Security Operations

Working Of Common Data Encryption Data Security In Cloud Computing Ppt Example
This slide represents the working flow of Common Data Encryption DES algorithm. The purpose of this slide is to outline the algorithm steps. This slide also explains the DES modes of operation, which include Digital Codebook, Cipher Block Chaining, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Working Of Common Data Encryption Data Security In Cloud Computing Ppt Example and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide represents the working flow of Common Data Encryption DES algorithm. The purpose of this slide is to outline the algorithm steps. This slide also explains the DES modes of operation, which include Digital Codebook, Cipher Block Chaining, etc.
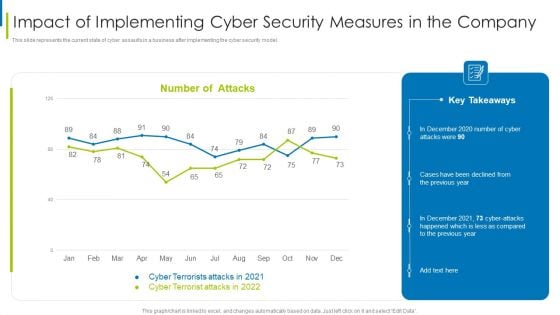
Cyber Terrorism Assault Impact Of Implementing Cyber Security Measures In The Company Professional PDF
This slide represents the current state of cyber assaults in a business after implementing the cyber security model.Deliver an awe inspiring pitch with this creative cyber terrorism assault impact of implementing cyber security measures in the company professional pdf bundle. Topics like impact of implementing cyber security measures in the company can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Construction Site Security Checklist To Ensure Systematic Progress Of Project Professional Pdf
Following slide shows the checklist for construction site safety to ensure orderly project progress which will assist in attaining overall growth. It includes parameters such as does work area is safe for employees, does employees have proper training of equipment, etc. Showcasing this set of slides titled Construction Site Security Checklist To Ensure Systematic Progress Of Project Professional Pdf. The topics addressed in these templates are Checklist Parameters, Comment. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Following slide shows the checklist for construction site safety to ensure orderly project progress which will assist in attaining overall growth. It includes parameters such as does work area is safe for employees, does employees have proper training of equipment, etc.
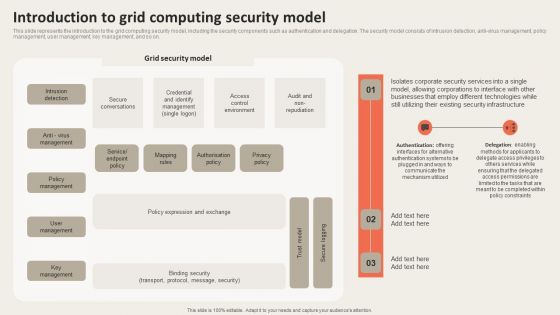
Grid Computing Applications Introduction To Grid Computing Security Model Rules PDF
This slide represents the introduction to the grid computing security model, including the security components such as authentication and delegation. The security model consists of intrusion detection, anti-virus management, policy management, user management, key management, and so on. Make sure to capture your audiences attention in your business displays with our gratis customizable Grid Computing Applications Introduction To Grid Computing Security Model Rules PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
Grid Computing For High Performance Solutions Introduction To Grid Computing Security Model Icons PDF
This slide represents the introduction to the grid computing security model, including the security components such as authentication and delegation. The security model consists of intrusion detection, anti-virus management, policy management, user management, key management, and so on. There are so many reasons you need a Grid Computing For High Performance Solutions Introduction To Grid Computing Security Model Icons PDF. The first reason is you cannot spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
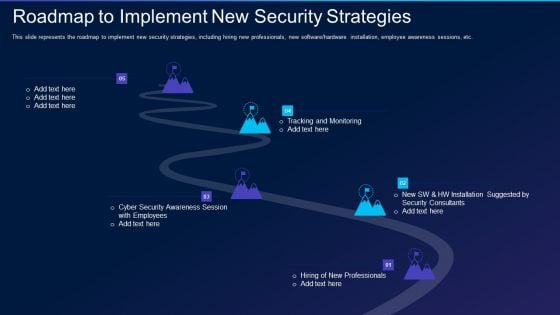
Cyber Exploitation IT Roadmap To Implement New Security Strategies Information PDF
This slide represents the roadmap to implement new security strategies, including hiring new professionals, new software or hardware installation, employee awareness sessions, etc. This is a cyber exploitation it roadmap to implement new security strategies information pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like tracking and monitoring, security consultants, cyber security awareness. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
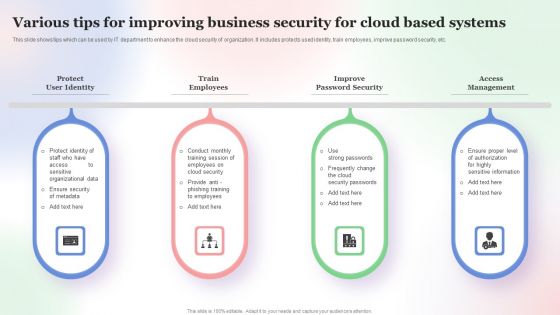
Various Tips For Improving Business Security For Cloud Based Systems Slides PDF
This slide shows tips which can be used by IT department to enhance the cloud security of organization. It includes protects used identity, train employees, improve password security, etc. Persuade your audience using this Various Tips For Improving Business Security For Cloud Based Systems Slides PDF. This PPT design covers Four stages, thus making it a great tool to use. It also caters to a variety of topics including Various Tips For Improving, Business Security, Cloud Based Systems. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
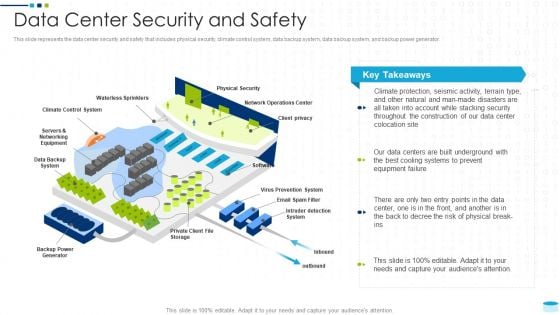
Data Center Infrastructure Management IT Data Center Security And Safety Demonstration PDF
This slide represents the data center security and safety that includes physical security, climate control system, data backup system, data backup system, and backup power generator. Deliver an awe inspiring pitch with this creative data center infrastructure management it data center security and safety demonstration pdf bundle. Topics like client privacy, physical security, waterless sprinklers, data backup system, virus prevention system can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Implementing Cybersecurity Awareness Program To Prevent Attacks Running Cyber Security Awareness Campaign Themes PDF
The purpose of this slide is to provide an overview of cyber security awareness campaign which can be used to educate staff members. The campaign covers information about the objectives, security awareness topics to cover and various activities which will be covered. Create an editable Implementing Cybersecurity Awareness Program To Prevent Attacks Running Cyber Security Awareness Campaign Themes PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre designed presentation templates help save time. Implementing Cybersecurity Awareness Program To Prevent Attacks Running Cyber Security Awareness Campaign Themes PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Company Introduction Voice Assistance Security Platform Investor Funding Presentation Professional Pdf
This slide represents the overview of Mycroft company which offers open source voice assistant and can be used in any field. It showcases industry, customer, headquarters, founded year, founders and legal name. Make sure to capture your audiences attention in your business displays with our gratis customizable Company Introduction Voice Assistance Security Platform Investor Funding Presentation Professional Pdf. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide represents the overview of Mycroft company which offers open source voice assistant and can be used in any field. It showcases industry, customer, headquarters, founded year, founders and legal name.

