Security Management
Project Security Administration IT 30 60 90 Days Plan Ideas PDF
This is a project security administration it 30 60 90 days plan ideas pdf template with various stages. Focus and dispense information on threestages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like 30 60 90 days plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Table Of Contents Fordeploying Cyber Security Incident Response Administration Structure PDF
If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Table Of Contents Fordeploying Cyber Security Incident Response Administration Structure PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.
Development And Integration Of Cyber Security Incident Administration Table Of Contents Diagrams PDF
Want to ace your presentation in front of a live audience Our Development And Integration Of Cyber Security Incident Administration Table Of Contents Diagrams PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.

Table Of Contents Development And Integration Of Cyber Security Incident Administration Portrait PDF
If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Table Of Contents Development And Integration Of Cyber Security Incident Administration Portrait PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates
Operational Safety Guidelines Air Workplace Safety Protocol And Security Practices Icons Pdf
This slides highlights the operational safety guidelines to minimize air compressor hazards. It showcases different protective gears with pre operation, operation and post operation. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download Operational Safety Guidelines Air Workplace Safety Protocol And Security Practices Icons Pdf to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the Operational Safety Guidelines Air Workplace Safety Protocol And Security Practices Icons Pdf. This slides highlights the operational safety guidelines to minimize air compressor hazards. It showcases different protective gears with pre operation, operation and post operation.
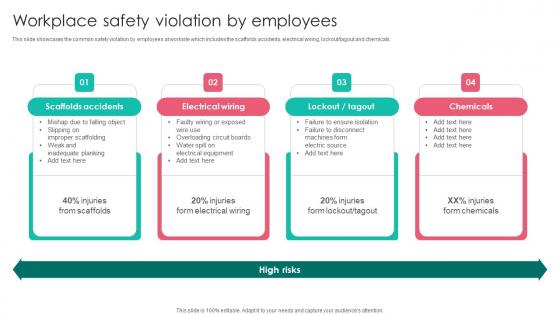
Workplace Safety Violation By Employees Workplace Safety Protocol And Security Practices Demonstration Pdf
This slide showcases the common safety violation by employees at worksite which includes the scaffolds accidents, electrical wiring, lockout tagout and chemicals. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Workplace Safety Violation By Employees Workplace Safety Protocol And Security Practices Demonstration Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Workplace Safety Violation By Employees Workplace Safety Protocol And Security Practices Demonstration Pdf today and make your presentation stand out from the rest This slide showcases the common safety violation by employees at worksite which includes the scaffolds accidents, electrical wiring, lockout tagout and chemicals.
Develop Corporate Cyber Security Risk Mitigation Plan Our Expertise For Organization Cyber Protection Services Background PDF
Presenting develop corporate cyber security risk mitigation plan our expertise for organization cyber protection services background pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like mobile app development, onsite developer, business intelligence analytic. In addtion, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.

Conduct Inspection Examine Poor Workplace Safety Protocol And Security Practices Elements Pdf
This slide highlights the poor work practices at worksites which showcases defective tools usage, improper lifting, high load at extension cords with general principal for inspections. Find highly impressive Conduct Inspection Examine Poor Workplace Safety Protocol And Security Practices Elements Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Conduct Inspection Examine Poor Workplace Safety Protocol And Security Practices Elements Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide highlights the poor work practices at worksites which showcases defective tools usage, improper lifting, high load at extension cords with general principal for inspections.

Safety Guidelines Handling Power Workplace Safety Protocol And Security Practices Guidelines Pdf
This slide highlights the safety guidelines which showcases the general precautions while handling power tools to prevent accidents. It also highlights on different personal protective equipment while using tools Create an editable Safety Guidelines Handling Power Workplace Safety Protocol And Security Practices Guidelines Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Safety Guidelines Handling Power Workplace Safety Protocol And Security Practices Guidelines Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide highlights the safety guidelines which showcases the general precautions while handling power tools to prevent accidents. It also highlights on different personal protective equipment while using tools
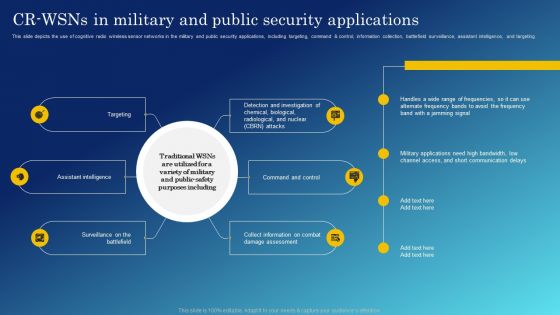
Cognitive Sensing Innovation CR Wsns In Military And Public Security Applications Inspiration PDF

Cyber Security Administration In Organization Workplace Incident Summary Report Brochure PDF
This slide can be utilized to report any workplace incident. After filling this form it will be forwarded to Business unit safety director and HR representative. This is a cyber security administration in organization workplace incident summary report brochure pdf template with various stages. Focus and dispense information on eigt stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like incident, employees, location, emergency, assistance. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Worker Participation To Eliminate Safety Workplace Safety Protocol And Security Practices Icons Pdf
This slide highlights the worker participation to remove safety risks which includes motivate workers for participation, report safety concerns, provide information access to workers and eliminate participation barrier. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Worker Participation To Eliminate Safety Workplace Safety Protocol And Security Practices Icons Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Worker Participation To Eliminate Safety Workplace Safety Protocol And Security Practices Icons Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide highlights the worker participation to remove safety risks which includes motivate workers for participation, report safety concerns, provide information access to workers and eliminate participation barrier.
