Security Operations
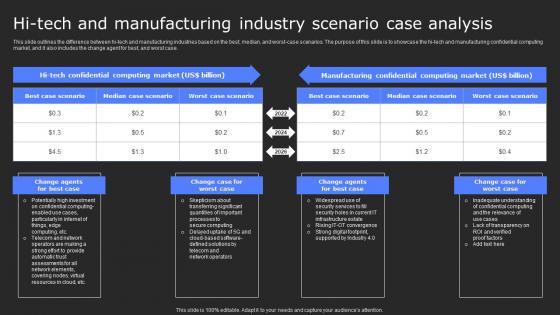
Hi Tech And Manufacturing Industry Scenario Secure Computing Framework Rules Pdf
This slide outlines the difference between hi-tech and manufacturing industries based on the best, median, and worst-case scenarios. The purpose of this slide is to showcase the hi-tech and manufacturing confidential computing market, and it also includes the change agent for best, and worst case. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Hi Tech And Manufacturing Industry Scenario Secure Computing Framework Rules Pdf to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Hi Tech And Manufacturing Industry Scenario Secure Computing Framework Rules Pdf. This slide outlines the difference between hi-tech and manufacturing industries based on the best, median, and worst-case scenarios. The purpose of this slide is to showcase the hi-tech and manufacturing confidential computing market, and it also includes the change agent for best, and worst case.
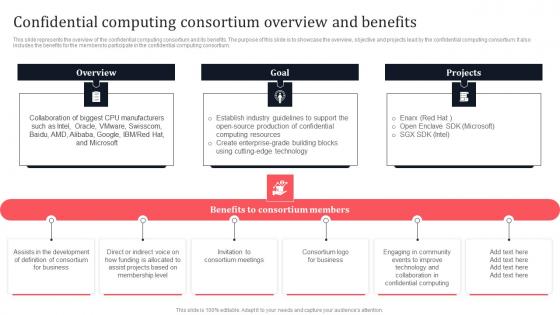
Confidential Computing Consortium Overview And Benefits Secure Multi Party Demonstration Pdf
This slide represents the overview of the confidential computing consortium and its benefits. The purpose of this slide is to showcase the overview, objective and projects lead by the confidential computing consortium. It also includes the benefits for the members to participate in the confidential computing consortium. If you are looking for a format to display your unique thoughts, then the professionally designed Confidential Computing Consortium Overview And Benefits Secure Multi Party Demonstration Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Confidential Computing Consortium Overview And Benefits Secure Multi Party Demonstration Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide represents the overview of the confidential computing consortium and its benefits. The purpose of this slide is to showcase the overview, objective and projects lead by the confidential computing consortium. It also includes the benefits for the members to participate in the confidential computing consortium.

Working Components Of Secure Web Gateway Architecture Web Threat Protection System
This slide represents the key elements involved in the working of Secure Web Gateway. The purpose of this slide is to explain the different components of SWG. These include traffic inspection, URL filtering, application control, website content inspection, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Working Components Of Secure Web Gateway Architecture Web Threat Protection System and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide represents the key elements involved in the working of Secure Web Gateway. The purpose of this slide is to explain the different components of SWG. These include traffic inspection, URL filtering, application control, website content inspection, etc.
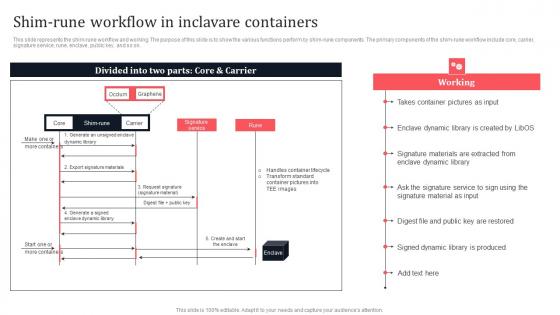
Shim Rune Workflow In Inclavare Containers Secure Multi Party Ideas Pdf
This slide represents the shim-rune workflow and working. The purpose of this slide is to show the various functions perform by shim-rune components. The primary components of the shim-rune workflow include core, carrier, signature service, rune, enclave, public key, and so on. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Shim Rune Workflow In Inclavare Containers Secure Multi Party Ideas Pdf can be your best option for delivering a presentation. Represent everything in detail using Shim Rune Workflow In Inclavare Containers Secure Multi Party Ideas Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide represents the shim-rune workflow and working. The purpose of this slide is to show the various functions perform by shim-rune components. The primary components of the shim-rune workflow include core, carrier, signature service, rune, enclave, public key, and so on.
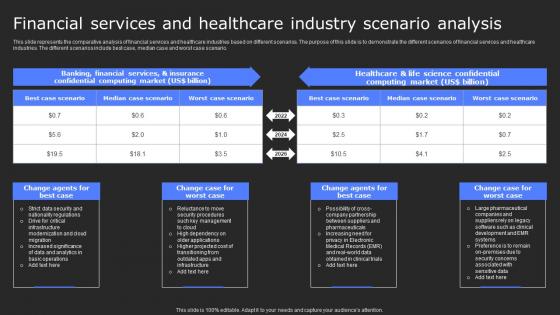
Financial Services And Healthcare Industry Scenario Secure Computing Framework Clipart Pdf
This slide represents the comparative analysis of financial services and healthcare industries based on different scenarios. The purpose of this slide is to demonstrate the different scenarios of financial services and healthcare industries. The different scenarios include best case, median case and worst case scenario. Retrieve professionally designed Financial Services And Healthcare Industry Scenario Secure Computing Framework Clipart Pdf to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide represents the comparative analysis of financial services and healthcare industries based on different scenarios. The purpose of this slide is to demonstrate the different scenarios of financial services and healthcare industries. The different scenarios include best case, median case and worst case scenario.
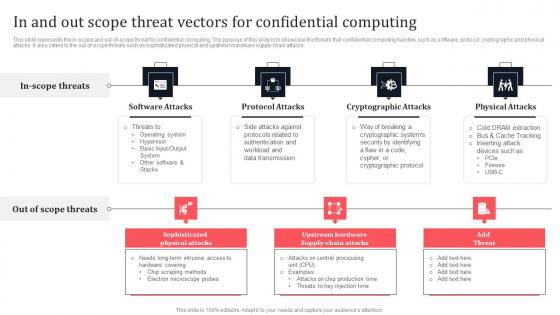
In And Out Scope Threat Vectors For Confidential Computing Secure Multi Party Elements Pdf
This slide represents the in-scope and out-of-scope threat for confidential computing. The purpose of this slide is to showcase the threats that confidential computing handles, such as software, protocol, cryptographic and physical attacks. It also caters to the out of scope threats such as sophisticated physical and upstream hardware supply-chain attacks. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download In And Out Scope Threat Vectors For Confidential Computing Secure Multi Party Elements Pdf to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the In And Out Scope Threat Vectors For Confidential Computing Secure Multi Party Elements Pdf This slide represents the in-scope and out-of-scope threat for confidential computing. The purpose of this slide is to showcase the threats that confidential computing handles, such as software, protocol, cryptographic and physical attacks. It also caters to the out of scope threats such as sophisticated physical and upstream hardware supply-chain attacks.

