Security Services
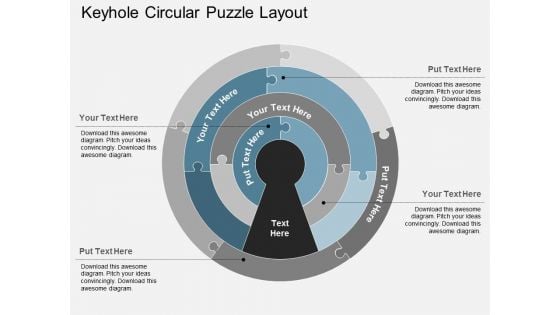
Keyhole Circular Puzzle Layout Powerpoint Templates
This slide has been designed with circular puzzle with key hole in center. This Powerpoint template is suitable to present key steps of success. This professional slide helps in making an instant impact on viewers.

Cloud Computing Project Analysis Diagram Powerpoint Template
Our above PPT slide contains graphics of cloud with technology icons. This PowerPoint template may be used for project related to cloud computing. Use this diagram to impart more clarity to data and to create more sound impact on viewers.
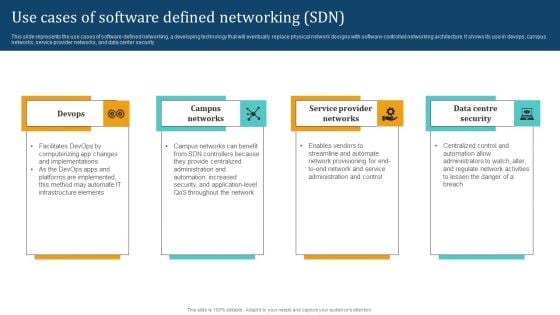
Empowering Network Agility Through SDN Use Cases Of Software Defined Networking SDN Elements PDF
This slide represents the use cases of software defined networking, a developing technology that will eventually replace physical network designs with software controlled networking architecture. It shows its use in devops, campus networks, service provider networks, and data center security. Presenting this PowerPoint presentation, titled Empowering Network Agility Through SDN Use Cases Of Software Defined Networking SDN Elements PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Empowering Network Agility Through SDN Use Cases Of Software Defined Networking SDN Elements PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Empowering Network Agility Through SDN Use Cases Of Software Defined Networking SDN Elements PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.
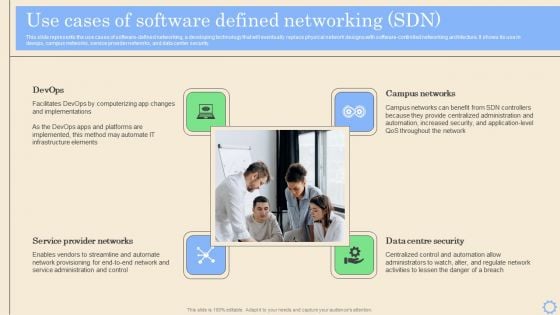
Software Defined Networking Development Strategies Use Cases Of Software Defined Networking SDN Ideas PDF
This slide represents the use cases of software-defined networking, a developing technology that will eventually replace physical network designs with software-controlled networking architecture. It shows its use in devops, campus networks, service provider networks, and data center security. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Software Defined Networking Development Strategies Use Cases Of Software Defined Networking SDN Ideas PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Software Defined Networking Development Strategies Use Cases Of Software Defined Networking SDN Ideas PDF today and make your presentation stand out from the rest.

Deploying SDN System Use Cases Of Software Defined Networking SDN Ideas PDF
This slide represents the use cases of software-defined networking, a developing technology that will eventually replace physical network designs with software-controlled networking architecture. It shows its use in DevOps, campus networks, service provider networks, and data center security. Slidegeeks has constructed Deploying SDN System Use Cases Of Software Defined Networking SDN Ideas PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.
Use Cases Of Software Defined Networking SDN Ppt Slides Show PDF
This slide represents the use cases of software-defined networking, a developing technology that will eventually replace physical network designs with software-controlled networking architecture. It shows its use in devops, campus networks, service provider networks, and data center security. This Use Cases Of Software Defined Networking SDN Ppt Slides Show PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
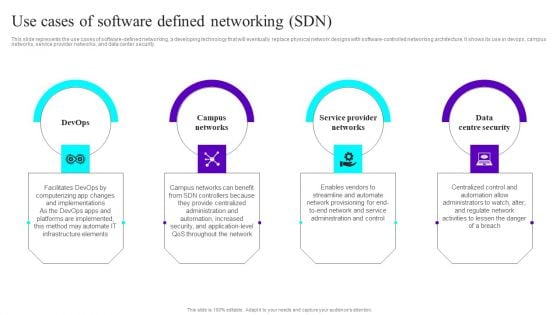
Use Cases Of Software Defined Networking SDN Ppt Styles Aids PDF
This slide represents the use cases of software-defined networking, a developing technology that will eventually replace physical network designs with software-controlled networking architecture. It shows its use in devops, campus networks, service provider networks, and data center security. This Use Cases Of Software Defined Networking SDN Ppt Styles Aids PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
Five Key Steps For Business Analysis Powerpoint Template
This PowerPoint template has been designed with five icons around key. This PowerPoint template helps to exhibit directions for strategic planning. Use this diagram slide to build an exclusive presentation.
