Security Services
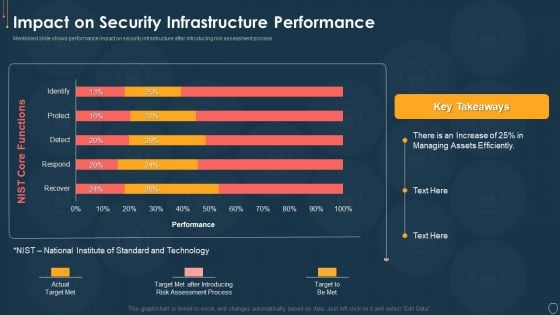
Cyber Security Risk Management Plan Impact On Security Infrastructure Performance Microsoft PDF
Mentioned slide shows performance impact on security infrastructure after introducing risk assessment process. Deliver and pitch your topic in the best possible manner with this cyber security risk management plan impact on security infrastructure performance microsoft pdf. Use them to share invaluable insights on efficiently, process, target, technology and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Security Risk Management Plan Information Security Risk Management Dashboard Sample PDF
Following slide covers information security risk management dashboard. It include KPIs such as risk analysis progress, percent risk, response progress for risks and number of risks encountered. Deliver an awe inspiring pitch with this creative cyber security risk management plan information security risk management dashboard sample pdf bundle. Topics like vulnerabilities, entities, action plan, risk analysis can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Developing Firm Security Strategy Plan Addressing Performance Indicators To Determine Security Standards Structure PDF
This slide provides information about performance indicators in order to determine security standards at workplace in terms of incidents, offender management, risk assessments. Deliver an awe inspiring pitch with this creative developing firm security strategy plan addressing performance indicators to determine security standards structure pdf bundle. Topics like incidents, offender management, risk assessments can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
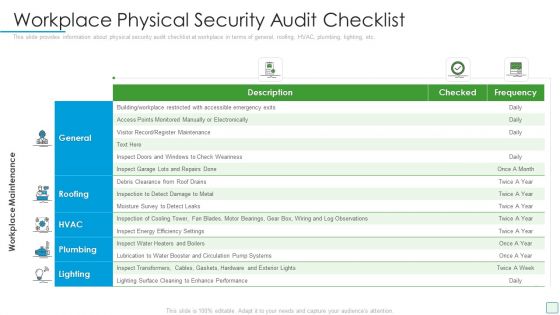
Developing Firm Security Strategy Plan Workplace Physical Security Audit Checklist Download PDF
This slide provides information about physical security audit checklist at workplace in terms of general, roofing, HVAC, plumbing, lighting, etc. Deliver an awe inspiring pitch with this creative developing firm security strategy plan workplace physical security audit checklist download pdf bundle. Topics like general, roofing, hvac, plumbing, lighting can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Information Security Compliance Dashboard Of Data Security Ppt Icon Vector PDF
This slide depicts the data security compliance report on how data and hardware are monitored in different categories such as standard, regulation, and asset type control. Deliver an awe inspiring pitch with this creative information security compliance dashboard of data security ppt icon vector pdf bundle. Topics like asset type control, control issues by standard, control issues by regulation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
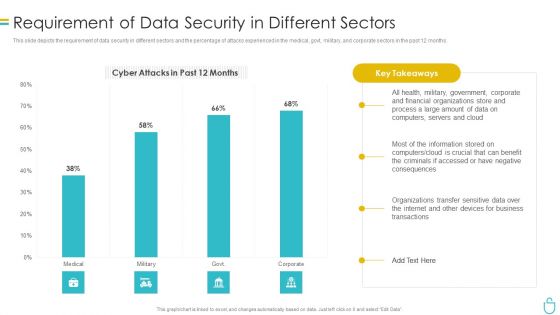
Information Security Requirement Of Data Security In Different Sectors Ppt File Infographic Template PDF
This slide depicts the requirement of data security in different sectors and the percentage of attacks experienced in the medical, govt, military, and corporate sectors in the past 12 months. Deliver an awe inspiring pitch with this creative information security requirement of data security in different sectors ppt file infographic template pdf bundle. Topics like process, financial, organizations, data, servers can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Information Security Data Security Awareness Training For Staff Ppt Visual Aids Pictures PDF
This slide represents the data security awareness training program for staff, including the name of the participants and what modules would be covered under training daily. Deliver and pitch your topic in the best possible manner with this information security data security awareness training for staff ppt visual aids pictures pdf. Use them to share invaluable insights on project managers, developers, senior executives, planning and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
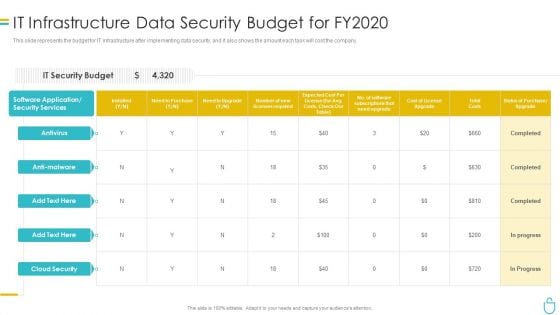
Information Security It Infrastructure Data Security Budget For FY2020 Ppt Inspiration File Formats PDF
