Security Management
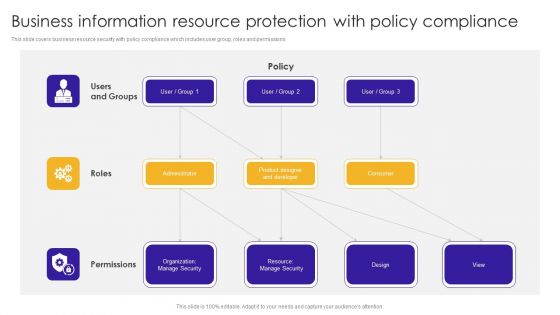
Business Information Resource Protection With Policy Compliance Information PDF
This slide covers business resource security with policy compliance which includes user group, roles and permissions. Showcasing this set of slides titled Business Information Resource Protection With Policy Compliance Information PDF. The topics addressed in these templates are Product Designer, Organization Manage, Resource Manage. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
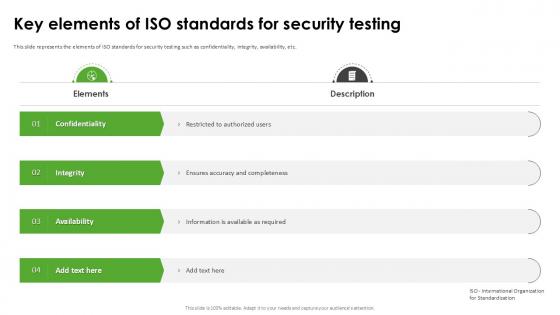
Key Elements Of Iso Standards Harnessing The World Of Ethical Ppt Presentation
This slide represents the elements of ISO standards for security testing such as confidentiality, integrity, availability, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Key Elements Of Iso Standards Harnessing The World Of Ethical Ppt Presentation and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide represents the elements of ISO standards for security testing such as confidentiality, integrity, availability, etc.

Clarify Roles And Responsibilities Of STO Exploring Investment Opportunities Infographics Pdf
The following slide illustrates major roles and responsibilities of security token offerings team to ensure successful launch. It includes elements such as technical officer, community manager, engineers, developers, founder, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Clarify Roles And Responsibilities Of STO Exploring Investment Opportunities Infographics Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. The following slide illustrates major roles and responsibilities of security token offerings team to ensure successful launch. It includes elements such as technical officer, community manager, engineers, developers, founder, etc.
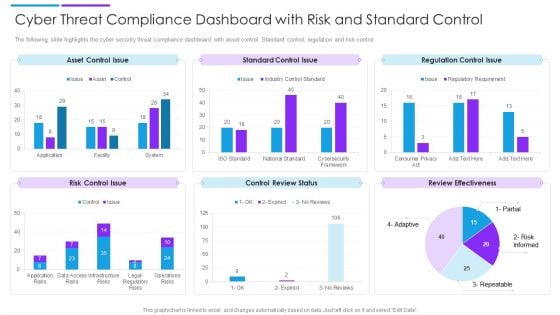
Cyber Threat Compliance Dashboard With Risk And Standard Control Sample PDF
The following slide highlights the cyber security threat compliance dashboard with asset control. Standard control, regulation and risk control. Showcasing this set of slides titled cyber threat compliance dashboard with risk and standard control sample pdf. The topics addressed in these templates are asset control issue, standard control issue, regulation control issue. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Factors Influencing Software Defined Networking SDN Adoption Evolution Of SDN Controllers Slides Pdf
This slide represents the factors influencing SDN adoption, including cultural change, security risks, interoperability, scalability, performance, and reliability. SDN is appealing regarding network simplicity and investment, and operational cost savings. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Factors Influencing Software Defined Networking SDN Adoption Evolution Of SDN Controllers Slides Pdf and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide represents the factors influencing SDN adoption, including cultural change, security risks, interoperability, scalability, performance, and reliability. SDN is appealing regarding network simplicity and investment, and operational cost savings.
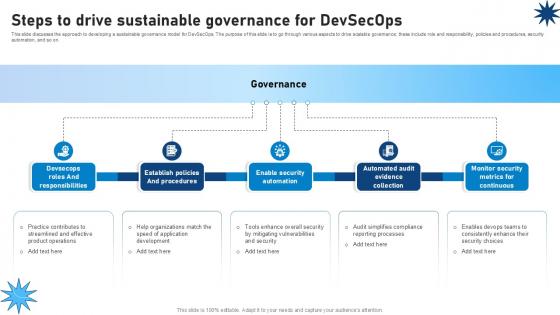
Steps To Drive Sustainable Governance For Devsecops Role Of Devsecops Ppt Sample
This slide discusses the approach to developing a sustainable governance model for DevSecOps. The purpose of this slide is to go through various aspects to drive scalable governance these include role and responsibility, policies and procedures, security automation, and so on. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Steps To Drive Sustainable Governance For Devsecops Role Of Devsecops Ppt Sample will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide discusses the approach to developing a sustainable governance model for DevSecOps. The purpose of this slide is to go through various aspects to drive scalable governance these include role and responsibility, policies and procedures, security automation, and so on.
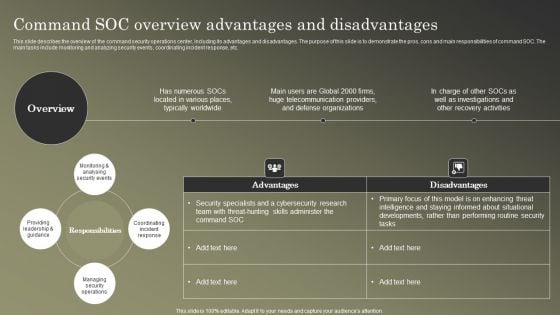
Cybersecurity Operations Cybersecops Command SOC Overview Advantages Mockup PDF
This slide describes the overview of the command security operations center, including its advantages and disadvantages. The purpose of this slide is to demonstrate the pros, cons and main responsibilities of command SOC. The main tasks include monitoring and analyzing security events, coordinating incident response, etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Cybersecurity Operations Cybersecops Command SOC Overview Advantages Mockup PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Cybersecurity Operations Cybersecops Command SOC Overview Advantages Mockup PDF
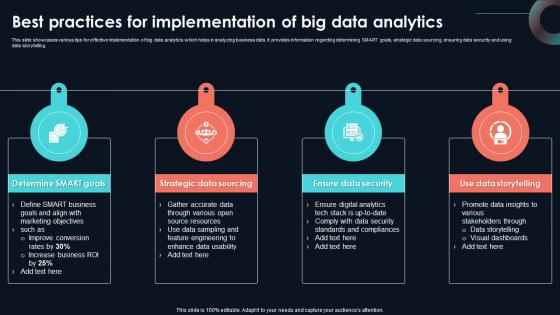
Best Practices For Implementation Of Developing Strategic Insights Using Big Data Analytics SS V
This slide showcases various tips for effective implementation of big data analytics which helps in analyzing business data. It provides information regarding determining SMART goals, strategic data sourcing, ensuring data security and using data storytelling. Present like a pro with Best Practices For Implementation Of Developing Strategic Insights Using Big Data Analytics SS V. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide showcases various tips for effective implementation of big data analytics which helps in analyzing business data. It provides information regarding determining SMART goals, strategic data sourcing, ensuring data security and using data storytelling.
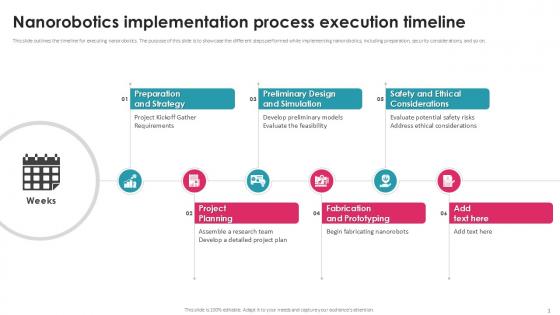
Nanorobotics Implementation Process Execution Timeline PPT Example
This slide outlines the timeline for executing nanorobotics. The purpose of this slide is to showcase the different steps performed while implementing nanorobotics, including preparation, security considerations, and so on. Find a pre-designed and impeccable Nanorobotics Implementation Process Execution Timeline PPT Example. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide outlines the timeline for executing nanorobotics. The purpose of this slide is to showcase the different steps performed while implementing nanorobotics, including preparation, security considerations, and so on.
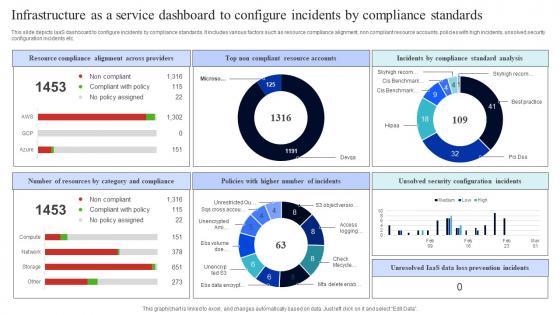
Infrastructure As A Service Dashboard To Configure Incidents By Compliance Standards Rules Pdf
This slide depicts IaaS dashboard to configure incidents by compliance standards. It includes various factors such as resource compliance alignment, non compliant resource accounts, policies with high incidents, unsolved security configuration incidents etc. Pitch your topic with ease and precision using this Infrastructure As A Service Dashboard To Configure Incidents By Compliance Standards Rules Pdf. This layout presents information on Resource Compliance Alignment, Across Providers, Top Non Compliant, Resource Accounts. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide depicts IaaS dashboard to configure incidents by compliance standards. It includes various factors such as resource compliance alignment, non compliant resource accounts, policies with high incidents, unsolved security configuration incidents etc.
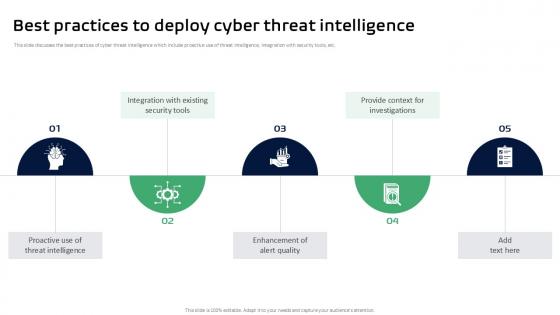
Best Practices To Deploy Cyber Threat Intelligence Ppt Slides
This slide discusses the best practices of cyber threat intelligence which include proactive use of threat intelligence, integration with security tools, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Best Practices To Deploy Cyber Threat Intelligence Ppt Slides for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide discusses the best practices of cyber threat intelligence which include proactive use of threat intelligence, integration with security tools, etc.

