Security Services
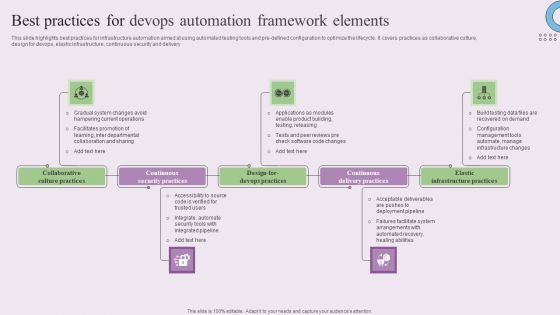
Best Practices For Devops Automation Framework Elements Themes PDF
This slide highlights best practices for infrastructure automation aimed at using automated testing tools and pre-defined configuration to optimize the lifecycle. It covers practices as collaborative culture, design for devops, elastic infrastructure, continuous security and delivery. Presenting Best Practices For Devops Automation Framework Elements Themes PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Collaborative Culture Practices, Continuous Security Practices, Continuous Delivery Practices. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Transformational IT Trends In Oil And Gas Industry Download PDF
This slide highlights mega trends in oil and gas industry aimed at facing legislation, competition, changes in market to maintain increased sustainability. It covers cloud messaging, security and operational risk management, smart mobility and smart and oil gas fields. Persuade your audience using this Transformational IT Trends In Oil And Gas Industry Download PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Cloud Messaging, Smart Mobility, Smart Oil Gas Fields, Security And Operational, Risk Management. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Why CASB Is Important For Businesses Ppt PowerPoint Presentation File Example File PDF
This slide outlines the importance of CASB for different organizations. The purpose of this slide is to showcase the various reasons for businesses to invest in the cloud access security broker model, including increased cloud adoption, better security, compliance, and cost-effective and centralized management. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Why CASB Is Important For Businesses Ppt PowerPoint Presentation File Example File PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.
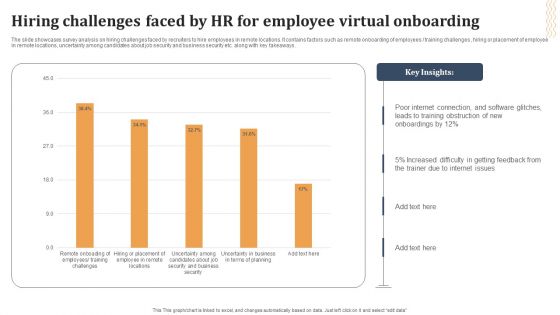
Hiring Challenges Faced By HR For Employee Virtual Onboarding Ideas PDF
The slide showcases survey analysis on hiring challenges faced by recruiters to hire employees in remote locations. It contains factors such as remote onboarding of employees training challenges , hiring or placement of employee in remote locations, uncertainty among candidates about job security and business security etc. along with key takeaways. Showcasing this set of slides titled Hiring Challenges Faced By HR For Employee Virtual Onboarding Ideas PDF. The topics addressed in these templates are Internet Connection, Software Glitches, Internet Issues. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
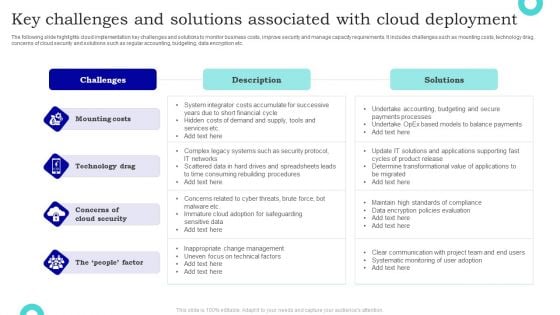
Key Challenges And Solutions Associated With Cloud Deployment Introduction PDF
The following slide highlights cloud implementation key challenges and solutions to monitor business costs, improve security and manage capacity requirements. It includes challenges such as mounting costs, technology drag, concerns of cloud security and solutions such as regular accounting, budgeting, data encryption etc. Pitch your topic with ease and precision using this Key Challenges And Solutions Associated With Cloud Deployment Introduction PDF. This layout presents information on Challenges, Description, Solutions. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Key AI Trends Associated With Financial Sector Applications And Impact Themes Pdf
This slide represents key artificial intelligence tools related to financial sector. It includes huperautomation, AI-powered advisory, financial security and personalized offering. Find a pre-designed and impeccable Key AI Trends Associated With Financial Sector Applications And Impact Themes Pdf. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide represents key artificial intelligence tools related to financial sector. It includes huperautomation, AI-powered advisory, financial security and personalized offering.
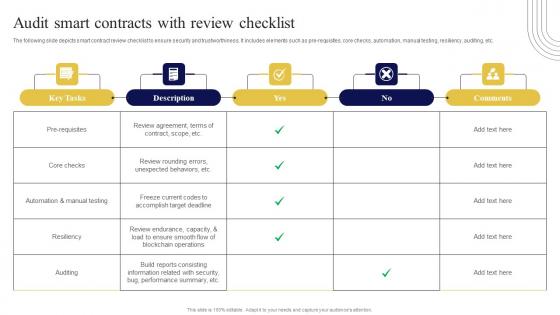
Audit Smart Contracts With Review Exploring Investment Opportunities Infographics Pdf
The following slide depicts smart contract review checklist to ensure security and trustworthiness. It includes elements such as pre-requisites, core checks, automation, manual testing, resiliency, auditing, etc. There are so many reasons you need a Audit Smart Contracts With Review Exploring Investment Opportunities Infographics Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. The following slide depicts smart contract review checklist to ensure security and trustworthiness. It includes elements such as pre-requisites, core checks, automation, manual testing, resiliency, auditing, etc.
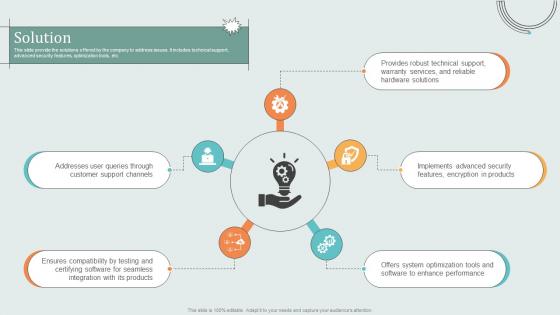
Solution Hardware Technology Provider Business Model BMC SS V
This slide provide the solutions offered by the company to address issues. It includes technical support, advanced security features, optimization tools, etc. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Solution Hardware Technology Provider Business Model BMC SS V and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide provide the solutions offered by the company to address issues. It includes technical support, advanced security features, optimization tools, etc.
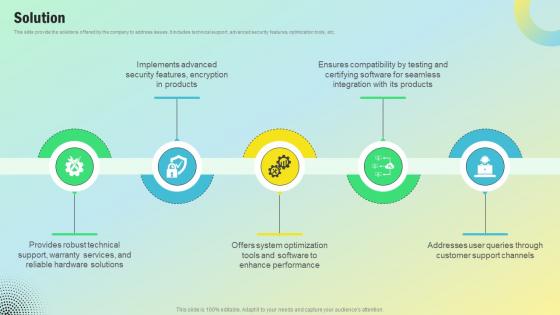
Solution Personal Computing Company Revenue Model BMC SS V
This slide provide the solutions offered by the company to address issues. It includes technical support, advanced security features, optimization tools, etc. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Solution Personal Computing Company Revenue Model BMC SS V and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide provide the solutions offered by the company to address issues. It includes technical support, advanced security features, optimization tools, etc.
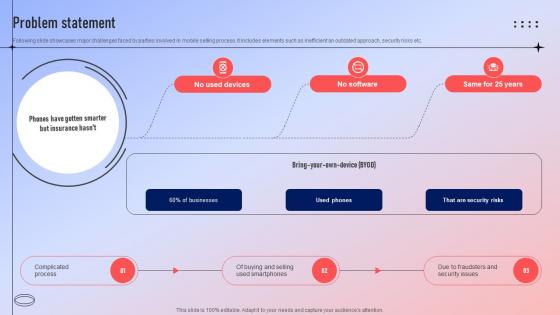
Problem Statement Fundraising Pitch Deck For Ecommerce Platform
Following slide showcases major challenges faced by parties involved in mobile selling process. It includes elements such as inefficient an outdated approach, security risks etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Problem Statement Fundraising Pitch Deck For Ecommerce Platform. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. Following slide showcases major challenges faced by parties involved in mobile selling process. It includes elements such as inefficient an outdated approach, security risks etc.