This slide represents the budget for IT infrastructure after implementing data security, and it also shows the amount each task will cost the company. Deliver and pitch your topic in the best possible manner with this information security it infrastructure data security budget for fy2020 ppt inspiration file formats pdf. Use them to share invaluable insights on costs, need to purchase, required, application and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
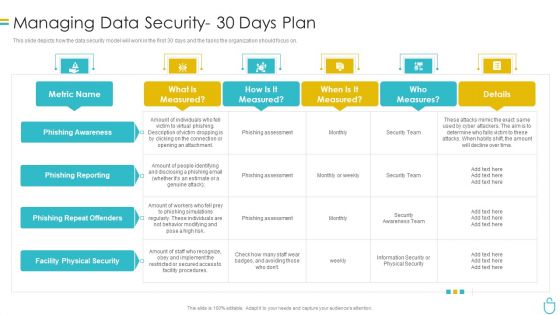
Information Security Managing Data Security 30 Days Plan Ppt Summary Slides PDF
This slide depicts how the data security model will work in the first 30 days and the tasks the organization should focus on. Deliver an awe inspiring pitch with this creative information security managing data security 30 days plan ppt summary slides pdf bundle. Topics like risk, procedures, implement, metric can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Table Of Contents Cyber Security Administration In Organization Security Sample PDF
This is a table of contents cyber security administration in organization security sample pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like ensuring, financial, assets, security, workforce. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Security Administration In Organization Addressing Asset Security Categorization Professional PDF
This slide provides details regarding asset security categorization on certain parameters such as ownership, location, confidentiality, integrity and availability. Deliver an awe inspiring pitch with this creative cyber security administration in organization addressing asset security categorization professional pdf bundle. Topics like executive, ownership, categorization, integrity can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
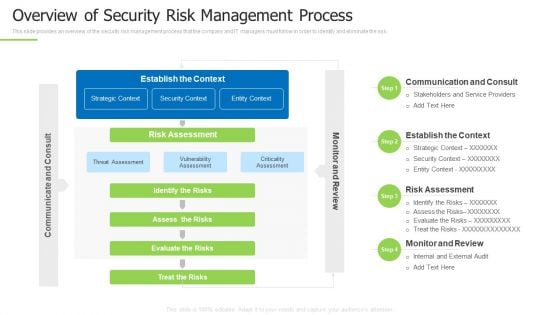
Techniques And Strategies To Reduce Security Management Risks Overview Of Security Risk Background PDF
This slide provides an overview of the security risk management process that the company and IT managers must follow in order to identify and eliminate the risk. Deliver an awe inspiring pitch with this creative techniques and strategies to reduce security management risks overview of security risk background pdf bundle. Topics like identify the risks, strategic context, vulnerability assessment can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Desktop Security Management Computer Security Awareness Training For Staff Template PDF
This slide represents the cybersecurity awareness training program for staff, including the name of the participants and what modules would be covered under training daily. Deliver an awe inspiring pitch with this creative desktop security management computer security awareness training for staff template pdf bundle. Topics like project managers, developers, senior executives, security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Corporate Security And Risk Management Table Of Contents Corporate Security Summary PDF
This is a corporate security and risk management table of contents corporate security summary pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like ensuring financial assets security, leveraging workforce, budget assessment, dashboard, impact assessment . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
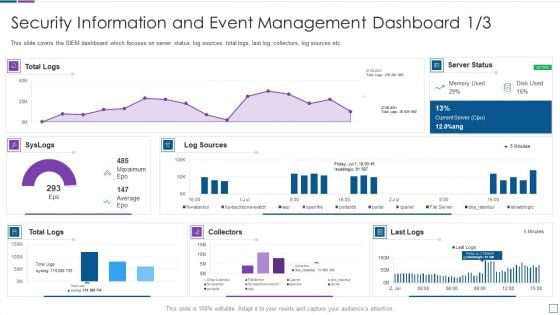
Real Time Assessment Of Security Threats Security Information And Event Management Microsoft PDF
This slide covers the SIEM dashboard which focuses on server status, log sources, total logs, last log, collectors, log sources etc. Deliver and pitch your topic in the best possible manner with this real time assessment of security threats security information and event management microsoft pdf. Use them to share invaluable insights on security information and event management dashboard and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
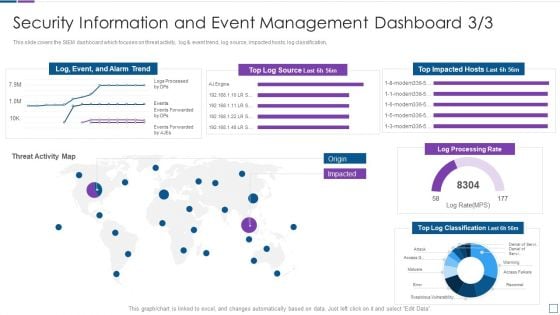
Security Information And Event Management Real Time Assessment Of Security Threats Template PDF