Web Access Control Solution Architecture Of Citrix Secure Web Gateway Proxy Solution
This slide represents the Secure Web Gateway solution provided by Citrix. The purpose of this slide is to demonstrate the architecture of Citrixs SWG solution. The key components included are users, firewall, internet, logstream, SWG appliance, etc. Slidegeeks is here to make your presentations a breeze with Web Access Control Solution Architecture Of Citrix Secure Web Gateway Proxy Solution With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide represents the Secure Web Gateway solution provided by Citrix. The purpose of this slide is to demonstrate the architecture of Citrixs SWG solution. The key components included are users, firewall, internet, logstream, SWG appliance, etc.
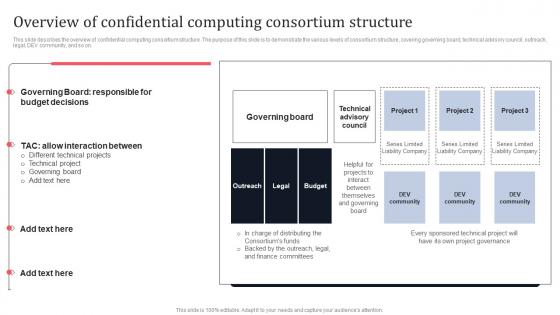
Overview Of Confidential Computing Consortium Structure Secure Multi Party Formats Pdf
This slide describes the overview of confidential computing consortium structure. The purpose of this slide is to demonstrate the various levels of consortium structure, covering governing board, technical advisory council, outreach, legal, DEV community, and so on. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Overview Of Confidential Computing Consortium Structure Secure Multi Party Formats Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Overview Of Confidential Computing Consortium Structure Secure Multi Party Formats Pdf You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today. This slide describes the overview of confidential computing consortium structure. The purpose of this slide is to demonstrate the various levels of consortium structure, covering governing board, technical advisory council, outreach, legal, DEV community, and so on.
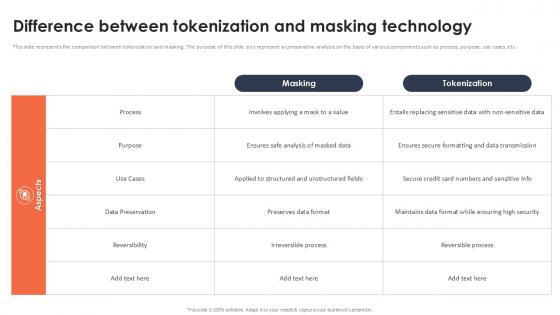
Difference Between Tokenization And Masking Technology Securing Your Data Ppt Powerpoint
This slide represents the comparison between tokenization and masking. The purpose of this slide is to represent a comparative analysis on the basis of various components such as process, purpose, use cases, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Difference Between Tokenization And Masking Technology Securing Your Data Ppt Powerpoint and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide represents the comparison between tokenization and masking. The purpose of this slide is to represent a comparative analysis on the basis of various components such as process, purpose, use cases, etc.
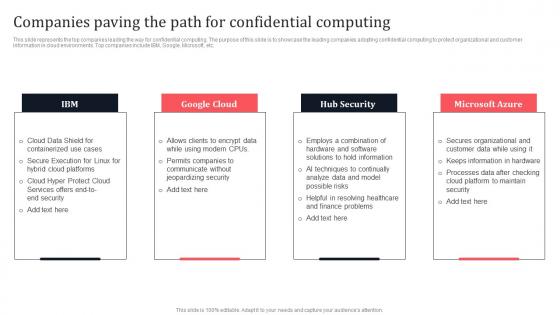
Companies Paving The Path For Confidential Computing Secure Multi Party Elements Pdf
This slide represents the top companies leading the way for confidential computing. The purpose of this slide is to showcase the leading companies adopting confidential computing to protect organizational and customer information in cloud environments. Top companies include IBM, Google, Microsoft, etc. There are so many reasons you need a Companies Paving The Path For Confidential Computing Secure Multi Party Elements Pdf The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide represents the top companies leading the way for confidential computing. The purpose of this slide is to showcase the leading companies adopting confidential computing to protect organizational and customer information in cloud environments. Top companies include IBM, Google, Microsoft, etc.
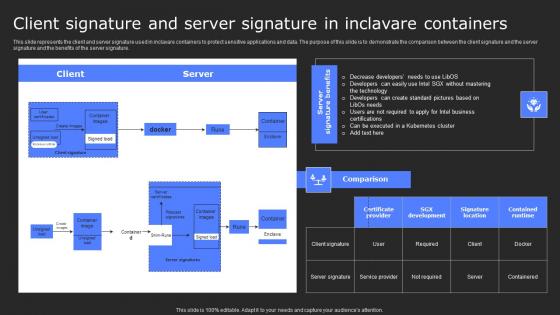
Client Signature And Server Signature In Secure Computing Framework Themes Pdf
This slide represents the client and server signature used in inclavare containers to protect sensitive applications and data. The purpose of this slide is to demonstrate the comparison between the client signature and the server signature and the benefits of the server signature. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Client Signature And Server Signature In Secure Computing Framework Themes Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide represents the client and server signature used in inclavare containers to protect sensitive applications and data. The purpose of this slide is to demonstrate the comparison between the client signature and the server signature and the benefits of the server signature.
