Security Operations

Working Areas Of Telecom Cost Management Portrait PDF
This slide shows areas to deploy telecom expense management initiative that ensure financial and operational efficiency in business. It includes various disciplines such as design, optimization, inventory, financial , security management etc. Persuade your audience using this Working Areas Of Telecom Cost Management Portrait PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Security Management, Contract Management, Financial Management. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
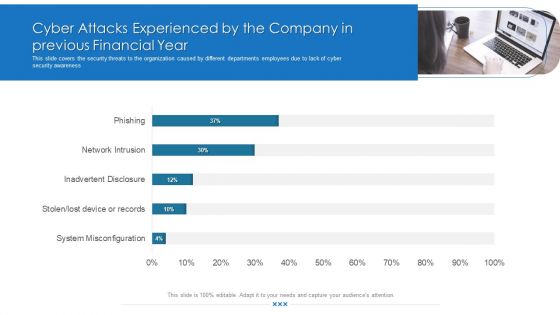
Cyber Attacks Experienced By The Company In Previous Financial Year Download PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. Deliver and pitch your topic in the best possible manner with this cyber attacks experienced by the company in previous financial year download pdf. Use them to share invaluable insights on cyber attacks experienced by the company in previous financial year and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
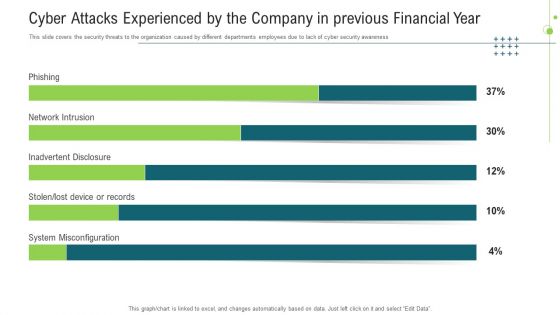
Cyber Attacks Experienced By The Company In Previous Financial Year Ppt Infographics PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. Deliver an awe inspiring pitch with this creative cyber attacks experienced by the company in previous financial year ppt infographics pdf bundle. Topics like cyber attacks experienced by the company in previous financial year can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
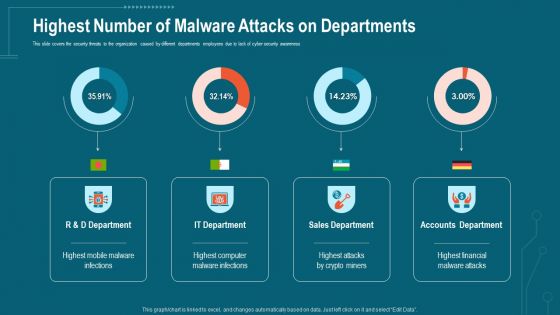
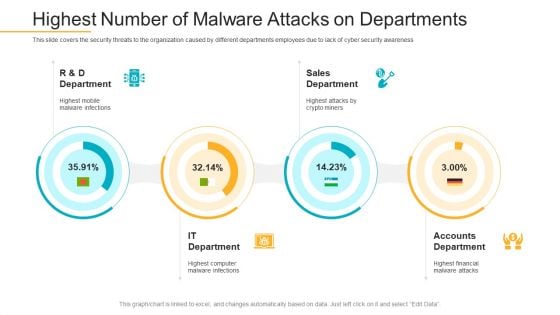
Companys Data Safety Recognition Highest Number Of Malware Attacks On Departments Sample PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. Deliver an awe-inspiring pitch with this creative companys data safety recognition highest number of malware attacks on departments sample pdf bundle. Topics like sales department, accounts department, it department can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
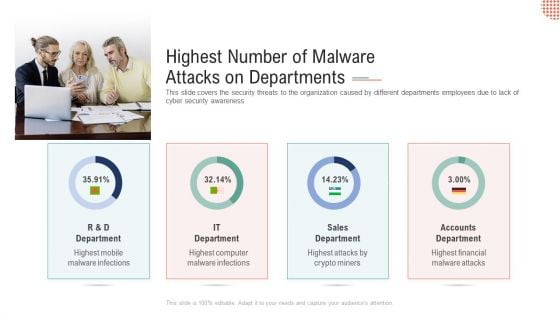
Highest Number Of Malware Attacks On Departments Ppt Inspiration Deck PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness Deliver an awe-inspiring pitch with this creative highest number of malware attacks on departments ppt inspiration deck pdf. bundle. Topics like r ans d department, sales department, accounts department can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Data Breach Prevention Recognition Highest Number Of Malware Attacks On Departments Pictures PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. Deliver and pitch your topic in the best possible manner with this data breach prevention recognition highest number of malware attacks on departments pictures pdf. Use them to share invaluable insights on sales department, accounts department, it department and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
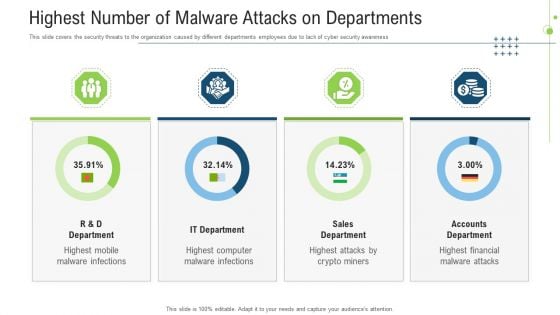
Highest Number Of Malware Attacks On Departments Ppt Gallery Ideas PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. Deliver an awe inspiring pitch with this creative highest number of malware attacks on departments ppt gallery ideas pdf bundle. Topics like accounts department, sales department, it department can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
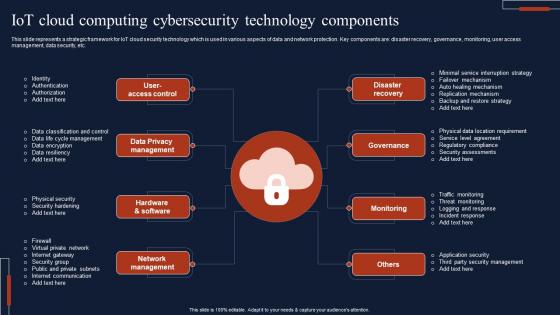
IOT Cloud Computing Cybersecurity Technology Components Template Pdf
This slide represents a strategic framework for IoT cloud security technology which is used in various aspects of data and network protection. Key components are disaster recovery, governance, monitoring, user access management, data security, etc. Pitch your topic with ease and precision using this IOT Cloud Computing Cybersecurity Technology Components Template Pdf This layout presents information on Privacy Management, Hardware And Software, Network Management It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide represents a strategic framework for IoT cloud security technology which is used in various aspects of data and network protection. Key components are disaster recovery, governance, monitoring, user access management, data security, etc.

