Security Operations
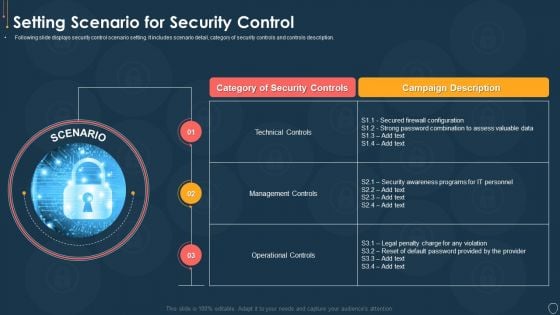
Cyber Security Risk Management Plan Setting Scenario For Security Control Microsoft PDF
Following slide displays security control scenario setting. It includes scenario detail, category of security controls and controls description. This is a cyber security risk management plan setting scenario for security control microsoft pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like category of security controls, campaign description, technical controls, management controls, operational controls. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Improving Restaurant Operations Objectives For Handling Restaurant Operations Effectively Ppt Visual Aids Pictures PDF
Presenting this set of slides with name improving restaurant operations objectives for handling restaurant operations effectively ppt visual aids pictures pdf. The topics discussed in these slides are efficient handling restaurant operations, managing restaurant staff, improving food and workplace safety standards. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
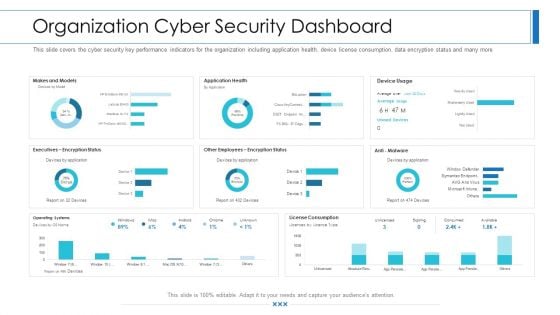
Workforce Security Realization Coaching Plan Organization Cyber Security Dashboard Template PDF
This slide covers the cyber security key performance indicators for the organization including application health, device license consumption, data encryption status and many more. Deliver an awe-inspiring pitch with this creative workforce security realization coaching plan organization cyber security dashboard template pdf bundle. Topics like makes and models, operating systems, encryption status, application health, license consumption can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
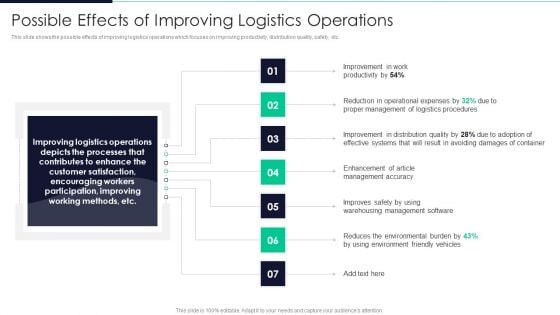
Developing Excellence In Logistics Operations Possible Effects Of Improving Logistics Operations Pictures PDF
This slide shows the possible effects of improving logistics operations which focuses on improving productivity, distribution quality, safety, etc.This is a Developing Excellence In Logistics Operations Possible Effects Of Improving Logistics Operations Pictures PDF template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Operational Expenses, Proper Management, Improvement Distribution You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
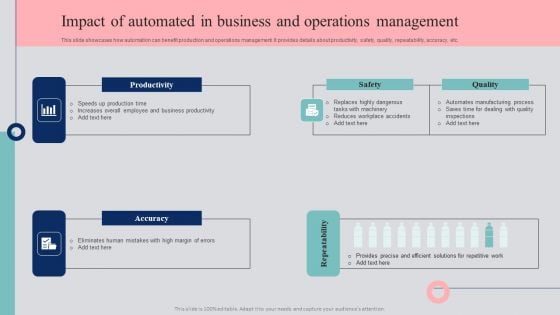
Automated Business Operations Management Impact Of Automated In Business And Operations Management Microsoft PDF
This slide showcases how automation can benefit production and operations management. It provides details about productivity, safety, quality, repeatability, accuracy, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Automated Business Operations Management Impact Of Automated In Business And Operations Management Microsoft PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
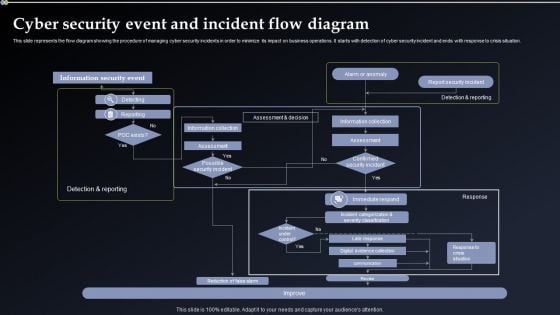
Deploying Cyber Security Incident Response Administration Cyber Security Event And Incident Portrait PDF
This slide represents the flow diagram showing the procedure of managing cyber security incidents in order to minimize its impact on business operations. It starts with detection of cyber security incident and ends with response to crisis situation. Welcome to our selection of the Deploying Cyber Security Incident Response Administration Cyber Security Event And Incident Portrait PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.