This slide covers the SIEM dashboard which focuses on threat activity, log and event trend, log source, impacted hosts, log classification. Deliver an awe inspiring pitch with this creative security information and event management real time assessment of security threats template pdf bundle. Topics like security information and event management dashboard can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Real Time Assessment Of Security Threats Agenda Of Real Time Assessment Of Security Threats Designs PDF
This is a real time assessment of security threats agenda of real time assessment of security threats designs pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like agenda of real time assessment of security threats. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
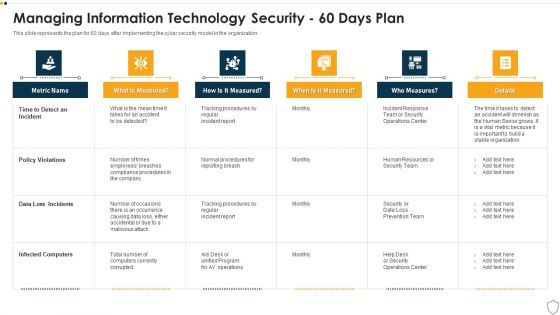
IT Security Managing Information Technology Security 60 Days Plan Professional PDF
This slide represents the plan for 60 days after implementing the cyber security model in the organization. Deliver an awe inspiring pitch with this creative it security managing information technology security 60 days plan professional pdf bundle. Topics like time to detect an incident, policy violations, data loss incidents, infected computers can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
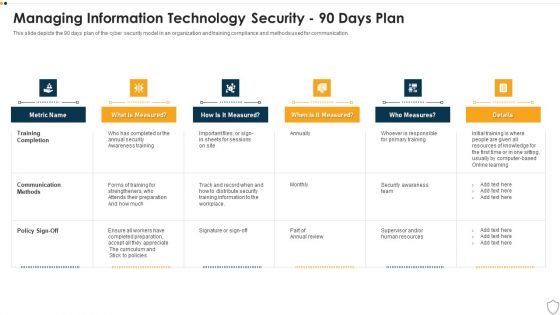
IT Security Managing Information Technology Security 90 Days Plan Sample PDF
This slide depicts the 90 days plan of the cyber security model in an organization and training compliance and methods used for communication. Deliver and pitch your topic in the best possible manner with this it security managing information technology security 90 days plan sample pdf. Use them to share invaluable insights on training completion, communication methods, policy sign off and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
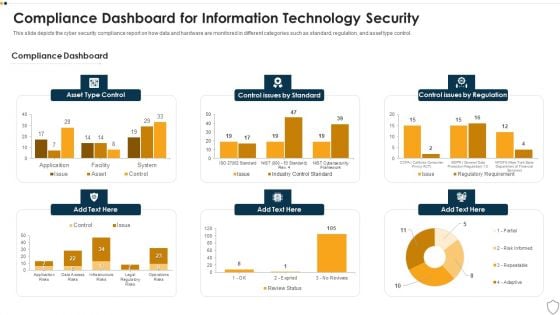
IT Security Compliance Dashboard For Information Technology Security Ppt Slides Brochure PDF
This slide depicts the cyber security compliance report on how data and hardware are monitored in different categories such as standard, regulation, and asset type control. Deliver an awe inspiring pitch with this creative it security compliance dashboard for information technology security ppt slides brochure pdf bundle. Topics like asset type control, control issues by standard, control issues by regulation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

IT Security Requirement Of Information Technology Security In Different Sectors Ppt File Display PDF
This slide depicts the requirement of cyber security in different sectors and the percentage of attacks experienced in the medical, govt, military, and corporate sectors in the past 12 months. Deliver an awe inspiring pitch with this creative it security requirement of information technology security in different sectors ppt file display pdf bundle. Topics like business transactions, organizations, financial, process can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
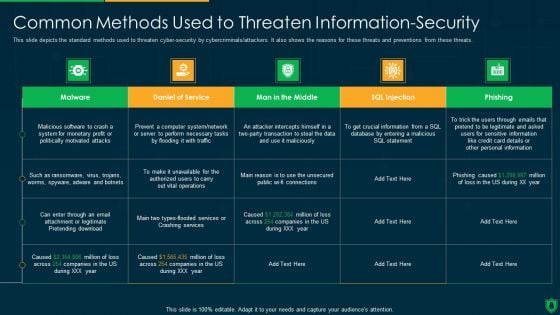
Info Security Common Methods Used To Threaten Information Security Ppt PowerPoint Presentation Gallery Clipart Images PDF
This slide depicts the standard methods used to threaten cyber-security by cybercriminals or attackers. It also shows the reasons for these threats and preventions from these threats. Deliver an awe inspiring pitch with this creative info security common methods used to threaten information security ppt powerpoint presentation gallery clipart images pdf bundle. Topics like personal information, phishing caused, sql statement can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
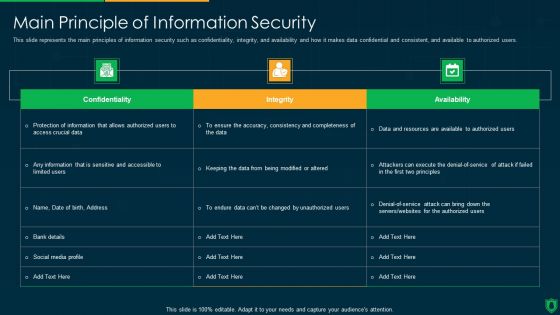
Info Security Main Principle Of Information Security Ppt PowerPoint Presentation File Background Designs PDF
This slide represents the main principles of information security such as confidentiality, integrity, and availability and how it makes data confidential and consistent, and available to authorized users. Deliver an awe inspiring pitch with this creative info security main principle of information security ppt powerpoint presentation file background designs pdf bundle. Topics like integrity, confidentiality, availability, data can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
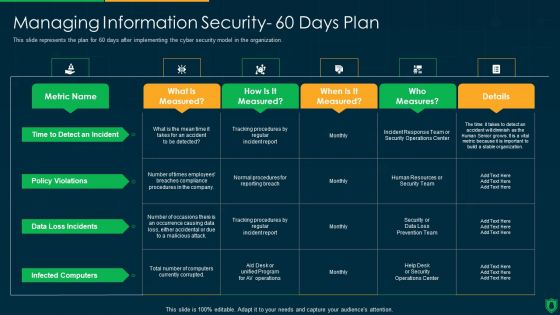
