Security Management

Supplementary Debt Financing Pitch Deck Key Sources Of Revenue Generation Summary PDF
Presenting supplementary debt financing pitch deck key sources of revenue generation summary pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like revenue, corporate, securities, investment, commission. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Set Up Social Media Profiles Ppt PowerPoint Presentation Show Model
This is a set up social media profiles ppt powerpoint presentation show model. This is a six stage process. The stages in this process are facebook, linkedin, instagram, twitter, you tube, pinterest.
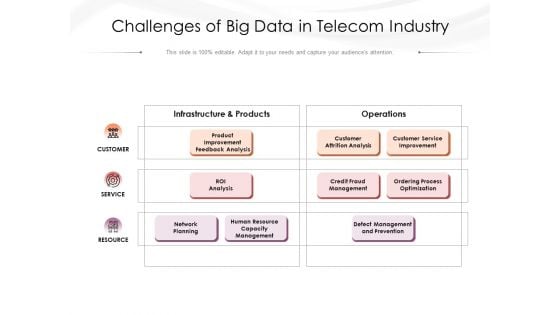
Challenges Of Big Data In Telecom Industry Ppt PowerPoint Presentation Show Model PDF
Presenting this set of slides with name challenges of big data in telecom industry ppt powerpoint presentation show model pdf. This is a three stage process. The stages in this process are infrastructure and products, operations, product improvement feedback analysis, customer attrition analysis, customer service improvement, roi analysis, credit fraud management, ordering process optimization, network planning, human resource capacity management, defect management and prevention, customer, service, resource. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
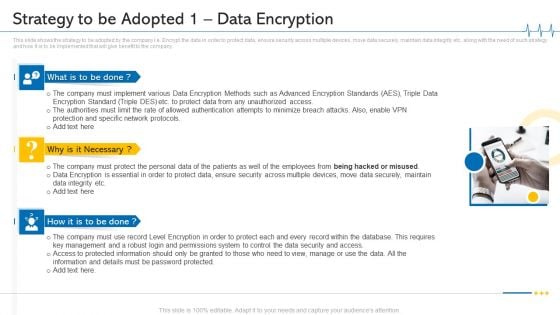
Minimize Cloud Risks Medical Care Business Case Competition Strategy To Be Adopted 1 Data Encryption Microsoft PDF
This slide shows the strategy to be adopted by the company i.e. Encrypt the data in order to protect data, ensure security across multiple devices, move data securely, maintain data integrity etc. along with the need of such strategy and how it is to be implemented that will give benefit to the company. Presenting minimize cloud risks medical care business case competition strategy to be adopted 1 data encryption microsoft pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Protection And Specific Network Protocols, Protect Data, Permissions System, Key Management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
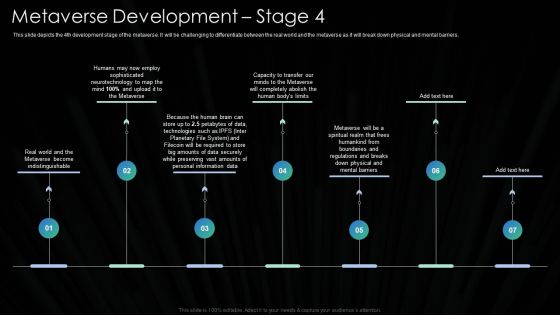
Metaverse Technology IT Metaverse Development Stage 4 Ppt PowerPoint Presentation File Gridlines PDF
This slide depicts the 4th development stage of the metaverse. It will be challenging to differentiate between the real world and the metaverse as it will break down physical and mental barriers. This is a Metaverse Technology IT Metaverse Development Stage 4 Ppt PowerPoint Presentation File Gridlines PDF template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Real World, Personal Information Data, Big Amounts, Data Securely. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
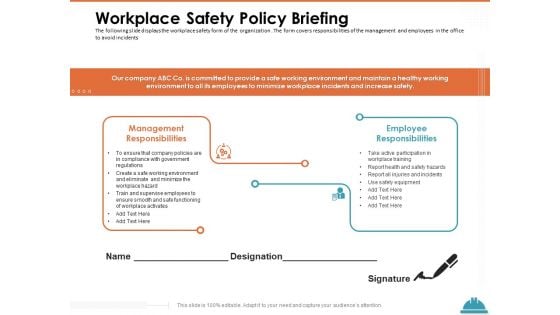
Train Employees Health Safety Workplace Safety Policy Briefing Ppt Ideas Inspiration PDF
Presenting this set of slides with name train employees health safety workplace safety policy briefing ppt ideas inspiration pdf. This is a two stage process. The stages in this process are management responsibilities, employee responsibilities. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
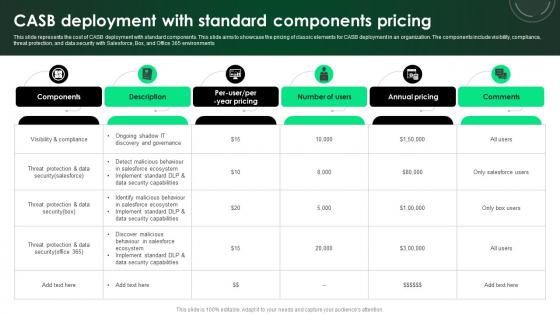
CASB 2 0 IT CASB Deployment With Standard Components Pricing
This slide represents the cost of CASB deployment with standard components. This slide aims to showcase the pricing of classic elements for CASB deployment in an organization. The components include visibility, compliance, threat protection, and data security with Salesforce, Box, and Office 365 environments. Whether you have daily or monthly meetings, a brilliant presentation is necessary. CASB 2 0 IT CASB Deployment With Standard Components Pricing can be your best option for delivering a presentation. Represent everything in detail using CASB 2 0 IT CASB Deployment With Standard Components Pricing and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide represents the cost of CASB deployment with standard components. This slide aims to showcase the pricing of classic elements for CASB deployment in an organization. The components include visibility, compliance, threat protection, and data security with Salesforce, Box, and Office 365 environments
procedure of record keeping system with ease of access ppt powerpoint presentation icon master slide
