Security Operations

Introduction Modern Billing Enhancing Customer Service Operations Using CRM Technology Formats Pdf
Following slide provide overview of modern billing software that helps to increase business operations efficiency. It include benefits such as high data security, flexibility, resource optimization etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Introduction Modern Billing Enhancing Customer Service Operations Using CRM Technology Formats Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. Following slide provide overview of modern billing software that helps to increase business operations efficiency. It include benefits such as high data security, flexibility, resource optimization etc.
Security Of Cloud Computing Ppt PowerPoint Presentation Inspiration Microsoft
This is a security of cloud computing ppt powerpoint presentation inspiration microsoft. This is a four stage process. The stages in this process are computer software, operating system, open source.
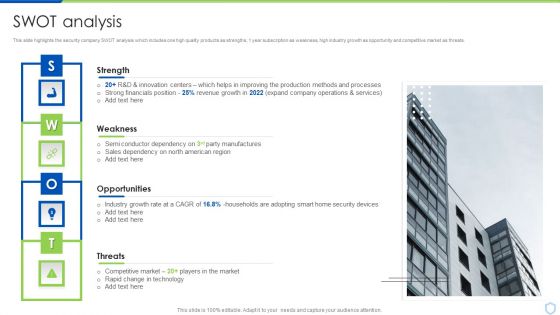
Security And Surveillance Company Profile SWOT Analysis Infographics PDF
This slide highlights the security company SWOT analysis which includes one high quality products as strengths, 1 year subscription as weakness, high industry growth as opportunity and competitive market as threats. This is a Security And Surveillance Company Profile SWOT Analysis Infographics PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Financials Position, Innovation Centers, Operations Services. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
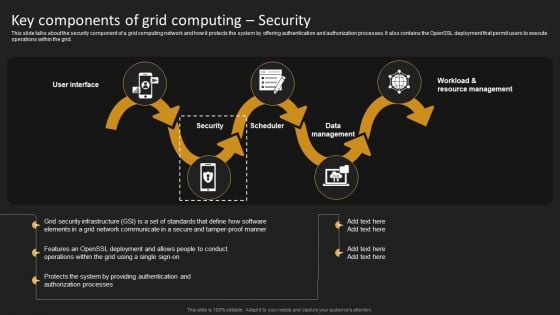
Key Components Of Grid Computing Security Structure PDF
This slide talks about the security component of a grid computing network and how it protects the system by offering authentication and authorization processes. It also contains the OpenSSL deployment that permit users to execute operations within the grid. Welcome to our selection of the Key Components Of Grid Computing Security Structure PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.
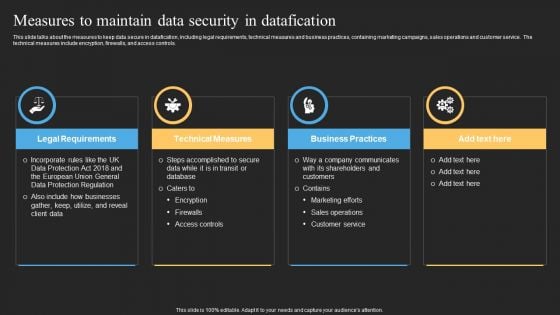
Datafy Measures To Maintain Data Security In Datafication Diagrams PDF
This slide talks about the measures to keep data secure in datafication, including legal requirements, technical measures and business practices, containing marketing campaigns, sales operations and customer service. The technical measures include encryption, firewalls, and access controls. Welcome to our selection of the Datafy Measures To Maintain Data Security In Datafication Diagrams PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.

National Security America PowerPoint Templates Ppt Backgrounds For Slides 1212
We present our National Security America PowerPoint Templates PPT Backgrounds For Slides 1212.Use our Americana PowerPoint Templates because you have the plans ready for them to absorb and understand. Use our Security PowerPoint Templates because you can gain the success to desired levels in one go. Download our Success PowerPoint Templates because iT outlines the entire thought process for the benefit of others. Tell it to the world with your characteristic aplomb. Use our Business PowerPoint Templates because you have churned your mind and come upwith solutions. Present our Stars PowerPoint Templates because the Venn graphic comprising interlinking circles geometrically demonstate how various functions operating independantly, to a large extent, are essentially interdependant.Use these PowerPoint slides for presentations relating to National security america, business, security, success, americana, stars. The prominent colors used in the PowerPoint template are Red, White, Blue navy. Customers tell us our National Security America PowerPoint Templates PPT Backgrounds For Slides 1212 are Ultra. Presenters tell us our security PowerPoint templates and PPT Slides are Exuberant. Use our National Security America PowerPoint Templates PPT Backgrounds For Slides 1212 will get their audience's attention. PowerPoint presentation experts tell us our america PowerPoint templates and PPT Slides are Ultra. Customers tell us our National Security America PowerPoint Templates PPT Backgrounds For Slides 1212 will save the presenter time. Presenters tell us our stars PowerPoint templates and PPT Slides are Perfect. Our National Security America PowerPoint Templates Ppt Backgrounds For Slides 1212 exist in abundance. They believe in giving you ample oppurtunities.

Chain Security PowerPoint Templates And PowerPoint Themes 1012
Chain Security PowerPoint Templates And PowerPoint Themes 1012-This PowerPoint template consists of an image of many linked chains connected to one circular green chain. This image represents the concept of security or steps of business strategies. This template also emphasize strong group between family, business etc. Present your views using our innovative slides and be assured of leaving a lasting impression. -Chain Security PowerPoint Templates And PowerPoint Themes 1012-This PowerPoint template can be used for presentations relating to-Chains of design, communication, security, business, teamwork, industrial Set a good example with our Chain Security PowerPoint Templates And PowerPoint Themes 1012. Be the benchmark for others to follow.

