Security Management
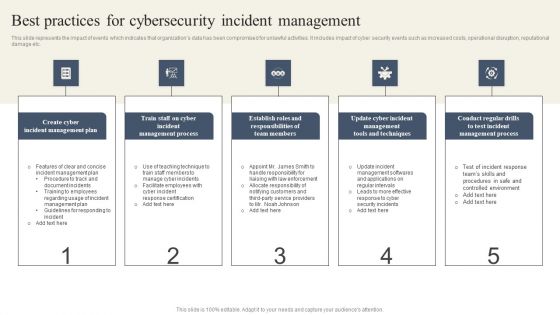
CYBER Security Breache Response Strategy Best Practices For Cybersecurity Incident Management Ideas PDF
This slide represents the impact of events which indicates that organizations data has been compromised for unlawful activities. It includes impact of cyber security events such as increased costs, operational disruption, reputational damage etc. Boost your pitch with our creative CYBER Security Breache Response Strategy Best Practices For Cybersecurity Incident Management Ideas PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Security And Human Resource Services Business Profile Executive Leadership And Management Sample PDF
This slide highlights the security guard company management team which includes companys chairman and MD, head of security operations, training, strategic growth and site. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Security And Human Resource Services Business Profile Executive Leadership And Management Sample PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

IoT Device Management Fundamentals Best Practices For Optimising IoT Healthcare Security IoT Ss V
This slide highlights key principles for managing IoT devices security in order to protect patients personal information. It covers best practices such as acquire unique e-certificate, administer private key storage, check digitally signed firmware, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give IoT Device Management Fundamentals Best Practices For Optimising IoT Healthcare Security IoT SS V a try. Our experts have put a lot of knowledge and effort into creating this impeccable IoT Device Management Fundamentals Best Practices For Optimising IoT Healthcare Security IoT SS V. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide highlights key principles for managing IoT devices security in order to protect patients personal information. It covers best practices such as acquire unique e-certificate, administer private key storage, check digitally signed firmware, etc.

Construction Management Services And Action Plan Interdependence Resiliency And Security Portrait PDF
Presenting construction management services and action plan interdependence resiliency and security portrait pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like infrastructure resilience wheel, lifecycle adaptive components of resilience framework, dimensions of infrastructure security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
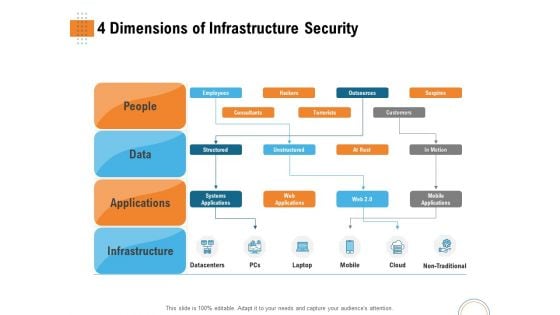
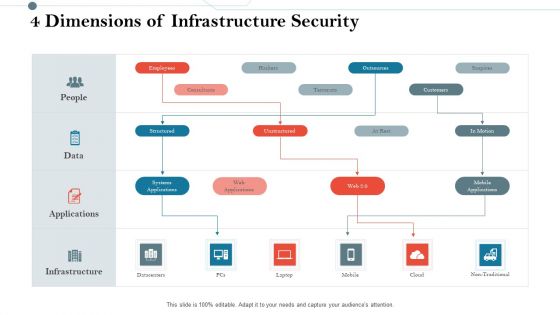
Utilizing Infrastructure Management Using Latest Methods 4 Dimensions Of Infrastructure Security Introduction PDF
Presenting utilizing infrastructure management using latest methods 4 dimensions of infrastructure security introduction pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like people, data, applications, infrastructure, datacentres, mobile, cloud, non traditional. In addition, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.
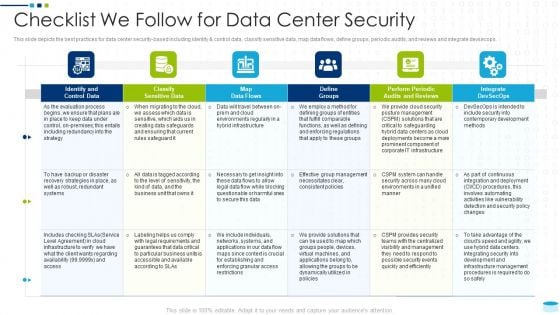
Data Center Infrastructure Management IT Checklist We Follow For Data Center Security Formats PDF
This slide depicts the best practices for data center security based including identity and control data, classify sensitive data, map data flows, define groups, periodic audits, and reviews and integrate devsecops. Deliver an awe inspiring pitch with this creative data center infrastructure management it checklist we follow for data center security formats pdf bundle. Topics like identity and control data, classify sensitive data, map data flows, define groups, periodic audits and reviews, integrate devsecops can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
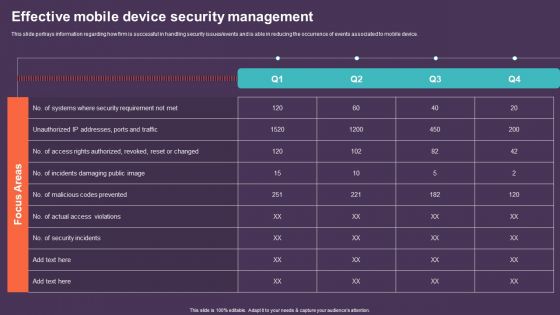
Mobile Device Management For Improving IT Operations Effective Mobile Device Security Mockup PDF
This slide portrays information regarding how firm is successful in handling security issues or events and is able in reducing the occurrence of events associated to mobile device. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Mobile Device Management For Improving IT Operations Effective Mobile Device Security Mockup PDF from Slidegeeks and deliver a wonderful presentation.
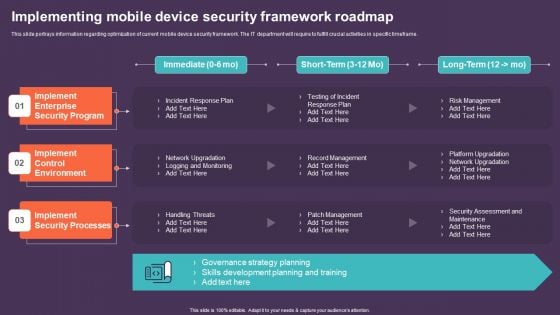
Mobile Device Management For Improving IT Operations Implementing Mobile Device Security Template PDF
This slide portrays information regarding optimization of current mobile device security framework. The IT department will require to fulfill crucial activities in specific timeframe. The Mobile Device Management For Improving IT Operations Implementing Mobile Device Security Template PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Security And Performance Digital Marketing Understand Campaign Anatomy For Advertising Management Topics PDF
This template covers the basic structure for google ads. It also depicts that google ads is the advertising management platform for google paid search pay per click search engine ads. Deliver and pitch your topic in the best possible manner with this Security And Performance Digital Marketing Understand Campaign Anatomy For Advertising Management Topics PDF. Use them to share invaluable insights on Throughout Campaign, Topic Incorporated, Numerous Content and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