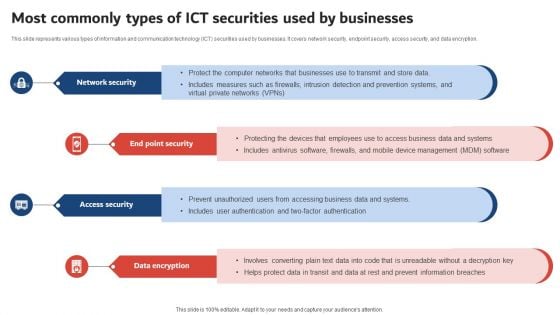
Execution Of ICT Strategic Plan Most Commonly Types Of ICT Securities Used By Businesses Microsoft PDF
This slide represents various types of information and communication technology ICT securities used by businesses. It covers network security, endpoint security, access security, and data encryption. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Execution Of ICT Strategic Plan Most Commonly Types Of ICT Securities Used By Businesses Microsoft PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Execution Of ICT Strategic Plan Most Commonly Types Of ICT Securities Used By Businesses Microsoft PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
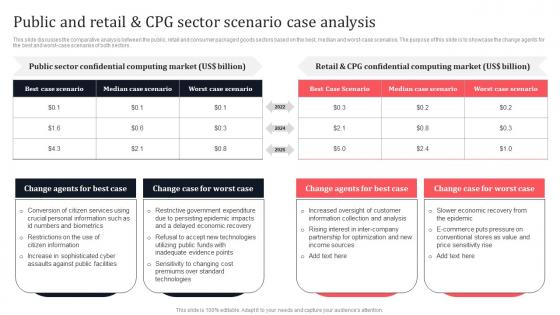
Public And Retail And CPG Sector Scenario Case Analysis Secure Multi Party Portrait Pdf
This slide discusses the comparative analysis between the public, retail and consumer packaged goods sectors based on the best, median and worst-case scenarios. The purpose of this slide is to showcase the change agents for the best and worst-case scenarios of both sectors. Slidegeeks is here to make your presentations a breeze with Public And Retail And CPG Sector Scenario Case Analysis Secure Multi Party Portrait Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first. This slide discusses the comparative analysis between the public, retail and consumer packaged goods sectors based on the best, median and worst-case scenarios. The purpose of this slide is to showcase the change agents for the best and worst-case scenarios of both sectors.
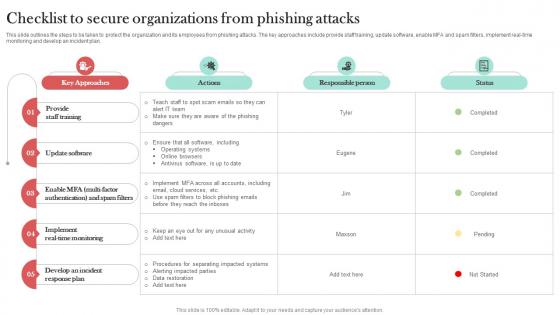
Checklist To Secure Organizations From Man In The Middle Phishing IT
This slide outlines the steps to be taken to protect the organization and its employees from phishing attacks. The key approaches include provide staff training, update software, enable MFA and spam filters, implement real-time monitoring and develop an incident plan. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Checklist To Secure Organizations From Man In The Middle Phishing IT template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Checklist To Secure Organizations From Man In The Middle Phishing IT that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide outlines the steps to be taken to protect the organization and its employees from phishing attacks. The key approaches include provide staff training, update software, enable MFA and spam filters, implement real-time monitoring and develop an incident plan.
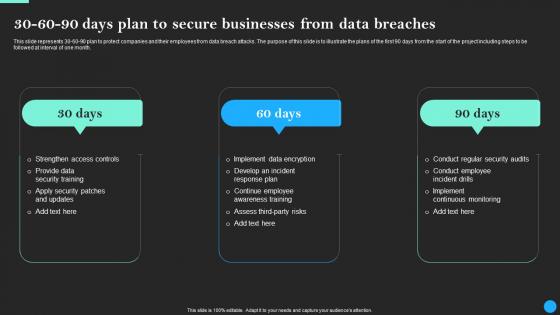
30 60 90 Days Plan To Secure Businesses From Data Breach Prevention Portrait Pdf
This slide represents 30-60-90 plan to protect companies and their employees from data breach attacks. The purpose of this slide is to illustrate the plans of the first 90 days from the start of the project including steps to be followed at interval of one month. Find a pre-designed and impeccable 30 60 90 Days Plan To Secure Businesses From Data Breach Prevention Portrait Pdf. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide represents 30-60-90 plan to protect companies and their employees from data breach attacks. The purpose of this slide is to illustrate the plans of the first 90 days from the start of the project including steps to be followed at interval of one month.
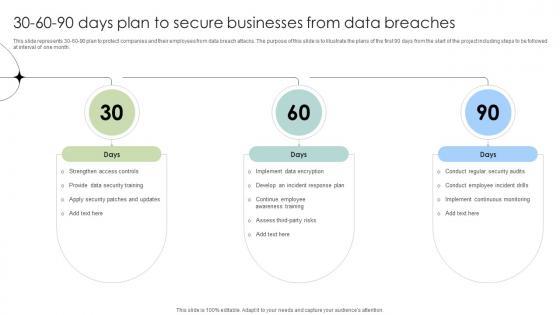
30 60 90 Days Plan To Secure Businesses From Data Breaches Data Fortification Strengthening Defenses
This slide represents 30-60-90 plan to protect companies and their employees from data breach attacks. The purpose of this slide is to illustrate the plans of the first 90 days from the start of the project including steps to be followed at interval of one month.Find a pre-designed and impeccable 30 60 90 Days Plan To Secure Businesses From Data Breaches Data Fortification Strengthening Defenses. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide represents 30-60-90 plan to protect companies and their employees from data breach attacks. The purpose of this slide is to illustrate the plans of the first 90 days from the start of the project including steps to be followed at interval of one month.

Redis Cache Data Structure IT Secure Server Configuration With Server Configuration Lock Diagrams PDF
This slide describes the secure server configuration with server configuration lock, which guarantees only users have access. Presenting redis cache data structure it secure server configuration with server configuration lock diagrams pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like securing, programmer, network. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
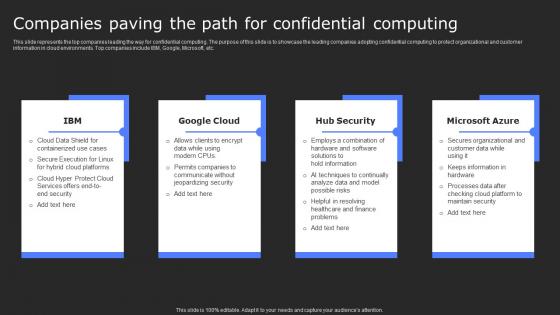
Companies Paving The Path For Confidential Secure Computing Framework Download Pdf
This slide represents the top companies leading the way for confidential computing. The purpose of this slide is to showcase the leading companies adopting confidential computing to protect organizational and customer information in cloud environments. Top companies include IBM, Google, Microsoft, etc. Present like a pro with Companies Paving The Path For Confidential Secure Computing Framework Download Pdf Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide represents the top companies leading the way for confidential computing. The purpose of this slide is to showcase the leading companies adopting confidential computing to protect organizational and customer information in cloud environments. Top companies include IBM, Google, Microsoft, etc.