Hacker Security PowerPoint Templates And PowerPoint Backgrounds 0211
Microsoft PowerPoint Template and Background with a conceptual illustration on the subject of computer hacking Our Hacker Security PowerPoint Templates And PowerPoint Backgrounds 0211 never fail to amaze. They catch every eye that comes by.
Encrypted Business Data Cyber Security Assessment Icon Professional PDF
Presenting Encrypted Business Data Cyber Security Assessment Icon Professional PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Manage Handy Backups, Incorporate Multi Layer Security, Train Employees, Invest In Protective Software. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

House With Key Security PowerPoint Templates And PowerPoint Themes 1112
House With Key Security PowerPoint Templates And PowerPoint Themes 1112-Develop competitive advantage with our above template which contains a diagram of greenhouse connected with keys. This image represents the concept of security. It portrays the concept of building, chain, development, investment, mortgage, residential etc. Our PPT images are so ideally designed that it reveals the very basis of our PPT template are an effective tool to make your clients understand. The structure of our templates allows you to effectively highlight the key issues concerning the growth of your business.-House With Key Security PowerPoint Templates And PowerPoint Themes 1112-This PowerPoint template can be used for presentations relating to-House with key, Security, Design, Business, Abstract, Metaphor The audience will always evince interest. Our House With Key Security PowerPoint Templates And PowerPoint Themes 1112 will make them apply their minds.

Information Technology Security Prepare Data Backup Ppt Layouts Slides PDF
This slide represents the preparation of data backup for sensitive information and how data backup should be created and stored within an organization. This is a information technology security prepare data backup ppt layouts slides pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like protect, information, manipulation, deletion, prevent . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
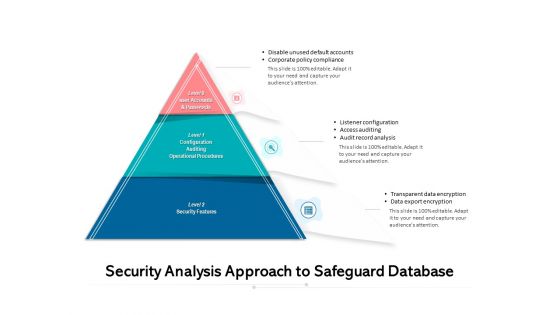
Security Analysis Approach To Safeguard Database Ppt PowerPoint Presentation Show Designs PDF
Persuade your audience using this security analysis approach to safeguard database ppt powerpoint presentation show designs pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including analysis, corporate policy compliance, operational procedures, security features. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
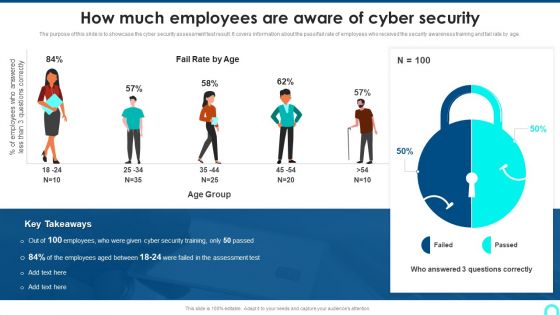
How Much Employees Are Aware Of Cyber Security Introduction PDF
The purpose of this slide is to showcase the cyber security assessment test result. It covers information about the pass fail rate of employees who received the security awareness training and fail rate by age.This is a How Much Employees Are Aware Of Cyber Security Introduction PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Questions Correctly, Employees Answered, Employees Between. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
File Lock Security Vector Icon Ppt PowerPoint Presentation Infographics Model
This is a file lock security vector icon ppt powerpoint presentation infographics model. This is a one stage process. The stages in this process are computer software, operating system, open source.

ISO 27001 Organizational Qualifying Procedure Security Domains That Will Be Addressed By ISMS Graphics PDF
This slide portrays different security domains that will be addressed by ISMS. Domains covered are security policy, asset management, physical and environmental security, cryptography and human resource security.Presenting ISO 27001 Organizational Qualifying Procedure Security Domains That Will Be Addressed By ISMS Graphics PDF to provide visual cues and insights. Share and navigate important information on nine stages that need your due attention. This template can be used to pitch topics like Asset Management, Operational Security, Physical And Environmental. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Traditional Perimeter Based Network Security Overview And Limitations Inspiration PDF
This slide represents the overview of traditional perimeter-based network security. The purpose of this slide is to showcase the various challenges of conventional perimeter-based security and how ZTNA can overcomethose challenges. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Traditional Perimeter Based Network Security Overview And Limitations Inspiration PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
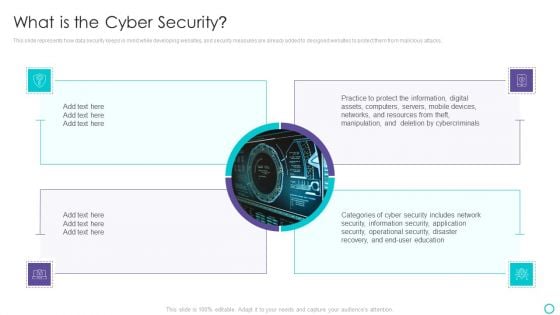
Website Designing And Development Service What Is The Cyber Security Diagrams PDF
This slide represents how data security keeps in mind while developing websites, and security measures are already added to designed websites to protect them from malicious attacks.Presenting Website Designing And Development Service What Is The Cyber Security Diagrams PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Practice To Protect, Information Digital, Operational Security In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
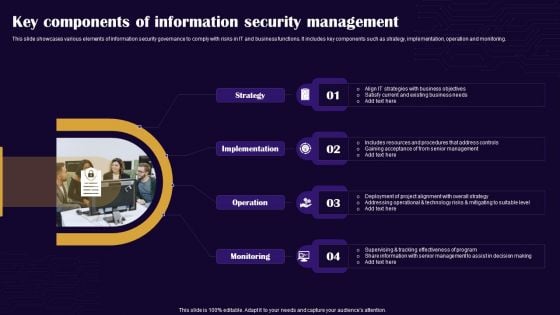
Key Components Of Information Security Management Graphics PDF
This slide showcases various elements of information security governance to comply with risks in IT and business functions. It includes key components such as strategy, implementation, operation and monitoring. Persuade your audience using this Key Components Of Information Security Management Graphics PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Strategy, Implementation, Operation. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
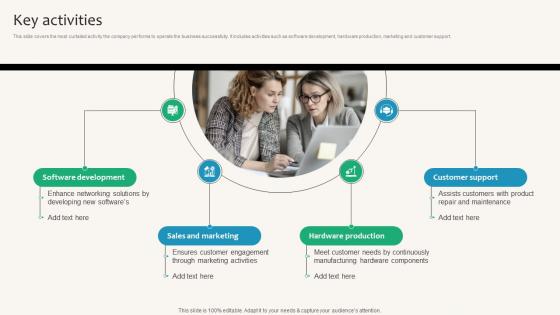
Key Activities Security Service Provider Business Model BMC SS V
This slide covers the most curtailed activity the company performs to operate the business successfully. It includes activities such as software development, hardware production, marketing and customer support. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Key Activities Security Service Provider Business Model BMC SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide covers the most curtailed activity the company performs to operate the business successfully. It includes activities such as software development, hardware production, marketing and customer support.