Best Practices To Optimize Cloud Migration Process Data Migration From On Premises
This slide showcases various tips which can be used for cloud migration success such as prioritize application, dependency mapping and create security measures. There are so many reasons you need a Best Practices To Optimize Cloud Migration Process Data Migration From On Premises. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide showcases various tips which can be used for cloud migration success such as prioritize application, dependency mapping and create security measures.

Address Challenges Associated With Legacy Systems DT SS V
This slide addresses the challenges associated with legacy systems and how it impact digital transformation of SMEs. It includes outdated technology, security vulnerabilities and lack of flexibility.Find a pre-designed and impeccable Address Challenges Associated With Legacy Systems DT SS V. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide addresses the challenges associated with legacy systems and how it impact digital transformation of SMEs. It includes outdated technology, security vulnerabilities and lack of flexibility.
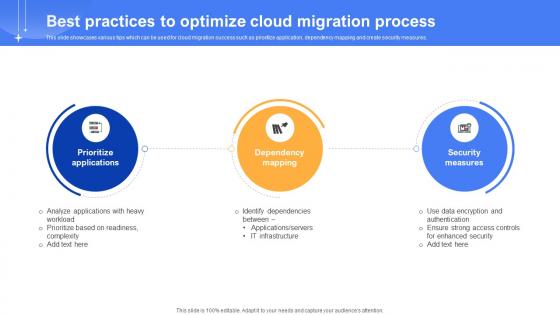
Effective Data Migration Best Practices To Optimize Cloud Migration Process
This slide showcases various tips which can be used for cloud migration success such as prioritize application, dependency mapping and create security measures. There are so many reasons you need a Effective Data Migration Best Practices To Optimize Cloud Migration Process. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide showcases various tips which can be used for cloud migration success such as prioritize application, dependency mapping and create security measures.