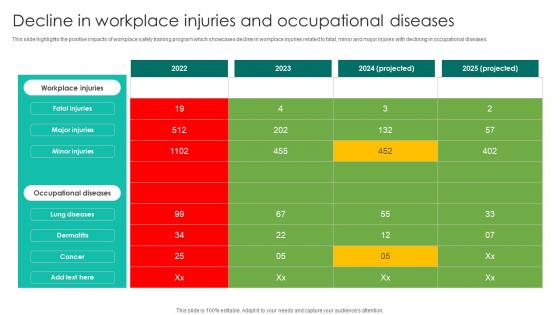
Decline In Workplace Injuries Workplace Safety Protocol And Security Practices Diagrams Pdf
This slide highlights the positive impacts of workplace safety training program which showcases decline in workplace injuries related to fatal, minor and major injures with declining in occupational diseases. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Decline In Workplace Injuries Workplace Safety Protocol And Security Practices Diagrams Pdf template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Decline In Workplace Injuries Workplace Safety Protocol And Security Practices Diagrams Pdf that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide highlights the positive impacts of workplace safety training program which showcases decline in workplace injuries related to fatal, minor and major injures with declining in occupational diseases.

Most Common Air Compressor Workplace Safety Protocol And Security Practices Microsoft Pdf
This slide highlights the common air compressor hazards which includes electrical dangers, fumes from diesel air compressor, high pressure injection and high noise form air compressor Are you searching for a Most Common Air Compressor Workplace Safety Protocol And Security Practices Microsoft Pdf that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Most Common Air Compressor Workplace Safety Protocol And Security Practices Microsoft Pdf from Slidegeeks today. This slide highlights the common air compressor hazards which includes electrical dangers, fumes from diesel air compressor, high pressure injection and high noise form air compressor
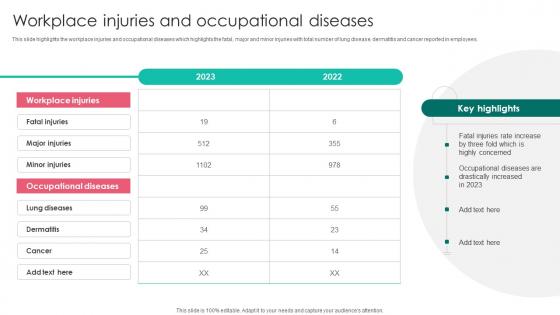
Workplace Injuries And Occupational Workplace Safety Protocol And Security Practices Download Pdf
This slide highlights the workplace injuries and occupational diseases which highlights the fatal, major and minor injuries with total number of lung disease, dermatitis and cancer reported in employees. Get a simple yet stunning designed Workplace Injuries And Occupational Workplace Safety Protocol And Security Practices Download Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Workplace Injuries And Occupational Workplace Safety Protocol And Security Practices Download Pdf can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide highlights the workplace injuries and occupational diseases which highlights the fatal, major and minor injuries with total number of lung disease, dermatitis and cancer reported in employees.
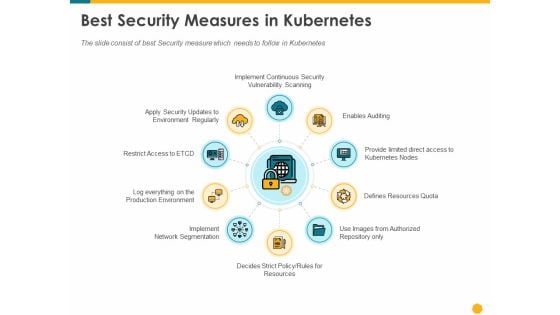
Deploying Docker Container And Kubernetes Within Organization Best Security Measures In Kubernetes Ppt PowerPoint Presentation PDF
Presenting this set of slides with name deploying docker container and kubernetes within organization best security measures in kubernetes ppt powerpoint presentation pdf. This is a ten stage process. The stages in this process are enables auditing provide limited direct access kubernetes nodes, resources quota, authorized repository, rules resources, implement, network segmentation, log everything production environment, restrict access to etcd. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
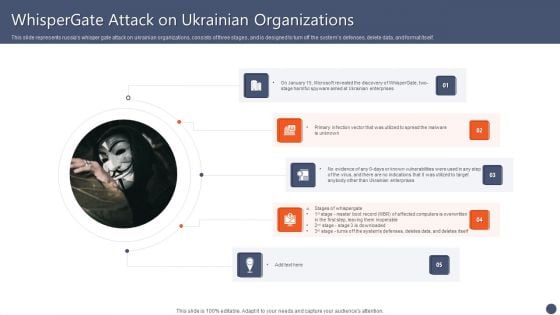
Series Of Cyber Security Attacks Against Ukraine 2022 Whispergate Attack On Ukrainian Organizations Information PDF
This slide represents russias whisper gate attack on ukrainian organizations, consists of three stages, and is designed to turn off the systems defenses, delete data, and format itself. Are you searching for a Series Of Cyber Security Attacks Against Ukraine 2022 Whispergate Attack On Ukrainian Organizations Information PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Series Of Cyber Security Attacks Against Ukraine 2022 Whispergate Attack On Ukrainian Organizations Information PDF from Slidegeeks today.
