Security Management

Overview Of Website Security Check To Improve Efficiency Step By Step Guide Slides PDF
Following slide represents overview and benefits to conduct security test to assure website authenticity and eliminate potential threats. It further covers description, example, benefits such as simpler fixes, educate developers etc. Want to ace your presentation in front of a live audience Our Overview Of Website Security Check To Improve Efficiency Step By Step Guide Slides PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. Following slide represents overview and benefits to conduct security test to assure website authenticity and eliminate potential threats. It further covers description, example, benefits such as simpler fixes, educate developers etc.
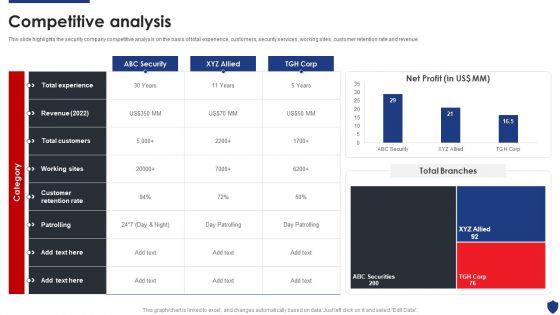
Security Officer Service Company Profile Competitive Analysis Ppt PowerPoint Presentation Gallery Rules PDF
This slide highlights the security company competitive analysis on the basis of total experience, customers, security services, working sites, customer retention rate and revenue. Deliver an awe inspiring pitch with this creative Security Officer Service Company Profile Competitive Analysis Ppt PowerPoint Presentation Gallery Rules PDF bundle. Topics like ABC Security, Total Experience, Total Customers can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
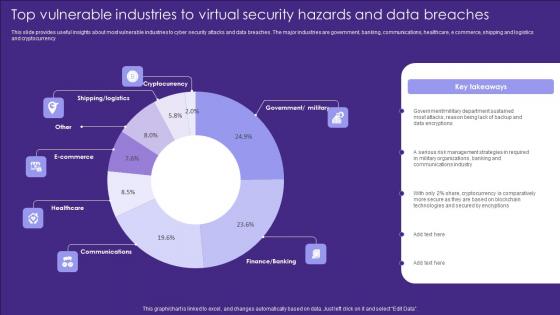
Top Vulnerable Industries To Virtual Security Hazards And Data Breaches Introduction Pdf
This slide provides useful insights about most vulnerable industries to cyber security attacks and data breaches. The major industries are government, banking, communications, healthcare, e commerce, shipping and logistics and cryptocurrency Pitch your topic with ease and precision using this Top Vulnerable Industries To Virtual Security Hazards And Data Breaches Introduction Pdf. This layout presents information on Cryptocurrency, Ecommerce, Healthcare. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide provides useful insights about most vulnerable industries to cyber security attacks and data breaches. The major industries are government, banking, communications, healthcare, e commerce, shipping and logistics and cryptocurrency

Types Of Website Security Threats And Vulnerabilities Step By Step Guide Structure PDF
Following slide exhibits types of security threats that negatively affect website operational efficiency and goodwill. It include types such as malware, viruses, spam links, DDoS with examples, impact and mitigation tools. There are so many reasons you need a Types Of Website Security Threats And Vulnerabilities Step By Step Guide Structure PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. Following slide exhibits types of security threats that negatively affect website operational efficiency and goodwill. It include types such as malware, viruses, spam links, DDoS with examples, impact and mitigation tools.
Addressing Food Processing Quality Standards Food Security Excellence Ppt Icon Example PDF
This slide provides information regarding the food processing quality standards that are defined in order to manage overall food quality. Deliver an awe inspiring pitch with this creative addressing food processing quality standards food security excellence ppt icon example pdf bundle. Topics like performance, effectiveness, dimensions compliance, parameters can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Manpower Corporate Security Business Profile Sales Revenue By Region And Services Icons PDF
This slide highlights the security company sales revenue by region and services. It showcases retail mall security, social event security, university hospital security, executive protection and building security. Deliver and pitch your topic in the best possible manner with this Manpower Corporate Security Business Profile Sales Revenue By Region And Services Icons PDF. Use them to share invaluable insights on Sales Revenue, Region And Services and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
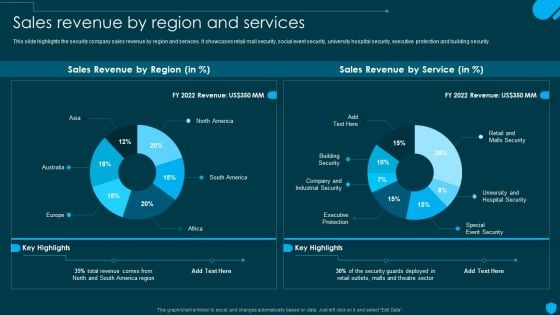
Security And Human Resource Services Business Profile Sales Revenue By Region Brochure PDF
This slide highlights the security company sales revenue by region and services. It showcases retail mall security, social event security, university hospital security, executive protection and building security. The Security And Human Resource Services Business Profile Sales Revenue By Region Brochure PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
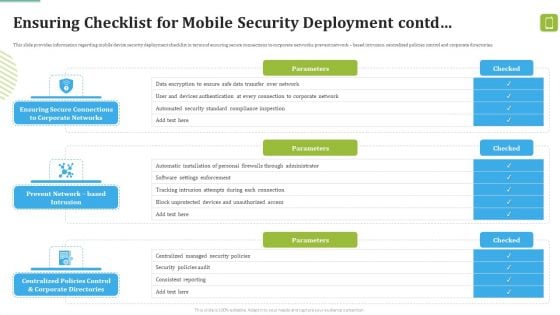
MDM Strategies At Office Ensuring Checklist For Mobile Security Deployment Contd Template PDF
This slide provides information regarding mobile device security deployment checklist in terms of device security, protection against malicious codes. Deliver and pitch your topic in the best possible manner with this MDM Strategies At Office Ensuring Checklist For Mobile Security Deployment Contd Template PDF. Use them to share invaluable insights on Against Malicious, Device Security, Automatic Configuration and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Top Rated Outdoor Security Lights In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Top Rated Outdoor Security Lights In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Top Rated Outdoor Security Lights that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Top Rated Outdoor Security Lights In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Security Access Control Iris Scanning System Ppt PowerPoint Presentation Show Gridlines
This is a security access control iris scanning system ppt powerpoint presentation show gridlines. This is a two stage process. The stages in this process are access rights, access management, business.
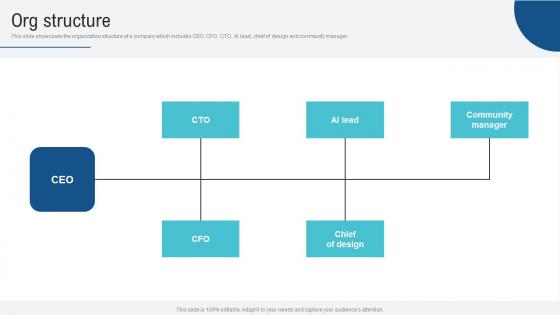
Org Structure Voice Assistance Security Platform Investor Funding Presentation Pictures Pdf
This slide showcases the organization structure of a company which includes CEO, CFO, CTO, AI lead, chief of design and community manager. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download Org Structure Voice Assistance Security Platform Investor Funding Presentation Pictures Pdf to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the Org Structure Voice Assistance Security Platform Investor Funding Presentation Pictures Pdf. This slide showcases the organization structure of a company which includes CEO, CFO, CTO, AI lead, chief of design and community manager.