IT System Risk Management Guide Financial Burden To Company From IT Security Breaches Background PDF
This slide highlights the financial burden of information technology security breaches which includes professional services, lost business opportunities, down time from multiple offices with losses. Present like a pro with IT System Risk Management Guide Financial Burden To Company From IT Security Breaches Background PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
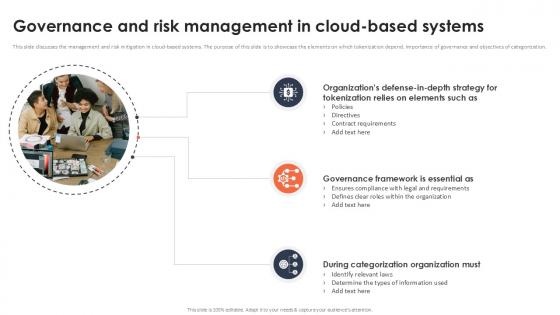
Governance And Risk Management In Cloud Based Systems Securing Your Data Ppt Example
This slide discusses the management and risk mitigation in cloud-based systems. The purpose of this slide is to showcase the elements on which tokenization depend, importance of governance and objectives of categorization. This modern and well-arranged Governance And Risk Management In Cloud Based Systems Securing Your Data Ppt Example provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide discusses the management and risk mitigation in cloud-based systems. The purpose of this slide is to showcase the elements on which tokenization depend, importance of governance and objectives of categorization.
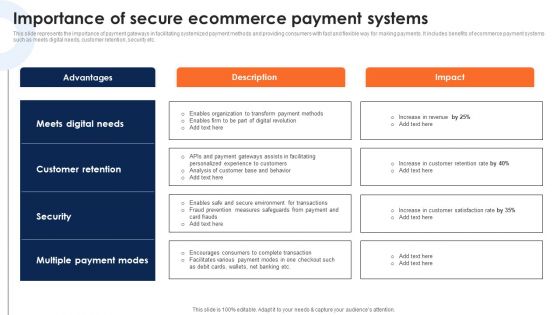
Importance Of Secure Ecommerce Payment Systems Deploying Ecommerce Order Management Software Rules PDF
This slide represents the importance of payment gateways in facilitating systemized payment methods and providing consumers with fast and flexible way for making payments. It includes benefits of ecommerce payment systems such as meets digital needs, customer retention, security etc.This modern and well-arranged Importance Of Secure Ecommerce Payment Systems Deploying Ecommerce Order Management Software Rules PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
Construction Management Services And Action Plan 4 Dimensions Of Infrastructure Security Rules PDF
Presenting construction management services and action plan 4 dimensions of infrastructure security rules pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like 30 60 90 days plan. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IoT Device Management Fundamentals IoT Device Authentication Methods To Ensure Data Security IoT Ss V
This slide showcases several IoT device authentication models for standardise and secure communication between machines. It included modules such as X.509 certificates, hardware security module, trusted platform module, and symmetric keys. Slidegeeks has constructed IoT Device Management Fundamentals IoT Device Authentication Methods To Ensure Data Security IoT SS V after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide showcases several IoT device authentication models for standardise and secure communication between machines. It included modules such as X.509 certificates, hardware security module, trusted platform module, and symmetric keys.
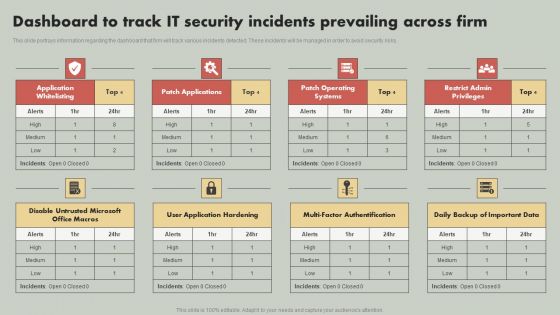
IT Reducing Costs And Management Tips Dashboard To Track IT Security Incidents Prevailing Across Firm Structure PDF
This slide portrays information regarding the dashboard that firm will track various incidents detected. These incidents will be managed in order to avoid security risks. Boost your pitch with our creative IT Reducing Costs And Management Tips Dashboard To Track IT Security Incidents Prevailing Across Firm Structure PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Managing IT Operating System 4 Dimensions Of Infrastructure Security Template PDF
Presenting this set of slides with name managing it operating system 4 dimensions of infrastructure security template pdf. The topics discussed in these slides are infrastructure, applications, data, people. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Secure Retirement Planning With Key Activities Strategic Wealth Management And Financial Fin SS V
This slide shows information which can be utilized to know basics of retirement planning. It also includes details about key activities included in retirement planning which are lifestyle assessment, income projection, etc. Get a simple yet stunning designed Secure Retirement Planning With Key Activities Strategic Wealth Management And Financial Fin SS V. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Secure Retirement Planning With Key Activities Strategic Wealth Management And Financial Fin SS V can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for. Grab this template today. This slide shows information which can be utilized to know basics of retirement planning. It also includes details about key activities included in retirement planning which are lifestyle assessment, income projection, etc.
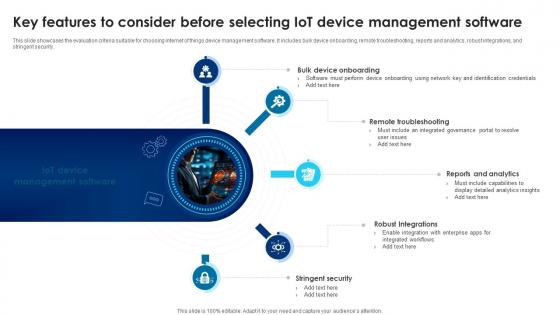
Building Trust With IoT Security Key Features To Consider Before Selecting IoT Device Management IoT SS V
This slide showcases the evaluation criteria suitable for choosing internet of things device management software. It includes bulk device onboarding, remote troubleshooting, reports and analytics, robust integrations, and stringent security. Take your projects to the next level with our ultimate collection of Building Trust With IoT Security Key Features To Consider Before Selecting IoT Device Management IoT SS V. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest This slide showcases the evaluation criteria suitable for choosing internet of things device management software. It includes bulk device onboarding, remote troubleshooting, reports and analytics, robust integrations, and stringent security.