Cyber Security Risk Management Plan Impact Assessment Matrix Information PDF
Deliver and pitch your topic in the best possible manner with this cyber security risk management plan impact assessment matrix information pdf. Use them to share invaluable insights on financial, reputation, regulatory, operational and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
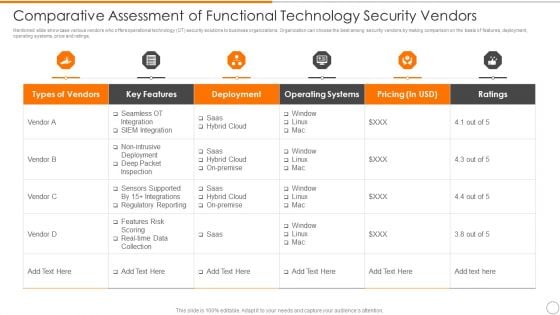
Comparative Assessment Of Functional Technology Security Vendors Professional PDF
Showcasing this set of slides titled comparative assessment of functional technology security vendors professional pdf. The topics addressed in these templates are deployment, operating systems, pricing. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Key Resources Security Service Provider Business Model BMC SS V
This slide covers the importance assets to operate business. It includes data centers, intellectual property, financial and human resources. Slidegeeks is here to make your presentations a breeze with Key Resources Security Service Provider Business Model BMC SS V With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide covers the importance assets to operate business. It includes data centers, intellectual property, financial and human resources.
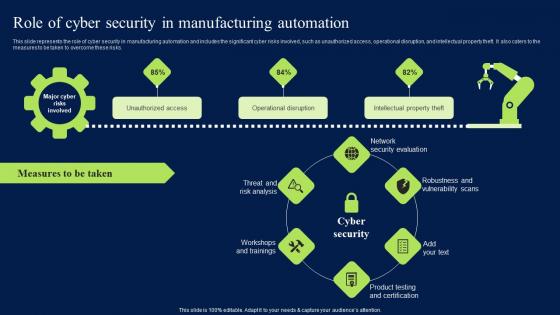
Role Of Cyber Security In Manufacturing Automation Clipart PDF
This slide represents the role of cyber security in manufacturing automation and includes the significant cyber risks involved, such as unauthorized access, operational disruption, and intellectual property theft. It also caters to the measures to be taken to overcome these risks. Find highly impressive Role Of Cyber Security In Manufacturing Automation Clipart PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Role Of Cyber Security In Manufacturing Automation Clipart PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide represents the role of cyber security in manufacturing automation and includes the significant cyber risks involved, such as unauthorized access, operational disruption, and intellectual property theft. It also caters to the measures to be taken to overcome these risks.
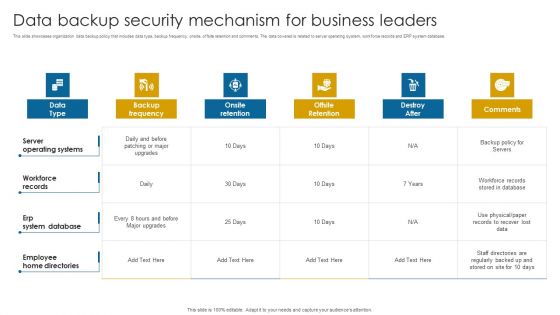
Data Backup Security Mechanism For Business Leaders Infographics PDF
This slide showcases organization data backup policy that includes data type, backup frequency, onsite, offsite retention and comments. The data covered is related to server operating system, workforce records and ERP system database.Showcasing this set of slides titled Data Backup Security Mechanism For Business Leaders Infographics PDF. The topics addressed in these templates are Operating Systems, Workforce Records, Employee Home Directories. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
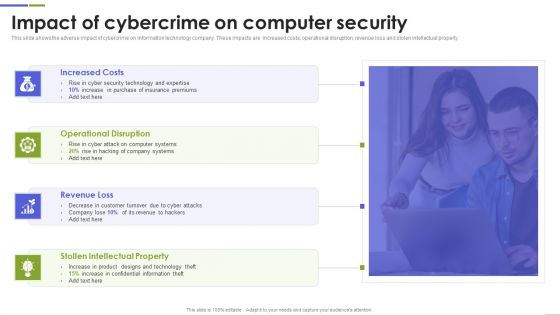
Impact Of Cybercrime On Computer Security Formats PDF
This slide shows the adverse impact of cybercrime on information technology company. These impacts are increased costs, operational disruption, revenue loss and stolen intellectual property. Persuade your audience using this Impact Of Cybercrime On Computer Security Formats PDF This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Increased Costs, Operational Disruption, Revenue Loss Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Organization Cyber Security Dashboard Ppt Icon Sample PDF
This slide covers the cyber security key performance indicators for the organization including application health, device license consumption, data encryption status and many more Deliver and pitch your topic in the best possible manner with this organization cyber security dashboard ppt icon sample pdf. Use them to share invaluable insights on makes and models, application health, license consumption, operating systems and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Implementing Cyber Security Incident Five Phases Of Cybersecurity Incident Clipart PDF
This slide represents the stages of the process which aims towards minimizing the impact of cyber security incidents on operational functions. It includes cyber security incident management stages such as plan and prepare, detect and report etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Implementing Cyber Security Incident Five Phases Of Cybersecurity Incident Clipart PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Implementing Cyber Security Incident Five Phases Of Cybersecurity Incident Clipart PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

