Security Management

Best Practices For Tokenization In Data Security Securing Your Data Ppt Example
The purpose of this slide is to highlight the best approaches for tokenization. The practices include broadening data tokenization scope, regularly revise policies, effective cyber security, etc. There are so many reasons you need a Best Practices For Tokenization In Data Security Securing Your Data Ppt Example The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. The purpose of this slide is to highlight the best approaches for tokenization. The practices include broadening data tokenization scope, regularly revise policies, effective cyber security, etc.
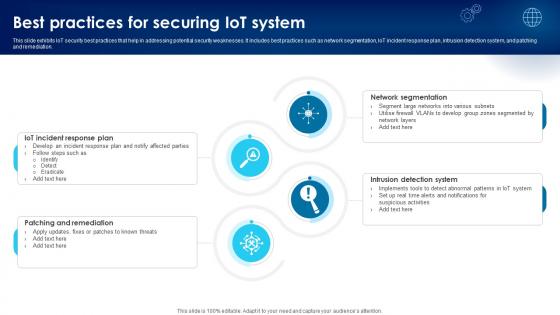
Building Trust With IoT Security Best Practices For Securing IoT System IoT SS V
This slide exhibits IoT security best practices that help in addressing potential security weaknesses. It includes best practices such as network segmentation, IoT incident response plan, intrusion detection system, and patching and remediation. Want to ace your presentation in front of a live audience Our Building Trust With IoT Security Best Practices For Securing IoT System IoT SS V can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide exhibits IoT security best practices that help in addressing potential security weaknesses. It includes best practices such as network segmentation, IoT incident response plan, intrusion detection system, and patching and remediation.
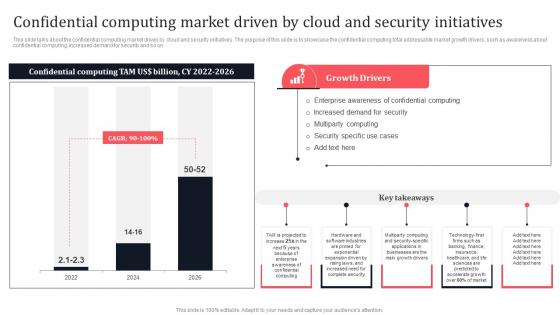
Confidential Computing Market Driven By Cloud And Security Secure Multi Party Microsoft Pdf
This slide talks about the confidential computing market driven by cloud and security initiatives. The purpose of this slide is to showcase the confidential computing total addressable market growth drivers, such as awareness about confidential computing, increased demand for security and so on. Make sure to capture your audiences attention in your business displays with our gratis customizable Confidential Computing Market Driven By Cloud And Security Secure Multi Party Microsoft Pdf These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide talks about the confidential computing market driven by cloud and security initiatives. The purpose of this slide is to showcase the confidential computing total addressable market growth drivers, such as awareness about confidential computing, increased demand for security and so on.
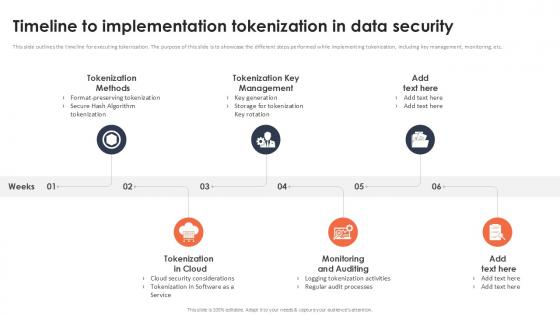
Timeline To Implementation Tokenization In Data Security Securing Your Data Ppt Sample
This slide outlines the timeline for executing tokenization. The purpose of this slide is to showcase the different steps performed while implementing tokenization, including key management, monitoring, etc. Get a simple yet stunning designed Timeline To Implementation Tokenization In Data Security Securing Your Data Ppt Sample It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Timeline To Implementation Tokenization In Data Security Securing Your Data Ppt Sample can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide outlines the timeline for executing tokenization. The purpose of this slide is to showcase the different steps performed while implementing tokenization, including key management, monitoring, etc.
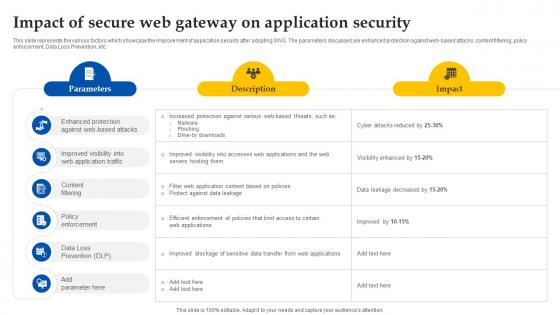
Web Access Control Solution Impact Of Secure Web Gateway On Application Security
This slide represents the various factors which showcase the improvement of application security after adopting SWG. The parameters discussed are enhanced protection against web-based attacks, content filtering, policy enforcement, Data Loss Prevention, etc. Welcome to our selection of the Web Access Control Solution Impact Of Secure Web Gateway On Application Security. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. This slide represents the various factors which showcase the improvement of application security after adopting SWG. The parameters discussed are enhanced protection against web-based attacks, content filtering, policy enforcement, Data Loss Prevention, etc.
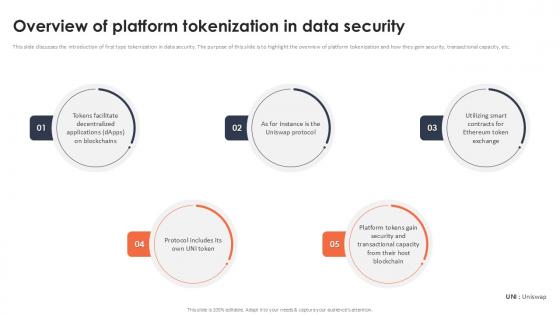
Overview Of Platform Tokenization In Data Security Securing Your Data Ppt Presentation
This slide discusses the introduction of first type tokenization in data security. The purpose of this slide is to highlight the overview of platform tokenization and how they gain security, transactional capacity, etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Overview Of Platform Tokenization In Data Security Securing Your Data Ppt Presentation to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Overview Of Platform Tokenization In Data Security Securing Your Data Ppt Presentation This slide discusses the introduction of first type tokenization in data security. The purpose of this slide is to highlight the overview of platform tokenization and how they gain security, transactional capacity, etc.