Data Breach Prevention Strategies For Enterprises Data Fortification Strengthening Defenses
The purpose of this slide is to outline the data breach mitigation strategies for businesses. These include access control, encryption, web security solutions, network security, up-to-date software and hardware, preparation, training employees and users, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Data Breach Prevention Strategies For Enterprises Data Fortification Strengthening Defenses. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. The purpose of this slide is to outline the data breach mitigation strategies for businesses. These include access control, encryption, web security solutions, network security, up-to-date software and hardware, preparation, training employees and users, etc.
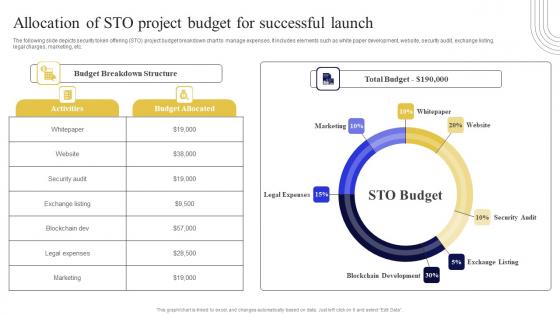
Allocation Of STO Project Budget For Exploring Investment Opportunities Demonstration Pdf
The following slide depicts security token offering STO project budget breakdown chart to manage expenses. It includes elements such as white paper development, website, security audit, exchange listing, legal charges, marketing, etc. Create an editable Allocation Of STO Project Budget For Exploring Investment Opportunities Demonstration Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Allocation Of STO Project Budget For Exploring Investment Opportunities Demonstration Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. The following slide depicts security token offering STO project budget breakdown chart to manage expenses. It includes elements such as white paper development, website, security audit, exchange listing, legal charges, marketing, etc.
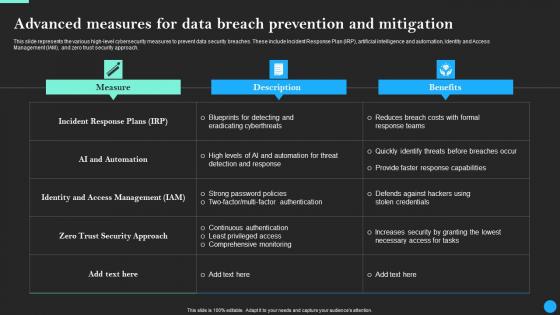
Advanced Measures For Data Breach Prevention Data Breach Prevention Inspiration Pdf
This slide represents the various high-level cybersecurity measures to prevent data security breaches. These include Incident Response Plan IRP, artificial intelligence and automation, Identity and Access Management IAM, and zero trust security approach. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Advanced Measures For Data Breach Prevention Data Breach Prevention Inspiration Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide represents the various high-level cybersecurity measures to prevent data security breaches. These include Incident Response Plan IRP, artificial intelligence and automation, Identity and Access Management IAM, and zero trust security approach.
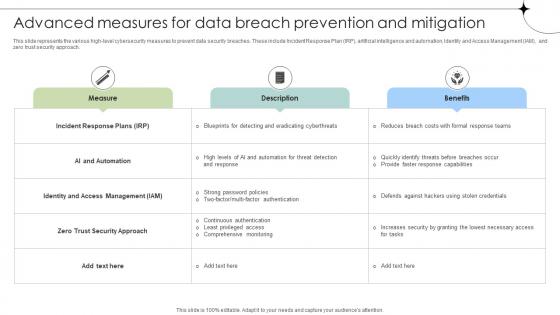
Advanced Measures For Data Breach Prevention And Mitigation Data Fortification Strengthening Defenses
This slide represents the various high-level cybersecurity measures to prevent data security breaches. These include Incident Response Plan IRP, artificial intelligence and automation, Identity and Access Management IAM, and zero trust security approach.Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Advanced Measures For Data Breach Prevention And Mitigation Data Fortification Strengthening Defenses for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide represents the various high-level cybersecurity measures to prevent data security breaches. These include Incident Response Plan IRP, artificial intelligence and automation, Identity and Access Management IAM, and zero trust security approach.

