Security Kubernetes
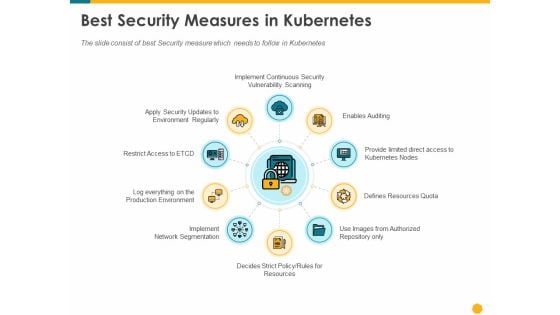
Deploying Docker Container And Kubernetes Within Organization Best Security Measures In Kubernetes Ppt PowerPoint Presentation PDF
Presenting this set of slides with name deploying docker container and kubernetes within organization best security measures in kubernetes ppt powerpoint presentation pdf. This is a ten stage process. The stages in this process are enables auditing provide limited direct access kubernetes nodes, resources quota, authorized repository, rules resources, implement, network segmentation, log everything production environment, restrict access to etcd. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Driving Digital Transformation Through Kubernetes And Containers Best Security Measures In Kubernetes Template PDF
Presenting this set of slides with name driving digital transformation through kubernetes and containers best security measures in kubernetes template pdf. This is a ten stage process. The stages in this process are implement continuous security vulnerability scanning, enables auditing, provide limited direct access to kubernetes nodes, defines resources quota, use images from authorized repository only, defines strict policy, rules for resources, implement network segmentation. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
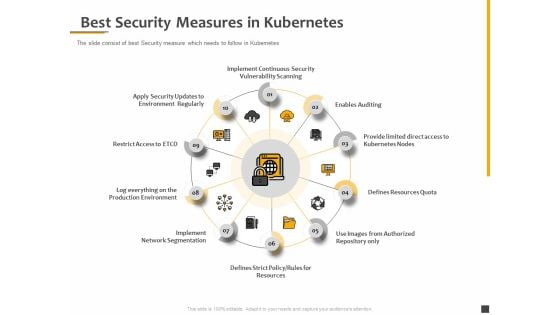
Understanding The Kubernetes Components Through Diagram Best Security Measures In Kubernetes Themes PDF
Presenting this set of slides with name understanding the kubernetes components through diagram best security measures in kubernetes themes pdf. This is a ten stage process. The stages in this process are implement continuous security vulnerability scanning, enables auditing, provide limited direct access to kubernetes nodes, defines resources quota, use images from authorized repository only, defines strict policy, rules for resources, implement network segmentation. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
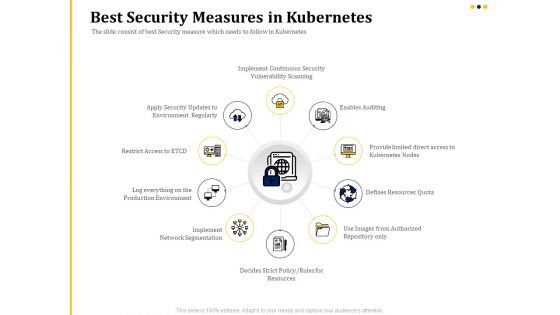
Understanding The Kubernetes Concepts And Architecture Best Security Measures In Kubernetes Ppt Outline Templates PDF
Presenting this set of slides with name understanding the kubernetes concepts and architecture best security measures in kubernetes ppt outline templates pdf. This is a ten stage process. The stages in this process are implement continuous security vulnerability scanning, enables auditing, provide limited direct access to kubernetes nodes, defines resources quota, use images from authorized repository only, defines strict policy, rules for resources, implement network segmentation. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
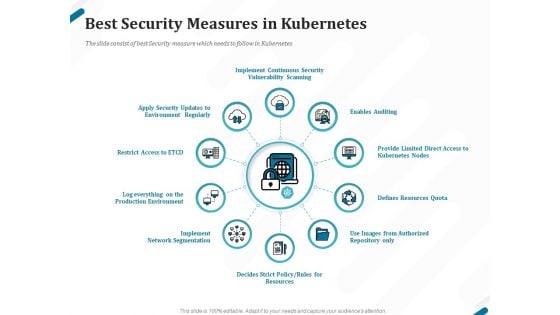
Kubernetes Containers Architecture Overview Best Security Measures In Kubernetes Ppt Pictures File Formats PDF
Presenting this set of slides with name kubernetes containers architecture overview best security measures in kubernetes ppt pictures file formats pdf. This is a ten stage process. The stages in this process are implement continuous security vulnerability scanning, enables auditing, provide limited direct access to kubernetes nodes, defines resources quota, use images from authorized repository only, defines strict policy, rules for resources, implement network segmentation. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Kubernetes Containers Architecture Overview Table Of Content Ppt Summary Layout Ideas PDF
Presenting this set of slides with name kubernetes containers architecture overview table of content ppt summary layout ideas pdf. This is a six stage process. The stages in this process are introduction kubernetes, kubernetes component, nodes kubernetes, kubernetes development process, networking kubernetes, security measures kubernetes. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Understanding The Kubernetes Components Through Diagram Table Of Contents Ppt Ideas Graphic Images
Presenting this set of slides with name understanding the kubernetes components through diagram table of contents ppt ideas graphic images. This is a six stage process. The stages in this process are introduction kubernetes, kubernetes component, nodes kubernetes, kubernetes development process, networking kubernetes, security measures kubernetes. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Understanding The Kubernetes Concepts And Architecture Table Of Contents Ppt Summary Inspiration PDF
Presenting this set of slides with name understanding the kubernetes concepts and architecture table of contents ppt summary inspiration pdf. This is a six stage process. The stages in this process are introduction kubernetes, kubernetes component, nodes kubernetes, kubernetes development process, networking kubernetes, security measures kubernetes. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Deploying Docker Container And Kubernetes Within Organization Table Of Contents Ppt PowerPoint Presentation Infographic Template Aids PDF