Types Of Secure Code Review In Application Security Testing Ppt Powerpoint Slides
This slide discusses the two types of secure code review in application security which are automated code review and manual code review. This Types Of Secure Code Review In Application Security Testing Ppt Powerpoint Slides from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide discusses the two types of secure code review in application security which are automated code review and manual code review.
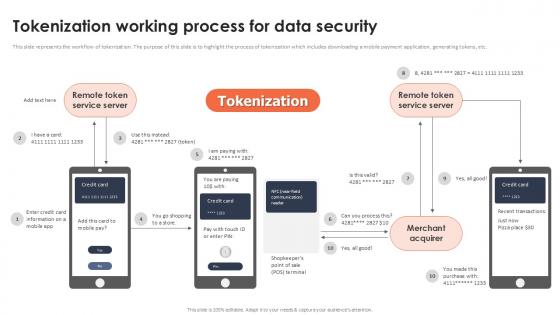
Tokenization Working Process For Data Security Securing Your Data Ppt Presentation
This slide represents the workflow of tokenization. The purpose of this slide is to highlight the process of tokenization which includes downloading a mobile payment application, generating tokens, etc. Find highly impressive Tokenization Working Process For Data Security Securing Your Data Ppt Presentation on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Tokenization Working Process For Data Security Securing Your Data Ppt Presentation for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide represents the workflow of tokenization. The purpose of this slide is to highlight the process of tokenization which includes downloading a mobile payment application, generating tokens, etc.
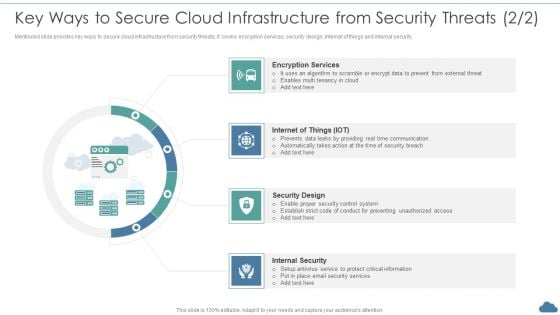
Cloud Optimization Infrastructure Model Key Ways To Secure Cloud Infrastructure From Security Threats Elements PDF
Mentioned slide provides key ways to secure cloud infrastructure from security threats. It covers encryption services, security design, internet of things and internal security.This is a Cloud Optimization Infrastructure Model Key Ways To Secure Cloud Infrastructure From Security Threats Elements PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Encryption Services, Security Design, Internal Security You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
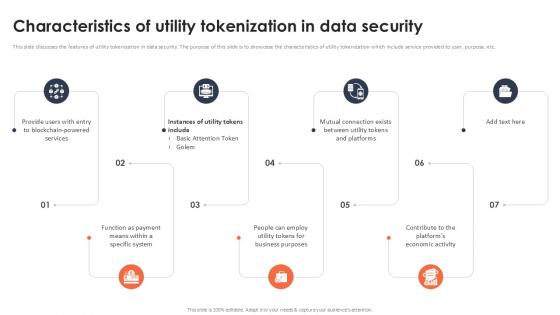
Characteristics Of Utility Tokenization In Data Security Securing Your Data Ppt Slide
This slide discusses the features of utility tokenization in data security. The purpose of this slide is to showcase the characteristics of utility tokenization which include service provided to user, purpose, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Characteristics Of Utility Tokenization In Data Security Securing Your Data Ppt Slide will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide discusses the features of utility tokenization in data security. The purpose of this slide is to showcase the characteristics of utility tokenization which include service provided to user, purpose, etc.
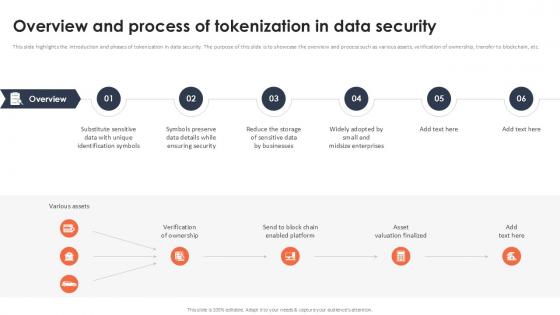
Overview And Process Of Tokenization In Data Security Securing Your Data Ppt Presentation
This slide highlights the introduction and phases of tokenization in data security. The purpose of this slide is to showcase the overview and process such as various assets, verification of ownership, transfer to blockchain, etc. Slidegeeks has constructed Overview And Process Of Tokenization In Data Security Securing Your Data Ppt Presentation after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide highlights the introduction and phases of tokenization in data security. The purpose of this slide is to showcase the overview and process such as various assets, verification of ownership, transfer to blockchain, etc.
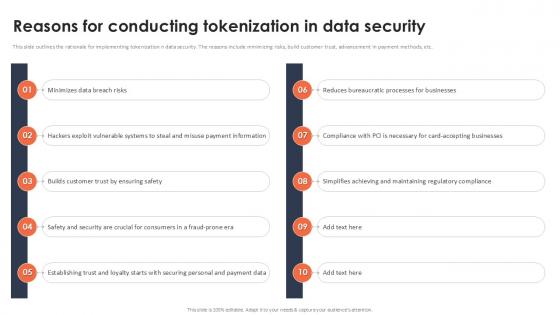
Reasons For Conducting Tokenization In Data Security Securing Your Data Ppt Presentation
This slide outlines the rationale for implementing tokenization n data security. The reasons include minimizing risks, build customer trust, advancement in payment methods, etc. Do you know about Slidesgeeks Reasons For Conducting Tokenization In Data Security Securing Your Data Ppt Presentation These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide outlines the rationale for implementing tokenization n data security. The reasons include minimizing risks, build customer trust, advancement in payment methods, etc.
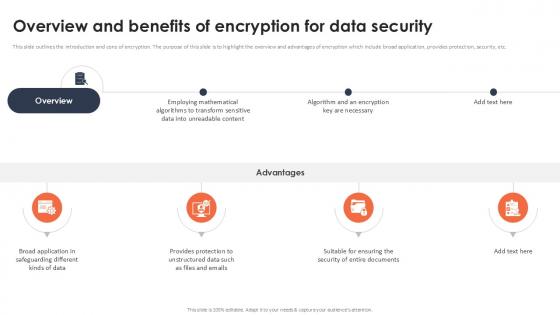
Overview And Benefits Of Encryption For Data Security Securing Your Data Ppt Powerpoint
This slide outlines the introduction and cons of encryption. The purpose of this slide is to highlight the overview and advantages of encryption which include broad application, provides protection, security, etc. Retrieve professionally designed Overview And Benefits Of Encryption For Data Security Securing Your Data Ppt Powerpoint to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide outlines the introduction and cons of encryption. The purpose of this slide is to highlight the overview and advantages of encryption which include broad application, provides protection, security, etc.
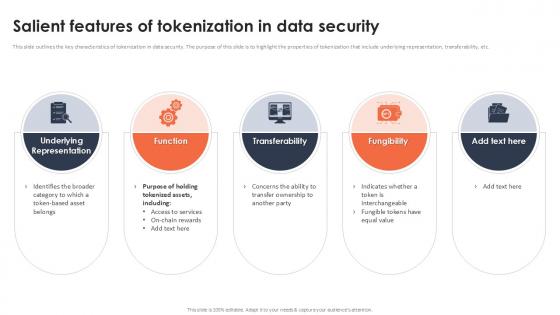
Salient Features Of Tokenization In Data Security Securing Your Data Ppt Sample
This slide outlines the key characteristics of tokenization in data security. The purpose of this slide is to highlight the properties of tokenization that include underlying representation, transferability, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Salient Features Of Tokenization In Data Security Securing Your Data Ppt Sample for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide outlines the key characteristics of tokenization in data security. The purpose of this slide is to highlight the properties of tokenization that include underlying representation, transferability, etc.