Cybersecurity Detail Impact Electronic Information Ppt Portfolio Rules PDF
This slide represents the current status of the cyber attacks in an organization after implementing the cyber security model. Deliver and pitch your topic in the best possible manner with this cybersecurity detail impact electronic information ppt portfolio rules pdf. Use them to share invaluable insights on detail impact electronic information security plan can reduce the risk of data breach in organization and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
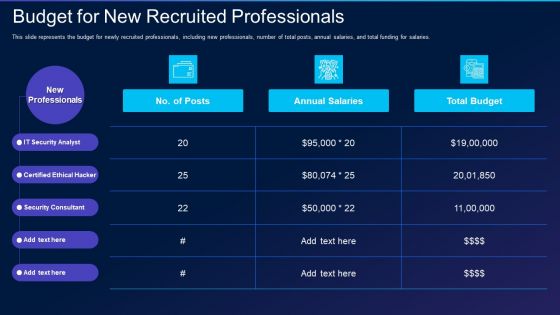
Cyber Exploitation IT Budget For New Recruited Professionals Demonstration PDF
This slide represents the budget for newly recruited professionals, including new professionals, number of total posts, annual salaries, and total funding for salaries. Deliver and pitch your topic in the best possible manner with this cyber exploitation it budget for new recruited professionals demonstration pdf. Use them to share invaluable insights on it security analyst, certified ethical hacker, security consultant and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Employee Upskilling Training Program Ppt Outline Layout Ideas PDF
Mentioned slide displays a five day employee upskilling training program that company will use to provide an in dept details about information security program activities and deliverables. Deliver and pitch your topic in the best possible manner with this employee upskilling training program ppt outline layout ideas pdf. Use them to share invaluable insights on security target, performance, risk, analysis and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
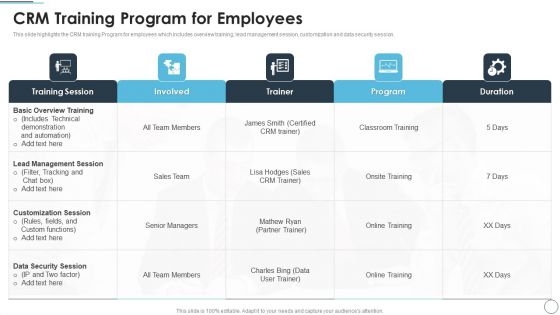
CRM Solutions Implementation Strategy CRM Training Program For Employees Diagrams PDF
This slide highlights the CRM training Program for employees which includes overview training, lead management session, customization and data security session.Deliver an awe inspiring pitch with this creative CRM Solutions Implementation Strategy CRM Solutions Implementation Strategy CRM Training Program For Employees Diagrams PDF bundle. Topics like Lead Management, Customization Session, Data Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Sales CRM Cloud Solutions Deployment CRM Training Program For Employees Graphics PDF
This slide highlights the CRM training Program for employees which includes overview training, lead management session, customization and data security session.Deliver an awe inspiring pitch with this creative Sales CRM Cloud Solutions Deployment CRM Training Program For Employees Graphics PDF bundle. Topics like Customization Session, Security Session, Overview Training can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
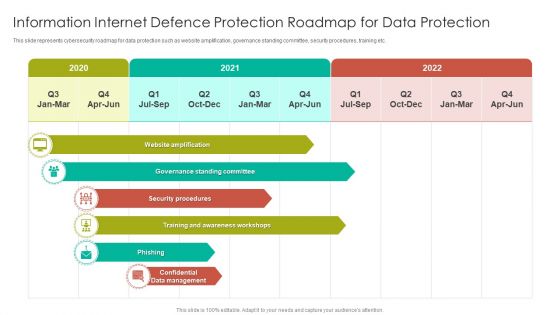
Information Internet Defence Protection Roadmap For Data Protection Topics PDF
This slide represents cybersecurity roadmap for data protection such as website amplification, governance standing committee, security procedures, training etc. Showcasing this set of slides titled Information Internet Defence Protection Roadmap For Data Protection Topics PDF. The topics addressed in these templates are Governance Standing, Security Procedures, Awareness Workshops. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting

Digitized Record Book Technology Pros And Cons Of Private Digital Ledger Download PDF
This slide represents the Pros and cons of the private blockchain framework based on factors such as speed, flexibility, trust-building, and security. Deliver an awe inspiring pitch with this creative digitized record book technology pros and cons of private digital ledger download pdf bundle. Topics like network, organization, data, lower security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
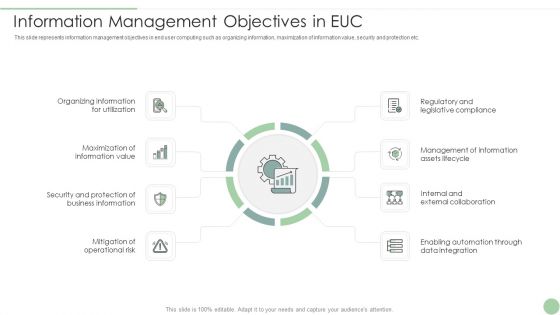
Information Management Objectives In EUC Ppt PowerPoint Presentation File Visuals PDF
This slide represents information management objectives in end user computing such as organizing information, maximization of information value, security and protection etc. Presenting Information Management Objectives In EUC Ppt PowerPoint Presentation File Visuals PDF to dispense important information. This template comprises eight stages. It also presents valuable insights into the topics including Organizing Information Utilization, Security And Protection, Business Information. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
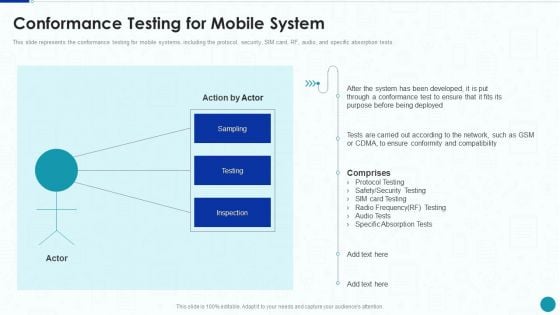
Compliance Testing IT Conformance Testing For Mobile System Microsoft PDF
This slide represents the conformance testing for mobile systems, including the protocol, security, SIM card, RF, audio, and specific absorption tests. Deliver an awe inspiring pitch with this creative Compliance Testing IT Conformance Testing For Mobile System Microsoft PDF bundle. Topics like Network, System, Security Testing can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