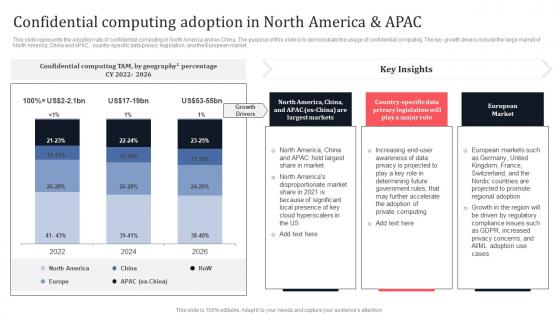
Confidential Computing Adoption In North America And APAC Secure Multi Party Brochure Pdf
This slide represents the adoption rate of confidential computing in North America and ex-China. The purpose of this slide is to demonstrate the usage of confidential computing. The key growth drivers include the large market of North America, China and APAC, country-specific data privacy legislation, and the European market. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Confidential Computing Adoption In North America And APAC Secure Multi Party Brochure Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide represents the adoption rate of confidential computing in North America and ex-China. The purpose of this slide is to demonstrate the usage of confidential computing. The key growth drivers include the large market of North America, China and APAC, country-specific data privacy legislation, and the European market.
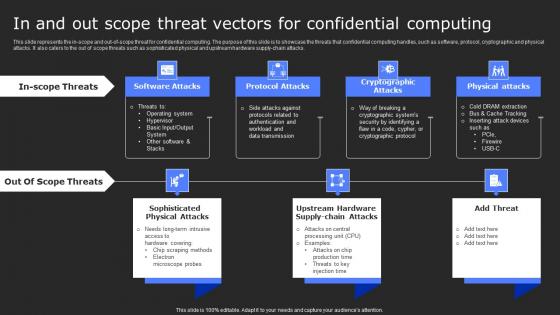
In And Out Scope Threat Vectors For Confidential Secure Computing Framework Inspiration Pdf
This slide represents the in-scope and out-of-scope threat for confidential computing. The purpose of this slide is to showcase the threats that confidential computing handles, such as software, protocol, cryptographic and physical attacks. It also caters to the out of scope threats such as sophisticated physical and upstream hardware supply-chain attacks. Take your projects to the next level with our ultimate collection of In And Out Scope Threat Vectors For Confidential Secure Computing Framework Inspiration Pdf. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest This slide represents the in-scope and out-of-scope threat for confidential computing. The purpose of this slide is to showcase the threats that confidential computing handles, such as software, protocol, cryptographic and physical attacks. It also caters to the out of scope threats such as sophisticated physical and upstream hardware supply-chain attacks.
Inclavare Confidential Containers Architecture In Tee Secure Multi Party Icons Pdf
This slide represents the architecture of inclavare confidential containers in the TEE environment. The purpose of this slide is to showcase the various components and features of inclavare containers. The primary components include Kubelet, containerd, shim-rune, rune, PAL API, Pod and so on. This Inclavare Confidential Containers Architecture In Tee Secure Multi Party Icons Pdf from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide represents the architecture of inclavare confidential containers in the TEE environment. The purpose of this slide is to showcase the various components and features of inclavare containers. The primary components include Kubelet, containerd, shim-rune, rune, PAL API, Pod and so on.
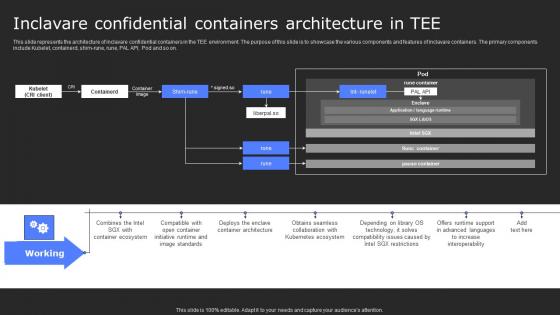
Inclavare Confidential Containers Architecture In Tee Secure Computing Framework Infographics Pdf
This slide represents the architecture of inclavare confidential containers in the TEE environment. The purpose of this slide is to showcase the various components and features of inclavare containers. The primary components include Kubelet, containerd, shim-rune, rune, PAL API, Pod and so on. Do you know about Slidesgeeks Inclavare Confidential Containers Architecture In Tee Secure Computing Framework Infographics Pdf These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide represents the architecture of inclavare confidential containers in the TEE environment. The purpose of this slide is to showcase the various components and features of inclavare containers. The primary components include Kubelet, containerd, shim-rune, rune, PAL API, Pod and so on.

One Page NDA Report To Secure Employee Confidentiality PDF Document PPT Template
Looking for a predesigned One Page NDA Report To Secure Employee Confidentiality PDF Document PPT Template Heres the perfect piece for you It has everything that a well-structured one-pager template should have. Besides, it is 100 percent editable, which offers you the cushion to make adjustments according to your preferences. Grab this One Page NDA Report To Secure Employee Confidentiality PDF Document PPT Template Download now.
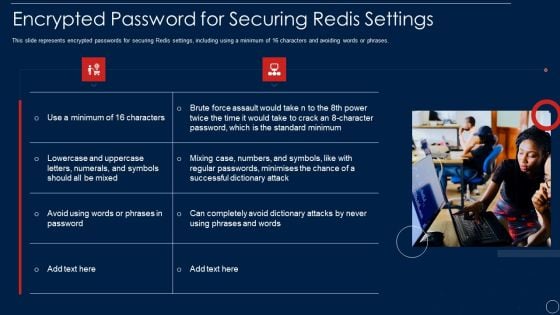
Redis Cache Data Structure IT Encrypted Password For Securing Redis Settings Formats PDF
This slide represents encrypted passwords for securing Redis settings, including using a minimum of 16 characters and avoiding words or phrases. This is a redis cache data structure it encrypted password for securing redis settings formats pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like encrypted password for securing redis settings. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
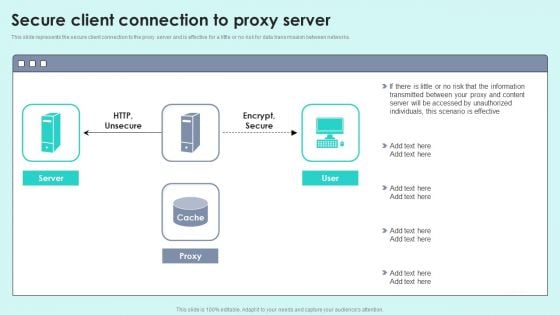
Secure Client Connection To Proxy Server Reverse Proxy For Load Balancing Portrait PDF
This slide represents the secure client connection to the proxy server and is effective for a little or no risk for data transmission between networks.Deliver an awe inspiring pitch with this creative Secure Client Connection To Proxy Server Reverse Proxy For Load Balancing Portrait PDF bundle. Topics like Transmitted Between, Accessed Unauthorized, Scenario Effective can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Reverse Proxy Web Server Secure Client Connection To Proxy Server Themes PDF
This slide represents the secure client connection to the proxy server and is effective for a little or no risk for data transmission between networks. Presenting this PowerPoint presentation, titled Reverse Proxy Web Server Secure Client Connection To Proxy Server Themes PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Reverse Proxy Web Server Secure Client Connection To Proxy Server Themes PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Reverse Proxy Web Server Secure Client Connection To Proxy Server Themes PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.

