentioned slide exhibits various best practices which can be implemented by followed by businesses to secure e-wallets. It includes best practices such as enable passwords, secure network connections, install reliable applications, secure login credentials, and keep personal data private. Retrieve professionally designed Cashless Payment Strategies To Enhance Business Performance Best Practices To Maintain Digital Wallet Security Brochure PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
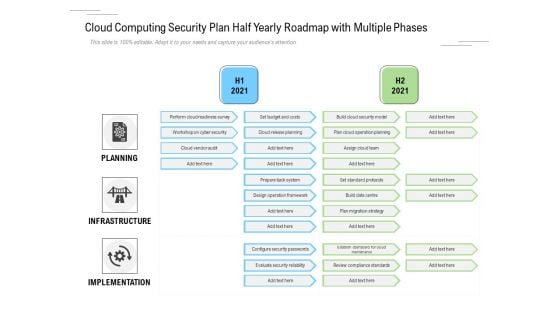
Cloud Computing Security Plan Half Yearly Roadmap With Multiple Phases Topics
Presenting our jaw dropping cloud computing security plan half yearly roadmap with multiple phases topics. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.
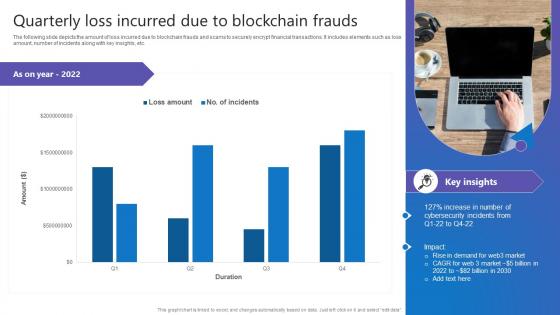
Quarterly Loss Incurred Due Comprehensive Guide To Blockchain Digital Security Themes Pdf
The following slide depicts the amount of loss incurred due to blockchain frauds and scams to securely encrypt financial transactions. It includes elements such as loss amount, number of incidents along with key insights, etc. This Quarterly Loss Incurred Due Comprehensive Guide To Blockchain Digital Security Themes Pdf from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. The following slide depicts the amount of loss incurred due to blockchain frauds and scams to securely encrypt financial transactions. It includes elements such as loss amount, number of incidents along with key insights, etc.
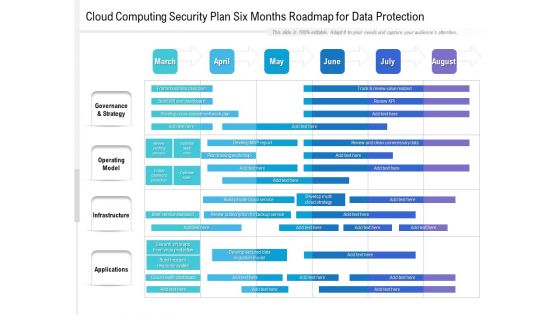
Cloud Computing Security Plan Six Months Roadmap For Data Protection Themes
Presenting our jaw dropping cloud computing security plan six months roadmap for data protection themes. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.
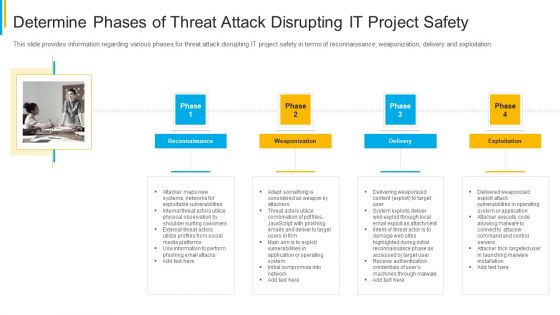
Project Security Administration IT Determine Phases Of Threat Attack Disrupting IT Project Safety Brochure PDF
This slide provides information regarding various phases for threat attack disrupting IT project safety in terms of reconnaissance, weaponization, delivery and exploitation. This is a project security administration it determine phases of threat attack disrupting it project safety brochure pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like reconnaissance, weaponization, delivery, exploitation. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
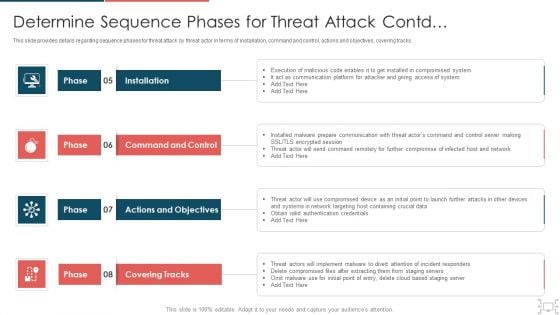
cyber security administration in organization determine sequence phases for threat attack access inspiration pdf
This slide provides details regarding sequence phases for threat attack by threat actor in terms of installation, command and control, actions and objectives, covering tracks. Presenting cyber security administration in organization determine sequence phases for threat attack access inspiration pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like communication, platform, access, compromised, session . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

 Home
Home