IT Threats Response Playbook Addressing The Various Security Incidents And Attacks Brochure PDF
Purpose of this slide is to educate team members about different security incidents and attacks. It includes information about traditional security incidents, cyber security attacks and common techniques.This is a IT Threats Response Playbook Addressing The Various Security Incidents And Attacks Brochure PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security Incidents, Security Attacks, Common Techniques. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
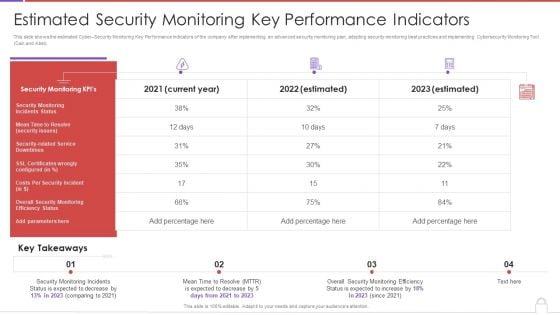
Methods To Develop Advanced Estimated Security Monitoring Key Performance Indicators Structure PDF
This slide shows the estimated Cyber Security Monitoring Key Performance Indicators of the company after implementing an advanced security monitoring plan, adopting security monitoring best practices and implementing Cybersecurity Monitoring Tool Cain and Abel. Deliver an awe inspiring pitch with this creative methods to develop advanced estimated security monitoring key performance indicators structure pdf bundle. Topics like security monitoring kpis, costs per security incident can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
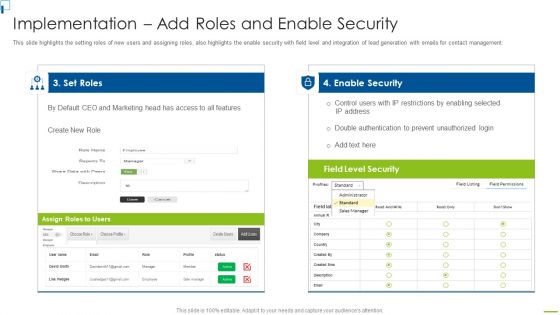
Designing And Deployment Implementation Add Roles And Enable Security Sample PDF
This slide highlights the setting roles of new users and assigning roles, also highlights the enable security with field level and integration of lead generation with emails for contact management. Deliver and pitch your topic in the best possible manner with this designing and deployment implementation add roles and enable security sample pdf. Use them to share invaluable insights on set roles, enable security, assign roles to users, field level security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Key Security Controls To Be Addressed In The Program Ppt Professional Vector PDF
Purpose of this slide is to provide information about key security controls that are to be addressed in companys information security program. Security controls covered are user application hardening, daily backups and patch applications. This is a key security controls to be addressed in the program ppt professional vector pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like key security controls to be addressed in the program. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Top Firewall As A Service Technology Trends Network Security Mockup Pdf
This slide outlines the top Firewall-as-a-Service trends. The purpose of this slide is to briefly explain the top current FWaaS trends. These include firewalls remain important, zero trust in the cloud, isolation of security from the underlying infrastructure, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Top Firewall As A Service Technology Trends Network Security Mockup Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Top Firewall As A Service Technology Trends Network Security Mockup Pdf today and make your presentation stand out from the rest This slide outlines the top Firewall-as-a-Service trends. The purpose of this slide is to briefly explain the top current FWaaS trends. These include firewalls remain important, zero trust in the cloud, isolation of security from the underlying infrastructure, etc.