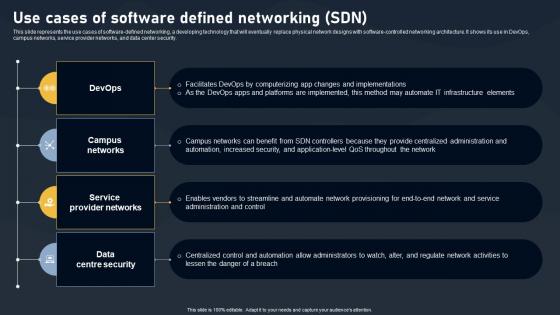
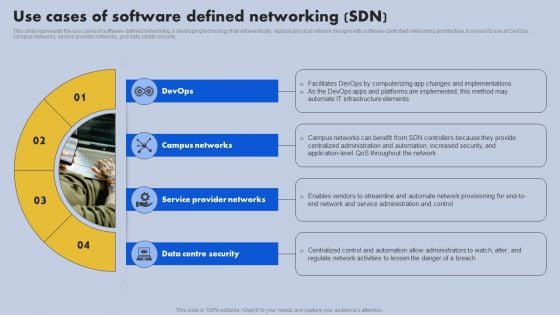
Use Cases Of Software Defined Networking SDN Building Blocks Summary Pdf
This slide represents the use cases of software-defined networking, a developing technology that will eventually replace physical network designs with software-controlled networking architecture. It shows its use in DevOps, campus networks, service provider networks, and data center security.Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Use Cases Of Software Defined Networking SDN Building Blocks Summary Pdf was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Use Cases Of Software Defined Networking SDN Building Blocks Summary Pdf. This slide represents the use cases of software defined networking, a developing technology that will eventually replace physical network designs with software controlled networking architecture. It shows its use in DevOps, campus networks, service provider networks, and data center security.

ESO System Center System Ppt PowerPoint Presentation File Portrait PDF
This slide covers enterprise security operation center system. It involves business security, data security, infrastructure, office network and application security. Showcasing this set of slides titled ESO System Center System Ppt PowerPoint Presentation File Portrait PDF. The topics addressed in these templates are Security Risks, Business Security, Data Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Food Ingredient Adulteration Vulnerability Prevention Strategy Information Pdf
This slide provide information about food ingredient fraud vulnerability mitigation plan to protect organization image. It includes elements such as facility security, building security and security assessments Showcasing this set of slides titled Food Ingredient Adulteration Vulnerability Prevention Strategy Information Pdf. The topics addressed in these templates are Security Assessments, Building Security, Facility Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide provide information about food ingredient fraud vulnerability mitigation plan to protect organization image. It includes elements such as facility security, building security and security assessments
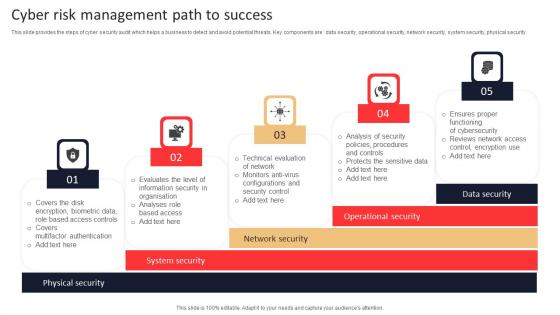
Cyber Risk Management Path To Success Inspiration Pdf
This slide provides the steps of cyber security audit which helps a business to detect and avoid potential threats. Key components are data security, operational security, network security, system security, physical security. Showcasing this set of slides titled Cyber Risk Management Path To Success Inspiration Pdf. The topics addressed in these templates are Biometric Data, Information Security, Analyses. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide provides the steps of cyber security audit which helps a business to detect and avoid potential threats. Key components are data security, operational security, network security, system security, physical security.
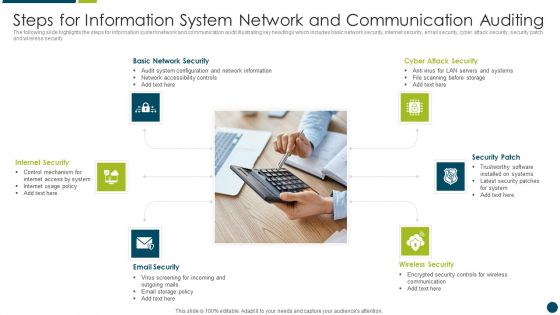
Steps For Information System Network And Communication Auditing Topics PDF
The following slide highlights the steps for information system network and communication audit illustrating key headings which includes basic network security, internet security, email security, cyber attack security, security patch and wireless security Presenting Steps For Information System Network And Communication Auditing Topics PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Basic Network Security, Internet Security, Security Patch. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully
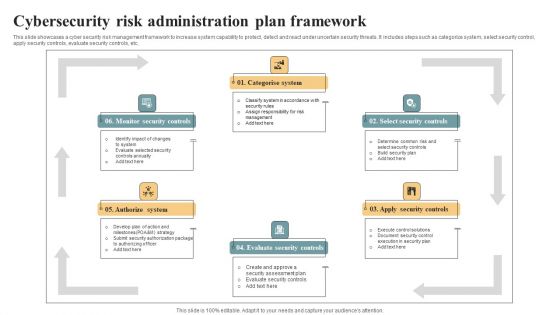
Cybersecurity Risk Administration Plan Framework Ideas PDF
This slide showcases a cyber security risk management framework to increase system capability to protect, detect and react under uncertain security threats. It includes steps such as categorize system, select security control, apply security controls, evaluate security controls, etc. Presenting Cybersecurity Risk Administration Plan Framework Ideas PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Categorise System, Select Security Controls, Apply Security Controls. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Convergence Strategy Information IT OT Team Responsibilities Based On Target Slides PDF
This slide covers IT or OT cyber security Team responsibilities including security department, security functions etc. Deliver an awe inspiring pitch with this creative Convergence Strategy Information IT OT Team Responsibilities Based On Target Slides PDF bundle. Topics like OT Security Functions, Security Architecture And Engineering, Primary Responsibility, Shared Responsibility can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
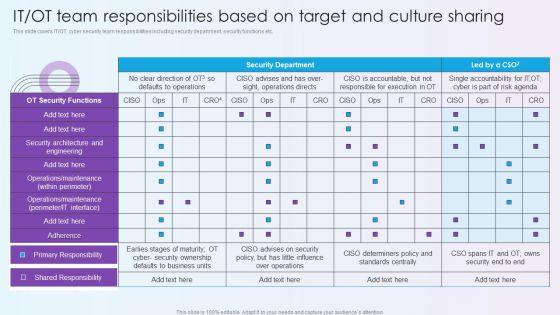
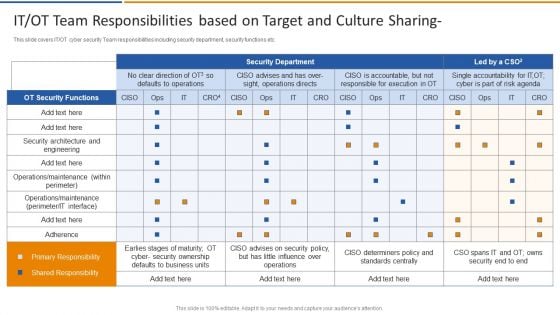
Digitalization Of Operative Enterprises IT OT Team Responsibilities Based On Target And Culture Sharing Microsoft PDF