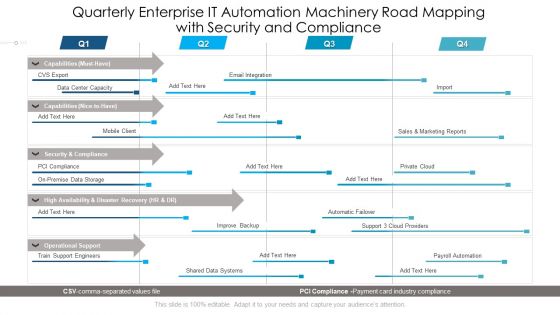
Quarterly Enterprise IT Automation Machinery Road Mapping With Security And Compliance Diagrams
Presenting our innovatively structured quarterly enterprise it automation machinery road mapping with security and compliance diagrams Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.
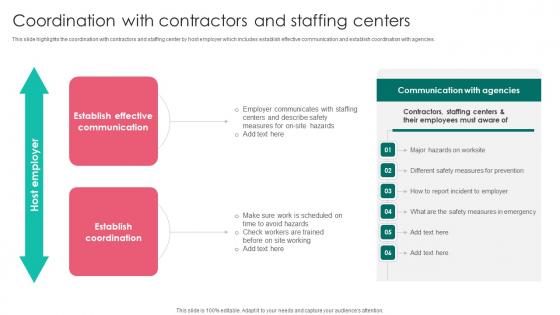
Coordination With Contractors Workplace Safety Protocol And Security Practices Ideas Pdf
This slide highlights the coordination with contractors and staffing center by host employer which includes establish effective communication and establish coordination with agencies. If you are looking for a format to display your unique thoughts, then the professionally designed Coordination With Contractors Workplace Safety Protocol And Security Practices Ideas Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Coordination With Contractors Workplace Safety Protocol And Security Practices Ideas Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide highlights the coordination with contractors and staffing center by host employer which includes establish effective communication and establish coordination with agencies.
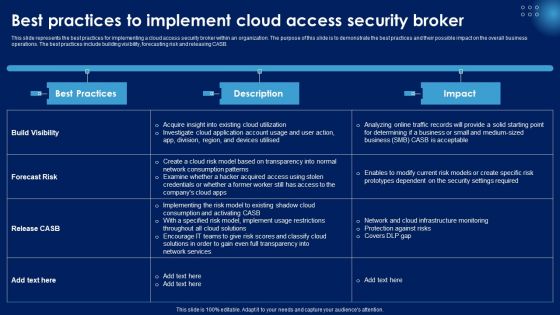
Best Practices To Implement Cloud Access Security Broker Ppt PowerPoint Presentation File Gallery PDF
This slide represents the best practices for implementing a cloud access security broker within an organization. The purpose of this slide is to demonstrate the best practices and their possible impact on the overall business operations. The best practices include building visibility, forecasting risk and releasing CASB. This Best Practices To Implement Cloud Access Security Broker Ppt PowerPoint Presentation File Gallery PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
Project Security Administration IT Determine Phases Of Threat Attack Disrupting Project Safety Contd Icons PDF
This slide provides information regarding various phases for threat attack disrupting IT project safety in terms of installation, command and control, actions and objectives, covering tracks. Presenting project security administration it determine phases of threat attack disrupting project safety contd icons pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like installation, command and control, actions and objectives, covering tracks. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
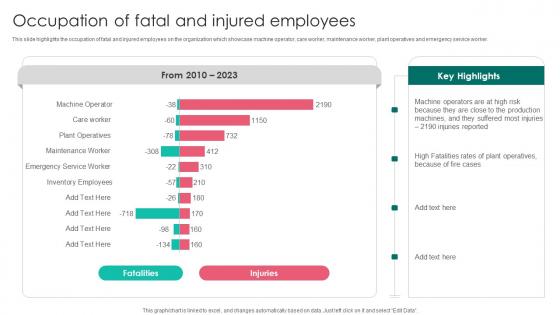
Occupation Of Fatal And Injured Workplace Safety Protocol And Security Practices Inspiration Pdf
This slide highlights the occupation of fatal and injured employees on the organization which showcase machine operator, care worker, maintenance worker, plant operatives and emergency service worker. Presenting this PowerPoint presentation, titled Occupation Of Fatal And Injured Workplace Safety Protocol And Security Practices Inspiration Pdf, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Occupation Of Fatal And Injured Workplace Safety Protocol And Security Practices Inspiration Pdf. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Occupation Of Fatal And Injured Workplace Safety Protocol And Security Practices Inspiration Pdf that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide highlights the occupation of fatal and injured employees on the organization which showcase machine operator, care worker, maintenance worker, plant operatives and emergency service worker.