Info Security Managing Information Security 60 Days Plan Ppt PowerPoint Presentation File Graphics Example PDF
This slide represents the plan for 60 days after implementing the cyber security model in the organization. Deliver and pitch your topic in the best possible manner with this info security managing information security 60 days plan ppt powerpoint presentation file graphics example pdf. Use them to share invaluable insights on policy violations, data loss incidents, infected computers, time to detect an incident and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
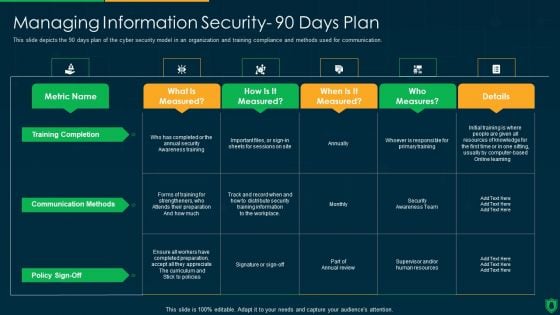
Info Security Managing Information Security 90 Days Plan Ppt PowerPoint Presentation Gallery Maker PDF
This slide depicts the 90 days plan of the cyber security model in an organization and training compliance and methods used for communication. Deliver an awe inspiring pitch with this creative info security managing information security 90 days plan ppt powerpoint presentation gallery maker pdf bundle. Topics like training completion, communication methods, policy sign off, measures can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Risk Management Model For Data Security Information Security Risk Assessment Worksheet Infographics PDF
This slide illustrates information security risk assessment worksheet. Risk covered are monetary loss, reputation loss and loss of customer confidence. Deliver and pitch your topic in the best possible manner with this Risk Management Model For Data Security Information Security Risk Assessment Worksheet Infographics PDF. Use them to share invaluable insights on Facilities And Equipment, Software Application, At Personnel Level, Monetary Loss, Risk and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
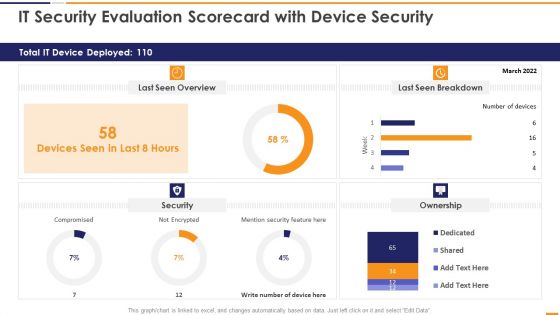
IT Security Evaluation Scorecard With Device Security Ppt Slides Good PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver an awe inspiring pitch with this creative IT Security Evaluation Scorecard With Device Security Ppt Slides Good PDF bundle. Topics like Total IT Device, Last Seen Overview, Last Seen Breakdown, Mention Security Feature can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
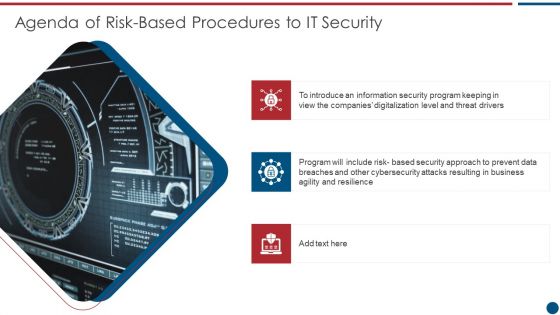
Risk Based Procedures To IT Security Agenda Of Risk Based Procedures To It Security Guidelines PDF
This is a Risk Based Procedures To IT Security Agenda Of Risk Based Procedures To It Security Guidelines PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Information Security, Program Keeping, Threat Drivers. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
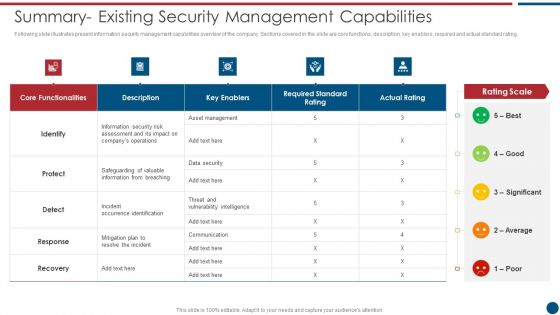
Risk Based Procedures To IT Security Summary Existing Security Management Capabilities Topics PDF
Following slide illustrates present information security management capabilities overview of the company. Sections covered in the slide are core functions, description, key enablers, required and actual standard rating. Deliver an awe inspiring pitch with this creative Risk Based Procedures To IT Security Summary Existing Security Management Capabilities Topics PDF bundle. Topics like Asset Management, Key Enablers, Communication Plan can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
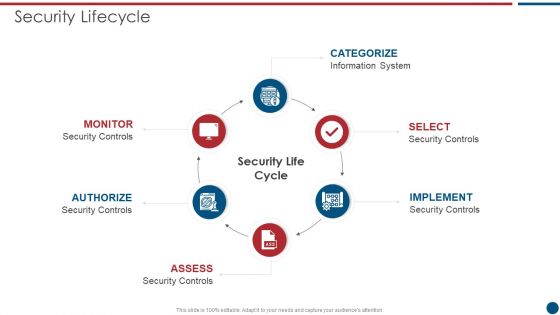
Risk Based Procedures To IT Security Security Lifecycle Ppt PowerPoint Presentation File Rules PDF
This is a Risk Based Procedures To IT Security Security Lifecycle Ppt PowerPoint Presentation File Rules PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Information System, Security Controls. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
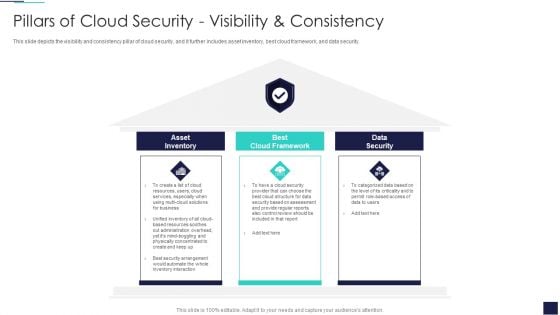
Cloud Information Security Pillars Of Cloud Security Visibility And Consistency Ppt Summary Layout PDF
This is a Cloud Information Security Pillars Of Cloud Security Visibility And Consistency Ppt Summary Layout PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Asset Inventory, Best Cloud, Data Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
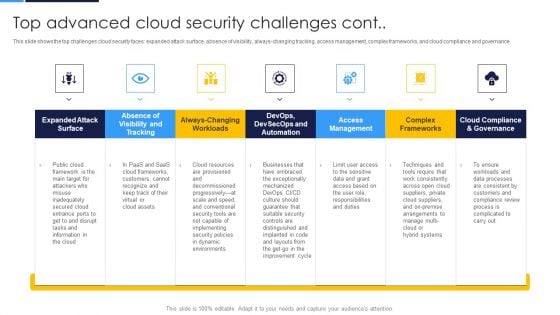
Cloud Security Assessment Top Advanced Cloud Security Challenges Cont Information PDF