CYBER Security Breache Response Strategy Five Phases Of Cybersecurity Incident Management Structure PDF
This slide represents the stages of the process which aims towards minimizing the impact of cyber security incidents on operational functions. It includes cyber security incident management stages such as plan and prepare, detect and report etc. Retrieve professionally designed CYBER Security Breache Response Strategy Five Phases Of Cybersecurity Incident Management Structure PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Effective Security Strategic Agenda For Hotels Introduction Pdf
This slide represents effective security action plan for hotels and motels. It further includes major security features such as area security, surveillance, contaminant protection and security personnel. Showcasing this set of slides titled Effective Security Strategic Agenda For Hotels Introduction Pdf. The topics addressed in these templates are Security, Action Taken, Responsible Authority. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide represents effective security action plan for hotels and motels. It further includes major security features such as area security, surveillance, contaminant protection and security personnel.

Statistics Of Cloud Data Security Client Side Encryption PPT Slide
This slide summarizes data security attacks across different organizational departments, such as sales, IT department, finance, marketing, operations, etc. The outlined attacks are data interception, unauthorized access, data breaches, etc. This Statistics Of Cloud Data Security Client Side Encryption PPT Slide from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide summarizes data security attacks across different organizational departments, such as sales, IT department, finance, marketing, operations, etc. The outlined attacks are data interception, unauthorized access, data breaches, etc.
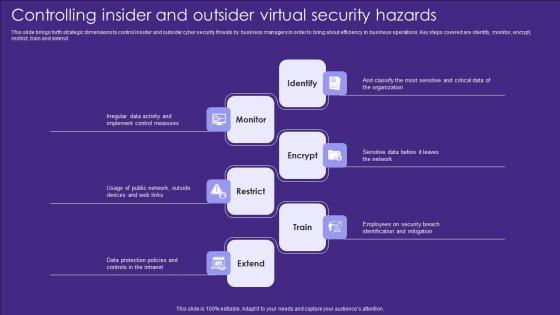
Controlling Insider And Outsider Virtual Security Hazards Designs Pdf
This slide brings forth strategic dimensions to control insider and outsider cyber security threats by business managers in order to bring about efficiency in business operations. Key steps covered are identify, monitor, encrypt, restrict, train and extend Showcasing this set of slides titled Controlling Insider And Outsider Virtual Security Hazards Designs Pdf. The topics addressed in these templates are Identify, Monitor, Encrypt. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide brings forth strategic dimensions to control insider and outsider cyber security threats by business managers in order to bring about efficiency in business operations. Key steps covered are identify, monitor, encrypt, restrict, train and extend
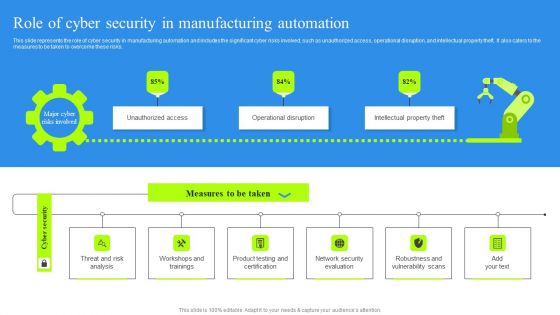
Role Of Cyber Security In Manufacturing Automation Portrait PDF
This slide represents the role of cyber security in manufacturing automation and includes the significant cyber risks involved, such as unauthorized access, operational disruption, and intellectual property theft. It also caters to the measures to be taken to overcome these risks. Find highly impressive Role Of Cyber Security In Manufacturing Automation Portrait PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Role Of Cyber Security In Manufacturing Automation Portrait PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now
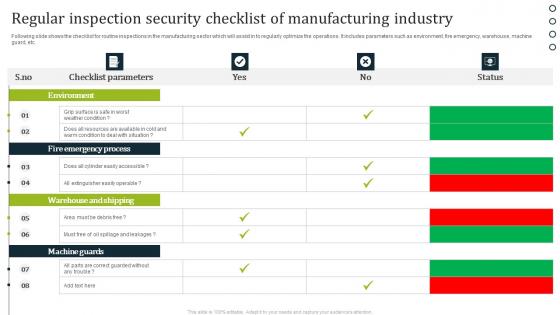
Regular Inspection Security Checklist Of Manufacturing Industry Demonstration Pdf
Following slide shows the checklist for routine inspections in the manufacturing sector which will assist in to regularly optimize the operations. It includes parameters such as environment, fire emergency, warehouse, machine guard, etc. Pitch your topic with ease and precision using this Regular Inspection Security Checklist Of Manufacturing Industry Demonstration Pdf. This layout presents information on Checklist Parameters, Status. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Following slide shows the checklist for routine inspections in the manufacturing sector which will assist in to regularly optimize the operations. It includes parameters such as environment, fire emergency, warehouse, machine guard, etc.