Presenting this set of slides with name procedure of record keeping system with ease of access ppt powerpoint presentation icon master slide. This is a four stage process. The stages in this process are records management policy, retention schedule, choose the right solution, ease of access. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Guarantee And Collateral Agreement Ppt PowerPoint Presentation File Layout Ideas
Presenting this set of slides with name guarantee and collateral agreement ppt powerpoint presentation file layout ideas. This is a one stage process. The stages in this process are collateral, documents granting, documents required. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Logistic Network Administration Solutions Deck Outline Ppt Layouts Information PDF
Presenting logistic network administration solutions deck outline ppt layouts information pdf to provide visual cues and insights. Share and navigate important information on ten stages that need your due attention. This template can be used to pitch topics like management process, inventory, planning, performance, strategic. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
best practices of record keeping system with icons ppt powerpoint presentation icon vector
Presenting this set of slides with name best practices of record keeping system with icons ppt powerpoint presentation icon vector. This is a four stage process. The stages in this process are records management policy, choose the right solution, retention schedule, ease of access. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
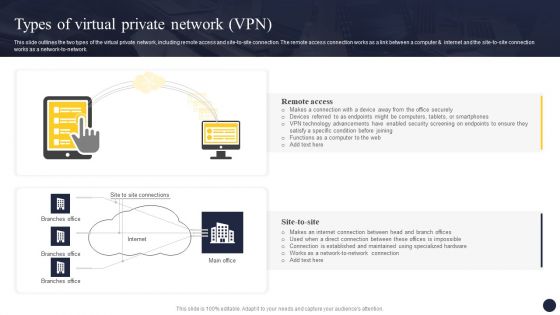
Integrating Naas Service Model To Enhance Types Of Virtual Private Network VPN Introduction PDF
This slide outlines the two types of the virtual private network, including remote access and site-to-site connection. The remote access connection works as a link between a computer and internet and the site-to-site connection works as a network-to-network. The Integrating Naas Service Model To Enhance Types Of Virtual Private Network VPN Introduction PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
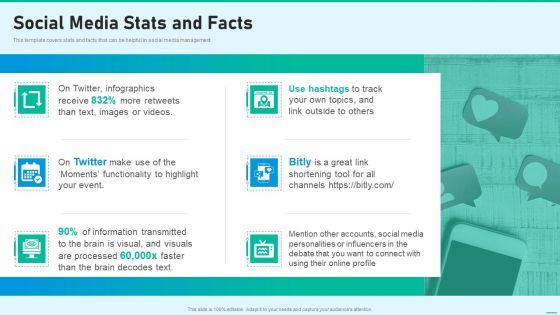
Social Network Playbook Social Media Stats And Facts Ppt Summary Guide PDF
This template covers stats and facts that can be helpful in social media management Presenting social network playbook social media stats and facts ppt summary guide pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like social media stats and facts. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Cloud Computing Protection And Privacy Icon Designs PDF
Presenting Cloud Computing Protection And Privacy Icon Designs PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Privacy Icon, Cloud Computing Protection. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Online Data Protection And Privacy Icon Structure PDF
Presenting Online Data Protection And Privacy Icon Structure PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Privacy Icon, Online Data Protection. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Privacy Protection Ppt PowerPoint Presentation Professional Graphics Template Cpb Pdf
Presenting this set of slides with name privacy protection ppt powerpoint presentation professional graphics template cpb pdf. This is an editable Powerpoint four stages graphic that deals with topics like privacy protection to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

VPN System For Network Protection Ppt PowerPoint Presentation File Shapes PDF
Presenting vpn system for network protection ppt powerpoint presentation file shapes pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including vpn system for network protection. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
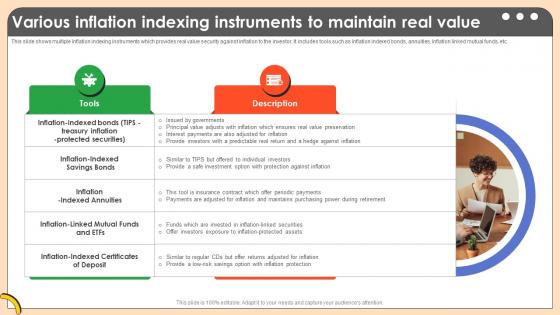
Various Inflation Indexing Instruments To Comprehensive Guide On Inflation Control CM SS V
This slide shows multiple inflation indexing instruments which provides real value security against inflation to the investor. It includes tools such as inflation indexed bonds, annuities, inflation linked mutual funds, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Various Inflation Indexing Instruments To Comprehensive Guide On Inflation Control CM SS V is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Various Inflation Indexing Instruments To Comprehensive Guide On Inflation Control CM SS V and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide shows multiple inflation indexing instruments which provides real value security against inflation to the investor. It includes tools such as inflation indexed bonds, annuities, inflation linked mutual funds, etc.