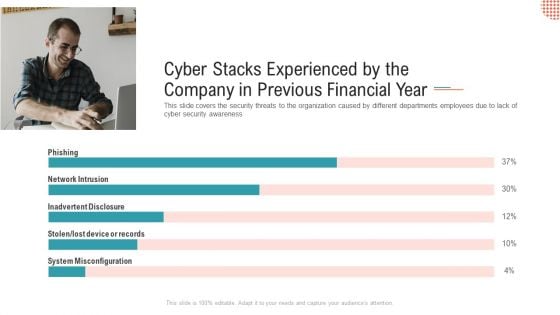
Cyber Stacks Experienced By The Company In Previous Financial Year Ppt Show Themes PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness Deliver and pitch your topic in the best possible manner with this cyber stacks experienced by the company in previous financial year ppt show themes pdf. Use them to share invaluable insights on network intrusion, inadvertent disclosure, system misconfiguration and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
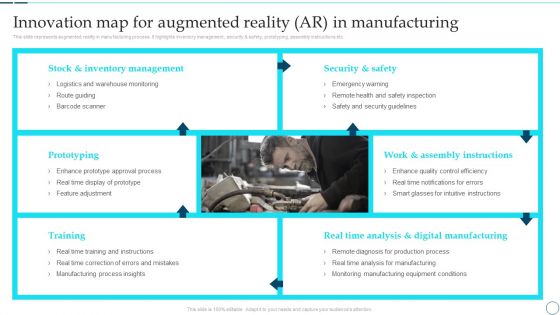
Deployment Of Smart Factory Solutions Innovation Map For Augmented Reality AR In Manufacturing Summary PDF
This slide represents augmented reality in manufacturing process. It highlights inventory management, security and safety, prototyping, assembly instructions etc. Deliver an awe inspiring pitch with this creative Deployment Of Smart Factory Solutions Innovation Map For Augmented Reality AR In Manufacturing Summary PDF bundle. Topics like Prototyping, Inventory Management, Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
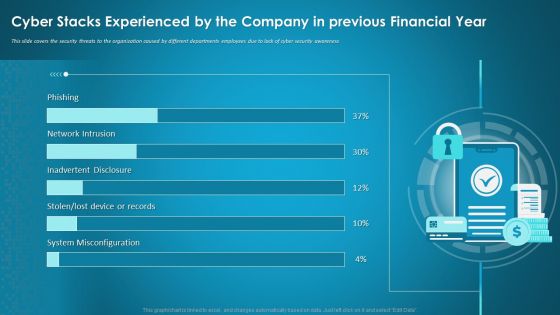
Cyber Stacks Experienced By The Company In Previous Financial Year Ppt Summary PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. Deliver an awe-inspiring pitch with this creative cyber stacks experienced by the company in previous financial year ppt summary pdf bundle. Topics like cyber stacks experienced by the company in previous financial year can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
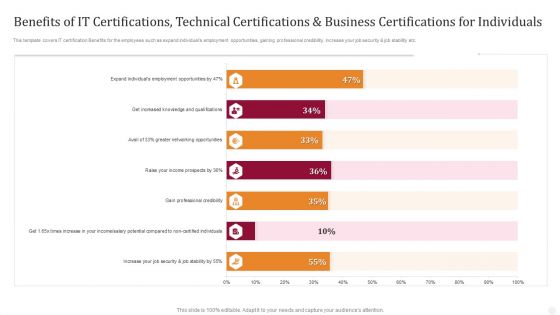
Benefits Of IT Certifications Technical Certifications And Business Certifications For Individuals Ideas PDF
This template covers IT certification Benefits for the employees such as expand individuals employment opportunities, gaining professional credibility, increase your job security job stability etc. Deliver an awe inspiring pitch with this creative Benefits Of IT Certifications Technical Certifications And Business Certifications For Individuals Ideas PDF bundle. Topics like Increase Security, Job Stability, Professional Credibility can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Data Center Infrastructure Management IT What Is A Data Center Designs PDF
This slide represents what a data center is, how they are managed, the type of information they store, and security and reliability of stored information. Deliver an awe inspiring pitch with this creative data center infrastructure management it what is a data center designs pdf bundle. Topics like organizations, intellectual resources, dependability, datacenter security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
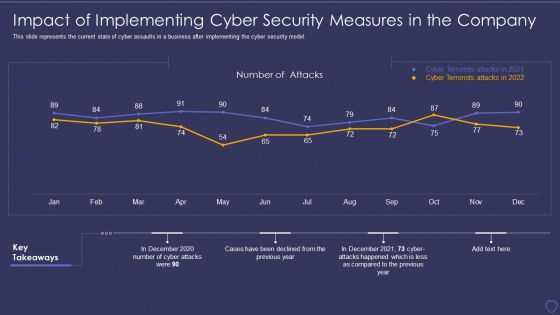
Global Cyber Terrorism Incidents On The Rise IT Impact Of Implementing Cyber Background PDF
This slide represents the current state of cyber assaults in a business after implementing the cyber security model. Deliver and pitch your topic in the best possible manner with this global cyber terrorism incidents on the rise it impact of implementing cyber background pdf. Use them to share invaluable insights on impact of implementing cyber security measures in the company and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Comparison Between ITIL V2 And ITIL V3 Ppt Outline Microsoft PDF
This slide represents the difference between ITIL v2 and ITIL v3, based on focus, approach, security management, number of processes, and functions. Deliver an awe inspiring pitch with this creative comparison between itil v2 and itil v3 ppt outline microsoft pdf bundle. Topics like product, process, management, security, strategy can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
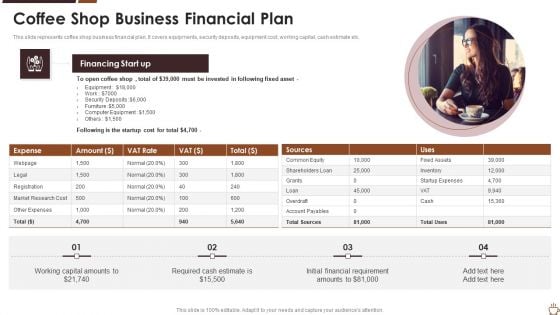
Coffee Shop Business Financial Plan Pictures PDF
This slide represents coffee shop business financial plan. It covers equipments, security deposits, equipment cost, working capital, cash estimate etc. Showcasing this set of slides titled coffee shop business financial plan pictures pdf. The topics addressed in these templates are security, financing, capital. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cloud Based Disaster Recovery Plan Slides PDF
This slide represents the cloud based disaster recovery plan and the various factors such as bandwidth, cloud storage, and security under consideration before implementing DR. Deliver an awe inspiring pitch with this creative Cloud Based Disaster Recovery Plan Slides PDF bundle. Topics like Information, Cloud Storage Prices, Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
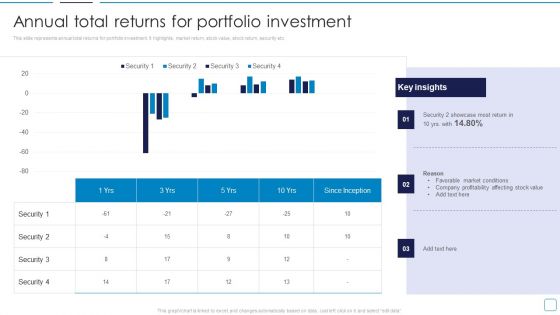
Portfolio Wealth Management Annual Total Returns For Portfolio Investment Designs PDF