Presenting this set of slides with name deploying docker container and kubernetes within organization table of contents ppt powerpoint presentation infographic template aids pdf. This is a six stage process. The stages in this process are introduction of kubernetes, kubernetes component, security measures in kubernetes, networking kubernetes, kubernetes development process, nodes kubernetes. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Container Security Practices Ppt PowerPoint Presentation Slides Portfolio Cpb
Presenting this set of slides with name container security practices ppt powerpoint presentation slides portfolio cpb. This is an editable Powerpoint four stages graphic that deals with topics like container security practices to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Addressing Mobile Device Management Mobile Device Security Management Slides PDF
This slide provides information regarding different mobile device management approach such as container and platform approach that can be selected by vendor based on requirement. Presenting Addressing Mobile Device Management Mobile Device Security Management Slides PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Corporate Owned, Personally Enabled, Equipment Personal. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
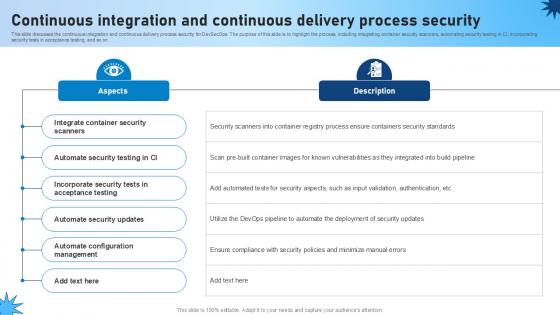
Continuous Integration And Continuous Delivery Process Security Role Of Devsecops Ppt Slide
This slide discusses the continuous integration and continuous delivery process security for DevSecOps. The purpose of this slide is to highlight the process, including integrating container security scanners, automating security testing in CI, incorporating security tests in acceptance testing, and so on. Present like a pro with Continuous Integration And Continuous Delivery Process Security Role Of Devsecops Ppt Slide Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide discusses the continuous integration and continuous delivery process security for DevSecOps. The purpose of this slide is to highlight the process, including integrating container security scanners, automating security testing in CI, incorporating security tests in acceptance testing, and so on.
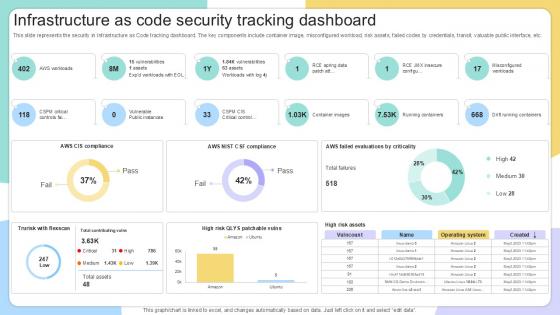
Infrastructure As Code Security IAC Tools For Performance Analysis PPT Slide
This slide represents the security in Infrastructure as Code tracking dashboard. The key components include container image, misconfigured workload, risk assets, failed codes by credentials, transit, valuable public interface, etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Infrastructure As Code Security IAC Tools For Performance Analysis PPT Slide to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Infrastructure As Code Security IAC Tools For Performance Analysis PPT Slide. This slide represents the security in Infrastructure as Code tracking dashboard. The key components include container image, misconfigured workload, risk assets, failed codes by credentials, transit, valuable public interface, etc.
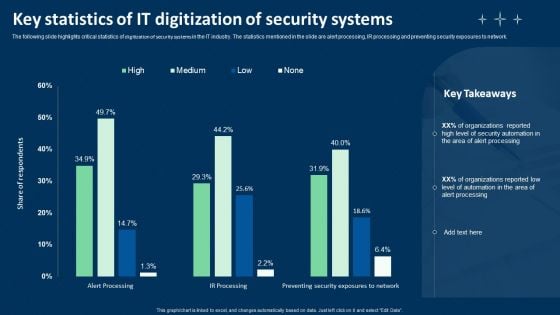
Key Statistics Of IT Digitization Of Security Systems Ppt Layouts Graphics PDF
The following slide highlights four step process of cloud digitization of security systems. The various steps are container configure management, using infrastructure as code, automating asset tagging and vulnerability scanning where security analysts should implement automation. Persuade your audience using this Key Statistics Of IT Digitization Of Security Systems Ppt Layouts Graphics PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Container Configure Management, Use Infrastructure, Code Automate Asset Tagging. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Multistep Process For Automating Cloud Security Operations Ppt Summary File Formats PDF
The following slide highlights four step process of cloud digitization of security systems. The various steps are container configure management, using infrastructure as code, automating asset tagging and vulnerability scanning where security analysts should implement automation. Persuade your audience using this Multistep Process For Automating Cloud Security Operations Ppt Summary File Formats PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Container Configure Management, Use Infrastructure Code, Automate Asset Tagging. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

On Ramp Option 2 Applications And Data Zero Trust Network Security Sample Pdf
This slide describes the second on-ramp option, which is the applications and data of ZTNA implementation. The purpose of this slide is to give an overview of practices and technologies used in this approach, such as data classification, data loss prevention, authentication and authorization of microservices, container security, etc. The On Ramp Option 2 Applications And Data Zero Trust Network Security Sample Pdf is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide describes the second on-ramp option, which is the applications and data of ZTNA implementation. The purpose of this slide is to give an overview of practices and technologies used in this approach, such as data classification, data loss prevention, authentication and authorization of microservices, container security, etc.