Major Roles And Responsibilities Of Financial Security Team Sample PDF
The following slide Major roles and responsibilities of financial security department . It includes information about risk level determination, laws and regulations, team training, operational compliance, automatic workflows, red flags, etc. Slidegeeks is here to make your presentations a breeze with Major Roles And Responsibilities Of Financial Security Team Sample PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
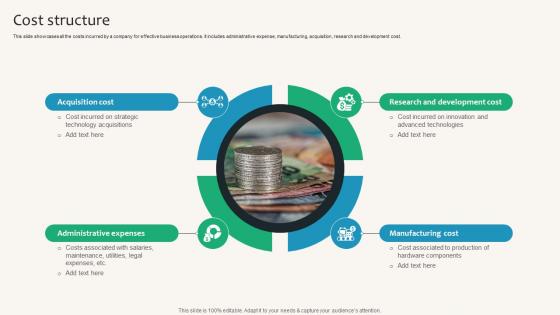
Cost Structure Security Service Provider Business Model BMC SS V
This slide showcases all the costs incurred by a company for effective business operations. It includes administrative expense, manufacturing, acquisition, research and development cost. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Cost Structure Security Service Provider Business Model BMC SS V for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide showcases all the costs incurred by a company for effective business operations. It includes administrative expense, manufacturing, acquisition, research and development cost.
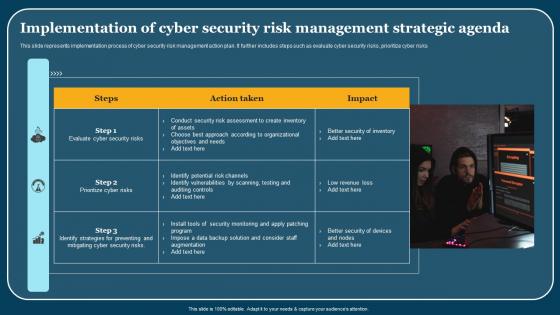
Implementation Of Cyber Security Risk Management Strategic Agenda Pictures Pdf
This slide represents implementation process of cyber security risk management action plan. It further includes steps such as evaluate cyber security risks, prioritize cyber risks. Pitch your topic with ease and precision using this Implementation Of Cyber Security Risk Management Strategic Agenda Pictures Pdf. This layout presents information on Steps, Action Taken, Impact. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide represents implementation process of cyber security risk management action plan. It further includes steps such as evaluate cyber security risks, prioritize cyber risks.
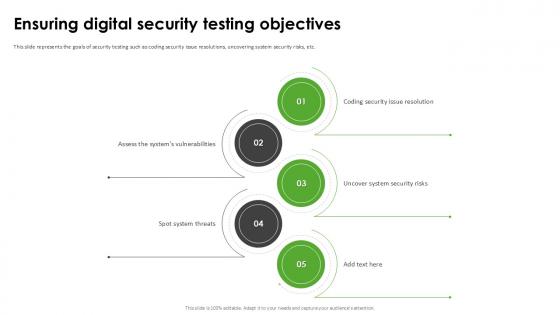
Ensuring Digital Security Harnessing The World Of Ethical Ppt Example
This slide represents the goals of security testing such as coding security issue resolutions, uncovering system security risks, etc. Slidegeeks is here to make your presentations a breeze with Ensuring Digital Security Harnessing The World Of Ethical Ppt Example With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide represents the goals of security testing such as coding security issue resolutions, uncovering system security risks, etc.

Key Parameters To Prepare Security Strategic Agenda Summary Pdf
This slide represents action plan for physical security to provide protection. It further includes security areas such as physical safeguards, administrative safeguards, technical safeguards, etc , their description, action taken, and date of completion. Pitch your topic with ease and precision using this Key Parameters To Prepare Security Strategic Agenda Summary Pdf. This layout presents information on Security Areas, Description, Action Taken. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide represents action plan for physical security to provide protection. It further includes security areas such as physical safeguards, administrative safeguards, technical safeguards, etc , their description, action taken, and date of completion.
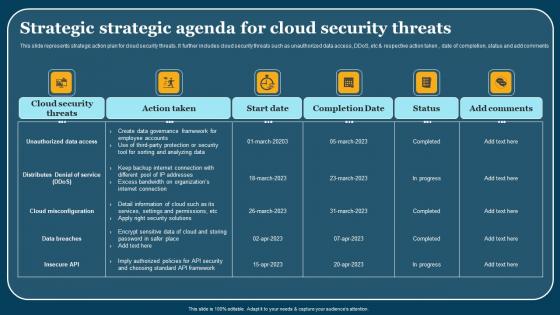
Strategic Strategic Agenda For Cloud Security Threats Ideas Pdf
This slide represents strategic action plan for cloud security threats. It further includes cloud security threats such as unauthorized data access, DDoS, etc and respective action taken , date of completion, status and add comments. Showcasing this set of slides titled Strategic Strategic Agenda For Cloud Security Threats Ideas Pdf. The topics addressed in these templates are Cloud Security Threats, Action Taken, Start Date. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide represents strategic action plan for cloud security threats. It further includes cloud security threats such as unauthorized data access, DDoS, etc and respective action taken , date of completion, status and add comments.