Cloud Computing Security And Compliance Ppt Powerpoint Presentation File Graphic Tips
This is a cloud computing security and compliance ppt powerpoint presentation file graphic tips. This is a three stage process. The stages in this process are cloud computing, cloud management, cloud governance.

Employee Safety Program Workplace Safety Protocol And Security Practices Brochure Pdf
This slide showcases the assessment and improvement of safety program which includes monitoring performance, examining program and checking improvement opportunities. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Employee Safety Program Workplace Safety Protocol And Security Practices Brochure Pdf was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Employee Safety Program Workplace Safety Protocol And Security Practices Brochure Pdf This slide showcases the assessment and improvement of safety program which includes monitoring performance, examining program and checking improvement opportunities.
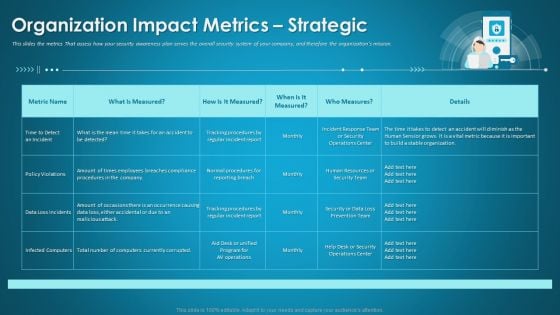
Organizational Network Security Awareness Staff Learning Organization Impact Metrics Strategic Structure PDF
This slides the metrics That assess how your security awareness plan serves the overall security system of your company, and therefore the organizations mission. Deliver and pitch your topic in the best possible manner with this organizational network security awareness staff learning organization impact metrics strategic structure pdf. Use them to share invaluable insights on human resources, security operations, organization and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Info Safety And ISO 27001 Performance Indicators To Measure Information Security Sample PDF
Following slide illustrates performance indicators for measuring information security controls. It includes controls details, performance indicator formula, target and periodicity. Deliver and pitch your topic in the best possible manner with this Info Safety And ISO 27001 Performance Indicators To Measure Information Security Sample PDF. Use them to share invaluable insights on Information Security Policy, Information Security Training, Asset Inventory and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Network Security Using Firewall As A Service Ppt PowerPoint Presentation Complete Deck With Slides
This Network Security Using Firewall As A Service Ppt PowerPoint Presentation Complete Deck With Slides is designed to help you retain your audiences attention. This content-ready PowerPoint Template enables you to take your audience on a journey and share information in a way that is easier to recall. It helps you highlight the crucial parts of your work so that the audience does not get saddled with information download. This eight three slide PPT Deck comes prepared with the graphs and charts you could need to showcase your information through visuals. You only need to enter your own data in them. Download this editable PowerPoint Theme and walk into that meeting with confidence. Our Network Security Using Firewall As A Service Ppt PowerPoint Presentation Complete Deck With Slides are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Cybersecurity Risk Administration Plan Setting Scenario For Security Control Topics PDF
Following slide displays security control scenario setting. It includes scenario detail, category of security controls and controls description.Presenting Cybersecurity Risk Administration Plan Setting Scenario For Security Control Topics PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Category Of Security Controls, Controls Description, Secured Firewall Configuration In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Optimization Of IoT Remote Monitoring Security System Used In Smart Homes For Protection IoT SS V
This slide provides an overview of the smart security systems used in houses to enhance safety. The slide includes components, types and features that are it allows access to authorized people, store data and provide protection against vulnerabilities. This Optimization Of IoT Remote Monitoring Security System Used In Smart Homes For Protection IoT SS V is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Optimization Of IoT Remote Monitoring Security System Used In Smart Homes For Protection IoT SS V features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide provides an overview of the smart security systems used in houses to enhance safety. The slide includes components, types and features that are it allows access to authorized people, store data and provide protection against vulnerabilities.