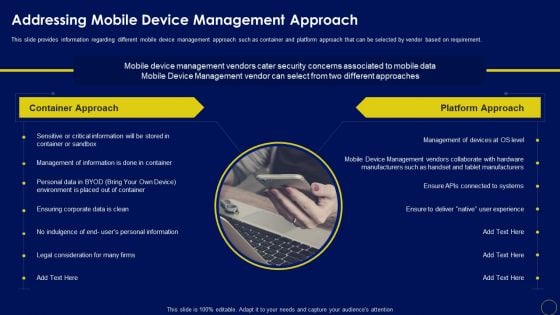
Addressing Mobile Device Management Approach Mobile Device Security Management Designs PDF
This slide provides information regarding different mobile device management approach such as container and platform approach that can be selected by vendor based on requirement. This is a Addressing Mobile Device Management Approach Mobile Device Security Management Designs PDF template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Container Approach, Platform Approach, Critical Information. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Addressing Mobile Device Management Business Mobile Device Security Management Download PDF
This slide provides information regarding different mobile device management approach such as container and platform approach that can be selected by vendor based on requirement. This modern and well-arranged Addressing Mobile Device Management Business Mobile Device Security Management Download PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
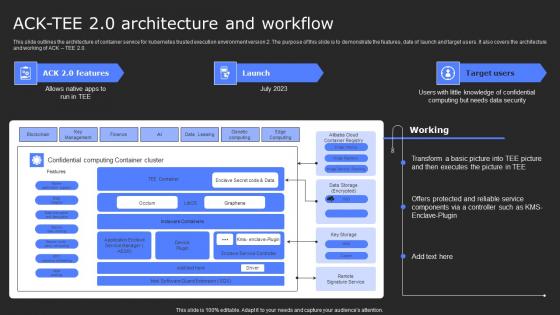
Acktee 20 Architecture And Workflow Secure Computing Framework Guidelines Pdf
This slide outlines the architecture of container service for kubernetes trusted execution environment version 2. The purpose of this slide is to demonstrate the features, date of launch and target users. It also covers the architecture and working of ACK TEE 2.0. Boost your pitch with our creative Acktee 20 Architecture And Workflow Secure Computing Framework Guidelines Pdf. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide outlines the architecture of container service for kubernetes trusted execution environment version 2. The purpose of this slide is to demonstrate the features, date of launch and target users. It also covers the architecture and working of ACK TEE 2.0.
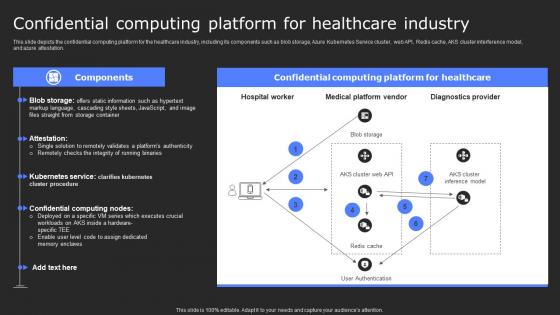
Confidential Computing Platform For Healthcare Secure Computing Framework Structure Pdf
This slide depicts the confidential computing platform for the healthcare industry, including its components such as blob storage, Azure Kubernetes Service cluster, web API, Redis cache, AKS cluster interference model, and azure attestation. Welcome to our selection of the Confidential Computing Platform For Healthcare Secure Computing Framework Structure Pdf. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today This slide depicts the confidential computing platform for the healthcare industry, including its components such as blob storage, Azure Kubernetes Service cluster, web API, Redis cache, AKS cluster interference model, and azure attestation.
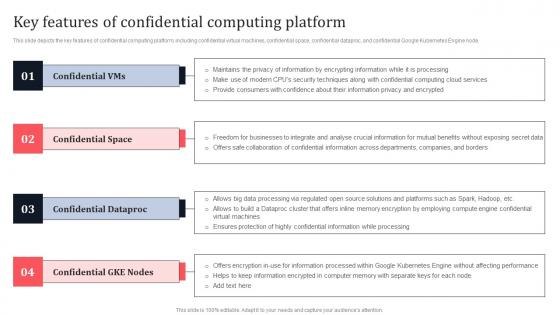
Key Features Of Confidential Computing Platform Secure Multi Party Background Pdf
This slide depicts the key features of confidential computing platform, including confidential virtual machines, confidential space, confidential dataproc, and confidential Google Kubernetes Engine node. Find a pre-designed and impeccable Key Features Of Confidential Computing Platform Secure Multi Party Background Pdf The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide depicts the key features of confidential computing platform, including confidential virtual machines, confidential space, confidential dataproc, and confidential Google Kubernetes Engine node.