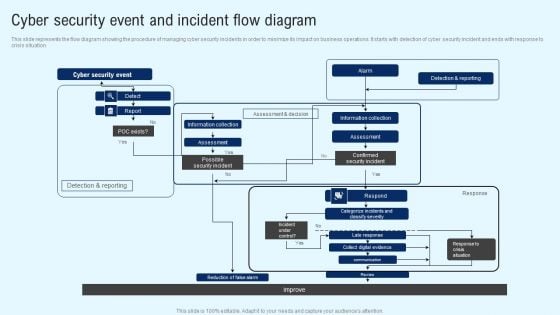
Implementing Cyber Security Incident Cyber Security Event And Incident Flow Diagram Download PDF
This slide represents the flow diagram showing the procedure of managing cyber security incidents in order to minimize its impact on business operations. It starts with detection of cyber security incident and ends with response to crisis situation. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Implementing Cyber Security Incident Cyber Security Event And Incident Flow Diagram Download PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Organizational Security Solutions Prerequisites For Effective Secops Implementation Summary PDF
This slide portrays information regarding the prerequisites that essential for effective implementation of SecOps in terms of development and operations team, etc. This is a organizational security solutions prerequisites for effective secops implementation summary pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like development, data available, security with compliance, operations team. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
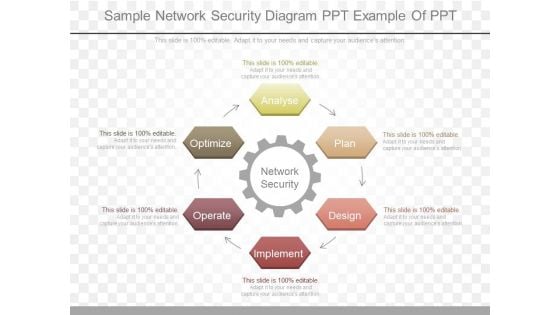
Sample Network Security Diagram Ppt Example Of Ppt
This is a sample network security diagram ppt example of ppt. This is a six stage process. The stages in this process are network security, analyse, plan, design, implement, operate, optimize.
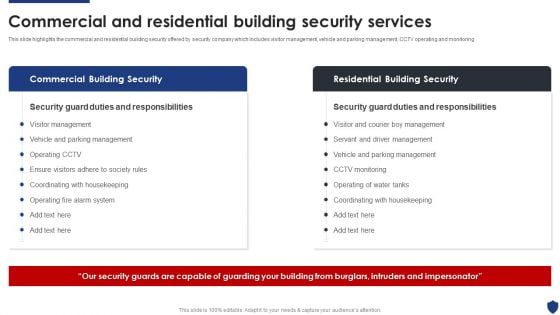
Security Officer Service Company Profile Commercial And Residential Building Security Services Clipart PDF
This slide highlights the commercial and residential building security offered by security company which includes visitor management, vehicle and parking management, CCTV operating and monitoring. Deliver an awe inspiring pitch with this creative Security Officer Service Company Profile Commercial And Residential Building Security Services Clipart PDF bundle. Topics like Commercial Building Security, Residential Building Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
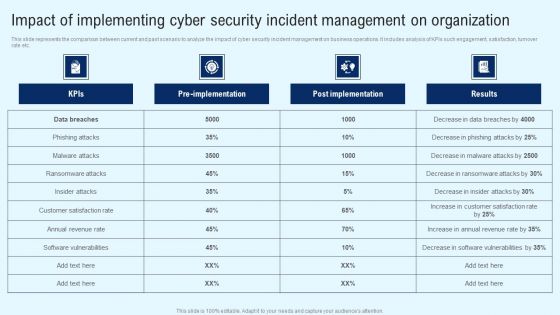
Implementing Cyber Security Incident Impact Of Implementing Cyber Security Incident Mockup PDF
This slide represents the comparison between current and past scenario to analyze the impact of cyber security incident management on business operations. It includes analysis of KPIs such engagement, satisfaction, turnover rate etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Implementing Cyber Security Incident Impact Of Implementing Cyber Security Incident Mockup PDF can be your best option for delivering a presentation. Represent everything in detail using Implementing Cyber Security Incident Impact Of Implementing Cyber Security Incident Mockup PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
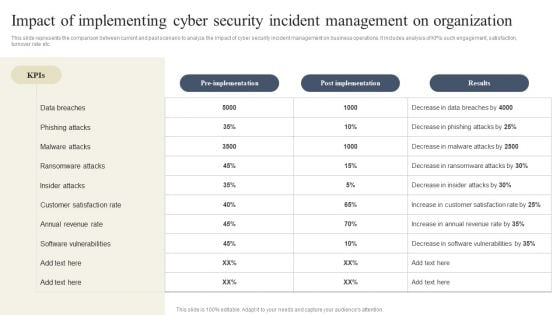
CYBER Security Breache Response Strategy Impact Of Implementing Cyber Security Incident Management Inspiration PDF
This slide represents the comparison between current and past scenario to analyze the impact of cyber security incident management on business operations. It includes analysis of KPIs such engagement, satisfaction, turnover rate etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download CYBER Security Breache Response Strategy Impact Of Implementing Cyber Security Incident Management Inspiration PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the CYBER Security Breache Response Strategy Impact Of Implementing Cyber Security Incident Management Inspiration PDF.