This slide represents annual total returns for portfolio investment. It highlights, market return, stock value, stock return, security etc. Deliver and pitch your topic in the best possible manner with this Portfolio Wealth Management Annual Total Returns For Portfolio Investment Designs PDF. Use them to share invaluable insights on Security 2 Showcase, Favorable Market Conditions and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
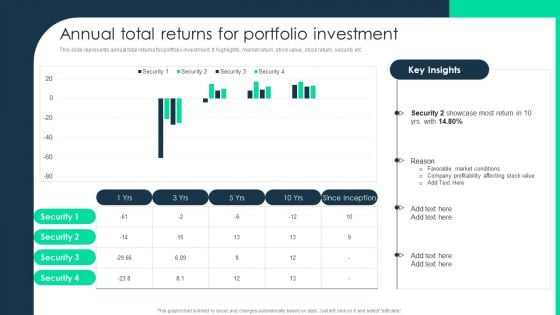
Annual Total Returns For Portfolio Investment Background PDF
This slide represents annual total returns for portfolio investment. It highlights, market return, stock value, stock return, security etc. Deliver and pitch your topic in the best possible manner with this Annual Total Returns For Portfolio Investment Background PDF. Use them to share invaluable insights on Security, Market Conditions, Stock Value and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
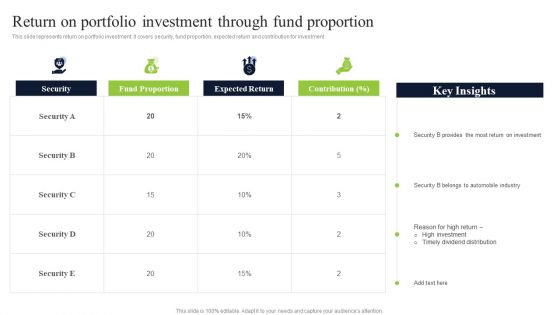
Diversified Profitable Portfolio Return On Portfolio Investment Through Fund Proportion Download PDF
This slide represents return on portfolio investment. It covers security, fund proportion, expected return and contribution for investment. Deliver an awe inspiring pitch with this creative Diversified Profitable Portfolio Return On Portfolio Investment Through Fund Proportion Download PDF bundle. Topics like Investment, Automobile Industry, Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Data Breach Prevention Implementation Budget Data Breach Prevention Ideas Pdf
This slide represents the estimated and actual cost of implementing data breach prevention measures in an organization. The cost categories are security software and tools, employee training, security consultants, data encryption, and network security. If you are looking for a format to display your unique thoughts, then the professionally designed Data Breach Prevention Implementation Budget Data Breach Prevention Ideas Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Data Breach Prevention Implementation Budget Data Breach Prevention Ideas Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide represents the estimated and actual cost of implementing data breach prevention measures in an organization. The cost categories are security software and tools, employee training, security consultants, data encryption, and network security.
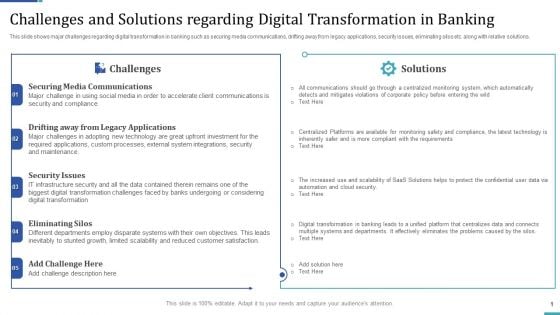
Industry Transformation Approaches Banking Sector Employee Development Challenges And Solutions Regarding Introduction PDF
This slide shows major challenges regarding digital transformation in banking such as securing media communications, drifting away from legacy applications, security issues, eliminating silos etc. along with relative solutions. Presenting industry transformation approaches banking sector employee development challenges and solutions regarding introduction pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like securing media communications, security issues, eliminating silos. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Other Cyber Strategies Of KPMG For Client Data Protection Structure PDF
This slide covers introduction to KPMG strategy related to operations for business transformation. The purpose of this template is to provide an overview based on benefits of KPMG operational strategies along with insights and key operations at KPMG. It includes operations such as advisory, tax and legal services, audit, etc. This modern and well-arranged Other Cyber Strategies Of KPMG For Client Data Protection Structure PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
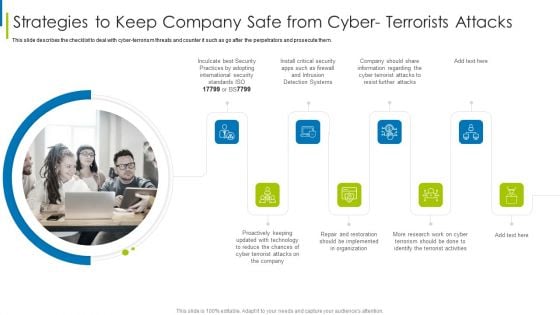
Cyber Terrorism Assault Strategies To Keep Company Safe From Cyber Terrorists Attacks Pictures PDF
This slide describes the checklist to deal with cyber terrorism threats and counter it such as go after the perpetrators and prosecute them.Presenting cyber terrorism assault strategies to keep company safe from cyber terrorists attacks pictures pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like inculcate best security, practices by adopting, international security In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
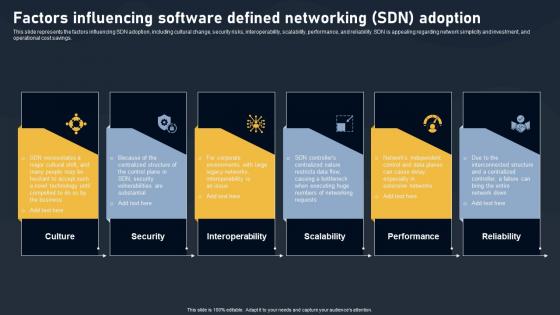
Factors Influencing Software Defined Networking Adoption SDN Building Blocks Template Pdf
This slide represents the factors influencing SDN adoption, including cultural change, security risks, interoperability, scalability, performance, and reliability. SDN is appealing regarding network simplicity and investment, and operational cost savings.Slidegeeks has constructed Factors Influencing Software Defined Networking Adoption SDN Building Blocks Template Pdf after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide represents the factors influencing SDN adoption, including cultural change, security risks, interoperability, scalability, performance, and reliability. SDN is appealing regarding network simplicity and investment, and operational cost savings.