Managing E Commerce Business Accounting Pci Certification For Increasing Security Of Online Transactions Download PDF
This slide depicts payment card industry PCI certification for increasing security of online transactions. It provides information about authorization, 2 way authentication, one time password OTP, repository, cyber attacks, compliance, data breach, etc. The Managing E Commerce Business Accounting Pci Certification For Increasing Security Of Online Transactions Download PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Implementing Management System To Enhance Ecommerce Processes Importance Of Secure Ecommerce Payment Systems Graphics PDF
This slide represents the importance of payment gateways in facilitating systemized payment methods and providing consumers with fast and flexible way for making payments. It includes benefits of ecommerce payment systems such as meets digital needs, customer retention, security etc. The Implementing Management System To Enhance Ecommerce Processes Importance Of Secure Ecommerce Payment Systems Graphics PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Secure Method For Storing Private Keys Offline In Paper Cryptocurrency Management With Blockchain
This slide highlights the overview of paper wallets in the crypto world. The purpose of this slide is to outline some basic features of a paper wallet such as present in a physical medium, having to download the code for transactions, have a unique identifiers, etc.Whether you have daily or monthly meetings, a brilliant presentation is necessary. Secure Method For Storing Private Keys Offline In Paper Cryptocurrency Management With Blockchain can be your best option for delivering a presentation. Represent everything in detail using Secure Method For Storing Private Keys Offline In Paper Cryptocurrency Management With Blockchain and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide highlights the overview of paper wallets in the crypto world. The purpose of this slide is to outline some basic features of a paper wallet such as present in a physical medium, having to download the code for transactions, have a unique identifiers, etc.
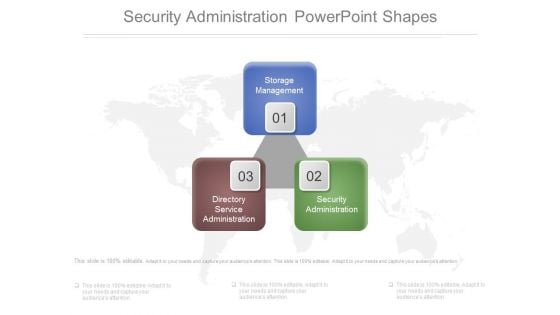
Security Administration Powerpoint Shapes
This is a security administration powerpoint shapes. This is a three stage process. The stages in this process are storage management, directory service administration, security administration.
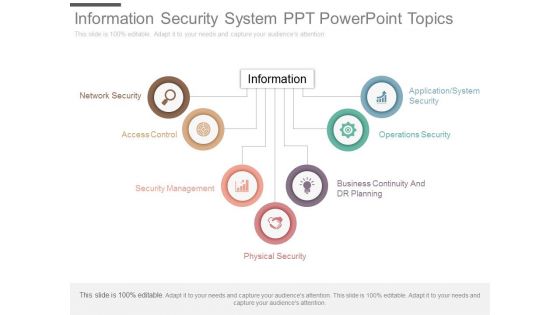
Information Security System Ppt Powerpoint Topics
This is a information security system ppt powerpoint topics. This is a seven stage process. The stages in this process are network security, access control, security management, physical security, business continuity and dr planning, operations security, application system security, information.
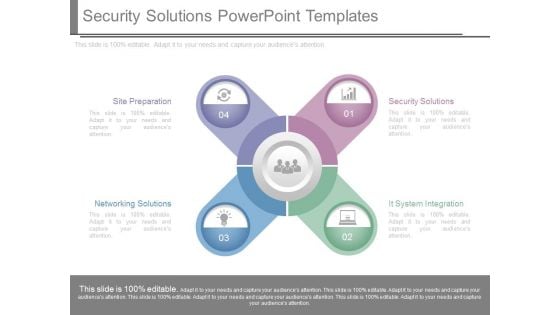
Security Solutions Powerpoint Templates
This is a security solutions powerpoint templates. This is a four stage process. The stages in this process are site preparation, networking solutions, security solutions, it system integration.