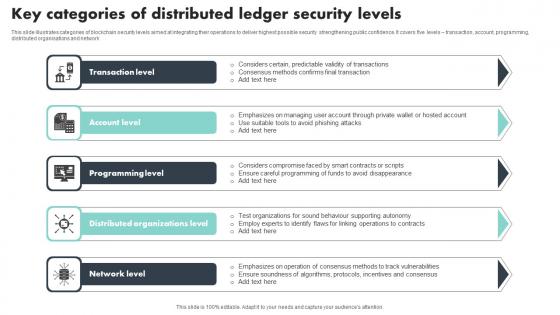
Key Categories Of Distributed Ledger Security Levels Portrait Pdf
This slide illustrates categories of blockchain security levels aimed at integrating their operations to deliver highest possible security strengthening public confidence. It covers five levels transaction, account, programming, distributed organisations and network Pitch your topic with ease and precision using this Key Categories Of Distributed Ledger Security Levels Portrait Pdf This layout presents information on Transaction Level, Account Level, Programming Level It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide illustrates categories of blockchain security levels aimed at integrating their operations to deliver highest possible security strengthening public confidence. It covers five levels transaction, account, programming, distributed organisations and network

Blockchain Business Methodology Impact On Business Operations Information PDF
This slide covers the details related to the advantages of blockchain technology for business. The purpose of this template is to defines blockchain as it helps to increase trust, security, transparency and bring other benefits to businesses. It includes details related to innovation, reduced cost, etc. Pitch your topic with ease and precision using this Blockchain Business Methodology Impact On Business Operations Information PDF. This layout presents information on Innovation, Security And Privacy, Tokenization, Cost. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
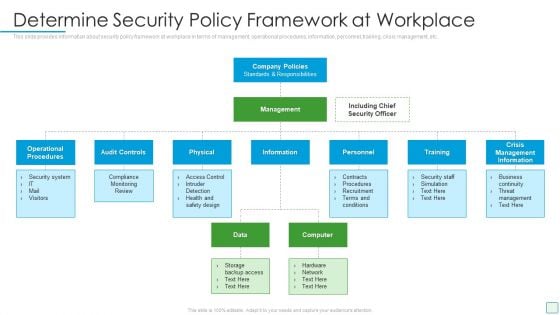
Developing Firm Security Strategy Plan Determine Security Policy Framework At Workplace Template PDF
This slide provides information about security policy framework at workplace in terms of management, operational procedures, information, personnel, training, crisis management, etc. Presenting developing firm security strategy plan determine security policy framework at workplace template pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like operational procedures, audit controls, physical, training, crisis management information. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
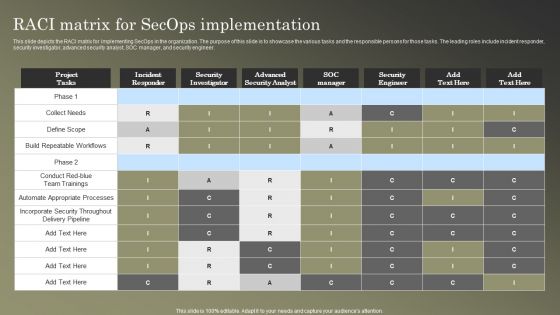
Cybersecurity Operations Cybersecops RAC Matrix For Secops Implementation Inspiration PDF
This slide depicts the RACI matrix for implementing SecOps in the organization. The purpose of this slide is to showcase the various tasks and the responsible persons for those tasks. The leading roles include incident responder, security investigator, advanced security analyst, SOC manager, and security engineer. Present like a pro with Cybersecurity Operations Cybersecops RAC Matrix For Secops Implementation Inspiration PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
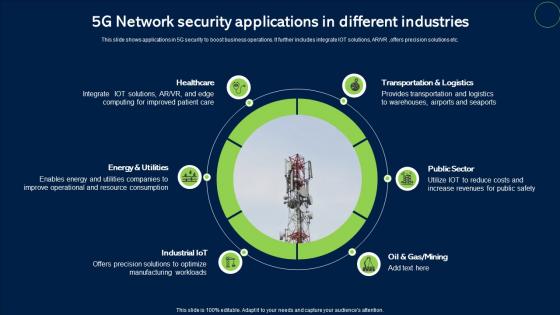
5G Network Security Applications In Different Industries Infographics Pdf
This slide shows applications in 5G security to boost business operations. It further includes integrate IOT solutions, ARVR ,offers precision solutions etc. Showcasing this set of slides titled 5G Network Security Applications In Different Industries Infographics Pdf. The topics addressed in these templates are Healthcare, Public Sector, Transportation And Logistics. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide shows applications in 5G security to boost business operations. It further includes integrate IOT solutions, ARVR ,offers precision solutions etc.
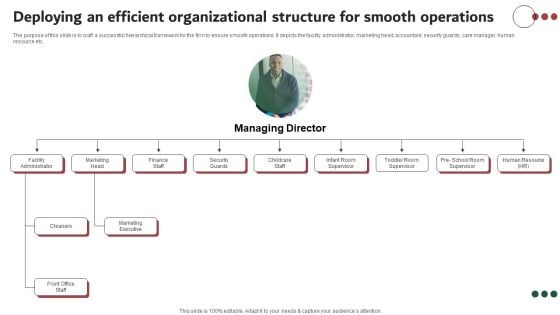
Deploying An Efficient Organizational Structure For Smooth Operations Summary PDF
The purpose of this slide is to craft a successful hierarchical framework for the firm to ensure smooth operations. It depicts the facility administrator, marketing head, accountant, security guards, care manager, human resource etc. Find a pre-designed and impeccable Deploying An Efficient Organizational Structure For Smooth Operations Summary PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
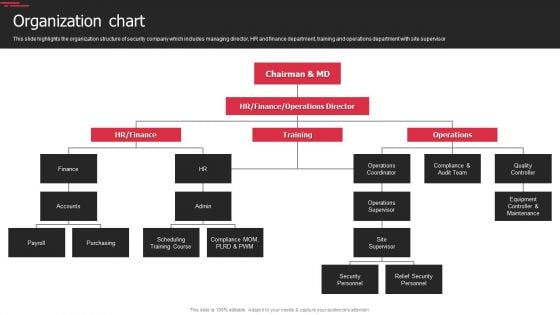
Security Agency Business Profile Organization Chart Topics PDF
This slide highlights the organization structure of security company which includes managing director, HR and finance department, training and operations department with site supervisor. This is a Security Agency Business Profile Organization Chart Topics PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Operations Supervisor, Security Personnel, Relief Security Personnel. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Virtual Security Hazards Detection And Response Topics Pdf
This slide illustrates ways to detect cyber security risks that emerge in business organizations and provides techniques to respond to such attacks. The response techniques are to reduce access time, optimize operations of security centre, adopt proactive cybersecurity and set intruder traps Showcasing this set of slides titled Virtual Security Hazards Detection And Response Topics Pdf. The topics addressed in these templates are Security Centre, Access Time, Cybersecurity. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide illustrates ways to detect cyber security risks that emerge in business organizations and provides techniques to respond to such attacks. The response techniques are to reduce access time, optimize operations of security centre, adopt proactive cybersecurity and set intruder traps

Managing Cyber Security In Manufacturing 30 Days Plan Diagrams PDF
This slide describes the first 30 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. Are you searching for a Managing Cyber Security In Manufacturing 30 Days Plan Diagrams PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Managing Cyber Security In Manufacturing 30 Days Plan Diagrams PDF from Slidegeeks today. This slide describes the first 30 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details.