Effective Data Migration Quality Assurance Testing Checklist For Effective Cloud
Tis slide showcases application quality assurance testing checklist which includes functional, integration, performance and security testing strategies. Boost your pitch with our creative Effective Data Migration Quality Assurance Testing Checklist For Effective Cloud. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. Tis slide showcases application quality assurance testing checklist which includes functional, integration, performance and security testing strategies.
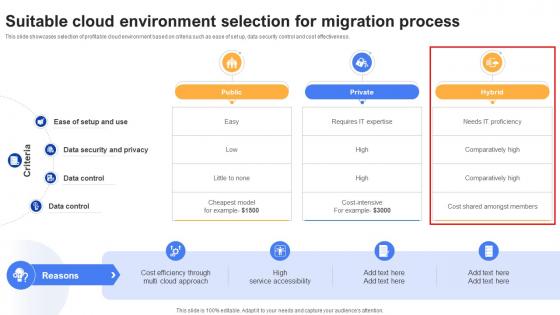
Effective Data Migration Suitable Cloud Environment Selection For Migration
This slide showcases selection of profitable cloud environment based on criteria such as ease of set up, data security control and cost effectiveness. There are so many reasons you need a Effective Data Migration Suitable Cloud Environment Selection For Migration. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide showcases selection of profitable cloud environment based on criteria such as ease of set up, data security control and cost effectiveness.
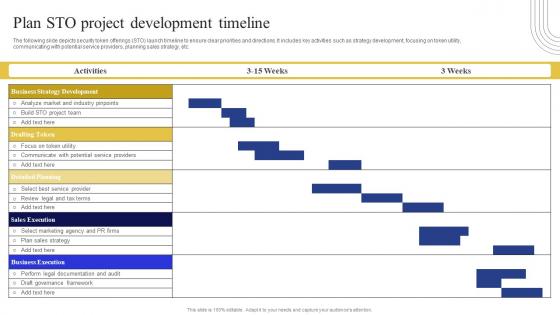
Plan Sto Project Development Timeline Exploring Investment Opportunities Themes Pdf
The following slide depicts security token offerings STO launch timeline to ensure clear priorities and directions. It includes key activities such as strategy development, focusing on token utility, communicating with potential service providers, planning sales strategy, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Plan Sto Project Development Timeline Exploring Investment Opportunities Themes Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. The following slide depicts security token offerings STO launch timeline to ensure clear priorities and directions. It includes key activities such as strategy development, focusing on token utility, communicating with potential service providers, planning sales strategy, etc.

Roadmap For Cloud Data Client Side Encryption PPT Presentation
This slide represents the roadmap to implement cryptographic cloud security in an organization. The main components included are determine sensitive data and required encryption technique, choose a cloud service provider, implement solution in cloud, etc. The Roadmap For Cloud Data Client Side Encryption PPT Presentation is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide represents the roadmap to implement cryptographic cloud security in an organization. The main components included are determine sensitive data and required encryption technique, choose a cloud service provider, implement solution in cloud, etc.
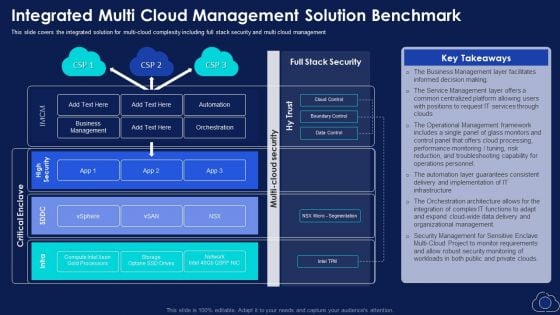
Integrated Multi Cloud Management Solution Benchmark Microsoft PDF
This slide covers the integrated solution for multi cloud complexity including full stack security and multi cloud management. Deliver and pitch your topic in the best possible manner with this Integrated Multi Cloud Management Solution Benchmark Microsoft PDF. Use them to share invaluable insights on Service Management, Business Management, Performance Monitoring and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Companys Data Safety Recognition Communication Plan General Format Themes PDF
This slide covers the schedule communication plan for security awareness program including brief description, frequency and audience. Deliver an awe-inspiring pitch with this creative companys data safety recognition communication plan general format themes pdf bundle. Topics like communication, description, frequency, audience can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
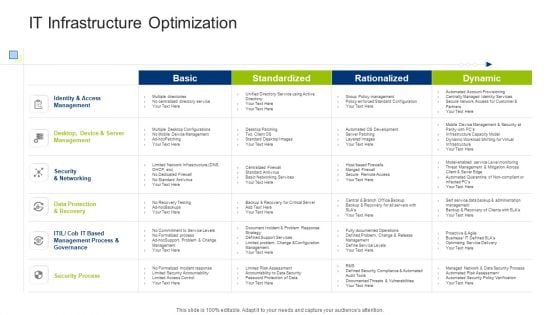
Infrastructure Building Administration IT Infrastructure Optimization Formats PDF
Deliver and pitch your topic in the best possible manner with this infrastructure building administration it infrastructure optimization formats pdf. Use them to share invaluable insights on identity and access management, security and networking, data protection and recovery and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Event Management Proposal Template Ppt PowerPoint Presentation Gallery Guidelines PDF
Presenting this set of slides with name event management proposal template ppt powerpoint presentation gallery guidelines pdf. The topics discussed in these slides are catering, grounds, security and transportation. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Table Of Contents For Upgrading Total Project Safety IT Graphics PDF
Deliver an awe inspiring pitch with this creative table of contents for upgrading total project safety it graphics pdf bundle. Topics like security centre implementation, project safety management, dashboard analysis, budget assessment, project management team can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