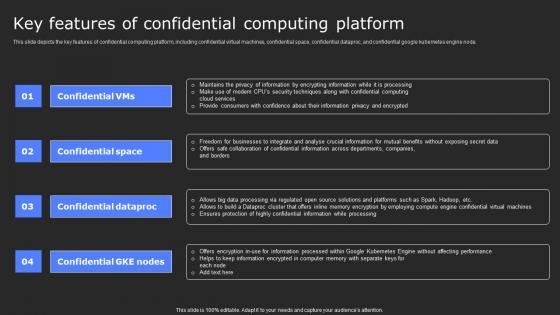
Key Features Of Confidential Computing Platform Secure Computing Framework Brochure Pdf
This slide depicts the key features of confidential computing platform, including confidential virtual machines, confidential space, confidential dataproc, and confidential google kubernetes engine node. Create an editable Key Features Of Confidential Computing Platform Secure Computing Framework Brochure Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Key Features Of Confidential Computing Platform Secure Computing Framework Brochure Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide depicts the key features of confidential computing platform, including confidential virtual machines, confidential space, confidential dataproc, and confidential google kubernetes engine node.
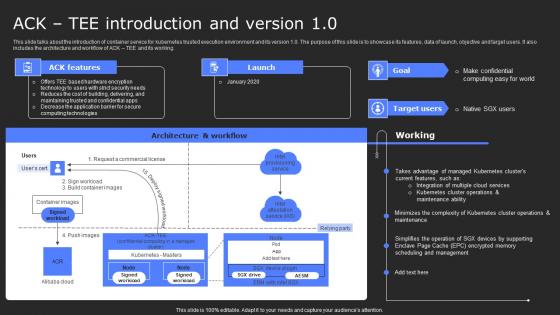
ACK Tee Introduction And Version 10 Secure Computing Framework Slides Pdf
This slide talks about the introduction of container service for kubernetes trusted execution environment and its version 1.0. The purpose of this slide is to showcase its features, data of launch, objective and target users. It also includes the architecture and workflow of ACK TEE and its working. Find a pre-designed and impeccable ACK Tee Introduction And Version 10 Secure Computing Framework Slides Pdf. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide talks about the introduction of container service for kubernetes trusted execution environment and its version 1.0. The purpose of this slide is to showcase its features, data of launch, objective and target users. It also includes the architecture and workflow of ACK TEE and its working.
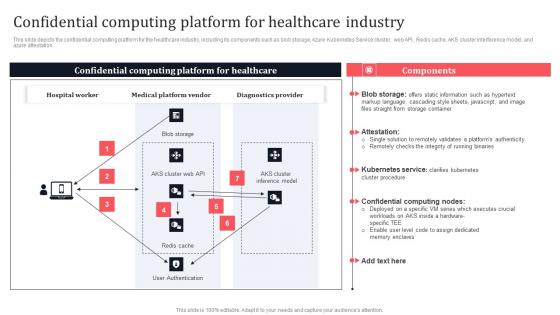
Confidential Computing Platform For Healthcare Industry Secure Multi Party Information Pdf
This slide depicts the confidential computing platform for the healthcare industry, including its components such as blob storage, Azure Kubernetes Service cluster, web API, Redis cache, AKS cluster interference model, and azure attestation. This modern and well-arranged Confidential Computing Platform For Healthcare Industry Secure Multi Party Information Pdf provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide depicts the confidential computing platform for the healthcare industry, including its components such as blob storage, Azure Kubernetes Service cluster, web API, Redis cache, AKS cluster interference model, and azure attestation.
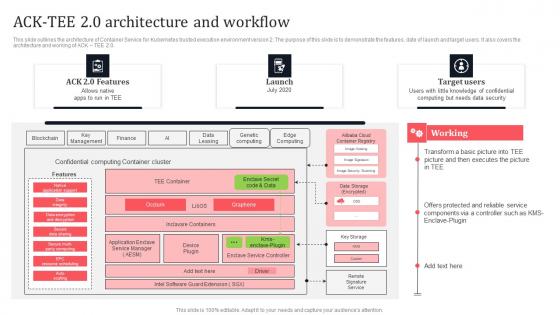
Ack Tee 2 0 Architecture And Workflow Secure Multi Party Mockup Pdf
This slide outlines the architecture of Container Service for Kubernetes trusted execution environment version 2. The purpose of this slide is to demonstrate the features, date of launch and target users. It also covers the architecture and working of ACK TEE 2.0. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Ack Tee 2 0 Architecture And Workflow Secure Multi Party Mockup Pdf to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Ack Tee 2 0 Architecture And Workflow Secure Multi Party Mockup Pdf This slide outlines the architecture of Container Service for Kubernetes trusted execution environment version 2. The purpose of this slide is to demonstrate the features, date of launch and target users. It also covers the architecture and working of ACK TEE 2.0.
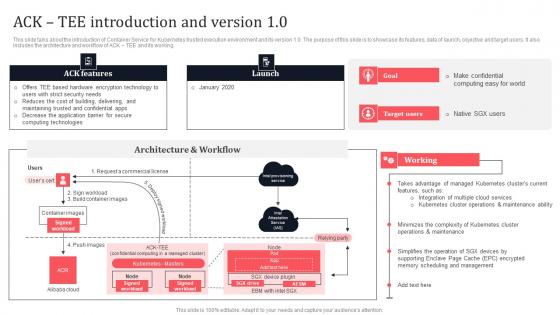
Ack Tee Introduction And Version 1 0 Secure Multi Party Slides Pdf
This slide talks about the introduction of Container Service for Kubernetes trusted execution environment and its version 1.0. The purpose of this slide is to showcase its features, data of launch, objective and target users. It also includes the architecture and workflow of ACK TEE and its working. This Ack Tee Introduction And Version 1 0 Secure Multi Party Slides Pdf from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide talks about the introduction of Container Service for Kubernetes trusted execution environment and its version 1.0. The purpose of this slide is to showcase its features, data of launch, objective and target users. It also includes the architecture and workflow of ACK TEE and its working.