Zero Trust Model Features Of Zero Trust Network Access Security Model
This slide represents the main features of ZTNA. The purpose of this slide is to showcase the various features of zero trust network access, including safeguarding private apps, connecting security controls to apps more closely, restriction of access, recognizing internal app use, and so on. This modern and well-arranged Zero Trust Model Features Of Zero Trust Network Access Security Model provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide represents the main features of ZTNA. The purpose of this slide is to showcase the various features of zero trust network access, including safeguarding private apps, connecting security controls to apps more closely, restriction of access, recognizing internal app use, and so on.
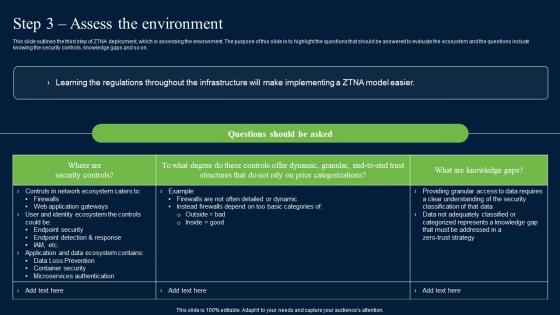
Step 3 Assess The Environment Zero Trust Network Security Brochure Pdf
This slide outlines the third step of ZTNA deployment, which is assessing the environment. The purpose of this slide is to highlight the questions that should be answered to evaluate the ecosystem and the questions include knowing the security controls, knowledge gaps and so on. Want to ace your presentation in front of a live audience Our Step 3 Assess The Environment Zero Trust Network Security Brochure Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide outlines the third step of ZTNA deployment, which is assessing the environment. The purpose of this slide is to highlight the questions that should be answered to evaluate the ecosystem and the questions include knowing the security controls, knowledge gaps and so on.
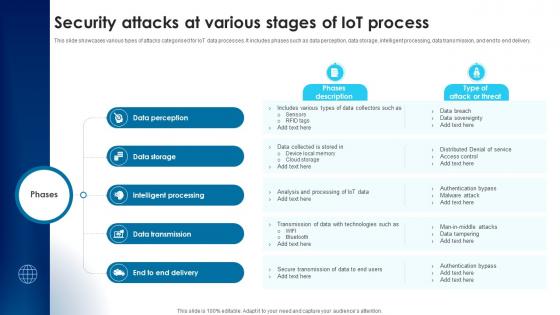
Building Trust With IoT Security Attacks At Various Stages Of IoT Process IoT SS V
This slide showcases various types of attacks categorised for IoT data processes. It includes phases such as data perception, data storage, intelligent processing, data transmission, and end to end delivery. Create an editable Building Trust With IoT Security Attacks At Various Stages Of IoT Process IoT SS V that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Building Trust With IoT Security Attacks At Various Stages Of IoT Process IoT SS V is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide showcases various types of attacks categorised for IoT data processes. It includes phases such as data perception, data storage, intelligent processing, data transmission, and end to end delivery.
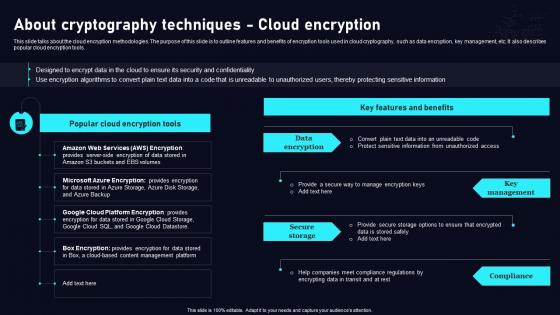
Cloud Data Security Using Cryptography About Cryptography Techniques Cloud Download Pdf
This slide talks about the cloud encryption methodologies. The purpose of this slide is to outline features and benefits of encryption tools used in cloud cryptography, such as data encryption, key management, etc. It also describes popular cloud encryption tools. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Cloud Data Security Using Cryptography About Cryptography Techniques Cloud Download Pdf was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Cloud Data Security Using Cryptography About Cryptography Techniques Cloud Download Pdf This slide talks about the cloud encryption methodologies. The purpose of this slide is to outline features and benefits of encryption tools used in cloud cryptography, such as data encryption, key management, etc. It also describes popular cloud encryption tools.
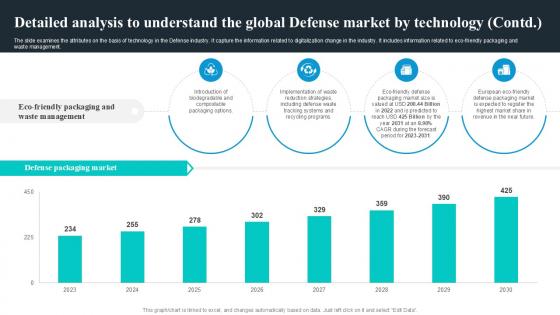
Detailed Analysis To Understand Global Security Industry PPT PowerPoint IR SS V
The slide examines the attributes on the basis of technology in the Defense industry. It capture the information related to digitalization change in the industry. It includes information related to eco-friendly packaging and waste management. Present like a pro with Detailed Analysis To Understand Global Security Industry PPT PowerPoint IR SS V. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. The slide examines the attributes on the basis of technology in the Defense industry. It capture the information related to digitalization change in the industry. It includes information related to eco-friendly packaging and waste management.
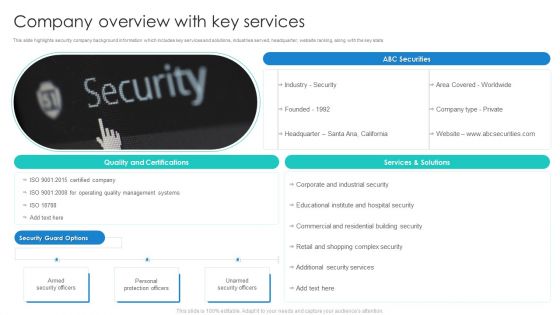
Manpower Corporate Security Business Profile Company Overview With Key Services Formats PDF
This slide highlights security company background information which includes key services and solutions, industries served, headquarter, website ranking, along with the key stats. Deliver an awe inspiring pitch with this creative Manpower Corporate Security Business Profile Company Overview With Key Services Formats PDF bundle. Topics like Armed Security Officer, Personal Protection Officers, Unarmed Security Officers can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Icons Slide For Building Trust With IoT Security And Privacy Measures IoT SS V
If you are looking for a format to display your unique thoughts, then the professionally designed Icons Slide For Building Trust With IoT Security And Privacy Measures IoT SS V is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Icons Slide For Building Trust With IoT Security And Privacy Measures IoT SS V and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. Our Icons Slide For Building Trust With IoT Security And Privacy Measures IoT SS V are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
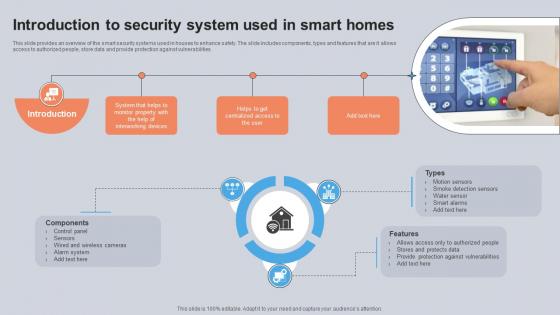
Introduction To Security System Used In Smart Homes Utilizing Smart Appliances IoT SS V
This slide provides an overview of the smart security systems used in houses to enhance safety. The slide includes components, types and features that are it allows access to authorized people, store data and provide protection against vulnerabilities. Create an editable Introduction To Security System Used In Smart Homes Utilizing Smart Appliances IoT SS V that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Introduction To Security System Used In Smart Homes Utilizing Smart Appliances IoT SS V is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide provides an overview of the smart security systems used in houses to enhance safety. The slide includes components, types and features that are it allows access to authorized people, store data and provide protection against vulnerabilities.