Security Services Presentation Background Images
This is a security services presentation background images. This is an eight stage process. The stages in this process are payment services, security services, authorization services, configuration manager, persistence services, stock control services, user interface services, core cash services.

Cloud Security Assessment Enterprise Cloud Security Solutions Introduction PDF
This slide describes the enterprise cloud security solutions, including multi-factor authentication, managing accounts and service proactively, being careful about shadow IT, and analyzing the cost-benefits of hybrid cloud.Deliver and pitch your topic in the best possible manner with this Cloud Security Assessment Enterprise Cloud Security Solutions Introduction PDF. Use them to share invaluable insights on Manage Accounts, Services Proactively, Processes Fingerprints and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
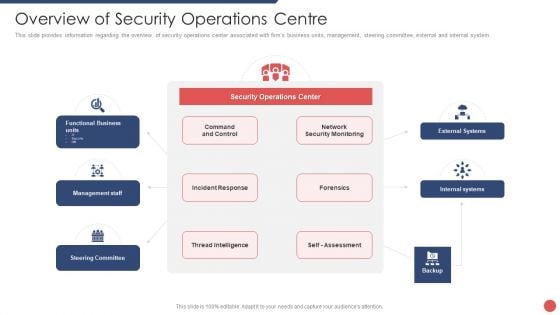
Security Functioning Centre Overview Of Security Operations Centre Summary PDF
This slide provides information regarding the overview of security operations center associated with firms business units, management, steering committee, external and internal system. Deliver and pitch your topic in the best possible manner with this security functioning centre overview of security operations centre summary pdf. Use them to share invaluable insights on management, thread intelligence, network security monitoring and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
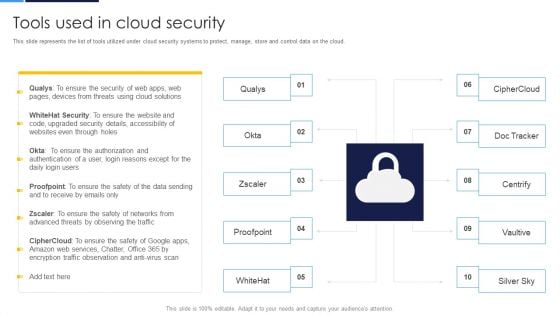
Cloud Security Assessment Tools Used In Cloud Security Designs PDF
This slide represents the list of tools utilized under cloud security systems to protect, manage, store and control data on the cloud.Deliver an awe inspiring pitch with this creative Cloud Security Assessment Tools Used In Cloud Security Designs PDF bundle. Topics like Advanced Threats, Traffic Observation, Details Accessibility can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cloud Security Assessment Roadmap Of Cloud Security Implementation Information PDF
This slide defines the roadmap of cloud security implementation in an organization and what tasks would be performed in each months interval starting from January.Presenting Cloud Security Assessment Roadmap Of Cloud Security Implementation Information PDF to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like Configuration Management, Services Management, Security Measures. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IT Security Elements Of Information Technology Security Operational Security Ppt Professional Format Ideas PDF
This slide defines the operational security element of cyber security. It also shows the best practices for operational security such as change management processes, deploys automation, etc. This is a it security elements of information technology security operational security ppt professional format ideas pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like change management processes, deploy automation, plan for disaster, restrict device access, implement dual control. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Information Security Elements Of Data Security Operational Security Ppt Icon Background Designs PDF