Factors Influencing Software Defined Networking SDN Adoption Evolution Of SDN Controllers Slides Pdf
This slide represents the factors influencing SDN adoption, including cultural change, security risks, interoperability, scalability, performance, and reliability. SDN is appealing regarding network simplicity and investment, and operational cost savings. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Factors Influencing Software Defined Networking SDN Adoption Evolution Of SDN Controllers Slides Pdf and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide represents the factors influencing SDN adoption, including cultural change, security risks, interoperability, scalability, performance, and reliability. SDN is appealing regarding network simplicity and investment, and operational cost savings.

Major Roles And Responsibilities Of Financial Mitigating Corporate Scams And Robberies Topics Pdf
The following slide Major roles and responsibilities of financial security department . It includes information about risk level determination, laws and regulations, team training, operational compliance, automatic workflows, red flags, etc. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Major Roles And Responsibilities Of Financial Mitigating Corporate Scams And Robberies Topics Pdf from Slidegeeks and deliver a wonderful presentation. The following slide Major roles and responsibilities of financial security department . It includes information about risk level determination, laws and regulations, team training, operational compliance, automatic workflows, red flags, etc.

IoT Device Management Fundamentals Diagnostic Checks Performed By IoT Platform IoT Ss V
This slide provides diagnostic checks types to identify issues and block security threats. It includes diagnostic checks such as connectivity checks, auto update checks, operational status, key vault certificate accessibility, credentials store accessibility, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward IoT Device Management Fundamentals Diagnostic Checks Performed By IoT Platform IoT SS V template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal IoT Device Management Fundamentals Diagnostic Checks Performed By IoT Platform IoT SS V that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide provides diagnostic checks types to identify issues and block security threats. It includes diagnostic checks such as connectivity checks, auto update checks, operational status, key vault certificate accessibility, credentials store accessibility, etc.
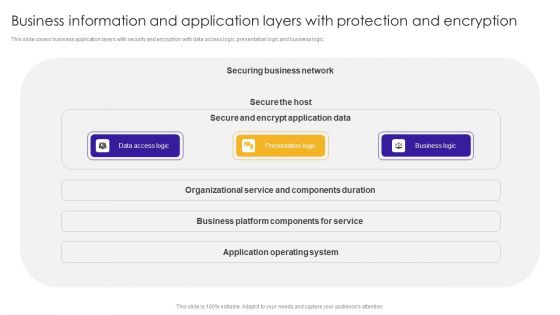
Business Information And Application Layers With Protection And Encryption Brochure PDF
This slide covers business application layers with security and encryption with data access logic, presentation logic and business logic.Pitch your topic with ease and precision using this Business Information And Application Layers With Protection And Encryption Brochure PDF. This layout presents information on Organizational Service, Components Duration, Operating System. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

ERP Powerpoint Ppt Template Bundles
Want to outdo your competitors Create a persuasive presentation template, pitch your business offerings, and win your clients using this well-structured ERP Powerpoint Ppt Template Bundles. Deploy this presentation template of colorful, graphical Education Sector, Health Care, Food Industry, Workflow Management, Resource Allocation slides that encourages a roomful of people to go through the entire proposal. Use this actionable PPT slide and highlight your company background, products, team, and experience to create the desired impact. Incorporate this presentation template and save time and effort in creating a presentation from scratch to highlight the uniqueness of your business. Download now. Enterprise Resource Planning ERP is a software system that support organizations in optimizing their key business processes, such as finance, HR, manufacturing, supply chain, sales, and procurement, by offering a unified perspective of operations and providing a unified data source. The purpose is to enhance operational efficiency, provide real-time data and insights and reduce operational expenses. This template includes ERP systems applications across various domains, security threats and prevention strategies, role of AI and major impacts.
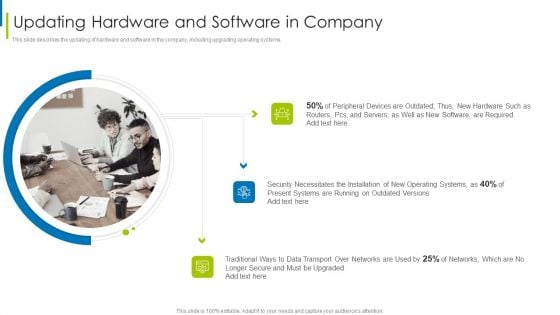
Cyber Terrorism Assault Updating Hardware And Software In Company Infographics PDF
This slide describes the updating of hardware and software in the company, including upgrading operating systems.Deliver an awe inspiring pitch with this creative cyber terrorism assault updating hardware and software in company infographics pdf bundle. Topics like peripheral devices, security necessitates, traditional ways to data transport can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
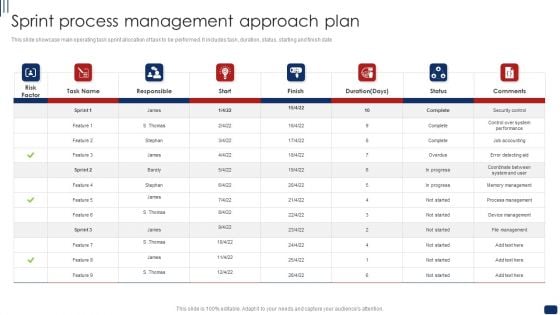