Online Business Challenges And Best Practices Brochure Pdf
The slide displays pain points in e-commerce along with best practices to prevent facing these issues. It includes challenges such as limited capital, huge marketing efforts, cyber security issues, etc and best practices such as government support, public relation strategy, etc. Pitch your topic with ease and precision using this Online Business Challenges And Best Practices Brochure Pdf. This layout presents information on Pain Points, Best Practices. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. The slide displays pain points in e-commerce along with best practices to prevent facing these issues. It includes challenges such as limited capital, huge marketing efforts, cyber security issues, etc and best practices such as government support, public relation strategy, etc.
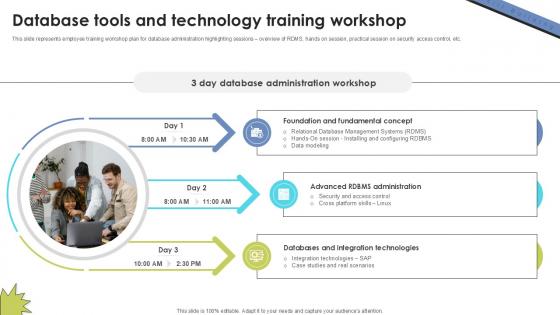
Database Tools And Technology Skill Building Plan For Application PPT Presentation DTE SS V
This slide represents employee training workshop plan for database administration highlighting sessions overview of RDMS, hands on session, practical session on security access control, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Database Tools And Technology Skill Building Plan For Application PPT Presentation DTE SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide represents employee training workshop plan for database administration highlighting sessions overview of RDMS, hands on session, practical session on security access control, etc.

Key Challenges Faced By Businesses Digital Platform Administration For B2B Ecommerce Clipart Pdf
This slide represents major challenges during b2b payments faced by businesses along with solutions. It covers interoperability between business, security breaches, broken financial workflow and lack of cash flow tracking. Are you searching for a Key Challenges Faced By Businesses Digital Platform Administration For B2B Ecommerce Clipart Pdf that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Key Challenges Faced By Businesses Digital Platform Administration For B2B Ecommerce Clipart Pdf from Slidegeeks today. This slide represents major challenges during b2b payments faced by businesses along with solutions. It covers interoperability between business, security breaches, broken financial workflow and lack of cash flow tracking.