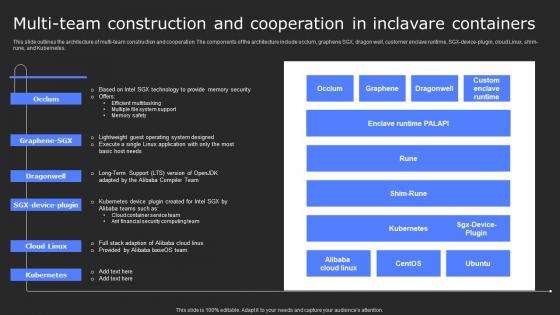
Multi Team Construction And Cooperation In Secure Computing Framework Background Pdf
This slide outlines the architecture of multi-team construction and cooperation. The components of the architecture include occlum, graphene SGX, dragon well, customer enclave runtime, SGX-device-plugin, cloud Linux, shim-rune, and Kubernetes. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Multi Team Construction And Cooperation In Secure Computing Framework Background Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide outlines the architecture of multi-team construction and cooperation. The components of the architecture include occlum, graphene SGX, dragon well, customer enclave runtime, SGX-device-plugin, cloud Linux, shim-rune, and Kubernetes.
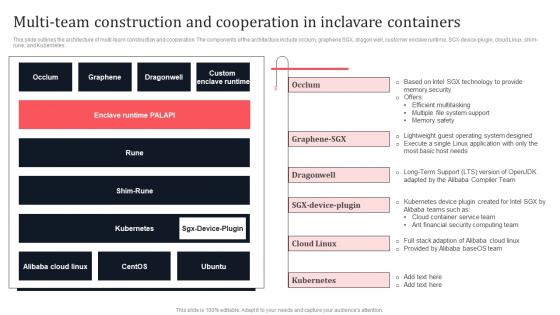
Multi Team Construction And Cooperation In Inclavare Containers Secure Multi Party Pictures Pdf
This slide outlines the architecture of multi-team construction and cooperation. The components of the architecture include occlum, graphene SGX, dragon well, customer enclave runtime, SGX-device-plugin, cloud Linux, shim-rune, and Kubernetes. Boost your pitch with our creative Multi Team Construction And Cooperation In Inclavare Containers Secure Multi Party Pictures Pdf Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide outlines the architecture of multi-team construction and cooperation. The components of the architecture include occlum, graphene SGX, dragon well, customer enclave runtime, SGX-device-plugin, cloud Linux, shim-rune, and Kubernetes.

Products And Services Offered Data Management Company Investor Funding Pitch Deck
This slide shows the various product or solutions offered by an IT company which consists of data protection, hybrid cloud, data lakehouse, kubernetes, rnsomeware protection, hyperstore object storage, hyperfile NAS storage, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Products And Services Offered Data Management Company Investor Funding Pitch Deck to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide shows the various product or solutions offered by an IT company which consists of data protection, hybrid cloud, data lakehouse, kubernetes, rnsomeware protection, hyperstore object storage, hyperfile NAS storage, etc.
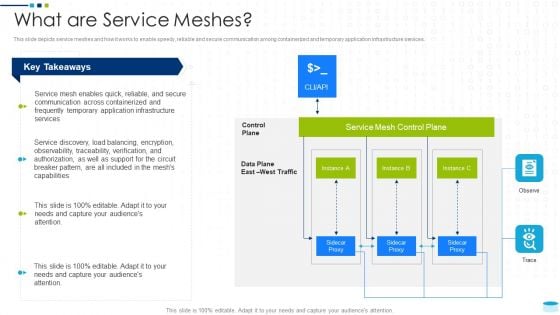
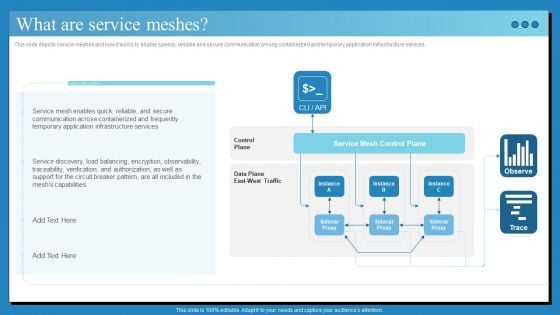
Data Center Infrastructure Management IT What Are Service Meshes Slides PDF
This slide depicts service meshes and how it works to enable speedy, reliable and secure communication among containerized and temporary application infrastructure services. Deliver and pitch your topic in the best possible manner with this data center infrastructure management it what are service meshes slides pdf. Use them to share invaluable insights on service, communication, infrastructure, capabilities and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Data Center Infrastructure Technologies What Are Service Meshes Topics PDF
This slide depicts service meshes and how it works to enable speedy, reliable and secure communication among containerized and temporary application infrastructure services. Explore a selection of the finest Data Center Infrastructure Technologies What Are Service Meshes Topics PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Data Center Infrastructure Technologies What Are Service Meshes Topics PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

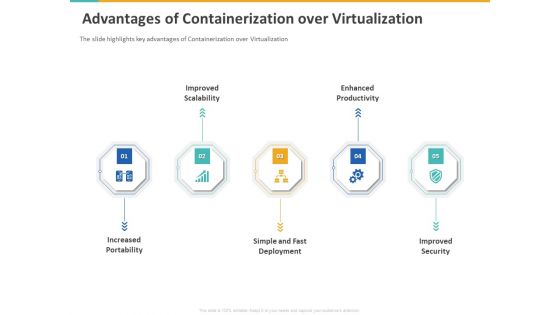
Road Digital Transformation Through Containerization Advantages Of Containerization Over Virtualization Structure PDF
The slide highlights key advantages of containerization over virtualization. This is a road digital transformation through containerization advantages of containerization over virtualization structure pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like increased portability, improved scalability, simple and fast deployment, enhanced productivity, improved security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
A Step By Step Guide To Continuous Deployment Advantages Of Containerization Over Virtualization Introduction PDF
Presenting this set of slides with name a step by step guide to continuous deployment advantages of containerization over virtualization introduction pdf. This is a five stage process. The stages in this process are increased portability, improved scalability, simple and fast deployment, enhanced productivity, improved security. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Development And Operations Pipeline IT Periodic Table Of Devops Tools Designs PDF