This slide shows the top challenges cloud security faces expanded attack surface, absence of visibility, always-changing tracking, access management, complex frameworks, and cloud compliance and governance. Deliver and pitch your topic in the best possible manner with this Cloud Security Assessment Top Advanced Cloud Security Challenges Cont Information PDF. Use them to share invaluable insights on Dynamic Environments, Resources Are Provisioned, Access Management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
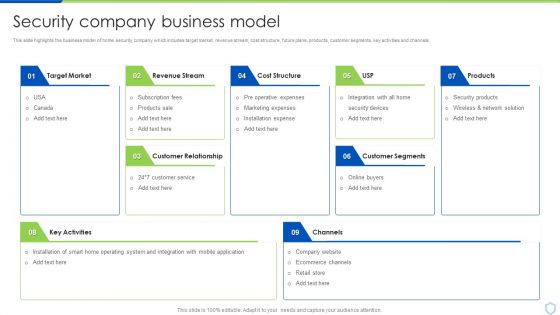
Security And Surveillance Company Profile Security Company Business Model Designs PDF
This slide highlights the business model of home security company which includes target market, revenue stream, cost structure, future plans, products, customer segments, key activities and channels. Deliver an awe inspiring pitch with this creative Security And Surveillance Company Profile Security Company Business Model Designs PDF bundle. Topics like Target Market, Revenue Stream, Cost Structure can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
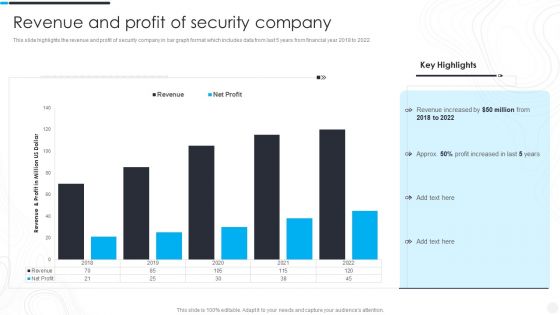
Security Camera System Company Profile Revenue And Profit Of Security Company Clipart PDF
This slide highlights the revenue and profit of security company in bar graph format which includes data from last 5 years from financial year 2018 to 2022.Deliver and pitch your topic in the best possible manner with this Security Camera System Company Profile Revenue And Profit Of Security Company Clipart PDF. Use them to share invaluable insights on Revenue Increased, Profit Increased, Key Highlights and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Security Camera System Company Profile Security Company Business Model Mockup PDF
This slide highlights the business model of home security company which includes target market, revenue stream, cost structure, future plans, products, customer segments, key activities and channels. Deliver an awe inspiring pitch with this creative Security Camera System Company Profile Security Company Business Model Mockup PDF bundle. Topics like Revenue Stream, Customer Relationship, Customer Segments can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
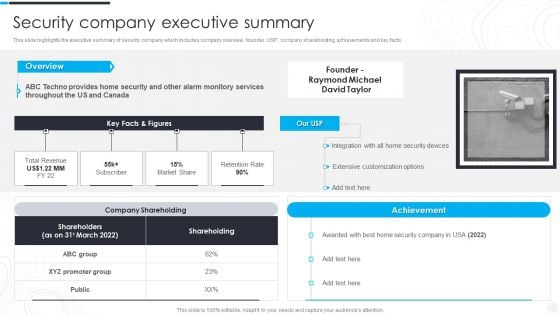
Security Camera System Company Profile Security Company Executive Summary Formats PDF
This slide highlights the executive summary of security company which includes company overview, founder, USP, company shareholding, achievements and key facts.Deliver an awe inspiring pitch with this creative Security Camera System Company Profile Security Company Executive Summary Formats PDF bundle. Topics like Company Shareholding, Customization Options, Raymond Michael can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Information Security Risk Evaluation Budget For Information Security Risk Management Diagrams PDF
This slide showcases budget that can should be allocated for different information security risk management activities. It provides information about employees training, software implementation, risk monitoring and data backup.Deliver an awe inspiring pitch with this creative Information Security Risk Evaluation Budget For Information Security Risk Management Diagrams PDF bundle. Topics like Training Of Employees, Software Implementation, Risk Monitoring can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Information Security Risk Evaluation Checklist For Information Security Risk Management Microsoft PDF
This slide showcases challenges involved in formulating risk management program for information security. It also shows solutions to tackle the challenges and impact of implementing them.Deliver an awe inspiring pitch with this creative Information Security Risk Evaluation Checklist For Information Security Risk Management Microsoft PDF bundle. Topics like Identifying Potential, Defining Mitigation, Created Sales can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
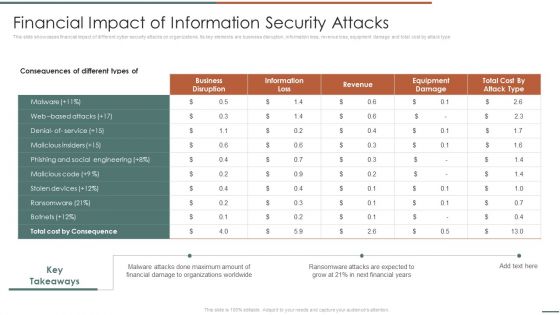
Information Security Risk Evaluation Financial Impact Of Information Security Attacks Background PDF