A48 Zero Trust Network Access Architectural Models
This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption. Boost your pitch with our creative A48 Zero Trust Network Access Architectural Models. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption.

Zero Trust Network Access System Use Cases Summary PDF
This slide outlines multiple use cases of zero-trust network access systems. The purpose of this slide is to showcase the main use cases of the ZTNA model, which are replacing VPN and MPLS connections, internal firewall replacement, securing remote access to private apps, limiting user access, and so on. Boost your pitch with our creative Zero Trust Network Access System Use Cases Summary PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
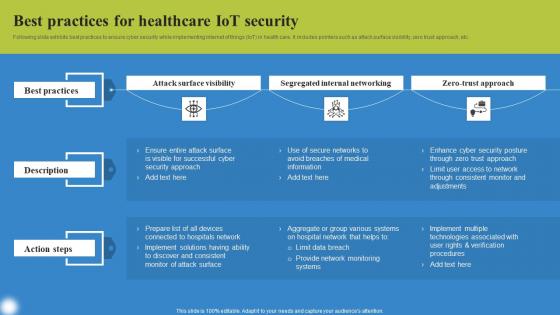
Best Practices For Healthcare Deploying IoT Solutions For Enhanced Healthcare Template Pdf
Following slide exhibits best practices to ensure cyber security while implementing internet of things IoT in health care. It includes pointers such as attack surface visibility, zero trust approach, etc. This modern and well arranged Best Practices For Healthcare Deploying IoT Solutions For Enhanced Healthcare Template Pdf provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. Following slide exhibits best practices to ensure cyber security while implementing internet of things IoT in health care. It includes pointers such as attack surface visibility, zero trust approach, etc.
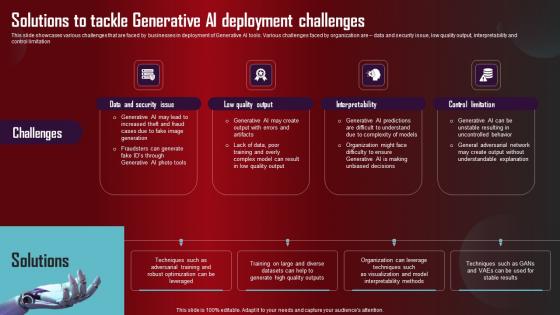
Solutions To Tackle Generative AI Role Of Generative AI Tools Across Portrait Pdf
This slide showcases various challenges that are faced by businesses in deployment of Generative AI tools. Various challenges faced by organization are data and security issue, low quality output, interpretability and control limitation Present like a pro with Solutions To Tackle Generative AI Role Of Generative AI Tools Across Portrait Pdf Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide showcases various challenges that are faced by businesses in deployment of Generative AI tools. Various challenges faced by organization are data and security issue, low quality output, interpretability and control limitation.

Implement General Data Protection Regulation DT SS V
This slide presents actions to establish a safe-custodian image in retail industry. It includes integrating general data protection and regulation with steps understand GDPR, data audit, consent and legal basis, privacy notices and policies, data security and breach notification and ongoing compliance. Find a pre-designed and impeccable Implement General Data Protection Regulation DT SS V. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide presents actions to establish a safe-custodian image in retail industry. It includes integrating general data protection and regulation with steps understand GDPR, data audit, consent and legal basis, privacy notices and policies, data security and breach notification and ongoing compliance.
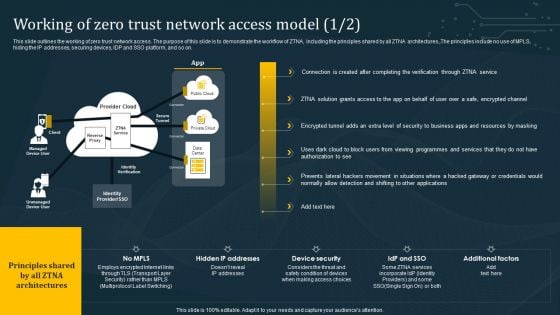
Working Of Zero Trust Network Access Model Summary PDF
This slide outlines the working of zero trust network access. The purpose of this slide is to demonstrate the workflow of ZTNA, including the principles shared by all ZTNA architectures. The principles include no use of MPLS, hiding the IP addresses, securing devices, IDP and SSO platform, and so on. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Working Of Zero Trust Network Access Model Summary PDF from Slidegeeks and deliver a wonderful presentation.
Strategies For Conveyance Of Large Event Safety Plan Icons Pdf
This slide highlights major strategies to communicate effectively for large event security plans in order to ensure the safety of the business and enhance confidence among stakeholders. Key strategies are to inspect the venue, conduct a risk assessment, assess large-scale attacks, etc. Pitch your topic with ease and precision using this Strategies For Conveyance Of Large Event Safety Plan Icons Pdf. This layout presents information on Inspect The Venue, Conduct Risk Assessment, Crowd Controlling Measures. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide highlights major strategies to communicate effectively for large event security plans in order to ensure the safety of the business and enhance confidence among stakeholders. Key strategies are to inspect the venue, conduct a risk assessment, assess large-scale attacks, etc.