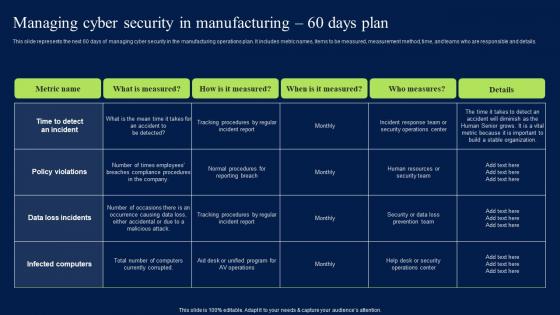
Managing Cyber Security In Manufacturing 60 Days Plan Mockup PDF
This slide represents the next 60 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. Retrieve professionally designed Managing Cyber Security In Manufacturing 60 Days Plan Mockup PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide represents the next 60 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details.
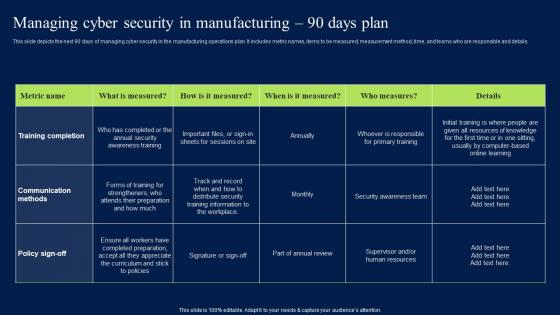
Managing Cyber Security In Manufacturing 90 Days Plan Professional PDF
This slide depicts the next 90 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, andteams who are responsible and details. Slidegeeks has constructed Managing Cyber Security In Manufacturing 90 Days Plan Professional PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide depicts the next 90 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details.
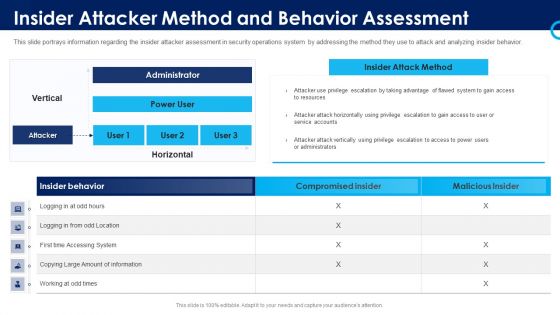
Organizational Security Solutions Insider Attacker Method And Behavior Assessment Introduction PDF
This slide portrays information regarding the insider attacker assessment in security operations system by addressing the method they use to attack and analyzing insider behavior. Deliver and pitch your topic in the best possible manner with this organizational security solutions insider attacker method and behavior assessment introduction pdf. Use them to share invaluable insights on insider attacker method and behaviour assessment and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
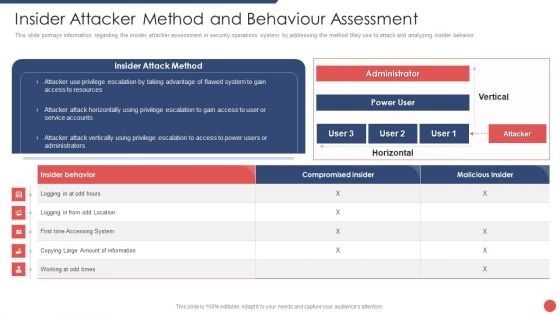
Security Functioning Centre Insider Attacker Method And Behaviour Assessment Ideas PDF
This slide portrays information regarding the insider attacker assessment in security operations system by addressing the method they use to attack and analyzing insider behavior. Deliver and pitch your topic in the best possible manner with this security functioning centre insider attacker method and behaviour assessment ideas pdf. Use them to share invaluable insights on insider attacker method and behaviour assessment and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Security Functioning Centre Table Of Contents Ppt Professional Graphic Tips PDF
Presenting security functioning centre table of contents ppt professional graphic tips pdf to provide visual cues and insights. Share and navigate important information on thirteen stages that need your due attention. This template can be used to pitch topics like dashboard, impact analysis, incident management, security operations centre, technologies. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
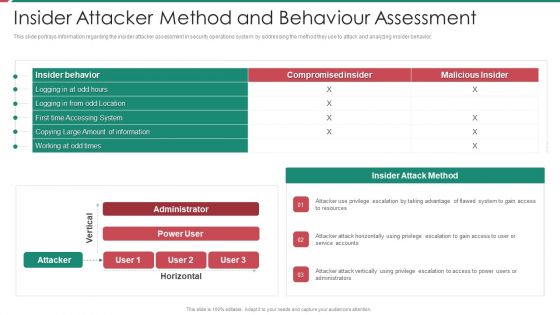
Security And Process Integration Insider Attacker Method And Behaviour Assessment Microsoft PDF
This slide portrays information regarding the insider attacker assessment in security operations system by addressing the method they use to attack and analyzing insider behavior. Deliver and pitch your topic in the best possible manner with this security and process integration insider attacker method and behaviour assessment microsoft pdf. Use them to share invaluable insights on insider attacker method and behaviour assessment and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cybersecurity Operations Cybersecops Impact Of Secops Implementation On Business Guidelines PDF
This slide represents the impact of implementing security operations in an organization. The purpose of this slide is to demonstrate how SecOps can benefit a company. The benefits include streamlined IT operations, prioritizing merge and consolidating proactive security, and so on. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Cybersecurity Operations Cybersecops Impact Of Secops Implementation On Business Guidelines PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Framework Of Information IT Security Action Program Slides PDF
This slide focuses on information security action program framework which covers governance plan, security standards, stakeholder engagement and operational management to manage risks, handling threat, data security management, etc.Showcasing this set of slides titled Framework Of Information IT Security Action Program Slides PDF The topics addressed in these templates are Security Standards, Data Protection, Response Structure All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Security Functioning Centre Prerequisites For Effective Secops Implementation Professional PDF
This slide portrays information regarding the prerequisites that essential for effective implementation of SecOps in terms of development and operations team, etc. This is a security functioning centre prerequisites for effective secops implementation professional pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like development team, operations team, performing, security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Banking Operations Management Lockers And Safe Deposits Services Introduction PDF