Virtual Private Network Tunnel Icon With Globe And Lock Ppt PowerPoint Presentation Gallery Ideas PDF
Presenting virtual private network tunnel icon with globe and lock ppt powerpoint presentation gallery ideas pdf to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including virtual private network tunnel icon with globe and lock. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Comprehensive Manual For Blockchain Best Practices For Effectively Using BCT SS V
This slide covers tips to develop private network based blockchain platform. It includes practices such as identifying the participants or stakeholders ensuring their commitments, selecting appropriate consensus mechanism, regularly updating and monitoring security measures, conducting thorough testing and quality assurance, implementing effective communication, etc. Get a simple yet stunning designed Comprehensive Manual For Blockchain Best Practices For Effectively Using BCT SS V. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Comprehensive Manual For Blockchain Best Practices For Effectively Using BCT SS V can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide covers tips to develop private network based blockchain platform. It includes practices such as identifying the participants or stakeholders ensuring their commitments, selecting appropriate consensus mechanism, regularly updating and monitoring security measures, conducting thorough testing and quality assurance, implementing effective communication, etc.

Major Focus Of White Box Testing Gray Box Testing Best Practices
This slide represents the area of focus for white box testing in software development. The purpose of this slide is to highlight the primary emphasis of white box testing which include path checking, output validation, security testing, and so on. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Major Focus Of White Box Testing Gray Box Testing Best Practices and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide represents the area of focus for white box testing in software development. The purpose of this slide is to highlight the primary emphasis of white box testing which include path checking, output validation, security testing, and so on.
Cosmetics And Skin Care Company Profile Organizational Structure Ppt Summary Icons PDF
This slide highlights the organizational structure of cosmetics and beauty products company which includes different departments such as management and planning, good manufacturing practice, reliability guarantee, etc. This is a Cosmetics And Skin Care Company Profile Organizational Structure Ppt Summary Icons PDF template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like GMP Promotion Department, Reliability Guarantee Department, Sales Development. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Data Governance IT Data Stewardship Program Creation Process Icons PDF
This slide describes the process of data stewardship program for a new program or evaluation of the existing one, including the factors that should be included. It also caters to the oversight and management of various elements such as data protection, privacy, risk control, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Data Governance IT Data Stewardship Program Creation Process Icons PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Data Governance IT Data Stewardship Program Creation Process Icons PDF today and make your presentation stand out from the rest.
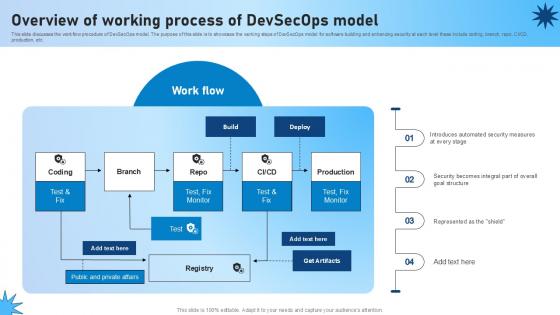
Overview Of Working Process Of Devsecops Model Role Of Devsecops Ppt Sample
This slide discusses the workflow procedure of DevSecOps model. The purpose of this slide is to showcase the working steps of DevSecOps model for software building and enhancing security at each level these include coding, branch, repo, CI CD, production, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Overview Of Working Process Of Devsecops Model Role Of Devsecops Ppt Sample for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide discusses the workflow procedure of DevSecOps model. The purpose of this slide is to showcase the working steps of DevSecOps model for software building and enhancing security at each level these include coding, branch, repo, CI CD, production, etc.