Competitive Dynamics And Developments Global Security Industry PPT Template IR SS V
The slide represents a detailed overview of competitive landscape. The purpose of this slide is to help stakeholders in understanding the competitive environment and aids in making informed strategic decision. The key players list include major Defense companies. There are so many reasons you need a Competitive Dynamics And Developments Global Security Industry PPT Template IR SS V. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. The slide represents a detailed overview of competitive landscape. The purpose of this slide is to help stakeholders in understanding the competitive environment and aids in making informed strategic decision. The key players list include major Defense companies.

Cybersecurity Managing Electronic Information Security 60 Days Plan Ppt Ideas Graphics Tutorials PDF
This slide represents the plan for 60 days after implementing the cyber security model in the organization. This slide represents the plan for 60 days after implementing the cyber security model in the organization. Deliver an awe inspiring pitch with this creative cybersecurity managing electronic information security 60 days plan ppt ideas graphics tutorials pdf bundle. Topics like measured, security, team, organization can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Information Systems Security And Risk Management Plan Meet Our Team Template PDF
Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Information Systems Security And Risk Management Plan Impact Of Information Security Loss On Organization Clipart PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Information Systems Security And Risk Management Plan Impact Of Information Security Loss On Organization Clipart PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Current Security Monitoring Key Portrait PDF
This slide shows some of the current Security Monitoring challenges and issues that are faced by the company and cyber security monitoring managers. This is a continuous development evaluation plan eliminate cyber attacks current security monitoring key portrait pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like malware attacks, pnishing attacks, ransomware. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
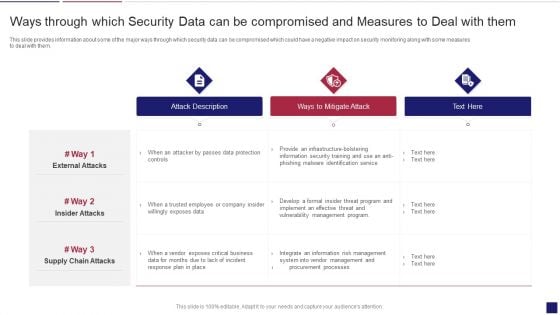
Continuous Development Evaluation Plan Eliminate Cyber Attacks Ways Through Which Security Clipart PDF
This slide provides information about some of the major ways through which security data can be compromised which could have a negative impact on security monitoring along with some measures to deal with them. Deliver an awe inspiring pitch with this creative continuous development evaluation plan eliminate cyber attacks ways through which security clipart pdf bundle. Topics like attack description, ways to mitigate attack, external attacks can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Cybersecurity Risk Scorecard Information Security Companies Risk Coverage Scorecard Icons PDF
Deliver an awe inspiring pitch with this creative cybersecurity risk scorecard information security companies risk coverage scorecard icons pdf bundle. Topics like hacker protection, network security, cubit score can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
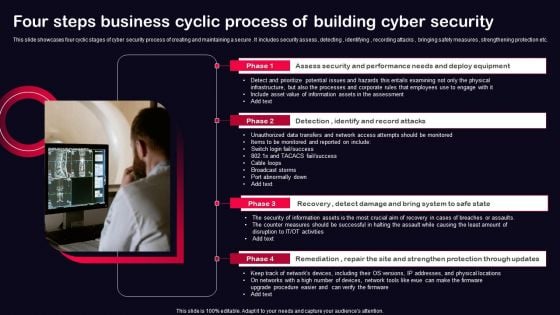
Four Steps Business Cyclic Process Of Building Cyber Security Ppt PowerPoint Presentation File Model PDF
This slide showcases four cyclic stages of cyber security process of creating and maintaining a secure . It includes security assess , detecting , identifying , recording attacks , bringing safety measures , strengthening protection etc. Presenting Four Steps Business Cyclic Process Of Building Cyber Security Ppt PowerPoint Presentation File Model PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Recovery, Remediation, Repair, Site And Strengthen, Protection Through Updates. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
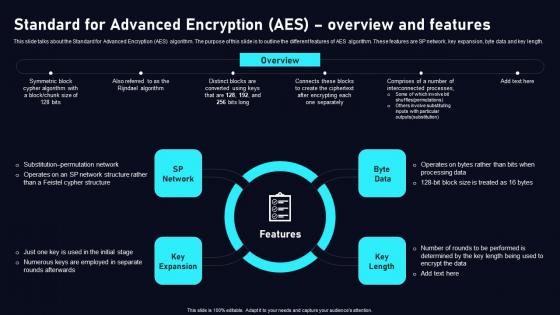
Standard For Advanced Encryption AES Cloud Data Security Using Cryptography Template Pdf
This slide talks about the Standard for Advanced Encryption AES algorithm. The purpose of this slide is to outline the different features of AES algorithm. These features are SP network, key expansion, byte data and key length. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Standard For Advanced Encryption AES Cloud Data Security Using Cryptography Template Pdf can be your best option for delivering a presentation. Represent everything in detail using Standard For Advanced Encryption AES Cloud Data Security Using Cryptography Template Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide talks about the Standard for Advanced Encryption AES algorithm. The purpose of this slide is to outline the different features of AES algorithm. These features are SP network, key expansion, byte data and key length.