CIO Role In Digital Evolution Role Of Chief Information Security Officer Infographics PDF
This slide covers the role of chief information security officer which includes embed security information, stay informed, hire solid security staff, etc. Presenting CIO Role In Digital Evolution Role Of Chief Information Security Officer Infographics PDF to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like Dependable Business, Security Information, Team Members. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
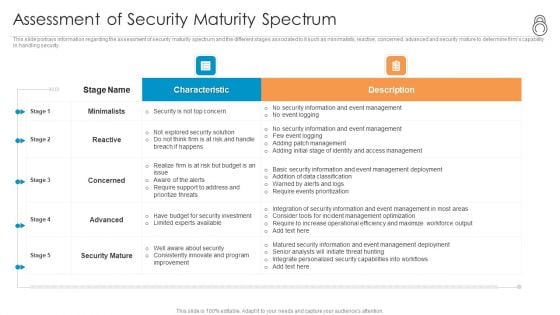
Enhanced Protection Corporate Event Administration Assessment Of Security Maturity Spectrum Background PDF
This slide portrays information regarding the assessment of security maturity spectrum and the different stages associated to it such as minimalists, reactive, concerned, advanced and security mature to determine firms capability in handling security. Deliver an awe inspiring pitch with this creative enhanced protection corporate event administration assessment of security maturity spectrum background pdf bundle. Topics like minimalists, reactive, concerned, advanced, security mature can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Emerging Trends In Cryptographic Data Security In Cloud Computing Ppt Powerpoint
This slide describes the cloud cryptography trends. The purpose of this slide is to highlight the emerging trends in the field of cloud encryption. These include homomorphic encryption, quantum-safe cryptography, secure multi-party computation, etc. Explore a selection of the finest Emerging Trends In Cryptographic Data Security In Cloud Computing Ppt Powerpoint here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Emerging Trends In Cryptographic Data Security In Cloud Computing Ppt Powerpoint to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide describes the cloud cryptography trends. The purpose of this slide is to highlight the emerging trends in the field of cloud encryption. These include homomorphic encryption, quantum-safe cryptography, secure multi-party computation, etc.

Information Technology Strategy Role Of Chief Information Security Officer Rules PDF
This slide covers the role of chief information security officer which includes embed security information, stay informed, hire solid security staff, etc. This is a information technology strategy role of chief information security officer rules pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security information, stay informed, monthly reports. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Industry Laws And Regulations In Global Security Industry PPT Slide IR SS V
The slide highlights industry laws and regulations in Defense industry. It is to ensure market stability, consumer protection and foster innovation while mitigating risks. It includes regulatory compliance and intellectual property, legal and regulatory. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Industry Laws And Regulations In Global Security Industry PPT Slide IR SS V template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Industry Laws And Regulations In Global Security Industry PPT Slide IR SS V that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers The slide highlights industry laws and regulations in Defense industry. It is to ensure market stability, consumer protection and foster innovation while mitigating risks. It includes regulatory compliance and intellectual property, legal and regulatory.

Workplace Safety Protocol And Security Practices Table Of Contents Themes Pdf
Slidegeeks is here to make your presentations a breeze with Workplace Safety Protocol And Security Practices Table Of Contents Themes Pdf With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first Our Workplace Safety Protocol And Security Practices Table Of Contents Themes Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Esteemed Clientele Voice Assistance Security Platform Investor Funding Presentation Ideas Pdf
The slide outlines clients served by an IT company that offers open source technologies to build platforms for voice powered applications. It highlights clients photo and the name of customer. This Esteemed Clientele Voice Assistance Security Platform Investor Funding Presentation Ideas Pdf is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Esteemed Clientele Voice Assistance Security Platform Investor Funding Presentation Ideas Pdf features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today The slide outlines clients served by an IT company that offers open source technologies to build platforms for voice powered applications. It highlights clients photo and the name of customer.