This slide defines the operational security element of data security. It also shows the best practices for operational security such as change management processes, deploys automation, etc. This is a information security elements of data security operational security ppt icon background designs pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like change management processes, deploy automation, plan for disaster, implement dual control, restrict device access. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
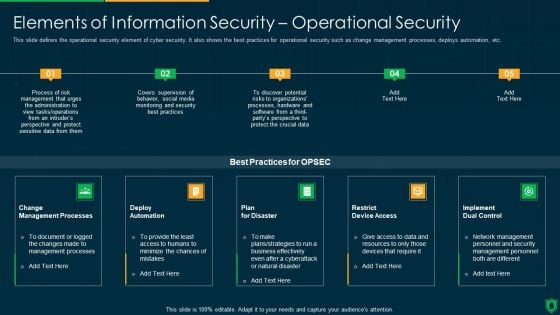
Info Security Elements Of Information Security Operational Security Ppt PowerPoint Presentation File Backgrounds PDF
This slide defines the operational security element of cyber security. It also shows the best practices for operational security such as change management processes, deploys automation, etc. This is a info security elements of information security operational security ppt powerpoint presentation file backgrounds pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like change management processes, deploy automation, plan for disaster, implement dual control. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
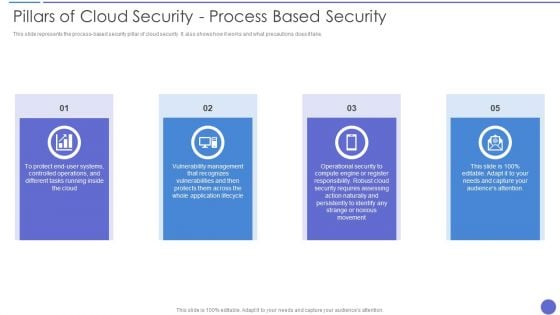
Pillars Of Cloud Security Process Based Security Information PDF
This slide represents the process based security pillar of cloud security. It also shows how it works and what precautions does it take. This is a Pillars Of Cloud Security Process Based Security Information PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Vulnerability Management, Application, Security Requires. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
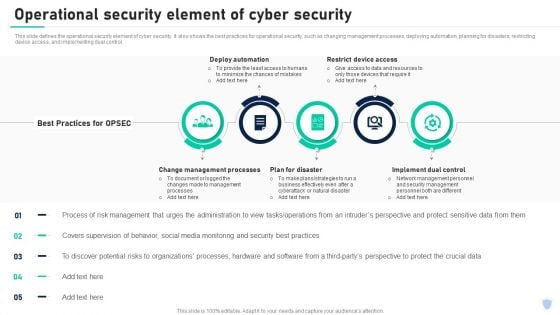
Cyber Security Components To Enhance Processes Operational Security Element Of Cyber Security Graphics PDF
This slide defines the operational security element of cyber security. It also shows the best practices for operational security, such as changing management processes, deploying automation, planning for disasters, restricting device access, and implementing dual control. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Cyber Security Components To Enhance Processes Operational Security Element Of Cyber Security Graphics PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Cyber Security Components To Enhance Processes Operational Security Element Of Cyber Security Graphics PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Mobile Security Powerpoint Presentation Slides
You will save yourself your energy and hours of time when you choose to use this impactful PowerPoint Deck. This Mobile Security Powerpoint Presentation Slides has been tailor-made to your business needs which ensures that you will always be prepared for that next meeting. Worry can not touch you when you present in your area of expertise using this PPT Template Bundle. With a modern design and easy to follow structure, this PowerPoint Presentation has Mobile Threat Defense, Mobile Authentication, Mobile Encryption, Mobile Privacy, Mobile Vulnerability Management-slides, which ensures that you can cover you need to without much work. Create your next presentation using this PPT Theme to deliver a memorable performance. The mobile security powerpoint template covers key aspects of mobile security, including threats, vulnerabilities, best practices, and implementation strategies.