This slide showcases financial impact of different cyber security attacks on organizations. Its key elements are business disruption, information loss, revenue loss, equipment damage and total cost by attack type.Deliver an awe inspiring pitch with this creative Information Security Risk Evaluation Financial Impact Of Information Security Attacks Background PDF bundle. Topics like Business Disruption, Cost By Consequence, Malware Attacks can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Information Security Risk Evaluation Gap Assessment Of Organization Information Security Icons PDF
This slide showcases gap assessment of information security capabilities of organization. It also provides solutions to tackle the problems faced by company like, frequent malware attacks and lack of awareness among employees.Deliver an awe inspiring pitch with this creative Information Security Risk Evaluation Gap Assessment Of Organization Information Security Icons PDF bundle. Topics like Frequent Malware, Phishing Attacks, Ransomware Attacks can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
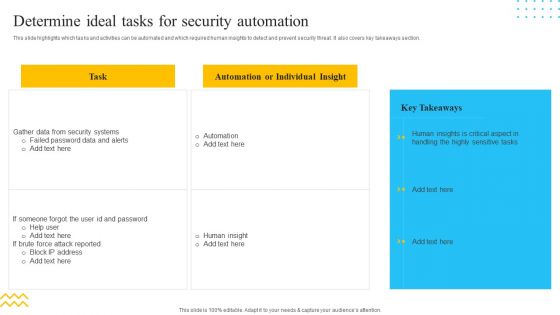
IT Security Automation Tools Integration Determine Ideal Tasks For Security Automation Template PDF
This slide highlights which tasks and activities can be automated and which required human insights to detect and prevent security threat. It also covers key takeaways section. Deliver an awe inspiring pitch with this creative IT Security Automation Tools Integration Determine Ideal Tasks For Security Automation Template PDF bundle. Topics like Automation, Individual Insight, Gather Data can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
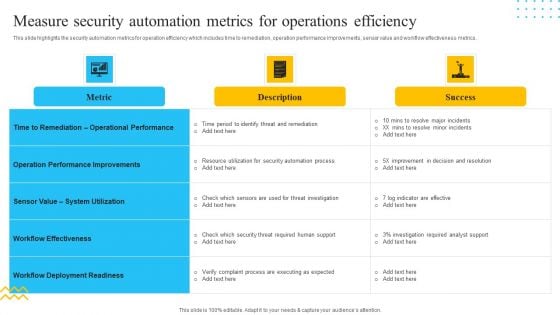
IT Security Automation Tools Integration Measure Security Automation Metrics For Operations Template PDF
This slide highlights the security automation metrics for operation efficiency which includes time to remediation, operation performance improvements, sensor value and workflow effectiveness metrics. Deliver and pitch your topic in the best possible manner with this IT Security Automation Tools Integration Measure Security Automation Metrics For Operations Template PDF. Use them to share invaluable insights on Metric, Operation Performance Improvements, Success and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
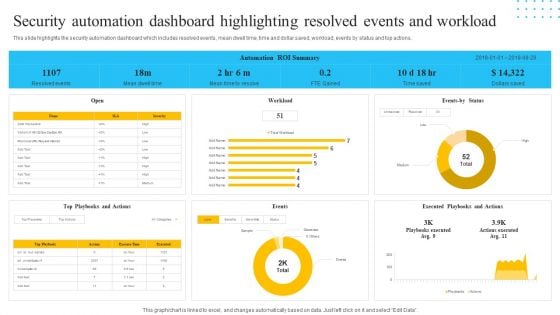
IT Security Automation Tools Integration Security Automation Dashboard Highlighting Resolved Inspiration PDF
This slide highlights the security automation dashboard which includes resolved events, mean dwell time, time and dollar saved, workload, events by status and top actions. Deliver an awe inspiring pitch with this creative IT Security Automation Tools Integration Security Automation Dashboard Highlighting Resolved Inspiration PDF bundle. Topics like Events Status, Workload, Events, Open can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
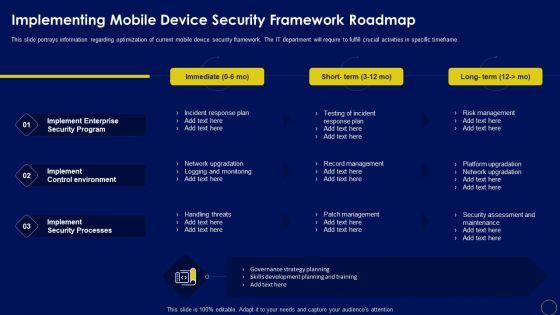
Implementing Mobile Device Security Framework Roadmap Business Mobile Device Security Sample PDF
This slide portrays information regarding optimization of current mobile device security framework. The IT department will require to fulfill crucial activities in specific timeframe. There are so many reasons you need a Implementing Mobile Device Security Framework Roadmap Business Mobile Device Security Sample PDF. The first reason is you can notspend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
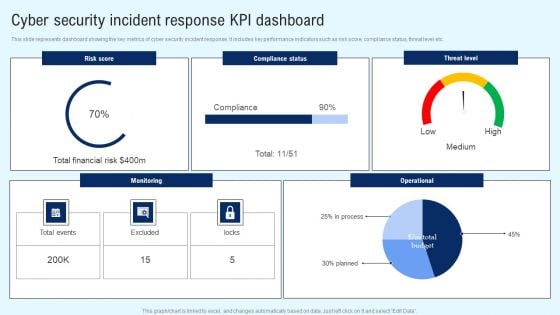
Implementing Cyber Security Incident Cyber Security Incident Response KPI Dashboard Clipart PDF
This slide represents dashboard showing the key metrics of cyber security incident response. It includes key performance indicators such as risk score, compliance status, threat level etc. There are so many reasons you need a Implementing Cyber Security Incident Cyber Security Incident Response KPI Dashboard Clipart PDF. The first reason is you cannot spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
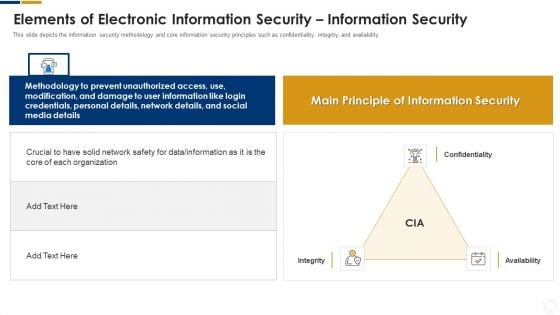
Cybersecurity Elements Of Electronic Information Security Information Security Ppt Pictures Slide PDF