Zero Trust Network Access Architectural Models Ideas Pdf
This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption. There are so many reasons you need a Zero Trust Network Access Architectural Models Ideas Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption.
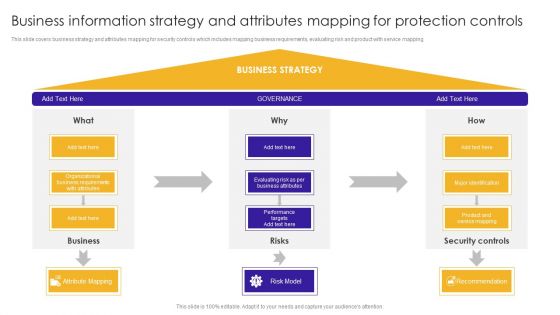
Business Information Strategy And Attributes Mapping For Protection Controls Portrait PDF
This slide covers business strategy and attributes mapping for security controls which includes mapping business requirements, evaluating risk and product with service mapping. Showcasing this set of slides titled Business Information Strategy And Attributes Mapping For Protection Controls Portrait PDF. The topics addressed in these templates are Major Identification, Service Mapping, Recommendation. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
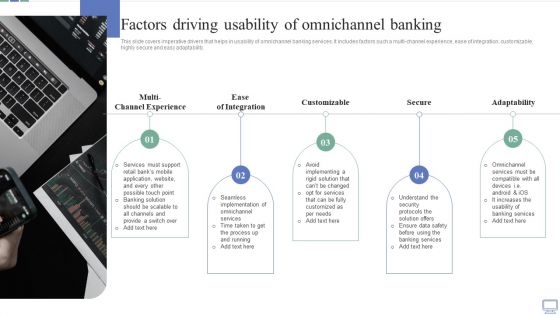
Omnichannel Banking Services Platform Factors Driving Usability Of Omnichannel Banking Background PDF
This slide covers imperative drivers that helps in usability of omnichannel banking services. It includes factors such a multi channel experience, ease of integration, customizable, highly secure and easy adaptability. Get a simple yet stunning designed Omnichannel Banking Services Platform Factors Driving Usability Of Omnichannel Banking Background PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Omnichannel Banking Services Platform Factors Driving Usability Of Omnichannel Banking Background PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Performing Cyber Training Exercises For Improving Cybersecurity With Incident Introduction PDF
Purpose of this slide is to address and perform various cyber training exercises in order to secure companys assets. Exercises covered are defense in depth, capture the flag etc.Welcome to our selection of the Performing Cyber Training Exercises For Improving Cybersecurity With Incident Introduction PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100precent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.

Aiops Use Cases Related To Cloudops Devops And Secops Information PDF
This slide describes the AIOps use cases to automate cloudops, devops, and secops operations. This slide aims to showcase how aiops can be applied to multi-cloud operations, development environments, and secure applications in real-time. Welcome to our selection of the Aiops Use Cases Related To Cloudops Devops And Secops Information PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today
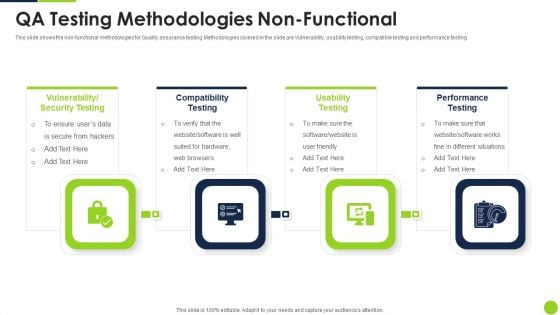
Agile Methodology Quality Control QA Testing Methodologies Non Functional Ppt Infographics Elements PDF
Presenting agile methodology quality control qa testing methodologies non functional ppt infographics elements pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like security testing, compatibility testing, usability testing, performance testing. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
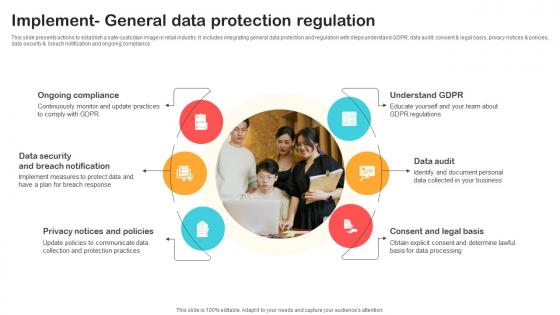
Implement General Data Protection Regulation Optimizing Retail Operations With Digital DT SS V
This slide presents actions to establish a safe-custodian image in retail industry. It includes integrating general data protection and regulation with steps understand GDPR, data audit, consent and legal basis, privacy notices and policies, data security and breach notification and ongoing compliance. Find a pre-designed and impeccable Implement General Data Protection Regulation Optimizing Retail Operations With Digital DT SS V. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide presents actions to establish a safe-custodian image in retail industry. It includes integrating general data protection and regulation with steps understand GDPR, data audit, consent and legal basis, privacy notices and policies, data security and breach notification and ongoing compliance.

Exit Strategy Email And Data Protection Platform Capital Funding Pitch Deck PPT Template
This slide covers the exit strategy of the email security software company. It includes various exit options such as merger and acquisition and initial public offering. Present like a pro with Exit Strategy Email And Data Protection Platform Capital Funding Pitch Deck PPT Template. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide covers the exit strategy of the email security software company. It includes various exit options such as merger and acquisition and initial public offering.
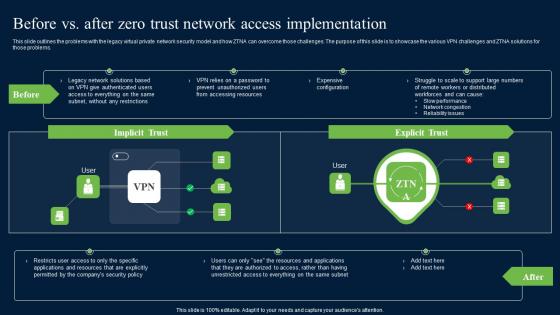
Before Vs After Zero Trust Network Access Brochure Pdf
This slide outlines the problems with the legacy virtual private network security model and how ZTNA can overcome those challenges. The purpose of this slide is to showcase the various VPN challenges and ZTNA solutions for those problems. Create an editable Before Vs After Zero Trust Network Access Brochure Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Before Vs After Zero Trust Network Access Brochure Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide outlines the problems with the legacy virtual private network security model and how ZTNA can overcome those challenges. The purpose of this slide is to showcase the various VPN challenges and ZTNA solutions for those problems.