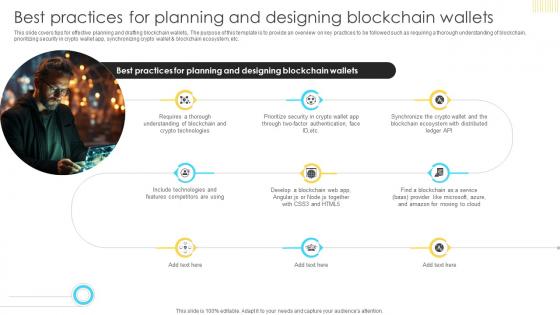
Mastering Blockchain Wallets Best Practices For Planning And Designing Blockchain BCT SS V
This slide covers tips for effective planning and drafting blockchain wallets,. The purpose of this template is to provide an overview on key practices to be followed such as requiring a thorough understanding of blockchain, prioritizing security in crypto wallet app, synchronizing crypto wallet and blockchain ecosystem, etc. Want to ace your presentation in front of a live audience Our Mastering Blockchain Wallets Best Practices For Planning And Designing Blockchain BCT SS V can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide covers tips for effective planning and drafting blockchain wallets,. The purpose of this template is to provide an overview on key practices to be followed such as requiring a thorough understanding of blockchain, prioritizing security in crypto wallet app, synchronizing crypto wallet and blockchain ecosystem, etc.
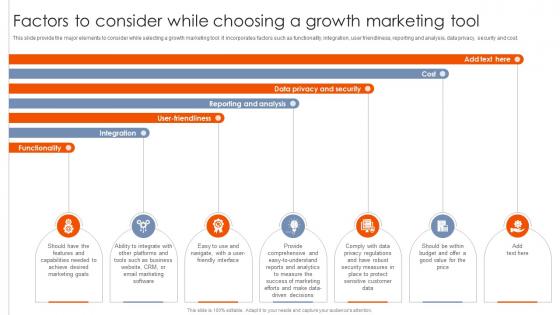
Best Practices For Using Growth Factors To Consider While Choosing A Growth MKT SS V
This slide provide the major elements to consider while selecting a growth marketing tool. It incorporates factors such as functionality, integration, user friendliness, reporting and analysis, data privacy, security and cost. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Best Practices For Using Growth Factors To Consider While Choosing A Growth MKT SS V a try. Our experts have put a lot of knowledge and effort into creating this impeccable Best Practices For Using Growth Factors To Consider While Choosing A Growth MKT SS V. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide provide the major elements to consider while selecting a growth marketing tool. It incorporates factors such as functionality, integration, user friendliness, reporting and analysis, data privacy, security and cost.
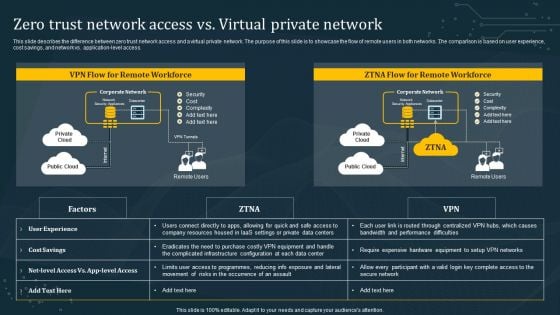
Zero Trust Network Access Vs Virtual Private Network Ideas PDF
This slide describes the difference between zero trust network access and a virtual private network. The purpose of this slide is to showcase the flow of remote users in both networks. The comparison is based on user experience, cost savings, and network vs. application-level access. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Zero Trust Network Access Vs Virtual Private Network Ideas PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
Company Asset Protection Ppt PowerPoint Presentation Inspiration Diagrams Cpb
This is a company asset protection ppt powerpoint presentation inspiration diagrams cpb. This is a six stage process. The stages in this process are company asset protection, business, management, marketing.
Asset Protection Strategies Ppt PowerPoint Presentation Icon Designs Cpb
This is a asset protection strategies ppt powerpoint presentation icon designs cpb. This is a three stage process. The stages in this process are asset protection strategies, business, management, marketing.