This slide highlights the lockers and safe deposits services which includes 5 different types of locker showcases annual locker rent with dual key security, safety, ease of location and convenient locker sizes. Presenting Banking Operations Management Lockers And Safe Deposits Services Introduction PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Convenient Locker Sizes, Dual Key Security, Ease Of Location, Safety. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
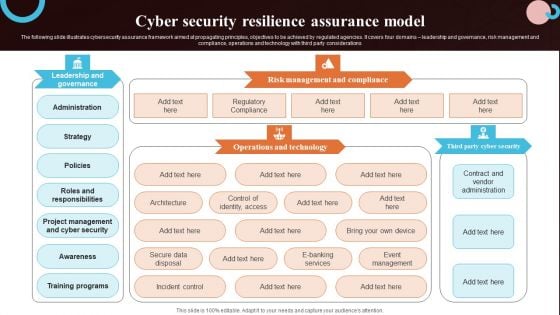
Cyber Security Resilience Assurance Model Slides PDF
The following slide illustrates cybersecurity assurance framework aimed at propagating principles, objectives to be achieved by regulated agencies. It covers four domains leadership and governance, risk management and compliance, operations and technology with third party considerations. Pitch your topic with ease and precision using this Cyber Security Resilience Assurance Model Slides PDF. This layout presents information on Awareness, Training Programs, Project Management. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Organizational Security Solutions Budget For Effective Secops System Management Rules PDF
Firm has prepared the budget for managing security operational system management. It also provides information about the software used and the duration required for implementation. Deliver and pitch your topic in the best possible manner with this organizational security solutions budget for effective secops system management rules pdf. Use them to share invaluable insights on functional area, software, implement duration, cost of implementation and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
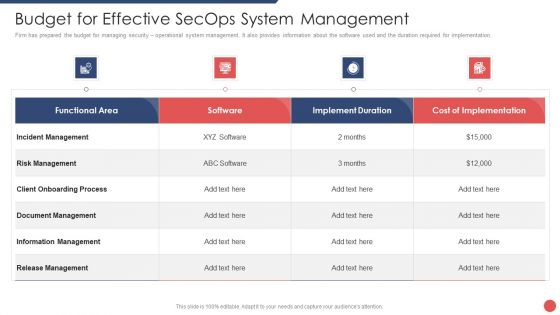
Security Functioning Centre Budget For Effective Secops System Management Formats PDF
Firm has prepared the budget for managing security operational system management. It also provides information about the software used and the duration required for implementation. Deliver and pitch your topic in the best possible manner with this security functioning centre budget for effective secops system management formats pdf. Use them to share invaluable insights on incident management, risk management, client onboarding process and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Security And Process Integration Budget For Effective Secops System Management Brochure PDF
Firm has prepared the budget for managing security operational system management. It also provides information about the software used and the duration required for implementation. Deliver and pitch your topic in the best possible manner with this security and process integration budget for effective secops system management brochure pdf. Use them to share invaluable insights on functional area, software, implement duration, cost of implementation and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cybersecurity Operations Cybersecops About Co Managed SOC Overview Objectives Template PDF
This slide talks about the overview of the co-managed security operation center, including its objective and benefits. The purpose of this slide is to highlight the main benefits of co-managed SOC, covering enhancing threat detection and response, scalability, cost savings and increased security knowledge. If you are looking for a format to display your unique thoughts, then the professionally designed Cybersecurity Operations Cybersecops About Co Managed SOC Overview Objectives Template PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Cybersecurity Operations Cybersecops About Co Managed SOC Overview Objectives Template PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Cybersecurity Operations Cybersecops Critical Functional Areas Of Secops Teams Background PDF
This slide describes the critical functions of security operations. The purpose of this slide is to demonstrate the various functions performed by SecOps teams in an organization. The main functions include threat intelligence, security monitoring, incident response, forensics and root cause analysis, etc. Boost your pitch with our creative Cybersecurity Operations Cybersecops Critical Functional Areas Of Secops Teams Background PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Cybersecurity Key Elements Of Electronic Information Security Ppt Styles Smartart PDF
This slide represents the different elements of cyber security such as application security, network security, information security, etc. This is a cybersecurity key elements of electronic information security ppt styles smartart pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like application security, network security, cloud security, operational security, information security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