Conclusion And Recommendation Global Security Industry PPT Sample IR SS V
This slide highlights the conclusion of global Defense market. The purpose of this slide is to provide a brief insights on how the Defense market is going related to its growth. On a global scale, defense industry is a highly competitive and dynamic sector. It covers understanding of global market, diversification of products and services offered, and emerging middle class expansion. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Conclusion And Recommendation Global Security Industry PPT Sample IR SS V a try. Our experts have put a lot of knowledge and effort into creating this impeccable Conclusion And Recommendation Global Security Industry PPT Sample IR SS V. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide highlights the conclusion of global Defense market. The purpose of this slide is to provide a brief insights on how the Defense market is going related to its growth. On a global scale, defense industry is a highly competitive and dynamic sector. It covers understanding of global market, diversification of products and services offered, and emerging middle class expansion.

Global Data Security Industry Report Analyzing Barriers To Entry In The Cybersecurity Industry IR SS V
The slide exhibits significant barriers to cybersecurity market entry, providing valuable insights for entrepreneurs, investors, and policymakers. These barriers make it difficult for new companies to compete with established players in the industry. Barriers include technical knowledge, regulatory compliance, High R and D cost, legal and ethical challenges. Create an editable Global Data Security Industry Report Analyzing Barriers To Entry In The Cybersecurity Industry IR SS V that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Global Data Security Industry Report Analyzing Barriers To Entry In The Cybersecurity Industry IR SS V is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. The slide exhibits significant barriers to cybersecurity market entry, providing valuable insights for entrepreneurs, investors, and policymakers. These barriers make it difficult for new companies to compete with established players in the industry. Barriers include technical knowledge, regulatory compliance, High R and D cost, legal and ethical challenges.
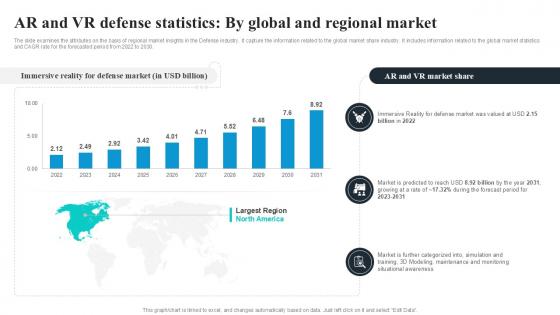
AR And VR Defense Statistics By Global Security Industry PPT Slide IR SS V
The slide examines the attributes on the basis of regional market insights in the Defense industry. It capture the information related to the global market share industry. It includes information related to the global market statistics and CAGR rate for the forecasted period from 2022 to 2030. Create an editable AR And VR Defense Statistics By Global Security Industry PPT Slide IR SS V that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. AR And VR Defense Statistics By Global Security Industry PPT Slide IR SS V is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. The slide examines the attributes on the basis of regional market insights in the Defense industry. It capture the information related to the global market share industry. It includes information related to the global market statistics and CAGR rate for the forecasted period from 2022 to 2030.

Global Data Security Industry Report Covid 19 Impact Assessment On Cybersecurity Industry IR SS V
The slide represents a comprehensive analysis of the covid-19 impact on the cybersecurity industry The purpose is to understand how the pandemic has shaped cybersecurity adoption and the significance of adapting cybersecurity technologies responsibly amidst global challenges. It covers both positive and negative impacts. Get a simple yet stunning designed Global Data Security Industry Report Covid 19 Impact Assessment On Cybersecurity Industry IR SS V. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Global Data Security Industry Report Covid 19 Impact Assessment On Cybersecurity Industry IR SS V can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. The slide represents a comprehensive analysis of the covid-19 impact on the cybersecurity industry The purpose is to understand how the pandemic has shaped cybersecurity adoption and the significance of adapting cybersecurity technologies responsibly amidst global challenges. It covers both positive and negative impacts.
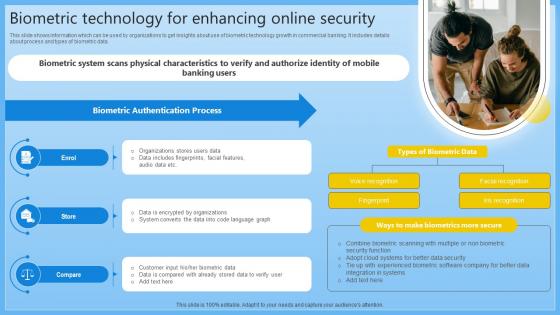
Biometric Technology For Enhancing Online Security Complete Guide On Managing Banking Fin SS V
This slide shows information which can be used by organizations to get insights about use of biometric technology growth in commercial banking. It includes details about process and types of biometric data. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Biometric Technology For Enhancing Online Security Complete Guide On Managing Banking Fin SS V can be your best option for delivering a presentation. Represent everything in detail using Biometric Technology For Enhancing Online Security Complete Guide On Managing Banking Fin SS V and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide shows information which can be used by organizations to get insights about use of biometric technology growth in commercial banking. It includes details about process and types of biometric data.