Common Use Cases Of Tokenization In Data Security Securing Your Data Ppt Sample
This slide outlines the typical scenarios where tokenization is applied within data security contexts. The use cases include reducing compliance scope, restricting access to sensitive data, etc. Slidegeeks is here to make your presentations a breeze with Common Use Cases Of Tokenization In Data Security Securing Your Data Ppt Sample With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide outlines the typical scenarios where tokenization is applied within data security contexts. The use cases include reducing compliance scope, restricting access to sensitive data, etc.

Cybersecurity Operations Cybersecops RACI Matrix For SOC As A Service Security Model Microsoft PDF
This slide outlines the RACI matrix for the SOC-as-a-Service security model. The purpose of this slide is to highlight the various roles and responsibilities in a SOC as a Service environment. The main roles include SOC manager, security analyst, security architecture, compliance auditor, and SOC coordinator. Slidegeeks is here to make your presentations a breeze with Cybersecurity Operations Cybersecops RACI Matrix For SOC As A Service Security Model Microsoft PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

CASB 2 0 IT Cloud Access Security Broker And Secure Web Gateway
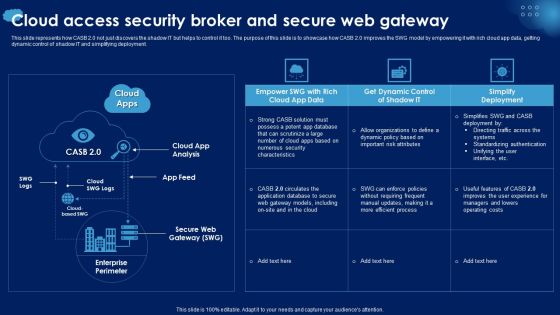
This slide represents how CASB 2.0 not just discovers the shadow IT but helps to control it too. The purpose of this slide is to showcase how CASB 2.0 improves the SWG model by empowering it with rich cloud app data, getting dynamic control of shadow IT and simplifying deployment. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our CASB 2 0 IT Cloud Access Security Broker And Secure Web Gateway was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into CASB 2 0 IT Cloud Access Security Broker And Secure Web Gateway. This slide represents how CASB 2.0 not just discovers the shadow IT but helps to control it too. The purpose of this slide is to showcase how CASB 2.0 improves the SWG model by empowering it with rich cloud app data, getting dynamic control of shadow IT and simplifying deployment.

Building Trust With IoT Security Edge Computing Role In Securing IoT Data IoT SS V
This slide showcases the significant role of edge computing in enhancing IoT data security and privacy. It include role such as data filtering and processing, localised threat identification, and reduce attack surface. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Building Trust With IoT Security Edge Computing Role In Securing IoT Data IoT SS V and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide showcases the significant role of edge computing in enhancing IoT data security and privacy. It include role such as data filtering and processing, localised threat identification, and reduce attack surface.

Tokenization In Payment Card Industry For Data Security Securing Your Data Ppt Example
This slide outlines the introduction of tokenization in payment card industry. The purpose of this slide is to showcase the process of tokenization in payment card industry to secure non sharable details of client. Slidegeeks is here to make your presentations a breeze with Tokenization In Payment Card Industry For Data Security Securing Your Data Ppt Example With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide outlines the introduction of tokenization in payment card industry. The purpose of this slide is to showcase the process of tokenization in payment card industry to secure non sharable details of client.