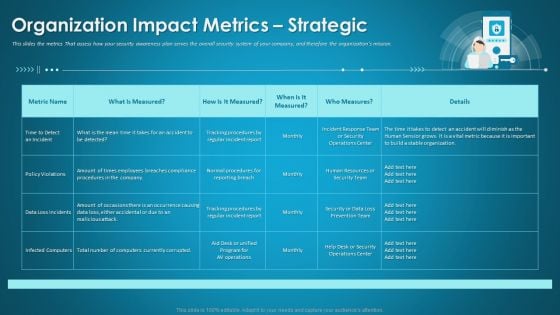
Organizational Network Security Awareness Staff Learning Organization Impact Metrics Strategic Structure PDF
This slides the metrics That assess how your security awareness plan serves the overall security system of your company, and therefore the organizations mission. Deliver and pitch your topic in the best possible manner with this organizational network security awareness staff learning organization impact metrics strategic structure pdf. Use them to share invaluable insights on human resources, security operations, organization and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Info Safety And ISO 27001 Security Domains That Will Be Addressed By Isms Sample PDF
This slide portrays different security domains that will be addressed by ISMS. Domains covered are security policy, asset management, physical and environmental security, cryptography and human resource security. Presenting Info Safety And ISO 27001 Security Domains That Will Be Addressed By Isms Sample PDF to provide visual cues and insights. Share and navigate important information on nine stages that need your due attention. This template can be used to pitch topics like Security Policy, Asset Management, Physical And Environmental Security, Operational Security, Access Control. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
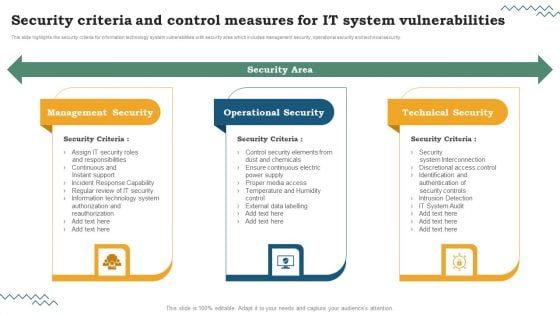
IT System Risk Management Guide Security Criteria And Control Measures For IT System Vulnerabilities Icons PDF
This slide highlights the security criteria for information technology system vulnerabilities with security area which includes management security, operational security and technical security. The IT System Risk Management Guide Security Criteria And Control Measures For IT System Vulnerabilities Icons PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
Software Development Life Cycle Planning Security Criteria And Control Measures For IT System Vulnerabilities Brochure PDF
This slide highlights the security criteria for information technology system vulnerabilities with security area which includes management security, operational security and technical security. The Software Development Life Cycle Planning Security Criteria And Control Measures For IT System Vulnerabilities Brochure PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Information Security And Policy Example Ppt Design
This is a information security and policy example ppt design. This is a six stage process. The stages in this process are client and operation structure, training and presentation, information flow, aggregation control, department size vs operation size, access control and network infrastructure.
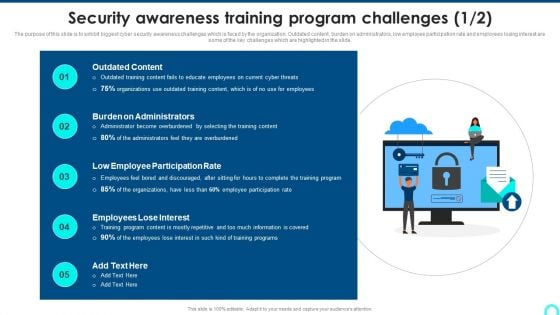
Security Awareness Training Program Challenges Rules PDF
The purpose of this slide is to exhibit biggest cyber security awareness challenges which is faced by the organization. Outdated content, burden on administrators, low employee participation rate and employees losing interest are some of the key challenges which are highlighted in the slide. Presenting Security Awareness Training Program Challenges Rules PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Outdated Content, Burden On Administrators, Employee Participation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Web Development What Is The Cyber Security Designs PDF
This slide represents how data security keeps in mind while developing websites, and security measures are already added to designed websites to protect them from malicious attacks.Presenting Web Development What Is The Cyber Security Designs PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Categories Of Cyber, Operational Security, Includes Network Security In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Chain Cross Business Security PowerPoint Templates And PowerPoint Themes 1012
Chain Cross Business Security PowerPoint Templates And PowerPoint Themes 1012-With these pre-designed chains you can visualize almost any type of concept, chronological process or steps of your strategies. This Targets the Security in Life, Business as shown above. This Template points to the Chain Security which signifies Team Work. It shows the number of chains crossed together to secure the family ,Business etc.-Chain Cross Business Security PowerPoint Templates And PowerPoint Themes 1012-This PowerPoint template can be used for presentations relating to-Chain cross, security, business, chains, success, leadership Achieve strategic & tactical operations with our Chain Cross Business Security PowerPoint Templates And PowerPoint Themes 1012. They will make you look good.