This slide covers IT or OT cyber security team responsibilities including security department, security functions etc. Deliver and pitch your topic in the best possible manner with this Digitalization Of Operative Enterprises IT OT Team Responsibilities Based On Target And Culture Sharing Microsoft PDF. Use them to share invaluable insights on Security Functions, Security Ownership, Determiners and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Smart Venture Digitial Transformation IT OT Team Responsibilities Based On Target Structure PDF
This slide covers IT or OT cyber security Team responsibilities including security department, security functions etc. Deliver an awe inspiring pitch with this creative Smart Venture Digitial Transformation IT OT Team Responsibilities Based On Target Structure PDF bundle. Topics like OT Security Functions, Security architecture, Primary Responsibility can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
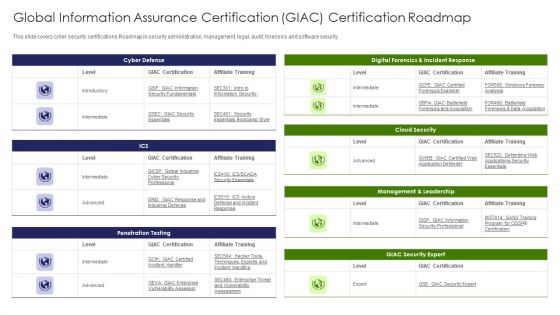
IT Professional Data Certification Program Global Information Assurance Certification GIAC Certification Roadmap Sample PDF
This slide covers cyber security certifications Roadmap in security administration, management, legal, audit, forensics and software security. Deliver and pitch your topic in the best possible manner with this IT Professional Data Certification Program Global Information Assurance Certification GIAC Certification Roadmap Sample PDF. Use them to share invaluable insights on Cloud Security, Management, Security Expert and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Stock Photo 3d Globe Green Glass PowerPoint Slide
This graphic image has been crafted with globe and chain. In this image globe is secured with chain which shows the concept of global security. Use this image to display global security issues and benefits in any presentation.
Acquired Customer Relationship Ppt PowerPoint Presentation Complete Deck With Slides
This is a acquired customer relationship ppt powerpoint presentation complete deck with slides. This is a one stage process. The stages in this process are customer planning, communication, business, marketing, network.

Top To Down Approach For Business Information Protection Demonstration PDF
This slide covers top to down approach for business security which includes security leadership, program, policies and management. Further, it includes user management and information asset security.Pitch your topic with ease and precision using this Top To Down Approach For Business Information Protection Demonstration PDF. This layout presents information on Security Leadership, Security Program, Security Policies. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
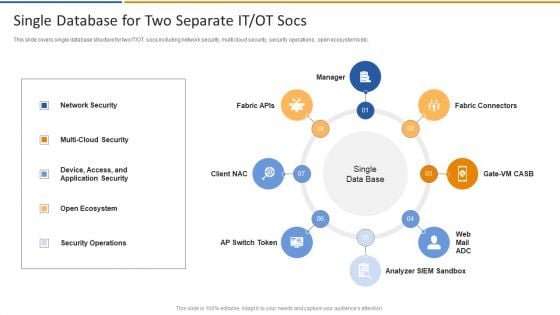
Smart Venture Digitial Transformation Single Database For Two Separate IT OT Socs Inspiration PDF
This slide covers single database structure for two IT or OT socs including network security, multi cloud security, security operations , open ecosystems etc. Presenting Smart Venture Digitial Transformation Single Database For Two Separate IT OT Socs Inspiration PDF to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like Network Security, Multi Cloud Security, Device Access, Application Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
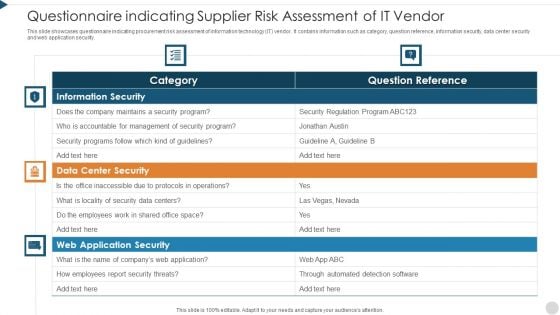
Questionnaire Indicating Supplier Risk Assessment Of It Vendor Themes PDF
This slide showcases questionnaire indicating procurement risk assessment of information technology IT vendor. It contains information such as category, question reference, information security, data center security and web application security. Pitch your topic with ease and precision using this questionnaire indicating supplier risk assessment of it vendor themes pdf. This layout presents information on information security, data center security, web application security. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Five Steps Risk Management Process Of Insurance Process Mockup PDF
This slide show the risk management process which can be used by banking insurance company. It includes information security program, security codes, cyber security and training. Pitch your topic with ease and precision using this Five Steps Risk Management Process Of Insurance Process Mockup PDF. This layout presents information on Information Security Program, Security Codes, Cyber Security. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
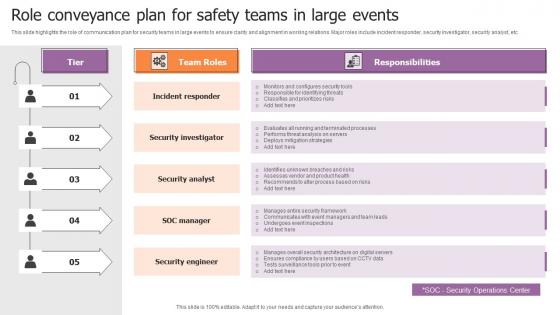
Role Conveyance Plan For Safety Teams In Large Events Ideas Pdf
This slide highlights the role of communication plan for security teams in large events to ensure clarity and alignment in working relations. Major roles include incident responder, security investigator, security analyst, etc. Showcasing this set of slides titled Role Conveyance Plan For Safety Teams In Large Events Ideas Pdf. The topics addressed in these templates are Incident Responder, Security Investigator, Security Analyst. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide highlights the role of communication plan for security teams in large events to ensure clarity and alignment in working relations. Major roles include incident responder, security investigator, security analyst, etc.