Defining Business Priorities To Ensure Information Security Ppt Pictures Gallery PDF
This slide illustrates the key business priorities of the organization such as efficient risk management, standardized incident management process to ensure information security. This is a defining business priorities to ensure information security ppt pictures gallery pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like reduce, risk, security, implement, communication. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Roadmap To Implement Tokenization For Data Security Securing Your Data Ppt Sample
This slide outlines the deployment for tokenization. The purpose of this slide is to highlight the steps that an organization should take while implementing tokenization including, generating tokens, identifying sensitive data, etc. Boost your pitch with our creative Roadmap To Implement Tokenization For Data Security Securing Your Data Ppt Sample Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide outlines the deployment for tokenization. The purpose of this slide is to highlight the steps that an organization should take while implementing tokenization including, generating tokens, identifying sensitive data, etc.
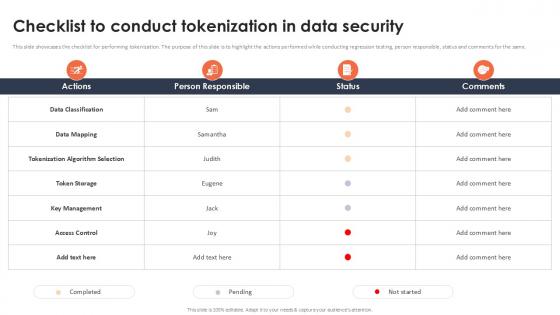
Checklist To Conduct Tokenization In Data Security Securing Your Data Ppt Example
This slide showcases the checklist for performing tokenization. The purpose of this slide is to highlight the actions performed while conducting regression testing, person responsible, status and comments for the same. Present like a pro with Checklist To Conduct Tokenization In Data Security Securing Your Data Ppt Example Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide showcases the checklist for performing tokenization. The purpose of this slide is to highlight the actions performed while conducting regression testing, person responsible, status and comments for the same.

Before Vs After Implementing Tokenization In Data Security Securing Your Data Ppt Example
This slide showcases the comparative analysis of the before versus after tokenization. The purpose of this slide is to showcase the different performance metrics and how tokenization has improved these metrics. Want to ace your presentation in front of a live audience Our Before Vs After Implementing Tokenization In Data Security Securing Your Data Ppt Example can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide showcases the comparative analysis of the before versus after tokenization. The purpose of this slide is to showcase the different performance metrics and how tokenization has improved these metrics.

Data Security Benefits Of Adopting Tokenization Securing Your Data Ppt Presentation
This slide discusses the cons of tokenization. The purpose of this slide is to showcase the advantages of tokenization such as utilizing less resources, decreases risk, stimulates innovation, etc. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Data Security Benefits Of Adopting Tokenization Securing Your Data Ppt Presentation and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide discusses the cons of tokenization. The purpose of this slide is to showcase the advantages of tokenization such as utilizing less resources, decreases risk, stimulates innovation, etc.
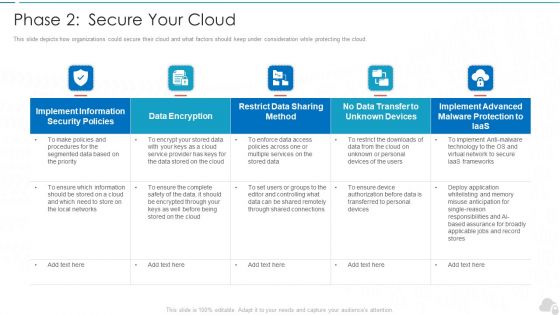
Phase 2 Secure Your Cloud Cloud Computing Security IT Ppt Slides Skills PDF
This slide depicts how organizations could secure their cloud and what factors should keep under consideration while protecting the cloud. Deliver an awe inspiring pitch with this creative phase 2 secure your cloud cloud computing security it ppt slides skills pdf bundle. Topics like implement, security policies, data encryption, services, frameworks can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
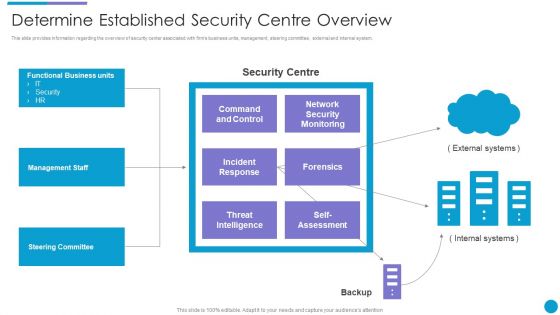
Major Techniques For Project Safety IT Determine Established Security Centre Overview Summary PDF
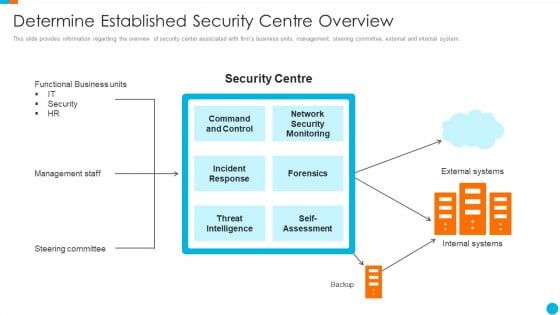
This slide provides information regarding the overview of security center associated with firms business units, management, steering committee, external and internal system. Presenting major techniques for project safety it determine established security centre overview summary pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like management staff, steering committee, functional business units, threat intelligence. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
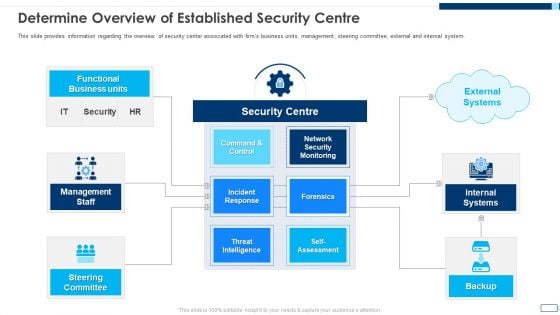
Evolving BI Infrastructure Determine Overview Of Established Security Centre Slides PDF
This slide provides information regarding the overview of security center associated with firms business units, management, steering committee, external and internal system. Presenting evolving bi infrastructure determine overview of established security centre slides pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like management staff, steering committee, internal systems, backup, functional business units. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Upgrading Total Project Safety IT Determine Established Security Centre Overview Sample PDF
This slide provides information regarding the overview of security center associated with firms business units, management, steering committee, external and internal system. This is a upgrading total project safety it determine established security centre overview sample pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like incident response, forensics, threat intelligence, command and control, network security monitoring. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Table Of Contents For Secure Access Service Edge Cloud Security Model Ppt Professional Backgrounds PDF
Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Table Of Contents For Secure Access Service Edge Cloud Security Model Ppt Professional Backgrounds PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Table Of Contents For Secure Access Service Edge Cloud Security Model Ppt Professional Backgrounds PDF today and make your presentation stand out from the rest.