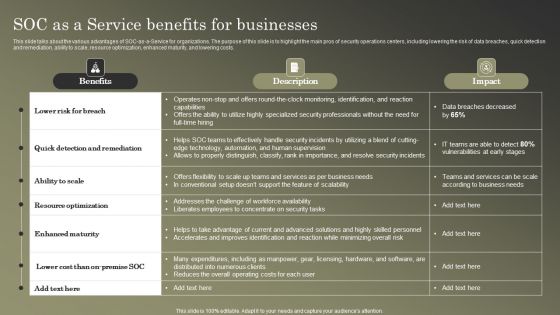
Cybersecurity Operations Cybersecops SOC As A Service Benefits For Businesses Portrait PDF
This slide talks about the various advantages of SOC-as-a-Service for organizations. The purpose of this slide is to highlight the main pros of security operations centers, including lowering the risk of data breaches, quick detection and remediation, ability to scale, resource optimization, enhanced maturity, and lowering costs. Find highly impressive Cybersecurity Operations Cybersecops SOC As A Service Benefits For Businesses Portrait PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Cybersecurity Operations Cybersecops SOC As A Service Benefits For Businesses Portrait PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.

Cybersecurity Operations Cybersecops Dedicated SOC Overview Pros And Cons Guidelines PDF
This slide outlines the overview of dedicated SOC, including its goal and advantages and disadvantages. The purpose of this slide is to showcase the dedicated security operations center covering its benefits and drawbacks. The goal of this SOC center is to monitor information systems around the clock. Create an editable Cybersecurity Operations Cybersecops Dedicated SOC Overview Pros And Cons Guidelines PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre designed presentation templates help save time. Cybersecurity Operations Cybersecops Dedicated SOC Overview Pros And Cons Guidelines PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Cybersecurity Operations Cybersecops Overview And Benefits Of Virtual SOC Model Infographics PDF
This slide represents the overview, benefits and disadvantages of virtual security operation center model. The purpose of this slide is to highlight the advantage, disadvantages and alternative approaches for VSOC such as outsourcing of virtual SOC model. This modern and well arranged Cybersecurity Operations Cybersecops Overview And Benefits Of Virtual SOC Model Infographics PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Addressing Role Of Chief Security Officer At Workplace Clipart PDF
This slide provides information regarding role of chief security officer at workplace and determine their key priorities in terms of day to day operations, security, compliance, innovation, etc. Create an editable Addressing Role Of Chief Security Officer At Workplace Clipart PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Addressing Role Of Chief Security Officer At Workplace Clipart PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
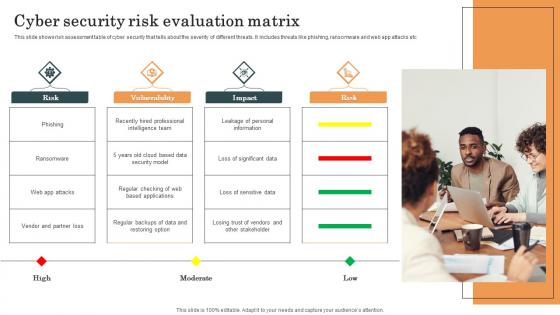
Cyber Security Risk Evaluation Matrix Survey SS
This slide shows risk assessment table of cyber security that tells about the severity of different threats. It includes threats like phishing, ransomware and web app attacks etc. Pitch your topic with ease and precision using this Cyber Security Risk Evaluation Matrix Survey SS. This layout presents information on Cyber Security, Risk Evaluation Matrix, Web App Attacks. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide shows risk assessment table of cyber security that tells about the severity of different threats. It includes threats like phishing, ransomware and web app attacks etc.

Cyber Security Strategic Agenda Checklist Mockup Pdf
This slide represents action plan of checklist of cyber security. It further includes tasks such as determine potential areas like challenges regarding cyber security and security loopholes, etc and their status. Showcasing this set of slides titled Cyber Security Strategic Agenda Checklist Mockup Pdf. The topics addressed in these templates are Cyber Security, Strategic Agenda Checklist. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide represents action plan of checklist of cyber security. It further includes tasks such as determine potential areas like challenges regarding cyber security and security loopholes, etc and their status.

Sustainable Improving Security By Green Computing Technology
This slide outlines how green computing can improve security. The purpose of this slide is to showcase the pillars of data security, security concerns and solution, and different antivirus software that can help users to protect their computers and networks. Create an editable Sustainable Improving Security By Green Computing Technology that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Sustainable Improving Security By Green Computing Technology is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide outlines how green computing can improve security. The purpose of this slide is to showcase the pillars of data security, security concerns and solution, and different antivirus software that can help users to protect their computers and networks.
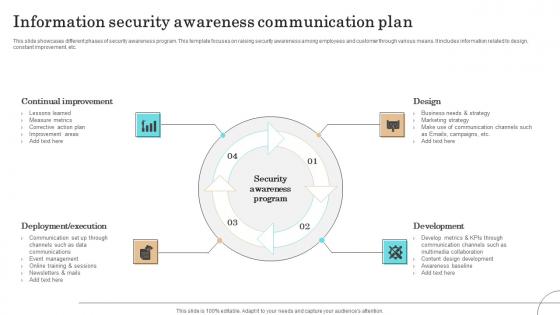
Information Security Awareness Communication Plan Formats Pdf
This slide showcases different phases of security awareness program. This template focuses on raising security awareness among employees and customer through various means. It includes information related to design, constant improvement, etc.Pitch your topic with ease and precision using this Information Security Awareness Communication Plan Formats Pdf This layout presents information on Continual Improvement, Deployment Execution, Communication It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide showcases different phases of security awareness program. This template focuses on raising security awareness among employees and customer through various means. It includes information related to design, constant improvement, etc.