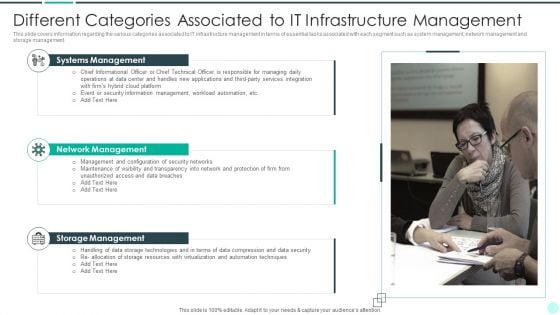
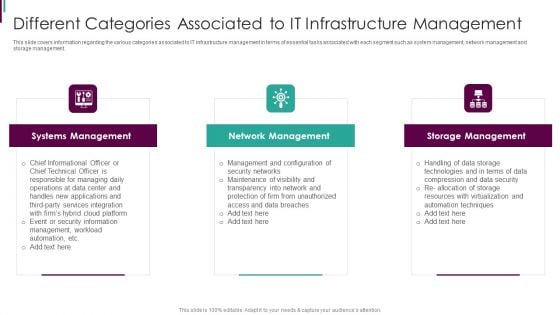
Executing Advance Data Analytics At Workspace Different Categories Associated Background PDF
This slide covers information regarding the various categories associated to IT infrastructure management in terms of essential tasks associated with each segment such as system management, network management and storage management. This is a executing advance data analytics at workspace different categories associated background pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like systems management, network management, storage management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Developing Business Analytics Framework Different Categories Associated Infographics PDF
This slide covers information regarding the various categories associated to IT infrastructure management in terms of essential tasks associated with each segment such as system management, network management and storage management. Presenting Developing Business Analytics Framework Different Categories Associated Infographics PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Systems Management, Network Management, Storage Management In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Customer Data Platform Safety And Privacy Usability Of CDP Software Tool Professional Pdf
The following slide depicts CDP security and privacy statistics to ensure customer data safety and compliance. It includes elements such as unified customer database, boosted efficiencies, return on investment etc. If you are looking for a format to display your unique thoughts, then the professionally designed Customer Data Platform Safety And Privacy Usability Of CDP Software Tool Professional Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Customer Data Platform Safety And Privacy Usability Of CDP Software Tool Professional Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. The following slide depicts CDP security and privacy statistics to ensure customer data safety and compliance. It includes elements such as unified customer database, boosted efficiencies, return on investment etc.
Virtual Private Network Ppt PowerPoint Presentation Inspiration Tips Cpb
Presenting this set of slides with name virtual private network ppt powerpoint presentation inspiration tips cpb. This is an editable Powerpoint three stages graphic that deals with topics like virtual private network to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Data Protection Multi Cloud Data Encryption Introduction PDF
This slide covers data protection and encryption framework in multi cloud with multi layer protection and data management. This is a Data Protection Multi Cloud Data Encryption Introduction PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Object Store Appliance, Spectrum Protect, Data Rock Manager. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Technologies Used To Protect Data In Confidential Computing Technologies Guidelines Pdf
This slide depicts the related technologies used to protect the information in processing. The purpose of this slide is to showcase the technologies and comparison between these technologies based on security and scalability. The technologies include homomorphic encryption, multi-party computation, and so on. Present like a pro with Technologies Used To Protect Data In Confidential Computing Technologies Guidelines Pdf Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide depicts the related technologies used to protect the information in processing. The purpose of this slide is to showcase the technologies and comparison between these technologies based on security and scalability. The technologies include homomorphic encryption, multi-party computation, and so on.

Zero Trust Model Zero Trust Network Access Architectural Models
This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption. This Zero Trust Model Zero Trust Network Access Architectural Models is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Zero Trust Model Zero Trust Network Access Architectural Models features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption.
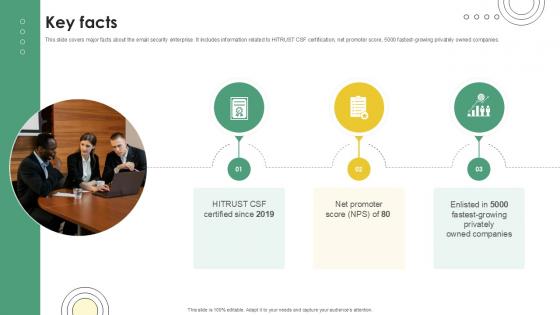
Key Facts Email And Data Protection Platform Capital Funding Pitch Deck PPT PowerPoint
This slide covers major facts about the email security enterprise. It includes information related to HITRUST CSF certification, net promoter score, 5000 fastest-growing privately owned companies. If you are looking for a format to display your unique thoughts, then the professionally designed Key Facts Email And Data Protection Platform Capital Funding Pitch Deck PPT PowerPoint is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Key Facts Email And Data Protection Platform Capital Funding Pitch Deck PPT PowerPoint and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide covers major facts about the email security enterprise. It includes information related to HITRUST CSF certification, net promoter score, 5000 fastest-growing privately owned companies.

Zero Trust Network Access Architectural Models Software Defined Perimeter SDP
This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption. This Zero Trust Network Access Architectural Models Software Defined Perimeter SDP is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Zero Trust Network Access Architectural Models Software Defined Perimeter SDP features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption.