Cloud Security Assessment Pillars Of Cloud Security Process Based Security Mockup PDF
This slide represents the process-based security pillar of cloud security. It also shows how it works and what precautions does it take.This is a Cloud Security Assessment Pillars Of Cloud Security Process Based Security Mockup PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Vulnerability Management, Recognizes Vulnerabilities, Operational Security You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Security Network Security Ppt PowerPoint Presentation Show Rules
This is a cyber security network security ppt powerpoint presentation show rules. This is a nine stage process. The stages in this process are business, lock, planning, strategy, marketing, security.
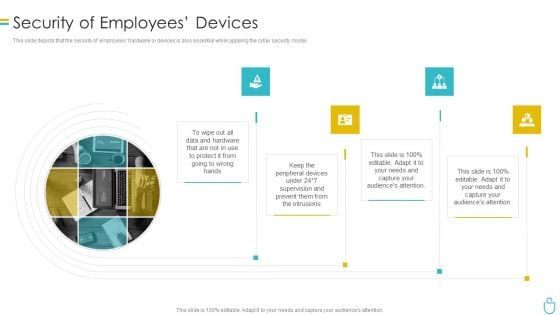
Information Security Security Of Employees Devices Ppt Model Infographics PDF
This slide depicts that the security of employees hardware or devices is also essential while applying the cyber security model. Presenting information security security of employees devices ppt model infographics pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like security of employees devices. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
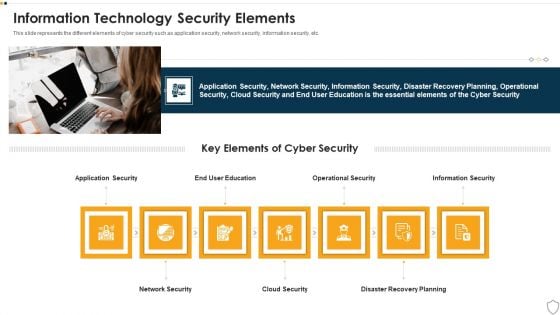
IT Security Information Technology Security Elements Ppt Images PDF
This slide represents the different elements of cyber security such as application security, network security, information security, etc. This is a it security information technology security elements ppt images pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like application security, network security, cloud security, disaster recovery planning, operational security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Pillars Of Cloud Security Network Security Rules PDF
This slide defines the network security pillar of cloud security and what precautions are taken to protect networks from attacks. This is a Pillars Of Cloud Security Network Security Rules PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Secure, Network, Information. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Security Checklist Security Patches And Updates Summary PDF
This slide depicts the importance of security patches and timely updates of security technologies. It also shows how it is crucial to scan systems, servers, and frameworks regularly. Presenting Cloud Security Checklist Security Patches And Updates Summary PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Security Patches, Measures, Organization. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
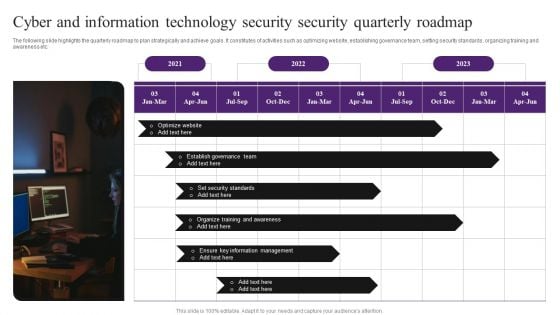
Cyber And Information Technology Security Security Quarterly Roadmap Elements PDF
The following slide highlights the quarterly roadmap to plan strategically and achieve goals. It constitutes of activities such as optimizing website, establishing governance team, setting security standards, organizing training and awareness etc. Presenting Cyber And Information Technology Security Security Quarterly Roadmap Elements PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Optimize Website, Information Management, Organize Training. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Bestinformation Technology Security And Data Security Practices Slides PDF
The following slide highlights the best practices to protect the business from security threats. It includes activities such as installing and upgrading protective software, adopting strong password policy, applying multi-layer authentication etc. Persuade your audience using this Bestinformation Technology Security And Data Security Practices Slides PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Adopt Strong Password Policy, Make Regular Backups, Resource Information. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
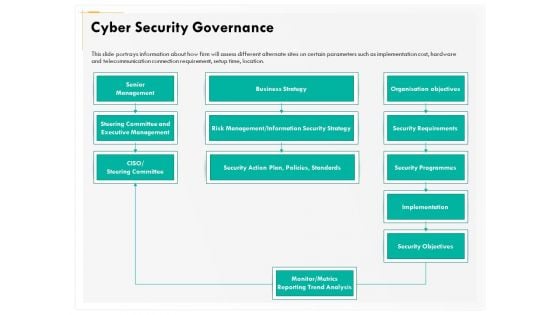
Computer Security Incident Handling Cyber Security Governance Ppt Gallery Summary PDF
Presenting this set of slides with name computer security incident handling cyber security governance ppt gallery summary pdf. The topics discussed in these slides are senior management, business strategy, security objectives, implementation, security requirements, risk management or information security strategy. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Best Practices For Implementing Application Security Application Security Testing
This slide discusses the best approaches for application security deployment which include assess threats, shift security left, control rights, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Best Practices For Implementing Application Security Application Security Testing can be your best option for delivering a presentation. Represent everything in detail using Best Practices For Implementing Application Security Application Security Testing and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide discusses the best approaches for application security deployment which include assess threats, shift security left, control rights, etc.