Cloud Information Security Phase 2 Secure Your Cloud Ppt Slides Guidelines PDF
This slide depicts how organizations could secure their cloud and what factors should keep under consideration while protecting the cloud. Deliver an awe inspiring pitch with this creative Cloud Information Security Phase 2 Secure Your Cloud Ppt Slides Guidelines PDF bundle. Topics like Implement Information, Data Encryption, Implement Advanced can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Cloud Access Security Broker And Secure Web Gateway Ppt PowerPoint Presentation Diagram Images PDF
This slide represents how CASB 2.0 not just discovers the shadow IT but helps to control it too. The purpose of this slide is to showcase how CASB 2.0 improves the SWG model by empowering it with rich cloud app data, getting dynamic control of shadow IT and simplifying deployment. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Cloud Access Security Broker And Secure Web Gateway Ppt PowerPoint Presentation Diagram Images PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Cloud Access Security Broker And Secure Web Gateway Ppt PowerPoint Presentation Diagram Images PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.
Information Technology Security Set Measures For Secure Communication Ppt Professional Portrait PDF
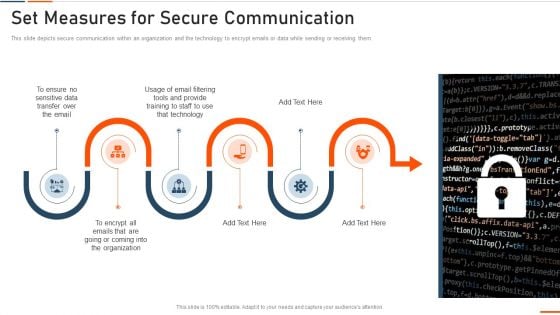
This is a information technology security set measures for secure communication ppt professional portrait pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like sensitive data, transfer, technology, training, organization. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Secure Access Service Edge Cloud Security Model Table Of Contents Ppt Layouts Format Ideas PDF
Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Secure Access Service Edge Cloud Security Model Table Of Contents Ppt Layouts Format Ideas PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Secure Access Service Edge Cloud Security Model Table Of Contents Ppt Layouts Format Ideas PDF.
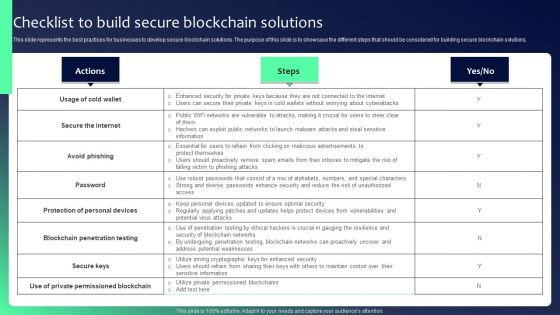
Blockchain Security Solutions Deployment Checklist To Build Secure Blockchain Diagrams PDF
This slide represents the best practices for businesses to develop secure blockchain solutions. The purpose of this slide is to showcase the different steps that should be considered for building secure blockchain solutions. Want to ace your presentation in front of a live audience Our Blockchain Security Solutions Deployment Checklist To Build Secure Blockchain Diagrams PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.

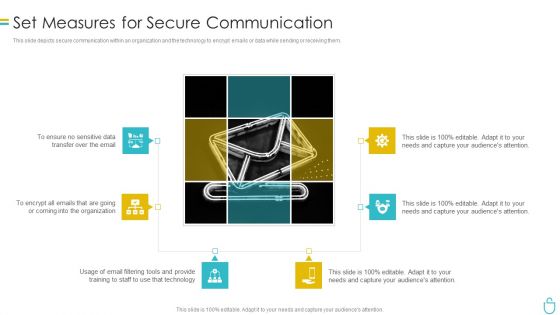
Info Security Set Measures For Secure Communication Ppt PowerPoint Presentation Gallery Graphics Design PDF
This slide depicts secure communication within an organization and the technology to encrypt emails or data while sending or receiving them. This is a info security set measures for secure communication ppt powerpoint presentation gallery graphics design pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like sensitive data, organization, email filtering tools, technology. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Information Security Set Measures For Secure Communication Ppt Outline Slide Download PDF
This slide depicts secure communication within an organization and the technology to encrypt emails or data while sending or receiving them. This is a information security set measures for secure communication ppt outline slide download pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like organization, technology. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
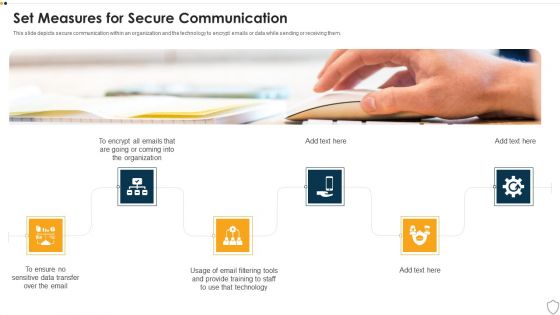
IT Security Set Measures For Secure Communication Ppt Infographic Template Background Designs PDF
This slide depicts secure communication within an organization and the technology to encrypt emails or data while sending or receiving them. This is a it security set measures for secure communication ppt infographic template background designs pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like technology, training, organization, data transfer. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
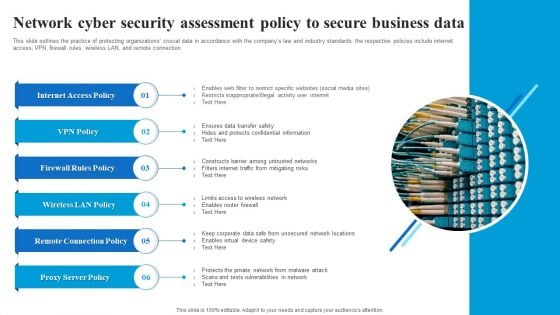
Network Cyber Security Assessment Policy To Secure Business Data Microsoft PDF
This slide outlines the practice of protecting organizations crucial data in accordance with the companys law and industry standards. the respective policies include internet access, VPN, firewall rules, wireless LAN, and remote connection. Showcasing this set of slides titled Network Cyber Security Assessment Policy To Secure Business Data Microsoft PDF. The topics addressed in these templates are Internet Access Policy, Firewall Rules Policy, Wireless LAN Policy, Remote Connection Policy. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Secure Access Service Edge Cloud Security Model Ppt PowerPoint Presentation Complete Deck With Slides
With well-researched insights and carefully-constructed design, this Secure Access Service Edge Cloud Security Model Ppt PowerPoint Presentation Complete Deck With Slides is all that you need for your next business meeting with clients and win them over. Add your data to graphs, charts, and tables that are already ready to display it with stunning visuals and help your audience recall your work. With this PPT Complete Deck, you will be able to display your knowledge of the subject as well as your skills as a communicator. Share your ideas and make an impact on the audience with this PowerPoint Layout and ensure that you are known as a presentation professional. Download this PPT Template Bundle to create the most interesting presentation anyone has ever seen.