Advantages And Working Of Secure SDLC Phases Of Software Development Procedure Professional PDF
This slide represents the advantages and working of secure software development life cycle, including its various phases, such as concept, planning, design and development, testing, release, sustain, and disposal.Create an editable Advantages And Working Of Secure SDLC Phases Of Software Development Procedure Professional PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Advantages And Working Of Secure SDLC Phases Of Software Development Procedure Professional PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Employee Benefits Template Social Securities Ppt PowerPoint Presentation Layouts Background Image
Presenting this set of slides with name employee benefits template social securities ppt powerpoint presentation layouts background image. This is a five stage process. The stages in this process are finance, marketing, management, investment, analysis. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Budget To Implement Secure Access Service Edge Ppt Icon Outfit PDF
This slide depicts the budget calculation for implementing a secure access service edge model in an organization. The purpose of this slide is to showcase the estimated and actual cost and variance for SASE model spending. The key components include SD-WAN, SWG, ZTNA, CASB, and FWaaS. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Budget To Implement Secure Access Service Edge Ppt Icon Outfit PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Budget To Implement Secure Access Service Edge Ppt Icon Outfit PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Securing Data Over Google Cloud Google Cloud Computing System Professional PDF
This slide represents what measures are taken to secure the data stored on the Google Cloud, including IAM, data encryption, authentication, and bucket lock.Presenting Securing Data Over Google Cloud Google Cloud Computing System Professional PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Access Management, Protect Information, Compute Engine. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
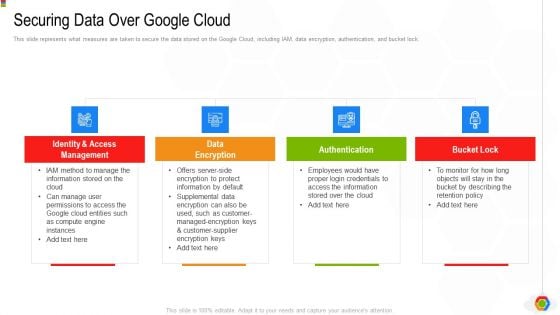
Google Cloud Console IT Securing Data Over Google Cloud Ppt Pictures Slides PDF
This slide represents what measures are taken to secure the data stored on the Google Cloud, including IAM, data encryption, authentication, and bucket lock. This is a google cloud console it securing data over google cloud ppt pictures slides pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like identity and access management, data encryption, authentication, bucket lock. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Web Access Control Solution 30 60 90 Days Plan To Integrate Secure Web Gateway Into Organizational
This slide represents 30-60-90 plan to implement Secure Web Gateway into firm. The purpose of this slide is to illustrate the plans of the first 90 days from the start, including steps to be followed at interval of one month. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Web Access Control Solution 30 60 90 Days Plan To Integrate Secure Web Gateway Into Organizational will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide represents 30-60-90 plan to implement Secure Web Gateway into firm. The purpose of this slide is to illustrate the plans of the first 90 days from the start, including steps to be followed at interval of one month.

Google Cloud Computing System Securing Data Over Google Cloud Microsoft PDF
This slide represents what measures are taken to secure the data stored on the Google Cloud, including IAM, data encryption, authentication, and bucket lock. Presenting Google Cloud Computing System Securing Data Over Google Cloud Microsoft PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Access Management, Data Encryption, Authentication. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Reverse Proxy Server IT Secure Client Connection To Proxy Server Ppt Icon Graphics Template PDF
This slide represents the secure client connection to the proxy server and is effective for a little or no risk for data transmission between networks. This is a reverse proxy server it secure client connection to proxy server ppt icon graphics template pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like server, proxy, cache. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
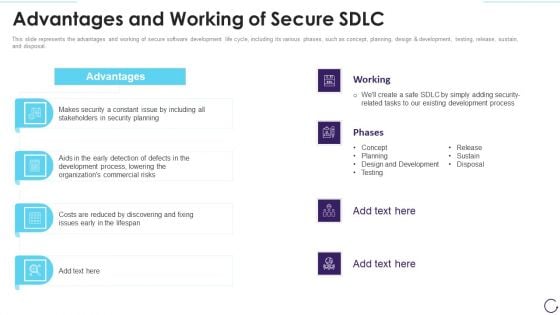
Application Development Life Cycle Advantages And Working Of Secure Sdlc Microsoft PDF
This slide represents the advantages and working of secure software development life cycle, including its various phases, such as concept, planning, design and development, testing, release, sustain, and disposal. Presenting 30 60 90 days plan for software development life cycle structure pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like advantages and working of secure sdlc. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Securing Market Leadership Through Competitive Excellence Table Of Contents Portrait PDF
Whether you have daily or monthly meetings, a brilliant presentation is necessary. Securing Market Leadership Through Competitive Excellence Table Of Contents Portrait PDF can be your best option for delivering a presentation. Represent everything in detail using Securing Market Leadership Through Competitive Excellence Table Of Contents Portrait PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Web Access Control Solution Steps To Select Next Generation Secure Web Gateway
This slide demonstrates the points to be kept in mind while choosing next generation secure web gateway. The purpose of this slide is to explain how to select a next generation SWG. These are adopt real cloud architecture, adapts to new threats, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Web Access Control Solution Steps To Select Next Generation Secure Web Gateway can be your best option for delivering a presentation. Represent everything in detail using Web Access Control Solution Steps To Select Next Generation Secure Web Gateway and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide demonstrates the points to be kept in mind while choosing next generation secure web gateway. The purpose of this slide is to explain how to select a next generation SWG. These are adopt real cloud architecture, adapts to new threats, etc.