Deliver an awe inspiring pitch with this creative development and operations pipeline it periodic table of devops tools designs pdf bundle. Topics like database, deployment, security, containerization, monitoring can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Introduction To Shipment Tracking IoT Fleet Monitoring Ppt Slide IoT SS V
This slide provides an overview of vehicle tracking through IoT-enabled devices. The slide further includes types and applications of container tracking solutions that are asset tracking, inventory management, safety and security, inbound and outbound logistics. This modern and well-arranged Introduction To Shipment Tracking IoT Fleet Monitoring Ppt Slide IoT SS V provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide provides an overview of vehicle tracking through IoT-enabled devices. The slide further includes types and applications of container tracking solutions that are asset tracking, inventory management, safety and security, inbound and outbound logistics.

Roadmap To Identify And Launch Devops Initiatives Ppt Professional Slide Download PDF
This template covers DevOps implementation roadmaps starting from organizing devOps initiative, then building, containerizing, integrating, test automation and monitoring etc. Deliver and pitch your topic in the best possible manner with this roadmap to identify and launch devops initiatives ppt professional slide download pdf. Use them to share invaluable insights on process, security, strategy, opportunities and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

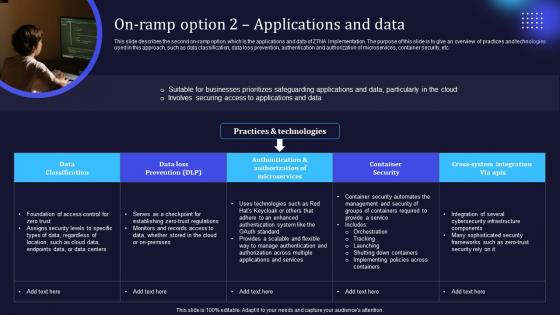
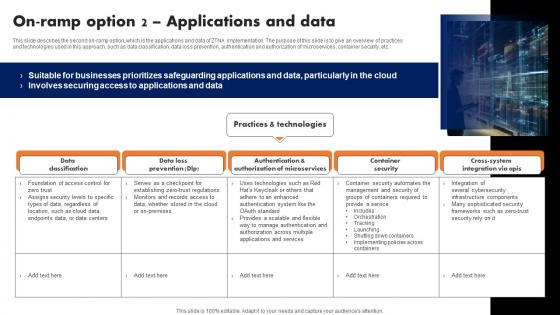
On Ramp Option 2 Applications And Data Zero Trust Network Access
This slide describes the second on-ramp option, which is the applications and data of ZTNA implementation. The purpose of this slide is to give an overview of practices and technologies used in this approach, such as data classification, data loss prevention, authentication and authorization of microservices, container security, etc. Slidegeeks is here to make your presentations a breeze with On Ramp Option 2 Applications And Data Zero Trust Network Access With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide describes the second on-ramp option, which is the applications and data of ZTNA implementation. The purpose of this slide is to give an overview of practices and technologies used in this approach, such as data classification, data loss prevention, authentication and authorization of microservices, container security, etc.
Zero Trust Model On Ramp Option 2 Applications And Data
This slide describes the second on-ramp option, which is the applications and data of ZTNA implementation. The purpose of this slide is to give an overview of practices and technologies used in this approach, such as data classification, data loss prevention, authentication and authorization of microservices, container security, etc. Slidegeeks has constructed Zero Trust Model On Ramp Option 2 Applications And Data after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide describes the second on-ramp option, which is the applications and data of ZTNA implementation. The purpose of this slide is to give an overview of practices and technologies used in this approach, such as data classification, data loss prevention, authentication and authorization of microservices, container security, etc.
On Ramp Option 2 Applications And Data Software Defined Perimeter SDP
This slide describes the second on-ramp option, which is the applications and data of ZTNA implementation. The purpose of this slide is to give an overview of practices and technologies used in this approach, such as data classification, data loss prevention, authentication and authorization of microservices, container security, etc. The On Ramp Option 2 Applications And Data Software Defined Perimeter SDP is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide describes the second on-ramp option, which is the applications and data of ZTNA implementation. The purpose of this slide is to give an overview of practices and technologies used in this approach, such as data classification, data loss prevention, authentication and authorization of microservices, container security, etc.