Stock Photo Blue Umbrella Over Usa Flag Print Text PowerPoint Slide
This Power Point slide has been designed with graphic of blue umbrella and US flag design. This image slide contains the concept of USA security and protection schemes. Use this professional design to build presentation for security related topics.
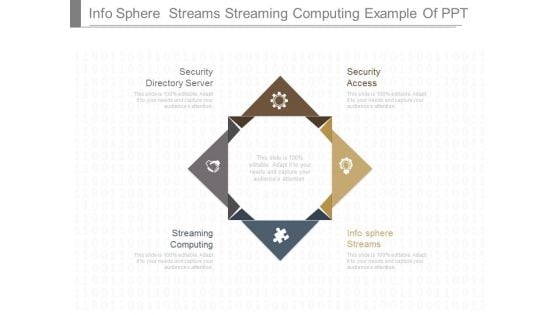
Info Sphere Streams Streaming Computing Example Of Ppt
This is a info sphere streams streaming computing example of ppt. This is a four stage process. The stages in this process are security directory server, security access, streaming computing, info sphere streams.

Critical Infrastructure And Climate Powerpoint Guide
This is a critical infrastructure and climate powerpoint guide. This is a four stage process. The stages in this process are critical infrastructure and climate, national security strategy, execute order, homeland security review.

Profile Monitoring Methodology Sample Diagram Sample Ppt Presentation
This is a profile monitoring methodology sample diagram sample ppt presentation. This is a five stage process. The stages in this process are macro analysis, security screening, gaussian kernel, security screening, sector and asset class focus.
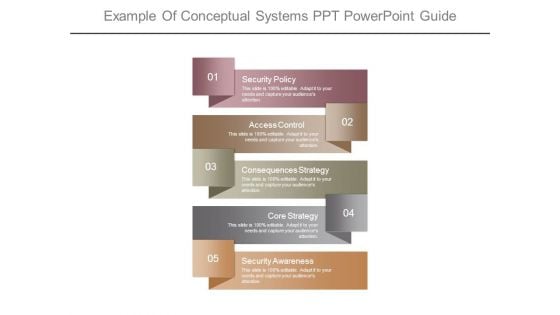
Example Of Conceptual Systems Ppt Powerpoint Guide
This is a example of conceptual systems ppt powerpoint guide. This is a five stage process. The stages in this process are security policy, access control, consequences strategy, core strategy, security awareness.
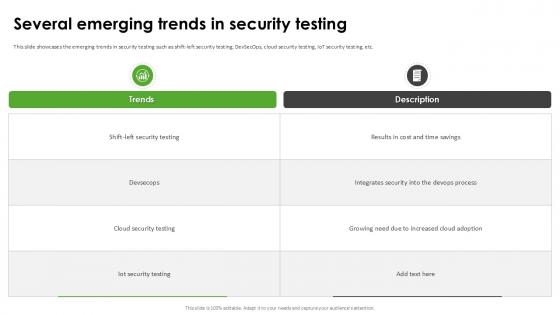
Several Emerging Trends In Harnessing The World Of Ethical Ppt Powerpoint
This slide showcases the emerging trends in security testing such as shift-left security testing, DevSecOps, cloud security testing, IoT security testing, etc. Are you searching for a Several Emerging Trends In Harnessing The World Of Ethical Ppt Powerpoint that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Several Emerging Trends In Harnessing The World Of Ethical Ppt Powerpoint from Slidegeeks today. This slide showcases the emerging trends in security testing such as shift-left security testing, DevSecOps, cloud security testing, IoT security testing, etc.