It Security Training Courses Strategic Agenda To Employees Portrait Pdf
This slide represents action plan for various training courses. It includes training courses such as complete cyber security courses, etc and their description, mode, duration, and budget. Showcasing this set of slides titled It Security Training Courses Strategic Agenda To Employees Portrait Pdf. The topics addressed in these templates are Training Courses, Description, Trainer Name. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide represents action plan for various training courses. It includes training courses such as complete cyber security courses, etc and their description, mode, duration, and budget.
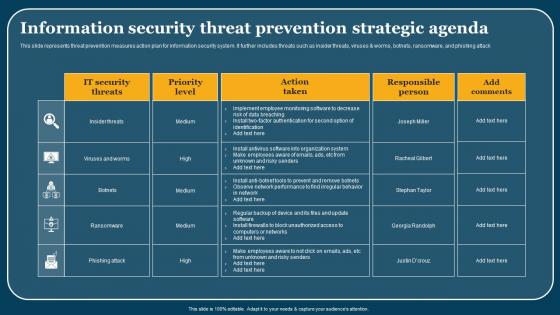
Information Security Threat Prevention Strategic Agenda Introduction Pdf
This slide represents threat prevention measures action plan for information security system. It further includes threats such as insider threats, viruses and worms, botnets, ransomware, and phishing attack. Pitch your topic with ease and precision using this Information Security Threat Prevention Strategic Agenda Introduction Pdf. This layout presents information on Security Threats, Priority Level, Action Taken. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide represents threat prevention measures action plan for information security system. It further includes threats such as insider threats, viruses and worms, botnets, ransomware, and phishing attack.
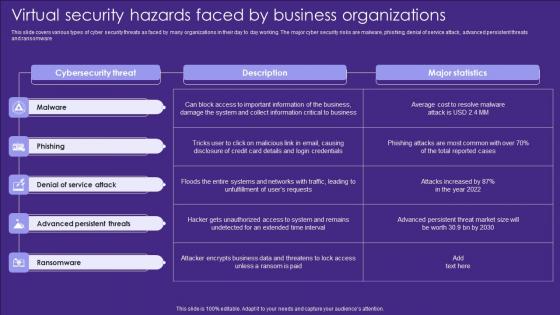
Virtual Security Hazards Faced By Business Organizations Sample Pdf
This slide covers various types of cyber security threats as faced by many organizations in their day to day working. The major cyber security risks are malware, phishing, denial of service attack, advanced persistent threats and ransomware Pitch your topic with ease and precision using this Virtual Security Hazards Faced By Business Organizations Sample Pdf. This layout presents information on Ransomware, Threats, Attack. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide covers various types of cyber security threats as faced by many organizations in their day to day working. The major cyber security risks are malware, phishing, denial of service attack, advanced persistent threats and ransomware
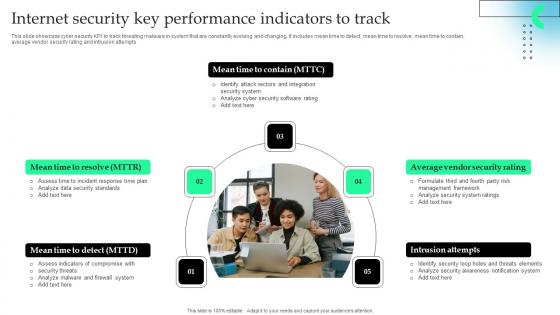
Internet Security Key Performance Indicators To Track Microsoft Pdf
This slide showcase cyber security KPI to track threating malware in system that are constantly evolving and changing. It includes mean time to detect, mean time to resolve, mean time to contain, average vendor security rating and intrusion attempts.Showcasing this set of slides titled Internet Security Key Performance Indicators To Track Microsoft Pdf The topics addressed in these templates are Firewall System, Security Standards, Identify Attack All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcase cyber security KPI to track threating malware in system that are constantly evolving and changing. It includes mean time to detect, mean time to resolve, mean time to contain, average vendor security rating and intrusion attempts.
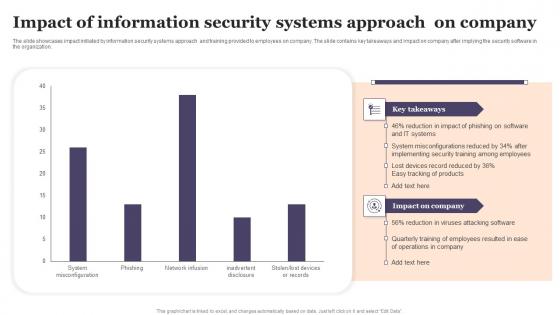
Impact Of Information Security Systems Approach On Company Designs Pdf
The slide showcases impact initiated by information security systems approach and training provided to employees on company. The slide contains key takeaways and impact on company after implying the security software in the organization. Showcasing this set of slides titled Impact Of Information Security Systems Approach On Company Designs Pdf The topics addressed in these templates are Impact Of Information, Security Systems, Approach On Company All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. The slide showcases impact initiated by information security systems approach and training provided to employees on company. The slide contains key takeaways and impact on company after implying the security software in the organization.
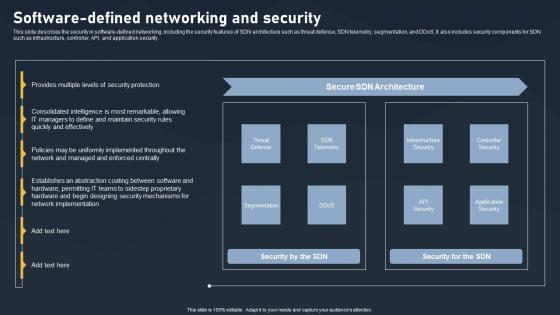
Software Defined Networking And Security SDN Building Blocks Portrait Pdf
This slide describes the security in software-defined networking, including the security features of SDN architecture such as threat defense, SDN telemetry, segmentation, and DDoS. It also includes security components for SDN such as infrastructure, controller, API, and application security.Whether you have daily or monthly meetings, a brilliant presentation is necessary. Software Defined Networking And Security SDN Building Blocks Portrait Pdf can be your best option for delivering a presentation. Represent everything in detail using Software Defined Networking And Security SDN Building Blocks Portrait Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide describes the security in software defined networking, including the security features of SDN architecture such as threat defense, SDN telemetry, segmentation, and DDoS. It also includes security components for SDN such as infrastructure, controller, API, and application security.