Dashboard To Track IT Security Playbook For Strategic Actions To Improve IT Performance Summary Pdf
This slide portrays information regarding the dashboard that firm will track various incidents detected. These incidents will be managed in order to avoid security risks. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Dashboard To Track IT Security Playbook For Strategic Actions To Improve IT Performance Summary Pdf and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide portrays information regarding the dashboard that firm will track various incidents detected. These incidents will be managed in order to avoid security risks.
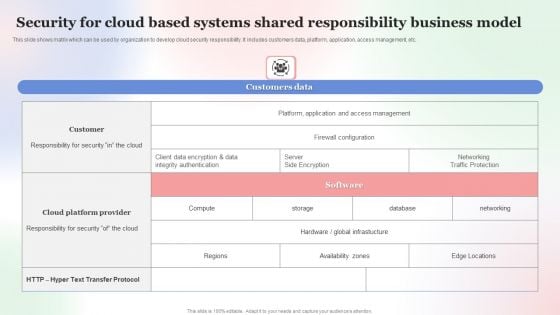
Security For Cloud Based Systems Shared Responsibility Business Model Professional PDF
This slide shows matrix which can be used by organization to develop cloud security responsibility. It includes customers data, platform, application, access management, etc. Showcasing this set of slides titled Security For Cloud Based Systems Shared Responsibility Business Model Professional PDF. The topics addressed in these templates are Security For Cloud Based, Systems Shared Responsibility, Business Model. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
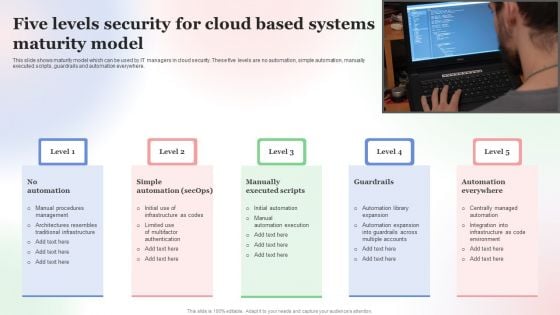
Five Levels Security For Cloud Based Systems Maturity Model Microsoft PDF
This slide shows maturity model which can be used by IT managers in cloud security. These five levels are no automation, simple automation, manually executed scripts, guardrails and automation everywhere. Presenting Five Levels Security For Cloud Based Systems Maturity Model Microsoft PDF to dispense important information. This template comprises Five stages. It also presents valuable insights into the topics including Five Levels Security, Cloud Based Systems, Maturity Model. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
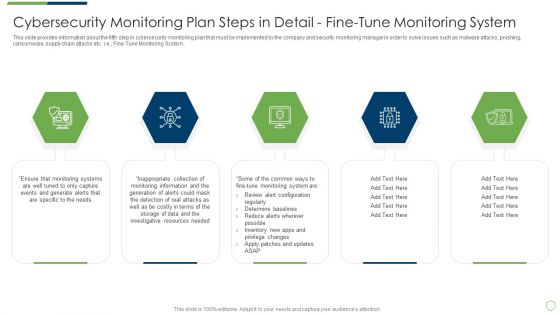
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Plan Steps In Detail Fine Sample PDF
This slide provides information about the third step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Monitoring Network Traffic. Deliver and pitch your topic in the best possible manner with this modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring plan steps in detail fine sample pdf. Use them to share invaluable insights on cybersecurity monitoring plan steps in detail monitoring network traffic and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Tools To Be Implemented Portrait PDF
This slide provides information about the fourth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Monitoring User Activity. Deliver an awe inspiring pitch with this creative modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring tools to be implemented portrait pdf bundle. Topics like cybersecurity monitoring plan steps in detail monitoring user activity can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
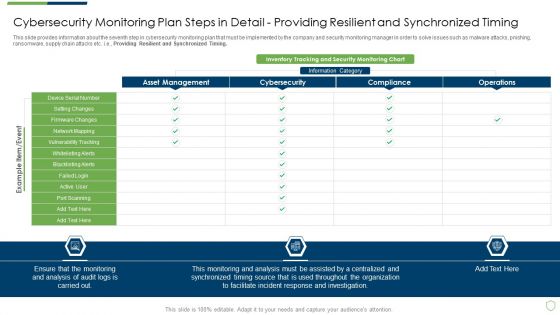
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Plan Steps In Detail Providing Sample PDF
This slide provides information about the second step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e., Monitoring All Systems. Deliver an awe inspiring pitch with this creative modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring plan steps in detail providing sample pdf bundle. Topics like cybersecurity monitoring plan steps in detail monitoring all systems can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Cyber Security Plan Road Map Of A Company Ppt PowerPoint Presentation Icon Show PDF
This slide represents 3 year cyber security plan road map of a company for website enhancement and implementing security to operational work with specific standards. It consists security standards, training and awareness phishing users and sensitive data management. Showcasing this set of slides titled Cyber Security Plan Road Map Of A Company Ppt PowerPoint Presentation Icon Show PDF. The topics addressed in these templates are Website Enhancement, Governance Subcommittee, Security Standards. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Communication Plan For Information Technology Security Based On Audience Type Demonstration PDF
This slide consists of a communication plan information technology security to be deployed by managers based on the type of audience. Key elements include communication, frequency, communication goal, owner, etc. Presenting Communication Plan For Information Technology Security Based On Audience Type Demonstration PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Project Status Report, Team Standup, Task Progress Updates. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Data Safety Initiatives Defining Business Priorities To Ensure Information Security Slides PDF
This slide illustrates the key business priorities of the organization such as efficient risk management, standardized incident management process to ensure information security. This is a data safety initiatives defining business priorities to ensure information security slides pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like efficient risk management, transparent communication, standardized incident management process. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Software Company Investor Funding Pitch Deck Client Testimonials Diagrams PDF
The following slide showcases perceptive of expert analysts about IT company i.e. Awake Society. It showcase reviews of IT manager, chief information security officer and IT director. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Security Software Company Investor Funding Pitch Deck Client Testimonials Diagrams PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
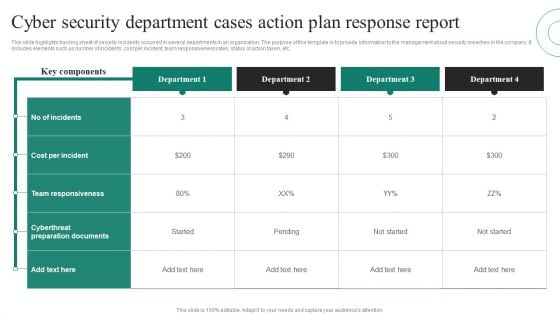
Cyber Security Department Cases Action Plan Response Report Ppt PowerPoint Presentation File Layout PDF
This slide highlights tracking sheet of security incidents occurred in several departments in an organization. The purpose of this template is to provide information to the management about security breaches in the company. It includes elements such as number of incidents, cost per incident, team responsiveness rates, status of action taken, etc. Pitch your topic with ease and precision using this Cyber Security Department Cases Action Plan Response Report Ppt PowerPoint Presentation File Layout PDF. This layout presents information on Key Components, Cost Per Incident, Team Responsiveness. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Methods Used By Asymmetric Algorithm Data Security In Cloud Computing Ppt Powerpoint
This slide talks about the various applications of asymmetric algorithm in cloud cryptography. The purpose of this slide is to explain how this technique can help in providing security in cloud computing. These are authentication, encryption, key management and digital signatures. Boost your pitch with our creative Methods Used By Asymmetric Algorithm Data Security In Cloud Computing Ppt Powerpoint. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide talks about the various applications of asymmetric algorithm in cloud cryptography. The purpose of this slide is to explain how this technique can help in providing security in cloud computing. These are authentication, encryption, key management and digital signatures.