Global Market Of Secure Access Service Edge Ppt Icon Shapes PDF
This slide depicts the global market size of the SASE market by components such as platforms and services. The purpose of this slide is to showcase the compound annual growth rate for the SASE model, including its growth drivers, such as cloud adoption, work-from-anywhere culture, and so on. Create an editable Global Market Of Secure Access Service Edge Ppt Icon Shapes PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Global Market Of Secure Access Service Edge Ppt Icon Shapes PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
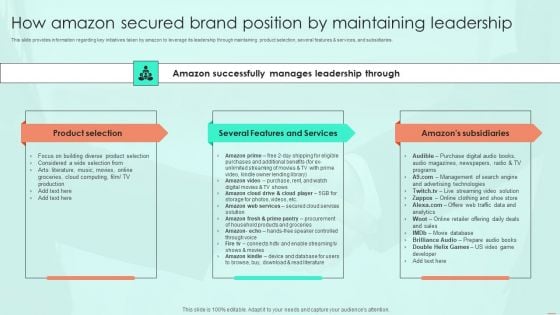
How Amazon Secured Brand Position By Maintaining Leadership Ppt PowerPoint Presentation File Model PDF
This slide provides information regarding key initiatives taken by amazon to leverage its leadership through maintaining product selection, several features and services, and subsidiaries. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give How Amazon Secured Brand Position By Maintaining Leadership Ppt PowerPoint Presentation File Model PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable How Amazon Secured Brand Position By Maintaining Leadership Ppt PowerPoint Presentation File Model PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today

Comparative Analysis Of Encryption And Tokenization In Ds Securing Your Data Ppt Presentation
This slide represents the comparison of encryption and tokenization. The purpose of this slide is to highlight different components of comparison such as definition, importance, objective, and so on Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Comparative Analysis Of Encryption And Tokenization In Ds Securing Your Data Ppt Presentation With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Comparative Analysis Of Encryption And Tokenization In Ds Securing Your Data Ppt Presentation today and make your presentation stand out from the rest This slide represents the comparison of encryption and tokenization. The purpose of this slide is to highlight different components of comparison such as definition, importance, objective, and so on

Overview And Importance Of Secure SDLC Phases Of Software Development Procedure Structure PDF
This slide represents the overview of the software development life cycle, including its goal, international standard, way of creating, designing, and developing software.Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Overview And Importance Of Secure SDLC Phases Of Software Development Procedure Structure PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Overview And Importance Of Secure SDLC Phases Of Software Development Procedure Structure PDF.

Securing Market Leadership Through Competitive Excellence Company Overview Five Guys Designs PDF
The following slide exhibits complete overview of Five Guys company related to food industry. Information covered in this slide is related to companys mission statement, major stakeholders, products offered, key details and facts and figures. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Securing Market Leadership Through Competitive Excellence Company Overview Five Guys Designs PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Securing Market Leadership Through Competitive Excellence Company Overview Five Guys Designs PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
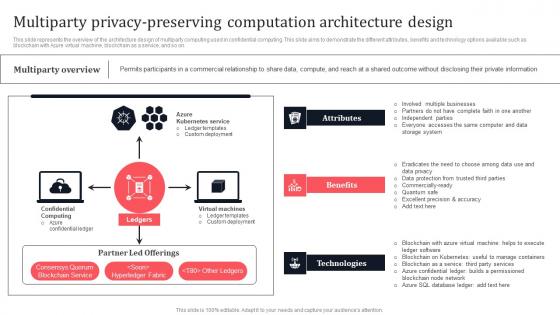
Multiparty Privacy Preserving Computation Architecture Design Secure Multi Party Demonstration Pdf
This slide represents the overview of the architecture design of multiparty computing used in confidential computing. This slide aims to demonstrate the different attributes, benefits and technology options available such as blockchain with Azure virtual machine, blockchain as a service, and so on. Create an editable Multiparty Privacy Preserving Computation Architecture Design Secure Multi Party Demonstration Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Multiparty Privacy Preserving Computation Architecture Design Secure Multi Party Demonstration Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide represents the overview of the architecture design of multiparty computing used in confidential computing. This slide aims to demonstrate the different attributes, benefits and technology options available such as blockchain with Azure virtual machine, blockchain as a service, and so on.
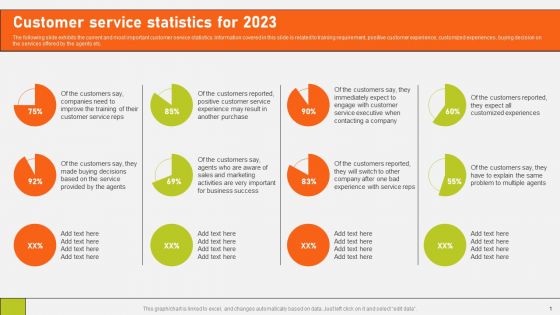
Securing Market Leadership Through Competitive Excellence Customer Service Statistics For 2023 Infographics PDF
The following slide exhibits the current and most important customer service statistics. Information covered in this slide is related to training requirement, positive customer experience, customized experiences, buying decision on the services offered by the agents etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Securing Market Leadership Through Competitive Excellence Customer Service Statistics For 2023 Infographics PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
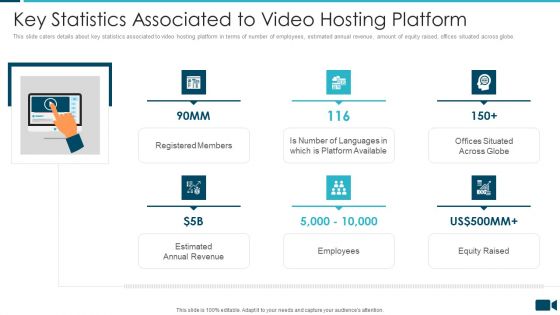
Secured Video Hosting Platform Investor Capital Funding Key Statistics Associated To Video Hosting Platform Rules PDF
This slide caters details about key statistics associated to video hosting platform in terms of number of employees, estimated annual revenue, amount of equity raised, offices situated across globe. Presenting secured video hosting platform investor capital funding key statistics associated to video hosting platform rules pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like registered members, employees, equity raised, estimated annual revenue. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Secured Video Hosting Platform Investor Capital Funding Future Initiatives By Online Video Hosting Platform Sample PDF
This slide caters details about future initiatives by online video hosting platform that will focus on leveraging relationships with members or clients or subscribers across globe. This is a secured video hosting platform investor capital funding future initiatives by online video hosting platform sample pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like future initiatives by online video hosting platform. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
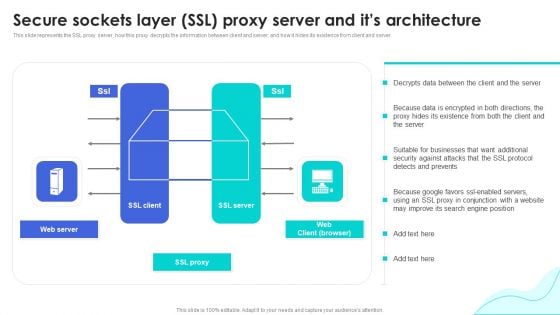
Reverse Proxy Web Server Secure Sockets Layer Ssl Proxy Server And Its Architecture Rules PDF
This slide represents the SSL proxy server, how this proxy decrypts the information between client and server, and how it hides its existence from client and server. Boost your pitch with our creative Reverse Proxy Web Server Secure Sockets Layer Ssl Proxy Server And Its Architecture Rules PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you dont have to invest time in any additional work. Just grab the template now and use them.