Global Data Security Industry Report Comprehensive Swot Analysis For Cybersecurity Industry IR SS V
The slide covers the cybersecurity industrys strengths, weaknesses, opportunities, and threats. The slide aims to identify internal and external factors impacting the industrys functioning. It will help stakeholders to develop strategies to achieve their objectives and improve efficiency. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Global Data Security Industry Report Comprehensive Swot Analysis For Cybersecurity Industry IR SS V a try. Our experts have put a lot of knowledge and effort into creating this impeccable Global Data Security Industry Report Comprehensive Swot Analysis For Cybersecurity Industry IR SS V. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today The slide covers the cybersecurity industrys strengths, weaknesses, opportunities, and threats. The slide aims to identify internal and external factors impacting the industrys functioning. It will help stakeholders to develop strategies to achieve their objectives and improve efficiency.

Global Data Security Industry Report Exploring Recent Developments In Cybersecurity Industry IR SS V
The slide highlights recent news and developments of major key players in the cybersecurity industry, enabling stakeholders to stay informed and make informed decisions. It covers developments related to acquisitions, collaborations, new product launches, and investments. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Global Data Security Industry Report Exploring Recent Developments In Cybersecurity Industry IR SS V can be your best option for delivering a presentation. Represent everything in detail using Global Data Security Industry Report Exploring Recent Developments In Cybersecurity Industry IR SS V and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. The slide highlights recent news and developments of major key players in the cybersecurity industry, enabling stakeholders to stay informed and make informed decisions. It covers developments related to acquisitions, collaborations, new product launches, and investments.
Employee Health And Employee Security Coaching Matrix Icon Ppt Inspiration Summary PDF
Presenting employee health and employee security coaching matrix icon ppt inspiration summary pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including employee health and employee security coaching matrix icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Highest Number Of Malware Attacks On Departments Hacking Prevention Awareness Training For IT Security Themes PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. Deliver and pitch your topic in the best possible manner with this highest number of malware attacks on departments hacking prevention awareness training for it security themes pdf. Use them to share invaluable insights on r and d department, it department, accounts department, sales department and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Cyber Security Types Attacks Ppt PowerPoint Presentation Summary Picture Cpb Pdf
Presenting this set of slides with name cyber security types attacks ppt powerpoint presentation summary picture cpb pdf. This is an editable Powerpoint four stages graphic that deals with topics like cyber security types attacks to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Website Programming IT What Is The Cyber Security Ppt PowerPoint Presentation Gallery Example File PDF
This slide represents how data security keeps in mind while developing websites, and security measures are already added to designed websites to protect them from malicious attacks. This is a website programming it what is the cyber security ppt powerpoint presentation gallery example file pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like protect information, digital assets, computers, servers, mobile devices, networks, and resources. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Identifying Employees For Information Security Training Programme Cybersecurity Risk Assessment Pictures PDF
This slide showcases plan that can help organization to conduct training for employees for information security risk management. It will enable employees to monitor risks and resolve them in timely manner. There are so many reasons you need a Identifying Employees For Information Security Training Programme Cybersecurity Risk Assessment Pictures PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
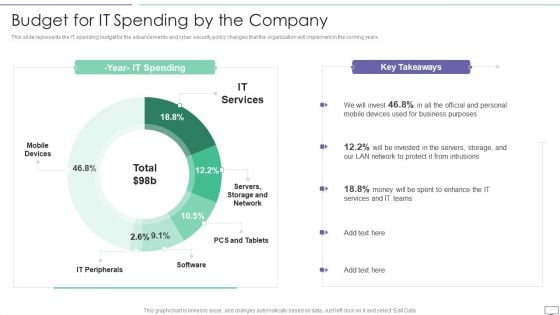
IT Security Hacker Budget For IT Spending By The Company Download PDF
This slide represents the IT spending budget for the advancements and cyber security policy changes that the organization will implement in the coming years.Deliver an awe inspiring pitch with this creative IT Security Hacker Budget For IT Spending By The Company Download PDF bundle. Topics like Business Purposes, Protect Intrusions, Services Teams can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
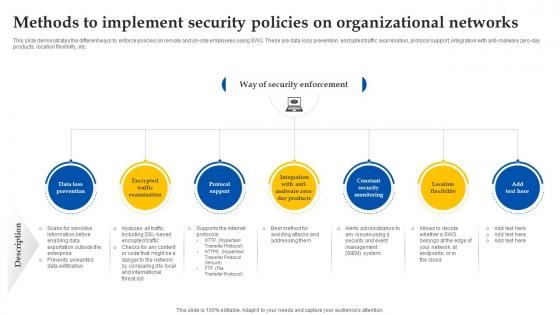
Web Access Control Solution Methods To Implement Security Policies On Organizational Networks
This slide demonstrates the different ways to enforce policies on remote and on-site employees using SWG. These are data loss prevention, encrypted traffic examination, protocol support, integration with anti-malware zero-day products, location flexibility, etc. Take your projects to the next level with our ultimate collection of Web Access Control Solution Methods To Implement Security Policies On Organizational Networks. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest This slide demonstrates the different ways to enforce policies on remote and on-site employees using SWG. These are data loss prevention, encrypted traffic examination, protocol support, integration with anti-malware zero-day products, location flexibility, etc.
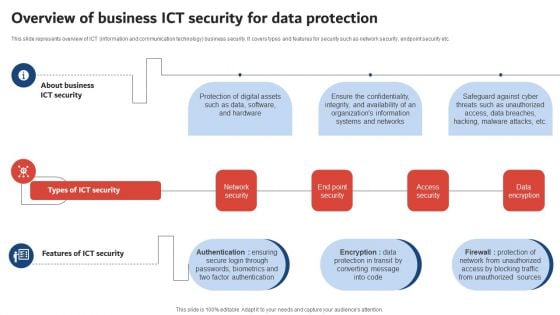
Execution Of ICT Strategic Plan Overview Of Business ICT Security For Data Protection Sample PDF
This slide represents overview of ICT information and communication technology business security. It covers types and features for security such as network security, endpoint security etc. Welcome to our selection of the Execution Of ICT Strategic Plan Overview Of Business ICT Security For Data Protection Sample PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.
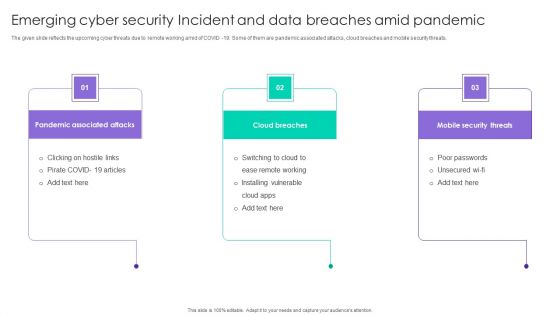
Emerging Cyber Security Incident And Data Breaches Amid Pandemic Ppt Ideas Skills PDF
The given slide reflects the upcoming cyber threats due to remote working amid of COVID -19. Some of them are pandemic associated attacks, cloud breaches and mobile security threats. Persuade your audience using this Emerging Cyber Security Incident And Data Breaches Amid Pandemic Ppt Ideas Skills PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Pandemic Associated Attacks, Cloud Breaches, Mobile Security Threats. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