CASB 2 0 IT Emerging Cloud Security Risks And Threats
This slide represents the emerging cloud security risks, and threats organizations can encounter. The purpose of this slide is to highlight the various threats that CASB deployment can help overcome, including VPNs, system misconfiguration, non-zero security permissions, and so on. Boost your pitch with our creative CASB 2 0 IT Emerging Cloud Security Risks And Threats. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide represents the emerging cloud security risks, and threats organizations can encounter. The purpose of this slide is to highlight the various threats that CASB deployment can help overcome, including VPNs, system misconfiguration, non-zero security permissions, and so on.

Top Rising Virtual Security Hazards In 2023 Elements Pdf
This slide illustrates top threats which are emerging in the field of cyber security from the year 2023 onwards. The cyber security risks as covered in this template are crypto jacking, IoT attacks, smart medical devices, connected cars and third party attacks Showcasing this set of slides titled Top Rising Virtual Security Hazards In 2023 Elements Pdf. The topics addressed in these templates are Crypto Jacking, Attacks, Medical Devices. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide illustrates top threats which are emerging in the field of cyber security from the year 2023 onwards. The cyber security risks as covered in this template are crypto jacking, IoT attacks, smart medical devices, connected cars and third party attacks
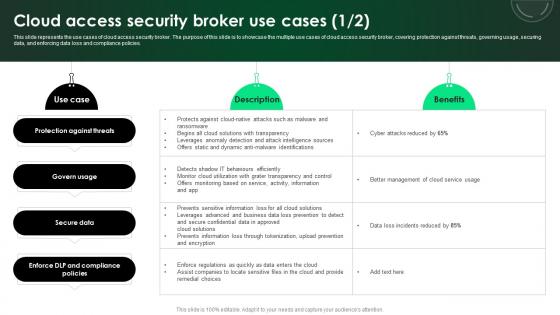
CASB 2 0 IT Cloud Access Security Broker Use Cases
This slide represents the use cases of cloud access security broker. The purpose of this slide is to showcase the multiple use cases of cloud access security broker, covering protection against threats, governing usage, securing data, and enforcing data loss and compliance policies. Presenting this PowerPoint presentation, titled CASB 2 0 IT Cloud Access Security Broker Use Cases, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this CASB 2 0 IT Cloud Access Security Broker Use Cases. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable CASB 2 0 IT Cloud Access Security Broker Use Cases that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide represents the use cases of cloud access security broker. The purpose of this slide is to showcase the multiple use cases of cloud access security broker, covering protection against threats, governing usage, securing data, and enforcing data loss and compliance policies.
Employee Incentives Icon For Healthcare And Financial Security Designs Pdf
Showcasing this set of slides titled Employee Incentives Icon For Healthcare And Financial Security Designs Pdf The topics addressed in these templates are Employee Incentives, Icon For Healthcare, Financial Security All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Our Employee Incentives Icon For Healthcare And Financial Security Designs Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

IT Security Hacker Interview Schedule For New Professionals Portrait PDF
This slide represents the interview schedule for new employees, including ethical hackers, security consultants, and IT security analysts to be hired to prevent hacking.Deliver and pitch your topic in the best possible manner with this IT Security Hacker Interview Schedule For New Professionals Portrait PDF. Use them to share invaluable insights on Ethical Hacker, Security Consultant, Security Analyst and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
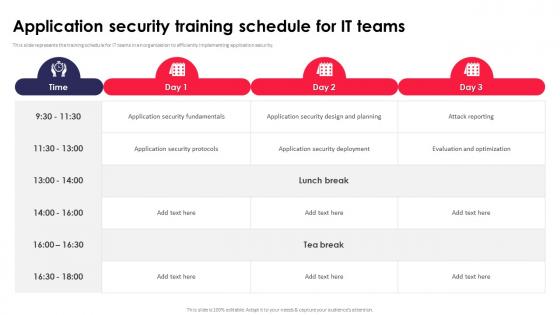
Application Security Training Schedule For IT Teams Ppt Powerpoint Portrait
This slide represents the training schedule for IT teams in an organization to efficiently implementing application security. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Application Security Training Schedule For IT Teams Ppt Powerpoint Portrait will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide represents the training schedule for IT teams in an organization to efficiently implementing application security.
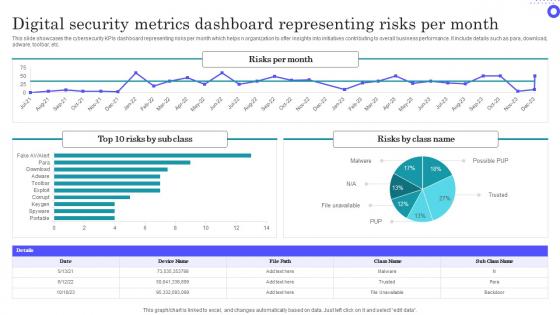
Digital Security Metrics Dashboard Representing Risks Per Month Themes Pdf
Showcasing this set of slides titled Digital Security Metrics Dashboard Representing Risks Per Month Themes Pdf The topics addressed in these templates are Digital Security, Metrics Dashboard, Representing Risks All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcases the cybersecurity KPIs dashboard representing risks per month which helps n organization to offer insights into initiatives contributing to overall business performance. It include details such as para, download, adware, toolbar, etc.