Future Of Digital Wallet Security And Safety In Depth Guide To Digital Wallets Fin SS V
This slide exhibits the future of digital wallet security using various technologies and regulations that help to promote the seamless working of online transactions. The major components are biometric authorization, government regulations, artificial intelligence, etc. Welcome to our selection of the Future Of Digital Wallet Security And Safety In Depth Guide To Digital Wallets Fin SS V. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. This slide exhibits the future of digital wallet security using various technologies and regulations that help to promote the seamless working of online transactions. The major components are biometric authorization, government regulations, artificial intelligence, etc.

Prevention Of Information How To Overcome The Security Awareness Training Introduction PDF
The purpose of this is to highlight various solutions which can be used to overcome the cyber security awareness challenges. The key solutions covered in the slide are introducing dynamic courses, fully managed training. If you are looking for a format to display your unique thoughts, then the professionally designed Prevention Of Information How To Overcome The Security Awareness Training Introduction PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Prevention Of Information How To Overcome The Security Awareness Training Introduction PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Implementing Cybersecurity Awareness Program To Prevent Attacks How To Overcome The Security Awareness Summary PDF
The purpose of this is to highlight various solutions which can be used to overcome the cyber security awareness challenges. The key solutions covered in the slide are introducing dynamic courses, fully managed training program, convenient program etc. If you are looking for a format to display your unique thoughts, then the professionally designed Implementing Cybersecurity Awareness Program To Prevent Attacks How To Overcome The Security Awareness Summary PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Implementing Cybersecurity Awareness Program To Prevent Attacks How To Overcome The Security Awareness Summary PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

How To Overcome The Security Awareness Training Program Challenges Infographics PDF
The purpose of this is to highlight various solutions which can be used to overcome the cyber security awareness challenges. The key solutions covered in the slide are introducing dynamic courses, fully managed training program, convenient program etc. Create an editable How To Overcome The Security Awareness Training Program Challenges Infographics PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. How To Overcome The Security Awareness Training Program Challenges Infographics PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Cryptographic Algorithms Used In Data Security In Cloud Computing Ppt Slide
This slide talks about algorithms used for implementing cryptography in data security. The purpose of this slide is to explain the different implementation steps. The techniques discussed are RSA Rivest, Shamir, Adleman cryptographic algorithm and Data Encryption Standard algorithm. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Cryptographic Algorithms Used In Data Security In Cloud Computing Ppt Slide was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Cryptographic Algorithms Used In Data Security In Cloud Computing Ppt Slide This slide talks about algorithms used for implementing cryptography in data security. The purpose of this slide is to explain the different implementation steps. The techniques discussed are RSA Rivest, Shamir, Adleman cryptographic algorithm and Data Encryption Standard algorithm.
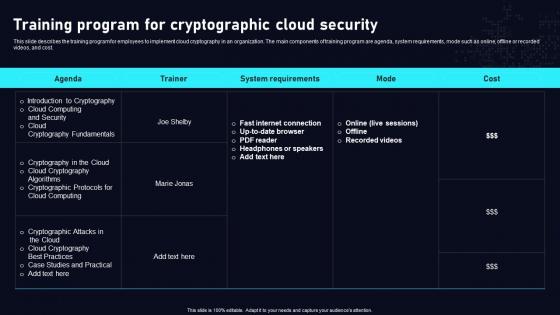
Training Program For Cryptographic Cloud Data Security Using Cryptography Sample Pdf
This slide describes the training program for employees to implement cloud cryptography in an organization. The main components of training program are agenda, system requirements, mode such as online, offline or recorded videos, and cost. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Training Program For Cryptographic Cloud Data Security Using Cryptography Sample Pdf template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Training Program For Cryptographic Cloud Data Security Using Cryptography Sample Pdf that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide describes the training program for employees to implement cloud cryptography in an organization. The main components of training program are agenda, system requirements, mode such as online, offline or recorded videos, and cost.
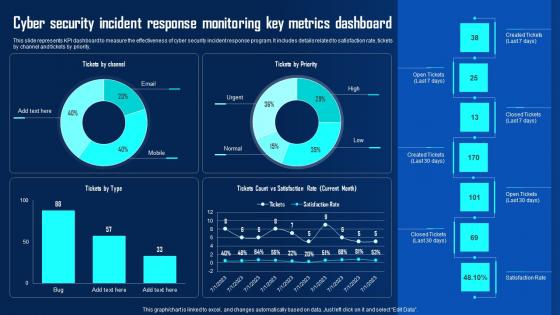
Cyber Security Incident Response Monitoring Key Ppt Powerpoint Presentation File Example File Pdf
This slide represents KPI dashboard to measure the effectiveness of cyber security incident response program. It includes details related to satisfaction rate, tickets by channel and tickets by priority. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Cyber Security Incident Response Monitoring Key Ppt Powerpoint Presentation File Example File Pdf was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Cyber Security Incident Response Monitoring Key Ppt Powerpoint Presentation File Example File Pdf This slide represents KPI dashboard to measure the effectiveness of cyber security incident response program. It includes details related to satisfaction rate, tickets by channel and tickets by priority.
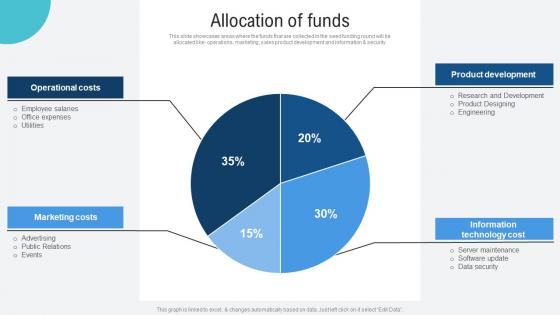
Allocation Of Funds Voice Assistance Security Platform Investor Funding Presentation Professional Pdf
This slide showcases areas where the funds that are collected in the seed funding round will be allocated like operations, marketing, sales product development and information and security. If you are looking for a format to display your unique thoughts, then the professionally designed Allocation Of Funds Voice Assistance Security Platform Investor Funding Presentation Professional Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Allocation Of Funds Voice Assistance Security Platform Investor Funding Presentation Professional Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide showcases areas where the funds that are collected in the seed funding round will be allocated like operations, marketing, sales product development and information and security.