Application Security Testing Cloud Native Application Security Overview
The purpose of this slide is to highlight the introduction of second type of web security, that is, cloud native application security. There are so many reasons you need a Application Security Testing Cloud Native Application Security Overview. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. The purpose of this slide is to highlight the introduction of second type of web security, that is, cloud native application security.
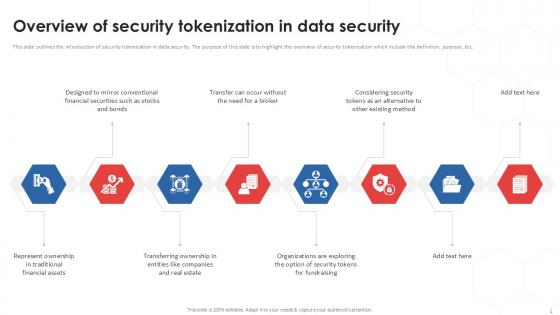
Overview Of Security Tokenization In Data Security PPT Sample
This slide outlines the introduction of security tokenization in data security. The purpose of this slide is to highlight the overview of security tokenization which include the definition, purpose, etc. Boost your pitch with our creative Overview Of Security Tokenization In Data Security PPT Sample. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide outlines the introduction of security tokenization in data security. The purpose of this slide is to highlight the overview of security tokenization which include the definition, purpose, etc.

Checklist To Implement Effective Application Security Application Security Testing
This slide showcases the actions performed while deploying application security, person responsible, status and comments for the same. If you are looking for a format to display your unique thoughts, then the professionally designed Checklist To Implement Effective Application Security Application Security Testing is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Checklist To Implement Effective Application Security Application Security Testing and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide showcases the actions performed while deploying application security, person responsible, status and comments for the same.

Introduction Of Application Security For Data Privacy Application Security Testing
This slide discusses the overview of application security which includes its objectives such as protecting data, minimize risk, etc. Explore a selection of the finest Introduction Of Application Security For Data Privacy Application Security Testing here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Introduction Of Application Security For Data Privacy Application Security Testing to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide discusses the overview of application security which includes its objectives such as protecting data, minimize risk, etc.

Security Testing Types Vulnerability Scanning Application Security Testing
This slide outlines the overview of vulnerability scanning in security testing for application security. Do you know about Slidesgeeks Security Testing Types Vulnerability Scanning Application Security Testing These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide outlines the overview of vulnerability scanning in security testing for application security.

Before Vs After Implementation Of Application Security Application Security Testing
This slide showcases the comparative analysis of the before versus after implementation of application security situation of an organization. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Before Vs After Implementation Of Application Security Application Security Testing. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Before Vs After Implementation Of Application Security Application Security Testing today and make your presentation stand out from the rest This slide showcases the comparative analysis of the before versus after implementation of application security situation of an organization.

Internet Security Framework For Data Security Summary Pdf
This slide showcase frame to handle cyber security threats and risk faced by organisation. It include identifying risk, protection, delete , respond and recover.Showcasing this set of slides titled Internet Security Framework For Data Security Summary Pdf The topics addressed in these templates are Policies And Standard, Data Collection, Establish Firewall All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcase frame to handle cyber security threats and risk faced by organisation. It include identifying risk, protection, delete , respond and recover.