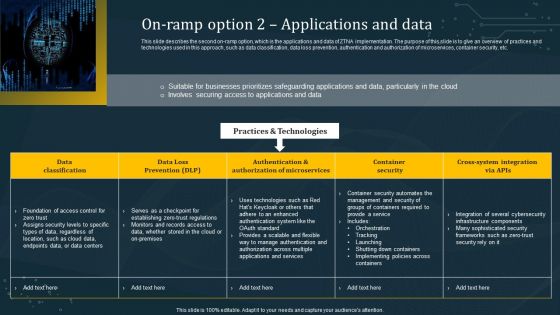
On Ramp Option 2 Applications And Data Template PDF
This slide describes the second on-ramp option, which is the applications and data of ZTNA implementation. The purpose of this slide is to give an overview of practices and technologies used in this approach, such as data classification, data loss prevention, authentication and authorization of microservices, container security, etc. Take your projects to the next level with our ultimate collection of On Ramp Option 2 Applications And Data Template PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest
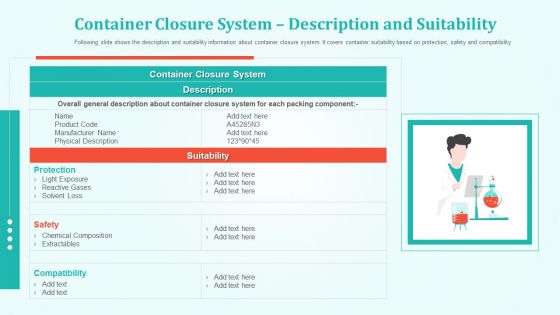
Container Closure System Description And Suitability Themes PDF
Following slide shows the description and suitability information about container closure system. It covers container suitability based on protection, safety and compatibility. Deliver an awe inspiring pitch with this creative container closure system description and suitability themes pdf bundle. Topics like protection, safety, compatibility can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Pharmaceutical Transformation For Inclusive Goods Container Closure System Description And Suitability Graphics PDF
Following slide shows the description and suitability information about container closure system. It covers container suitability based on protection, safety and compatibility. Deliver an awe inspiring pitch with this creative pharmaceutical transformation for inclusive goods container closure system description and suitability graphics pdf bundle. Topics like protection, safety, compatibility, suitability can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
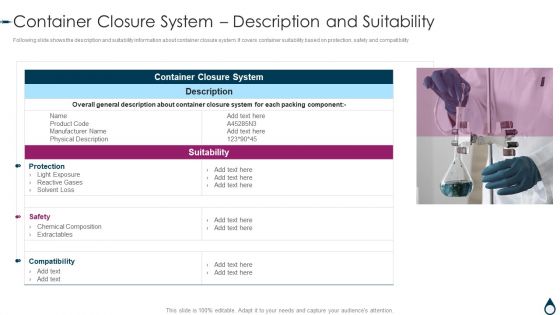
Quality Manufacturing Process For Generic Medicines Container Closure System Description Slides PDF
Following slide shows the description and suitability information about container closure system. It covers container suitability based on protection, safety and compatibility. Deliver an awe inspiring pitch with this creative Quality Manufacturing Process For Generic Medicines Container Closure System Description Slides PDF bundle. Topics like System, Compatibility, Suitability can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Supervisors Checking Stock Safety At Container Terminal Ppt PowerPoint Presentation Gallery Format PDF
Showcasing this set of slides titled supervisors checking stock safety at container terminal ppt powerpoint presentation gallery format pdf. The topics addressed in these templates are supervisors checking stock safety at container terminal. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
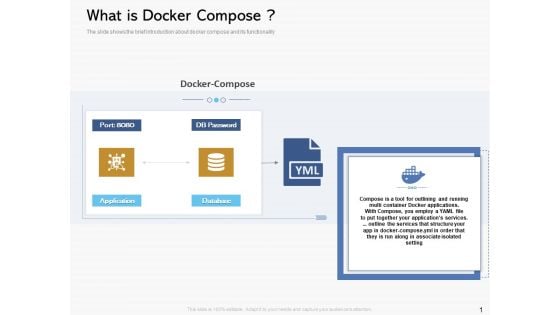
Road Digital Transformation Through Containerization What Is Docker Compose Designs PDF
The slide shows the brief introduction about docker compose and its functionality. Deliver and pitch your topic in the best possible manner with this road digital transformation through containerization what is docker compose designs pdf. Use them to share invaluable insights on docker compose, db password, application, database, docker applications and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Comprehensive Overview Of Food Packaging In Industry
The slide showcases overview and introduction of packaging that ensures protection of food from harmful environmental factors that may cause contamination or damage to the food quality in container. There are so many reasons you need a Comprehensive Overview Of Food Packaging In Industry. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. The slide showcases overview and introduction of packaging that ensures protection of food from harmful environmental factors that may cause contamination or damage to the food quality in container.

Comprehensive Guide On Current Strategies Comprehensive Overview Of Food Packaging In Industry
The slide showcases overview and introduction of packaging that ensures protection of food from harmful environmental factors that may cause contamination or damage to the food quality in container. There are so many reasons you need a Comprehensive Guide On Current Strategies Comprehensive Overview Of Food Packaging In Industry. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. The slide showcases overview and introduction of packaging that ensures protection of food from harmful environmental factors that may cause contamination or damage to the food quality in container.