Real Time Assessment Of Security Threats Need For SIEM Software In Your Company Template PDF
This slide covers the need for the SIEM software which focuses on detecting incidents, compliance regulations, and incident management. Presenting real time assessment of security threats need for siem software in your company template pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like detecting incidents, compliance with regulations, efficient incident management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
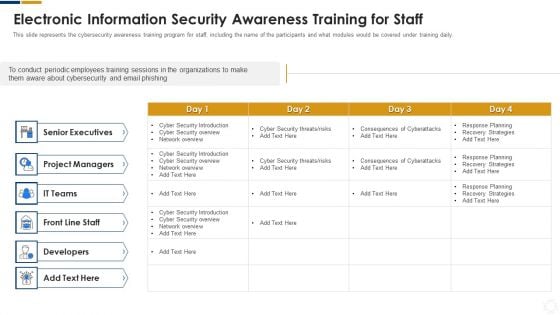
Cybersecurity Electronic Information Security Awareness Training For Staff Ppt Layouts Deck PDF
This slide represents the cybersecurity awareness training program for staff, including the name of the participants and what modules would be covered under training daily. Deliver an awe inspiring pitch with this creative cybersecurity electronic information security awareness training for staff ppt layouts deck pdf bundle. Topics like project managers, developers, senior executives, cyber security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Current Information And Data Security Capabilities Of Firm Cybersecurity Risk Assessment Infographics PDF
This slide showcases current capabilities of organization regarding information and data security. Its key component are risk management functions, required standard rating and actual standard rating. The Current Information And Data Security Capabilities Of Firm Cybersecurity Risk Assessment Infographics PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
Kpi Dashboard For Tracking Virtual Security Hazards Of Healthcare Organization Professional Pdf
This slide depicts dashboard for tracking cyber security risks faced by healthcare organizations to effectively manage the major threats and take action accordingly. The key performing indicators are percentage of risks exceeding threshold limit, breakdown of threat rating, action plan etc. Showcasing this set of slides titled Kpi Dashboard For Tracking Virtual Security Hazards Of Healthcare Organization Professional Pdf. The topics addressed in these templates are Analysis Progress, Resolution Progress, Threshold Limit. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide depicts dashboard for tracking cyber security risks faced by healthcare organizations to effectively manage the major threats and take action accordingly. The key performing indicators are percentage of risks exceeding threshold limit, breakdown of threat rating, action plan etc.
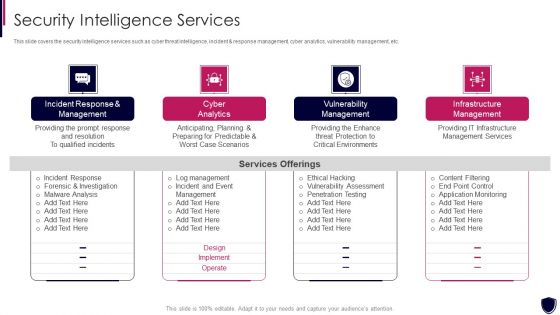
Enhancing Cyber Safety With Vulnerability Administration Security Intelligence Services Portrait PDF
This slide covers the security intelligence services such as cyber threat intelligence, incident and response management, cyber analytics, vulnerability management, etc. Presenting enhancing cyber safety with vulnerability administration security intelligence services portrait pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like incident response and management, cyber analytics, vulnerability management, infrastructure management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
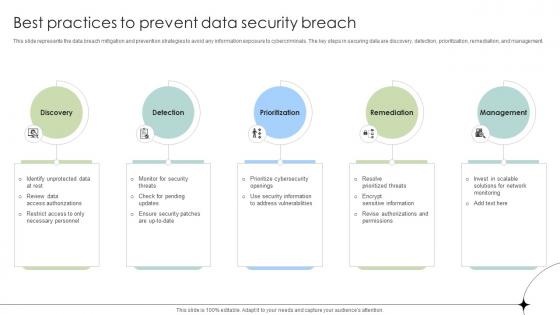
Best Practices To Prevent Data Security Breach Data Fortification Strengthening Defenses