Sprint Process Management Approach Plan Ppt Portfolio Backgrounds PDF
This slide showcase main operating task sprint allocation of task to be performed. It includes task, duration, status, starting and finish date. Pitch your topic with ease and precision using this Sprint Process Management Approach Plan Ppt Portfolio Backgrounds PDF. This layout presents information on Risk Factor, Responsible, Security Control, Process Management. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
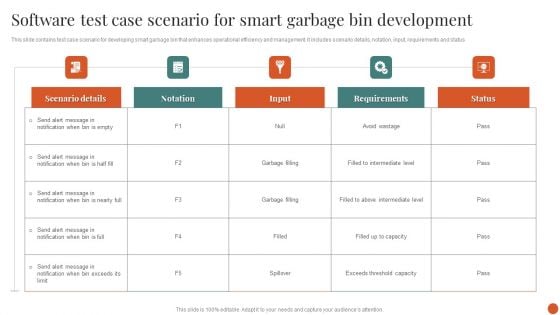
Software Test Case Scenario For Smart Garbage Bin Development Download PDF
This slide contains test case scenario for developing smart garbage bin that enhances operational efficiency and management. It includes scenario details, notation, input, requirements and status.Showcasing this set of slides titled Software Test Case Scenario For Smart Garbage Bin Development Download PDF. The topics addressed in these templates are Consuming Process, Personal Information, Security Standards. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
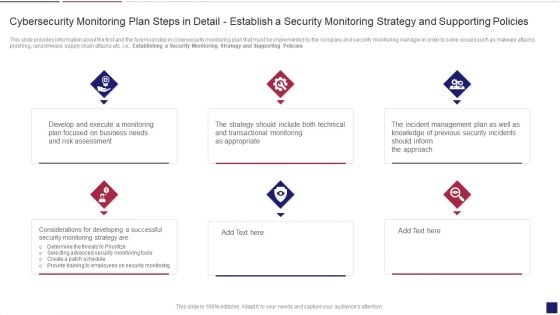
Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring Policies Inspiration PDF
This slide provides information about the first and the foremost step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Establishing a Security Monitoring Strategy and Supporting Policies. Presenting continuous development evaluation plan eliminate cyber attacks cybersecurity monitoring policies inspiration pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like cybersecurity monitoring plan steps in detail establish a security monitoring strategy and supporting policies. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
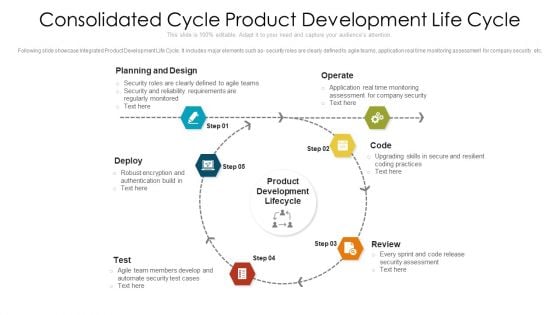
Consolidated Cycle Product Development Life Cycle Ppt PowerPoint Presentation File Show PDF
Following slide showcase Integrated Product Development Life Cycle. It includes major elements such as- security roles are clearly defined to agile teams, application real time monitoring assessment for company security etc. Presenting consolidated cycle product development life cycle ppt powerpoint presentation file show pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including planning and design, operate, deploy. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
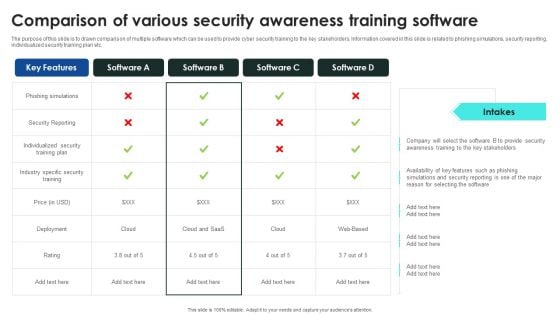
Implementing Cybersecurity Awareness Program To Prevent Attacks Comparison Of Various Ideas PDF
The purpose of this slide is to drawn comparison of multiple software which can be used to provide cyber security training to the key stakeholders. Information covered in this slide is related to phishing simulations, security reporting, individualized security training plan etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Implementing Cybersecurity Awareness Program To Prevent Attacks Comparison Of Various Ideas PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Implementing Cybersecurity Awareness Program To Prevent Attacks Comparison Of Various Ideas PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
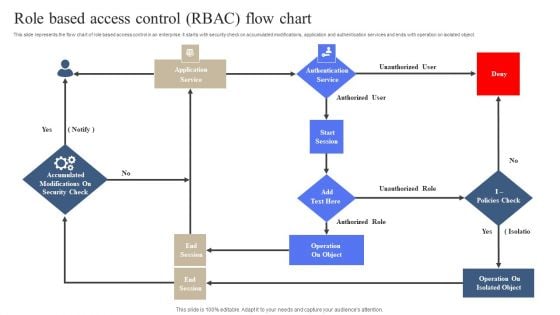
Role Based Access Control RBAC Flow Chart Slides PDF
This slide represents the flow chart of role based access control in an enterprise. It starts with security check on accumulated modifications, application and authentication services and ends with operation on isolated object. Persuade your audience using this Role Based Access Control RBAC Flow Chart Slides PDF. This PPT design covers One stage, thus making it a great tool to use. It also caters to a variety of topics including Operation On Object, Operation On Isolated Object. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
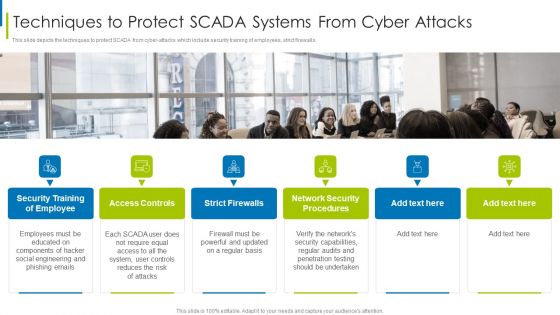
Cyber Terrorism Assault Techniques To Protect SCADA Systems From Cyber Attacks Demonstration PDF
This slide depicts the techniques to protect SCADA from cyber-attacks which include security training of employees, strict firewalls.Presenting cyber terrorism assault techniques to protect scada systems from cyber attacks demonstration pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like access controls, strict firewalls, network security procedures In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
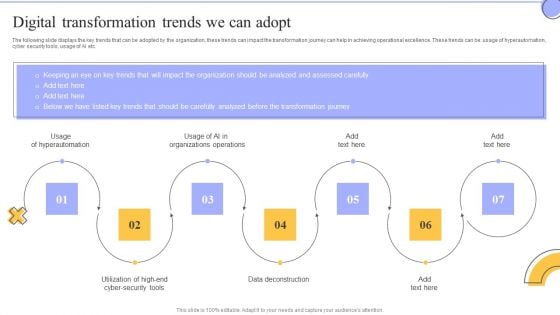
Change Administration Strategies Digital Transformation Trends We Can Adopt Demonstration PDF
The following slide displays the key trends that can be adopted by the organization, these trends can impact the transformation journey can help in achieving operational excellence. These trends can be usage of hyperautomation, cyber security tools, usage of AI etc. This is a Change Administration Strategies Digital Transformation Trends We Can Adopt Demonstration PDF template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Usage Hyperautomation, Data Deconstruction, Organizations Operations. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Executing Advance Data Analytics At Workspace Prerequisites For Firms Clipart PDF