Information Security Program Strategic Agenda Process Microsoft Pdf
This slide represents action plan process for information security programs. It consists of steps such as make information security team, manage assets and inventory, evaluate risk, manage risk, create incident recovery plan, etc. Showcasing this set of slides titled Information Security Program Strategic Agenda Process Microsoft Pdf. The topics addressed in these templates are Assets And Inventory, Evaluate Risk, Manage Risk. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide represents action plan process for information security programs. It consists of steps such as make information security team, manage assets and inventory, evaluate risk, manage risk, create incident recovery plan, etc.
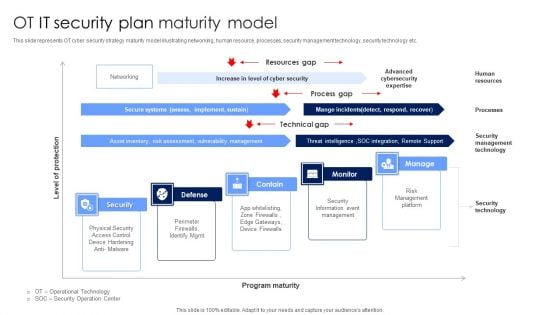
OT IT Security Plan Maturity Model Designs PDF
This slide represents OT cyber security strategy maturity model illustrating networking, human resource, processes, security management technology, security technology etc. Showcasing this set of slides titled OT IT Security Plan Maturity Model Designs PDF. The topics addressed in these templates are Security Information Event Management, Risk Management Platform, Security Technology. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Zero Trust Model Traditional Perimeter Based Network Security Overview
This slide represents the overview of traditional perimeter-based network security. The purpose of this slide is to showcase the various challenges of conventional perimeter-based security and how ZTNA can overcome those challenges. If you are looking for a format to display your unique thoughts, then the professionally designed Zero Trust Model Traditional Perimeter Based Network Security Overview is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Zero Trust Model Traditional Perimeter Based Network Security Overview and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide represents the overview of traditional perimeter-based network security. The purpose of this slide is to showcase the various challenges of conventional perimeter-based security and how ZTNA can overcome those challenges.
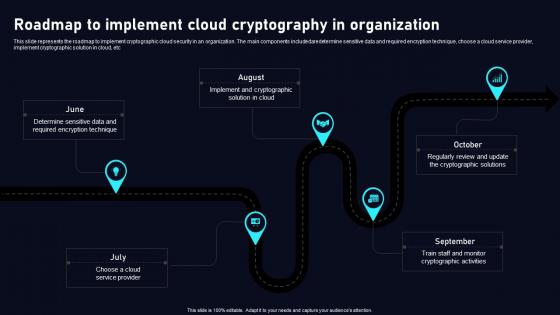
Roadmap To Implement Cloud Data Security Using Cryptography Information Pdf
This slide represents the roadmap to implement cryptographic cloud security in an organization. The main components includedaredetermine sensitive data and required encryption technique, choose a cloud service provider, implement cryptographic solution in cloud, etc Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Roadmap To Implement Cloud Data Security Using Cryptography Information Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Roadmap To Implement Cloud Data Security Using Cryptography Information Pdf today and make your presentation stand out from the rest This slide represents the roadmap to implement cryptographic cloud security in an organization. The main components includedaredetermine sensitive data and required encryption technique, choose a cloud service provider, implement cryptographic solution in cloud, etc

Application Security Testing Tool Pyramid Ppt Powerpoint Download
This slide represents the application security testing tool pyramid which includes tools such as correlation tools, test coverage analysis, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Application Security Testing Tool Pyramid Ppt Powerpoint Download a try. Our experts have put a lot of knowledge and effort into creating this impeccable Application Security Testing Tool Pyramid Ppt Powerpoint Download. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide represents the application security testing tool pyramid which includes tools such as correlation tools, test coverage analysis, etc.
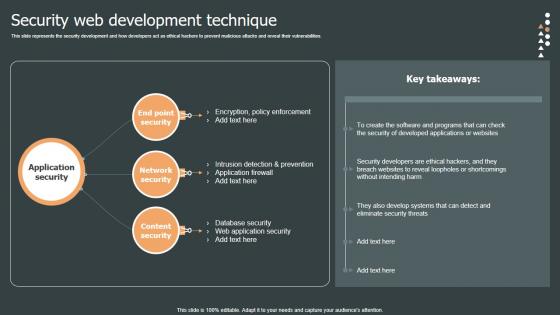
Security Web Development Role Web Designing User Engagement Topics PDF
This slide represents the security development and how developers act as ethical hackers to prevent malicious attacks and reveal their vulnerabilities. Are you searching for a Security Web Development Role Web Designing User Engagement Topics PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Security Web Development Role Web Designing User Engagement Topics PDF from Slidegeeks today. This slide represents the security development and how developers act as ethical hackers to prevent malicious attacks and reveal their vulnerabilities.
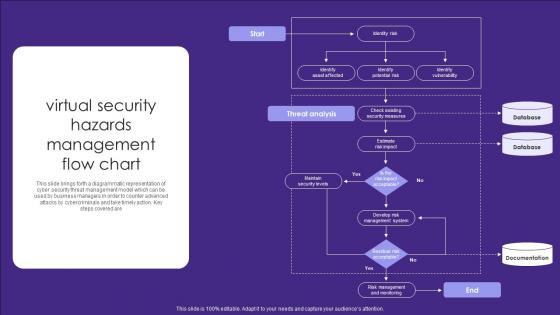
Virtual Security Hazards Management Flow Chart Infographics Pdf
This slide brings forth a diagrammatic representation of cyber security threat management model which can be used by business managers in order to counter advanced attacks by cybercriminals and take timely action. Key steps covered are Showcasing this set of slides titled Virtual Security Hazards Management Flow Chart Infographics Pdf. The topics addressed in these templates are Security Measures, Database, Documentation. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide brings forth a diagrammatic representation of cyber security threat management model which can be used by business managers in order to counter advanced attacks by cybercriminals and take timely action. Key steps covered are

CASB 2 0 IT Cloud Access Security Broker Pillar Overview
This slide represents the four major pillars of cloud access security broker. The purpose of this slide is to showcase the main pillars of implementing a cloud access security broker. The pillars include compliance, visibility, threat protection, and data security. Are you searching for a CASB 2 0 IT Cloud Access Security Broker Pillar Overview that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download CASB 2 0 IT Cloud Access Security Broker Pillar Overview from Slidegeeks today. This slide represents the four major pillars of cloud access security broker. The purpose of this slide is to showcase the main pillars of implementing a cloud access security broker. The pillars include compliance, visibility, threat protection, and data security.


 Continue with Email
Continue with Email

 Home
Home


