This slide represents the data breach mitigation and prevention strategies to avoid any information exposure to cybercriminals. The key steps in securing data are discovery, detection, prioritization, remediation, and management. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Best Practices To Prevent Data Security Breach Data Fortification Strengthening Defenses a try. Our experts have put a lot of knowledge and effort into creating this impeccable Best Practices To Prevent Data Security Breach Data Fortification Strengthening Defenses. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide represents the data breach mitigation and prevention strategies to avoid any information exposure to cybercriminals. The key steps in securing data are discovery, detection, prioritization, remediation, and management.
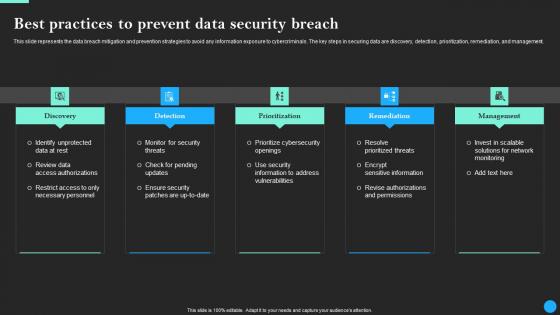
Best Practices To Prevent Data Security Breach Data Breach Prevention Information Pdf
This slide represents the data breach mitigation and prevention strategies to avoid any information exposure to cybercriminals. The key steps in securing data are discovery, detection, prioritization, remediation, and management. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Best Practices To Prevent Data Security Breach Data Breach Prevention Information Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Best Practices To Prevent Data Security Breach Data Breach Prevention Information Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide represents the data breach mitigation and prevention strategies to avoid any information exposure to cybercriminals. The key steps in securing data are discovery, detection, prioritization, remediation, and management.
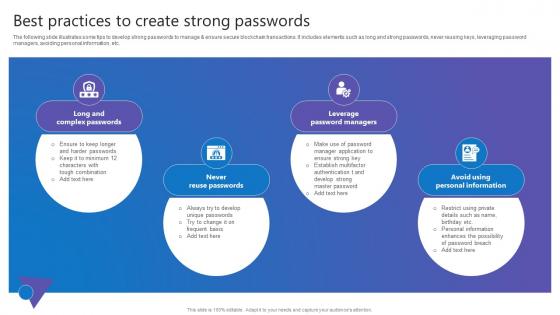
Best Practices To Create Comprehensive Guide To Blockchain Digital Security Clipart Pdf
The following slide illustrates some tips to develop strong passwords to manage and ensure secure blockchain transactions. It includes elements such as long and strong passwords, never reusing keys, leveraging password managers, avoiding personal information, etc. This Best Practices To Create Comprehensive Guide To Blockchain Digital Security Clipart Pdf from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. The following slide illustrates some tips to develop strong passwords to manage and ensure secure blockchain transactions. It includes elements such as long and strong passwords, never reusing keys, leveraging password managers, avoiding personal information, etc.
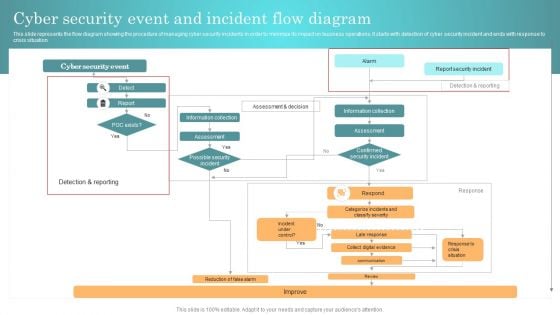
Incident Response Techniques Deployement Cyber Security Event And Incident Flow Diagram Structure PDF
This slide represents the flow diagram showing the procedure of managing cyber security incidents in order to minimize its impact on business operations. It starts with detection of cyber security incident and ends with response to crisis situation. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Incident Response Techniques Deployement Cyber Security Event And Incident Flow Diagram Structure PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Incident Response Techniques Deployement Cyber Security Event And Incident Flow Diagram Structure PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.


 Continue with Email
Continue with Email

 Home
Home


