Quarterly Cybersecurity Training Program And Schedule Timeline Rules PDF
This slide covers the roadmap for various courses in security awareness programs. It includes cyber system management, password security program, insider threats program, e mail security program.Presenting Quarterly Cybersecurity Training Program And Schedule Timeline Rules PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Risk Assessment, Security Program, Threats Program. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Cyber Exploitation IT Interview Schedule For New Professionals Icons PDF
This slide represents the interview schedule for new employees, including ethical hackers, security consultants, and IT security analysts to be hired to prevent hacking. Deliver and pitch your topic in the best possible manner with this cyber exploitation it interview schedule for new professionals icons pdf. Use them to share invaluable insights on it security analyst, certified ethical hacker, security consultant and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
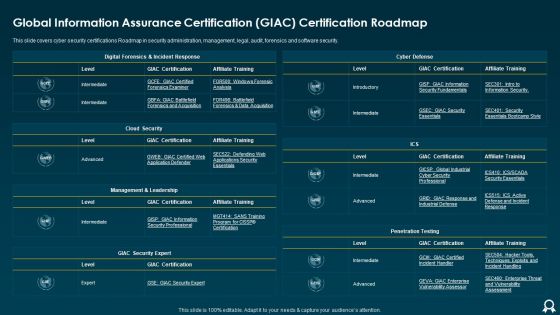
Global Information Assurance Certification GIAC Certification Roadmap Formats PDF
This slide covers cyber security certifications Roadmap in security administration, management, legal, audit, forensics and software security. Deliver an awe inspiring pitch with this creative Global Information Assurance Certification GIAC Certification Roadmap Formats PDF bundle. Topics like Cloud Security, Cyber Defense, Management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
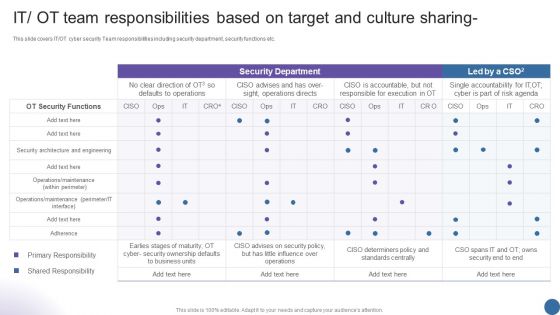
IT OT Team Responsibilities Based On Target Managing Organizational Transformation Microsoft PDF
This slide covers IT OT cyber security Team responsibilities including security department, security functions etc. Deliver an awe inspiring pitch with this creative IT OT Team Responsibilities Based On Target Managing Organizational Transformation Microsoft PDF bundle. Topics like Security Department, Team Responsibilities, Target can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
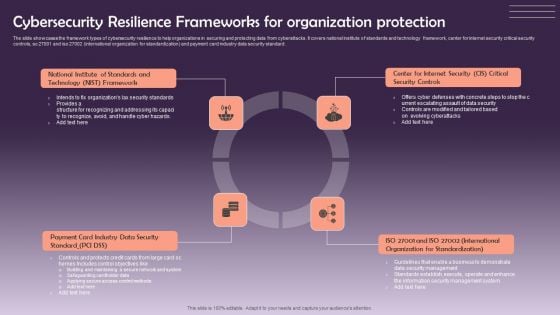
Cybersecurity Resilience Frameworks For Organization Protection Information PDF
The slide showcases the framework types of cybersecurity resilience to help organizations in securing and protecting data from cyberattacks. It covers national institute of standards and technology framework, center for internet security critical security controls, so 27001 and iso 27002 international organization for standardization and payment card industry data security standard. Presenting Cybersecurity Resilience Frameworks For Organization Protection Information PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Data Security, Organization For Standardization, Security Controls. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Table Of Contents Ppt Inspiration Guide PDF
Deliver an awe inspiring pitch with this creative table of contents ppt inspiration guide pdf bundle. Topics like security awareness program, security strategies, budget, communication plan, security awareness, cost can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
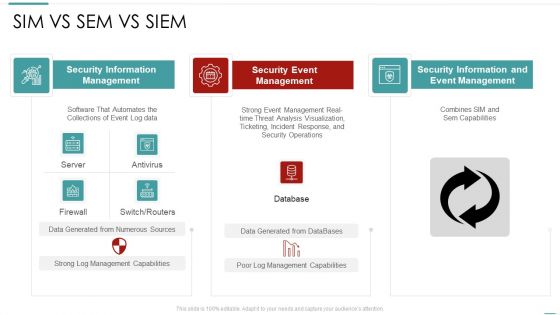
Risk Recognition Automation Sim Vs Sem Vs Siem Ppt Professional Background Designs PDF
Deliver and pitch your topic in the best possible manner with this risk recognition automation sim vs sem vs siem ppt professional background designs pdf. Use them to share invaluable insights on security information management, security event management, security information and event management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
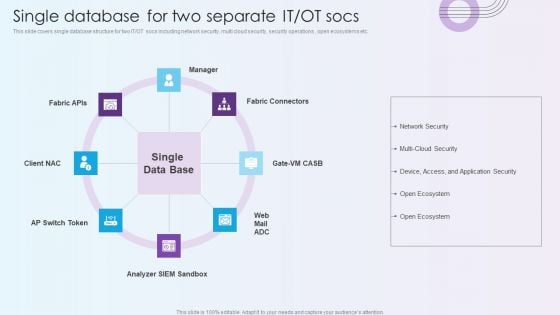
Digitalization Of Operative Enterprises Single Database For Two Separate IT OT Socs Structure PDF
This slide covers single database structure for two IT or OT socs including network security, multi cloud security, security operations , open ecosystems etc.This is a Digitalization Of Operative Enterprises Single Database For Two Separate IT OT Socs Structure PDF template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Analyzer, Network Security, Multi Cloud Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Five Steps Insurance Risk Management Procedure Professional PDF
This slide show the risk management process of an insurance company. It includes information security program, security codes, cyber security and training. Persuade your audience using this Five Steps Insurance Risk Management Procedure Professional PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Security Codes, Cyber Security, Stay Informed. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

IT Risk Control Strategies Risk Management Framework Mockup PDF
This slide shows the framework for information technology risk management which includes cyber security governance, IT and security risk assessment, training and awareness, security operation centre, independent audit and gap analysis. Persuade your audience using this IT Risk Control Strategies Risk Management Framework Mockup PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Cyber Security Governance, IT Risk Assessment, Security Assessment. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Major Advantages Of Banking Industry Revolution Challenges And Solutions Regarding Diagrams PDF
This slide shows the benefits of mobile banking that improves and enhances the banking services and leads to a positive digital banking transformation such as 24 7 service availability, paperless transactions, facilitation of location-based services, increased efficiency and compliance etc. Presenting major advantages of banking industry revolution challenges and solutions regarding diagrams pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like securing media communications, drifting away from legacy applications, security issues In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Conveyance Plan For Safety Touchpoints In Large Events Icons Pdf
This slide consists of a communication plan for security touchpoints in large events which need to be addressed by security teams to ensure the seamless movement of attendees. Major security touchpoints are outside venue, entrances, interior areas and admission events. Pitch your topic with ease and precision using this Conveyance Plan For Safety Touchpoints In Large Events Icons Pdf. This layout presents information on Outside Venue, Entrances, Interior Areas. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide consists of a communication plan for security touchpoints in large events which need to be addressed by security teams to ensure the seamless movement of attendees. Major security touchpoints are outside venue, entrances, interior areas and admission events.