This slide depicts the information security methodology and core information security principles such as confidentiality, integrity, and availability. This is a cybersecurity elements of electronic information security information security ppt pictures slide pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like organization, network, information, data. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Information Security Complete Data Security Implementation Checklist Ppt Icon Clipart PDF
This slide depicts the cyber security checklist and measures an organization should take to protect data and company assets from cyber attacks or natural disasters. This is a information security complete data security implementation checklist ppt icon clipart pdf template with various stages. Focus and dispense information on eleven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like strong passwords, antivirus software, frequent staff training, recovery planning, device security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
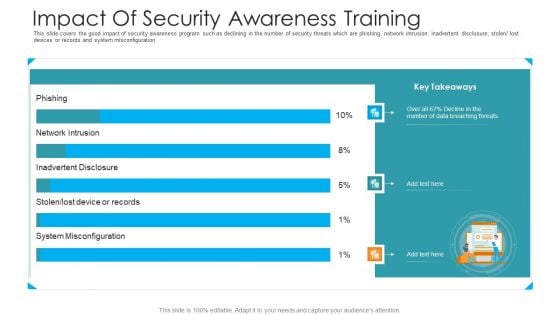
Impact Of Security Awareness Training Hacking Prevention Awareness Training For IT Security Infographics PDF
This slide covers the good impact of security awareness program such as declining in the number of security threats which are phishing, network intrusion, inadvertent disclosure, stolen or lost devices or records and system misconfiguration. Deliver an awe inspiring pitch with this creative impact of security awareness training hacking prevention awareness training for it security infographics pdf bundle. Topics like system misconfiguration, network intrusion breakdown, phishing breakdown can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
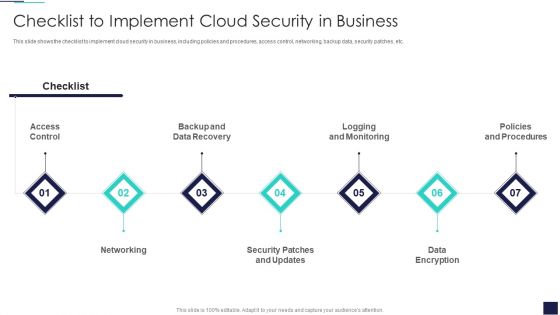
Cloud Information Security Checklist To Implement Cloud Security In Business Ppt Ideas Background Image PDF
This slide shows the checklist to implement cloud security in business, including policies and procedures, access control, networking, backup data, security patches, etc. This is a Cloud Information Security Checklist To Implement Cloud Security In Business Ppt Ideas Background Image PDF template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Access Control, Data Encryption, Policies And Procedures. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Security Assessment Checklist To Implement Cloud Security In Business Ideas PDF
This slide shows the checklist to implement cloud security in business, including policies and procedures, access control, networking, backup data, security patches, etc.This is a Cloud Security Assessment Checklist To Implement Cloud Security In Business Ideas PDF template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Access Control, Data Encryption, Logging And Monitoring You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Information Security Cloud Security Checklist Policies And Procedures Ppt Inspiration Objects PDF
This slide depicts the policies and procedures of the cloud security checklist. It also represents how it is essential to create new and update the current policies in an organization. Presenting Cloud Information Security Cloud Security Checklist Policies And Procedures Ppt Inspiration Objects PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Implement Policies, Protect Data, Security Procedures. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Ensuring Checklist For Mobile Security Deployment Business Mobile Device Security Management Sample PDF
This slide provides information regarding mobile device security deployment checklist in terms of device security, protection against malicious codes. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Ensuring Checklist For Mobile Security Deployment Business Mobile Device Security Management Sample PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
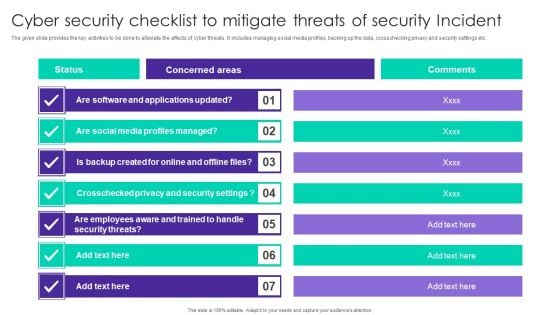
Cyber Security Checklist To Mitigate Threats Of Security Incident Ppt Model Example PDF
The given slide provides the key activities to be done to alleviate the effects of cyber threats. It includes managing social media profiles, backing up the data, crosschecking privacy and security settings etc. Showcasing this set of slides titled Cyber Security Checklist To Mitigate Threats Of Security Incident Ppt Model Example PDF. The topics addressed in these templates are Concerned Areas, Social Media Profiles, Security Threats. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