Cybersecurity Risk Administration Plan System Categorization Worksheet Download PDF
This slide illustrates system categorization worksheet. It includes information about security system such as system name, its version, system location and other general information.Deliver and pitch your topic in the best possible manner with this Cybersecurity Risk Administration Plan System Categorization Worksheet Download PDF Use them to share invaluable insights on Accessible Within Organization, Individual System, Accessible To Key Shareholders and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
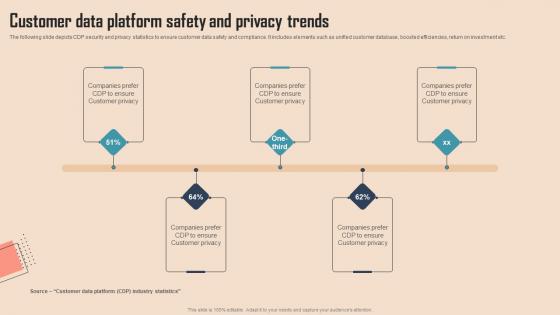
Customer Data Platform Safety And Comprehensive CDP Guide For Promoters Brochure Pdf
The following slide depicts CDP security and privacy statistics to ensure customer data safety and compliance. It includes elements such as unified customer database, boosted efficiencies, return on investment etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Customer Data Platform Safety And Comprehensive CDP Guide For Promoters Brochure Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. The following slide depicts CDP security and privacy statistics to ensure customer data safety and compliance. It includes elements such as unified customer database, boosted efficiencies, return on investment etc.

Zero Trust Network Access Step 3 Assess The Environment
This slide outlines the third step of ZTNA deployment, which is assessing the environment. The purpose of this slide is to highlight the questions that should be answered to evaluate the ecosystem and the questions include knowing the security controls, knowledge gaps and so on. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Zero Trust Network Access Step 3 Assess The Environment and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide outlines the third step of ZTNA deployment, which is assessing the environment. The purpose of this slide is to highlight the questions that should be answered to evaluate the ecosystem and the questions include knowing the security controls, knowledge gaps and so on.
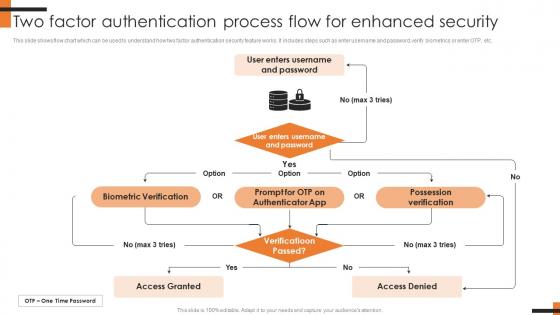
Two Factor Authentication Process Flow For Comprehensive Smartphone Banking Diagrams Pdf
This slide shows flow chart which can be used to understand how two factor authentication security feature works. It includes steps such as enter username and password, verify biometrics or enter OTP, etc. The Two Factor Authentication Process Flow For Comprehensive Smartphone Banking Diagrams Pdf is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide shows flow chart which can be used to understand how two factor authentication security feature works. It includes steps such as enter username and password, verify biometrics or enter OTP, etc.
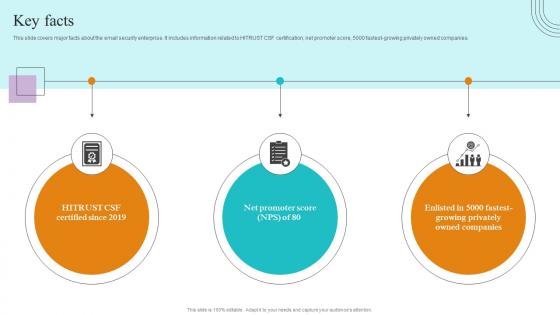
Key Facts Paubox Capital Funding Pitch Deck Graphics Pdf
This slide covers major facts about the email security enterprise. It includes information related to HITRUST CSF certification, net promoter score, 5000 fastest growing privately owned companies. Make sure to capture your audiences attention in your business displays with our gratis customizable Key Facts Paubox Capital Funding Pitch Deck Graphics Pdf. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide covers major facts about the email security enterprise. It includes information related to HITRUST CSF certification, net promoter score, 5000 fastest growing privately owned companies.
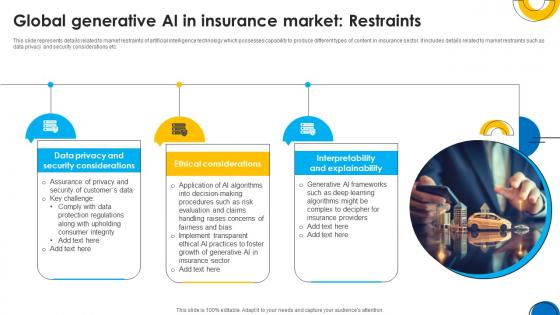
A101 Implementing ChatGpt In Insurance Global Generative Ai In Insurance ChatGpt SS V
This slide represents details related to market restraints of artificial intelligence technology which possesses capability to produce different types of content in insurance sector. It includes details related to market restraints such as data privacy and security considerations etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate A101 Implementing ChatGpt In Insurance Global Generative Ai In Insurance ChatGpt SS V for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide represents details related to market restraints of artificial intelligence technology which possesses capability to produce different types of content in insurance sector. It includes details related to market restraints such as data privacy and security considerations etc.
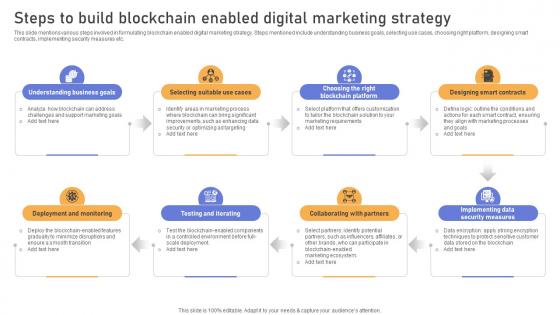
Comprehensive Look At Blockchain Steps To Build Blockchain Enabled Digital BCT SS V
This slide mentions various steps involved in formulating blockchain enabled digital marketing strategy. Steps mentioned include understanding business goals, selecting use cases, choosing right platform, designing smart contracts, implementing security measures etc. Present like a pro with Comprehensive Look At Blockchain Steps To Build Blockchain Enabled Digital BCT SS V. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide mentions various steps involved in formulating blockchain enabled digital marketing strategy. Steps mentioned include understanding business goals, selecting use cases, choosing right platform, designing smart contracts, implementing security measures etc.
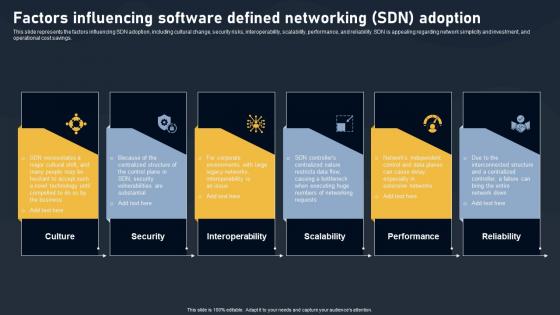
Factors Influencing Software Defined Networking Adoption SDN Building Blocks Template Pdf
This slide represents the factors influencing SDN adoption, including cultural change, security risks, interoperability, scalability, performance, and reliability. SDN is appealing regarding network simplicity and investment, and operational cost savings.Slidegeeks has constructed Factors Influencing Software Defined Networking Adoption SDN Building Blocks Template Pdf after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide represents the factors influencing SDN adoption, including cultural change, security risks, interoperability, scalability, performance, and reliability. SDN is appealing regarding network simplicity and investment, and operational cost savings.