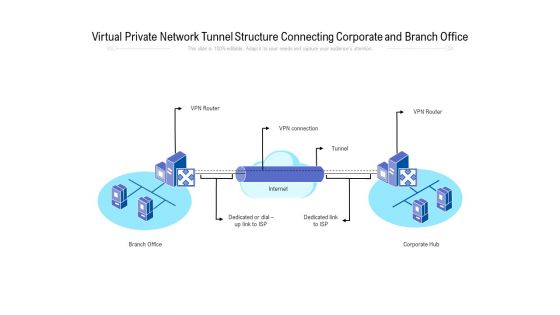
Virtual Private Network Tunnel Structure Connecting Corporate And Branch Office Ppt PowerPoint Presentation File Pictures PDF
Presenting virtual private network tunnel structure connecting corporate and branch office ppt powerpoint presentation file pictures pdf to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including virtual private network tunnel structure connecting corporate and branch office. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Smart Phone With Safety And Protection Shield Vector Icon Ppt PowerPoint Presentation File Design Ideas PDF
Persuade your audience using this smart phone with safety and protection shield vector icon ppt powerpoint presentation file design ideas pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including smart phone with safety and protection shield vector icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Document With Privacy Lock Vector Icon Ppt PowerPoint Presentation File Diagrams PDF
Presenting document with privacy lock vector icon ppt powerpoint presentation file diagrams pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including document with privacy lock vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Data Protection Flow Chart For Business Safety Ppt PowerPoint Presentation Icon Example File PDF
Persuade your audience using this data protection flow chart for business safety ppt powerpoint presentation icon example file pdf. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including access network, traffic mirroring, access. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
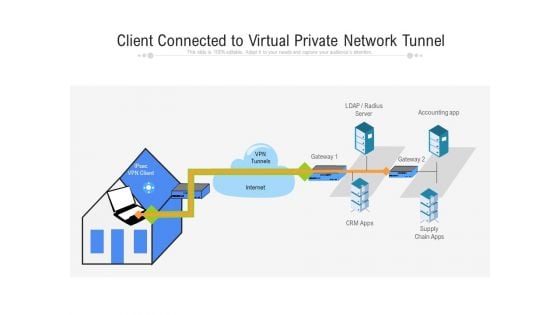
Client Connected To Virtual Private Network Tunnel Ppt PowerPoint Presentation File Graphics Download PDF
Presenting client connected to virtual private network tunnel ppt powerpoint presentation file graphics download pdf to dispense important information. This template comprises two stages. It also presents valuable insights into the topics including client connected to virtual private network tunnel. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Major Milestones Achieved Email And Data Protection Platform Capital Funding Pitch Deck PPT Slide
This slide covers key awards and recognitions achieved by the company. It includes awards such as top rated software, rising star of email security software, highest rated HIPAA compliant messaging solution. If you are looking for a format to display your unique thoughts, then the professionally designed Major Milestones Achieved Email And Data Protection Platform Capital Funding Pitch Deck PPT Slide is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Major Milestones Achieved Email And Data Protection Platform Capital Funding Pitch Deck PPT Slide and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide covers key awards and recognitions achieved by the company. It includes awards such as top rated software, rising star of email security software, highest rated HIPAA compliant messaging solution.

Hierarchy Of Controls Protective Equipment Ppt PowerPoint Presentation Infographic Template Smartart
Presenting this set of slides with name hierarchy of controls protective equipment ppt powerpoint presentation infographic template smartart. This is a three stage process. The stages in this process are business, management, planning, strategy, marketing. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Wireless Banking To Improve Two Factor Authentication Process Flow For Enhanced Fin SS V
This slide shows flow chart which can be used to understand how two factor authentication security feature works. It includes steps such as enter username and password, verify biometrics or enter OTP, etc. Are you searching for a Wireless Banking To Improve Two Factor Authentication Process Flow For Enhanced Fin SS V that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Wireless Banking To Improve Two Factor Authentication Process Flow For Enhanced Fin SS V from Slidegeeks today. This slide shows flow chart which can be used to understand how two factor authentication security feature works. It includes steps such as enter username and password, verify biometrics or enter OTP, etc.
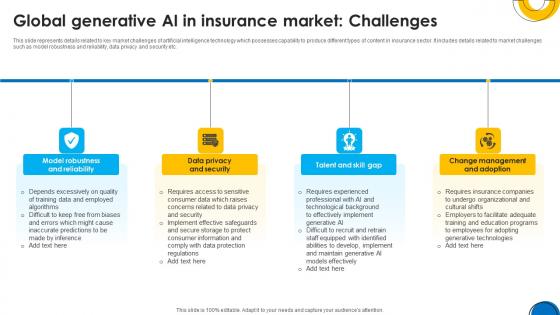
Implementing ChatGpt In Insurance Global Generative AI In Insurance Market ChatGpt SS V
This slide represents details related to key market challenges of artificial intelligence technology which possesses capability to produce different types of content in insurance sector. It includes details related to market challenges such as model robustness and reliability, data privacy and security etc. If you are looking for a format to display your unique thoughts, then the professionally designed Implementing ChatGpt In Insurance Global Generative AI In Insurance Market ChatGpt SS V is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Implementing ChatGpt In Insurance Global Generative AI In Insurance Market ChatGpt SS V and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide represents details related to key market challenges of artificial intelligence technology which possesses capability to produce different types of content in insurance sector. It includes details related to market challenges such as model robustness and reliability, data privacy and security etc.