Business Information Application Protection Testing Flow Chart Themes PDF
This slide covers business application security testing flow chart which includes secure application model, security standard recognition and privacy testing.Pitch your topic with ease and precision using this Business Information Application Protection Testing Flow Chart Themes PDF. This layout presents information on Security Consistency, Target Weighting, Target Recognition. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
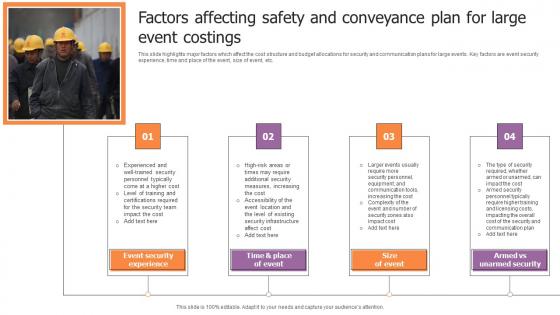
Factors Affecting Safety And Conveyance Plan For Large Event Costings Pictures Pdf
This slide highlights major factors which affect the cost structure and budget allocations for security and communication plans for large events. Key factors are event security experience, time and place of the event, size of event, etc. Pitch your topic with ease and precision using this Factors Affecting Safety And Conveyance Plan For Large Event Costings Pictures Pdf. This layout presents information on Event Security Experience, Size Of Event, Armed Vs Unarmed Security. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide highlights major factors which affect the cost structure and budget allocations for security and communication plans for large events. Key factors are event security experience, time and place of the event, size of event, etc.
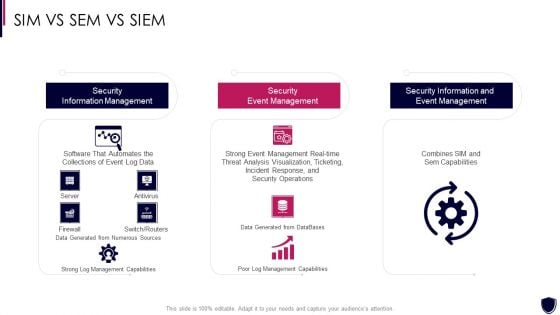
Enhancing Cyber Safety With Vulnerability Administration SIM Vs SEM Vs SIEM Brochure PDF
Presenting enhancing cyber safety with vulnerability administration sim vs sem vs siem brochure pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like security information management, security event management, security information and event management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Major Challenges And Solutions Harnessing The World Of Ethical Ppt Powerpoint
This slide represents the major challenges of security testing with solutions such as dynamic threat landscape, false positives in security testing, limitation of security testing efficiency, etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Major Challenges And Solutions Harnessing The World Of Ethical Ppt Powerpoint was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Major Challenges And Solutions Harnessing The World Of Ethical Ppt Powerpoint This slide represents the major challenges of security testing with solutions such as dynamic threat landscape, false positives in security testing, limitation of security testing efficiency, etc.
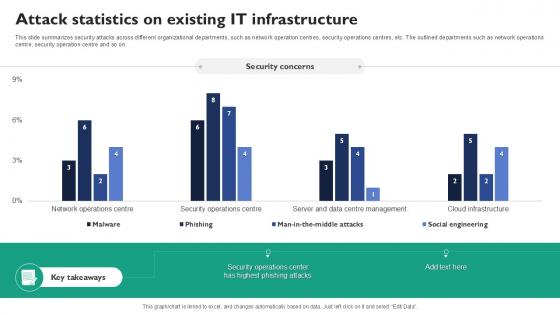
Attack Statistics On Existing It Infrastructure Corrective Regression Testing Ppt Slides
This slide summarizes security attacks across different organizational departments, such as network operation centres, security operations centres, etc. The outlined departments such as network operations centre, security operation centre and so on. Boost your pitch with our creative Attack Statistics On Existing It Infrastructure Corrective Regression Testing Ppt Slides. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide summarizes security attacks across different organizational departments, such as network operation centres, security operations centres, etc. The outlined departments such as network operations centre, security operation centre and so on.
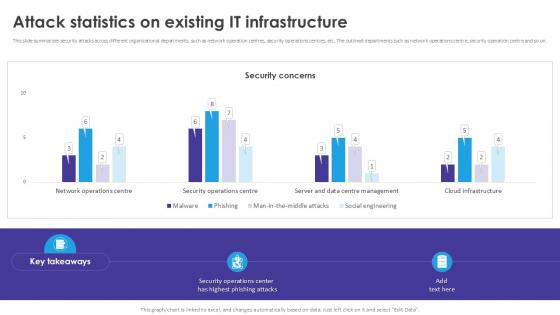
Attack Statistics On Existing Automated Regression Testing And Achieving PPT Slide
This slide summarizes security attacks across different organizational departments, such as network operation centres, security operations centres, etc. The outlined departments such as network operations centre, security operation centre and so on. Boost your pitch with our creative Attack Statistics On Existing Automated Regression Testing And Achieving PPT Slide Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide summarizes security attacks across different organizational departments, such as network operation centres, security operations centres, etc. The outlined departments such as network operations centre, security operation centre and so on.