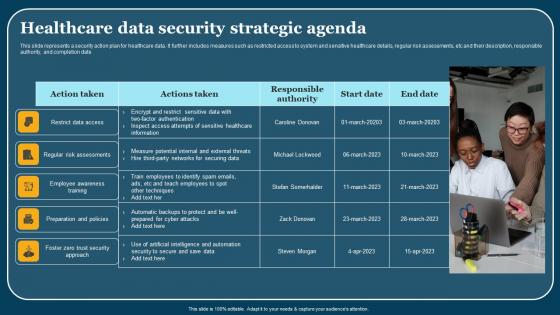
Healthcare Data Security Strategic Agenda Themes Pdf
This slide represents a security action plan for healthcare data. It further includes measures such as restricted access to system and sensitive healthcare details, regular risk assessments, etc and their description, responsible authority, and completion date. Showcasing this set of slides titled Healthcare Data Security Strategic Agenda Themes Pdf. The topics addressed in these templates are Employee Awareness Training, Action Taken. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide represents a security action plan for healthcare data. It further includes measures such as restricted access to system and sensitive healthcare details, regular risk assessments, etc and their description, responsible authority, and completion date.

Security Handbook For Corporate Personnel Information Pdf
Create an editable Security Handbook For Corporate Personnel Information Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Security Handbook For Corporate Personnel Information Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. Following slide exhibits impact of effective internal communication on employee based on measurement performance indicators. It include elements such as engagement rate, turnover rate, productivity etc.
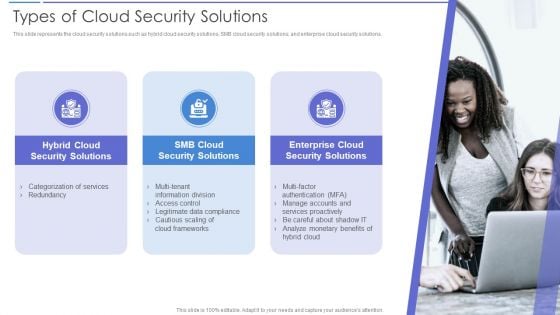
Types Of Cloud Security Solutions Demonstration PDF
This slide represents the cloud security solutions such as hybrid cloud security solutions, SMB cloud security solutions, and enterprise cloud security solutions. This is a Types Of Cloud Security Solutions Demonstration PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Analyze, Services Proactively, Information Division. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
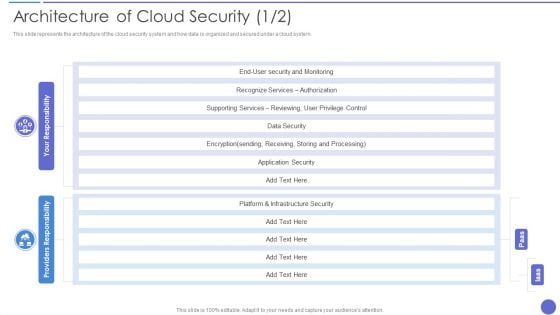
Architecture Of Cloud Security Ideas PDF
This slide represents the architecture of the cloud security system and how data is organized and secured under a cloud system. Deliver an awe inspiring pitch with this creative Architecture Of Cloud Security Ideas PDF bundle. Topics like Recognize Services, Supporting Services, Infrastructure Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
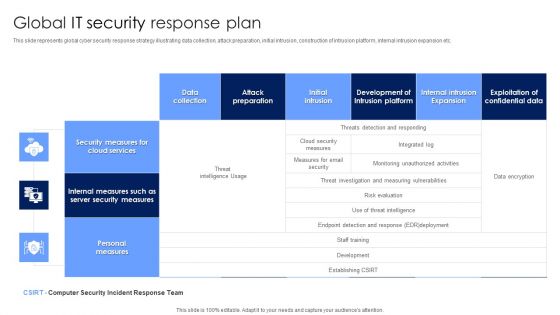
Global IT Security Response Plan Diagrams PDF
This slide represents global cyber security response strategy illustrating data collection, attack preparation, initial intrusion, construction of intrusion platform, internal intrusion expansion etc. Showcasing this set of slides titled Global IT Security Response Plan Diagrams PDF. The topics addressed in these templates are Security Measures, Cloud Services, Personal Measures. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
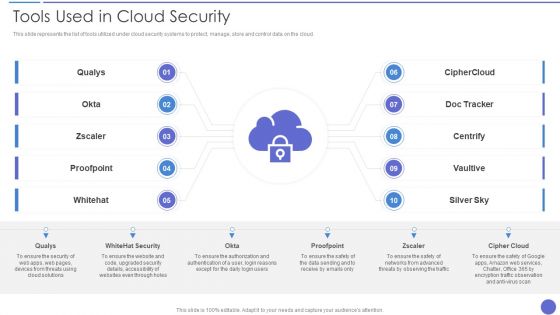
Tools Used In Cloud Security Template PDF
This slide represents the list of tools utilized under cloud security systems to protect, manage, store and control data on the cloud. Presenting Tools Used In Cloud Security Template PDF to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like Qualys, Whitehat Security, Cipher Cloud. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.


 Continue with Email
Continue with Email

 Home
Home


