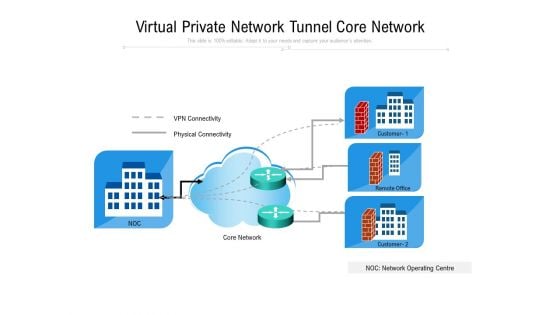
Virtual Private Network Tunnel Core Network Ppt PowerPoint Presentation Gallery Professional PDF
Persuade your audience using this virtual private network tunnel core network ppt powerpoint presentation gallery professional pdf. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including virtual private network tunnel core network. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Overview Cybersecurity And Data Protection In Digital Transformation DT SS V
This slide presents an overview into the landscape of cybersecurity and data protection with its advantages. It also presents a survey analysis on share of SMEs that have implemented essential and basic IT security initiatives.Find highly impressive Overview Cybersecurity And Data Protection In Digital Transformation DT SS V on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Overview Cybersecurity And Data Protection In Digital Transformation DT SS V for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide presents an overview into the landscape of cybersecurity and data protection with its advantages. It also presents a survey analysis on share of SMEs that have implemented essential and basic IT security initiatives.
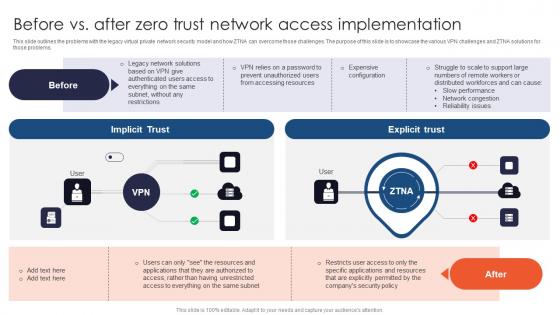
Zero Trust Network Access Before Vs After Zero Trust Network Access Implementation
This slide outlines the problems with the legacy virtual private network security model and how ZTNA can overcome those challenges. The purpose of this slide is to showcase the various VPN challenges and ZTNA solutions for those problems. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Zero Trust Network Access Before Vs After Zero Trust Network Access Implementation and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide outlines the problems with the legacy virtual private network security model and how ZTNA can overcome those challenges. The purpose of this slide is to showcase the various VPN challenges and ZTNA solutions for those problems.
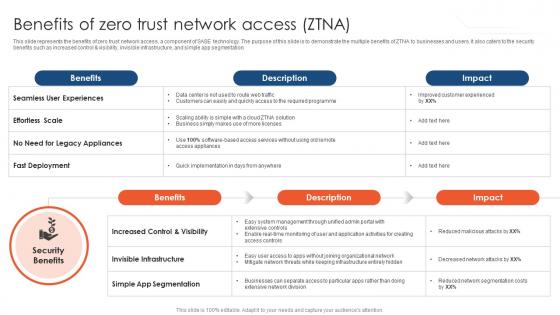
Zero Trust Network Access Benefits Of Zero Trust Network Access ZTNA
This slide represents the benefits of zero trust network access, a component of SASE technology. The purpose of this slide is to demonstrate the multiple benefits of ZTNA to businesses and users. It also caters to the security benefits such as increased control and visibility, invisible infrastructure, and simple app segmentation. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Zero Trust Network Access Benefits Of Zero Trust Network Access ZTNA template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Zero Trust Network Access Benefits Of Zero Trust Network Access ZTNA that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide represents the benefits of zero trust network access, a component of SASE technology. The purpose of this slide is to demonstrate the multiple benefits of ZTNA to businesses and users. It also caters to the security benefits such as increased control and visibility, invisible infrastructure, and simple app segmentation.