API Management For Building Software Applications Present Application Programming Interface Issues Guidelines PDF
Presenting this set of slides with name api management for building software applications present application programming interface issues guidelines pdf. This is a four stage process. The stages in this process are technological complexity, security risks, high consumption time, expensive. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Housing Mortgage Additional Benefits For Home Loan Proposal Ppt Slides Background PDF
Deliver an awe inspiring pitch with this creative housing mortgage additional benefits for home loan proposal ppt slides background pdf bundle. Topics like credit cards, easy security investment can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
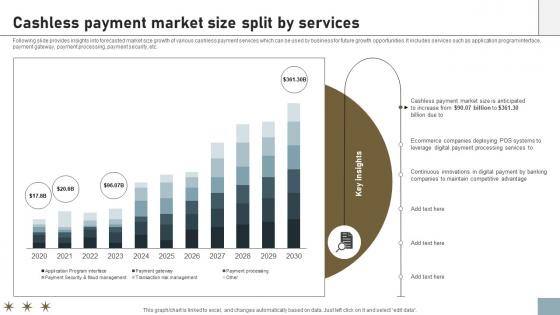
Online Payment Techniques For Providing Cashless Payment Market Size Split
Following slide provides insights into forecasted market size growth of various cashless payment services which can be used by business for future growth opportunities. It includes services such as application program interface, payment gateway, payment processing, payment security, etc. Take your projects to the next level with our ultimate collection of Online Payment Techniques For Providing Cashless Payment Market Size Split. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest Following slide provides insights into forecasted market size growth of various cashless payment services which can be used by business for future growth opportunities. It includes services such as application program interface, payment gateway, payment processing, payment security, etc.

Client Testimonials Email And Data Protection Platform Capital Funding Pitch Deck PPT Slide
This slide covers customer reviews about the email security company. It includes positive feedback related to user-friendly secure email software, helpful and professional team, seamless integration with Gmail. Create an editable Client Testimonials Email And Data Protection Platform Capital Funding Pitch Deck PPT Slide that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Client Testimonials Email And Data Protection Platform Capital Funding Pitch Deck PPT Slide is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide covers customer reviews about the email security company. It includes positive feedback related to user-friendly secure email software, helpful and professional team, seamless integration with Gmail.

Problem Statement Email And Data Protection Platform Capital Funding Pitch Deck PPT Slide
This slide covers major email security issues faced by customers. It includes issues such as inadequate secure file-sharing options and spam and viruses overwhelming email systems. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Problem Statement Email And Data Protection Platform Capital Funding Pitch Deck PPT Slide was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Problem Statement Email And Data Protection Platform Capital Funding Pitch Deck PPT Slide This slide covers major email security issues faced by customers. It includes issues such as inadequate secure file-sharing options and spam and viruses overwhelming email systems.

Zero Trust Model Case Study Intellectual Property Protection
This slide represents the case study for implementing the ZTNA security model into a food and beverage organization to secure intellectual property, supply chain and manufacturing. The purpose of this slide is to highlight the key requirements, solutions and impact of ZTNA implementation on the business. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Zero Trust Model Case Study Intellectual Property Protection will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide represents the case study for implementing the ZTNA security model into a food and beverage organization to secure intellectual property, supply chain and manufacturing. The purpose of this slide is to highlight the key requirements, solutions and impact of ZTNA implementation on the business.
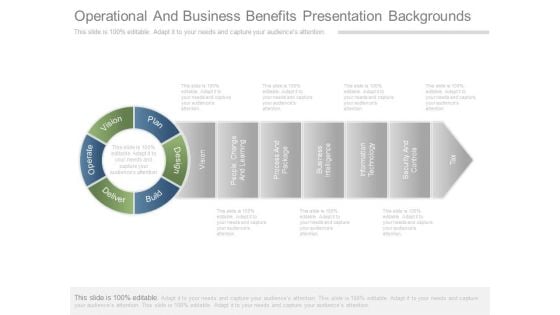
Operational And Business Benefits Presentation Backgrounds
This is a operational and business benefits presentation backgrounds. This is a seven stage process. The stages in this process are vision, plan, design, build, deliver, operate, people change and learning, process and package, business intelligence, information technology, security and controls, tax.