Cyber Security Administration In Organization Evaluating Financial Practices In Firm Rules PDF
The firm can track the financial performance by looking the financial practices it follows in order to avoid any early signs of financial distress. Presenting cyber security administration in organization evaluating financial practices in firm rules pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like evaluating financial practices in firm. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Identifying Information Security Threats And Impact On Organization Cybersecurity Risk Assessment Formats PDF
This slide showcases various threats that can be faced by organization and can result in financial plus reputational loss. It also showcases impact of threats on operational capability of organization. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Identifying Information Security Threats And Impact On Organization Cybersecurity Risk Assessment Formats PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Identifying Information Security Threats And Impact On Organization Cybersecurity Risk Assessment Formats PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
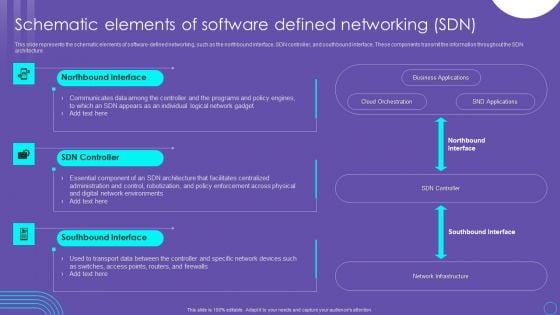
SDN Security Architecture Schematic Elements Of Software Defined Networking SDN Pictures PDF
This slide represents the schematic elements of software defined networking, such as the northbound interface, SDN controller, and southbound interface. These components transmit the information throughout the SDN architecture. Create an editable SDN Security Architecture Schematic Elements Of Software Defined Networking SDN Pictures PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. SDN Security Architecture Schematic Elements Of Software Defined Networking SDN Pictures PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
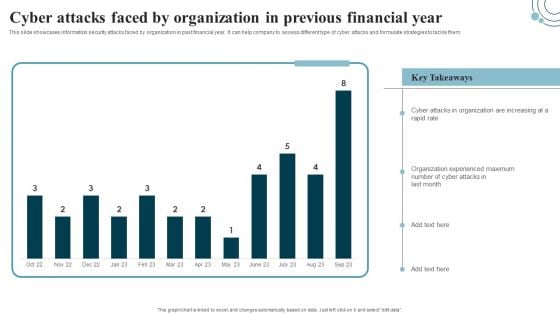
Developing IT Security Strategy Cyber Attacks Faced By Organization In Previous Summary PDF
This slide showcases information security attacks faced by organization in past financial year. It can help company to assess different type of cyber attacks and formulate strategies to tackle them. Retrieve professionally designed Developing IT Security Strategy Cyber Attacks Faced By Organization In Previous Summary PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
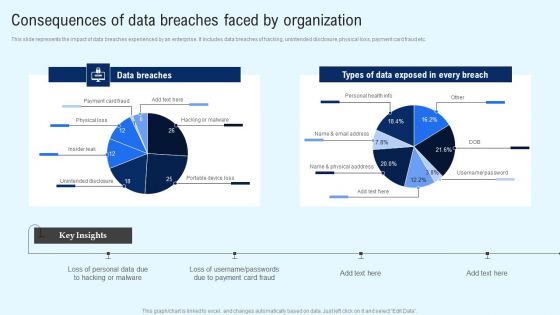
Implementing Cyber Security Incident Consequences Of Data Breaches Faced By Organization Infographics PDF
This slide represents the impact of data breaches experienced by an enterprise. It includes data breaches of hacking, unintended disclosure, physical loss, payment card fraud etc. Create an editable Implementing Cyber Security Incident Consequences Of Data Breaches Faced By Organization Infographics PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre designed presentation templates help save time. Implementing Cyber Security Incident Consequences Of Data Breaches Faced By Organization Infographics PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
Information Security Define Access Control Measures For Employees Ppt Icon Pictures PDF
This slide represents how it is essential to minimize the rights or access of employees in an organization to keep data safe and prevent it from deletion, manipulation. This is a information security define access control measures for employees ppt icon pictures pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like networks, organization. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Auditing Committees For Food Quality Review Food Security Excellence Ppt Summary Example Topics PDF
This slide provides information regarding the different committees such as steering committees, general assembly meet, will review overall quality. Deliver an awe inspiring pitch with this creative auditing committees for food quality review food security excellence ppt summary example topics pdf bundle. Topics like acceptance criteria, quality audit review, corrective actions, quality document control, prepared quality control can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Information Technology Security Define Access Control Measures For Employees Ppt Professional Design Templates PDF
This slide represents how it is essential to minimize the rights access of employees in an organization to keep data safe and prevent it from deletion, manipulation. This is a information technology security define access control measures for employees ppt professional design templates pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like staff duties, organization, roles, access, permissions. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
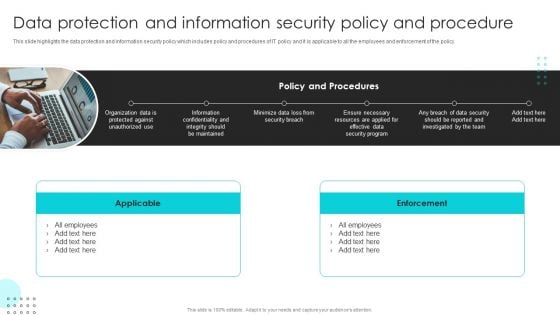
Company Rules And Regulations Manual Data Protection And Information Security Policy And Procedure Download PDF
This slide highlights the data protection and information security policy which includes policy and procedures of IT policy and it is applicable to all the employees and enforcement of the policy. Slidegeeks is here to make your presentations a breeze with Company Rules And Regulations Manual Data Protection And Information Security Policy And Procedure Download PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Table Of Contents For Organizing Security Awareness Training To Minimize Downtime Themes PDF
Boost your pitch with our creative Table Of Contents For Organizing Security Awareness Training To Minimize Downtime Themes PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you dont have to invest time in any additional work. Just grab the template now and use them.