Confidential Computing Architecture Based On Azure Services Secure Multi Party Icons Pdf
This slide represents the architecture of confidential computing based on Azure confidential computing services. The purpose of this slide is to showcase the problems with typical approaches and confidential computing solutions. It also includes the architecture components such as sensitive data, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Confidential Computing Architecture Based On Azure Services Secure Multi Party Icons Pdf With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Confidential Computing Architecture Based On Azure Services Secure Multi Party Icons Pdf today and make your presentation stand out from the rest. This slide represents the architecture of confidential computing based on Azure confidential computing services. The purpose of this slide is to showcase the problems with typical approaches and confidential computing solutions. It also includes the architecture components such as sensitive data, etc.
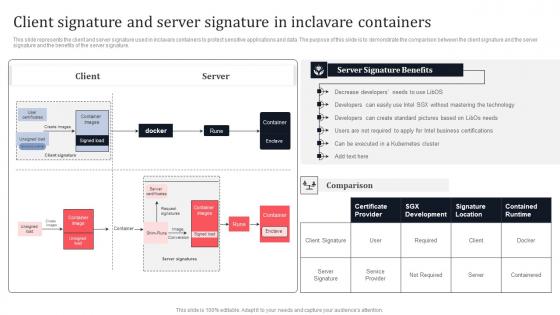
Client Signature And Server Signature In Inclavare Containers Secure Multi Party Mockup Pdf
This slide represents the client and server signature used in inclavare containers to protect sensitive applications and data. The purpose of this slide is to demonstrate the comparison between the client signature and the server signature and the benefits of the server signature. Want to ace your presentation in front of a live audience Our Client Signature And Server Signature In Inclavare Containers Secure Multi Party Mockup Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide represents the client and server signature used in inclavare containers to protect sensitive applications and data. The purpose of this slide is to demonstrate the comparison between the client signature and the server signature and the benefits of the server signature.
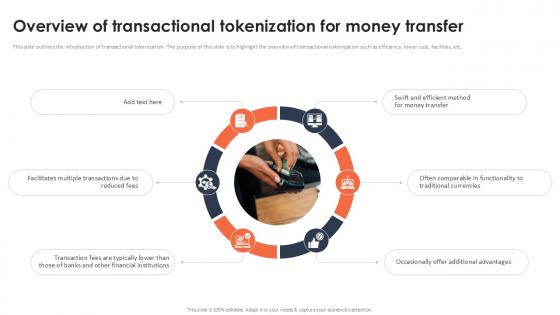
Overview Of Transactional Tokenization For Money Transfer Securing Your Data Ppt Sample
This slide outlines the introduction of transactional tokenization. The purpose of this slide is to highlight the overview of transactional tokenization such as efficiency, lower cost, facilities, etc. Take your projects to the next level with our ultimate collection of Overview Of Transactional Tokenization For Money Transfer Securing Your Data Ppt Sample Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest This slide outlines the introduction of transactional tokenization. The purpose of this slide is to highlight the overview of transactional tokenization such as efficiency, lower cost, facilities, etc.
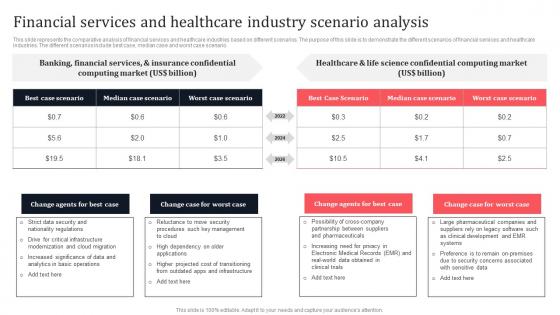
Financial Services And Healthcare Industry Scenario Analysis Secure Multi Party Sample Pdf
This slide represents the comparative analysis of financial services and healthcare industries based on different scenarios. The purpose of this slide is to demonstrate the different scenarios of financial services and healthcare industries. The different scenarios include best case, median case and worst case scenario. The Financial Services And Healthcare Industry Scenario Analysis Secure Multi Party Sample Pdf is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide represents the comparative analysis of financial services and healthcare industries based on different scenarios. The purpose of this slide is to demonstrate the different scenarios of financial services and healthcare industries. The different scenarios include best case, median case and worst case scenario.

Online Venue Advertising Plan Hyundai Venue Campaign For Securing Millennial Influencers Strategy SS V
This slide represents the case study of Hyundai Venue Take On The City Campaign in order to provide understanding of real life use of venue marketing. It includes details related to challenges, strategy implemented and results of Hyundai venue Take on the city campaign. Present like a pro with Online Venue Advertising Plan Hyundai Venue Campaign For Securing Millennial Influencers Strategy SS V. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide represents the case study of Hyundai Venue Take On The City Campaign in order to provide understanding of real life use of venue marketing. It includes details related to challenges, strategy implemented and results of Hyundai venue Take on the city campaign.