Zero Trust Network Access Comparison Between Zero Trust Model SDP And VPN
This slide represents the comparison between the zero trust security model, software-defined perimeter, and virtual private network. The purpose of this slide is to showcase the difference as well as the relationship between three security technologies such as zero trust, SDP and VPN. Welcome to our selection of the Zero Trust Network Access Comparison Between Zero Trust Model SDP And VPN. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. This slide represents the comparison between the zero trust security model, software-defined perimeter, and virtual private network. The purpose of this slide is to showcase the difference as well as the relationship between three security technologies such as zero trust, SDP and VPN.
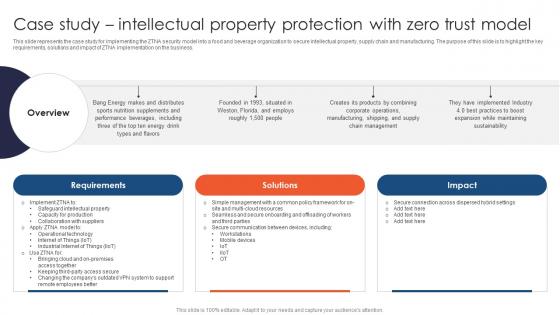
Zero Trust Network Access Case Study Intellectual Property Protection With Zero Trust Model
This slide represents the case study for implementing the ZTNA security model into a food and beverage organization to secure intellectual property, supply chain and manufacturing. The purpose of this slide is to highlight the key requirements, solutions and impact of ZTNA implementation on the business. Make sure to capture your audiences attention in your business displays with our gratis customizable Zero Trust Network Access Case Study Intellectual Property Protection With Zero Trust Model. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide represents the case study for implementing the ZTNA security model into a food and beverage organization to secure intellectual property, supply chain and manufacturing. The purpose of this slide is to highlight the key requirements, solutions and impact of ZTNA implementation on the business.
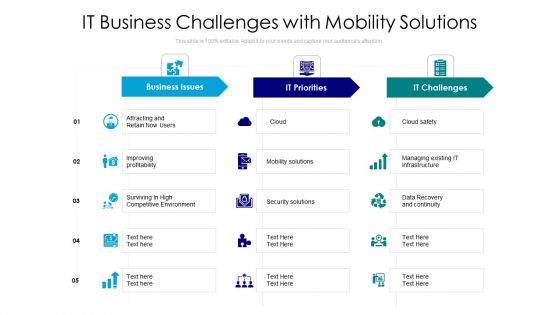
IT Business Challenges With Mobility Solutions Ppt PowerPoint Presentation File Example Topics PDF
Presenting it business challenges with mobility solutions ppt powerpoint presentation file example topics pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including mobility solutions, cloud safety, security solutions. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
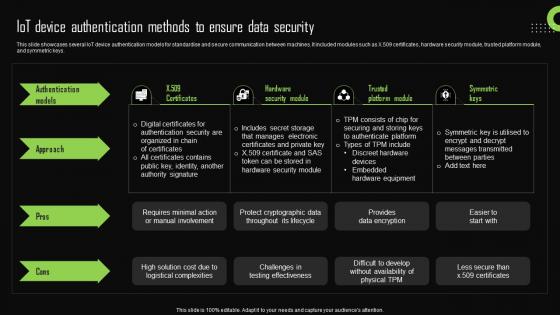
Iot Device Authentication Methods To Ensure Data Iot Device Management Download Pdf
This slide showcases several IoT device authentication models for standardise and secure communication between machines. It included modules such as X.509 certificates, hardware security module, trusted platform module, and symmetric keys. Slidegeeks has constructed after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide showcases several IoT device authentication models for standardise and secure communication between machines. It included modules such as X.509 certificates, hardware security module, trusted platform module, and symmetric keys.
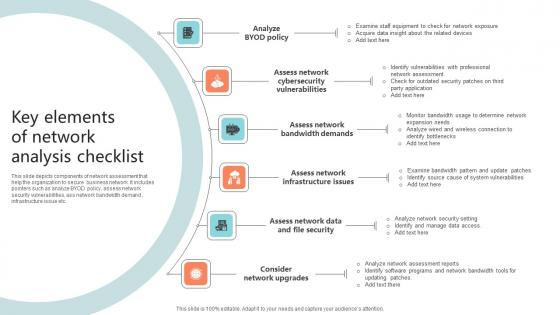
Key Elements Of Network Analysis Checklist Microsoft Pdf
This slide depicts components of network assessment that help the organization to secure business network. It includes pointers such as analyze BYOD policy, assess network security vulnerabilities, ass network bandwidth demand , infrastructure issue etc.Pitch your topic with ease and precision using this Key Elements Of Network Analysis Checklist Microsoft Pdf This layout presents information on Cybersecurity Vulnerabilities, Bandwidth Demands, Assess Network It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide depicts components of network assessment that help the organization to secure business network. It includes pointers such as analyze BYOD policy, assess network security vulnerabilities, ass network bandwidth demand , infrastructure issue etc.
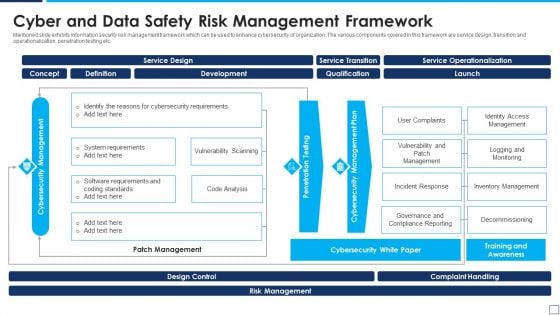
Cyber And Data Safety Risk Management Framework Designs PDF
Mentioned slide exhibits information security risk management framework which can be used to enhance cybersecurity of organization. The various components covered in this framework are service design, transition and operationalization, penetration testing etc. Showcasing this set of slides titled cyber and data safety risk management framework designs pdf. The topics addressed in these templates are service design, development, service operationalization. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
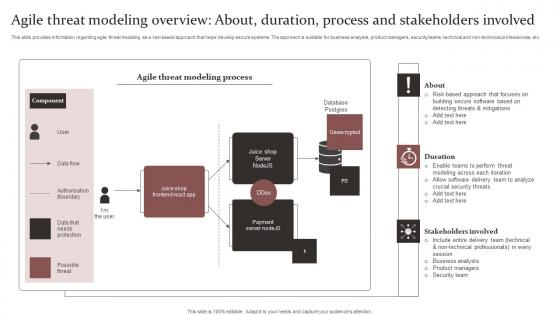