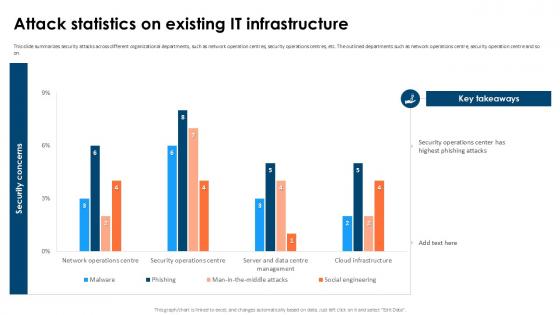
Attack Statistics On Partial Regression Testing For A Best PPT Slide
This slide summarizes security attacks across different organizational departments, such as network operation centres, security operations centres, etc. The outlined departments such as network operations centre, security operation centre and so on. Boost your pitch with our creative Attack Statistics On Partial Regression Testing For A Best PPT Slide Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide summarizes security attacks across different organizational departments, such as network operation centres, security operations centres, etc. The outlined departments such as network operations centre, security operation centre and so on.
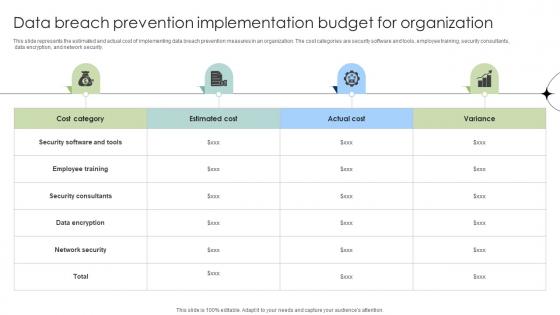
Data Breach Prevention Implementation Budget For Organization Data Fortification Strengthening Defenses
This slide represents the estimated and actual cost of implementing data breach prevention measures in an organization. The cost categories are security software and tools, employee training, security consultants, data encryption, and network security.If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Data Breach Prevention Implementation Budget For Organization Data Fortification Strengthening Defenses and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide represents the estimated and actual cost of implementing data breach prevention measures in an organization. The cost categories are security software and tools, employee training, security consultants, data encryption, and network security.
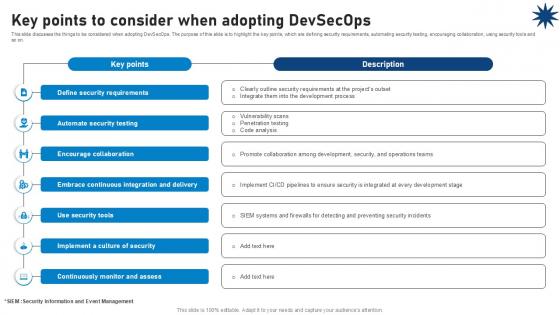
Key Points To Consider When Adopting Devsecops Role Of Devsecops Ppt Sample
This slide discusses the things to be considered when adopting DevSecOps. The purpose of this slide is to highlight the key points, which are defining security requirements, automating security testing, encouraging collaboration, using security tools and so on. Find a pre-designed and impeccable Key Points To Consider When Adopting Devsecops Role Of Devsecops Ppt Sample The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide discusses the things to be considered when adopting DevSecOps. The purpose of this slide is to highlight the key points, which are defining security requirements, automating security testing, encouraging collaboration, using security tools and so on.
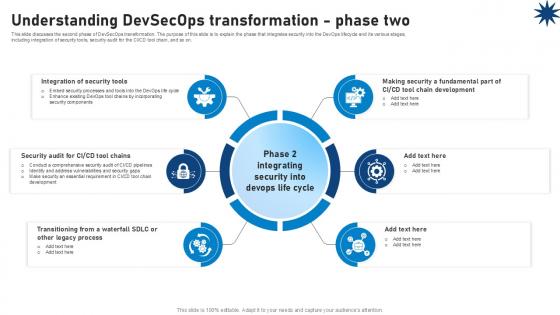
Understanding Devsecops Transformation Phase Two Role Of Devsecops Ppt Powerpoint
This slide discusses the second phase of DevSecOps transformation. The purpose of this slide is to explain the phase that integrates security into the DevOps lifecycle and its various stages, including integration of security tools, security audit for the CICD tool chain, and so on. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Understanding Devsecops Transformation Phase Two Role Of Devsecops Ppt Powerpoint and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide discusses the second phase of DevSecOps transformation. The purpose of this slide is to explain the phase that integrates security into the DevOps lifecycle and its various stages, including integration of security tools, security audit for the CICD tool chain, and so on.
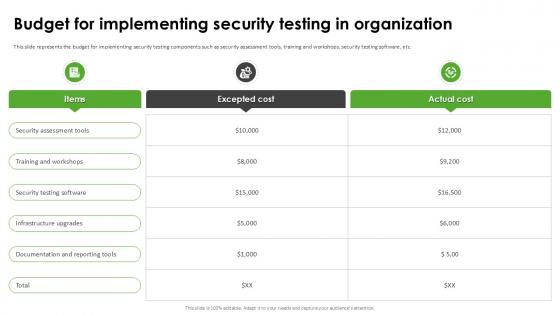
Budget For Implementing Harnessing The World Of Ethical Ppt Presentation
This slide represents the budget for implementing security testing components such as security assessment tools, training and workshops, security testing software, etc. Get a simple yet stunning designed Budget For Implementing Harnessing The World Of Ethical Ppt Presentation It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Budget For Implementing Harnessing The World Of Ethical Ppt Presentation can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide represents the budget for implementing security testing components such as security assessment tools, training and workshops, security testing software, etc.