Overview Need For Implementing Data Security Across Optimizing Retail Operations With Digital DT SS V
This slide analyses the need of implementing data security initiatives to address key customer data challenges in retail industry. It also mentions types of customer data collected such as account, location, browsing, and profile.Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Overview Need For Implementing Data Security Across Optimizing Retail Operations With Digital DT SS V was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Overview Need For Implementing Data Security Across Optimizing Retail Operations With Digital DT SS V. This slide analyses the need of implementing data security initiatives to address key customer data challenges in retail industry. It also mentions types of customer data collected such as account, location, browsing, and profile.
Security Systems Smart Grid Training Ppt PowerPoint Presentation Visual Aids Example File
This is a security systems smart grid training ppt powerpoint presentation visual aids example file. This is a ten stage process. The stages in this process are security systems, smart grid training.
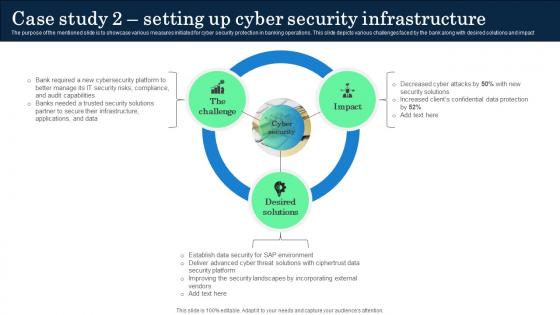
Case Study 2 Setting Up Cyber Security Infrastructure Incorporating Banking Operational Growth
The purpose of the mentioned slide is to showcase various measures initiated for cyber security protection in banking operations. This slide depicts various challenges faced by the bank along with desired solutions and impact. Present like a pro with Case Study 2 Setting Up Cyber Security Infrastructure Incorporating Banking Operational Growth. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. The purpose of the mentioned slide is to showcase various measures initiated for cyber security protection in banking operations. This slide depicts various challenges faced by the bank along with desired solutions and impact

Intelligent Architecture Growing Cyber Security Issues Ppt Professional Design Templates PDF
The slide provides the major cyber security issues Unprecedented Attacks, Cyber Espionage, and Data Theft along with the split of total information security incidents by the type of incident Deliver an awe inspiring pitch with this creative intelligent architecture growing cyber security issues ppt professional design templates pdf bundle. Topics like organizations, cyber security, business can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Organizational Network Security Awareness Staff Learning Table Of Contents Introduction PDF
Deliver and pitch your topic in the best possible manner with this organizational network security awareness staff learning table of contents introduction pdf. Use them to share invaluable insights on security awareness training, organization impact metrics, security awareness, communication plan, budget and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
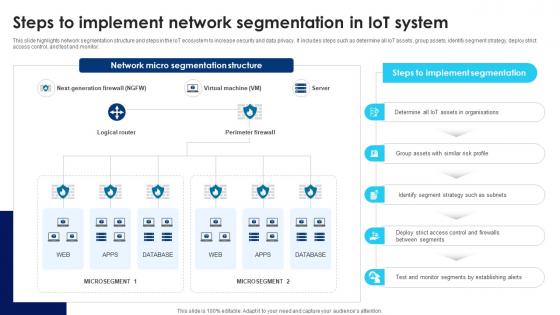
Building Trust With IoT Security Steps To Implement Network Segmentation In IoT System IoT SS V
This slide highlights network segmentation structure and steps in the IoT ecosystem to increase security and data privacy. It includes steps such as determine all IoT assets, group assets, identify segment strategy, deploy strict access control, and test and monitor. Slidegeeks is here to make your presentations a breeze with Building Trust With IoT Security Steps To Implement Network Segmentation In IoT System IoT SS V With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide highlights network segmentation structure and steps in the IoT ecosystem to increase security and data privacy. It includes steps such as determine all IoT assets, group assets, identify segment strategy, deploy strict access control, and test and monitor.
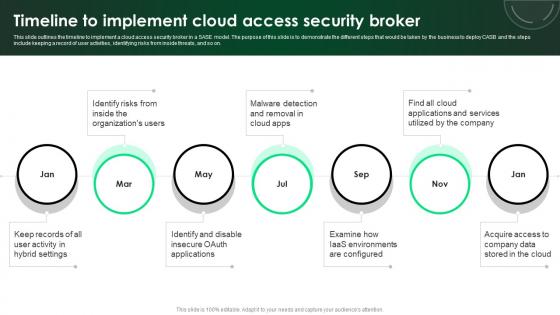
CASB 2 0 IT Timeline To Implement Cloud Access Security Broker
This slide outlines the timeline to implement a cloud access security broker in a SASE model. The purpose of this slide is to demonstrate the different steps that would be taken by the business to deploy CASB and the steps include keeping a record of user activities, identifying risks from inside threats, and so on. Make sure to capture your audiences attention in your business displays with our gratis customizable CASB 2 0 IT Timeline To Implement Cloud Access Security Broker. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide outlines the timeline to implement a cloud access security broker in a SASE model. The purpose of this slide is to demonstrate the different steps that would be taken by the business to deploy CASB and the steps include keeping a record of user activities, identifying risks from inside threats, and so on.