Zero Trust Model Benefits Of Zero Trust Network Access ZTNA
This slide represents the benefits of zero trust network access, a component of SASE technology. The purpose of this slide is to demonstrate the multiple benefits of ZTNA to businesses and users. It also caters to the security benefits such as increased control and visibility, invisible infrastructure, and simple app segmentation. Get a simple yet stunning designed Zero Trust Model Benefits Of Zero Trust Network Access ZTNA. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Zero Trust Model Benefits Of Zero Trust Network Access ZTNA can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide represents the benefits of zero trust network access, a component of SASE technology. The purpose of this slide is to demonstrate the multiple benefits of ZTNA to businesses and users. It also caters to the security benefits such as increased control and visibility, invisible infrastructure, and simple app segmentation.
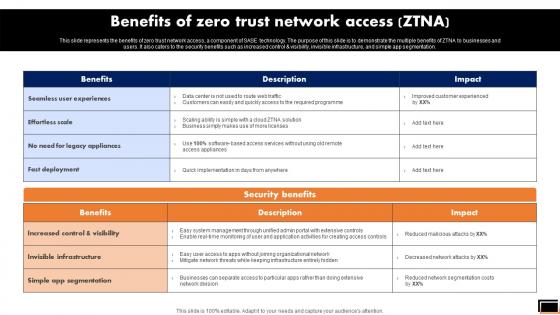
Benefits Of Zero Trust Network Access Ztna Software Defined Perimeter SDP
This slide represents the benefits of zero trust network access, a component of SASE technology. The purpose of this slide is to demonstrate the multiple benefits of ZTNA to businesses and users. It also caters to the security benefits such as increased control and visibility, invisible infrastructure, and simple app segmentation. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Benefits Of Zero Trust Network Access Ztna Software Defined Perimeter SDP for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide represents the benefits of zero trust network access, a component of SASE technology. The purpose of this slide is to demonstrate the multiple benefits of ZTNA to businesses and users. It also caters to the security benefits such as increased control and visibility, invisible infrastructure, and simple app segmentation.
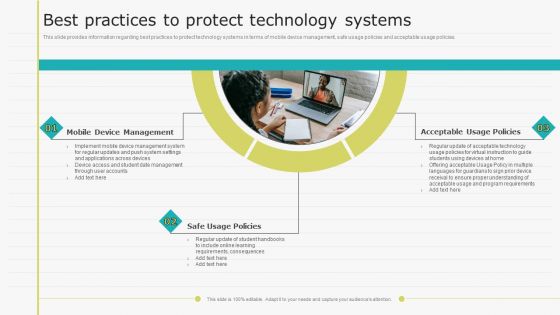
Virtual Learning Playbook Best Practices To Protect Technology Systems Slides PDF
This slide provides information regarding best practices to protect technology systems in terms of mobile device management, safe usage policies and acceptable usage policies. Presenting Virtual Learning Playbook Best Practices To Protect Technology Systems Slides PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Mobile Device Management, Safe Usage Policies, Acceptable Usage Policies. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Strategies For KPMG For Client Data Protection Pictures PDF
This slide covers techniques to secure customers confidential data through several cyber security strategies. The purpose for this template is to provide an overview on important elements of top techniques deployed by the company . It includes strategies such as people, process, data and technology and regulatory. Boost your pitch with our creative Cyber Strategies For KPMG For Client Data Protection Pictures PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Roadmap To Implement Zero Trust Network Access Model Software Defined Perimeter SDP
This slide outlines the roadmap to implementing an organizations zero-trust network access model. The purpose of this slide is to showcase the various steps to be taken while deploying the ZTNA security model, including assessing current network infrastructure, developing a ZTNA strategy, choosing a ZTNA solution, etc. This Roadmap To Implement Zero Trust Network Access Model Software Defined Perimeter SDP from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide outlines the roadmap to implementing an organizations zero-trust network access model. The purpose of this slide is to showcase the various steps to be taken while deploying the ZTNA security model, including assessing current network infrastructure, developing a ZTNA strategy, choosing a ZTNA solution, etc.
Business Asset Protection Ppt Powerpoint Presentation Model Mockup Cpb
This is a business asset protection ppt powerpoint presentation model mockup cpb. This is a three stage process. The stages in this process are business asset protection.

Protection Creditors Ppt PowerPoint Presentation Model Graphics Design Cpb
This is a protection creditors ppt powerpoint presentation model graphics design cpb. This is a six stage process. The stages in this process are protection creditors.
Best Asset Protection Ppt PowerPoint Presentation Summary Template Cpb
This is a best asset protection ppt powerpoint presentation summary template cpb. This is a seven stage process. The stages in this process are best asset protection.
Protect Assets Ppt Powerpoint Presentation Icon Ideas Cpb
This is a protect assets ppt powerpoint presentation icon ideas cpb. This is a five stage process. The stages in this process are protect assets.


 Continue with Email
Continue with Email

 Home
Home


