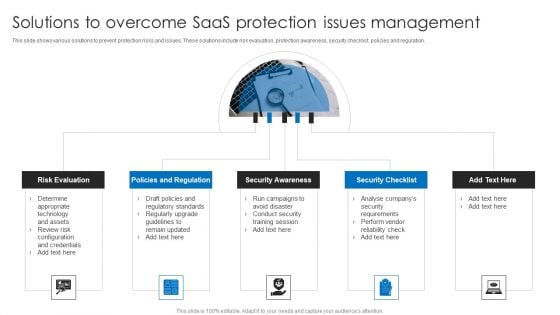
Solutions To Overcome Saas Protection Issues Management Information PDF
This slide shows various solutions to prevent protection risks and issues. These solutions include risk evaluation, protection awareness, security checklist, policies and regulation. Presenting Solutions To Overcome Saas Protection Issues Management Information PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Policies And Regulation, Security Awareness, Security Checklist, Risk Evaluation. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
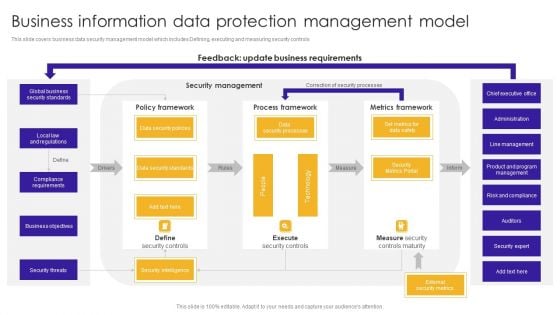
Business Information Data Protection Management Model Structure PDF
This slide covers business data security management model which includes Defining, executing and measuring security controls.Pitch your topic with ease and precision using this Business Information Data Protection Management Model Structure PDF. This layout presents information on Compliance Requirements, Security Standards, Controls Maturity. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
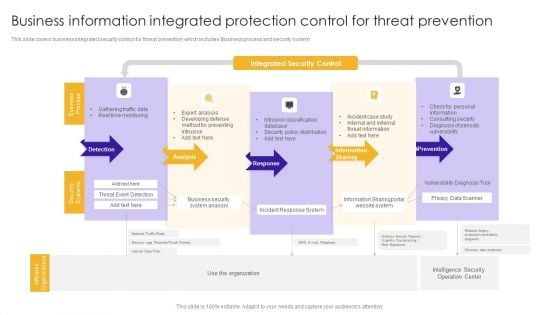
Business Information Integrated Protection Control For Threat Prevention Graphics PDF
This slide covers business integrated security control for threat prevention which includes Business process and security system.Pitch your topic with ease and precision using this Business Information Integrated Protection Control For Threat Prevention Graphics PDF. This layout presents information on Incident Response, Security Policy Distribution, Threat Information. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
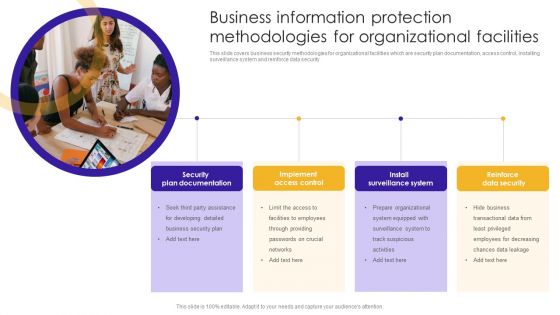
Business Information Protection Methodologies For Organizational Facilities Demonstration PDF
This slide covers business security methodologies for organizational facilities which are security plan documentation, access control, installing surveillance system and reinforce data security.Presenting Business Information Protection Methodologies For Organizational Facilities Demonstration PDF to dispense important information. This template comprises one stage. It also presents valuable insights into the topics including Plan Documentation, Implement Access, Surveillance System. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
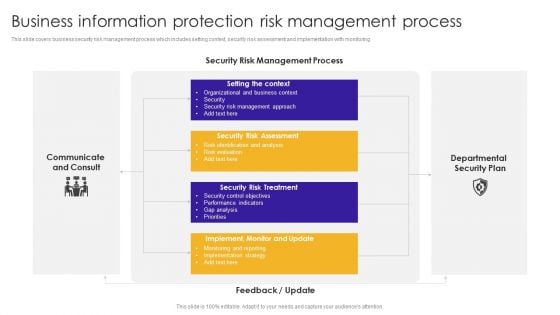
Business Information Protection Risk Management Process Structure PDF
This slide covers business security risk management process which includes setting context, security risk assessment and implementation with monitoring. Pitch your topic with ease and precision using this Business Information Protection Risk Management Process Structure PDF. This layout presents information on Organizational Business, Security Risk Assessment, Performance Indicators. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
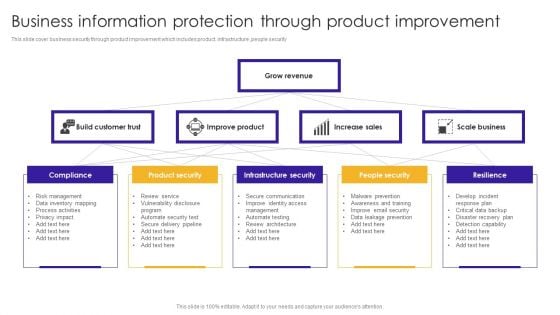
Business Information Protection Through Product Improvement Infographics PDF
This slide cover business security through product improvement which includes product, infrastructure ,people security. Pitch your topic with ease and precision using this Business Information Protection Through Product Improvement Infographics PDF. This layout presents information on Improve Product, Scale Business, Infrastructure Security. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.


 Continue with Email
Continue with Email

 Home
Home


