Enhancing Cyber Safety With Vulnerability Administration SIEM Integrations Inspiration PDF
This is a enhancing cyber safety with vulnerability administration siem integrations inspiration pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security events, network logs, applications and devices, it infrastructure. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Business Model Email And Data Protection Platform Capital Funding Pitch Deck PPT Template
This slide covers the business model canvas for email security software firm. It includes information about key partners, key activities, value proposition, key resources, distribution channels, customer relationships, customer segments, cost structure, revenue streams. Boost your pitch with our creative Business Model Email And Data Protection Platform Capital Funding Pitch Deck PPT Template. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide covers the business model canvas for email security software firm. It includes information about key partners, key activities, value proposition, key resources, distribution channels, customer relationships, customer segments, cost structure, revenue streams.
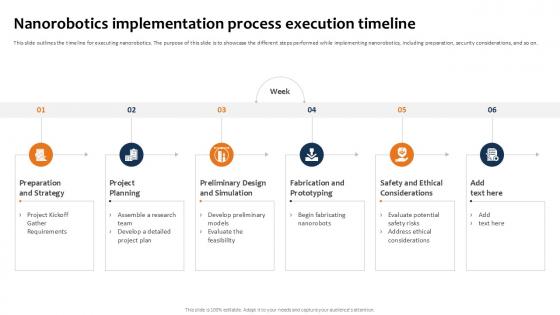
Nanorobotics Implementation Building The Future Of Robotic Ppt Slide
This slide outlines the timeline for executing nanorobotics. The purpose of this slide is to showcase the different steps performed while implementing nanorobotics, including preparation, security considerations, and so on.The Nanorobotics Implementation Building The Future Of Robotic Ppt Slide is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide outlines the timeline for executing nanorobotics. The purpose of this slide is to showcase the different steps performed while implementing nanorobotics, including preparation, security considerations, and so on.
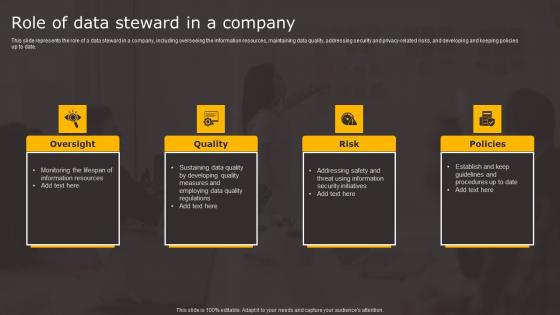
Data Stewardship In Business Processes Role Of Data Steward In A Company Background Pdf
This slide represents the role of a data steward in a company, including overseeing the information resources, maintaining data quality, addressing security and privacy related risks, and developing and keeping policies up to date. Make sure to capture your audiences attention in your business displays with our gratis customizable Data Stewardship In Business Processes Role Of Data Steward In A Company Background Pdf. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide represents the role of a data steward in a company, including overseeing the information resources, maintaining data quality, addressing security and privacy related risks, and developing and keeping policies up to date.
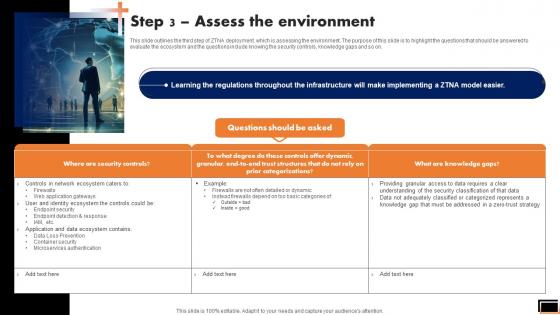
Step 3 Assess The Environment Software Defined Perimeter SDP
This slide outlines the third step of ZTNA deployment, which is assessing the environment. The purpose of this slide is to highlight the questions that should be answered to evaluate the ecosystem and the questions include knowing the security controls, knowledge gaps and so on. There are so many reasons you need a Step 3 Assess The Environment Software Defined Perimeter SDP. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide outlines the third step of ZTNA deployment, which is assessing the environment. The purpose of this slide is to highlight the questions that should be answered to evaluate the ecosystem and the questions include knowing the security controls, knowledge gaps and so on.
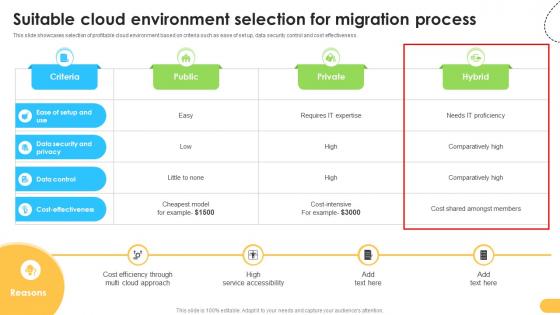
Suitable Cloud Environment Selection For Data Migration From On Premises
This slide showcases selection of profitable cloud environment based on criteria such as ease of set up, data security control and cost effectiveness. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Suitable Cloud Environment Selection For Data Migration From On Premises to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Suitable Cloud Environment Selection For Data Migration From On Premises. This slide showcases selection of profitable cloud environment based on criteria such as ease of set up, data security control and cost effectiveness.
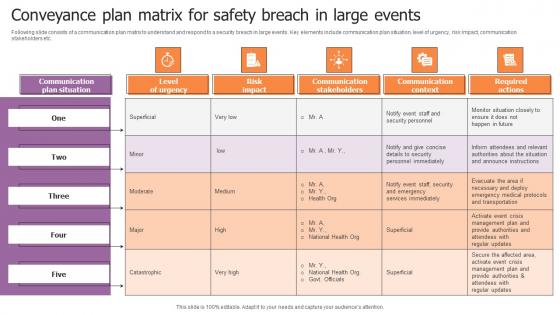
Conveyance Plan Matrix For Safety Breach In Large Events Diagrams Pdf
Following slide consists of a communication plan matrix to understand and respond to a security breach in large events. Key elements include communication plan situation, level of urgency, risk impact, communication stakeholders etc. Pitch your topic with ease and precision using this Conveyance Plan Matrix For Safety Breach In Large Events Diagrams Pdf. This layout presents information on Level Of Urgency, Risk Impact, Communication Stakeholders. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Following slide consists of a communication plan matrix to understand and respond to a security breach in large events. Key elements include communication plan situation, level of urgency, risk impact, communication stakeholders etc.