Security Testing Types Penetration Testing Application Security Testing
This slide discusses the overview of penetration testing for application security which includes the purpose of penetration testing. Take your projects to the next level with our ultimate collection of Security Testing Types Penetration Testing Application Security Testing. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest This slide discusses the overview of penetration testing for application security which includes the purpose of penetration testing.

Major Impact Of Application Security On Organization Application Security Testing
This slide showcases the after application security impact on business along with factors that have improved the overall performance. Slidegeeks has constructed Major Impact Of Application Security On Organization Application Security Testing after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide showcases the after application security impact on business along with factors that have improved the overall performance.
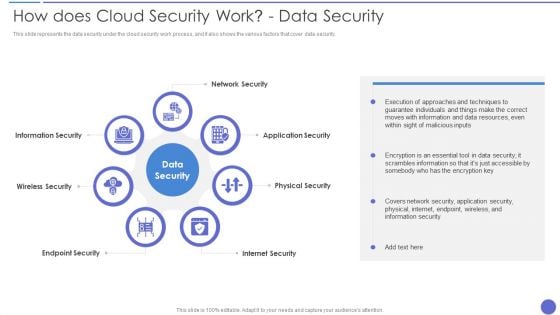
How Does Cloud Security Work Data Security Infographics PDF
This slide represents the data security under the cloud security work process, and it also shows the various factors that cover data security. This is a How Does Cloud Security Work Data Security Infographics PDF template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Application Security, Physical Security, Internet Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
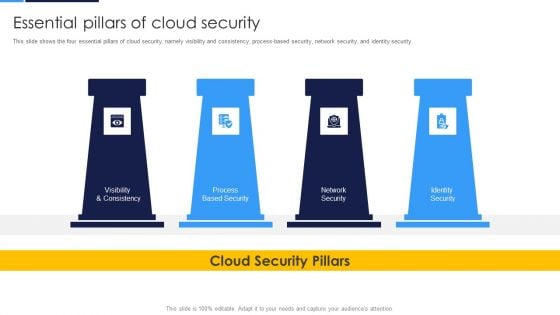
Cloud Security Assessment Essential Pillars Of Cloud Security Clipart PDF
This slide shows the four essential pillars of cloud security, namely visibility and consistency, process based security, network security, and identity security.Presenting Cloud Security Assessment Essential Pillars Of Cloud Security Clipart PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Visibility And Consistency, Network Security, Identity Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Budget Allocation For Implementing Application Security Application Security Testing
This slide showcases the technology cost breakdown for different components such as internet, software, IT staff, etc. Find highly impressive Budget Allocation For Implementing Application Security Application Security Testing on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Budget Allocation For Implementing Application Security Application Security Testing for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide showcases the technology cost breakdown for different components such as internet, software, IT staff, etc.
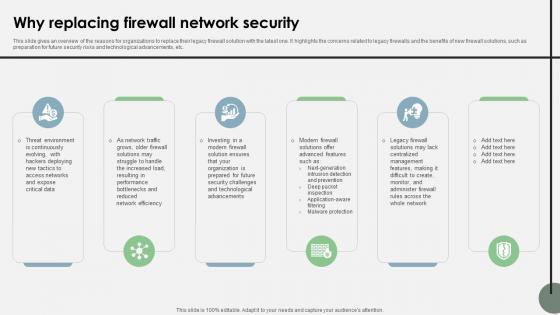
Why Replacing Firewall Network Security Cloud Security Firewall Proposal
This slide gives an overview of the reasons for organizations to replace their legacy firewall solution with the latest one. It highlights the concerns related to legacy firewalls and the benefits of new firewall solutions, such as preparation for future security risks and technological advancements, etc.Stand out from the crowd with our dynamic Why Replacing Firewall Network Security Cloud Security Firewall Proposal template. Designed to help you make a statement, this single-slide PPT template is fully customizable to suit your unique needs. With eye-catching visuals and seamless editing options, you can create impactful presentations in minutes. Say goodbye to boring slides and unlock your presentation potential with our top-notch template. This slide gives an overview of the reasons for organizations to replace their legacy firewall solution with the latest one. It highlights the concerns related to legacy firewalls and the benefits of new firewall solutions, such as preparation for future security risks and technological advancements, etc.

Top Five Application Security Trends Application Security Testing
This slide showcases the five trends of application security which include, AppSec and CloudSec merge, expanding attack surfaces, etc. Slidegeeks has constructed Top Five Application Security Trends Application Security Testing after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide showcases the five trends of application security which include, AppSec and CloudSec merge, expanding attack surfaces, etc.

Security Testing Types Code Review Application Security Testing
This slide outlines the introduction of secure code review in application security for efficient working of an application. This Security Testing Types Code Review Application Security Testing from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide outlines the introduction of secure code review in application security for efficient working of an application.


 Continue with Email
Continue with Email

 Home
Home


