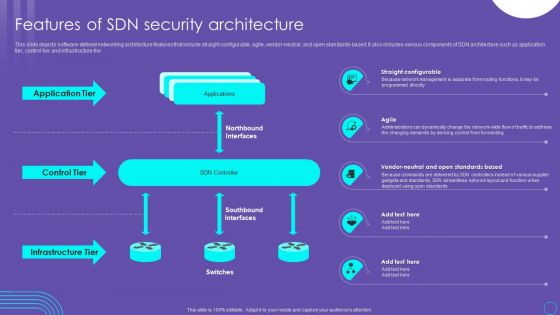
Features Of SDN Security Architecture Ppt PowerPoint Presentation File Ideas PDF
This slide depicts software defined networking architecture features that include straight configurable, agile, vendor neutral, and open standards based. It also includes various components of SDN architecture such as application tier, control tier and infrastructure tier. Find highly impressive Features Of SDN Security Architecture Ppt PowerPoint Presentation File Ideas PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Features Of SDN Security Architecture Ppt PowerPoint Presentation File Ideas PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now
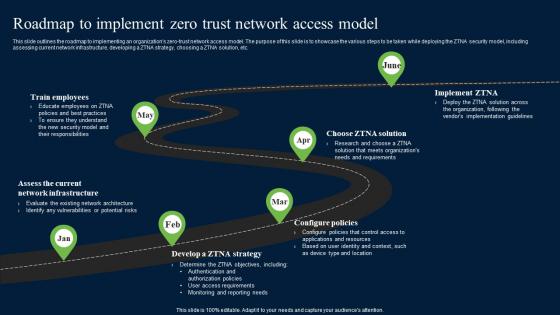
Roadmap To Implement Zero Trust Network Access Model Zero Trust Network Security Graphics Pdf
This slide outlines the roadmap to implementing an organizations zero-trust network access model. The purpose of this slide is to showcase the various steps to be taken while deploying the ZTNA security model, including assessing current network infrastructure, developing a ZTNA strategy, choosing a ZTNA solution, etc. This Roadmap To Implement Zero Trust Network Access Model Zero Trust Network Security Graphics Pdf from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide outlines the roadmap to implementing an organizations zero-trust network access model. The purpose of this slide is to showcase the various steps to be taken while deploying the ZTNA security model, including assessing current network infrastructure, developing a ZTNA strategy, choosing a ZTNA solution, etc.

Workforce Security Realization Coaching Plan Idea Generation Ppt Infographics Display PDF
This is a workforce security realization coaching plan idea generation ppt infographics display pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like idea generation. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Workforce Security Realization Coaching Plan Post It Notes Ppt Slides Graphics Template PDF
This is a workforce security realization coaching plan post it notes ppt slides graphics template pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like post it notes. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
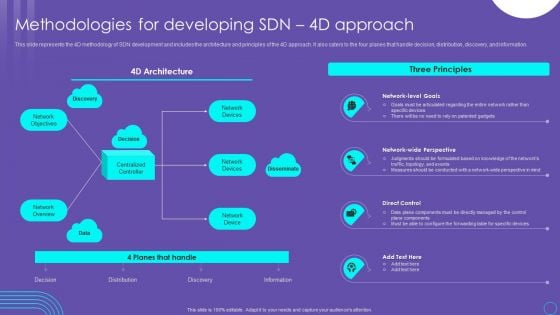
SDN Security Architecture Methodologies For Developing SDN 4D Approach Download PDF
This slide represents the 4D methodology of SDN development and includes the architecture and principles of the 4D approach. It also caters to the four planes that handle decision, distribution, discovery, and information. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download SDN Security Architecture Methodologies For Developing SDN 4D Approach Download PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the SDN Security Architecture Methodologies For Developing SDN 4D Approach Download PDF.

Implementing Cybersecurity Awareness Program To Prevent Attacks Security Awareness Training Program Challenges Introduction PDF
The purpose of this slide is to exhibit biggest cyber security awareness challenges which is faced by the organization. Outdated content, burden on administrators, low employee participation rate and employees losing interest are some of the key challenges which are highlighted in the slide. Want to ace your presentation in front of a live audience Our Implementing Cybersecurity Awareness Program To Prevent Attacks Security Awareness Training Program Challenges Introduction PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.