Strategy To Be Adopted 2 Educate And Increase Employee Awareness Ppt Pictures File Formats PDF
This slide shows the strategy to be adopted by the company i.e. Educate and provide proper data security training to the employees, make them familiar with latest security techniques etc. along with the need of such strategy and how it is to be implemented that will give benefit to the company. Presenting strategy to be adopted 2 educate and increase employee awareness ppt pictures file formats pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like technologies, financial control procedures, operating system maintenance. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
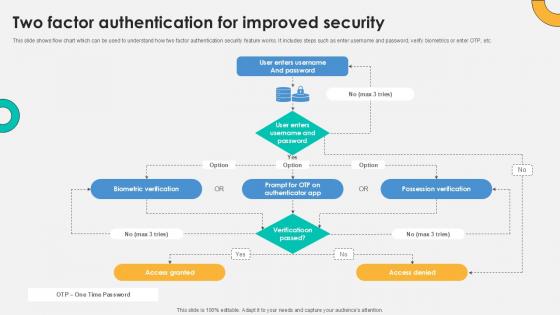
Two Factor Authentication For Everything About Bitcoin PPT Presentation Fin SS V
This slide shows flow chart which can be used to understand how two factor authentication security feature works. It includes steps such as enter username and password, verify biometrics or enter OTP, etc. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Two Factor Authentication For Everything About Bitcoin PPT Presentation Fin SS V and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide shows flow chart which can be used to understand how two factor authentication security feature works. It includes steps such as enter username and password, verify biometrics or enter OTP, etc.
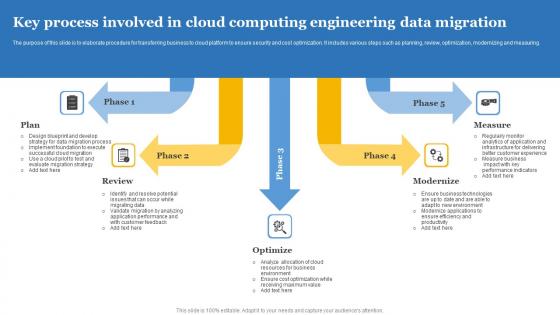
Key Process Involved In Cloud Computing Engineering Data Migration Mockup Pdf
The purpose of this slide is to elaborate procedure for transferring business to cloud platform to ensure security and cost optimization. It includes various steps such as planning, review, optimization, modernizing and measuring. Pitch your topic with ease and precision using this Key Process Involved In Cloud Computing Engineering Data Migration Mockup Pdf This layout presents information on Plan, Review, Optimize, Modernize, Measure It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. The purpose of this slide is to elaborate procedure for transferring business to cloud platform to ensure security and cost optimization. It includes various steps such as planning, review, optimization, modernizing and measuring.

Major Roles And Responsibilities Of Financial Mitigating Corporate Scams And Robberies Topics Pdf
The following slide Major roles and responsibilities of financial security department . It includes information about risk level determination, laws and regulations, team training, operational compliance, automatic workflows, red flags, etc. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Major Roles And Responsibilities Of Financial Mitigating Corporate Scams And Robberies Topics Pdf from Slidegeeks and deliver a wonderful presentation. The following slide Major roles and responsibilities of financial security department . It includes information about risk level determination, laws and regulations, team training, operational compliance, automatic workflows, red flags, etc.

Benefits Of Integrating Digital Transformation And Erp Erp And Digital Transformation For Maximizing DT SS V
This slide showcases the benefits of integrating digital transformation and enterprise resource planning system. It includes data security and compliance, accelerated innovation, employee collaboration, business insights, cost optimization, competitive advantage and sustainability.Get a simple yet stunning designed Benefits Of Integrating Digital Transformation And Erp Erp And Digital Transformation For Maximizing DT SS V. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Benefits Of Integrating Digital Transformation And Erp Erp And Digital Transformation For Maximizing DT SS V can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide showcases the benefits of integrating digital transformation and enterprise resource planning system. It includes data security and compliance, accelerated innovation, employee collaboration, business insights, cost optimization, competitive advantage and sustainability.

Social Media Hiring Strategic Procedure Job Description Form To Target Right Candidate Graphics PDF
This slide focuses on job description form to target right candidate by defining job title, department name, supervisor, location, contact number, key responsibilities and accountabilities, etc. Deliver and pitch your topic in the best possible manner with this Social Media Hiring Strategic Procedure Job Description Form To Target Right Candidate Graphics PDF. Use them to share invaluable insights on Financial Procedures, Ensuring Inventory, Security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Interoperability Challenges In IOT Manufacturing Devices Streamlining Production Ppt Presentation
This slide aims to analyze interoperability challenges faced by organizations in IoT ecosystem of manufacturing devices. It includes lack of standardization, fragmentation of communication protocols, security and privacy concerns, etc. Do you know about Slidesgeeks Interoperability Challenges In IOT Manufacturing Devices Streamlining Production Ppt Presentation These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide aims to analyze interoperability challenges faced by organizations in IoT ecosystem of manufacturing devices. It includes lack of standardization, fragmentation of communication protocols, security and privacy concerns, etc.