Agile Threat Modeling Overview About Duration Process Guide For Ethical Technology Icons Pdf
This slide provides information regarding agile threat modeling as a risk-based approach that helps develop secure systems. The approach is suitable for business analysts, product managers, security teams, technical and non-technical professionals, etc. Create an editable Agile Threat Modeling Overview About Duration Process Guide For Ethical Technology Icons Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Agile Threat Modeling Overview About Duration Process Guide For Ethical Technology Icons Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide provides information regarding agile threat modeling as a risk-based approach that helps develop secure systems. The approach is suitable for business analysts, product managers, security teams, technical and non-technical professionals, etc.
Agile Threat Modeling Overview Responsible Technology Governance Manual Slides Pdf
This slide provides information regarding agile threat modeling as a risk based approach that helps develop secure systems. The approach is suitable for business analysts, product managers, security teams, technical and non technical professionals, etc. Create an editable Agile Threat Modeling Overview Responsible Technology Governance Manual Slides Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Agile Threat Modeling Overview Responsible Technology Governance Manual Slides Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide provides information regarding agile threat modeling as a risk based approach that helps develop secure systems. The approach is suitable for business analysts, product managers, security teams, technical and non technical professionals, etc.
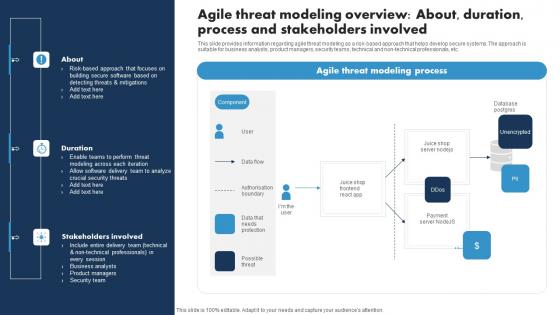
Agile Threat Modeling Overview About Duration Responsible Tech Guide To Manage Inspiration Pdf
This slide provides information regarding agile threat modeling as a risk-based approach that helps develop secure systems. The approach is suitable for business analysts, product managers, security teams, technical and non-technical professionals, etc. Create an editable Agile Threat Modeling Overview About Duration Responsible Tech Guide To Manage Inspiration Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Agile Threat Modeling Overview About Duration Responsible Tech Guide To Manage Inspiration Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide provides information regarding agile threat modeling as a risk-based approach that helps develop secure systems. The approach is suitable for business analysts, product managers, security teams, technical and non-technical professionals, etc.
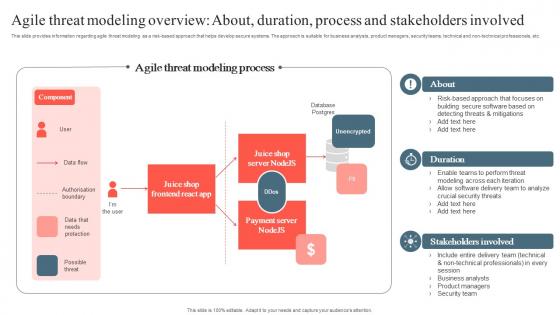
Playbook To Remediate False Agile Threat Modeling Overview About Download Pdf
This slide provides information regarding agile threat modeling as a risk based approach that helps develop secure systems. The approach is suitable for business analysts, product managers, security teams, technical and non technical professionals, etc. Want to ace your presentation in front of a live audience Our Playbook To Remediate False Agile Threat Modeling Overview About Download Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use. This slide provides information regarding agile threat modeling as a risk based approach that helps develop secure systems. The approach is suitable for business analysts, product managers, security teams, technical and non technical professionals, etc.
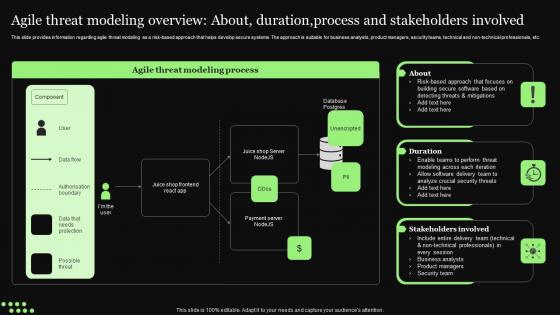
Ethical Technology Utilization Agile Threat Modeling Overview Duration process Formats Pdf
This slide provides information regarding agile threat modeling as a risk based approach that helps develop secure systems. The approach is suitable for business analysts, product managers, security teams, technical and non technical professionals, etc. Create an editable Ethical Technology Utilization Agile Threat Modeling Overview Duration process Formats Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Ethical Technology Utilization Agile Threat Modeling Overview Duration process Formats Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide provides information regarding agile threat modeling as a risk based approach that helps develop secure systems. The approach is suitable for business analysts, product managers, security teams, technical and non technical professionals, etc.