IT Security Hacker Altered Business Practices Due To Hacking Structure PDF
This slide represents that hackers forced the company to alter business practices followed by years and shut down online shopping stores in some regions.Deliver an awe inspiring pitch with this creative IT Security Hacker Altered Business Practices Due To Hacking Structure PDF bundle. Topics like Stored Information, Personal Information, Social Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Online Network Security Against Hackers And Internet Threats Ppt PowerPoint Presentation File Show PDF
Persuade your audience using this online network security against hackers and internet threats ppt powerpoint presentation file show pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including online network security against hackers and internet threats. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
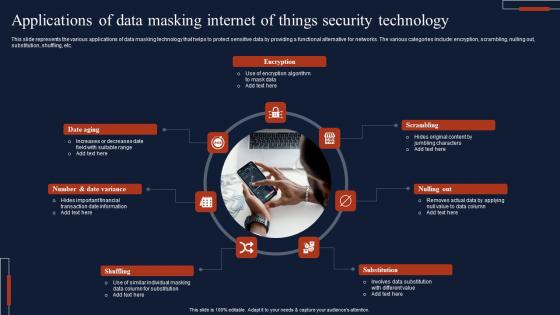
Applications Of Data Masking Internet Of Things Security Technology Topics Pdf
This slide represents the various applications of data masking technology that helps to protect sensitive data by providing a functional alternative for networks. The various categories include encryption, scrambling, nulling out, substitution, shuffling, etc. Showcasing this set of slides titled Applications Of Data Masking Internet Of Things Security Technology Topics Pdf The topics addressed in these templates are Encryption, Scrambling, Substitution, Shuffling All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide represents the various applications of data masking technology that helps to protect sensitive data by providing a functional alternative for networks. The various categories include encryption, scrambling, nulling out, substitution, shuffling, etc.
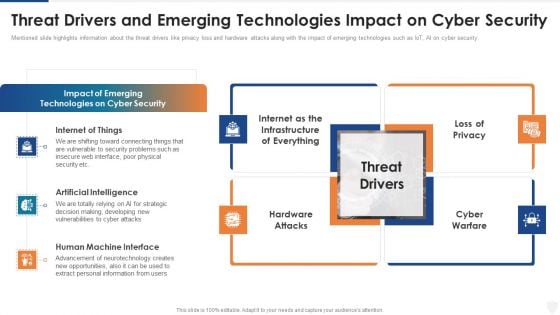
Threat Drivers And Emerging Technologies Impact On Cyber Security Ppt Slides Graphic Images PDF
Mentioned slide highlights information about the threat drivers like privacy loss and hardware attacks along with the impact of emerging technologies such as IoT, AI on cyber security. This is a threat drivers and emerging technologies impact on cyber security ppt slides graphic images pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security, developing, strategic, opportunities. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
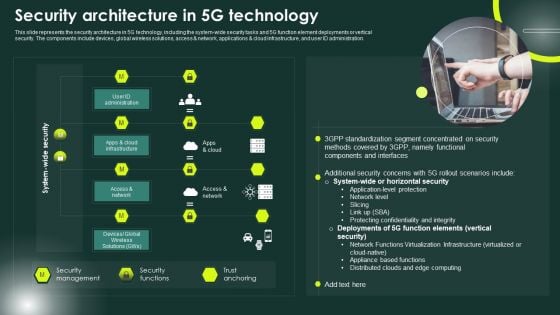
5G Network Applications And Features Security Architecture In 5G Technology Elements PDF
This slide represents the security architecture in 5G technology, including the system-wide security tasks and 5G function element deployments or vertical security. The components include devices, global wireless solutions, access and network, applications and cloud infrastructure, and user ID administration. Whether you have daily or monthly meetings, a brilliant presentation is necessary. 5G Network Applications And Features Security Architecture In 5G Technology Elements PDF can be your best option for delivering a presentation. Represent everything in detail using 5G Network Applications And Features Security Architecture In 5G Technology Elements PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Global Data Security Industry Report Key Considerations Assumptions Of Cybersecurity Industry Report IR SS V
The slide represents key considerations and limitations while building the cybersecurity industry report. The purpose of this slide is to provide framework and context for analysis and projections in addition to acknowledging uncertainties and potential risks in the future. Make sure to capture your audiences attention in your business displays with our gratis customizable Global Data Security Industry Report Key Considerations Assumptions Of Cybersecurity Industry Report IR SS V. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. The slide represents key considerations and limitations while building the cybersecurity industry report. The purpose of this slide is to provide framework and context for analysis and projections in addition to acknowledging uncertainties and potential risks in the future.