Performance Analysis Of Partial Regression Testing For A Best PPT Sample
The purpose of this slide is to indicate the performance analysis of the organizations current security infrastructure. The key components include where we are, the gap, where we want to be, and recommended solutions. Find highly impressive Performance Analysis Of Partial Regression Testing For A Best PPT Sample on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Performance Analysis Of Partial Regression Testing For A Best PPT Sample for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now The purpose of this slide is to indicate the performance analysis of the organizations current security infrastructure. The key components include where we are, the gap, where we want to be, and recommended solutions.
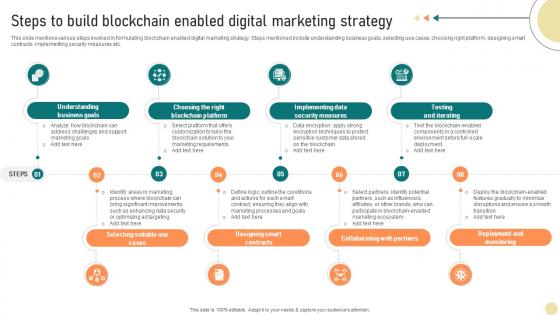
Visionary Guide To Blockchain Steps To Build Blockchain Enabled Digital Marketing BCT SS V
This slide mentions various steps involved in formulating blockchain enabled digital marketing strategy. Steps mentioned include understanding business goals, selecting use cases, choosing right platform, designing smart contracts, implementing security measures etc. Slidegeeks is here to make your presentations a breeze with Visionary Guide To Blockchain Steps To Build Blockchain Enabled Digital Marketing BCT SS V With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide mentions various steps involved in formulating blockchain enabled digital marketing strategy. Steps mentioned include understanding business goals, selecting use cases, choosing right platform, designing smart contracts, implementing security measures etc.

Building Stronger Customer Multiple Payment Options To Reduce Cart Abandonment SA SS V
This slide showcases the factors to consider before selecting payment options for e-commerce website that are location, compatibility, security and fraud. Retrieve professionally designed Building Stronger Customer Multiple Payment Options To Reduce Cart Abandonment SA SS V to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide showcases the factors to consider before selecting payment options for e-commerce website that are location, compatibility, security and fraud.
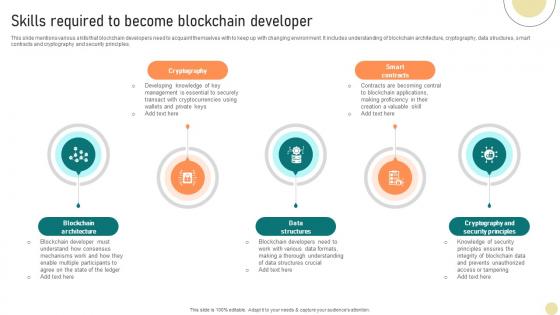
Visionary Guide To Blockchain Skills Required To Become Blockchain Developer BCT SS V
This slide mentions various skills that blockchain developers need to acquaint themselves with to keep up with changing environment. It includes understanding of blockchain architecture, cryptography, data structures, smart contracts and cryptography and security principles. Present like a pro with Visionary Guide To Blockchain Skills Required To Become Blockchain Developer BCT SS V. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide mentions various skills that blockchain developers need to acquaint themselves with to keep up with changing environment. It includes understanding of blockchain architecture, cryptography, data structures, smart contracts and cryptography and security principles.
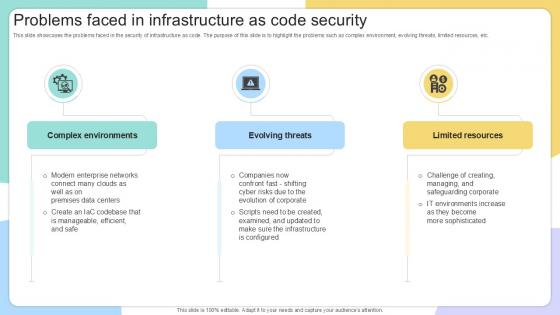
Problems Faced In Infrastructure As IAC Tools For Performance Analysis PPT PowerPoint
This slide showcases the problems faced in the security of infrastructure as code. The purpose of this slide is to highlight the problems such as complex environment, evolving threats, limited resources, etc. Present like a pro with Problems Faced In Infrastructure As IAC Tools For Performance Analysis PPT PowerPoint. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide showcases the problems faced in the security of infrastructure as code. The purpose of this slide is to highlight the problems such as complex environment, evolving threats, limited resources, etc.

Healthcare Information Technology Transforming Medicare Services Using Health Guidelines Pdf
This slide covers healthcare information technology trends to ensure effective transformation of health services. It involves key trends such as internet of medical things, cognitive automation and cyber security and data privacy. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Healthcare Information Technology Transforming Medicare Services Using Health Guidelines Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Healthcare Information Technology Transforming Medicare Services Using Health Guidelines Pdf today and make your presentation stand out from the rest This slide covers healthcare information technology trends to ensure effective transformation of health services. It involves key trends such as internet of medical things, cognitive automation and cyber security and data privacy.
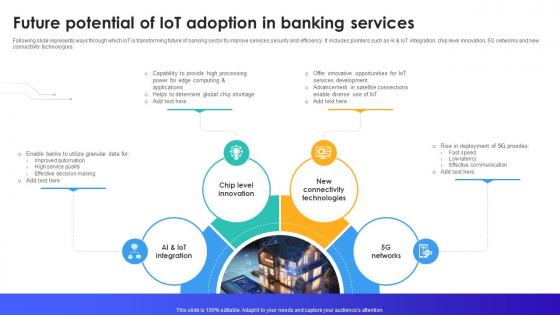
Future Potential Of IoT Adoption In Banking Services IoT In Banking For Digital Future IoT SS V
Following slide represents ways through which IoT is transforming future of banking sector to improve services security and efficiency. It includes pointers such as AI and IoT integration, chip level innovation, 5G networks and new connectivity technologies. There are so many reasons you need a Future Potential Of IoT Adoption In Banking Services IoT In Banking For Digital Future IoT SS V. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. Following slide represents ways through which IoT is transforming future of banking sector to improve services security and efficiency. It includes pointers such as AI and IoT integration, chip level innovation, 5G networks and new connectivity technologies.

Key Features Of Box Cloud Storage Platform Ultimate Guide To Adopt Box Inspiration PDF
This slide covers box cloud storage platforms key features. It includes various features such as security and compliance, collaboration, workflow, integration, develop tools and APIs, and artificial intelligence. Present like a pro with Key Features Of Box Cloud Storage Platform Ultimate Guide To Adopt Box Inspiration PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide covers box cloud storage platforms key features. It includes various features such as security and compliance, collaboration, workflow, integration, develop tools and APIs, and artificial intelligence.


 Continue with Email
Continue with Email

 Home
Home


