This slide covers information regarding prerequisite required for firm in order to implement effective intelligence infrastructure implementation such as requirement of development and operations team, protection od sensitive data available, etc. This is a executing advance data analytics at workspace prerequisites for firms clipart pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like requirement, development, team, performing, operations. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
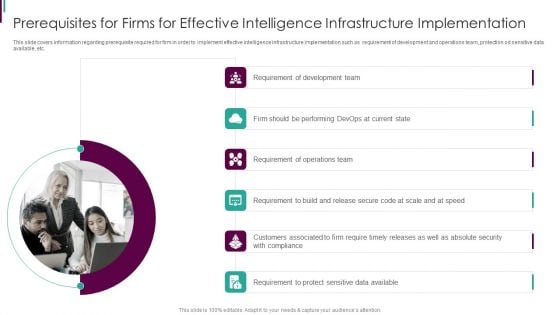
Developing Business Analytics Framework Prerequisites For Firms For Effective Intelligence Demonstration PDF
This slide covers information regarding prerequisite required for firm in order to implement effective intelligence infrastructure implementation such as requirement of development and operations team, protection od sensitive data available, etc.Presenting Developing Business Analytics Framework Prerequisites For Firms For Effective Intelligence Demonstration PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Requirement Development, Requirement Operations, Requirement Build In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Emerging Investment Opportunities In Green Financing Themes PDF
This slide brings forth the emerging investment opportunities for financial brands to shift their operations to attract new customers and retain old ones while protecting the planet and ensuring sustainable operations. Key elements are customer needs gap analysis, communication gap and in demand financial products Showcasing this set of slides titled Emerging Investment Opportunities In Green Financing Themes PDF. The topics addressed in these templates are Trust, Products, Analysis. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
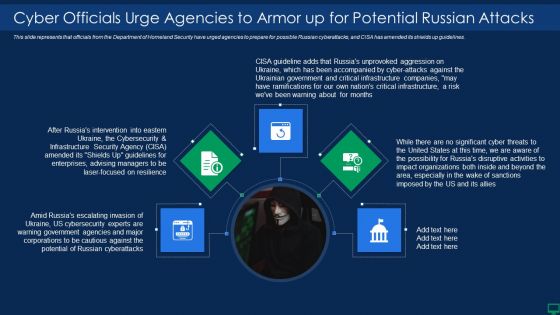
Russian Cyber Attacks On Ukraine IT Cyber Officials Urge Background PDF
This slide represents that officials from the Department of Homeland Security have urged agencies to prepare for possible Russian cyberattacks, and CISA has amended its shields up guidelines. Presenting russian cyber attacks on ukraine it cyber officials urge background pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like security, organizations, risk. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
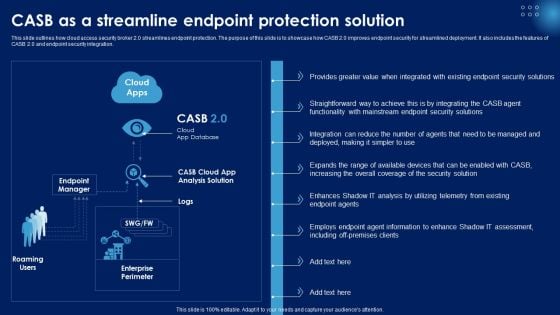
CASB As A Streamline Endpoint Protection Solution Ppt PowerPoint Presentation File Layouts PDF
This slide outlines how cloud access security broker 2.0 streamlines endpoint protection. The purpose of this slide is to showcase how CASB 2.0 improves endpoint security for streamlined deployment. It also includes the features of CASB 2.0 and endpoint security integration. Take your projects to the next level with our ultimate collection of CASB As A Streamline Endpoint Protection Solution Ppt PowerPoint Presentation File Layouts PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest.
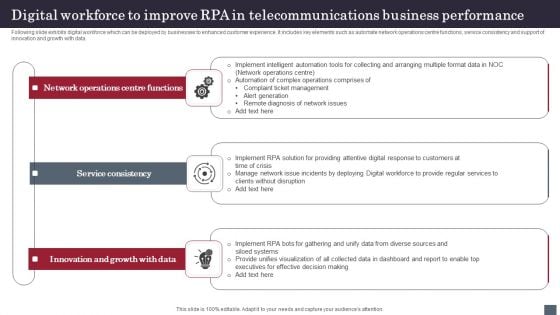
Digital Workforce To Improve RPA In Telecommunications Business Performance Mockup PDF
Following slide exhibits digital workforce which can be deployed by businesses to enhanced customer experience. It includes key elements such as automate network operations centre functions, service consistency and support of innovation and growth with data. Presenting Digital Workforce To Improve RPA In Telecommunications Business Performance Mockup PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Network Operations, Service Consistency, Innovation And Growth. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Checklist For Web Application Development Process Ppt Infographic Template Clipart Pdf
This slide represents the process checklist in order to develop web applications. It further includes activities such as design, UX, SEO checks, readability checks, performance checks, security checks, etc. Showcasing this set of slides titled Checklist For Web Application Development Process Ppt Infographic Template Clipart Pdf. The topics addressed in these templates are Readability Checks, Performance Checks, Security Checks. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide represents the process checklist in order to develop web applications. It further includes activities such as design, UX, SEO checks, readability checks, performance checks, security checks, etc.
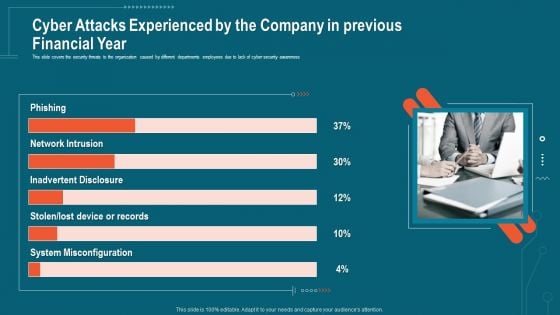
Companys Data Safety Recognition Cyber Attacks Experienced By The Company In Previous Financial Year Sample PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. This is a companys data safety recognition cyber attacks experienced by the company in previous financial year sample pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like system misconfiguration, inadvertent disclosure, network intrusion. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.


 Continue with Email
Continue with Email

 Home
Home


