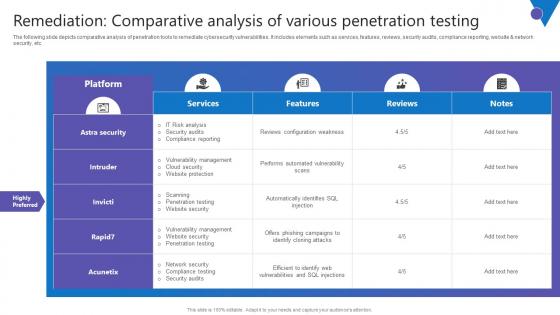
Remediation Comparative Analysis Comprehensive Guide To Blockchain Digital Security Portrait Pdf
The following slide depicts comparative analysis of penetration tools to remediate cybersecurity vulnerabilities. It includes elements such as services, features, reviews, security audits, compliance reporting, website and network security, etc. Take your projects to the next level with our ultimate collection of Remediation Comparative Analysis Comprehensive Guide To Blockchain Digital Security Portrait Pdf. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest The following slide depicts comparative analysis of penetration tools to remediate cybersecurity vulnerabilities. It includes elements such as services, features, reviews, security audits, compliance reporting, website and network security, etc.
Hacker Icon For Online Security Ppt PowerPoint Presentation Styles Example PDF
Persuade your audience using this hacker icon for online security ppt powerpoint presentation styles example pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including hacker icon for online security. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
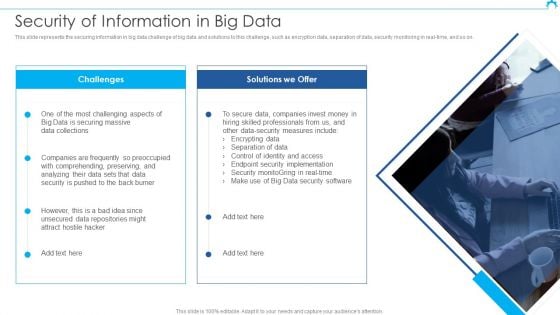
Big Data Architect Security Of Information In Big Data Graphics PDF
This slide represents the securing information in big data challenge of big data and solutions to this challenge, such as encryption data, separation of data, security monitoring in real-time, and so on.Deliver an awe inspiring pitch with this creative Big Data Architect Security Of Information In Big Data Graphics PDF bundle. Topics like Most Challenging, Securing Massive, Data Collections can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
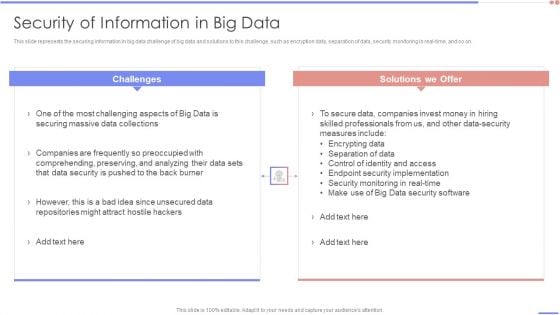
Data Analytics Management Security Of Information In Big Data Summary PDF
This slide represents the securing information in big data challenge of big data and solutions to this challenge, such as encryption data, separation of data, security monitoring in real-time, and so on.Deliver an awe inspiring pitch with this creative Data Analytics Management Security Of Information In Big Data Summary PDF bundle. Topics like Securing Massive, Companies Frequently, Comprehending Preserving can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
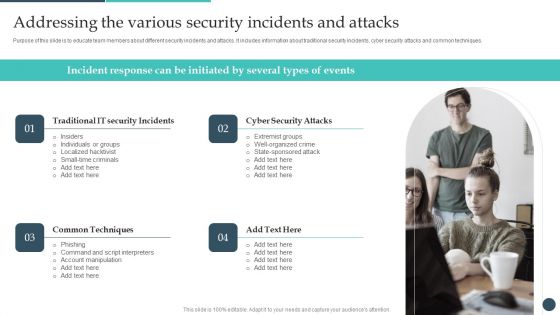
Safety Breach Response Playbook Addressing The Various Security Incidents And Attacks Infographics PDF
Purpose of this slide is to educate team members about different security incidents and attacks. It includes information about traditional security incidents, cyber security attacks and common techniques. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Safety Breach Response Playbook Addressing The Various Security Incidents And Attacks Infographics PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Smart Home System Security Threats Utilizing Smart Appliances IoT SS V
This slide provides an overview of the threats to smart house systems and their solution. Major threats covered are device hacking, distributed denial of service, data and identity theft. Take your projects to the next level with our ultimate collection of Smart Home System Security Threats Utilizing Smart Appliances IoT SS V. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest This slide provides an overview of the threats to smart house systems and their solution. Major threats covered are device hacking, distributed denial of service, data and identity theft.