Comprehensive Overview Of Effective Strategies For Strengthening Food Ppt Presentation
The slide showcases overview and introduction of packaging that ensures protection of food from harmful environmental factors that may cause contamination or damage to the food quality in container. There are so many reasons you need a Comprehensive Overview Of Effective Strategies For Strengthening Food Ppt Presentation. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. The slide showcases overview and introduction of packaging that ensures protection of food from harmful environmental factors that may cause contamination or damage to the food quality in container.
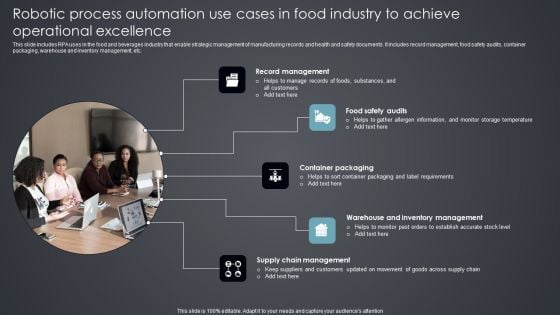
Robotic Process Automation Use Cases In Food Industry To Achieve Operational Excellence Information PDF
This slide includes RPA uses in the food and beverages industry that enable strategic management of manufacturing records and health and safety documents. It includes record management, food safety audits, container packaging, warehouse and inventory management, etc. Presenting Robotic Process Automation Use Cases In Food Industry To Achieve Operational Excellence Information PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Record Management, Food Safety Audits, Container Packaging. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
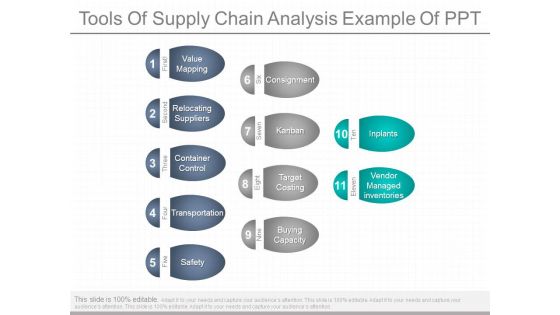
Tools Of Supply Chain Analysis Example Of Ppt
This is a tools of supply chain analysis example of ppt. This is a eleven stage process. The stages in this process are first, value mapping, second, relocating suppliers, three, container control, four, transportation, five, safety, six, consignment, seven, kanban, eight, target costing, nine, buying capacity, ten, inplants, eleven, vendor managed inventories.
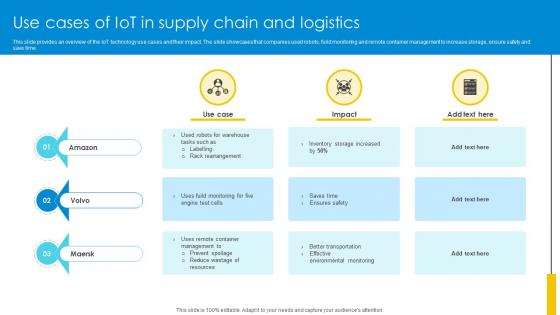
Use Cases Of IoT In Supply Chain And Logistics Optimizing Inventory Management IoT SS V
This slide provides an overview of the IoT technology use cases and their impact. The slide showcases that companies used robots, fuild monitoring and remote container management to increase storage, ensure safety and save time. Find a pre-designed and impeccable Use Cases Of IoT In Supply Chain And Logistics Optimizing Inventory Management IoT SS V. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide provides an overview of the IoT technology use cases and their impact. The slide showcases that companies used robots, fuild monitoring and remote container management to increase storage, ensure safety and save time.

Business People 3d Man With Recycle Bin Reuse PowerPoint Templates Ppt Backgrounds For Slides
We present our business people 3d man with recycle bin reuse PowerPoint templates PPT backgrounds for slides.Present our Technology PowerPoint Templates because It will get your audience in sync. Download and present our Success PowerPoint Templates because You are well armed with penetrative ideas. Our PowerPoint Templates and Slides will provide the gunpowder you need. Present our Business PowerPoint Templates because Watching this your Audience will Grab their eyeballs, they wont even blink. Download our Shapes PowerPoint Templates because Our PowerPoint Templates and Slides are Clear and concise. Use them and dispel any doubts your team may have. Download our Curves and Lines PowerPoint Templates because Our PowerPoint Templates and Slides are created by a hardworking bunch of busybees. Always flitting around with solutions gauranteed to please.Use these PowerPoint slides for presentations relating to 3d, Bin, Cap, Child, Clean, Concept, Conservation, Container, Eco, Ecologic, Ecological, Ecology, Empty, Environment, Environmental, Female, Garbage, Girl, Holding, Isolated, Male, Open, People, Person, Plastic, Protect, Recyclable, Recycle, Recycling, Recycling Bin, Red, Responsibility, Reusable, Reuse, Rubbish, Stand, Symbol, Thumb Up, Trash, Waste, White, Woman, Young. The prominent colors used in the PowerPoint template are Red, Gray, Black. Stand on your own feet with our Business People 3d Man With Recycle Bin Reuse PowerPoint Templates Ppt Backgrounds For Slides. They will deliver all the assistance you need.


 Continue with Email
Continue with Email

 Home
Home


