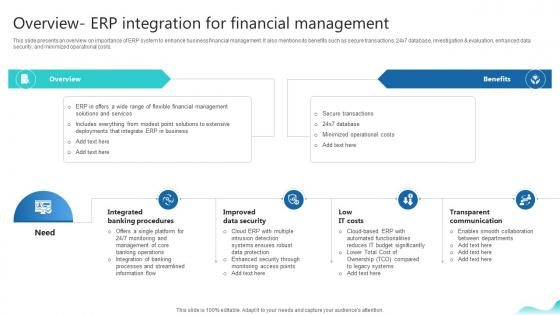
Overview Erp Integration For Financial Management Erp And Digital Transformation For Maximizing DT SS V
This slide presents an overview on importance of ERP system to enhance business financial management. It also mentions its benefits such as secure transactions, 24x7 database, investigation and evaluation, enhanced data security, and minimized operational costs.The Overview Erp Integration For Financial Management Erp And Digital Transformation For Maximizing DT SS V is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide presents an overview on importance of ERP system to enhance business financial management. It also mentions its benefits such as secure transactions, 24x7 database, investigation and evaluation, enhanced data security, and minimized operational costs.
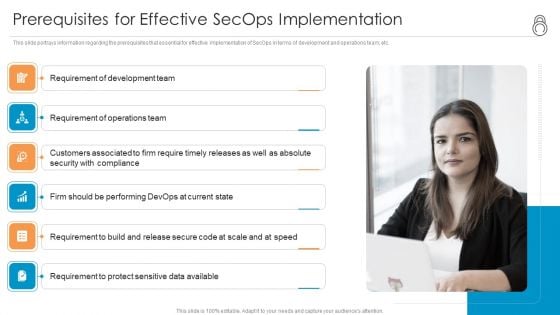
Enhanced Protection Corporate Event Administration Prerequisites For Effective Secops Implementation Inspiration PDF
This slide portrays information regarding the prerequisites that essential for effective implementation of SecOps in terms of development and operations team, etc. This is a enhanced protection corporate event administration prerequisites for effective secops implementation inspiration pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like development, data available, security with compliance, operations team. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
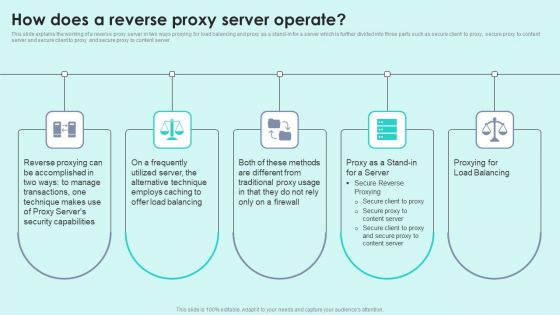
How Does A Reverse Proxy Server Operate Reverse Proxy For Load Balancing Infographics PDF
This slide explains the working of a reverse proxy server in two ways proxying for load balancing and proxy as a stand-in for a server which is further divided into three parts such as secure client to proxy, secure proxy to content server and secure client to proxy and secure proxy to content server.This is a How Does A Reverse Proxy Server Operate Reverse Proxy For Load Balancing Infographics PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Reverse Proxying, Accomplished Transactions, Technique Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
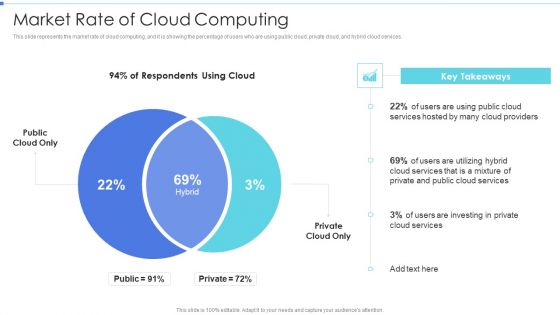
Cloud Based Service Models Market Rate Of Cloud Computing Diagrams PDF
This slide depicts the overview of the cloud service provider company, including its functionality, number of customers and partners, security, and operational expertise.This is a Cloud Based Service Models Market Rate Of Cloud Computing Diagrams PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Most Functionality, Largest Community, Operational Expertise. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
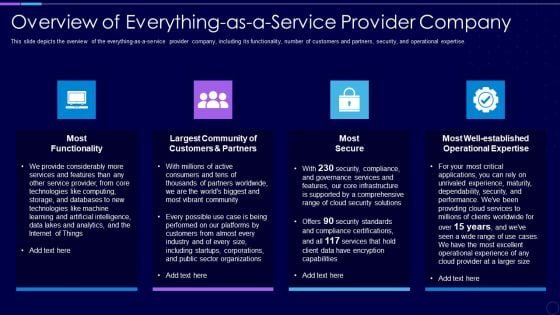
Overview Of Everything As A Service Provider Company Professional PDF
This slide depicts the overview of the everything as a service provider company, including its functionality, number of customers and partners, security, and operational expertise. This is a overview of everything as a service provider company professional pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like technologies, community, security, services. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Computing Services Overview Of Cloud Service Provider Company Rules PDF
This slide depicts the overview of the cloud service provider company, including its functionality, number of customers and partners, security, and operational expertise. This is a Cloud Computing Services Overview Of Cloud Service Provider Company Rules PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Most Functionality, Most Secure, Largest Community, Customers And Partners. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
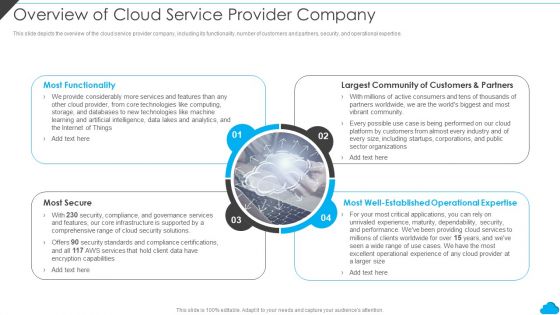
Cloud Distribution Service Models Overview Of Cloud Service Provider Company Inspiration PDF
This slide depicts the overview of the cloud service provider company, including its functionality, number of customers and partners, security, and operational expertise. Presenting Cloud Distribution Service Models Overview Of Cloud Service Provider Company Inspiration PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Largest Community, Most Functionality, Most Secure. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Overview Of Everything As A Service Xaas Cloud Computing Models Ppt PowerPoint Presentation Ideas Guide PDF
This slide depicts the overview of the everything as a service provider company, including its functionality, number of customers and partners, security, and operational expertise.This is a Overview Of Everything As A Service Xaas Cloud Computing Models Ppt PowerPoint Presentation Ideas Guide PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Most Functionality, Largest Community, Most Secure. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.


 Continue with Email
Continue with Email

 Home
Home


