Products And Services Offered Voice Assistance Security Platform Investor Funding Rules Pdf
This slide represents product and solution categories offered by business which are session replays, heatmaps, team dashboards, user journeys, user segmentation, funnel analytics, events analytics, issue analytics, 3rd party integrations, understand UX, increase conversions, drive engagement and resolve issues. Do you know about Slidesgeeks Products And Services Offered Voice Assistance Security Platform Investor Funding Rules Pdf These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide represents product and solution categories offered by business which are session replays, heatmaps, team dashboards, user journeys, user segmentation, funnel analytics, events analytics, issue analytics, 3rd party integrations, understand UX, increase conversions, drive engagement and resolve issues.

Cloud Access Security Broker Pillar Overview Ppt PowerPoint Presentation File Infographics PDF
This slide represents the four major pillars of cloud access security broker. The purpose of this slide is to showcase the main pillars of implementing a cloud access security broker. The pillars include compliance, visibility, threat protection, and data security. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Cloud Access Security Broker Pillar Overview Ppt PowerPoint Presentation File Infographics PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Cloud Access Security Broker Pillar Overview Ppt PowerPoint Presentation File Infographics PDF today and make your presentation stand out from the rest.

Implementing Cybersecurity Awareness Program To Prevent Attacks Practices To Improve Security Awareness Level Slides PDF
The purpose of this slide is to outline different approaches used to enhance the cyber security awareness level. Creating security awareness program, conducting quarterly training session and implementing cyber security drills are some of the major approaches which are highlighted in the slide. Take your projects to the next level with our ultimate collection of Implementing Cybersecurity Awareness Program To Prevent Attacks Practices To Improve Security Awareness Level Slides PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest.

Global Data Security Industry Report Commonly Used Acronyms In Cybersecurity Industry IR SS V
The slide represents acronyms and terminology used in the cybersecurity industry. The slide aims to help audience better comprehend and navigate industry specific language, allowing for improved communication and comprehension of cybersecurity industry concepts, trends, and discussions. There are so many reasons you need a Global Data Security Industry Report Commonly Used Acronyms In Cybersecurity Industry IR SS V. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. The slide represents acronyms and terminology used in the cybersecurity industry. The slide aims to help audience better comprehend and navigate industry specific language, allowing for improved communication and comprehension of cybersecurity industry concepts, trends, and discussions.

Implementing Cybersecurity Awareness Program To Prevent Attacks Evaluating IT System Security Formats PDF
The purpose of this slide is to outline the strength, weakness, opportunities and threat SWOT evaluation of organization cyber security. Organization can detect the potential risks and opportunities in the cyber security using SWOT model. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Implementing Cybersecurity Awareness Program To Prevent Attacks Evaluating IT System Security Formats PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Implementing Cybersecurity Awareness Program To Prevent Attacks Evaluating IT System Security Formats PDF today and make your presentation stand out from the rest.
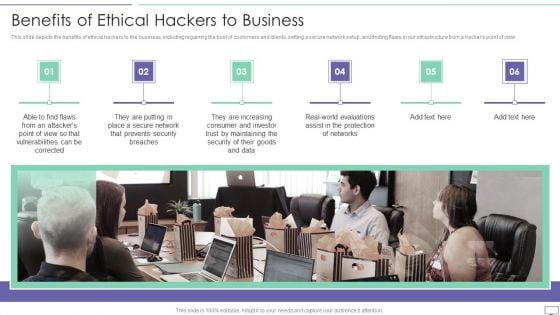
IT Security Hacker Benefits Of Ethical Hackers To Business Diagrams PDF
This slide depicts the benefits of ethical hackers to the business, including regaining the trust of customers and clients, setting a secure network setup, and finding flaws in our infrastructure from a hackers point of view.Presenting IT Security Hacker Benefits Of Ethical Hackers To Business Diagrams PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Consumer And Investor, Assist In The Protection, Prevents Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
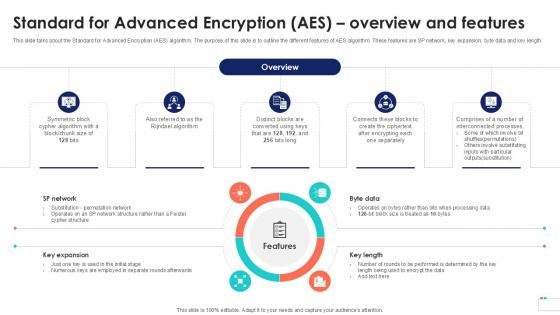
Standard For Advanced Encryption Data Security In Cloud Computing Ppt Sample
This slide talks about the Standard for Advanced Encryption AES algorithm. The purpose of this slide is to outline the different features of AES algorithm. These features are SP network, key expansion, byte data and key length. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Standard For Advanced Encryption Data Security In Cloud Computing Ppt Sample a try. Our experts have put a lot of knowledge and effort into creating this impeccable Standard For Advanced Encryption Data Security In Cloud Computing Ppt Sample. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide talks about the Standard for Advanced Encryption AES algorithm. The purpose of this slide is to outline the different features of AES algorithm. These features are SP network, key expansion, byte data and key length.
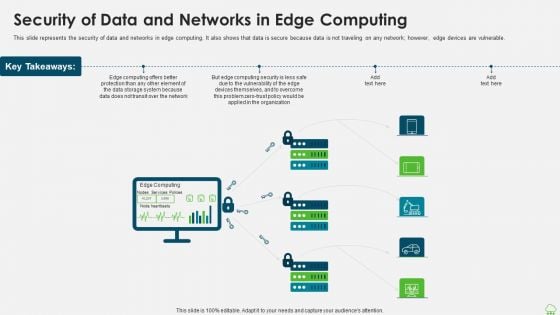
Distributed Computing IT Security Of Data And Networks In Edge Computing Themes PDF
This slide represents the security of data and networks in edge computing. It also shows that data is secure because data is not traveling on any network however, edge devices are vulnerable. Presenting distributed computing it security of data and networks in edge computing themes pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like organization, data storage, computing security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Endpoint Initiated Vs Service Initiated Zero Trust Network Security Microsoft Pdf
This slide represents the comparison between the two primary approaches to implementing zero-trust network access for organizations. The purpose of this slide is to showcase the endpoint-initiated and service-initiated approach of zero-trust network access. Find highly impressive Endpoint Initiated Vs Service Initiated Zero Trust Network Security Microsoft Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Endpoint Initiated Vs Service Initiated Zero Trust Network Security Microsoft Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide represents the comparison between the two primary approaches to implementing zero-trust network access for organizations. The purpose of this slide is to showcase the endpoint-initiated and service-initiated approach of zero-trust network access.
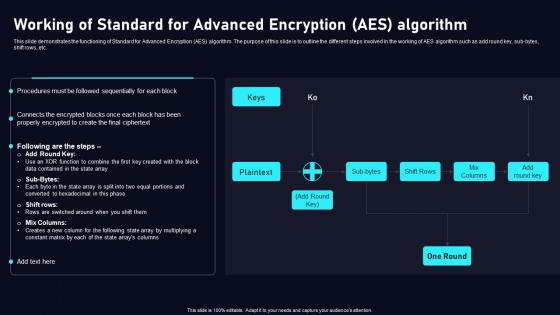
Working Of Standard For Advanced Cloud Data Security Using Cryptography Diagrams Pdf
This slide demonstrates the functioning of Standard for Advanced Encryption AES algorithm. The purpose of this slide is to outline the different steps involved in the working of AES algorithm such as add round key, sub bytes, shift rows, etc. Create an editableWorking Of Standard For Advanced Cloud Data Security Using Cryptography Diagrams Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save timeWorking Of Standard For Advanced Cloud Data Security Using Cryptography Diagrams Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide demonstrates the functioning of Standard for Advanced Encryption AES algorithm. The purpose of this slide is to outline the different steps involved in the working of AES algorithm such as add round key, sub bytes, shift rows, etc.
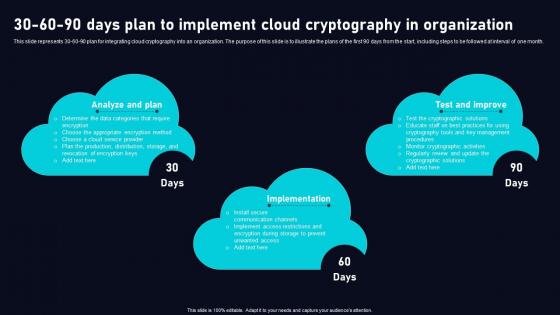
30 60 90 Days Plan To Implement Cloud Data Security Using Cryptography Slides Pdf
This slide represents 30 60 90 plan for integrating cloud cryptography into an organization. The purpose of this slide is to illustrate the plans of the first 90 days from the start, including steps to be followed at interval of one month. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give 30 60 90 Days Plan To Implement Cloud Data Security Using Cryptography Slides Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable 30 60 90 Days Plan To Implement Cloud Data Security Using Cryptography Slides Pdf You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide represents 30 60 90 plan for integrating cloud cryptography into an organization. The purpose of this slide is to illustrate the plans of the first 90 days from the start, including steps to be followed at interval of one month.