Overview Need For Implementing Data Security Across Retail DT SS V
This slide analyses the need of implementing data security initiatives to address key customer data challenges in retail industry. It also mentions types of customer data collected such as account, location, browsing, and profile.Make sure to capture your audiences attention in your business displays with our gratis customizable Overview Need For Implementing Data Security Across Retail DT SS V. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide analyses the need of implementing data security initiatives to address key customer data challenges in retail industry. It also mentions types of customer data collected such as account, location, browsing, and profile.

Cryptographic Algorithms Used In Cloud Data Security Using Cryptography Themes Pdf
This slide talks about algorithms used for implementing cryptography in data security. The purpose of this slide is to explain the different implementation steps. The techniques discussed are RSA Rivest, Shamir, Adleman cryptographic algorithm and Data Encryption Standard algorithm. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Cryptographic Algorithms Used In Cloud Data Security Using Cryptography Themes Pdf from Slidegeeks and deliver a wonderful presentation. This slide talks about algorithms used for implementing cryptography in data security. The purpose of this slide is to explain the different implementation steps. The techniques discussed are RSA Rivest, Shamir, Adleman cryptographic algorithm and Data Encryption Standard algorithm.

Mastering Blockchain Wallets Best Security Tips For Crypto Hardware Wallets BCT SS V
This slide covers best practices to increase security of hardware wallets. The purpose of this template is to provide an overview on recommendations for making wallets secure with practices such as never using or buying used wallets, buying from authorized dealers, setting a strong and unique pincode, etc. Present like a pro with Mastering Blockchain Wallets Best Security Tips For Crypto Hardware Wallets BCT SS V. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide covers best practices to increase security of hardware wallets. The purpose of this template is to provide an overview on recommendations for making wallets secure with practices such as never using or buying used wallets, buying from authorized dealers, setting a strong and unique pincode, etc.
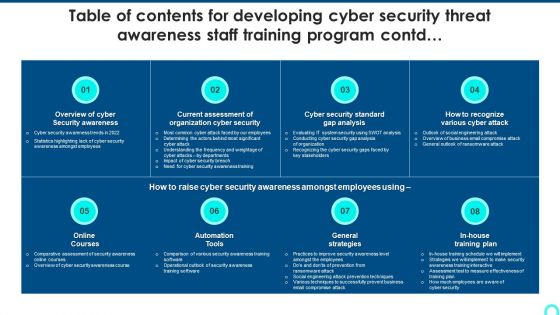
Table Of Contents For Developing Cyber Security Threat Awareness Staff Training Program Contd Topics PDF
Deliver an awe inspiring pitch with this creative Table Of Contents For Developing Cyber Security Threat Awareness Staff Training Program Contd Topics PDF bundle. Topics like Security Awareness, Current Assessment, Security Standard can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Email Security Market Research Report Industry Trends Ppt Infographics Styles PDF
Presenting this set of slides with name email security market research report industry trends ppt infographics styles pdf. This is a six stage process. The stages in this process are balance between risk and resilience, supply chain security, security adaptive approach. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Global Cloud Based Email Security Market Industry Trends Ppt Professional Example PDF
Presenting this set of slides with name global cloud based email security market industry trends ppt professional example pdf. This is a six stage process. The stages in this process are balance between risk and resilience, supply chain security, security adaptive approach. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
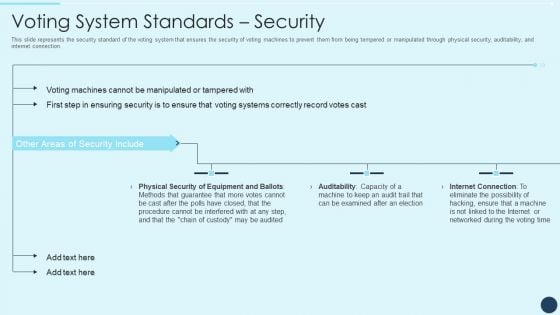
Electoral Mechanism IT Voting System Standards Security Ppt Professional Sample PDF
This slide represents the security standard of the voting system that ensures the security of voting machines to prevent them from being tempered or manipulated through physical security, auditability, and internet connection. Deliver an awe inspiring pitch with this creative electoral mechanism it voting system standards security ppt professional sample pdf bundle. Topics like physical security of equipment and ballots, auditability, internet connection can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.


 Continue with Email
Continue with Email

 Home
Home


