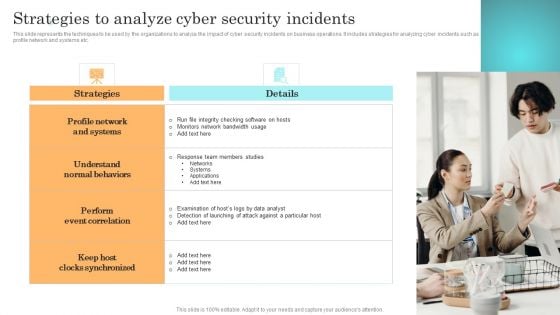
Incident Response Techniques Deployement Strategies To Analyze Cyber Security Incidents Sample PDF
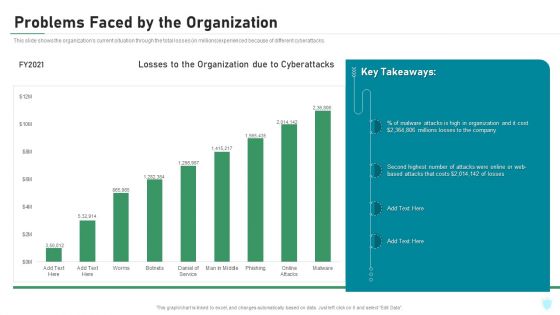
Problems Faced By The Organization IT Security IT Ppt Infographics Graphics PDF
This slide shows the organizations current situation through the total losses in millions experienced because of different cyberattacks. Deliver and pitch your topic in the best possible manner with this problems faced by the organization it security it ppt infographics graphics pdf. Use them to share invaluable insights on problems faced by the organization and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
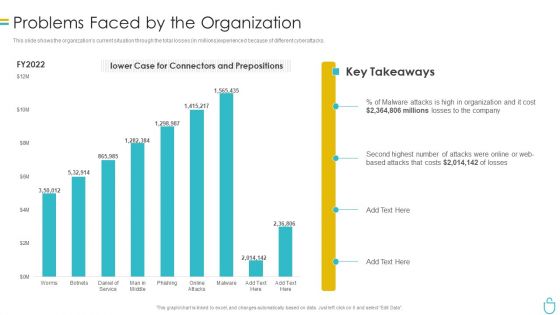
Information Security Problems Faced By The Organization Ppt Layouts Images PDF
This slide shows the organizations current situation through the total losses in millions experienced because of different cyberattacks. Deliver and pitch your topic in the best possible manner with this information security problems faced by the organization ppt layouts images pdf. Use them to share invaluable insights on organization, cost and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Information Technology Security Problems Faced By The Organization Ppt Ideas Visuals PDF
This slide shows the organizations current situation through the total losses ins millionsexperienced because of different cyberattacks. Deliver an awe inspiring pitch with this creative information technology security problems faced by the organization ppt ideas visuals pdf bundle. Topics like problems faced by the organization can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

IT Security Problems Faced By The Organization Ppt Model Professional PDF
This slide shows the organizations current situation through the total losses in millionsexperienced because of different cyberattacks. Deliver and pitch your topic in the best possible manner with this it security problems faced by the organization ppt model professional pdf. Use them to share invaluable insights on problems faced by the organization and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
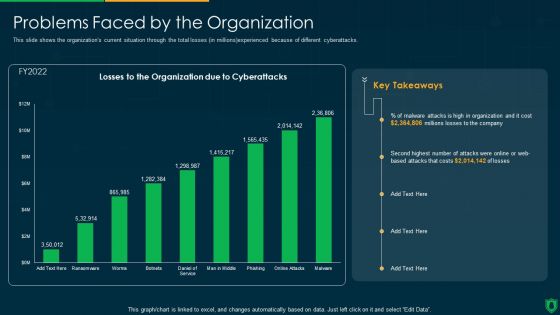
Info Security Problems Faced By The Organization Ppt PowerPoint Presentation File Slide PDF
This slide shows the organizations current situation through the total losses in millions experienced because of different cyberattacks. Deliver and pitch your topic in the best possible manner with this info security problems faced by the organization ppt powerpoint presentation file slide pdf. Use them to share invaluable insights on losses organization, due cyberattacks, cost and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
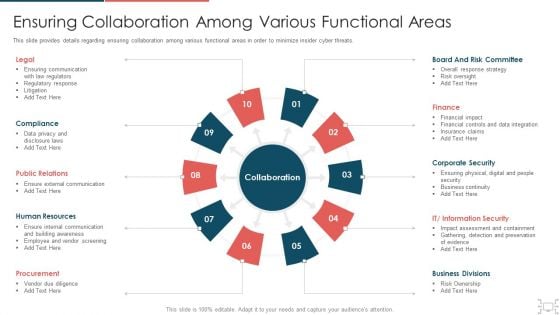
cyber security administration in organization ensuring collaboration among various functional areas brochure pdf
This slide provides details regarding ensuring collaboration among various functional areas in order to minimize insider cyber threats. Presenting cyber security administration in organization ensuring collaboration among various functional areas brochure pdf to provide visual cues and insights. Share and navigate important information on ten stages that need your due attention. This template can be used to pitch topics like communication, compliance, relations, resources, procurement . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
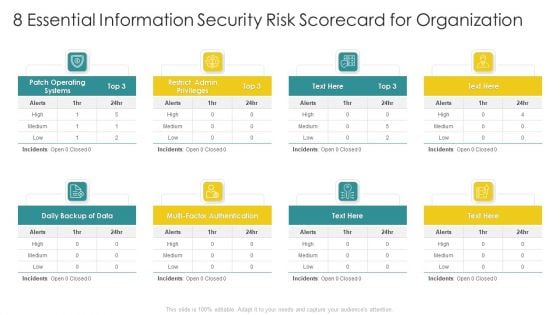
Cybersecurity Risk Scorecard 8 Essential Information Security Risk Scorecard For Organization Elements PDF
Presenting cybersecurity risk scorecard 8 essential information security risk scorecard for organization elements pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like 30 60 90 days plan. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Info Security Define Access Control Measures For Employees Ppt PowerPoint Presentation Gallery Icon PDF
This slide represents how it is essential to minimize the rights or access of employees in an organization to keep data safe and prevent it from deletion, manipulation. Presenting info security define access control measures for employees ppt powerpoint presentation gallery icon pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like access data, personnel according, duties or roles, organization. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