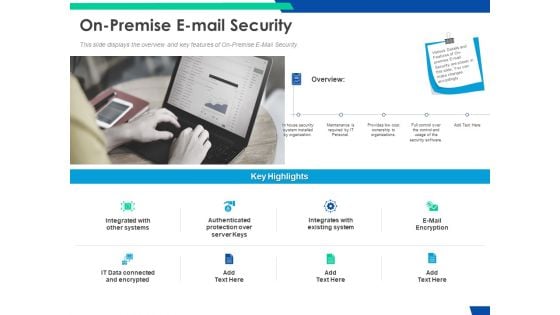
Cloud Based Email Security Market Report On Premise E Mail Security Ppt Ideas Design Inspiration PDF
This slide displays the overview and key features of On Premise E Mail Security. This is a cloud based email security market report on premise e mail security ppt ideas design inspiration pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like on premise e mail security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
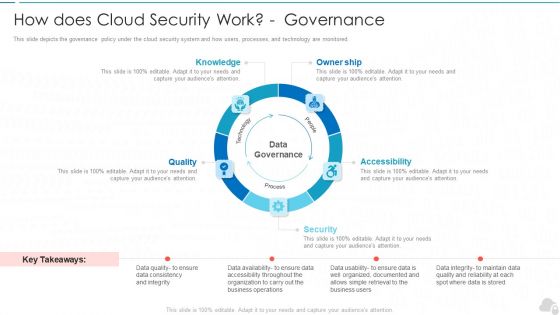
How Does Cloud Security Work Governance Cloud Computing Security IT Ppt Layouts Structure PDF
This slide depicts the governance policy under the cloud security system and how users, processes, and technology are monitored. This is a how does cloud security work governance cloud computing security it ppt layouts structure pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like knowledge, owner ship, quality, security, accessibility. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Security Checklist Policies And Procedures Cloud Computing Security IT Ppt Layouts Show PDF
This slide depicts the policies and procedures of the cloud security checklist. It also represents how it is essential to create new and update the current policies in an organization. This is a cloud security checklist policies and procedures cloud computing security it ppt layouts show pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like implement policies, cloud security, organization, policy violation. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
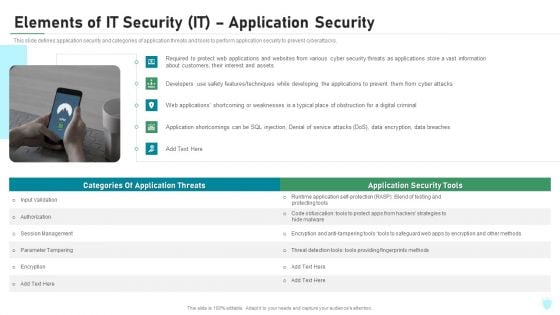
Elements Of IT Security IT Application Security Ppt Layouts Ideas PDF
This slide defines application security and categories of application threats and tools to perform application security to prevent cyberattacks. This is a elements of it security it application security ppt layouts ideas pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like management, encryption, authorization, techniques, cyber attacks. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
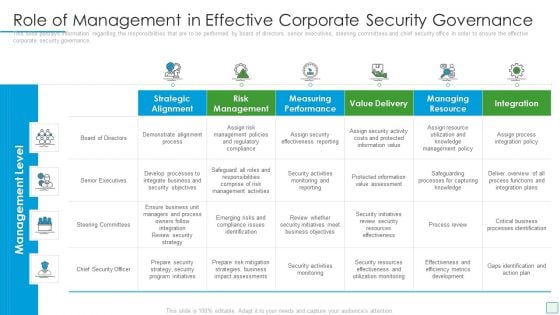
Developing Firm Security Strategy Plan Role Of Management In Effective Corporate Security Governance Slides PDF
This slide portrays information regarding the responsibilities that are to be performed by board of directors, senior executives, steering committees and chief security office in order to ensure the effective corporate security governance. Deliver an awe inspiring pitch with this creative developing firm security strategy plan role of management in effective corporate security governance slides pdf bundle. Topics like strategic alignment, risk management, measuring performance, value delivery, managing resource can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Developing Firm Security Strategy Plan Addressing Physical Security At Workplace Ideas PDF
This slide provides information about physical security at workplace in terms of workplace surveillance, employee monitoring, and factors to consider while implementing physical security such as industry guidelines, authority codes. Presenting developing firm security strategy plan addressing physical security at workplace ideas pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like workplace surveillance, employee monitoring. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
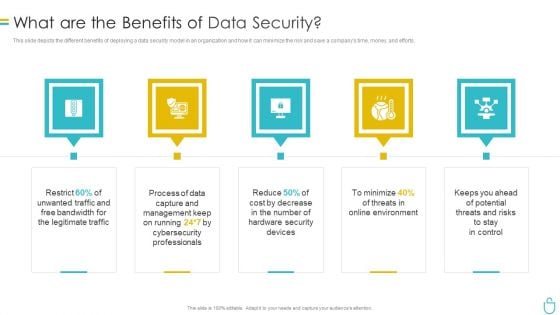
Information Security What Are The Benefits Of Data Security Ppt Infographics Example Topics PDF
This slide depicts the different benefits of deploying a data security model in an organization and how it can minimize the risk and save a companys time, money, and efforts. Presenting information security what are the benefits of data security ppt infographics example topics pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like management, hardware security, devices, environment, risks. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.


 Continue with Email
Continue with Email

 Home
Home


