Agile Threat Modeling Overview About Duration Process Crafting A Sustainable Company Designs Pdf
This slide provides information regarding agile threat modeling as a risk-based approach that helps develop secure systems. The approach is suitable for business analysts, product managers, security teams, technical and non-technical professionals, etc. Create an editable Agile Threat Modeling Overview About Duration Process Crafting A Sustainable Company Designs Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Agile Threat Modeling Overview About Duration Process Crafting A Sustainable Company Designs Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide provides information regarding agile threat modeling as a risk-based approach that helps develop secure systems. The approach is suitable for business analysts, product managers, security teams, technical and non-technical professionals, etc.

Client Testimonials Paubox Capital Funding Pitch Deck Professional Pdf
This slide covers customer reviews about the email security company. It includes positive feedback related to user friendly secure email software, helpful and professional team, seamless integration with Gmail. Get a simple yet stunning designed Client Testimonials Paubox Capital Funding Pitch Deck Professional Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Client Testimonials Paubox Capital Funding Pitch Deck Professional Pdf can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide covers customer reviews about the email security company. It includes positive feedback related to user friendly secure email software, helpful and professional team, seamless integration with Gmail.

Zero Trust Model Comparison Between Zero Trust Model SDP And VPN
This slide represents the comparison between the zero trust security model, software-defined perimeter, and virtual private network. The purpose of this slide is to showcase the difference as well as the relationship between three security technologies such as zero trust, SDP and VPN. Find highly impressive Zero Trust Model Comparison Between Zero Trust Model SDP And VPN on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Zero Trust Model Comparison Between Zero Trust Model SDP And VPN for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide represents the comparison between the zero trust security model, software-defined perimeter, and virtual private network. The purpose of this slide is to showcase the difference as well as the relationship between three security technologies such as zero trust, SDP and VPN.
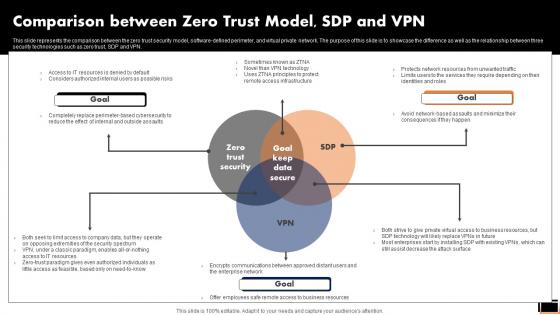
Comparison Between Zero Trust ModelSDP And Vpn Software Defined Perimeter SDP
This slide represents the comparison between the zero trust security model, software-defined perimeter, and virtual private network. The purpose of this slide is to showcase the difference as well as the relationship between three security technologies such as zero trust, SDP and VPN. Present like a pro with Comparative Assessment Of Ztna Version 1 0 And 2 0 Software Defined Perimeter SDP. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide represents the comparison between the zero trust security model, software-defined perimeter, and virtual private network. The purpose of this slide is to showcase the difference as well as the relationship between three security technologies such as zero trust, SDP and VPN.

Problem Statement Paubox Capital Funding Pitch Deck Graphics Pdf
This slide covers major email security issues faced by customers. It includes issues such as inadequate secure file sharing options and spam and viruses overwhelming email systems. Explore a selection of the finest Problem Statement Paubox Capital Funding Pitch Deck Graphics Pdf here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Problem Statement Paubox Capital Funding Pitch Deck Graphics Pdf to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide covers major email security issues faced by customers. It includes issues such as inadequate secure file sharing options and spam and viruses overwhelming email systems.

Zero Trust Model Zero Trust Network Access User Flow Overview
This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office. Retrieve professionally designed Zero Trust Model Zero Trust Network Access User Flow Overview to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office.
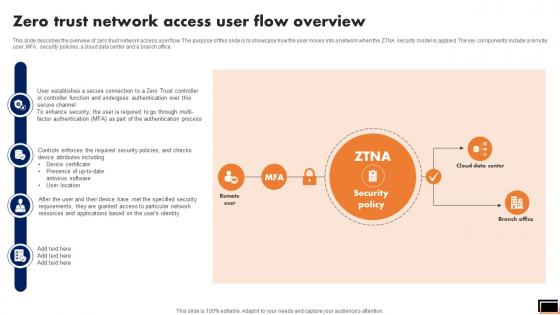
Zero Trust Network Access User Flow Overview Software Defined Perimeter SDP
This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office. Retrieve professionally designed Zero Trust Network Access User Flow Overview Software Defined Perimeter SDP to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office.

Login For Income Statement Powerpoint Template
Our above slide display graphics of log in page on mobile phone with money flowing out of tap. Download this diagram slide to display security measures for money saving account. Adjust the above diagram in your business presentations to visually support your content.