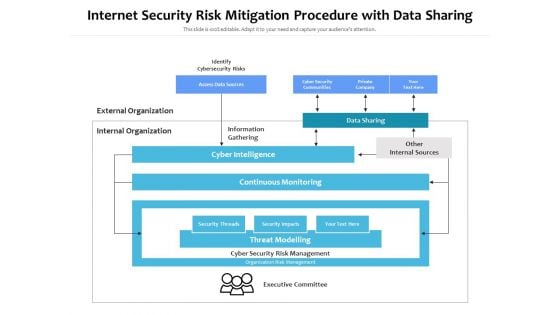
Internet Security Risk Mitigation Procedure With Data Sharing Ppt PowerPoint Presentation Pictures Show PDF
Persuade your audience using this internet security risk mitigation procedure with data sharing ppt powerpoint presentation pictures show pdf. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including identify cybersecurity risks, external organization, internal organization, information gathering, data sharing, other internal sources, cyber intelligence, continuous monitoring. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Organizational Network Awareness Staff Learning Security Training Program Frameworks Contd Formats PDF
This slide outlines the criteria, describes possible positions that could be subject to instruction, instruction information sources, and metrics to assess training success in those control areas. Deliver an awe-inspiring pitch with this creative organizational network awareness staff learning security training program frameworks contd formats pdf bundle. Topics like target audience for training, source content, metrics can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
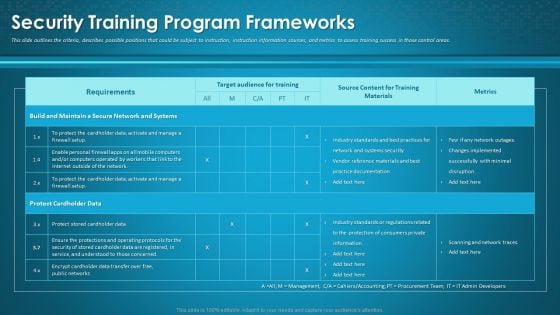
Organizational Network Awareness Staff Learning Security Training Program Frameworks Sample PDF
This slide outlines the criteria, describes possible positions that could be subject to instruction, instruction information sources, and metrics to assess training success in those control areas. Deliver and pitch your topic in the best possible manner with this organizational network awareness staff learning security training program frameworks sample pdf. Use them to share invaluable insights on target audience for training, source content, metrics and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Firewall As A Service Performance Tracking Dashboard Network Security Guidelines Pdf
This slide represents the dashboard to track the performance of Firewall-as-a-Service deployed by different organizations. The purpose of this slide is to showcase the overall performance of FWaaS by demonstrating statistics of monthly threat status, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Firewall As A Service Performance Tracking Dashboard Network Security Guidelines Pdf template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Firewall As A Service Performance Tracking Dashboard Network Security Guidelines Pdf that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide represents the dashboard to track the performance of Firewall-as-a-Service deployed by different organizations. The purpose of this slide is to showcase the overall performance of FWaaS by demonstrating statistics of monthly threat status, etc.
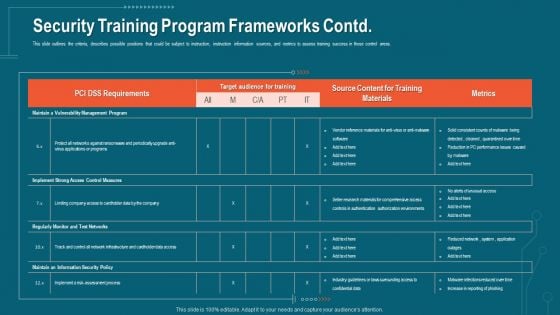
Companys Data Safety Recognition Security Training Program Frameworks Contd Infographics PDF
This slide outlines the criteria, describes possible positions that could be subject to instruction, instruction information sources, and metrics to assess training success in those control areas. Deliver and pitch your topic in the best possible manner with this companys data safety recognition security training program frameworks contd infographics pdf. Use them to share invaluable insights on requirements, target audience, metrics, training materials and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
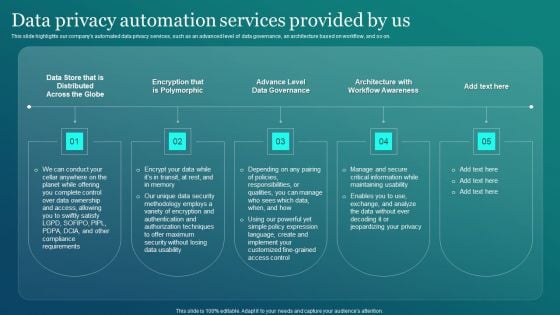
Information Security Data Privacy Automation Services Provided By Us Sample PDF
This slide highlights our companys automated data privacy services, such as an advanced level of data governance, an architecture based on workflow, and so on. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download Information Security Data Privacy Automation Services Provided By Us Sample PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the Information Security Data Privacy Automation Services Provided By Us Sample PDF.