Global Data Security Industry Report Emerging Threat Trends In Cybersecurity Industry IR SS V
The slide presents the latest threat trends in the global cybersecurity industry. The purpose of the slide is to raise awareness about the evolving landscape of cyber threats, which is crucial for individuals and organizations to stay protected. It covers threat such as automotive hacking, cloud services attacks, social engineering attacks, 5g network threats, and ransomware attacks. Slidegeeks is here to make your presentations a breeze with Global Data Security Industry Report Emerging Threat Trends In Cybersecurity Industry IR SS V With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first The slide presents the latest threat trends in the global cybersecurity industry. The purpose of the slide is to raise awareness about the evolving landscape of cyber threats, which is crucial for individuals and organizations to stay protected. It covers threat such as automotive hacking, cloud services attacks, social engineering attacks, 5g network threats, and ransomware attacks.

Comparative Assessment Of Smart Home Security Systems Utilizing Smart Appliances IoT SS V
This slide provides an overview of the various smart home systems used to enhance safety. The comparison is done on the basis of features, compatible voice assistants, rating, installation type and price. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Comparative Assessment Of Smart Home Security Systems Utilizing Smart Appliances IoT SS V a try. Our experts have put a lot of knowledge and effort into creating this impeccable Comparative Assessment Of Smart Home Security Systems Utilizing Smart Appliances IoT SS V. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide provides an overview of the various smart home systems used to enhance safety. The comparison is done on the basis of features, compatible voice assistants, rating, installation type and price.
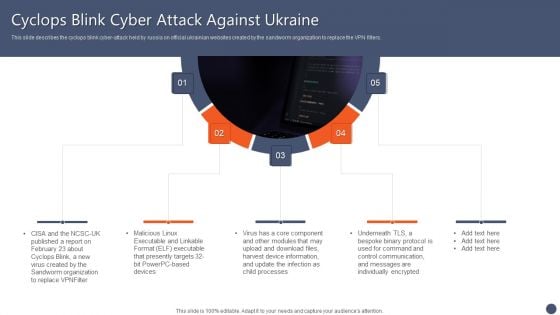
Series Of Cyber Security Attacks Against Ukraine 2022 Cyclops Blink Cyber Attack Against Ukraine Sample PDF
This slide describes the cyclops blink cyber attack held by russia on official ukrainian websites created by the sandworm organization to replace the VPN filters. Get a simple yet stunning designed Series Of Cyber Security Attacks Series Of Cyber Security Attacks Against Ukraine 2022 Cyclops Blink Cyber Attack Against Ukraine Sample PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Series Of Cyber Security Attacks Against Ukraine 2022 Cyclops Blink Cyber Attack Against Ukraine Sample PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.


 Continue with Email
Continue with Email

 Home
Home


