Zero Trust Network Access Roadmap To Implement Zero Trust Network Access Model

Software Defined Perimeter SDP Roadmap To Implement Zero Trust Network Access Model
This slide outlines the roadmap to implementing the zero-trust network access model. The purpose of this slide is to showcase the various steps to be taken while deploying the ZTNA security model, including identifying assets and defining the protection surface, understanding the business existing security model, etc. Boost your pitch with our creative Software Defined Perimeter SDP Roadmap To Implement Zero Trust Network Access Model. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide outlines the roadmap to implementing the zero-trust network access model. The purpose of this slide is to showcase the various steps to be taken while deploying the ZTNA security model, including identifying assets and defining the protection surface, understanding the business existing security model, etc.
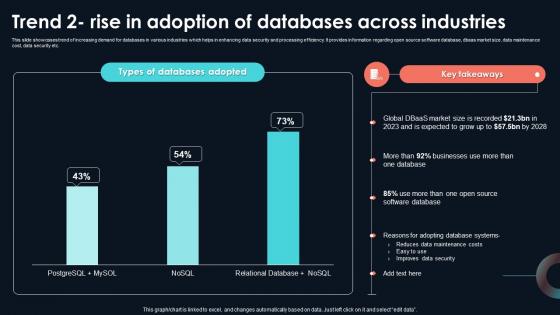
Trend 2 Rise In Adoption Of Databases Across Developing Strategic Insights Using Big Data Analytics SS V
This slide showcases trend of increasing demand for databases in various industries which helps in enhancing data security and processing efficiency. It provides information regarding open source software database, dbaas market size, data maintenance cost, data security etc. This Trend 2 Rise In Adoption Of Databases Across Developing Strategic Insights Using Big Data Analytics SS V from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide showcases trend of increasing demand for databases in various industries which helps in enhancing data security and processing efficiency. It provides information regarding open source software database, dbaas market size, data maintenance cost, data security etc.

Data Breach Prevention Strategies For Enterprises Data Breach Prevention Slides Pdf
The purpose of this slide is to outline the data breach mitigation strategies for businesses. These include access control, encryption, web security solutions, network security, up-to-date software and hardware, preparation, training employees and users, etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Data Breach Prevention Strategies For Enterprises Data Breach Prevention Slides Pdf was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Data Breach Prevention Strategies For Enterprises Data Breach Prevention Slides Pdf The purpose of this slide is to outline the data breach mitigation strategies for businesses. These include access control, encryption, web security solutions, network security, up-to-date software and hardware, preparation, training employees and users, etc.

Zero Trust Network Access User Flow Overview Download Pdf
This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office. Slidegeeks is here to make your presentations a breeze with Zero Trust Network Access User Flow Overview Download Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office.

Zero Trust Network Access User Flow Overview Ppt File Deck
This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office. The Zero Trust Network Access User Flow Overview Ppt File Deck is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office.
Banners With Globe Bulb Clock And Lock Icons Powerpoint Templates
This PowerPoint template has been designed with graphics of banners with business icons. You may use this slide to display global technology and security concepts. This diagram provides an effective way of displaying information you can edit text, color, shade and style as per you need.

Problem Statement ICT Solutions Provider Investor Funding Elevator Pitch Deck
This slide caters to details about several problems in the market faced by prospects. These pain points are 5G technology issues, security issues, smart devices are expensive and cloud computing security breaches. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Problem Statement ICT Solutions Provider Investor Funding Elevator Pitch Deck was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Problem Statement ICT Solutions Provider Investor Funding Elevator Pitch Deck This slide caters to details about several problems in the market faced by prospects. These pain points are 5G technology issues, security issues, smart devices are expensive and cloud computing security breaches.

Benefits Of Devsecops Model In Organization Role Of Devsecops Ppt Example
This slide explains the importance of the DevSecOps model in an organization. The purpose of this slide is to highlight the Benefits these are faster delivery, improved security posture, reduced cost, enhanced value of DevSecOps, improved security integration and peace, etc. Create an editable Benefits Of Devsecops Model In Organization Role Of Devsecops Ppt Example that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Benefits Of Devsecops Model In Organization Role Of Devsecops Ppt Example is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide explains the importance of the DevSecOps model in an organization. The purpose of this slide is to highlight the Benefits these are faster delivery, improved security posture, reduced cost, enhanced value of DevSecOps, improved security integration and peace, etc.
Networking Device Icon Circle Arrow Ppt PowerPoint Presentation Complete Deck
Presenting this set of slides with name networking device icon circle arrow ppt powerpoint presentation complete deck. The topics discussed in these slides are technology, router device, circle, arrow, security shield. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
IT Management Elements Shown Through Three Gears Ppt PowerPoint Presentation Icon Files PDF
Presenting it management elements shown through three gears ppt powerpoint presentation icon files pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including incident management, security management, network management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
IT Management Elements Shown Through Four Gears Ppt PowerPoint Presentation Gallery Clipart Images PDF
Presenting it management elements shown through four gears ppt powerpoint presentation gallery clipart images pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including incident management, security management, network management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.


 Continue with Email
Continue with Email

 Home
Home


