On Ramp Option 2 Applications And Data Zero Trust Network Security Sample Pdf
This slide describes the second on-ramp option, which is the applications and data of ZTNA implementation. The purpose of this slide is to give an overview of practices and technologies used in this approach, such as data classification, data loss prevention, authentication and authorization of microservices, container security, etc. The On Ramp Option 2 Applications And Data Zero Trust Network Security Sample Pdf is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide describes the second on-ramp option, which is the applications and data of ZTNA implementation. The purpose of this slide is to give an overview of practices and technologies used in this approach, such as data classification, data loss prevention, authentication and authorization of microservices, container security, etc.
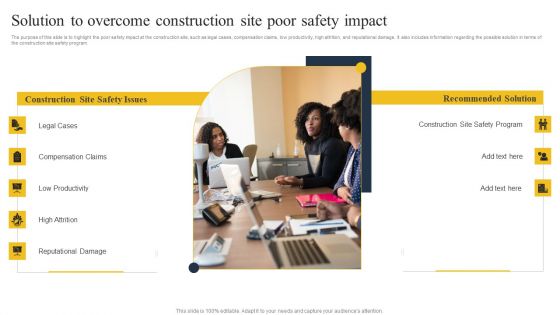
Security Control Techniques For Real Estate Project Solution To Overcome Construction Site Poor Guidelines PDF
Present like a pro with Security Control Techniques For Real Estate Project Solution To Overcome Construction Site Poor Guidelines PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
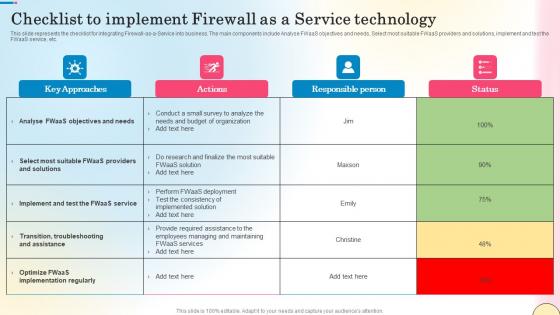
Checklist To Implement Firewall As A Service Technology Network Security Mockup Pdf
This slide represents the checklist for integrating Firewall-as-a-Service into business. The main components include Analyse FWaaS objectives and needs, Select most suitable FWaaS providers and solutions, implement and test the FWaaS service, etc. Find highly impressive Checklist To Implement Firewall As A Service Technology Network Security Mockup Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Checklist To Implement Firewall As A Service Technology Network Security Mockup Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide represents the checklist for integrating Firewall-as-a-Service into business. The main components include Analyse FWaaS objectives and needs, Select most suitable FWaaS providers and solutions, implement and test the FWaaS service, etc.
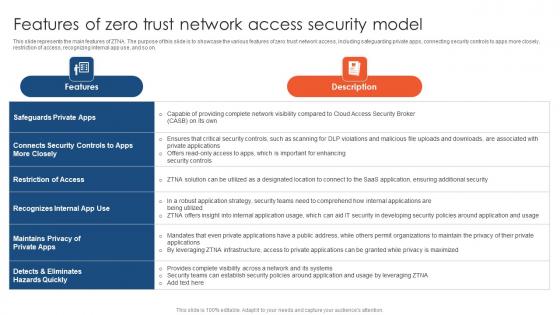
Zero Trust Network Access Features Of Zero Trust Network Access Security Model
This slide represents the main features of ZTNA. The purpose of this slide is to showcase the various features of zero trust network access, including safeguarding private apps, connecting security controls to apps more closely, restriction of access, recognizing internal app use, and so on. Slidegeeks has constructed Zero Trust Network Access Features Of Zero Trust Network Access Security Model after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide represents the main features of ZTNA. The purpose of this slide is to showcase the various features of zero trust network access, including safeguarding private apps, connecting security controls to apps more closely, restriction of access, recognizing internal app use, and so on.

Ensuring Food Safety Practices To Prevent Contamination Food Security Excellence Ppt Outline Styles PDF
This slide provides information regarding food safety practices and checklist implemented by firm in order to prevent food contamination. Deliver an awe inspiring pitch with this creative ensuring food safety practices to prevent contamination food security excellence ppt outline styles pdf bundle. Topics like ensuring food safety practices to prevent contamination can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Data Breach Prevention Recognition Security Training Program Frameworks Contd Template PDF
This slide outlines the criteria, describes possible positions that could be subject to instruction, instruction information sources, and metrics to assess training success in those control areas. Deliver an awe-inspiring pitch with this creative data breach prevention recognition security training program frameworks contd template pdf bundle. Topics like measures, instruction information sources, target audience can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Investment Banking Security Underwriting Pitchbook IPO Timeline Pre IPO To Post IPO Pictures PDF
The slide provides the timeline of IPO issue and covers the five steps i.e. Pre-IPO planning, Preparation for Filing, SEC Review, Road Show, and Post IPODeliver an awe inspiring pitch with this creative Investment Banking Security Underwriting Pitchbook IPO Timeline Pre IPO To Post IPO Pictures PDF bundle. Topics like Organizational Meeting, Preparation Filling, Internal Controls can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.


 Continue with Email
Continue with Email

 Home
Home


































